STEM(MITRE) CTF: Cyber Challenge 2019
Contents
Binary RE
In Plain Text
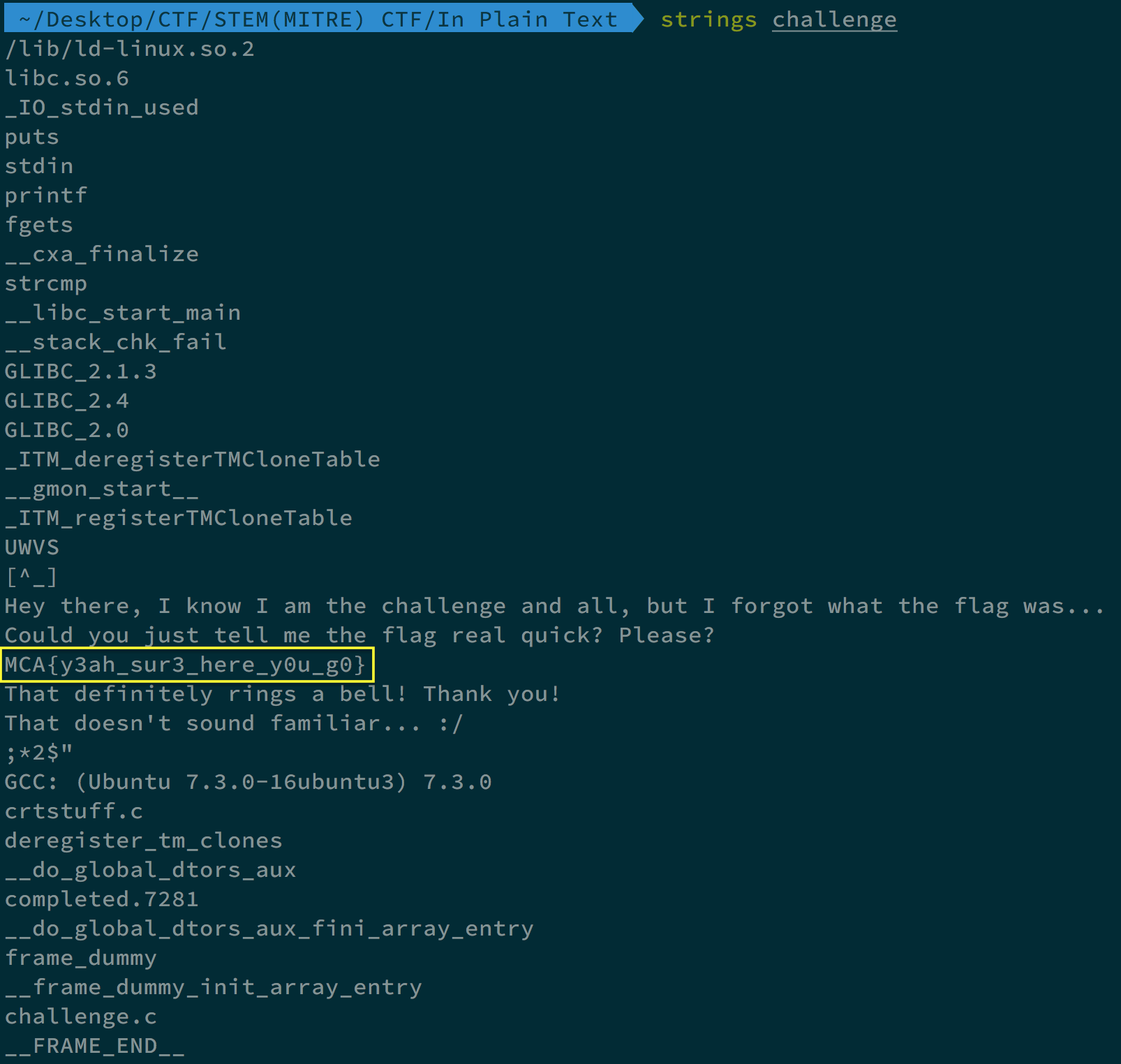
We got a file called “challenge”. By using strings challenge command, we can see the flag.
Web
TODO
When connecting to http://138.247.13.110, we can see as follows:
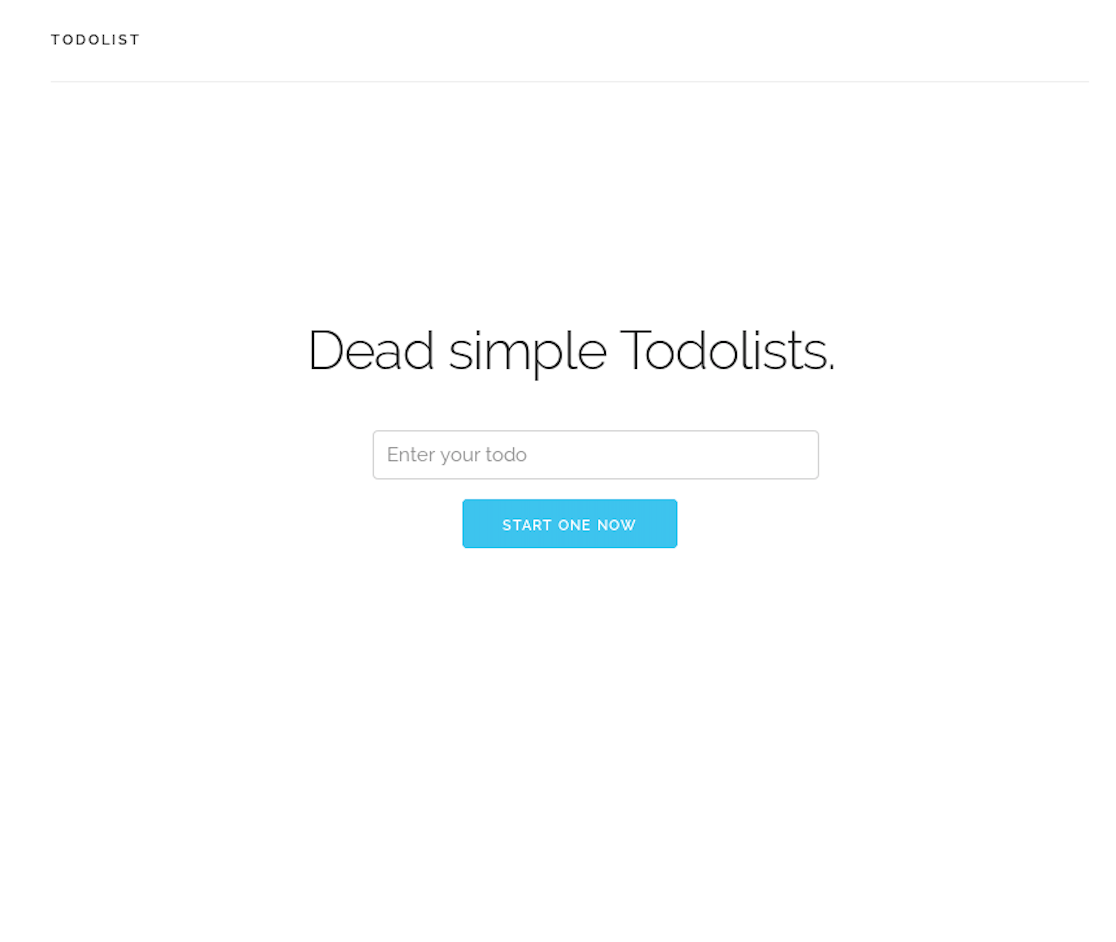
If we type anything in the box and press “START ONE NOW”, we will connect to http://138.247.13.110/todolist/1000, and seems like it is other’s todolist, by changing the number in the URL such as http://138.247.13.110/todolist/23, we can more todolist.
I used OWASP ZAP fuzzer to look for string matching flag or MCA in the content of the website from number 0 to 1000, and got MCA{al3x4_5et_a_r3minder} in the website http://138.247.13.110/todolist/678/
Grab Bag
Nomination
In this challenge, we are given the following picture.

By using Stegsolve, we can get the flag MCA{g1jVx4a2zcpoZx2q}.

Linux
Clean Room
When we ssh to ctf@138.247.13.108, the commands we can use are restricted. By commanding echo $SHELL, it shows that we are using the restricted bash - rbash.
I used ssh ctf@138.247.13.108 -t bash to make myself log in and got bash, and finally got the flag MCA{ieHaisoh4eif2ae} in a directory called root.
Author L3o
LastMod 2019-02-27