Overthewire Semtex Wargame
Contents
Description:
You have to solve Semtex 0 to get a username/password for login. Once logged in, you have to make your way from one level to the next, each one containing a small security hole/feature that has been installed for you. Your mission is to find out how to exploit the weakness and to cause interesting behavior :)
Level 0
semtex.labs.overthewire.org
Receive data until the port is closed.
Every second byte you receive is trash, ignore it. The other bytes are an executable that shows you the password.
Then login to semtex1@semtex.labs.overthewire.org on port 2229
| x86/elf: | amd64/elf: | ppc/mach-O: |
|---|---|---|
| Connect to port 24000 | Connect to port 24001 | Connect to port 24002 |
I use a python program to discard every second byte, and save every first byte to a file named hello. When we execute it, we can get the password B#4j%XXc.
|
|
Level 0 -> Level 1
A password has been crypted using the /semtex/semtex1 tool. The crypted password is HRXDZNWEAWWCP. You have to reverse engineer the algorithm and decrypt the password. You might try the -v switch for encrypt.
The ciphertext given to us is HRXDZNWEAWWCP, which contains 13 characters. If we execute /semtex/semtex1 AAAAAAAAAAAAA, we can get the ciphertext AXMDNNPKTEKUL. And replace AAAAAAAAAAAAA with BAAAAAAAAAAAA, we can get AXMDNNPKTELUL, it seems that the 11th character has added 1. We can get the similar effect on other characters and positions with ABAAAAAAAAAAA, AABAAAAAAAAAA etc.
I write a python program to count the offset for us.
|
|
And we can get the plaintext, MUESLIMUHAHAH, which is also the password.
Level 1 -> Level 2
This program checks your user ID.
Perhaps you can trick it, so that it thinks you have a different one.
Think dynamically.
When we execute /semtex/semtex2, it will tell us
EUID == 6002
This is not the devils number. Think dynamically!
When we do ltrace, we can make sure that it uses geteuid() to get EUID. We can use function hooking in this challenge.
|
|
After we run gcc -m32 -fPIC -c hookid.c, ld -shared -m elf_i386 -o hookid.so hookid.o -ldl, and LD_PRELOAD="./hookid.so" /semtex/semtex2, we can get the password jJjl2Msl.
Level 2 -> Level 3
You are almost on Semtex 3, there is just one big door before you. It is locked with a number lock. Analyze and use the locks in /semtex/semtex3 to adjust all the numbers in the correct way. They will open your way to the next level.
Tip : If you are not good at math, you should consider brute force. Rewrite the program and try all possible combinations of the locks. It wont take more than a few seconds ;)
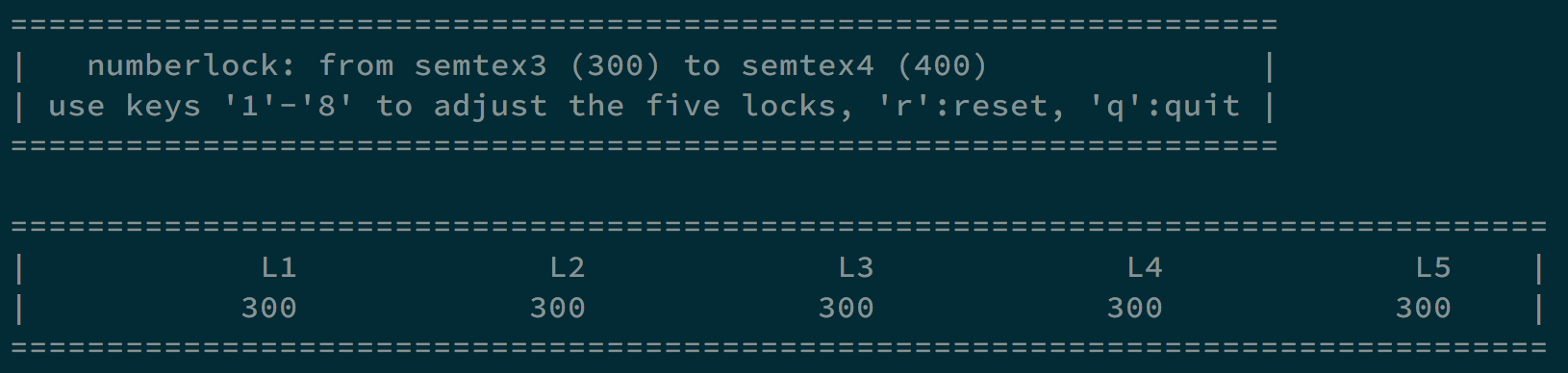
After we tried every key, we can get the information about how each key interact with every lock. e.g. for key 1, it adds 5 on lock 1, adds 2 on lock 2, adds 1 on lock 3, adds 7 on lock 4, and adds 5 on lock 5.
We need to make every lock from 300 to 400, so we can brute force with different combinations of keys.
|
|
Finally, we can get the combination 1,1,2,2,2,3,4,5,5,5,6,7,7, which can make every lock to 400 and give us shell.
We can get the flag in /etc/semtex_pass/semtex4, which is d%kj1//...
Level 3 -> Level 4
Pass prints the password for the level you are on. Try to make it print the next level’s password. This time it is not so easy:
When we execute /semtex/semtex4, it gives us your password is d%kj1//... If we use strace, we can see that it uses geteuid to get id. However, since this program is statically linked, we cannot use function hooking.
We need to use ptrace this time.
|
|
It creates a child process to execute /semtex/semtex4, and the parent process trace its syscall. If the child process is executing geteuid, it will put 6005, which is the id of semtex5, to the output. In this way, we can make our euid to 6005 and get the password HELICOTRMA.
Level 4 -> Level 5
Make 10 connections to port 24027 from different IP’s. On each connection you will receive a string of 10 ASCII characters. XOR this string with the Semtex5 password, character by character. Then send back the 10 characters followed by another string of exactly 10 characters which identifies you (can be anything within A-Z, a-z, 0-9). The first 10 characters that you send, are different on every connection, the last 10 have to be the same. If you do not send the correct string back within 5 seconds you are disconnected. Once connected with at least 10 different IP’s You will receive the password on one connection, chosen randomly.
**Note: Your connections time out in 2 minutes and you cannot connect from an IP that is still connected. May the sockets be with you. **
For this challenge, we need to use multi-thread because the password will be sent on random connection after all connection got the right answer.
|
|
We put the connection part in function challenge. First, we create 10 threads, each thread executes challenge with different IP addresses. Once they sent the answer back to the server, they will sleep for 15 seconds to wait for other threads. One of the connection can get the password again_mue5li at the end.
Level 5 -> Level 6
Not open yet.
Author L3o
LastMod 2019-11-26