WPICTF 2020
Contents
Recon
inspector
my sources tell me that the flag might be at wpictf.xyz
In https://wpictf.xyz source code, there is a comment <!-- If you are looking for a WPI{FLAG}, you CANT be a robot! -->.
We take a look at https://wpictf.xyz/robots.txt, and there is User-agent: * Disallow: /inspector.txt.
Access https://wpictf.xyz/inspector.txt, and it gives us I heard that the WPICSC club webpage may be of use to you..
Read source code in https://web.cs.wpi.edu/~csc/index.html, and we see a comment <!-- VGhpcyBzaXRlIGlzIHB1cmVseSBpbmZvcm1hdGlvbi4gQnV0IHdlIGFwcHJlY2 lhdGUgdGhlIGVmZm9ydCBkZWNvZGluZyB0aGlzLg== -->, but after decoding it with base64, we get This site is purely information. But we appreciate the effort decoding this..
After further investigation in the source code, we get another comment <!-- Check out our prizes-->.
Access https://ctf.wpictf.xyz/prizes, and we can see the flag WPI{1nsp3ct0r_H@ck3R} in the comment.
dns_wizard
Can you find it?
Run dig wpictf.xyz TXT, and we can see a base64 encoded string V1BJezFGMHVuZF9UaDNfRE5TLXJlY29yZH0=.
After running echo -n "V1BJezFGMHVuZF9UaDNfRE5TLXJlY29yZH0=" | base64 -D, we can get the flag WPI{1F0und_Th3_DNS-record}.
hellofellowchallengers
The flag could be any one of us! He could be in this very room… He could be you! He could be me! He could even be…
I create a script to get the strings containing wpi, flag, or fellow in teams particpating WPICTF.
|
|
And we can get <a href="/teams/568">WPI{the_best_teams_make_the_flags}</a>, which contains our flag.
Reverse
danger-Live-and-Malicious-Code
Like the title says, this challenge is dangerous and contains live malware.
We get a html contains javascript. Use JS Nice to give it a better look.
|
|
We deleted the line with popupWindow and execute it, since with the for loop at the end of the file, it will give us infinite popup windows.
c, d, and e are strings. When we concat them, we can see the flag WPI{Oh_nose_procoding_detected}.
Linux
Suckmore Shell 2.0
After its abysmal performance at WPICTF 2019, suckmore shell v1 has been replaced with a more secure, innovative and performant version, aptly named suckmore shell V2.
After we ssh into smsh@smsh.wpictf.xyz, we use ls to see the flag.
Execute more flag, and we can get the flag WPI{SUckmoreSoftwareN33dz2G3TitTogeTHER}.
Web
👉😎👉
👈😎👈Zoop👉😎👉Zoop…
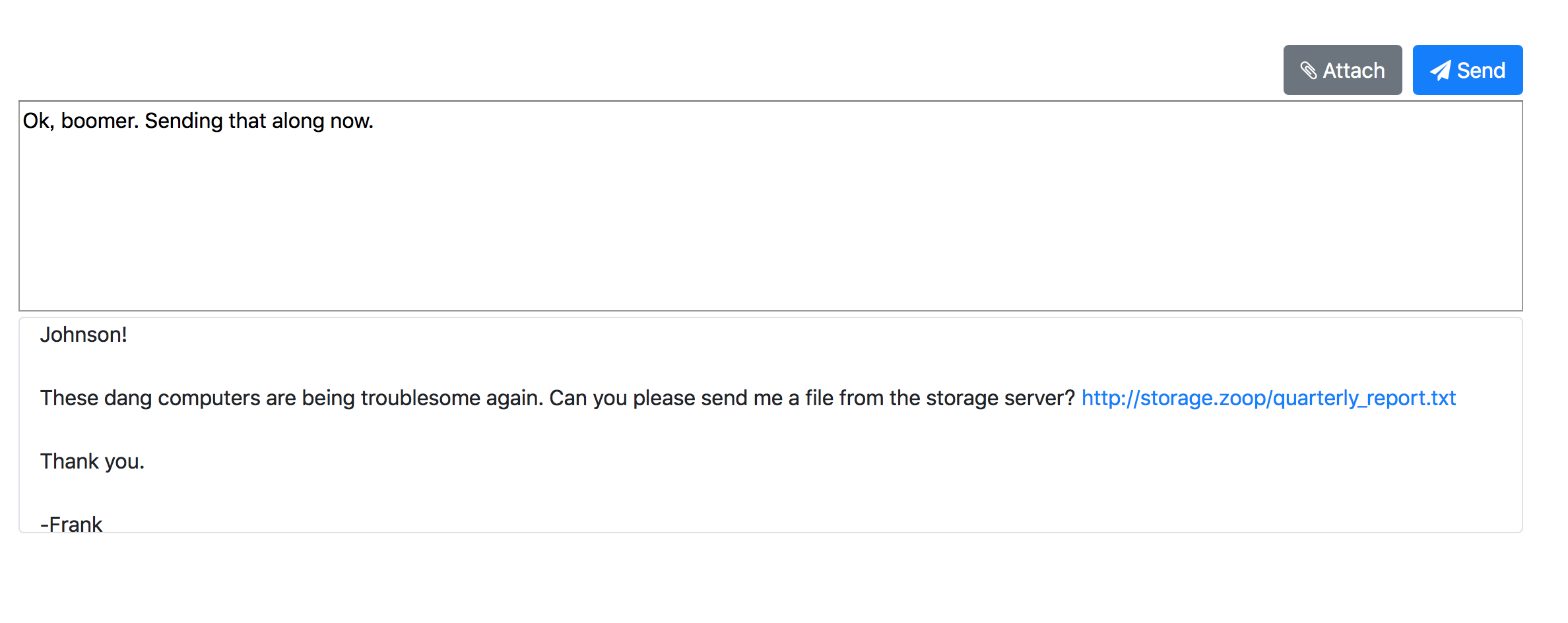
On the website, Frank said we need to send a file to him. So we press Attach.
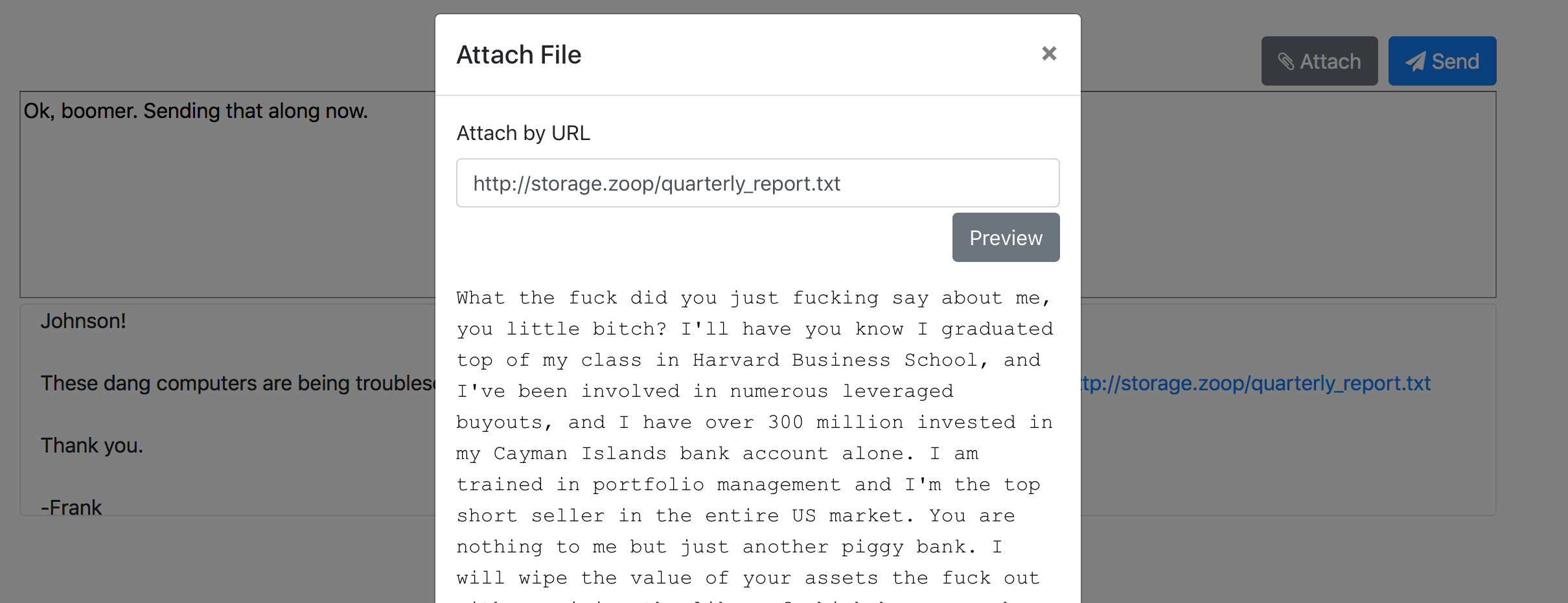
In this window, we can preview the text in a given file. Change the url to http://storage.zoop/flag.txt , and we can see the flag WPI{tH4nKs_z00m3r_jh0n50n}.
dorsia2
Firefox doesnt like the page… try chromium.
We get the source code to this challenge from a video.
|
|
Using Burp Suite to modify the request of the website to the following.
|
|
And we can get the flag WPI{1_H4VE_2_return_SOME_VIDE0TAP3S}.
autograder
A prof made a little homework grader at https://autograder.wpictf.xyz/ but I heard he is hiding a flag at /home/ctf/flag.txt
It tells us to enter our code and solve the problem, but actually, we don’t need to care about it.
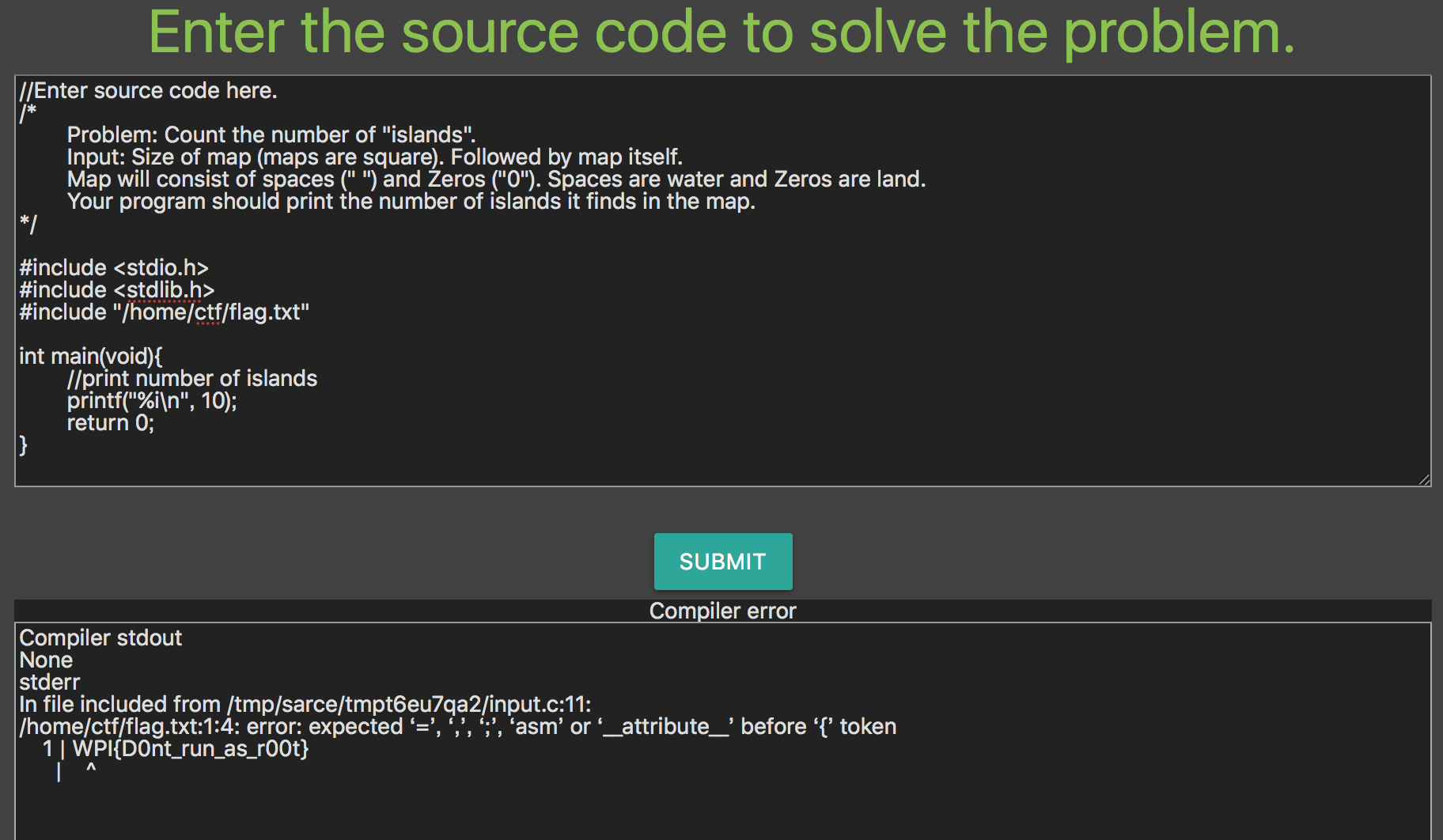
Add include "/home/ctf/flag.txt" to the code, we will get error message, and it contains the flag WPI{D0nt_run_as_r00t}.
Pwn
dorsia3
nc dorsia3.wpictf.xyz 31337 or 31338 or 31339
We are given the source code, the executable, and its libc libc.so.6.
|
|
It is a problem of format string vulnerability with printf.
First, we get the address of a and system - 288, from gdb, we can see that the return address is at a + 113.
Use one_gadget to find useful gadgets. We get one in libc.so.6 at 0x3d0e0.
The address of system is at 0x3d200 in libc.so.6, we can have our gadget address at run time with (system - 288) + 288 - 0x3d200 + 0x3d0e0.
With both the address of return address and our gadget, we can get the shell by sending format string vulnerability payload.
|
|
After we get the shell, we can get the flag WPI{Th3re_is_an_idea_of_4_Pa7rick_BatemaN}.
Author L3o
LastMod 2020-04-21