HackCon 2019
Contents
Steganography
Small icon much wow
We got an image stego.jpg.

By using binwalk, we see that there is another .jpg file in it.
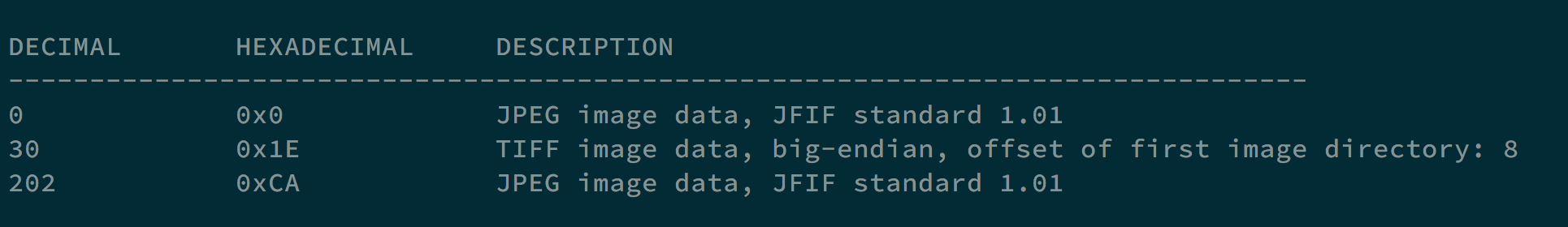
Using command dd if=stego.jpg of=stego1.jpg skip=202 bs=1, we can get the hidden image.

Accessing the QR code, we got the flag d4rk{flAg_h1dd3n_1n_th3_thumbnail}c0de.
Crypto
OTP
hackerman is so dank that he decided to play around with OTPs.
he did the following:
message1 ^ key = cipher1
message2 ^ key = cipher2
He gives you cipher1 and cipher2 and challenges you to find the concatenation of messages 1 and 2.
Are you dank enough to find this?
Oh and also, ‘meme’ is so popular that hackerman used the word in both his messages.
cipher1 is ‘\x05F\x17\x12\x14\x18\x01\x0c\x0b4’
cipher2 is ‘>\x1f\x00\x14\n\x08\x07Q\n\x0e’
Both without quotes
cipher1 ^ cipher2 = message1 ^ message2
Executing the program below, and we can find the flag d4rk{meme__meme}c0de.
|
|
Pwn
baby b0f
We got a 64-bit executable q1.
Using ghidra, we can decompile its main function.
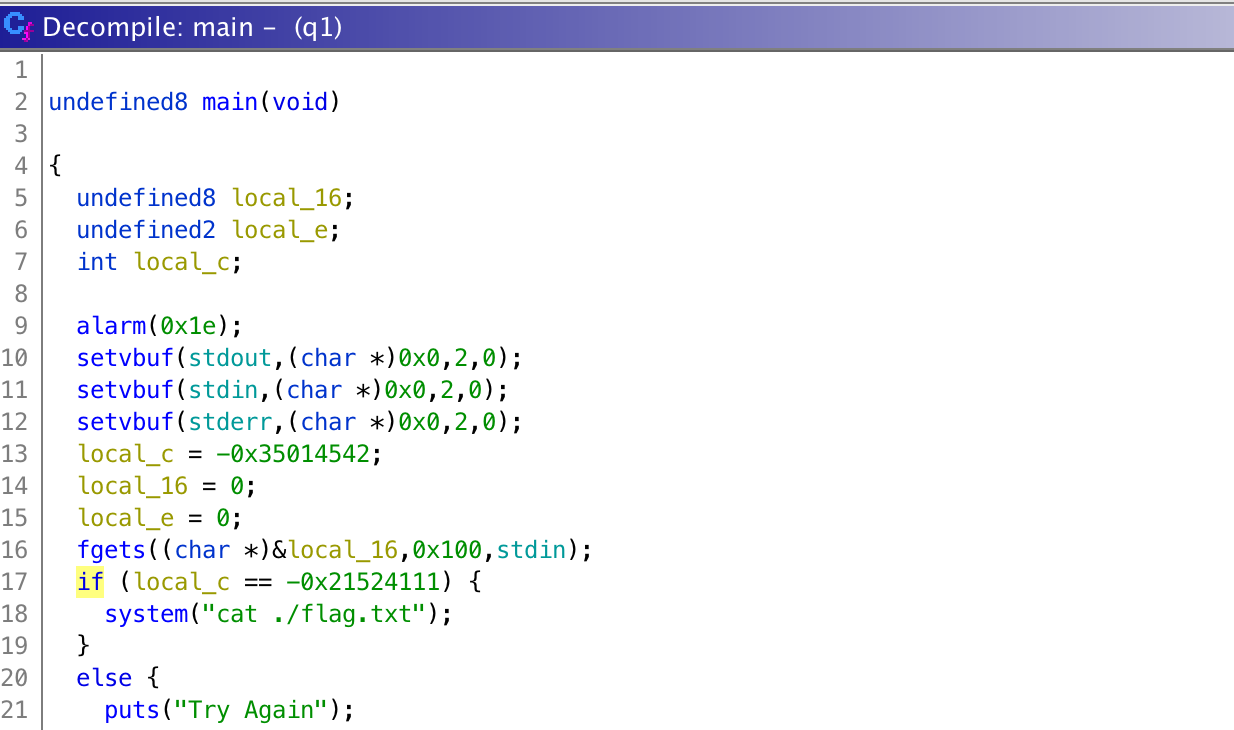
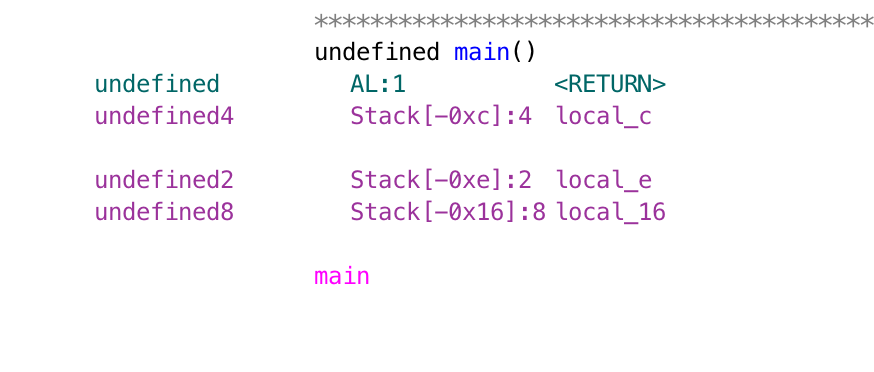
If we make local_c to the value, which is 0xdeadbeef, we can get the flag d4rk{W3lc0me_t0_th3_w0rld_0f_pwn}c0de.
|
|
Author L3o
LastMod 2019-08-24